Artificial Intelligence Algorithms for Malware Detection in Android-Operated Mobile Devices
Abstract
:1. Introduction
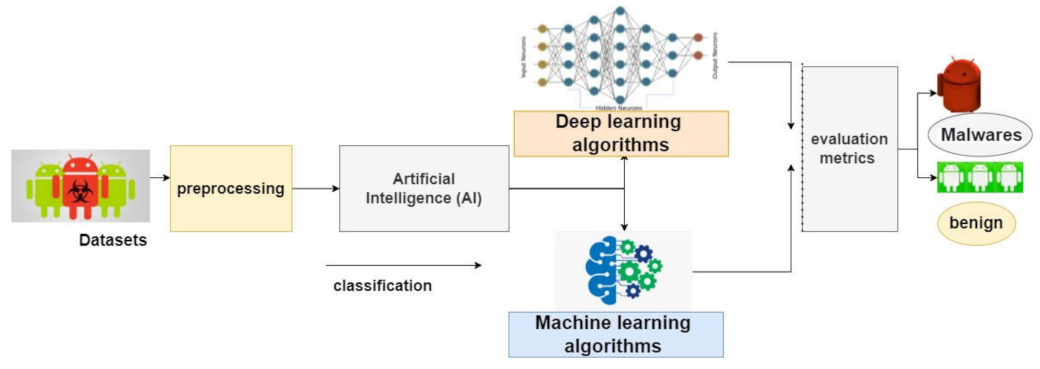
- The development of intrusion detection in the Android system using various machine learning and deep learning algorithms.
- The proposed system was tested and evaluated using two standard Android datasets.
- A comparison between the tested algorithms and different state-of-the-arts models is presented.
- The sensitivity analysis was used to find significant relationships between dataset features and the proposed classes of the datasets.
2. Background of Study
3. Materials and Methods
- (1)
- What are the appropriate machine learning and deep learning algorithms to detect malware in Android?
- (2)
- What are the validation accuracy, robustness, and efficiency of the proposed machine learning and deep learning models related to the detection of Android malware?
3.1. Android Dataset
3.1.1. CICAndMal2017
3.1.2. The Drebin Dataset
