Abstract
The accurate and reliable monitoring of ventilation parameters is key to intelligent ventilation systems. In order to realize the visualization of airflow, it is essential to solve the airflow reconstruction problem using few sensors. In this study, a new concept called independent cut set that depends on the structure of the underlying graph is presented to determine the minimum number and location of sensors. We evaluated its effectiveness in a coal mine owned by Jinmei Corporation Limited (Jinmei Co., Ltd., Shanghai, China). Our results indicated that fewer than 30% of tunnels needed to have wind speed sensors set up to reconstruct the well-posed airflow of all the tunnels (>200 in some mines). The results showed that the algorithm was feasible. The reconstructed air volume of the ventilation network using this algorithm was the same as the actual air volume. The algorithm provides theoretical support for flow reconstruction.
1. Introduction
Coal is a primary energy source and plays a key role in economic development in many countries. In China, coal accounts for 40–45% of total carbon emissions [1]. Meanwhile, due to the unique working environment in coal mines, the requirements for safe operations are very high. The working environment affects the safety of those working in coal mines. Mining accidents could cause significant loss of life, as well as economic losses to a country. In 2020 alone, 573 Chinese miners died in 434 mining accidents such as leaks of poisonous gases, explosions of natural gases, and the collapsing of mine stopes, especially from underground coal mining [2]. An efficient and reliable ventilation system is essential for safe and efficient production of coal [3].
Intelligent ventilation is a development trend for coal mines and other types of mines. The Chinese National Development and Reform Commission and eight other ministries jointly issued Guiding Opinions on Accelerating the Intelligent Development of Coal Mines to improve the intelligence level of coal mines. A set of systems, including development design, geological guarantee, mining, transportation, and ventilation, are needed to achieve the goal of intelligent decision-making and automation systems operating collaboratively by 2025 [4,5]. Intelligent coal mining is to be fully realized by 2035 [6]. The reliable operation of mine ventilation systems is the basis for safe production in intelligent coal and noncoal mines. Intelligent mine ventilation is a new ventilation system that can be adjusted automatically on demand, which is the development trend of mine ventilation technology in China [7]. Proper monitoring of airflows for all tunnels plays a key role in the development of intelligent mine ventilation systems [8,9]. Airflow monitoring depends on sensors. Hu [10] studied the influence of wall roughness on wind speed distribution to improve the accuracy of monitoring. However, mine ventilation is a very complex network system involving hundreds or even thousands of tunnels. As shown in Figure 1, the Changcun coal mine in Shanxi province, China has 2061 tunnels. It may be impossible to install wind speed sensors in every tunnel due to the high installation and maintenance costs. Air monitoring was highlighted in the assessment of mine ventilation systems and air pollution to improve health and safety for miners [11]. Therefore, it is of great importance to economically determine the minimum number of wind speed sensors that can sample sufficient information to accurately reconstruct the whole network. Airflow reconstruction consists of well-posed reconstruction and underdetermined reconstruction. The so-called well-posed reconstruction is to reconstruct the airflows of the whole network with the minimum number of sensors when the number of sensors is sufficient. The underdetermined reconstruction is realized when the number of sensors is insufficient. The independent cut set algorithm is a well-posed airflow reconstruction algorithm.
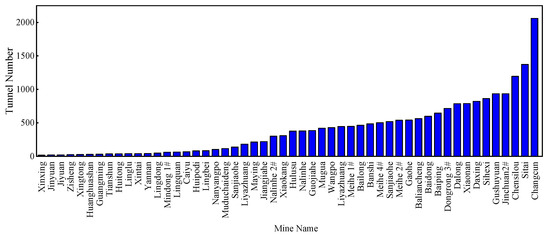
Figure 1.
The number of tunnels in mines in China.
A fully visual environment of ventilation parameters is very important to realize intelligent ventilation of mines. In order to visualize the air volume, an air volume reconstruction algorithm is proposed in this paper. In past studies, optimization and reconstruction technologies of sensor networks were widely used in flow monitoring [12], for the development of intelligent systems [13], and for leak location diagnosis for water [14,15,16], oil [17,18], and gas [19,20,21] pipeline networks. Singh et al. [22] proposed a method to identify ideal monitoring sites for water quality. Huang et al. [23] established a PSO-LSTM model to realize the identification of sources with abnormal radon exhalation rates. Castillo et al. [24] proposed a method of flow reconstruction by constructing a matrix of constraints to give bounds on the number of sensors required. In this method, the construction of a constraint matrix depends on all possible paths of the network. For complex networks, the measurement process in this method will also be very complex. The method was optimized to reduce the impact of network complexity [25]. However, the construction of a constraint matrix depends on the network path; although it has been optimized, the construction process is still very complex. Rinaudo et al. [26] proposed a minimum number of sensors arrangement method to determine the temperature. Although this method reduces the cost of monitoring, the measurement process is too complex. Balaji et al. [27] proposed a method to maximize sensor lifetime by activating sensor covers one at a time to monitor the whole network. This method mainly depends on the effective usage of available resources. Li et al. [28] put forward a novel method based on deep learning techniques and transfer learning to deal with large-scale missing data problems. Ng [29] proposed a method to calculate the number of sensors without depending on the path. He [30] developed an efficient algorithm to determine the smallest subset of links in a traffic network for sensor installation. Muduli et al. [31] proposed a novel wireless sensor network deployment scheme for environmental monitoring in longwall coal mines, which provided the best area coverage and was very cost-effective. Automated ventilation system adjustment software has been developed by monitoring the air volume of the minimum remainder branch in the network, and all air volumes of the branches in the network can be obtained by inverse calculation of associated branches [32]. Song et al. [33] proposed a method for determining the changing trend of gas concentration in the goaf. Lyu et al. [34] proposed a gas concentration prediction method based on the ARMA model, the CHAOS model, and the encoder–decoder model (single-sensor and multisensor). Foorginezhad et al. [35] proposed advanced sensing systems utilized for relevant monitoring and recommendations for improving sensing accuracy.
