Botnet Defense System: Observability, Controllability, and Basic Command and Control Strategy
Abstract
1. Introduction
- The concept of observability and controllability was firstly introduced and discussed in the research area of botnet disinfection.
- The mechanism of command and control was clarified in terms of Petri nets [6] theoretically.
- A command and control strategy, named Withdrawal strategy, was proposed and the effect was quantitatively confirmed through simulation evaluation.
2. Related Work
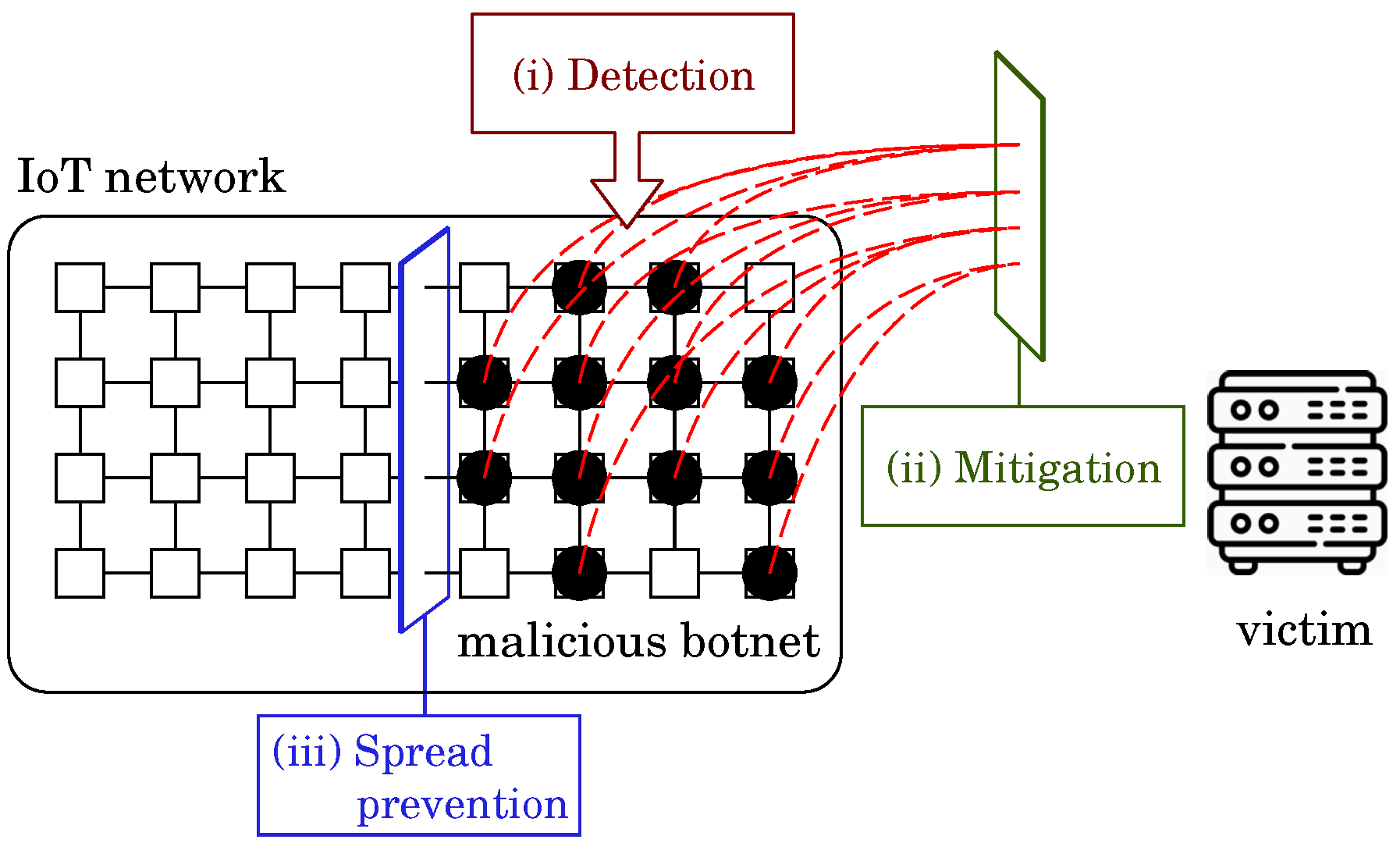
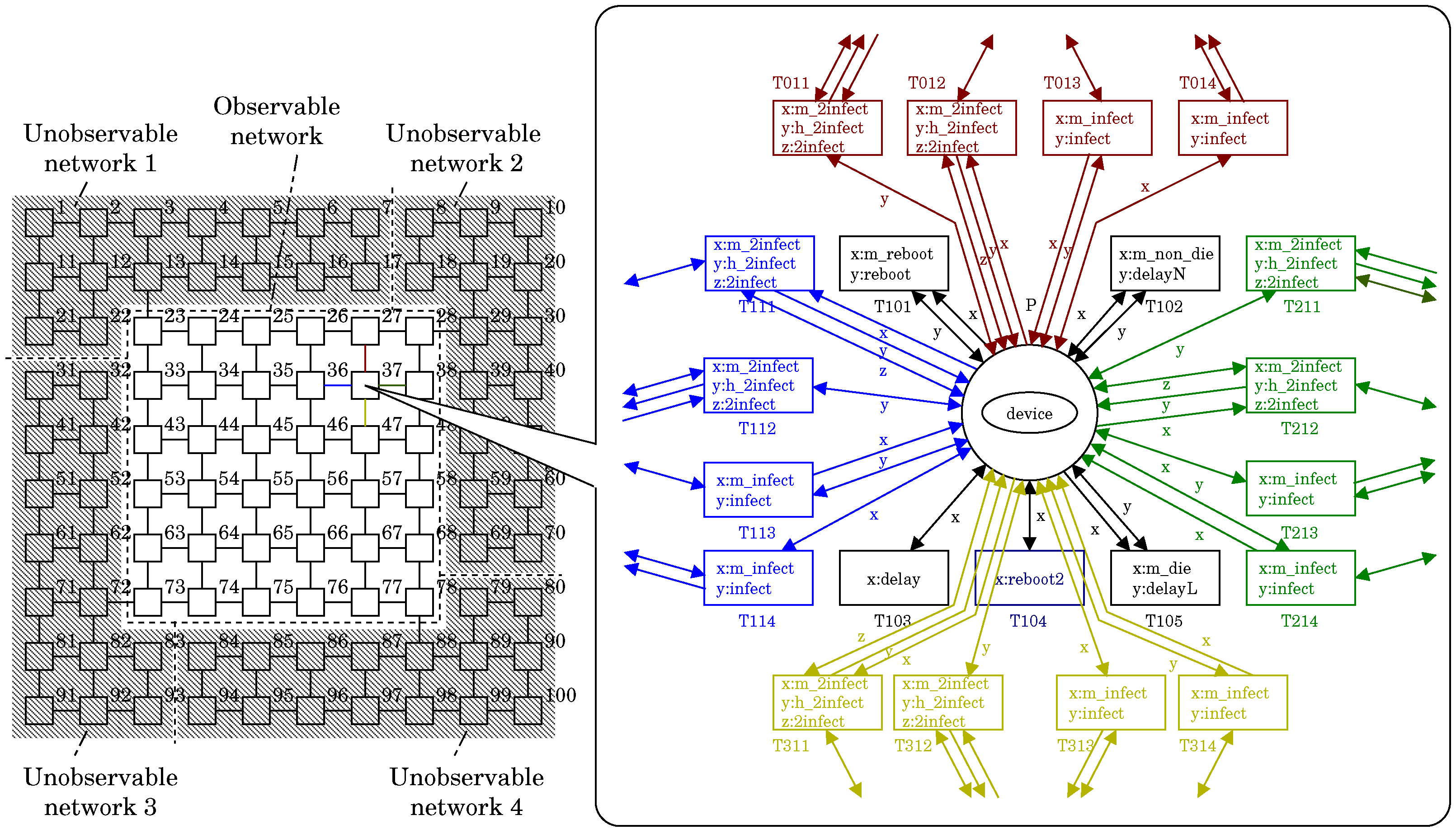
3. Botnet Defense System (BDS)
- Step 1
- Monitoring: Monitor the IoT system and check if the system is infected by any malicious botnet. Once detecting the malicious botnet, the BDS investigates it and collects the information such as its type and spread status.
- Step 2
- Strategy Planning: Plan strategies for disinfecting the malicious botnet based on the information obtained in Step 1.
- Step 3
- Botnet Building: Build the white-hat botnet by sending white-hat worms [23] to the IoT systems according to the strategy.
- Step 4
- Botnet C&C: Command and control the white-hat botnet spreading autonomously for disinfecting the malicious botnet according to the strategy.
- Lifespan: The worm is only available for a limited time. It will destroy itself at the end of a given time. That is, the time period means the lifespan of the white-hat worm. Even after the worm self-destructs, the device remains a white-hat bot and is immune until being rebooted.
- Secondary infectivity: The worm can infect the device that has already been a malicious bot and then clear the malicious bot from the device.
4. Observability, Controllability, and Command and Control Strategy
4.1. Observability and Controllability by BDS
- n is said to be observable by the BDS if the BDS can check whether there is any bot at n. If there is a connection from n to the BDS, the BDS can check whether there is any bot at n.
- n is said to be controllable by the BDS if the BDS can send a white-hat worm to n. If there is a connection from the BDS to n, the BDS can send a white-hat worm to n.
