In terms of the research status of color image encryption: Liu et al. [
7] proposed a color image hyperchaotic encryption algorithm using DNA dynamic coding and adaptive arrangement and designed a new four-dimensional hyperchaotic system and plain-image-related adaptive permutation method, which makes the operation result more unpredictable and improves the sensitivity of the algorithm to plain images and keys. Zou et al. [
8] used DNA coding and sequencing to construct short DNA strands and long DNA strands, in which short DNA strands were used for DNA strand exchange and long DNA strands were used for DNA strand diffusion, and the experimental results verified that the proposed algorithm has high safety and excellent efficiency. Samiullah et al. [
9] propose a new symmetric block cipher scheme. It uses DNA-based dynamic S-boxes and hyperchaotic systems connected with MD5 to generate obfuscation and diffusion to encrypt color images, greatly improving the computational efficiency of encryption algorithms. Liu et al. [
10] proposed a hyperchaotic image encryption algorithm based on plain image information and DNA calculation, which enhanced the relationship between pixel position, grayscale value and plain image, which not only showed excellent encryption performance, but also resisted various typical attacks. Liang et al. [
11] introduced DNA strand displacement and a four-dimensional multi-stable superchaotic system, which increased the connection between the original image and the key so that the encryption algorithm has good resistance to exhaustive attacks, statistical attacks and known original image attacks on RGB color images. Chu et al. [
12] proposed a three-dimensional image encryption method based on the memristor chaotic system and RNA cross-mutation. During the entire encryption process, the Arnold matrix, RNA encoding and decoding rules, and crossover and mutation algorithms are determined by the memristor chaotic system, which can encrypt 3D images at the same time and effectively resist various attacks. Lu et al. [
13] proposed an adaptive compression encryption method for content based on CS and ribonucleic acid (RNA). Chaotic sequences driven by pure image hashes are utilized throughout the encryption process, enhancing the correlation between the algorithm and the pure image, improving resistance to known and selected plain image attacks. Ghorbani et al. [
