HeriLedger—A New Generation of Blockchains for Cultural Heritage Preservation
Abstract
:1. Introduction
- Which technology, TBC or IOTA, better meets the heritage preservation needs when considering mobile phones (and IoT), along with sustainability, privacy with accountability, and quantum computing resistance? Can this be a variation of one of them or some hybrid solution?
- As current approaches often pay little attention to a fine-grained business context—what are the needs of the intended users and organizations in the given cultural heritage context?
- Apart from cryptocurrency, can there be another kind (or a variation) of users’ incentive for linking the technological and business domains?
- Is there a structured approach for appropriately linking the technological and business domains through business models, which can serve as a reference approach?
2. State-of-the-Art Overview and Evaluation
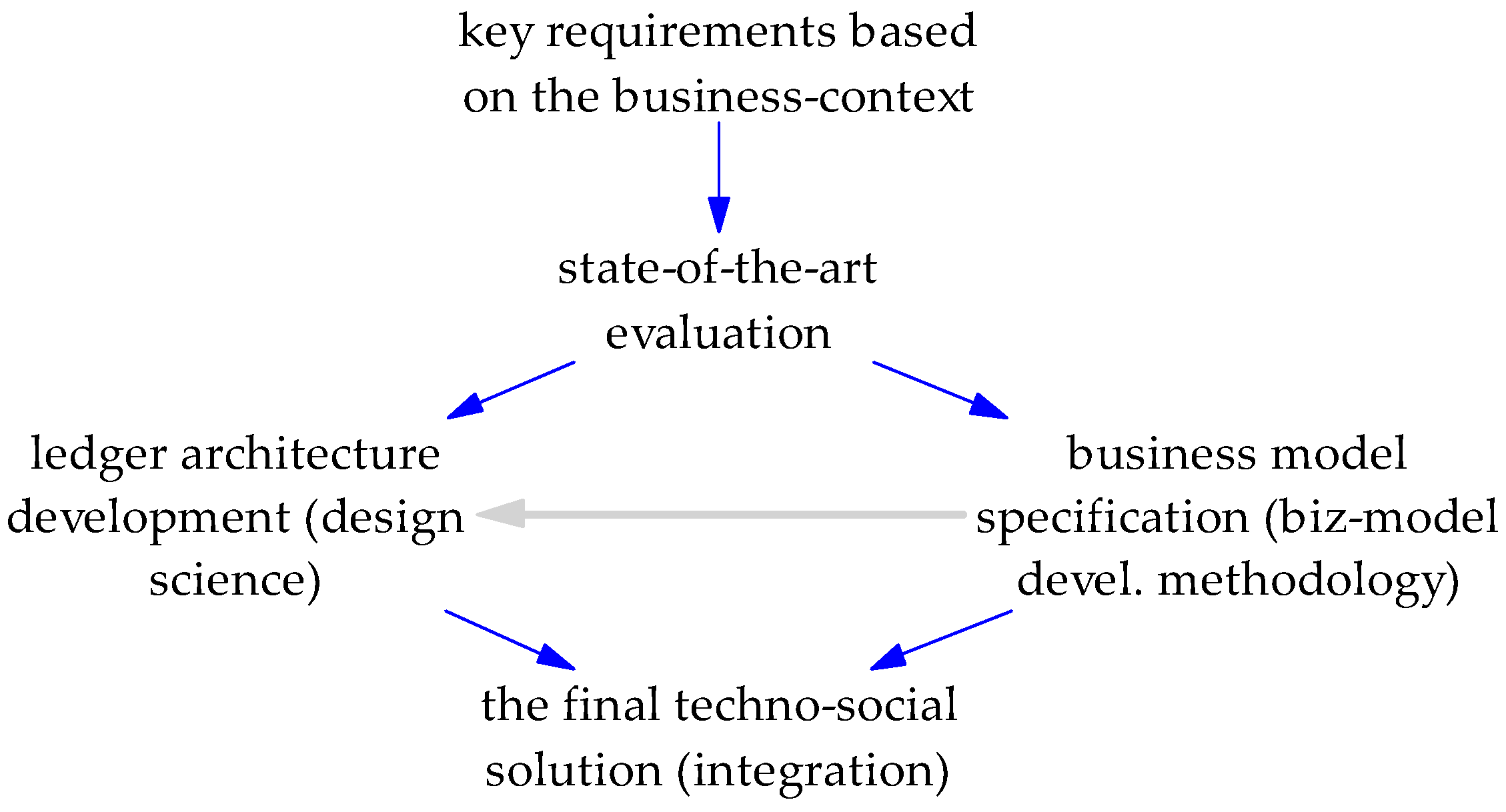
3. The Methodological Approach to HeriLedger Development
- Design science as the basis, complemented with,
- Risk management,
- Cryptographic protocols development,
- And business model development.