4.2. Observability and Controllability by White-Hat Bot
- is said to be observable by w if w can check whether there is any bot at . If there is a connection from to n, i.e., , w can check whether there is any bot at .
- is said to be controllable by w if w can send a white-hat worm to . If there is a connection from n to , i.e., , w can send a white-hat worm to .
4.3. Observability and Controllability by BDS via White-Hat Botnet
- w can exchange messages with the BDS if n is observable and controllable by the BDS.
- can exchange messages with w if is observable and controllable by w.
- Let u be a node unobservable by the BDS. u is said to be observable by the BDS via the white-hat botnet if the BDS can check whether there is any bot at u via the white-hat botnet.
- Let u be a node uncontrollable by the BDS. u is said to be controllable by the BDS via the white-hat botnet if the BDS can send a white-hat worm to u via the white-hat botnet.
- (i)
- Let u be a node of unobservable by the BDS. u is observable by the BDS via the white-hat botnet if and only if there is a white-hat bot w by which u is observable and a white-hat bot at a node observable by the BDS such that w is linked with .
- (ii)
- Let u be a node of uncontrollable by the BDS. u is controllable by the BDS via the white-hat botnet if and only if there is a white-hat bot w by which u is controllable and a white-hat bot at a node controllable by the BDS such that w is linked with .
- (i)
- Let u be a node of unobservable by the BDS. u is observable by the BDS via the white-hat botnet if and only if there is a path ρ between u and a node observable by the BDS such that every node on ρ has a white-hat bot except u.
- (ii)
- Let u be a node of uncontrollable by the BDS. u is controllable by the BDS via the white-hat botnet if and only if there is a path ρ between u and a node uncontrollable by the BDS such that every node on ρ has a white-hat bot except u.
4.4. Basic Command and Control Strategy
- The white-hat botnet is bloated and has too much waste compared to the benefits; or
- The white-hat botnet is too weak to disinfect the malicious botnet and should be rebuilt.
5. Simulation Evaluation
5.1. Modeling and Simulation
5.2. Evaluation Indicators
- Infection rate of malicious bots at simulation step t:where
- –
- is the number of nodes, i.e., devices, in the given network;
- –
- is the number of malicious bots in the whole network at t. This breaks down into:
- is the number of malicious bots on the nodes observable by the BDS at t;
- is the number of malicious bots on the nodes indirectly observable by the BDS via the white-hat botnet at t;