Mine ventilation networks are similar to traffic networks on topology. Mine ventilation networks are high-order nonlinear systems [36]. In the literature, different approaches have been used for determining the minimum number of sensors needed to identify the location of a ventilation system’s faults [37], such as the coverage of node flowrate method [38], the least full-coverage distribution method [39], minimum tree principle [40], tabu search (TS), Pareto ant colony algorithm (HPACA) [41], and the GA-DBPSO algorithm [42,43]. Changing the airflow in any one of the tunnels leads to changes in other associated tunnels. The sensitivity is used for measuring the airflow relationship between all the tunnels [44].
However, a mine ventilation system is a complex network, with different complexity levels in different areas. There are some problems with considering the accuracy to determine the minimum sensors’ location and reconstruct the air volume of all tunnels in the mines. In this study, we aimed to solve the problems of sensor optimization and air flow reconstruction, and realize the air volume monitoring of the whole air network economically and effectively. In this paper, we propose an algorithm for the well-posed reconstruction of the airflow in a mine ventilation network. The algorithm is based on the structure of the underlying graph, and makes it possible to have a unique, optimized solution to the air volume of tunnels. Compared with other methods, this algorithm involves lower costs and a simpler process.
The rest of this paper is organized as follows. We state the problems we aimed to study, provide a theoretical analysis of our research, and explain some concepts that need to be used in Section 2. In Section 3, we introduce the methods of sensor location optimization and flow reconstruction. The above-mentioned methods are transformed into algorithms, and the specific calculation process is expressed by matrices and formulas, which are verified by taking a single-source and single-sink network as an example in Section 4 and Section 5. In Section 6, we verify the algorithm by taking multisource and multisink network by the ventilation data of a coal mine. The main conclusions of this paper are given in Section 7.
2. Problem Statement
Our goal was to locate wind speed sensors so that the airflow of a ventilation network could be inferred from the measurements while minimizing the number of sensors used. We propose a well-posed flow reconstruction algorithm, which uses the flow conservation equations and breadth-first search algorithm to search the whole ventilation network, establish the equations, and then solve the airflow reconstruction problem.
2.1. Possibility Analysis on Well-Posed Flow Reconstruction
The correlation between the junction number and tunnel number was obtained, as shown in Figure 2. The junction number increases linearly with the tunnel number. This means that there is more mass conservation at the junctions as the tunnel number increases. For a mine ventilation network with a single sink and a single source, m − 1 mass conservation equations can be established for m junctions with a connecting sink and source as a virtual junction. There are n tunnels in the mine, and n unknown parameters, so n − m + 1 wind speed sensors are needed for the well-posed flow reconstruction if the sensors are set up accurately. Similarly, n − m + k − 1 wind speed sensors are used for multisinks and a multisource network (k denotes the total number of the sinks and sources). The above analysis indicates that the minimum number of sensors needed for a well-posed solution may be under 100 when the tunnel number is less than 380, while more than 300 sensors need to be installed when the tunnel number is over 1500; 100–300 sensors are needed if the range of tunnel numbers is 380–1500, as shown in Figure 3. This shows that the calculation complexity is also affected by the network structure.
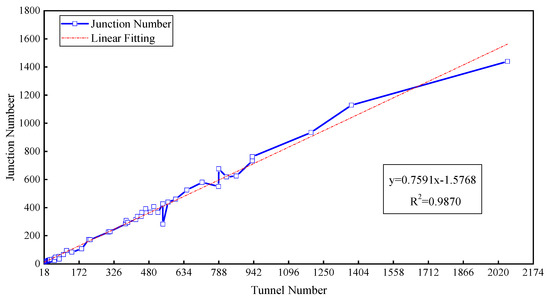
Figure 2.
Correlation between the junction number and tunnel number.
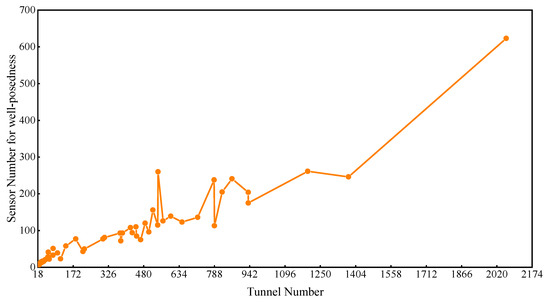
Figure 3.
The number of sensors required for well-posed reconstruction.
Figure 4 shows that the ratio of sensor to tunnel number (RST) for well-posed reconstruction is over 30% and even up to 63% when there are fewer than 150 tunnels in the mine, while the RST is below 30% when the tunnels number more than 150. The above data demonstrated that sensors in some mines can be set up for well-posed flow reconstruction where the RST is less than 30% or there are few tunnels. However, there will be no solution or multiple solutions for the reconstruction if the locations of sensors are inaccurate. Therefore, the installation locations of sensors are critical for flow reconstruction.
