Protection Schemes in HPON Networks Based on the PWFBA Algorithm
Abstract
1. Introduction
2. Network Traffic Protection in HPON Networks
3. PFWBA Algorithm Principles
3.1. E-DBA and PFEBR Principles
3.2. PFWBA Principles
- group 1: if ONUi
- group 2: Vi > VMean and ONUi
- group 3: otherwise
4. Simulation Program of the Advanced HPON Network Traffic Protection
4.1. Method 1—Uniform Utilization of Wavelengths
4.2. Method 2—Non-Uniform Utilization of Wavelengths
4.3. Method 3—Fixed Wavelength Priority Bandwidth Allocation FWBPA
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kramer, G. What Is Passive Optical Network? McGraw-Hill: New York, NY, USA, 2005; Volume 17. [Google Scholar]
- Sen, D.; Kaur, R.; Kaur, K.; Bhamrah, M.S. A Review on passive optical network with colorless onu technology. In Proceedings of the International Conference on Emerging Technologies: AI, IoT, and CPS for Science & Technology Applications, Chandigarh, India, 6–7 September 2021. [Google Scholar]
- Rodrigues, C.; Rodrigues, F.; Pinho, C.; Bento, N.; Amorim, M.; Teixeira, A. 25 and 50G optical access network deployment forecasts using bi-logistic curves. In Proceedings of the 2021 Optical Fiber Communications Conference and Exhibition (OFC), San Francisco, CA, USA, 6–10 June 2021; pp. 1–3. [Google Scholar] [CrossRef]
- Kumari, M.; Sharma, R.; Sheetal, A. A review of a hybrid IoT-NG-PON system for translational bioinformatics in healthcare. Transl. Bioinform. Healthc. Med. 2021, 13, 59–68. [Google Scholar] [CrossRef]
- Róka, R. Performance Analysis of TDM-PON Protection Schemes by Means of the PON Network Availability Evaluator. In Proceedings of the Seventh International Congress on Information and Communication Technology; Springer: Singapore, 2023; pp. 295–303. [Google Scholar] [CrossRef]
- Róka, R. Performance Analysis of Wavelength Division Multiplexing-Based Passive Optical Network Protection Schemes by Means of the Network Availability Evaluator. Appl. Sci. 2022, 12, 7911. [Google Scholar] [CrossRef]