- is the number of malicious bots on the nodes unobservable by the BDS even via the white-hat botnet at t.
- Infection rate of white-hat bots at simulation step t:where
- –
- is the number of white-hat bots in the whole network at t. This breaks down into:
- is the number of white-hat bots on the nodes observable by the BDS at t;
- is the number of white-hat bots on the nodes indirectly observable by the BDS via the white-hat botnet at t;
- is the number of white-hat bots on the nodes unobservable by the BDS even via the white-hat botnet at t.
5.3. Hierarchical Case
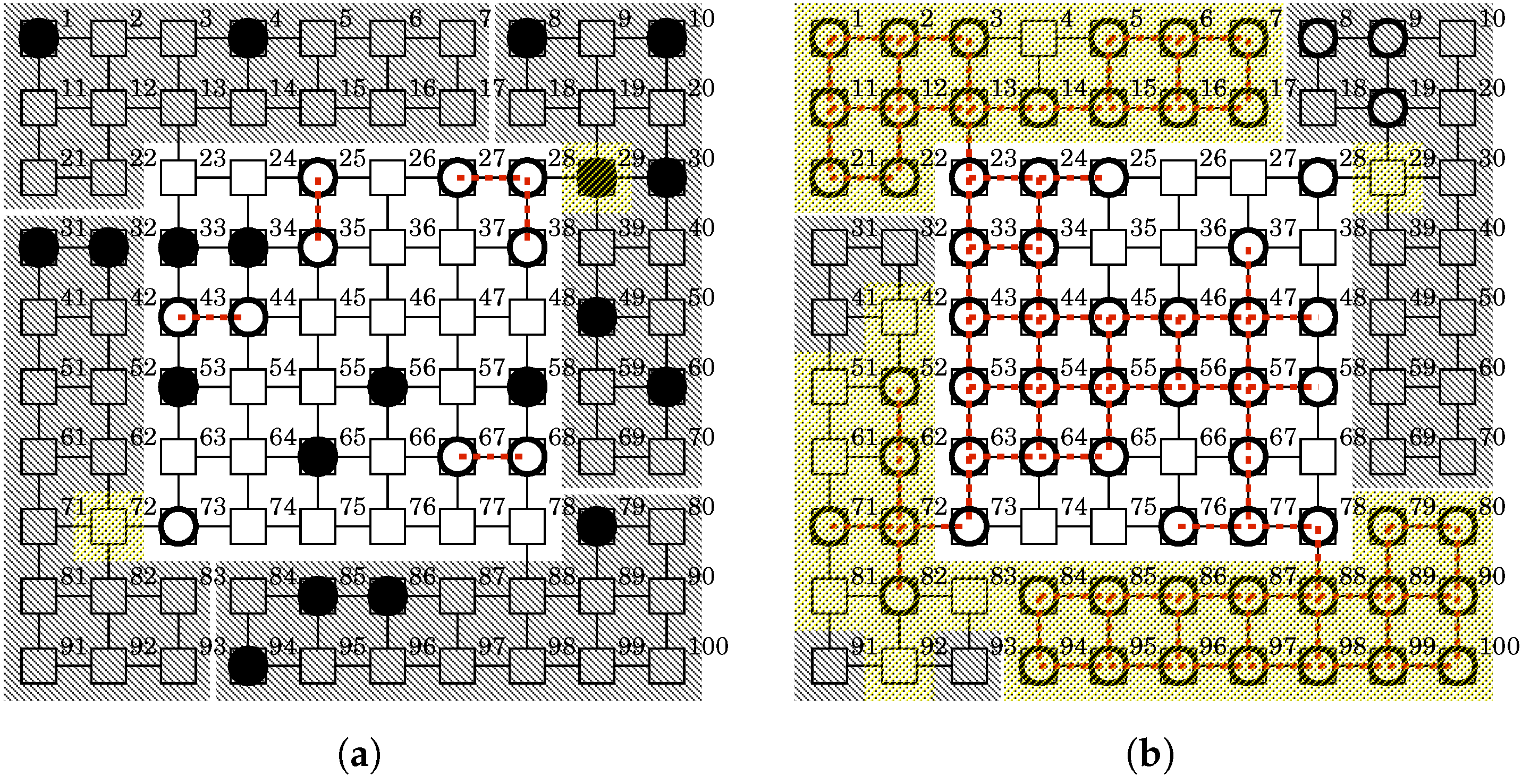
- Let when the BDS detects a malicious botnet and launches white-hat worms to build a white-hat botnet. Let and , respectively, denote before and after launching the white-hat worms. Assume the malicious botnet consists of 20 bots, i.e., and they are placed at random in the whole network.
- The BDS adopts the few-elite strategy and randomly sends 10 white-hat worms to observable nodes, i.e., . Figure 9a shows an example of the state at . Assume the white-hat worms have the capabilities below.
- Lifespan ℓ is 3, 4 or 5 steps
- Possibility of secondary infection is 50%
Assume each device reboots at 11 steps after infection. - When , the BDS adopts the Withdrawal strategy and commands the white-hat botnet to self-destruct. Let and , respectively, denote before and after sending the self-destruction order. Figure 9b shows an example of the state at .
5.4. General Case
- Number of observable and controllable nodes is 10, 20 or 30
- Number of white-hat worms launched by the BDS is 10, 20 or 30, but .
5.5. Discussion
6. Conclusions
- (i)
- Resident strategy of white-hat botnets: Malicious botnets will invade IoT systems not just once, but many times. This strategy aims to make a small number of the white-hat bots stay permanently so as to promptly respond to invading botnets at an earlier stage.
- (ii)
- Heterogeneous strategy of white-hat botnets: Like Mirai, white hat botnets have variants with different capabilities. This strategy aims to synergically enhance defense by operating multiple variants in combination.
- (iii)
- Reinforcement learning-based planning of building and C&C strategies of white-hat botnets: Supervised learning-based planning of strategies has been proposed in Reference [27] but requires data collection and labeling before learning. Reinforcement learning works well with multi-agent systems and is expected to dynamically optimize strategies without human intervention.
- (iv)
- Not only technical but also ethical, legal and social issues (ELSI), empirical testing and system implementation.