14] proposed a safe and effective encryption scheme based on ribonucleic acid (RNA) and 2D He and non-maps, which improved the advantages of the most advanced algorithm. Sha et al. [
15] proposed an image cryptographic system based on the genetic center law (GCD), Gartner–Moria–Pratt (KMP) algorithm and chaotic system, which realizes DNA-level bidirectional pixel shuffling through shared stack push operation to accelerate the shuffling of overall pixels and replaces pixel values by simulating the protein synthesis process in GCD, with satisfactory low time complexity and excellent safety effects. Zhang et al. [
16] defined the 3D bit plane based on the genetic center method, converted k raw images into 8-bit binary and converted to 3D matrix, arranged the 3D matrix by rotating the bit plane and arranged between the bit planes, encoded the scrambled 3D matrix into DNA code and obtained encrypted images through RNA decoding operations, which has strong security and ideal performance. Hasimoto-Beltran et al. [
17] propose a new integer chaos-based coupling mapping lattice CML, and encrypt images based on random bit flipping of bitstreams that are not exposed to the attacker’s dynamic reference point (DRP) and random selection of the CML byte trajectories of DRP and bit flipping processes, which has good security and scalability. Li et al. [
18] studied an optical image encryption scheme based on fractional Fourier transform and a five-dimensional host-induced nonlinear fractional-order laser ultra-chaotic system and implemented the system by analyzing the dynamic characteristics of the proposed fractional-order laser super chaotic system and using the DSP platform. An image encryption scheme combining BP neural network, GF(17) domain diffusion and hyperchaotic random point scrambling algorithm is proposed, which provides new research prospects for optical image encryption. Kumar et al. [
19] proposed image encryption of light carrying optical vortex arrays to minimize the quality degradation during actual implementation, providing an effective method for designing optical cryptographic systems. Chen et al. [
20] proposed an exciting optical image encryption method based on spatial nonlinear optics, which realized the high degree of freedom to explore and apply light and provided new research prospects for the development of optical encryption for the protection of information in various optical structures and optical materials. Cheremkhin et al. [