- Róka, R.; Hudcová, L.; Koval’ová, A. The Performance Analysis of the FSO System Utilization in the Long Reach PON Network using the HPON Network Configurator. In Proceedings of the 2022 45th International Conference on Telecommunications and Signal Processing (TSP), Prague, Czech Republic, 13–15 July 2022; pp. 164–168. [Google Scholar] [CrossRef]
- Róka, R. Hybrid PON Networks—Features, Architectures and Configuration; LAP LAMBERT ACADEMIC PUBL: London, UK, 2015. [Google Scholar]
- Bosternak, Z.; Róka, R. Bandwidth scheduling methods for the upstream traffic in passive optical networks. Prz. Elektrotechniczny 2018, 94, 1–4. [Google Scholar] [CrossRef]
- Bosternak, Z.; Róka, R. Approach of the T-CONT allocation to increase the bandwidth in passive optical networks. Radioengineering 2017, 26, 954–960. [Google Scholar] [CrossRef]
- Mahloo, M.; Dixit, A.; Chen, J.; Mas Machuca, C.; Lannoo, B.; Colle, D.; Wosinska, L. Toward reliable hybrid WDM/TDM passive optical networks. IEEE Commun. Mag. 2014, 52. [Google Scholar] [CrossRef]
- Mas Machuca, C.; Chen, J.; Wosinska, L. Cost-efficient protection in TDM PONs. IEEE Commun. Mag. 2012, 50, 110–117. [Google Scholar] [CrossRef]
- Imtiaz, W.A.; Iqbal, J.; Qamar, A.; Ali, H.; Idrus, S.M. Impact of fiber duplication on protection architectures feasibility for passive optical networks. In Optical Fiber and Wireless Communications; InTechOpen: London, UK, 2017. [Google Scholar] [CrossRef]
- Qiu, Y.; Chan, C.K. A novel survivable architecture for hybrid WDM/TDM passive optical networks. Opt. Commun. 2014, 312, 52–56. [Google Scholar] [CrossRef]
- Wong, E.; Machuca, C.M.; Wosinska, L. Survivable hybrid passive optical converged network architectures based on reflective monitoring. J. Light. Technol. 2016, 34, 4317–4328. [Google Scholar] [CrossRef]
- Róka, R. Optimization of traffic protection schemes for utilization in hybrid passive optical networks. Int. J. Appl. Innov. Eng. Manag. 2016, 5, 107–116. [Google Scholar]
- Róka, R. Converged Fi-Wi passive optical networks and their designing using the HPON network configurator. In Paving the Way for 5G Through the Convergence of Wireless Systems; IGI Global: Hershey, PA, USA, 2019; pp. 150–184. [Google Scholar] [CrossRef]