- The goal of the model is to enable the preservation of digital and digitized cultural heritage in an open and immutable way with DLTs based on cryptography.
- The solution should link the main players, which are cultural heritage institutions (like museums, galleries, and archeological sites), with the main users, which are domestic and foreign tourists and education institutions. By doing so, it should reduce preservation costs for cultural institutions while providing tangible benefits to the users.
- The solution should enable adding value by, e.g., enabling the use of the artifacts preserved in a DLT in new ways such as mixed reality, virtual reality, etc.
- The main purpose of the developed DLT is the preservation of the artifacts and not transactions with them—although these may happen, their volume can be neglected (e.g., a transfer of ownership in case of donations or a relocation from a gallery into a museum, etc.).
- The solution should meet the technological reality—by focusing on smartphones, even undeveloped countries can benefit from the solution (note that according to [26], 83.72% of the world population owns a smartphone).
3.1. The Business Context Elaboration
3.2. Technological Solution Development
- A signer generates a secret key sk, which consists of two sequences of 256 b long random values:
- 2.
- Next, the signer generates the corresponding public key pk that also consists of two sequences, each 256 b long, which are obtained by hashing the secret key values. The obtained sequences are made publicly available, and these represent the signer’s public key:
- 3.
- When signing a file F, the signer first hashes the file and looks at the i-th bit in the hash—if this bit equals 0, the signature value is sk0,I; otherwise, it is sk1,i. Now when any third party checks the signature, (s)he hashes the i-th position in the signature of F. If it equals 0, the check is made with H(sk0,i) (if its value is pk0,i); for value 1 at the i-th position, pk1,i is compared with H(sk1,i).
- A signer generates the initial (parent) public and secret key pair:
- 2.
- Afterward, s/he generates n (child) secret keys and stores the initial {,} pair:
- 3.
- Next, by hashing the private keys’ values, given in step 2 (s)he obtains the corresponding (child) public keys.
- 4.
- Finally, the signer uses these public-private key pairs in reverse order, making the first signature withThen with , and so on in the corresponding reverse manner the private keys are used.
- M authenticates his/her mobile phone to the wallet via mph. The wallet generates a challenge that is sent via mobile network to the phone. The user enters the challenge, which activates the wallet.
- M’s wallet calculates H(pkn || mpn) = pa, where pa stands for M’s linkable public address, and announces this public address (in ordinary TBC, public address is only a hashed public key value, extended with a checksum value, which can be also added in the case of PwLID). M’s wallet discards the mpn.
- When successful, the network awards M with an e-coupon by digitally signing a transaction of this e-coupon to pa.
- When M wants to spend the e-coupon, (s)he does so at I by making a transaction with her/his private key skn to the institution’s (“sink”) public address.
- To prevent forgery, the institution I requires her/his pkn to check the signature.
- Next, the institution I starts the ZKP to verify that M knows the secret behind pa, i.e., his/her mpn (so that the right mobile phone number is awarded, the one that has spent computing resources). ZKP is such that it is quantum computing resistant, e.g., [38].