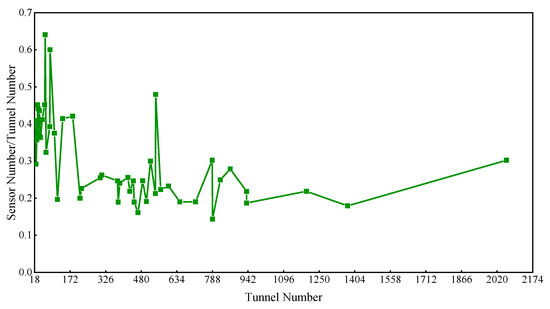
Figure 4.
Ratio of sensor to tunnel number.
2.2. Flow Conservation Equation
Ventilation networks are represented by means of a directed graph:
where
corresponds to the set of junctions,
is the junction number,
represents the set of tunnels, and
is the tunnel number.
The out branches set is denoted as . The in branches set is denoted as . are the set of the source junctions and the sink junctions, respectively. For any junction , inflow equals outflow:
A generalized equation of mass can be derived from Equation (2) and the algebraic sum of the tunnels’ flow mass is in any directed cut set of the network with sinks and sources:
where
represents the directed cut set;
is the cut set number;
is the total mass of the network.
2.3. Improved Breadth-First Search
An exact mathematical model (i.e., a direct solution) may not be found for some problems. In this case, search methods are generally used to solve the issues, among which a breadth-first search (BFS) is the simplest method.
A BFS is one of the graph algorithms. The process is to search for every possible edge by traditional BFS; each junction can only be visited once. The basic idea is to start from a junction v in the graph. In turn, the graph is traversed in breadth first from the unreachable adjacent junctions of v until the junctions in the graph are connected with the paths of v visited. If any junctions in the graph are not visited at this time, the breadth-first traversal is performed again from a junction that has not been visited until all the junctions in the graph have been accessed.
Figure 5 is a ventilation network diagram of single source and single sink. It shows a schematic diagram of an independent cut set. If we launch a BFS from junction (the following access order is not unique, and the second point can be either or ), we may get an access process as follows: . We then go back to . We can get the access process as follows: . For the same reason, we can go back to . We can then continue to search . The search is finished when all junctions are visited. The result of each BFS must be a connected component of the graph.
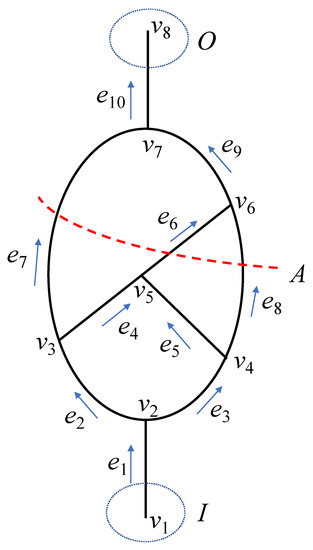
Figure 5.
Schematic diagram of independent cut set. (Red line represents cut line, and and represent source junction and sink junction respectively).
According to the analysis in Section 2.1, the spanning tree structure meets the requirements of well-posed reconstruction. Therefore, an improved breadth-first search (IBFS) method is proposed, based on the spanning tree structure instead of the whole network.
An IBFS is a search algorithm based on the spanning tree structure. The first step of an IBFS is to determine the spanning tree and sort the junctions and tunnels of the spanning tree. Then, all source and sink junctions of the spanning tree must be determined. The source junction is taken as the starting junction to start the search, and the incidence branches of the junction are searched. After searching all incidence branches, the search must be continued according to the previous step with the end junction of the incidence branch as the starting junction until the sink junction is searched. The previous junction must then be considered as the starting junction, and other branches are searched for. If there are no other branches, the retreat is continued until the starting junction with other branches is found and the search is maintained. When all branches of the spanning tree are searched, the search ends.
Take Figure 5 as an example; form a spanning tree. If we launch an IBFS from junction , we may get an access process as follows: . Because is a sink of the spanning tree, we need to go back to . The adjacent junction of junction has an incidence branch. The next search starts from . The process is as follows: . When all branches of the spanning tree have been searched, the search ends. The IBFS is the basis of our research on sensor optimization and air volume reconstruction. The following algorithms need to use IBFS.
2.4. Definition of Single Junction Cut Sets
In the directed graph after deleting junction , all tunnels associated with from the graph cannot be connected. This is called a single junction cut set ().
In Figure 5, . In other words, there are eight single junction cut sets in the directed graph:
,
,
,
,
,
,
,
,
,
.
2.5. Definition of Independent Cut Set
A new concept called independent cut set is proposed. The source–sink matrix describes the ventilation flow in the mine. The source junction set is I, and the sink junction set is O. In the mine ventilation network , a cut partitions into two subsets, and . The cut set of a cut is the set , which is called the independent cut set. The independent cut set can divide the input and output junctions into two disjointed parts, which means that the removal of all edges disconnects all paths from the input to output junctions, as shown in Figure 5.
2.6. Algorithm of Independent Cut Set
An independent cut set search algorithm for a single-source, single-sink ventilation network was studied. The graph is described as:
,
,
,
V and
The sources set is denoted by where represents the sink set, . First, single-junction cut sets , were obtained, such as for the junction . A spanning tree that connects all junctions in the mine network without forming a cycle was created, including some tunnels on demand. The spanning tree was then changed to an undirected graph. The breadth-first search starts from the source junction . When it comes to junction in the spanning tree, the independent cut set is calculated by . It was followed until the searching of all the junctions of the spanning tree was completed (see Figure 6).