- Róka, R. Optimization of the optical power budget for various WDM-PON network designs with traffic protection securing. In Proceedings of the 2018 26th International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Split, Croatia, 13–15 September 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Hwang, I.-S.; Shyu, Z.-D.; Chang, C.-C.; Lee, J.Y. Fault-tolerant architecture with dynamic wavelength and bandwidth allocation scheme in WDM-EPON. Photonic Netw. Commun. 2009, 18, 160–173. [Google Scholar] [CrossRef]
- Radivojevic, M.R.; Matavulj, P. Novel wavelength and bandwidth allocation algorithms for WDM EPON with QoS support. Photonic Netw. Commun. 2010, 20, 73–182. [Google Scholar] [CrossRef]
- Róka, R. Wavelength allocation and scheduling methods for various WDM-PON network designs with traffic protection securing. In Design, Implementation, and Analysis of Next Generation Optical Networks; IGI Global: Hershey, PA, USA, 2020; pp. 1–39. [Google Scholar] [CrossRef]
- Róka, R.; Mokráň, M. Performance analysis and selection of wavelength channels based on the FWM effect influence in optical DWDM systems. Simul. Model. Pract. Theory 2022, 118, 102558. [Google Scholar] [CrossRef]
- Róka, R. An effective evaluation of wavelength scheduling for various WDM-PON network designs with traffic protection provision. Symmetry 2021, 13, 1540. [Google Scholar] [CrossRef]

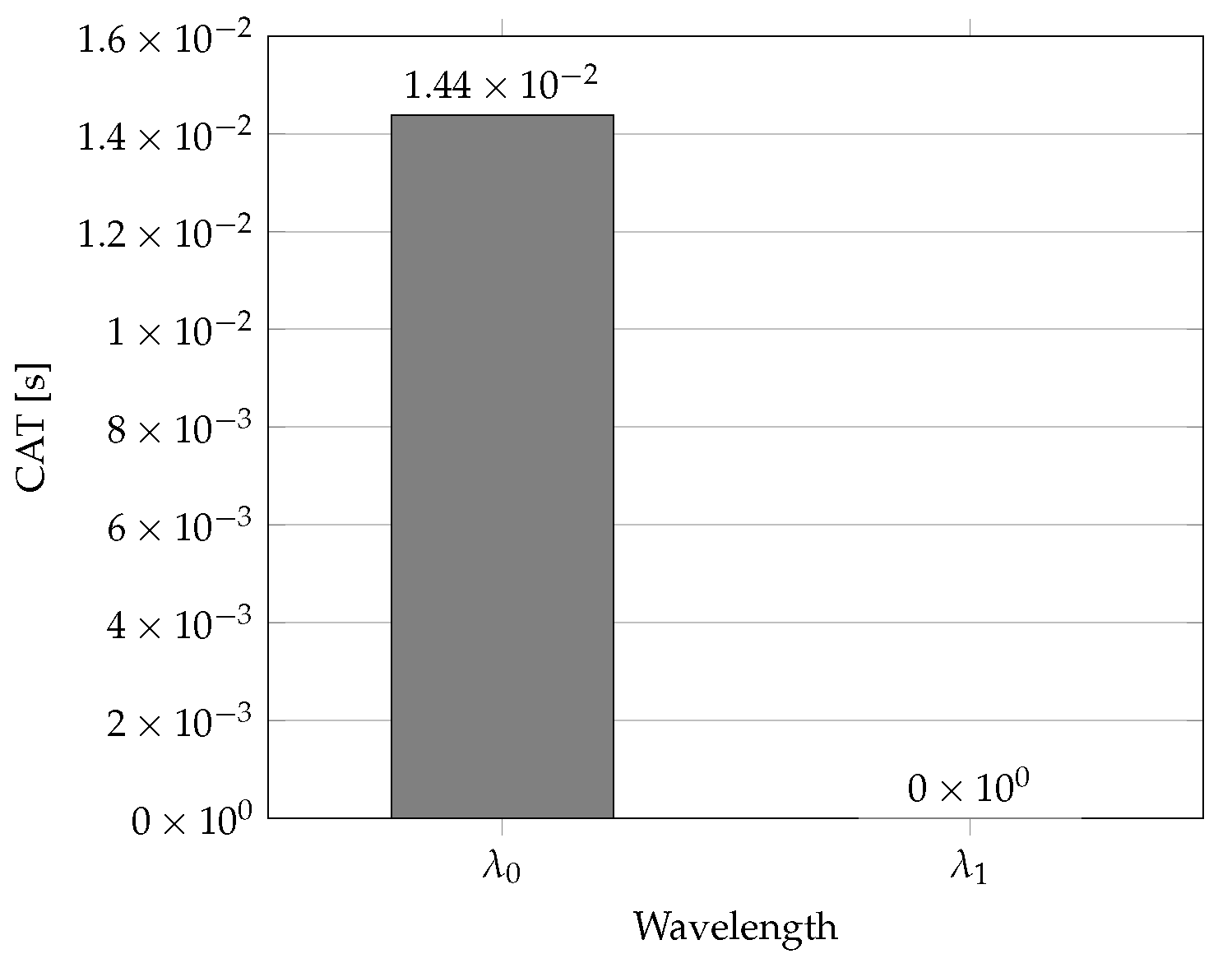
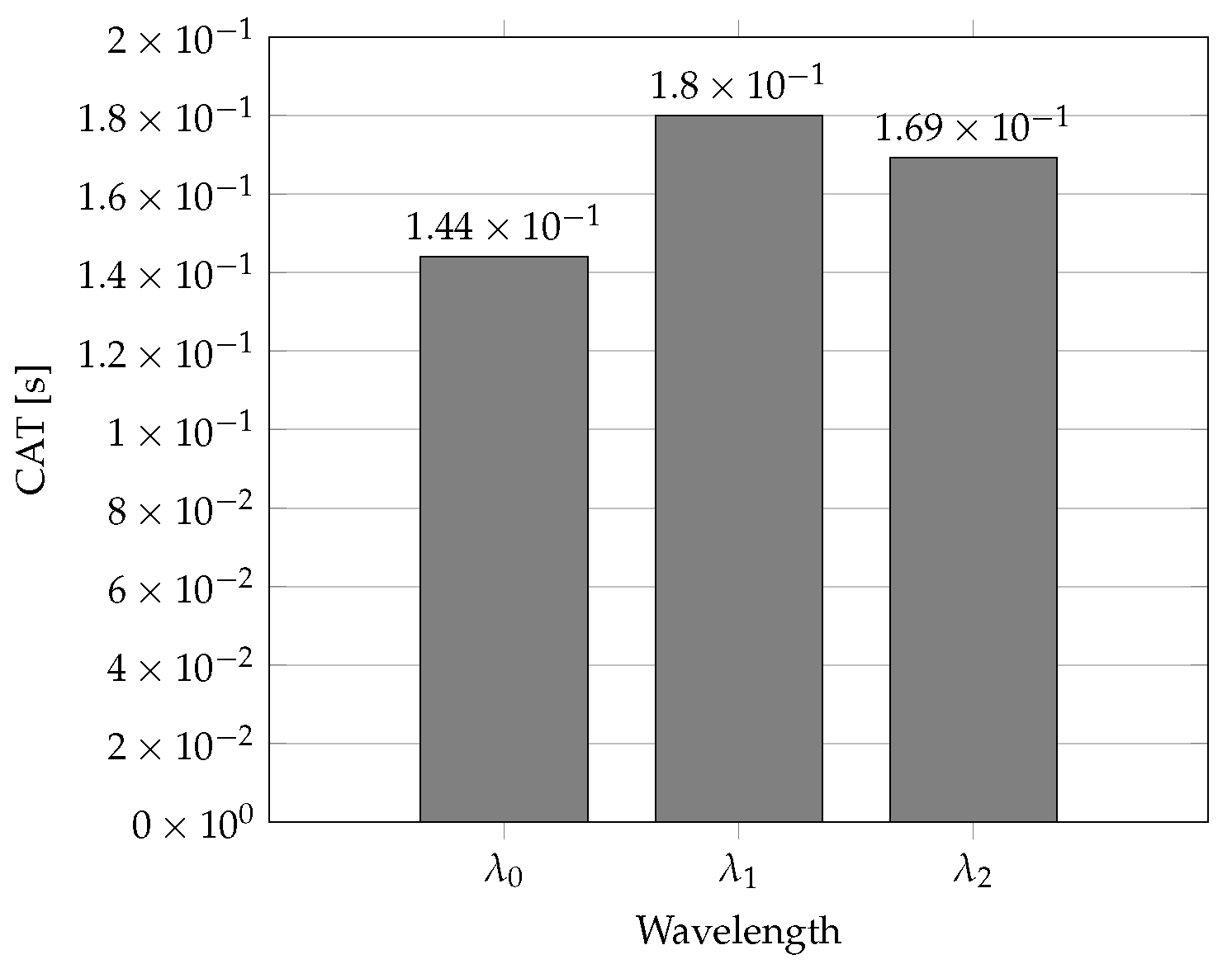
| Parameter | Parameter Value |
|---|---|
| Service cycle duration | 2 ms |
| Guard time | 5 μs |
| RTT range | 50–200 μs |
| OLT capacity per 1 wavelength | 1 Gbps |
| Number of ONU units | 8 |
| Number of units in the UDL | 2 |
| Number of ONU wavelengths | 2 (method 1 and 2) 3 (method 3) |
| ONU No. | Median | EF_pred. | AF_pred. | BE_pred. | EF_grant | AF_grant | BE_grant | Total Granted | Wavelength No. |
|---|---|---|---|---|---|---|---|---|---|
| 0 | 2,347,024 | 0 | 4102 | 9995 | 0 | 4102 | 9995 | 14,097 | 0 |
| 1 | 8,952,064 | 1451 | 3530 | 8172 | 1451 | 3530 | 8172 | 13,153 | 1 |