21] proposed the optical implementation of an information optical encryption system using a new multi-level customizable digital data container with high data density, which has efficient error correction ability. Kumar et al. [
22] propose two-dimensional XORor-logic manipulation of beams carrying optical vortex arrays, which brings new possibilities for high-dimensional data processing, cryptography, and computing. Chen et al. [
23] propose an RG-based VSS scheme that encodes multiple secret images at once, which has no pixel expansion and higher secret sharing ability than traditional VC-based VSS. Chen et al. [
24] proposed a new RG-based VSS scheme, which not only improves the capacity of secret communication, but also avoids the problem of pixel expansion, thereby significantly reducing the overhead of storage and communication. De et al. [
25] improved several schemes and provided many upper limits for the random grid model by exploiting (many) known outcomes in the deterministic model and provided new schemes for the deterministic model by utilizing some of the known outcomes of the random grid model. Lin et al. [
26] propose a random grid-chain-based encryption scheme suitable for processing batch binary, grayscale, and color images, and its decryption process is done by the human vision system, which requires neither additional pixel expansion nor any coding base matrix. Shyu et al. [
27] devised an innovative algorithm for visual multi-secret sharing using circular or cylindrical random meshes, which is able to share multiple (instead of just or two) secret images in two shares without causing any additional pixel expansion compared to traditional visual cryptography. Cheng et al. [
28] adopt ultra-chaotic system and permutation-diffusion architecture to realize the encryption of color images by mixing RGB components, strengthen the dependence between the three components of RGB, and greatly improve the algorithm’s ability to resist statistical attacks and differential attacks. Xiong et al. [