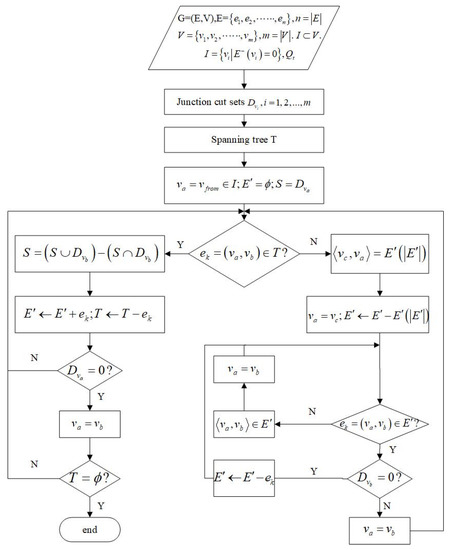
Figure 6.
Flow diagram for the independent cut set.
Take the network shown in Figure 5, for example; the network graph is:
,
.
The spanning tree is:
.
The single junction cut sets for every junction are:
.
According to the flow diagram, the process of obtaining the independent cut set is as shown in Table 1.

Table 1.
The independent cut set of the graph in Figure 5.
3. Methods of Location Optimization and Flow Reconstruction
3.1. Location Optimization of Wind Speed Sensors
In order to study the minimum number and location of sensors that can completely recover the airflow in a mine network, an algorithm based on the topological structure of the network and the information was developed. The algorithm creates spanning trees and uses the IBFS, a well-known graph traversal algorithm, to search. The inputs of the algorithm on the location of wind speed sensors are the directed graph and single junction cut set, while the output is the independent cut set. The procedures of the algorithm are as follows:
- Change all junctions in with a single junction and find the single-junction cut set of all junctions.
- Initialize .
- Use IBFS over spanning tree starting at . Denote and as the visited edges and junctions, respectively.
- Obtain the independent cut set while : end if ; otherwise, search the next spanning tree. To avoid repeated searches, the edges and junctions passing by should be recorded for every independent cut set obtained.
- If any junctions in the graph are not visited at this time, the breadth-first traversal must be performed again from a junction that has not been visited until all the junctions in the graph have been accessed.
- Put the known air volume into Equation (3) to solve for the unknown air volume.
3.2. Flow Reconstruction Method by the Wind Speed Sensors
According to the Chinese industry standards GB/T51272-2018 and AQ2031-2011, it is compulsory to install wind speed sensors in main return tunnels, the return tunnels of all mining areas, and the return tunnels of all sublevels. These tunnels are seen as cotrees for the spanning tree, which can be generated according to the cotrees by the Kruskal algorithm.
As shown in Figure 6, the independent cut sets can be searched by the spanning tree. There is a flow equation, Equation (3), for every independent cut set. Taking Table 1 as an example, seven flow equations can be set. is the air volume of the main fan that must be monitored. It is assumed that , , and .
Equation (4) is solved by the Gaussian elimination method. The air volume of the tunnels in the spanning tree is , , , , , , and .
4. Algorithm Optimization of Sensor Location Problem
In this paper, we propose an independent cut set algorithm for well-posed reconstruction of the airflow in a mine ventilation network; however, its process is too complex. For a large-scale ventilation network, the calculation amount and complexity are very large. In order to simplify the calculation process, the independent cut set algorithm can be optimized by matrixing the calculation process, i.e., all equations in the calculation process can be expressed by matrix. With the help of matrix characteristics, the sensor location problem can be calculated more quickly and intuitively. In addition, there is a mature calculation program for the matrix problem. It is more convenient to solve the matrix problem by computer than to directly solve the newly defined algorithm. Especially for large-scale network problems, faster and more accurate calculations can be made.
4.1. Optimization of Single Junction Cut Set
In order to more clearly represent the single junction cut sets, we can use the complete incidence matrix to express the single junction cut sets of each junction. The complete incidence matrix is a 0-1-(−1) matrix that describes the mine ventilation network structure through the spatial relationships between the tunnels and junctions of the network. Each column element of the matrix represents each tunnel of the mine ventilation network. Each row element denotes the junction. The matrix can be expressed as follows:
where is the complete incidence matrix of the network of dimension and is 0, 1, or −1. indicates that and junction are associated, and is the out branch of . indicates that is the in branch of . Through the definition of single junction cut sets, if branch and junction are associated, then belongs to . Therefore, is an element of when . On the contrary, indicates that and junction are not related.
The matrix can be represented through a set of column vectors. denotes the complete incidence matrix with junctions and tunnels, and can be expressed as follows:
where is the row vector of dimension . , i.e., (). , corresponding to all nonzero entries in , is the single-junction cut set corresponding to junction ; that is, is all the elements of .
4.2. Optimization of Independent Cut Set Algorithm
In Section 2.6, it is revealed that the independent cut set is calculated by , which is a equation related to the single junction cut set and independent cut set. From Section 4.1, we know the matrix form of the single junction cut sets , i.e., complete incidence matrix (see Equations (5) and (6)). Therefore, we can convert the solution process of the independent cut set into matrix form. An independent cut set–branch incidence matrix can be established to obtain the independent cut set of the ventilation network. The matrix can be expressed as follows:
where is the independent cut set–branch incidence matrix of the network of dimension and is 0 or 1. indicates that is a subset of the independent cut set at junction . denotes that does not belong to the independent cut set at junction . Compared with the complete incidence matrix, each column element of the new matrix still represents each branch of the ventilation network. However, row elements are expressed by independent cut sets . In Section 4.1, the complete incidence matrix (see Equation (6)) is expressed as follows:
Through the calculation formula of independent cut sets , we can obtain the matrix expression:
where corresponds to all nonzero entries and in is the independent cut sets. According to Equation (8), we can obtain the matrix form of the independent cut set.