3.2. Preprocessing
Min–Max Normalization Method
3.3. Classification Algorithms
3.3.1. K-Nearest Neighbors (KNN)
3.3.2. Support Vector Machine (SVM)
3.3.3. Linear Discriminant Analysis (LDA)
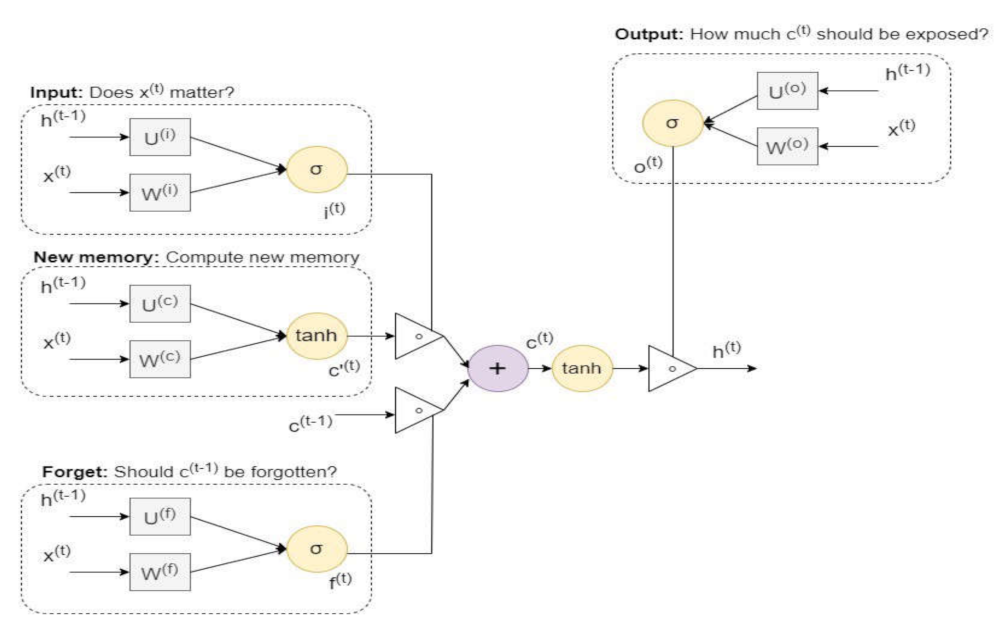
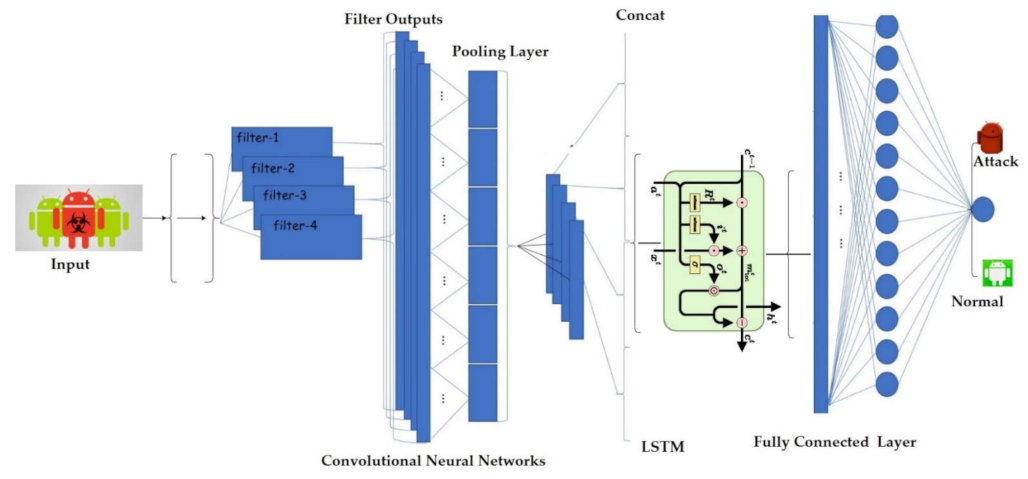
3.3.4. Deep Learning Models
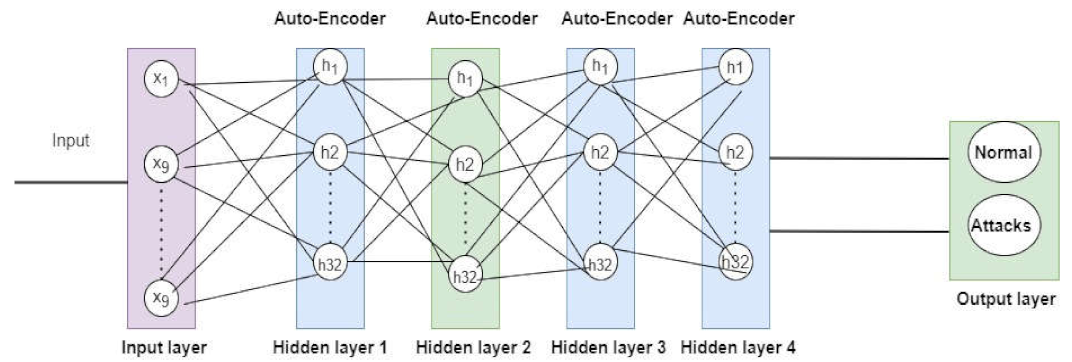
3.3.5. Autoencoder (AE)
3.4. Performance Measurements
4. Results
4.1. Splitting the Data
4.2. Experimental Environments
4.3. Model Performance
4.3.1. Performance of the Machine Learning Models
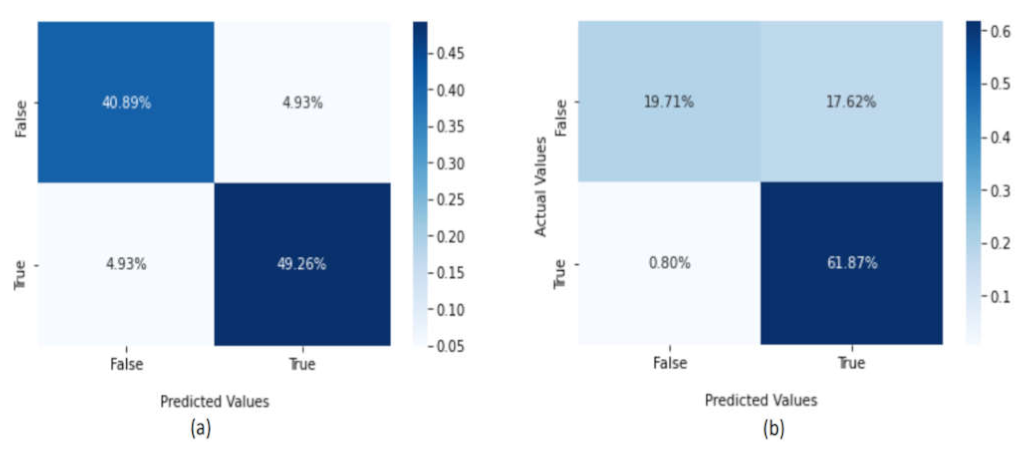
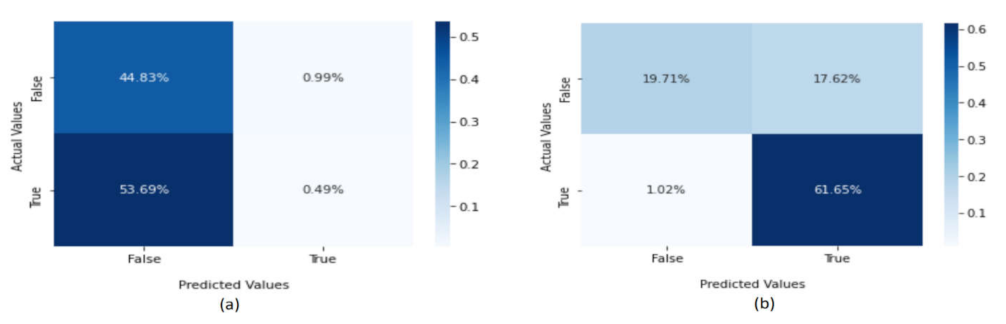
4.3.2. Performance of the Deep Learning Models
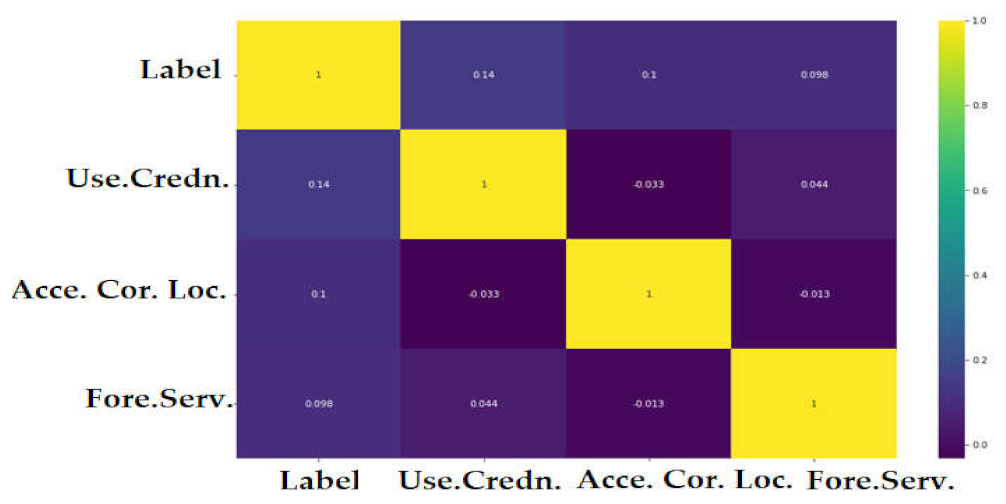
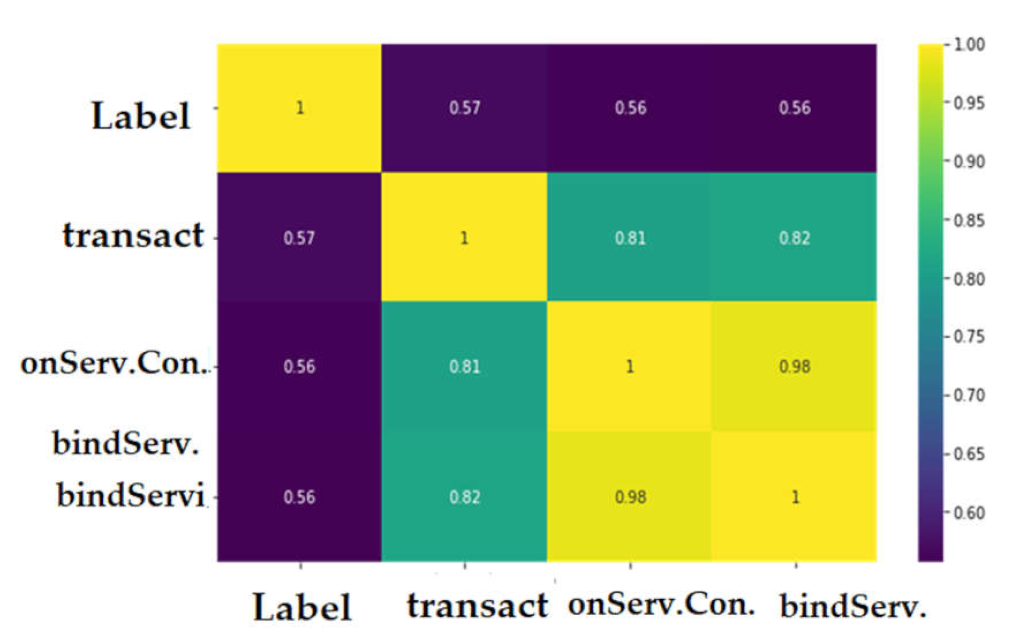
4.4. Sensitivity Analysis
5. Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- McAfee Mobile Threat Report Q1. 2020. Available online: https://www.mcafee.com/en-us/consumer-support/2020-mobilethreat-report.html (accessed on 2 December 2021).