29] proposed a color image chaotic encryption algorithm combining cyclic redundancy check (CRC) and nine-house graph, after moving and shuffling pixels through the nine-house graph theory, extracting R, G, and B components to form a binary matrix, and finally cyclic shifting according to cyclic redundancy check (CRC), which better solved the problem of insufficient entropy of cipher image information. Chai et al. [
30] used dynamic DNA encryption and chaos system to encrypt color images, first shuffling the three components R, G and B by using plain synchronous components and then converting the permutations and combinations into DNA matrix for encryption according to DNA coding rules, which effectively improved the ability of the algorithm to resist plain attacks. Tsafack et al. [
31] proposed a new two-dimensional trigonometric logistics-sine-cosine mapping, which first generates three sets of key streams from the map and calculates the Hamming distance in combination with the image R, G and B components, and finally XOR the output distance vector with the key stream to realize the encryption of the image, which greatly improves the security of the cryptosystem. Fei et al. [
32] proposed an image encryption algorithm for jump diffusion based on a two-dimensional absolute sine–cosine coupling chaotic system (2D-ASCC) with higher complexity and better pseudo-randomness, which effectively improves the security performance of the encryption algorithm. Hoang et al. [
33] proposed a chaos-based multi-image encryption algorithm, which adopts the permutation diffusion architecture for the first time and constructs the disturbance amount according to the pixel coordinates and the original image content, respectively, in the process of pixel arrangement and diffusion, so that the encryption algorithm has good resistance to differential attacks. Sridevi et al. [
34] proposed a chaos-assisted color image encryption algorithm. First, the color image is split into RGB planes, and then chaotic maps and attractors are introduced to double obfuscate and diffuse the images, and finally, the separated RGB planes are merged to produce encrypted images, which greatly improves the anti-attack ability of the algorithm. Pour et al. [
35] proposed an image encryption algorithm with a large key space and good attack resistance. The algorithm uses chaos game representation (CGR) images to encrypt images, converting image pixels into binary and combining them to generate binary strings, with each pair of bits acting as a letter of the DNA sequence. Zhang et al. [