5. Sensor Location and Flow Reconstruction Based on Algorithm Optimization
5.1. Sensor Location Based on Algorithm Optimization
Take the network shown in Figure 5 as an example; according to Equation (1), the network graph is:
The junctions and tunnels have been sorted in Figure 5. The whole calculation process is carried out according to the IBFS. According to Equations (5) and (6), we can obtain the single junction cut set expressed by the matrix, that is, the complete incidence matrix of ventilation network . In order to facilitate the presentation of the row vector and column vector corresponding to each element of the complete incidence matrix, we show the complete incidence matrix corresponding to Figure 5 in the form of Table 2.

Table 2.
The complete incidence matrix (corresponding to Figure 5).
The matrix can be expressed as . According to Equation (6), the form of its column vector is . All nonzero entries in are the result of , that is, ; the first single junction cut set is Similarly, all nonzero entries in are the result of , that is, and the second single junction cut set is , etc. Through the matrix, we can easily obtain the single-junction cut sets of each junction, and the result conforms to the definition of single-junction cut sets.
In order to obtain the independent cut set, is substituted into Equation (8). The results are shown in Table 3.

Table 3.
Independent cut set–branch incidence matrix (corresponding to Figure 5).
The matrix can be expressed as . The form of its column vector is . All nonzero entries in are the results of the independent cut set. For example, and the first independent cut set is ; and the second independent cut set is ; and the first independent cut set is , etc.
5.2. Flow Reconstruction Based on Algorithm Optimization
In order to simplify the calculation process, the solution of the independent cut set is obtained by a matrix. Therefore, we can also express the calculation of Equation (3) by a matrix. According to Equation (3), the air volume in each tunnel can be denoted by air volume set , and its expression is as follows:
where denotes the tunnel number and represents the air volume of the tunnel. According to Equation (3), the following equation can be obtained:
where is the column vector of dimension ,
.
In Figure 5, and . It is assumed that , , and . From Equation (10),
After simplifying the above formula, the following equation can be obtained:
The air volume of the tunnels in the spanning tree is , , , , , , and .
6. Case Study
According to the standards AQ1028-2006 and GB/T 10178, the ventilation network is a fluid network formed by conveying air flow pipelines; various regulating facilities, power facilities, and air flow pipelines are connected. Figure 7 is the ventilation network of a coal mine run by Jinmei Co., Ltd. , where the tunnel number is , and the junction number is . Table 4 shows the whole tunnel’s reconstructed air volume and simulated air volume. The test air volume [45] is obtained by a mine ventilation simulation system (MVSS) [46]. The principle of solving the network by MVSS is to establish the mathematical equations for the ventilation resistance law, the air volume balance law, the air pressure balance law, the known total air volume of the fans, and the ventilation resistance coefficient, and then solve them. The main fans are installed in , , and , and their characteristic equations are shown in Equation (11). For a multisource and multisink ventilation network, all sources and sinks should be connected to become a single-source and single-sink network. In a ventilation network, if the spanning tree is removed, the remaining part is called the cotree. As shown in Figure 8, 33 wind speed sensors are used for the network, including 30 cotrees and 3 wind shafts with fans. The tunnels that must be set up with wind speed sensors are, , , , , , , , , , , , , and . A spanning tree is generated that does not include the above tunnels (the magenta in Figure 8). Considering the difficulty of testing the lower wind speed, most of the cotrees should not contain the tunnels with structures such as throttles and confined walls. Based on the flow diagram in Figure 5, the air volume of the spanning trees can be calculated by the linear flow equation system of the independent cut sets.
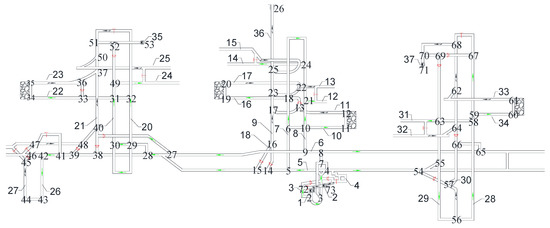
Figure 7.
A coal mine ventilation system used by Jinmei Co., Ltd. (Red indicates the position of air doors or wind windows, and black arrows indicate the exhaust air flow. Green is the incoming air flow as well as the fresh air flow. Each number indicates the junction number and tunnel number).

Table 4.
Ventilation system of Jinmei coal mine.
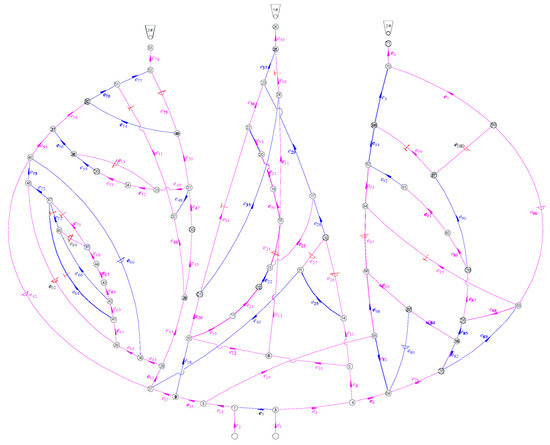
Figure 8.