- If there is a reason to break privacy (accountability is required), I also requires the mpn to fully check the transaction and indirectly identify M before accepting the e-coupon.
- Version of the software/protocol,
- The serial number SN of the transaction block,
- The hash of the previous block (except for the first block),
- The transactions’ Merkle’s tree root,
- The nonce N of the block that has led to “solution” of the block that is being mined,
- The timestamp when the block was approved (obtained from a mobile network).
- The transaction header with a serial number in the form SN.M, where SN denotes a block’s serial number, and M denotes transaction’s serial number within the block;
- The awarded e-coupon with the transaction’s block serial number (each coupon has a fixed value) linked to a pa;
- The spending of the e-coupon, one for each e-coupon issued (in case of unspent e-coupon, this value is “null”, otherwise this field has the owner’s signature of the consumed e-coupon to a “sink address” of an institution where the e-coupon was exchanged for a tangible product or a service);
- The hash value of the (preserved) cultural artifact;
- The URL pointing to the location where the mentioned digital/digitized artifact is stored (this field can also be used as a cross-ledger link, e.g., an URL pointer to an NFT ledger).
3.3. Business Model Specification
- (a)
- Customer segments include domestic and foreign tourists, where the meaning of tourists has to be interpreted rather broadly to include visitors to galleries, cultural events, attendees, etc. It is common for all of them that they provide free computational resources on their mobile phones for HeriLedger.
- (b)
- Value proposition is manyfold. Regarding cultural heritage institutions, the value proposition is to reduce their operations’ costs by outsourcing the heritage preservation processes. Regarding the tourists, these become a part of something of greater importance, while the services offered can be the basis for additional added value, e.g., in enhanced or virtual reality applications. This latter case is especially appropriate for educating children and younger generations. As to society in general, this solution enables wider, even global, accessibility to cultural heritage.
- (c)
- Key activities are certainly documentation and preservation of cultural artifacts, which, if not already digital, have to be digitized. Further, the central key activity is the initial production of the HeriLedger application, while its maintenance is not expected to require notable inputs. Due to its nature, this app could be open source, initially funded by a national government or EU funds. Finally, appropriate coordination with tourist organizations is needed.
- (d)
- Key partnerships are mainly those related to tourist organizations. Clear interests of tourist organizations must be identified. The direct incomes are straightforward to identify, but the proposed solution contributes to the incomes indirectly by increasing tourist visits. This leads to higher incomes in this sector and gross domestic product in general.
- (e)
- Key resources are digitized and digital cultural heritage artifacts, tourists, and the mobile app for bootstrapping and maintaining the new ledger. It is necessary to emphasize that the related APIs will make it an open solution and enable its use by other services, such as augmented and virtual reality.
- (f)
- Costs’ structure includes core processes costs and their migration to the mobile app development and maintenance, and marketing of the new ledger service until it is accepted, i.e., up and running. However, if open-source implementation is provided, the latter costs will be negligible for cultural institutions.
- (g)
- Customer relationships—these cover primarily tourists with their involvement in the heritage preservation processes through e-coupons, being traded for underutilized mobile phones and computing resources.
- (h)
- Channels—the main one is the so far weak (or non-existing link) between the tourist sector and the heritage preservation sector. This will be another important improvement enabled by HeriLedger solution.
- (i)
- Revenue streams are directly identifiable by heritage organizations and institutions, while for tourist organizations, they are, as mentioned, mainly indirect. This will likely require certain state involvement to promote the presented approach until its benefits become visible to a larger society.
4. Discussion
- Sybil attack and general security,
- e-coupons stealing and their double spending,
- privacy provisioning,
- quantum computing resistance and,
- lightweight implementation.
5. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Statista, Number of Cryptocurrencies Worldwide from 2013 to January 2022; Hamburg, Germany, 2022.
- Goldman Sachs CEO David Solomon Believes Blockchain Is More Important Than Bitcoin—Blockchain Bitcoin News. Available online: https://news.bitcoin.com/goldman-sachs-ceo-david-solomon-believes-blockchain-is-more-important-than-bitcoin/ (accessed on 13 October 2022).