36] designed a two-dimensional sine–cosine coupled chaotic system (2D-SCCM) with better randomness and traversability and wider hyperchaotic range, and proposed a color image encryption algorithm with high encryption efficiency and strong security based on the chaotic system. The algorithm first uses a combination of pure image and hash function to generate a key, then fuses the random sequence generated by 2D-SCCM and Arnold map to construct an S-Box, and finally encrypts the color image by constructing an S-Box, chaos system and hash function. Su et al. [
37] proposed an image encryption algorithm based on binary tree space–time chaos and middle-order traversal. The algorithm uses the intermediate traversal sequence to sort the plain images and introduces a coupled mapping lattice to generate a chaotic sequence; it sets the chaotic interference value and finally performs an XOR operation on the adjacent pixels of the image to encrypt the image, which has good robustness. Zhang et al. [
38] proposed a multi-digital image encryption algorithm with excellent image encryption effect and security. The cyclic matrix is constructed by logical mapping, and the sparse transformation of plain images is realized by combining discrete cosine transformation (DCT), and the Lorenz chaotic system and logic graph are used to generate chaotic bond sequences to encrypt images. Li et al. [
39] proposed a multi-image encryption scheme based on a DNA chaos algorithm based on a computational integral imaging framework. By merging multiple images into one image with a computational integral imaging algorithm, the efficiency and security of image encryption are significantly improved, and the contour effect caused by the DNA encryption algorithm is solved because of the high randomness of the chaotic algorithm. To reduce redundant encryption operations and focus on protecting important areas, Song et al. [
40] proposed a fast image encryption algorithm based on the object detection model and chaotic system, so that the detected objects were well-protected. Yu et al. [
41] proposed an image encryption algorithm with good attack resistance. The algorithm uses the scattering medium as the physical key and fuses the four-step phase-shifted digital hologram to convert the plain image into four noise-like holograms, and achieve the effect of encrypting the image by combining the wavelet transform (LWT) into a new image. Adeel et al. [