Coal mine ventilation used by Jinmei Co., Ltd. The magenta represents spanning trees and the blue represents cotrees.
The reconstructed air volume in Table 4 was obtained by the independent cut set algorithm. Similarly, the results obtained by the independent cut set algorithm followed the three basic laws of air volume distribution. Their basic principles are similar. We also used part of the test air volume as a known quantity for the calculation. Therefore, their calculation results should be the same; otherwise, they will prove that the independent cut set algorithm is incorrect. It can be seen from Table 4 that their results were exactly the same. It is feasible to use the independent cut set algorithm to determine the minimum number and location of sensors through the case study. By placing sensors on the cotrees, the air volume of the spanning trees can be obtained. Due to the uniqueness of the well-posed solution, the error of flow reconstruction is zero (see Table 4). There will be no errors or other solutions.
Figure 5 is an example of a simple network with a single source and single sink, and Figure 8 is an example of a complex ventilation network with multiple sources and multiple sinks. Through the calculation of these two examples, it was found that the independent cut-set algorithm was suitable for both of the examples. Therefore, the independent cut set algorithm can be used to solve the sensor optimization and air volume reconstruction problems of all types of ventilation networks. In line with previous research, the calculation complexity was also affected by the network structure. Due to the uniqueness of the well-posed solution, the error of the result can only come from the measurement accuracy of the sensor and will not be affected by other factors. Moreover, the existing solution is unique and has no errors.
7. Conclusions
In this research, the wind speed sensor location problem of the mine ventilation network was solved by using the independent cut set algorithm, which is a new concept based on the structure of the underlying graph. Firstly, we found the problems: the sensor number was and we located flow sensors in the cotrees that must be set up with sensors according to the Chinese standards. The calculation complexity was affected by the network structure. Secondly, we discussed the possibility of well-posed reconstruction based on the mine ventilation networks. Fewer than 30% of tunnels need to be set up with wind speed sensors to achieve a well-posed reconstruction of the airflow in all the tunnels if the mines have over 200 tunnels. For mines with fewer than 200 tunnels, more than 30% of tunnels should be installed with sensors. Due to the uniqueness of the well-posed solution, there is no error in the results unless the sensor accuracy does not meet the standard. Lastly, the algorithm of independent cut sets was presented for the well-posed reconstructions. The flow reconstructions were shown to be computationally efficient for the coal mine ventilation system used by Jinmei Co., Ltd. This algorithm works on velocity sensor distribution rather than sensors of hazardous and combustible gas. This algorithm is a well-posed reconstruction algorithm. It can only be used to determine the minimum number and location of sensors and cannot solve the underdetermined reconstruction of a given number of sensors. Therefore, the premise of using this algorithm is that the number of sensors will be sufficient. This study provides researchers with a sensor optimization scheme when the number of sensors is insufficient and provides the possibility for air volume reconstruction. At the same time, it reduces the cost for the air volume monitoring of the whole air network and provides some theoretical support for the realization of intelligent ventilation. In the following research, we will discuss the sensor location under the condition of underdetermined reconstruction.
Author Contributions
Conceptualization, K.G.; writing—original draft preparation, K.G. and Z.L.; writing—review and editing, K.G., Z.L., Y.L., Y.H. and C.Z.; supervision, K.G., Z.L. and Y.L. All authors have read and agreed to the published version of the manuscript.
Funding
The work is supported by National Natural Science Foundation of China (No.52104194 and 52074148).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The datasets generated and analyzed during the current study are available from the corresponding author upon reasonable request.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Zhang, W.H.; Yan, Q.Y.; Yuan, J.H.; He, G.; Teng, T.-L.; Zhang, M.J.; Zeng, Y. A realistic pathway for coal-fired power in China from 2020 to 2030. J. Clean. Prod. 2020, 275, 122859. [Google Scholar] [CrossRef]
- Zhao, Y.H.; Zheng, X.Z.; Hu, H.J.; Wang, S.F.; Lu, N. Press Conference of the State Administration of Mine Safety. Beijing. 2021. Available online: https://www.chinamine-safety.gov.cn/xw/xwfbh/ (accessed on 10 February 2022).