- Yerima, S.Y.; Khan, S. Longitudinal Performance Analysis of Machine Learning based Android Malware Detectors. In Proceedings of the 2019 International Conference on Cyber Security and Protection of Digital Services (Cyber Security), Oxford, UK, 3–4 June 2019. [Google Scholar]
- Grill, B.B.; Ruthven, M.; Zhao, X. “Detecting and Eliminating Chamois, a Fraud Botnet on Android” Android Developers Blog. March 2017. Available online: https://android-developers.googleblog.com/2017/03/detecting-and-eliminating-chamois-fraud.html (accessed on 12 December 2021).
- Clarke, E.; Emerson, E.; Sistla, A. Automatic verification of finite-state concurrent systems using temporal logic specifications. ACM Trans. Program. Lang. Syst. 1986, 8, 244–263. [Google Scholar] [CrossRef]
- Andersen, J.R.; Andersen, N.; Enevoldsen, S.; Hansen, M.M.; Larsen, K.G.; Olesen, S.R.; Srba, J.; Wortmann, J.K. CAAL: Concurrency workbench, Aalborg edition. In Proceedings of the Theoretical Aspects of Computing—ICTAC 2015—12th International Colloquium, Cali, Colombia, 29–31 October 2015; Springer: Cham, Switzerland, 2015; pp. 573–582. [Google Scholar]
- Alothman, B.; Rattadilok, P. Android botnet detection: An integrated source code mining approach. In Proceedings of the 12th International Conference for Internet Technology and Secured Transactions (ICITST), Cambridge, UK, 11–14 December 2017; pp. 111–115. [Google Scholar]
- Haystack. Mobile Issues. Available online: https://safeguarde.com/mobile-apps-stealing-your-information/ (accessed on 14 January 2022).
- AV-TEST. Security Institute. Available online: https://www.av-test.org/en/statistics/malware/ (accessed on 14 January 2022).
- Alzahrani, A.J.; Ghorbani, A.A. Real-Time Signature-Based Detection Approach For Sms Botnet. In Proceedings of the 2015 13th Annual Conference on Privacy, Security and Trust (PST), Izmir, Turkey, 21–23 July 2015; pp. 157–164. [Google Scholar]
- Girei, D.A.; Shah, M.A.; Shahid, M.B. An Enhanced Botnet Detection Technique For Mobile Devices Using Log Analysis. In Proceedings of the 2016 22nd International Conference on Automation and Computing (ICAC), Colchester, UK, 7–8 September 2016; pp. 450–455. [Google Scholar]
- Gilski, P.; Stefanski, J. Android OS: A Review. Tem. J. 2015, 4, 116. Available online: https://www.temjournal.com/content/41/14/temjournal4114.pdf (accessed on 19 May 2021).
- Android Developers. Privacy in Android 11. Available online: https://developer.android.com/about/versions/11/privacy (accessed on 10 January 2022).
- Syarif, A.R.; Gata, W. Intrusion Detection System Using Hybrid Binary PSO and K-Nearest Neighborhood Algorithm. In Proceedings of the 2017 11th International Conference on Information & Communication Technology and System (ICTS), Surabaya, Indonesia, 31 October 2017; pp. 181–186. [Google Scholar]
- Huanran., W.; Hui, H.; Weizhe, Z. Demadroid: Object Reference Graph-Based Malware Detection in Android. Secur. Commun. Netw. 2018, 2018, 7064131. [Google Scholar]
- LeCun, Y.; Bengio, Y.; Hinton, G. Deep learning. Nature 2015, 521, 436–444. [Google Scholar] [CrossRef] [PubMed]
- Liu, K.; Xu, S.; Xu, G.; Zhang, M.; Sun, D.; Liu, H. A Review of Android Malware Detection Approaches Based on Machine Learning. IEEE Access 2020, 8, 124579–124607. [Google Scholar] [CrossRef]
- Goeschel, K. Reducing False Positives In Intrusion Detection Systems Using Data-Mining Techniques Utilizing Support Vector Machines, Decision Trees, And Naive Bayes for Off-Line Analysis. In Proceedings of the SoutheastCon 2016, Norfolk, VA, USA, 30 March–3 April 2016; pp. 1–6. [Google Scholar]
- Kuttranont, P.; Boonprakob, K.; Phaudphut, C.; Permpol, S.; Aimtongkhamand, P.; KoKaew, U.; Waikham, B.; So-In, C. Parallel KNN and Neighborhood Classification Implementations on GPU for Network Intrusion Detection. J. Telecommun. Electron. Comput. Eng. (JTEC) 2017, 9, 29–33. [Google Scholar]
- Mehedi, S.T.; Anwar, A.; Rahman, Z.; Ahmed, K. Deep Transfer Learning Based Intrusion Detection System for Electric Vehicular Networks. Sensors 2021, 21, 4736. [Google Scholar] [CrossRef]
- Kalash, M.; Rochan, M.; Mohammed, N.; Bruce, N.D.B.; Wang, Y.; Iqbal, F. Malware Classification with Deep Convolutional Neural Networks. In Proceedings of the 2018 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 26–28 February 2018; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2018; pp. 1–5. [Google Scholar]
- Diro, A.; Chilamkurti, N. Leveraging LSTM networks for attack detection in fog-to-things communications. IEEE Commun. Mag. 2018, 56, 124–130. [Google Scholar] [CrossRef]
- Čeponis, D.; Goranin, N. Investigation of Dual-Flow Deep Learning Models LSTM-FCN and GRU-FCN Efficiency against Single-Flow CNN Models for the Host-Based Intrusion and Malware Detection Task on Univariate Times Series Data. Appl. Sci. 2020, 10, 2373. [Google Scholar] [CrossRef] [Green Version]
- Alrawashdeh, K.; Purdy, C. Toward an Online Anomaly Intrusion Detection System Based On Deep Learning. In Proceedings of the 2016 15th IEEE International Conference on Machine Learning and Applications (ICMLA), Anaheim, CA, USA, 18–20 December 2016; pp. 195–200. [Google Scholar]
- Hojjatinia, S.; Hamzenejadi, S.; Mohseni, H. Android Botnet Detection using Convolutional Neural Networks. In Proceedings of the 2020 28th Iranian Conference on Electrical Engineering (ICEE), Tabriz, Iran, 4–6 August 2020. [Google Scholar]
- Farnaaz, N.; Jabbar, M. Random forest modeling for network intrusion detection system. Procedia Comput. Sci. 2016, 89, 213–217. [Google Scholar] [CrossRef] [Green Version]
- Alkahtani, H.; Aldhyani, T.H.H. Botnet Attack Detection by Using CNN-LSTM Model for Internet of Things Applications. Secur. Commun. Netw. 2021, 2021, 3806459. [Google Scholar] [CrossRef]