42] proposed a new method for encrypting color images based on a set of integer keys and a one-dimensional chaotic system, which improves the security of color image encryption by selecting the key associated with the chaotic system to optimize the security of the cryptographic image, which can be used for the secure encryption of image data. Basha et al. [
43] proposed a color image encryption technology based on bit-level chaos, which decomposes the color image into red, blue and green color image components based on the logistic-sine-tent-Chebyshev (LSTC) map for encryption, which has good resistance to statistical attacks, differential attacks and brute force attacks. Hosny et al. [
44] proposed a new color image cryptographic system that changes the value of image pixels according to the 2D logical sine diagram to reconstruct the scrambled image, and uses the key to diffuse the scrambled image to obtain an encrypted image, which has the characteristics of wide key space, high key sensitivity and good encryption effect. Wang et al. [
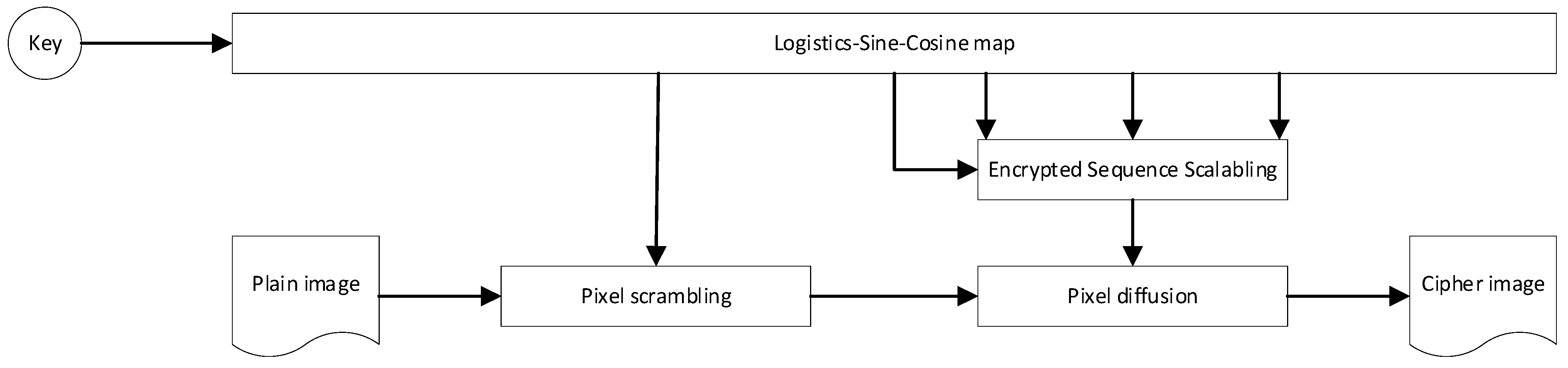
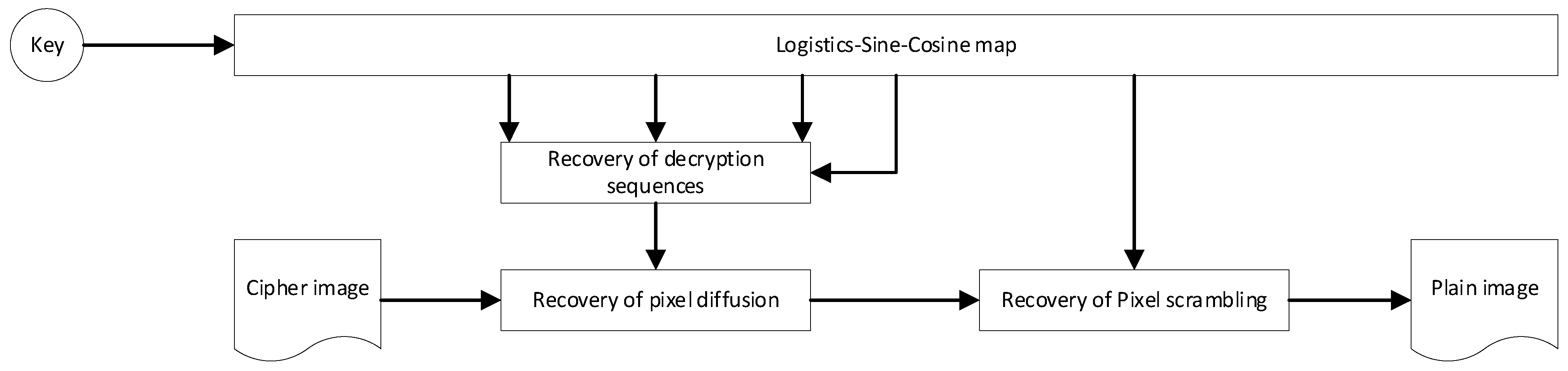
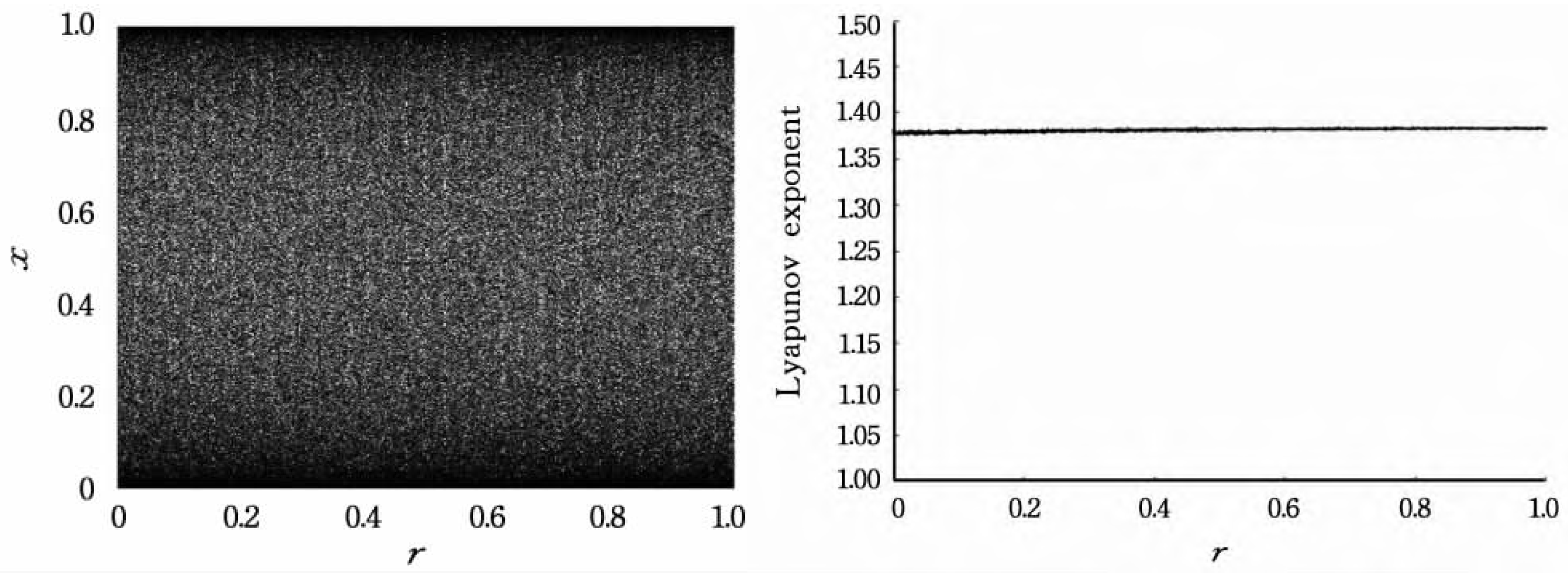
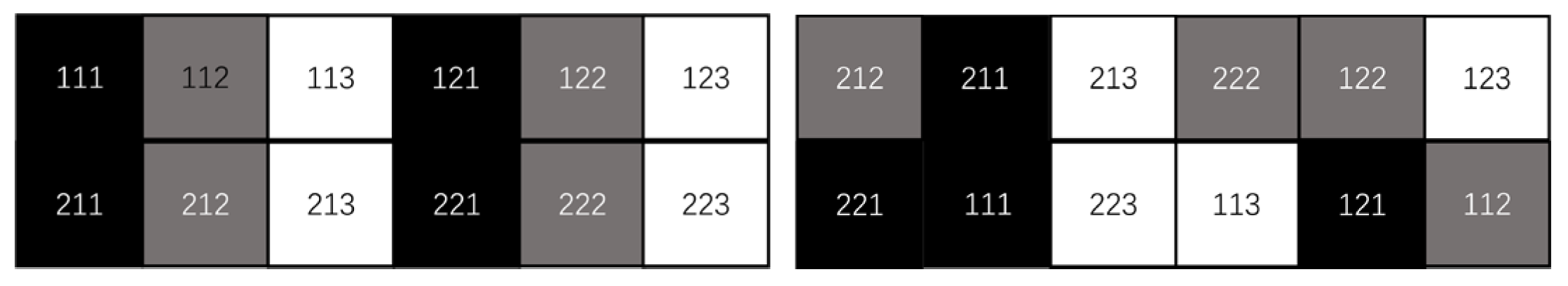
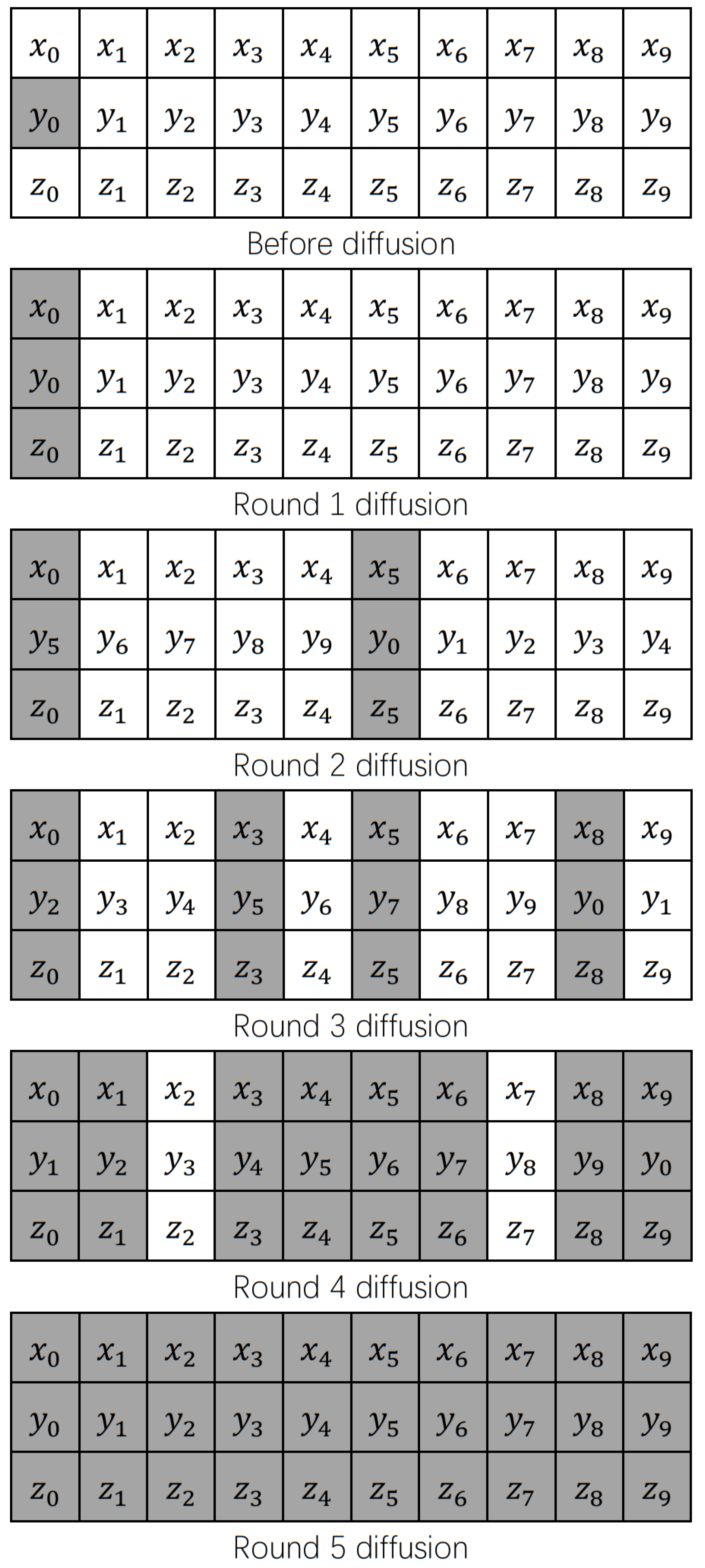
45] proposed a color image encryption algorithm based on Fisher-Yates scrambling and DNA subsequence operations (elongation operation, truncation operation, deletion operation and insertion operation), which uses the chaotic sequence generated by the Chen system and the Fisher-Yates scrambling method to scramble the plain image of the R, G and B channels, and then introduces DNA coding rules to destroy the scrambled plain-image information to obtain encrypted color images, which have good performance and can resist various typical attacks. Based on logistic sine–cosine mapping, the encryption algorithm in this paper generates the encryption sequence with high efficiency, and an efficient pixel scrambling method and three-round pixel diffusion method are designed based on the encryption sequence, which has high encryption efficiency, sufficient information entropy and good diffusion of cipher images. The encryption diagram and decryption diagram are shown in
Figure 1 and
Figure 2, respectively.