- Will NFTs Finally Fulfill the Blockchain Promise to Music? Available online: https://www.forbes.com/sites/bobbyowsinski/2021/03/07/will-nfts-finally-fulfill-the-blockchain-promise-to-music/?sh=7a8051ec5b9e (accessed on 13 October 2022).
- Baraniuk, C. Bitcoin’s Energy Consumption “Equals that of Switzerland”. Available online: https://www.bbc.com/news/technology-48853230 (accessed on 10 November 2022).
- Tully, S. Bitcoin Mining is Being Banned in Countries across the Globe—And Threatening the Future of Crypto. Available online: https://fortune.com/2022/01/05/crypto-blackouts-bitcoin-mining-bans-kosovo-iran-kazakhstan-iceland/ (accessed on 10 November 2022).
- Statista, Number of Internet of Things (IoT) Connected Devices Worldwide from 2019 to 2030; Hamburg, Germany, 2022.
- Hellani, H.; Sliman, L.; Samhat, A.E.; Exposito, E. Computing resource allocation scheme for DAG-based IOTA nodes. Sensors 2021, 21, 4703. [Google Scholar] [CrossRef] [PubMed]
- Malkov, A. What Makes a Blockchain Project Successful? Forbes, 2020. Available online: https://www.forbes.com/sites/forbesbusinesscouncil/2020/09/28/what-makes-a-blockchain-project-successful/ (accessed on 12 January 2022).
- De Haes, S.; van Grembergen, W. Enterprise Governance of Information Technology; Springer International Publishing: Cham, Switzerland, 2015. [Google Scholar] [CrossRef]
- Zhao, W. Tencent Mints NFTs to Digitize a World Heritage—On a Private Blockchain. Available online: https://www.theblock.co/post/117245/tencent-nft-mogao-caves-crypto (accessed on 12 September 2021).
- Van Aken, J.E. Management research as a design science: Articulating the research products of mode 2 knowledge production in management. Br. J. Manag. 2015, 16, 19–36. [Google Scholar] [CrossRef]
- Hevner, A.R.; March, S.T.; Park, J.; Ram, S. Design science in information systems research. MIS Q. 2004, 28, 75–105. [Google Scholar] [CrossRef] [Green Version]
- IOTA: Feeless and Free—IEEE Blockchain Initiative. Available online: https://blockchain.ieee.org/technicalbriefs/january-2019/iota-feeless-and-free (accessed on 16 September 2022).
- Franco, P. Understanding Bitcoin; John Wiley & Sons, Ltd.: Hoboken, NJ, USA, 2014. [Google Scholar] [CrossRef]
- Comer, D.E. Internetworking with TCP/IP, 2nd ed.; Prentice-Hall, Inc.: Hoboken, NJ, USA, 1991; Volume I. [Google Scholar]
- Kwok, Y.K.R. Peer-to-Peer Computing: Applications, Architecture, Protocols, and Challenges; Taylor and Francis Group, CRC Press: Boca Raton, FL, USA, 2011. [Google Scholar]
- Ullah, I.; de Roode, G.; Meratnia, N.; Havinga, P. Threat Modeling—How to Visualize Attacks on IOTA? Sensors 2021, 21, 1834. [Google Scholar] [CrossRef] [PubMed]
- Cullen, A.; Ferraro, P.; King, C.; Shorten, R. On the Resilience of DAG-Based Distributed Ledgers in IoT Applications. IEEE Internet Things J. 2020, 7, 7112–7122. [Google Scholar] [CrossRef]
- Popov, S. On the Timestamps in the Tangle; 2017. Available online: https://assets.ctfassets.net/r1dr6vzfxhev/4XgiKaTkUgEyW8O8qGg6wm/32f3a7c28022e35e4d5d0e858c0973a9/On_the_timestamps_in_the_tangle_-_20182502.pdf (accessed on 10 November 2022).