- Min, E.; Long, J.; Liu, Q.; Cui, J.; Chen, W. TR-IDS: Anomaly-based intrusion detection through text-convolutional neural network and random forest. Secur. Commun. Netw. 2018, 2018, 4943509. [Google Scholar] [CrossRef] [Green Version]
- Zeng, Y.; Gu, H.; Wei, W.; Guo, Y. Deep—Full—Range: A Deep Learning Based Network Encrypted Traffic Classification and Intrusion Detection Framework. IEEE Access 2019, 7, 45182–45190. [Google Scholar] [CrossRef]
- Alkahtani, H.; Aldhyani, T.; Al-Yaari, M. Adaptive anomaly detection framework model objects in cyberspace. Appl. Bionics Biomech. 2020, 2020, 6660489. [Google Scholar] [CrossRef] [PubMed]
- Kadir, A.F.A.; Stakhanova, N.; Ghorbani, A.A. Android Botnets: What Urls Are Telling Us. In Proceedings of the International Conference on Network and System Security, New York, NY, USA, 3–5 November 2015; Springer: New York, NY, USA, 2015; pp. 78–91. [Google Scholar]
- Anwar, S.; Zain, J.M.; Inayat, Z.; Haq, R.U.; Karim, A.; Jabir, A.N. A Static Approach Towards Mobile Botnet Detection. In Proceedings of the 2016 3rd International Conference on Electronic Design (ICED), Phuket, Thailand, 11–12 August 2016; pp. 563–567. [Google Scholar]
- Alqatawna, J.F.; Faris, H. Toward a Detection Framework for Android Botnet. In Proceedings of the 2017 International Conference on New Trends in Computing Sciences (ICTCS), Amman, Jordan, 11–13 October 2017; pp. 197–202. [Google Scholar]
- Abdullah, Z.; Saudi, M.M.; Anuar, N.B. ABC: Android botnet classification using feature selection and classification algorithms. Adv. Sci. Lett. 2017, 23, 4717–4720. [Google Scholar] [CrossRef]
- Toldinas, J.; Venčkauskas, A.; Damaševičius, R.; Grigaliūnas, Š.; Morkevičius, N.; Baranauskas, E. A Novel Approach for Network Intrusion Detection Using Multistage Deep Learning Image Recognition. Electronics 2021, 10, 1854. [Google Scholar] [CrossRef]
- Karim, A.; Rosli, S.; Syed, S. DeDroid: A Mobile Botnet Detection Approach Based on Static Analysis. In Proceedings of the 7th International Symposium on UbiCom Frontiers Innovative Research, Systems and Technologies, Beijing, China, 10–14 August 2015. [Google Scholar]
- The Drebin Dataset. Available online: https://www.sec.cs.tu-bs.de/~danarp/drebin/index.html (accessed on 28 December 2021).
- Deng, L. A tutorial survey of architectures, algorithms, and applications for deep learning. APSIPA Trans. Signal Inf. Process. 2014, 3, e2. [Google Scholar] [CrossRef] [Green Version]
- Berman, D.S.; Buczak, A.L.; Chavis, J.S.; Corbett, C.L. A survey of deep learning methods for cyber security. Information 2019, 10, 122. [Google Scholar] [CrossRef] [Green Version]
- Yilmaz, S.; Sen, S. Early Detection of Botnet Activities Using Grammatical Evolution. In Applications of Evolutionary Computation; Springer International Publishing: Berlin/Heidelberg, Germany, 2019; pp. 395–404. [Google Scholar]
- Yu, Y.; Long, J.; Liu, F.; Cai, Z. Machine Learning Combining with Visualization For Intrusion Detection: A survey. In Proceedings of the International Conference on Modeling Decisions for Artificial Intelligence, Sant Julià de Lòria, Andorra, 19–21 September 2016; pp. 239–249. [Google Scholar]
- Ahmed, A.A.; Jabbar, W.A.; Sadiq, A.S.; Patel, H. Deep learning-based classification model for botnet attack detection. J. Ambient. Intell. Humaniz. Comput. 2020, 2020, 1–10. [Google Scholar] [CrossRef]
- Alauthman, M.; Aslam, N.; Al-kasassbeh, M.; Khan, S.; Al-Qerem, A.; Raymond Choo, K. An efficient reinforcement learning-based Botnet detection approach. J. Netw. Comput. Appl. 2020, 150, 102479. [Google Scholar] [CrossRef]
- Mazini, M.; Shirazi, B.; Mahdavi, I. Anomaly network-based intrusion detection system using a reliable hybrid artificial bee colony and AdaBoost algorithms. J. King Saud Univ. Comput. Inf. Sci. 2019, 31, 541–553. [Google Scholar] [CrossRef]
- Asadi, M.; Jabraeil Jamali, M.A.; Parsa, S.; Majidnezhad, V. Detecting botnet by using particle swarm optimization algorithm based on voting system. Future Gener. Comput. Syst. 2020, 107, 95–111. [Google Scholar] [CrossRef]
- Al Shorman, A.; Faris, H.; Aljarah, I. Unsupervised intelligent system based on one class support vector machine and Grey Wolf optimization for IoT botnet detection. J. Ambient Intell. Humaniz. Comput. 2020, 11, 2809–2825. [Google Scholar] [CrossRef]
- Lin, K.C.; Chen, S.Y.; Hung, J.C. Botnet Detection Using Support Vector Machines with Artificial Fish Swarm Algorithm. J. Appl. Math. 2014, 2014, 986428. [Google Scholar] [CrossRef]
- Chen, T.; Mao, Q.; Yang, Y.; Lv, M.; Zhu, J. TinyDroid: A lightweight and efficient model for Android malware detection and classification. Mob. Inf. Syst. 2018, 2018, 4157156. [Google Scholar] [CrossRef]
- Nisa, M.; Shah, J.H.; Kanwal, S.; Raza, M.; Khan, M.A.; Damaševičius, R.; Blažauskas, T. Hybrid malware classification method using segmentation-based fractal texture analysis and deep convolution neural network features. Appl. Sci. 2020, 10, 4966. [Google Scholar] [CrossRef]
- Amin, M.; Shah, B.; Sharif, A.; Ali, T.; Kim, K.l.; Anwar, S. Android malware detection through generative adversarial networks. Trans. Emerg. Telecommun. Technol. 2019, 33, e3675. [Google Scholar] [CrossRef]
- Arp, D.; Spreitzenbarth, M.; Hubner, M.; Gascon, H.; Rieck, K.; Siemens, C. Drebin: Effective and Explainable Detection Of Android Malware In Your Pocket. In Proceedings of the 2014 Network and Distributed System Security Symposium, San Diego, CA, USA, 23–26 February 2014. [Google Scholar]
- Google Play. Available online: https://play.google.com/ (accessed on 2 January 2022).