Funding
Conflicts of Interest
Appendix A
Appendix A.1. Proof of Property 1
Appendix A.2. Proof of Property 2
- (i)
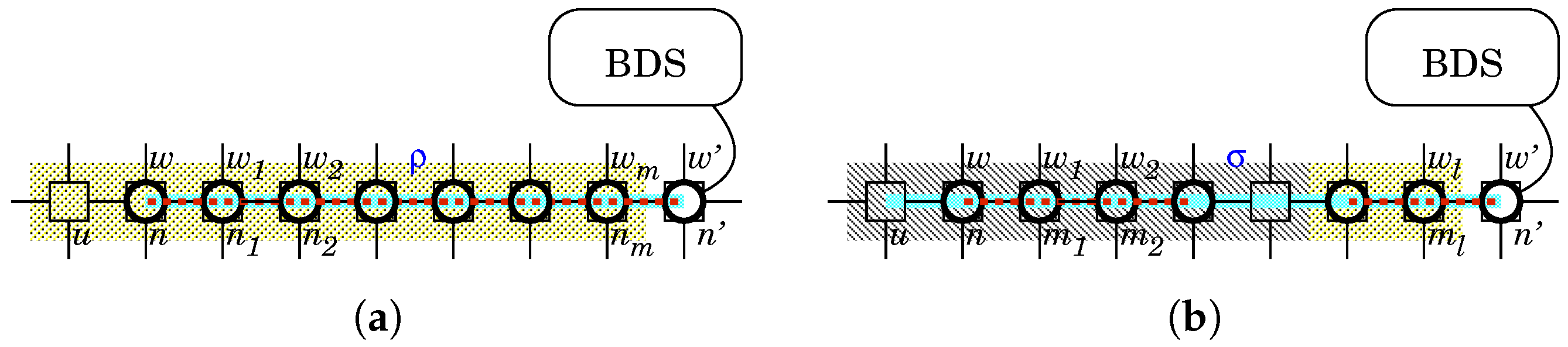
- The “if” part: w can check whether there is any bot at u from Definition 2 and then w can send the result as a message. w is linked with . From Definition 4, can receive the message from w. is observable by the BDS. From Definition 3, the BDS can receive the message from . Thus, the BDS can check whether there is any bot at u via the white-hat botnet.The “only if” part: Without w, there is no way to check whether there is any bot at u. Without , the BDS cannot receive any message from w and cannot check whether there is any bot at u.
- (ii)
- The “if” part: The BDS can create and send a message to launch a white-hat worm at u. is controllable by the BDS. From Definition 3, can receive the message from the BDS. is linked with w. From Definition 4, w can receive the message from . u is controllable by w. From Definition 2, w can send the white-hat worm to u. Thus, the BDS can send the white-hat worm to u via the white-hat botnet.The “only if” part: Without w, there is no way to launch a white-hat worm at u. Without , the BDS cannot send any message to w and cannot launch a white-hat worm at u.□
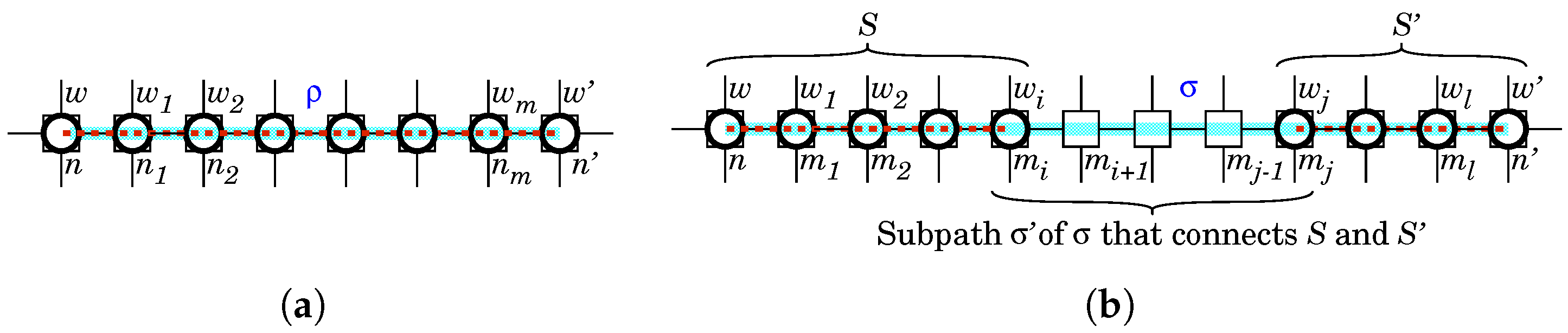
Appendix A.3. Proof of Corollary 1
- (i)
- The “if” part: Assume is denoted by a sequence of nodes . Every node on has a white-hat bot except u. Let w and be, respectively, white-hat bots at n and . u is observable by w because u is adjacent to n. w is linked with from Property 1 because and have a white-hat bot. is observable by the BDS. Thus, from Property 2, u is observable by the BDS via the white-hat botnet.The “only if” part: Assume that there is a white-hat bot w by which u is observable. Let n be a node that has w. Since there is not any path between n and such that every node on the path has a white-hat bot, w is not linked with from Property 1. Therefore from Property 2, u is not observable by the BDS via the white-hat botnet. On the other hand, assume that there is no white-hat bot by which u is observable. The proof follows immediately from Property 2.
- (ii)
- Similar to the proof of (i).□
References
- Antonakakis, M.; April, T.; Bailey, M.; Bernhard, M.; Bursztein, E.; Cochran, J.; Durumeric, J.; Halderman, J.A.; Invernizzi, L.; Kallitsis, M.; et al. Understanding the Mirai Botnet. In Proceedings of the 26th USENIX Security Symposium (SEC 2017), Vancouver, BC, Canada, 16–18 August 2017; pp. 1093–1110. [Google Scholar]
- Mirai BotNet. Available online: https://github.com/jgamblin/Mirai-Source-Code (accessed on 15 November 2018).