- Zhang, P.; Lan, H.Q.; Yu, M. Reliability evaluation for ventilation system of gas tunnel based on Bayesian network. Tunn. Undergr. Space Technol. 2021, 112, 103882. [Google Scholar] [CrossRef]
- Dong, L.J.; Hu, Q.C.; Tong, X.J.; Liu, Y.F. Velocity-Free MS/AE Source Location Method for Three-Dimensional Hole-Containing Structures. Engineering 2020, 6, 827–834. [Google Scholar] [CrossRef]
- Dong, L.J.; Tong, X.J.; Ma, J. Quantitative Investigation of Tomographic Effects in Abnormal Regions of Complex Structures. Engineering 2021, 7, 1011–1022. [Google Scholar] [CrossRef]
- Wang, G.F.; Xu, Y.X.; Ren, H.W. Intelligent and ecological coal mining as well as clean utilization technology in China: Review and prospects. Int. J. Min. Sci. Technol. 2019, 29, 161–169. [Google Scholar] [CrossRef]
- Wang, K.; Jiang, S.G.; Zhang, W.Q.; Wu, Z.Y.; Shao, H.; Kou, L.W. Destruction mechanism of gas explosion to ventilation facilities and automatic recovery technology. Int. J. Min. Sci. Technol. 2012, 22, 417–422. [Google Scholar] [CrossRef]
- Huang, D.; Liu, J.; Deng, L.J. A hybrid-encoding adaptive evolutionary strategy algorithm for windage alteration fault diagnosis. Process Saf. Environ. Prot. 2020, 136, 242–252. [Google Scholar] [CrossRef]
- Gao, K.; Deng, L.J.; Liu, J.; Wen, L.X.; Wong, D.; Liu, Z.Y. Study on Mine Ventilation Resistance Coefficient Inversion Based on Genetic Algorithm. Arch. Min. Sci. 2018, 63, 813–826. [Google Scholar]
- Hu, J.H.; Zhao, Y.; Zhou, T.; Ma, S.W.; Wang, X.L.; Zhao, L. Multi-factor influence of cross-sectional airflow distribution in roadway with rough roof. J. Cent. South Univ. 2021, 28, 2067–2078. [Google Scholar] [CrossRef]
- Mayala, L.P.; Veiga, M.M.; Khorzoughi, M.B. Assessment of mine ventilation systems and air pollution impacts on artisanal tanzanite miners at Merelani, Tanzania. J. Clean. Prod. 2016, 116, 118–124. [Google Scholar] [CrossRef]
- Liang, P.Y.; Han, Y.; Zhang, Y.Y.; Wen, Y.T.; Gao, Q.F.; Meng, J. Novel non-destructive testing method using a two-electrode planar capacitive sensor based on measured normalized capacitance values. Measurement 2021, 167, 108455. [Google Scholar] [CrossRef]
- Rodriguez-Vega, M.; Canudas-de-Wit, C.; Fourati, H. Location of turning ratio and flow sensors for flow reconstruction in large traffic networks. Transp. Res. Part B Methodol. 2019, 121, 21–40. [Google Scholar] [CrossRef]
- Hu, X.; Han, Y.M.; Yu, B.; Geng, Z.Q.; Fan, J.Z. Novel leakage detection and water loss management of urban water supply network using multiscale neural networks. J. Clean. Prod. 2021, 278, 123611. [Google Scholar] [CrossRef]
- Lau, P.-W.; Cheung, B.-Y.; Lai, W.-L.; Sham, J.-C. Characterizing pipe leakage with a combination of GPR wave velocity algorithms. Tunn. Undergr. Space Technol. 2021, 109, 103740. [Google Scholar]
- Liang, L.P.; Xu, K.J.; Wang, X.F.; Zhang, Z.; Yang, S.L.; Zhang, R. Statistical modeling and signal reconstruction processing method of EMF for slurry flow measurement. Measurement 2014, 54, 1–13. [Google Scholar] [CrossRef]
- Lu, H.F.; Iseley, T.; Behbahani, S.; Fu, L.D. Leakage detection techniques for oil and gas pipelines: State-of-the-art. Tunn. Undergr. Space Technol. 2020, 98, 103249. [Google Scholar] [CrossRef]
- Aida-zade, K.R.; Ashrafova, E.R. Localization of the points of leakage in an oil main pipeline under nonstationary conditions. J. Eng. Phys. Thermophys. 2012, 85, 1148–1156. [Google Scholar] [CrossRef]
- Zhang, Z.W.; Hou, L.F.; Yuan, M.Q.; Fu, M.; Qian, X.M.; Duanmu, W.; Li, Y.Z. Optimization monitoring distribution method for gas pipeline leakage detection in underground spaces. Tunn. Undergr. Space Technol. 2020, 104, 103545. [Google Scholar] [CrossRef]
- Santos, R.B.; de Sousa, E.O.; da Silva, F.V.; da Cruz, S.L.; Fileti, A.M.F. Detection and on-line prediction of leak magnitude in a gas pipeline using an acoustic method and neural network data processing. Braz. J. Chem. Eng. 2014, 31, 145–153. [Google Scholar] [CrossRef]
- Li, J.; Li, Y.L.; Huang, X.J.; Ren, J.H.; Feng, H.; Zhang, Y.; Yang, X.X. High-sensitivity gas leak detection sensor based on a compact microphone array. Measurement 2021, 174, 109017. [Google Scholar] [CrossRef]
- Singh, K.R.; Dutta, R.; Kalamdhad, A.S.; Kumar, B. An investigation on water quality variability and identification of ideal monitoring locations by using entropy based disorder indices. Sci. Total Environ. 2019, 647, 1444–1455. [Google Scholar] [CrossRef] [PubMed]
- Huang, D.; Liu, Y.; Liu, Y.H.; Song, Y.; Hong, C.S.; Li, X.Y. Identification of sources with abnormal radon exhalation rates based on radon concentrations in underground environments. Sci. Total Environ. 2022, 807, 150800. [Google Scholar] [CrossRef] [PubMed]