- VirusShare. Available online: https://virusshare.com/ (accessed on 2 January 2022).
- Intel Security/MacAfee. Available online: https://steppa.ca/portfolio-view/malware-threat-intel-datasets/ (accessed on 20 December 2021).
- Wandoujia App Market. Available online: https://www.wandoujia.com/apps (accessed on 2 January 2022).
- Google Playstore Appsin Kaggle. Available online: https://www.kaggle.com/gauthamp10/google-playstore-apps (accessed on 2 January 2022).
- CICMaldroid Dataset. Available online: https://www.unb.ca/cic/datasets/maldroid-2020.html (accessed on 2 January 2022).
- Alkahtani, H.; Aldhyani, T.H. Intrusion Detection System to Advance Internet of Things Infrastructure-Based Deep Learning Algorithma. Complexity 2021, 2021, 5579851. [Google Scholar] [CrossRef]
- Odusami, M.; Abayomi-Alli, O.; Misra, S.; Shobayo, O.; Damasevicius, R.; Maskeliunas, R. Android Malware Detection: A Survey. In Communications in Computer and Information Science, Proceedings of the International Conference on Applied Informatics, Bogota, Colombia, 1–3 November 2018; Springer: Cham, Switzerland, 2018; pp. 255–266. [Google Scholar]
- Yerima, S.Y.; Sezer, S. DroidFusion: A Novel Multilevel Classifier Fusion Approach for Android Malware Detection. IEEE Trans. Cyber. 2019, 49, 453–466. [Google Scholar] [CrossRef]
- Liu, G.; Zhao, H.; Fan, F.; Liu, G.; Xu, Q.; Nazir, S. An Enhanced Intrusion Detection Model Based on Improved kNN in WSNs. Sensors 2022, 22, 1407. [Google Scholar] [CrossRef]
- Aldallal, A.; Alisa, F. Effective Intrusion Detection System to Secure Data in Cloud Using Machine Learning. Symmetry 2021, 13, 2306. [Google Scholar] [CrossRef]
- Zheng, D.; Hong, Z.; Wang, N.; Chen, P. An Improved LDA-Based ELM Classification for Intrusion Detection Algorithm in IoT Application. Sensors 2020, 20, 1706. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Yann, L.; Yoshua, B. Convolutional Networks for Images, Speech, and Time-Series. Handb. Brain Theory Neural Netw. 1995, 10, 2571–2575. [Google Scholar]
- Rawat, W.; Wang, Z. Deep Convolutional Neural Networks for Image Classification: A Comprehensive Review. Neural Comput. 2017, 29, 2352–2449. [Google Scholar] [CrossRef]
- Hochreiter, S.; Schmidhuber, J. Long Short-Term Memory. Neural Comput. 1997, 9, 1735–1780. [Google Scholar] [CrossRef]
- Aldhyani, T.H.H.; Alkahtani, H. Attacks to Automatous Vehicles: A Deep Learning Algorithm for Cybersecurity. Sensors 2022, 22, 360. [Google Scholar] [CrossRef]
- Khan, M.A.; Khan, M.A.; Jan, S.U.; Ahmad, J.; Jamal, S.S.; Shah, A.A.; Pitropakis, N.; Buchanan, W.J. A Deep Learning-Based Intrusion Detection System for MQTT Enabled IoT. Sensors 2021, 21, 7016. [Google Scholar] [CrossRef]
- Tang, C.; Luktarhan, N.; Zhao, Y. SAAE-DNN: Deep Learning Method on Intrusion Detection. Symmetry 2020, 12, 1695. [Google Scholar] [CrossRef]
- Kunang, Y.N.; Nurmaini, S.; Stiawan, D.; Zarkasi, A.; Jasmir, F. Automatic Features Extraction Using Autoencoder in Intrusion Detection System. In Proceedings of the International Conference on Electrical Engineering and Computer Science (ICECOS), Pangkal Pinang, Indonesia, 2–4 October 2018; pp. 219–224. [Google Scholar]