- US Computer Emergency Readiness Team. Heightened DDoS Threat Posed by Mirai and Other Botnets; Alert TA16-288A. Available online: https://www.us-cert.gov/ncas/alerts/TA16-288A (accessed on 29 October 2019).
- Yamaguchi, S. Botnet Defense System: Concept, Design and Basic Strategy. Information 2020, 11, 516. [Google Scholar] [CrossRef]
- Chen, T.M. Increasing the Observability of Internet Behavior. Commun. ACM 2001, 44, 93–98. [Google Scholar] [CrossRef]
- Murata, T. Petri nets: Properties, analysis and applications. Proc. IEEE 1989, 77, 541–580. [Google Scholar] [CrossRef]
- Hiraishi, K. A Petri-net-based model for the mathematical analysis of multi-agent systems. IEICE Trans. Fundam. 2001, 84, 2829–2837. [Google Scholar]
- Thanh Vu, S.N.; Stege, M.; El-Habr, P.I.; Bang, J.; Dragoni, N. A Survey on Botnets: Incentives, Evolution, Detection and Current Trends. Future Internet 2021, 13, 198. [Google Scholar] [CrossRef]
- Said, N.B.; Biondi, F.; Bontchev, V.; Decourbe, O.; Given-Wilson, T.; Legay, A.; Quilbeuf, J. Detection of Mirai by Syntactic and Semantic Analysis. In Proceedings of the 29th IEEE International Symposium on Software Reliability Engineering (ISSRE 2018), Memphis, TN, USA, 15–18 October 2018; pp. 224–235. [Google Scholar]
- Bezerra, V.H.; da Costa, V.G.T.; Barbon Junior, S.; Miani, R.S.; Zarpelão, B.B. IoTDS: A One-Class Classification Approach to Detect Botnets in Internet of Things Devices. Sensors 2019, 19, 3188. [Google Scholar] [CrossRef] [PubMed]
- Soe, Y.N.; Feng, Y.; Santosa, P.I.; Hartanto, R.; Sakurai, K. Machine Learning-Based IoT-Botnet Attack Detection with Sequential Architecture. Sensors 2020, 20, 4372. [Google Scholar] [CrossRef] [PubMed]
- Meidan, Y.; Bohadana, M.; Mathov, Y.; Mirsky, Y.; Breitenbacher, D.; Shabtai, A.; Elovici, Y. N-BaIoT: Network-Based Detection of IoT Botnet Attacks Using Deep Autoencoders. IEEE Pervasive Comput. 2018, 17, 12–22. [Google Scholar] [CrossRef]
- Hoang, X.D.; Nguyen, Q.C. Botnet Detection Based On Machine Learning Techniques Using DNS Query Data. Future Internet 2018, 10, 43. [Google Scholar] [CrossRef]
- Mihoub, A.; Fredj, O.B.; Cheikhrouhou, O.; Derhab, A.; Krichen, M. Denial of Service Attack Detection and Mitigation for Internet of Things Using Looking-Back-Enabled Machine Learning Techniques. Comput. Electr. Eng. 2022, 98, 107716. [Google Scholar] [CrossRef]
- Manso, P.; Moura, J.; Serrão, C. SDN-Based Intrusion Detection System for Early Detection and Mitigation of DDoS Attacks. Information 2019, 10, 106. [Google Scholar] [CrossRef]
- Ceron, J.M.; Steding-Jessen, K.; Hoepers, C.; Granville, L.Z.; Margi, C.B. Improving IoT Botnet Investigation Using an Adaptive Network Layer. Sensors 2019, 19, 727. [Google Scholar] [CrossRef] [PubMed]
- Khattak, S.; Ahmed, Z.; Syed, A.A.; Khayam, S.A. BotFlex: A community-driven tool for botnet detection. J. Netw. Comput. Appl. 2015, 58, 144–154. [Google Scholar] [CrossRef]
- Frank, C.; Nance, C.; Jarocki, S.; Pauli, W.E.; Madison, S.D. Protecting IoT from Mirai botnets; IoT device hardening. J. Inf. Syst. Appl. Res. 2018, 11, 33–44. [Google Scholar]
- Gopal, T.S.; Meerolla, M.; Jyostna, G.; Reddy Lakshmi Eswari, P.; Magesh, E. Mitigating Mirai Malware Spreading in IoT Environment. In Proceedings of the 2018 International Conference on Advances in Computing, Communications and Informatics (ICACCI 2018), Bangalore, India, 19–22 September 2018; pp. 2226–2230. [Google Scholar]
- Snort. Available online: https://www.snort.org/ (accessed on 19 December 2021).
- Suricata. Available online: https://suricata.io/ (accessed on 19 December 2021).