- Castillo, E.; Jiménez, P.; Menendez, J.M.; Conejo, A.J. The Observability Problem in Traffic Models: Algebraic and Topological Methods. IEEE Trans. Intell. Transp. Syst. 2008, 9, 275–287. [Google Scholar] [CrossRef]
- Castillo, E.; Calviño, A.; Lo, H.K.; Menéndez, J.M.; Grande, Z. Non-planar hole-generated networks and link flow observability based on link counters. Transp. Res. Part B Methodol. 2014, 68, 239–261. [Google Scholar] [CrossRef]
- Rinaudo, P.; Paya-Zaforteza, I.; Calderón, P.A. Improving tunnel resilience against fires: A new methodology based on temperature monitoring. Tunn. Undergr. Space Technol. 2016, 52, 71–84. [Google Scholar] [CrossRef]
- Balaji, S.; Anitha, M.; Rekha, D.; Arivudainambi, D. Energy efficient target coverage for a wireless sensor network. Measurement 2020, 165, 108167. [Google Scholar] [CrossRef]
- Li, Y.T.; Bao, T.F.; Chen, H.; Zhang, K.; Shu, X.S.; Chen, Z.X.; Hu, Y.H. A large-scale sensor missing data imputation framework for dams using deep learning and transfer learning strategy. Measurement 2021, 178, 109377. [Google Scholar] [CrossRef]
- Ng, M. Synergistic sensor location for link flow inference without path enumeration: A node-based approach. Transp. Res. Part B Methodol. 2012, 46, 781–788. [Google Scholar] [CrossRef]
- He, S.X. A graphical approach to identify sensor locations for link flow inference. Transp. Res. Part B Methodol. 2013, 51, 65–76. [Google Scholar] [CrossRef]
- Muduli, L.; Jana, P.K.; Mishra, D.P. A novel wireless sensor network deployment scheme for environmental monitoring in longwall coal mines. Process Saf. Environ. Prot. 2017, 109, 564–576. [Google Scholar] [CrossRef]
- Wang, K.; Jiang, S.G.; Wu, Z.Y.; Shao, H.; Zhang, W.Q.; Pei, X.D.; Cui, C.B. Intelligent safety adjustment of branch airflow volume during ventilation-on-demand changes in coal mines. Process Saf. Environ. Prot. 2017, 111, 491–506. [Google Scholar] [CrossRef]
- Song, Y.W.; Yang, S.Q.; Hu, X.C.; Song, W.X.; Sang, N.W.; Cai, J.W.; Xu, Q. Prediction of gas and coal spontaneous combustion coexisting disaster through the chaotic characteristic analysis of gas indexes in goaf gas extraction. Process Saf. Environ. Prot. 2019, 129, 8–16. [Google Scholar] [CrossRef]
- Lyu, P.Y.; Chen, N.; Mao, S.J.; Li, M. LSTM based encoder-decoder for short-term predictions of gas concentration using multi-sensor fusion. Process Saf. Environ. Prot. 2020, 137, 93–105. [Google Scholar] [CrossRef]
- Foorginezhad, S.; Mohseni-Dargah, M.; Firoozirad, K.; Aryai, V.; Razmjou, A.; Abbassi, R.; Garaniya, V.; Beheshti, A.; Asadnia, M. Recent Advances in Sensing and Assessment of Corrosion in Sewage Pipelines. Process Saf. Environ. Prot. 2021, 147, 192–213. [Google Scholar] [CrossRef]
- Hu, Y.N.; Koroleva, O.I.; Krstić, M. Nonlinear control of mine ventilation networks. Syst. Control Lett. 2003, 49, 239–254. [Google Scholar] [CrossRef]
- Khan, K.S.; Tariq, M. Accurate Monitoring and Fault Detection in Wind Measuring Devices through Wireless Sensor Networks. Sensors 2014, 14, 22140–22158. [Google Scholar] [CrossRef] [Green Version]
- Sun, J.P.; Tang, L.; Li, C.S.; Zhu, N.; Zhang, B. Application of air-volume Proportion rule in optimal placement of gas sensor in mine. J. China Coal Soc. 2008, 33, 1126–1130. (In Chinese) [Google Scholar]
- Zhao, D.; Liu, J.; Pan, J.T.; Li, Z.X. Application study of air velocity fault source diagnosis technology for ventilation system in Daming Mine. Chin. J. Saf. Environ. 2012, 12, 204–207. (In Chinese) [Google Scholar]
- Dong, X.L.; Chen, S.; Zhao, D.; Pan, J.T. Study on Application of Minimum Tree Principle in Layout of Wind Speed Sensor in Mine. Chin. World Sci-Tech R D 2015, 37, 680–683. (In Chinese) [Google Scholar]
- Liang, S.H.; He, J.; Zheng, H.; Sun, R.H. Research on the HPACA Algorithm to Solve Alternative Covering Location Model for Methane Sensors. Procedia Comput. Sci. 2018, 139, 464–472. [Google Scholar] [CrossRef]
- Zhao, D.; Zhang, H.; Pan, J.T. Solving Optimization of A Mine Gas Sensor Layout Based on A Hybrid GA-DBPSO Algorithm. IEEE Sens. J. 2019, 19, 6400–6409. [Google Scholar] [CrossRef]
- Wu, C.Q.; Wang, L. On Efficient Deployment of Wireless Sensors for Coverage and Connectivity in Constrained 3D Space. Sensors 2017, 17, 2304. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Semin, M.A.; Levin, L.Y. Stability of air flows in mine ventilation networks. Process Saf. Environ. Prot. 2019, 124, 167–171. [Google Scholar] [CrossRef]
- Liu, J.; Jiang, Q.H.; Liu, L.; Wang, D.; Huang, D.; Deng, L.J.; Zhou, Q.C. Resistance variant fault diagnosis of mine ventilation system and position optimization of wind speed sensor. J. China Coal Soc. 2021, 46, 1907–1914. (In Chinese) [Google Scholar]
- Jia, J.Z.; Liu, J.; Geng, X.W. Mathematical model of mine ventilation simulation system. J. Liaoning Tech. Univ. 2003, 22, 88–90. (In Chinese) [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).