- Ginocchi, M.; Ponci, F.; Monti, A. Sensitivity Analysis and Power Systems: Can We Bridge the Gap? A Review and a Guide to Getting Started. Energies 2021, 14, 8274. [Google Scholar] [CrossRef]
- Nasirzadehdizaji, R.; Balik Sanli, F.; Abdikan, S.; Cakir, Z.; Sekertekin, A.; Ustuner, M. Sensitivity Analysis of Multi-Temporal Sentinel-1 SAR Parameters to Crop Height and Canopy Coverage. Appl. Sci. 2019, 9, 655. [Google Scholar] [CrossRef] [Green Version]
- Millar, S.; McLaughlin, N.; del Rincon, J.M.; Miller, P. Multi-view deep learning for zero-day Android malware detection. J. Inf. Secur. Appl. 2021, 58, 102718. [Google Scholar] [CrossRef]
- Kapratwar, A.; Di Troia, F.; Stamp, M. Static and Dynamic Analysis of Android Malware; ICISSP: Porto, Portugal, 2017; pp. 653–662. [Google Scholar]
- Qaisar, Z.H.; Li, R. Multimodal information fusion for android malware detection using lazy learning. Multimed. Tools Appl. 2021, 2021, 1–15. [Google Scholar] [CrossRef]
- Salehi, M.; Amini, M.; Crispo, B. Detecting Malicious Applications Using System Services Request Behavior. In Proceedings of the 16th EAI International Conference on Mobile and Ubiquitous Systems: Computing, Networking and Services, Houston, TX, USA, 12–14 November 2019; pp. 200–209. [Google Scholar]
- Koli, J. RanDroid: Android Malware Detection Using Random Machine Learning Classifiers. In Proceedings of the 2018 Technologies for Smart-City Energy Security and Power (ICSESP), Bhubaneswar, India, 28–30 March 2018; pp. 1–6. [Google Scholar]
- Kabakus, A.T. What static analysis can utmost offer for Android malware detection. Inf. Technol. Control 2019, 48, 235–249. [Google Scholar] [CrossRef] [Green Version]
- Lou, S.; Cheng, S.; Huang, J.; Jiang, F. TFDroid: Android Malware Detection By Topics And Sensitive Data Flows Using Machine Learning Techniques. In Proceedings of the 2019 IEEE 2nd International Conference on Information and Computer Technologies (ICICT), Kahului, HI, USA, 14–17 March 2019; pp. 30–36. [Google Scholar]
- Onwuzurike, L.; Mariconti, E.; Andriotis, P.; Cristofaro, E.D.; Ross, G.; Stringhini, G. MaMaDroid: Detecting Android malware by building Markov chains of behavioral models (extended version). ACM Trans. Priv. Secur. (TOPS) 2019, 22, 1–34. [Google Scholar] [CrossRef] [Green Version]
- Zhang, H.; Luo, S.; Zhang, Y.; Pan, L. An efficient Android malware detection system based on method-level behavioral semantic analysis. IEEE Access 2019, 7, 69246–69256. [Google Scholar] [CrossRef]
- Meng, G.; Xue, Y.; Xu, Z.; Liu, Y.; Zhang, J.; Narayanan, A. Semantic Modelling Of Android Malware For Effective Malware Comprehension, Detection, and Classification. In Proceedings of the 25th International Symposium on Software Testing and Analysis, Saarbrücken, Germany, 18–20 July 2016; pp. 306–317. [Google Scholar]
- Vu, L.N.; Jung, S. AdMat: A CNN-on-Matrix Approach to Android Malware Detection and Classification. IEEE Access 2021, 9, 39680–39694. [Google Scholar] [CrossRef]
- Jannat, U.S.; Hasnayeen, S.M.; Shuhan, M.K.B.; Ferdous, M.S. Analysis and Detection Of Malware in Android Applications Using Machine Learning. In Proceedings of the 2019 International Conference on Electrical, Computer and Communication Engineering (ECCE), Cox’sBazar, Bangladesh, 7–9 February 2019; pp. 1–7. [Google Scholar]