- Shinan, K.; Alsubhi, K.; Alzahrani, A.; Ashraf, M.U. Machine Learning-Based Botnet Detection in Software-Defined Network: A Systematic Review. Symmetry 2021, 13, 866. [Google Scholar] [CrossRef]
- Yamaguchi, S. White-Hat Worm to Fight Malware and Its Evaluation by Agent-Oriented Petri Nets. Sensors 2020, 20, 556. [Google Scholar] [CrossRef] [PubMed]
- ASERT Team. OMG—Mirai Minions are Wicked. Available online: https://www.netscout.com/blog/asert/omg-mirai-minions-are-wicked (accessed on 10 December 2020).
- Molesky, M.J.; Cameron, E.A. Internet of Things: An Analysis and Proposal of White Worm Technology. In Proceedings of the 37th IEEE International Conference on Consumer Electronics (ICCE 2019), Las Vegas, NV, USA, 11–13 January 2019. [Google Scholar]
- Pan, X.; Yamaguchi, S. Machine Learning White-Hat Worm Launcher for Tactical Response by Zoning in Botnet Defense System. Sensors 2022, 22, 4666. [Google Scholar] [CrossRef] [PubMed]
- Pan, X.; Yamaguchi, S.; Kageyama, T.; Kamlin, M.H.B. Machine-Learning-Based White-Hat Worm Launcher in Botnet Defense System. Int. J. Softw. Sci. Comput. Intell. 2022, 14, 1–14. [Google Scholar] [CrossRef]







| Category | Techniques |
|---|---|
| Detection | Signature-based (Said et al. [9]) |
| Anomaly and host-based (Bezerra et al. [10], Soe et al. [11]) | |
| Anomaly and network-based (Meidan et al. [12], Hoang et al. [13]) | |
| Looking-Back Approach (Mihoub et al. [14]) | |
| Mitigation | Software-defined network control (Manso et al. [15]) |
| Adaptive network layer (Ceron et al. [16]) | |
| Open source extensible tool (Khattak et al. [17]) | |
| Spread prevention | Mitigation and preventive steps (US-CERT [3]) |
| Hardening and prevention scripts (Frank et al. [18]) | |
| Whitelist-based solution (Gopal et al. [19]) |
| (a) Lifespan Steps | ||||||||
|---|---|---|---|---|---|---|---|---|
| Step | Malicious Bots | White-Hat Bots | ||||||
| 5.79 | 0.00 | 14.21 | 20.00% | 0.00 | 0.00 | 0.00 | 0.00% | |
| 5.79 | 0.26 | 13.95 | 20.00% | 10.00 | 0.00 | 0.00 | 10.00% | |
| 23.48 | 0.51 | 43.40 | 67.39% | 7.55 | 6.17 | 3.08 | 16.80% | |
| 23.48 | 0.51 | 43.40 | 67.39% | 0.00 | 0.00 | 3.08 | 3.08% | |
| (b) LifespanSteps | ||||||||
| Step | Malicious Bots | White-Hat Bots | ||||||
| 5.79 | 0.00 | 14.21 | 20.00% | 0.00 | 0.00 | 0.00 | 0.00% | |
| 5.79 | 0.26 | 13.95 | 20.00% | 10.00 | 0.00 | 0.00 | 10.00% | |
| 0.71 | 0.38 | 1.72 | 2.81% | 29.81 | 33.06 | 10.41 | 73.28% | |
| 0.71 | 0.38 | 1.72 | 2.81% | 0.00 | 0.00 | 10.41 | 10.41% | |
| (c) LifespanSteps | ||||||||
| Step | Malicious Bots | White-Hat Bots | ||||||
| 5.79 | 0.00 | 14.21 | 20.00% | 0.00 | 0.00 | 0.00 | 0.00% | |
| 5.79 | 0.26 | 13.95 | 20.00% | 10.00 | 0.00 | 0.00 | 10.00% | |
| 0.00 | 0.00 | 0.00 | 0.00% | 32.72 | 43.62 | 8.18 | 84.52% | |
| 0.00 | 0.00 | 0.00 | 0.00% | 0.00 | 0.00 | 8.18 | 8.18% | |
| (a) Lifespan Steps | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Malicious Bots | White-Hat Bots | ||||||||||
| Step | Step | Step | Step | ||||||||
| 10 | 10 | 0.51 | 0.20 | 4.33 | 5.04% | 5.04% | 7.28 | 63.99 | 1.21 | 72.47% | 1.21% |
| 20 | 10 | 1.01 | 0.18 | 3.84 | 5.04% | 5.04% | 14.67 | 56.83 | 0.97 | 72.47% | 0.97% |