| 2 | 19,351,201 | 5815 | 17,645 | 10,351 | 5815 | 17,645 | 10,351 | 33,811 | 0 |
| 3 | 55,532,304 | 4265 | 16,029 | 7162 | 4265 | 16,029 | 7162 | 27,456 | 0 |
| 4 | 33,031,001 | 6368 | 10,869 | 26,075 | 6368 | 18,069 | 26,075 | 50,512 | 1 |
| 5 | 196,077,476 | 1595 | 34,140 | 4363 | 1595 | 34,140 | 4363 | 40,098 | 0 |
| 6 | 864,900 | 505 | 2041 | 8482 | 505 | 2041 | 8482 | 11,028 | 1 |
| 7 | 92,679,129 | 745 | 0 | 1461 | 745 | 0 | 1461 | 2206 | 1 |
| ONU No. | Median | EF_pred. | AF_pred. | BE_pred. | EF_grant | AF_grant | BE_grant | Total Granted | Wavelength No. |
|---|---|---|---|---|---|---|---|---|---|
| 0 | 58,064,400 | 2119 | 0 | 5501 | 2119 | 0 | 5501 | 7620 | 0 |
| 1 | 6,948,496 | 5148 | 0 | 5141 | 5148 | 0 | 5141 | 10,289 | 0 |
| 2 | 274,576 | 8804 | 19,971 | 0 | 8804 | 19971 | 0 | 28,775 | 0 |
| 3 | 30,140,100 | 5037 | 23,569 | 4393 | 5037 | 23,569 | 4393 | 32,999 | 0 |
| 4 | 75,012,921 | 0 | 22,934 | 10,713 | 0 | 22,934 | 10,713 | 33,647 | 0 |
| 5 | 16,297,369 | 2088 | 6729 | 5312 | 2088 | 6729 | 5312 | 14,129 | 0 |
| 6 | 1,092,025 | 4560 | 0 | 2045 | 4560 | 0 | 2045 | 6605 | 0 |
| 7 | 31,329 | 4162 | 0 | 0 | 4162 | 0 | 0 | 4162 | 0 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Róka, R.; Fujdiak, R.; Holasova, E.; Kuchar, K.; Orgon, M.; Misurec, J. Protection Schemes in HPON Networks Based on the PWFBA Algorithm. Sensors 2022, 22, 9885. https://doi.org/10.3390/s22249885
Róka R, Fujdiak R, Holasova E, Kuchar K, Orgon M, Misurec J. Protection Schemes in HPON Networks Based on the PWFBA Algorithm. Sensors. 2022; 22(24):9885. https://doi.org/10.3390/s22249885
Chicago/Turabian StyleRóka, Rastislav, Radek Fujdiak, Eva Holasova, Karel Kuchar, Milos Orgon, and Jiri Misurec. 2022. "Protection Schemes in HPON Networks Based on the PWFBA Algorithm" Sensors 22, no. 24: 9885. https://doi.org/10.3390/s22249885
APA StyleRóka, R., Fujdiak, R., Holasova, E., Kuchar, K., Orgon, M., & Misurec, J. (2022). Protection Schemes in HPON Networks Based on the PWFBA Algorithm. Sensors, 22(24), 9885. https://doi.org/10.3390/s22249885