- Xu, K.; Li, Y.; Deng, R.H.; Chen, K. Deeprefiner: Multi-Layer Android Malware Detection System Applying Deep Neural Networks. In Proceedings of the 2018 IEEE European Symposium on Security and Privacy (EuroS&P), London, UK, 24–26 April 2018; pp. 473–487. [Google Scholar]
- McLaughlin, N.; Martinez del Rincon, J.; Kang, B.; Yerima, S.; Miller, P.; Sezer, S.; Safaei, Y.; Trickel, E.; Zhao, Z.; Doupé, A.; et al. Deep Android Malware Detection. In Proceedings of the Seventh ACM on Conference on Data and Application Security and Privacy, Scottsdale, AZ, USA, 22–24 March 2017; pp. 301–308. [Google Scholar]




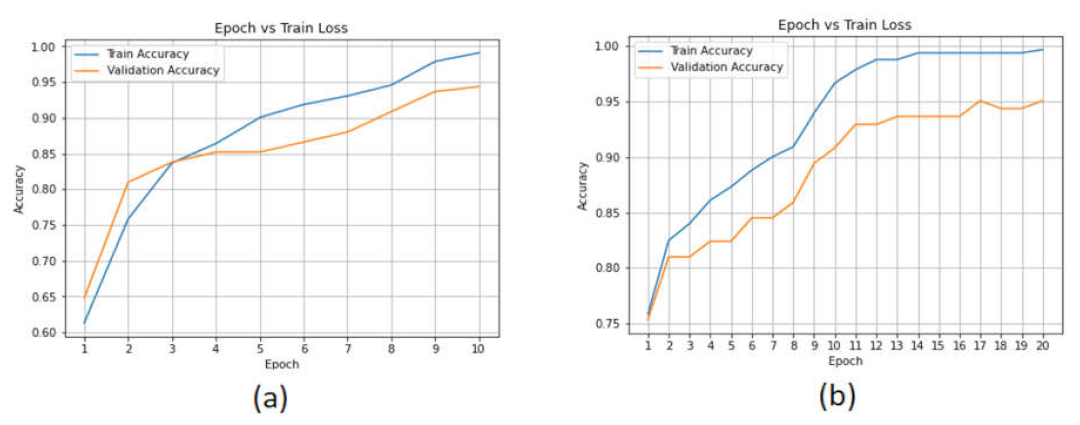

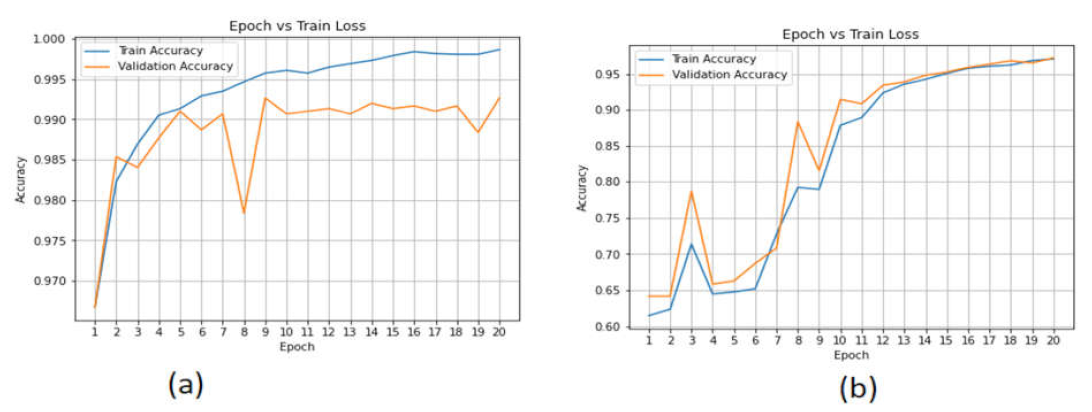
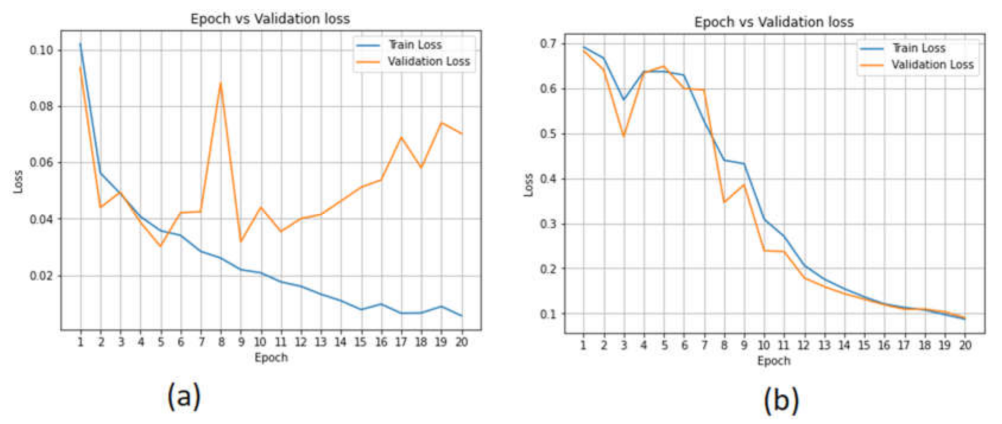
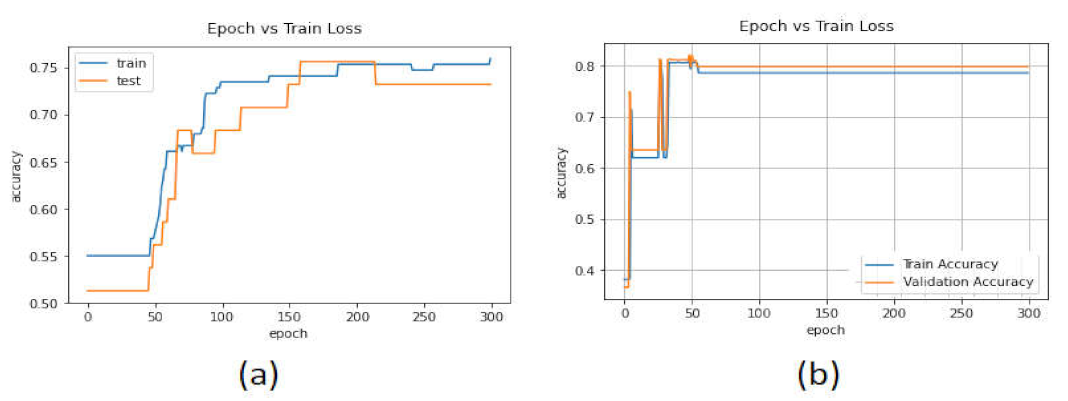


| Parameters | Values |
|---|---|
| Kernel size | 4 |
| Max pooling size | 4 |
| Drop out | 0.50 |
| Fully connected layer | 32 |
| Activation function | Relu |
| Optimizer | RSMprop |
| Epochs | 10, 20 |
| Batch size | 20 |
| Parameters | Values |
|---|---|
| Kernel size | 4 |
| Max pooling size | 4 |
| Drop out | 0.50 |
| Fully connected layer | 32 |
| Activation function | Relu |
| Optimizer | RSMprop |
| Epochs | 20 |
| Batch size | 150 |
| Datasets | Total Volume | Training | Testing |
|---|---|---|---|
| CICAndMal2017 | 676 | 473 | 203 |
| Drebin | 15,031 | 10,521 | 4510 |
| Hardware | Software |
|---|---|
| RAM size 8 GB | Python Version 3.6 |
| C.P.U. | Numpy Version 1.18.1 |
| TensorFlow library Version 2.10 | |
| Keras library Version 2.3.1 | |
| Matplotlib Version 3.2.0 | |
| NumPy library Version 1.01 |
| CICAndMal2017 Dataset | |||
|---|---|---|---|
| Metrics | Precision (%) | Recall (%) | F1-score (%) |
| Normal | 100 | 100 | 100 |
| Attacks | 100 | 100 | 100 |
| Accuracy | 100 | ||
| Weighted average | 100 | 100 | 100 |
| Drebin dataset | |||
| Metrics | Precision (%) | Recall (%) | F1-score (%) |
| Normal | 0.97 | 0.51 | 0.67 |
| Attacks | 0.77 | 0.99 | 0.86 |
| Accuracy | 80.71 | ||
| Weighted average | 0.84 | 0.81 | 0.79 |
| CICAndMal2017 | |||
|---|---|---|---|
| Metrics | Precision (%) | Recall (%) | F1-score (%) |
| Normal | 0.89 | 0.89 | 0.89 |
| Attacks | 0.91 | 0.91 | 0.91 |
| Accuracy | 0.90 | ||
| Weighted average | 0.90 | 0.90 | 0.90 |
| Drebin dataset | |||
| Metrics | Precision (%) | Recall (%) | F1-score (%) |
| Normal | 0.96 | 0.53 | 0.68 |
| Attacks | 0.78 | 0.99 | 0.87 |
| Accuracy | 81.57 | ||
| Weighted average | 0.85 | 0.82 | 0.80 |
| CICAndMal201 | |||
|---|---|---|---|
| Metrics | Precision (%) | Recall (%) | F1-Score (%) |
| Normal | 0.46 | 0.98 | 0.62 |
| Attacks | 0.33 | 0.01 | 0.02 |
| Accuracy | 45.32 | ||
| Weighted average | 0.39 | 0.45 | 0.29 |
| Drebin Dataset | |||
| Metrics | Precision (%) | Recall (%) | F1-score (%) |
| Normal | 0.95 | 0.53 | 0.68 |
| Attacks | 0.78 | 0.98 | 0.87 |
| Accuracy | 81.35 | ||
| Weighted average | 84 | 0.81 | 0.82 |
| Models | Loss | Accuracy (%) | Precision (%) | Recall (%) | F1 Score (%) |
|---|---|---|---|---|---|
| LSTM | 0.20 | 94.58 | 95.41 | 94.54 | 94.97 |
| CNN-LSTM | 0.16 | 95.07 | 97.16 | 93.63 | 95.53 |