| 20 | 1.49 | 0.34 | 5.66 | 7.49% | 7.49% | 14.22 | 55.78 | 0.83 | 70.83% | 0.83% | |
| 30 | 10 | 1.52 | 0.17 | 3.35 | 5.04% | 5.04% | 21.96 | 49.75 | 0.77 | 72.47% | 0.77% |
| 20 | 2.24 | 0.30 | 4.95 | 7.49% | 7.49% | 21.42 | 48.68 | 0.73 | 70.83% | 0.73% | |
| 30 | 2.38 | 0.11 | 5.45 | 7.94% | 7.94% | 20.49 | 47.33 | 0.56 | 68.38% | 0.56% | |
| (b) LifespanSteps | |||||||||||
| Malicious Bots | White-Hat Bots | ||||||||||
| Step | Step | Step | Step | ||||||||
| 10 | 10 | 0.00 | 0.00 | 0.00 | 0.00% | 0.00% | 8.72 | 77.93 | 0.53 | 87.19% | 0.53% |
| 20 | 10 | 0.00 | 0.00 | 0.00 | 0.00% | 0.00% | 17.55 | 69.16 | 0.48 | 87.19% | 0.48% |
| 20 | 0.00 | 0.00 | 0.00 | 0.00% | 0.00% | 17.38 | 69.08 | 0.36 | 86.83% | 0.36% | |
| 30 | 10 | 0.00 | 0.00 | 0.00 | 0.00% | 0.00% | 26.30 | 60.52 | 0.37 | 87.19% | 0.37% |
| 20 | 0.00 | 0.00 | 0.00 | 0.00% | 0.00% | 26.19 | 60.31 | 0.32 | 86.83% | 0.32% | |
| 30 | 0.00 | 0.00 | 0.00 | 0.00% | 0.00% | 26.18 | 60.64 | 0.29 | 87.11% | 0.29% | |
| (c) LifespanSteps | |||||||||||
| Malicious Bots | White-Hat Bots | ||||||||||
| Step | Step | Step | Step | ||||||||
| 10 | 10 | 0.00 | 0.00 | 0.00 | 0.00% | 0.00% | 9.16 | 81.50 | 0.17 | 90.82% | 0.17% |
| 20 | 10 | 0.00 | 0.00 | 0.00 | 0.00% | 0.00% | 18.34 | 72.35 | 0.13 | 90.82% | 0.13% |
| 20 | 0.00 | 0.00 | 0.00 | 0.00% | 0.00% | 18.15 | 72.62 | 0.14 | 90.91% | 0.14% | |
| 30 | 10 | 0.00 | 0.00 | 0.00 | 0.00% | 0.00% | 27.47 | 63.23 | 0.12 | 90.82% | 0.12% |
| 20 | 0.00 | 0.00 | 0.00 | 0.00% | 0.00% | 27.33 | 63.46 | 0.13 | 90.91% | 0.13% | |
| 30 | 0.00 | 0.00 | 0.00 | 0.00% | 0.00% | 27.25 | 63.40 | 0.10 | 90.74% | 0.10% | |
| References | Detection | Mitigation | Spread Prevention | Disinfection | Observability & Controllability, C&C |
|---|---|---|---|---|---|
| Said et al. (2018) [9] | × | × | × | × | |
| Bezerra et al. (2019) [10] | × | × | × | × | |
| Soe et al. (2020) [11] | × | × | × | × | |
| Meidan et al. (2018) [12] | × | × | × | × | |
| Hoang et al. (2018) [13] | × | × | × | × | |
| Mihoub et al. (2022) [14] | × | × | × | ||
| Manso et al. (2019) [15] | × | × | × | ||
| Ceron et al. (2019) [16] | × | × | × | × | |
| Khattak et al. (2015) [17] | × | × | × | × | |
| US-CERT (2016) [3] | × | × | × | × | |
| Frank et al. (2018) [18] | × | × | × | × | |
| Gopal et al. (2018) [19] | × | × | × | × | |
| Yamaguchi (2020) [23] | × | × | × | × | |
| Pan et al. (2022) [26] | × | × | × | × | |
| This study (2022) | × | × | × |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yamaguchi, S. Botnet Defense System: Observability, Controllability, and Basic Command and Control Strategy. Sensors 2022, 22, 9423. https://doi.org/10.3390/s22239423
Yamaguchi S. Botnet Defense System: Observability, Controllability, and Basic Command and Control Strategy. Sensors. 2022; 22(23):9423. https://doi.org/10.3390/s22239423
Chicago/Turabian StyleYamaguchi, Shingo. 2022. "Botnet Defense System: Observability, Controllability, and Basic Command and Control Strategy" Sensors 22, no. 23: 9423. https://doi.org/10.3390/s22239423
APA StyleYamaguchi, S. (2022). Botnet Defense System: Observability, Controllability, and Basic Command and Control Strategy. Sensors, 22(23), 9423. https://doi.org/10.3390/s22239423