| AE | 1.43 | 75.79 | 92.15 | 66.78 | 77.44 |
| Models | Loss | Accuracy (%) | Precision (%) | Recall (%) | F1 Score (%) |
|---|---|---|---|---|---|
| LSTM | 0.05 | 99.40 | 99.32 | 99.74 | 99.53 |
| AE | 3.65 | 56.65 | 41.18 | 65.71 | 51.11 |
| CNN-LSTM | 0.09 | 97.20 | 97.72 | 97.92 | 97.82 |
| Models | MAE | MSE | RMSE | R2 (%) |
|---|---|---|---|---|
| SVM | 0.00 | 0.0 | 0.0 | 100 |
| KNN | 0.0985 | 0.09852 | 0.313 | 63.31 |
| LDA | 0.429 | 0.4189 | 0.647 | 53.68 |
| Models | MAE | MSE | RMSE | R2 (%) |
|---|---|---|---|---|
| SVM | 0.1915 | 0.1915 | 0.437 | 31.57 |
| KNN | 0.1842 | 0.1842 | 0.429 | 33.35 |
| LDA | 0.1864 | 0.1864 | 0.431 | 32.09 |
| SVM | 0.1915 | 0.1915 | 0.437 | 31.57 |
| CICAndMal2017 Dataset | ||||
|---|---|---|---|---|
| Models | MAE | MSE | RMSE | R2 (%) |
| LSTM model | 0.0054 | 0.0541 | 0.232 | 88.25 |
| Autoencoder model | 0.339 | 0.339 | 0.5830 | 31.74 |
| CNN-LSTM | 0.049 | 0.049 | 0.221 | 80.31 |
| Drebin dataset | ||||
| Models | MAE | MSE | RMSE | R2 (%) |
| LSTM model | 0.0059 | 0.0059 | 0.077 | 97.39 |
| Autoencoder model | 0.2425 | 0.2279 | 0.177 | 17.91 |
| CNN-LSTM | 0.027 | 0.027 | 0.1671 | 87.84 |
| Reference | Year | Datasets | Model | Accuracy (%) |
|---|---|---|---|---|
| Ref. [72] | 2021 | Drebin | CNN | 91 |
| Ref. [73] | 2018 | Drebin | RF, J.48, NB, Simple Logistic, BayesNet TAN, BayesNet K2, SMO PolyKernel, IBK, SMO NPolyKernel | 88–96 |
| Ref. [74] | 2021 | Drebin | CBR, SVM, DT | 95 |
| Ref. [75] | 2019 | Drebin | Random forest tree | 96.7 |
| Ref. [76] | 2018 | Drebin | DT | 97.7 |
| Ref. [77] | 2019 | Drebin | RF with 1000 decision trees | 98.7 |
| Ref. [78] | 2019 | Drebin | SVM | 93.7 |
| Ref. [79] | 2019 | Drebin | Random forest tree | 94 |
| Ref. [80] | 2019 | Drebin | Random forest tree | 96 |
| Ref. [81] | 2016 | Drebin | Random forest tree | 97 |
| Ref. [82] | 2021 | Drebin | CNN | 98.2 |
| Proposed model | 2022 | Drebin | LSTM CNN-LSTM | 99.40 97.82 |
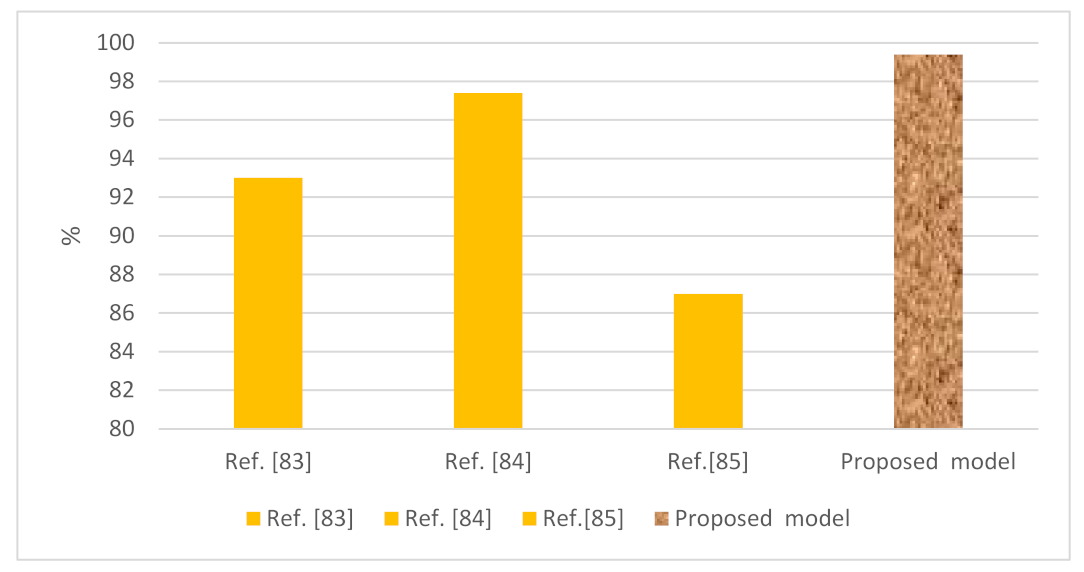
| Reference | Year | Datasets | Model | Accuracy (%) |
|---|---|---|---|---|
| Ref. [83] | 2019 | MalGenome, Kaggle, Androguard | Random forest tree | 93 |
| Ref. [84] | 2018 | Google Play, VirusShare, MassVet | LSTM | 97.4 |
| Ref. [85] | 2017 | Genome, IntelSecurity, MacAfee, Google Play | Deep CNN | 87 |
| 2022 | Drebin | LSTM CNN-LSTM | 99.40 97.82 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alkahtani, H.; Aldhyani, T.H.H. Artificial Intelligence Algorithms for Malware Detection in Android-Operated Mobile Devices. Sensors 2022, 22, 2268. https://doi.org/10.3390/s22062268
Alkahtani H, Aldhyani THH. Artificial Intelligence Algorithms for Malware Detection in Android-Operated Mobile Devices. Sensors. 2022; 22(6):2268. https://doi.org/10.3390/s22062268
Chicago/Turabian StyleAlkahtani, Hasan, and Theyazn H. H. Aldhyani. 2022. "Artificial Intelligence Algorithms for Malware Detection in Android-Operated Mobile Devices" Sensors 22, no. 6: 2268. https://doi.org/10.3390/s22062268
APA StyleAlkahtani, H., & Aldhyani, T. H. H. (2022). Artificial Intelligence Algorithms for Malware Detection in Android-Operated Mobile Devices. Sensors, 22(6), 2268. https://doi.org/10.3390/s22062268