- Ferraro, P.; King, C.; Shorten, R. On the Stability of Unverified Transactions in a DAG-Based Distributed Ledger. IEEE Trans. Autom. Control 2020, 65, 3772–3783. [Google Scholar] [CrossRef] [Green Version]
- Akhtar, M.M.; Rizvi, D.R.; Ahad, M.A.; Kanhere, S.S.; Amjad, M.; Coviello, G. Efficient Data Communication Using Distributed Ledger Technology and IOTA-Enabled Internet of Things for a Future Machine-to-Machine Economy. Sensors 2021, 21, 4354. [Google Scholar] [CrossRef] [PubMed]
- Attias, V.; Vigneri, L.; Dimitrov, V. Preventing Denial of Service Attacks in IoT Networks through Verifiable Delay Functions. In Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020. [Google Scholar] [CrossRef]
- Jurcut, A.; Niculcea, T.; Ranaweera, P.; Le-Khac, N.-A. Security Considerations for Internet of Things: A Survey. SN Comput. Sci. 2020, 1, 193. [Google Scholar] [CrossRef]
- Tennant, L. Improving the Anonymity of the IOTA Cryptocurrency; 2018. Available online: https://blog.iota.org/research-on-private-transactions-in-iota-cd546751e2c4/ (accessed on 10 November 2022).
- Christidis, K.; Devetsikiotis, M. Blockchains and Smart Contracts for the Internet of Things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Venter, J.C.; Adams, M.D.; Myers, E.W.; Li, P.W.; Mural, R.J.; Sutton, G.G.; Smith, H.O.; Yandell, M.; Evans, C.A.; Holt, R.A.; et al. The Sequence of the Human Genome. Science 2001, 291, 1304–1351. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Osterwalder, A.; Pigneur, Y. Business Model Generation: A Handbook for Visionaries, Game Changers, and Challengers; John Wiley & Sons: Hoboken, NJ, USA, 2010. [Google Scholar]
- Trček, D. Managing Information Systems Security and Privacy; Springer: Heidelberg, Germany, 2006. [Google Scholar] [CrossRef]
- Turn Your Smartphone into an IoT Device—IBM Developer. Available online: https://developer.ibm.com/tutorials/iot-mobile-phone-iot-device-bluemix-apps-trs/ (accessed on 8 September 2022).
- Research & Development. Assuring Authenticity in the Tangle with Signatures; IOTA Foundation: Berlin, Germany, 2019. [Google Scholar]
- Gent, E. Cryptocurrency Blockchains Don’t Need To Be Energy Intensive. IEEE Spectr. 2021, 7. [Google Scholar]
- Fournier, B.; Tong, V.V.T.; Guette, G. Accurate measurement of the energy consumption of security functions. In Proceedings of the 18th International Conference on Security and Cryptography (SECRYPT 2021), Online, 6–8 July 2021; Available online: https://hal.inria.fr/hal-03510709 (accessed on 10 November 2022).
- Lamport, L. Constructing Digital Signatures from a One-Way Function. 1979. Available online: https://www.microsoft.com/en-us/research/publication/constructing-digital-signatures-one-way-function/ (accessed on 10 November 2022).
- Menezes, A.J.; Vanstone, S.A.; van Oorschot, P.C. Handbook of Applied Cryptography, 1st ed.; CRC Press, Inc.: Boca Raton, FL, USA, 1996. [Google Scholar]
- Avoine, G.; Hernandez-Castro, J. Security of Ubiquitous Computing Systems Selected Topics: Selected Topics; Springer: Cham, Switzerland, 2021. [Google Scholar] [CrossRef]
- Wuille, P. BIP-32 Specification; 2012. Available online: https://github.com/bitcoin/bips/blob/master/bip-0032.mediawiki (accessed on 10 November 2022).
- BC Community. BitCoin Core 23.0. 2022. Available online: https://github.com/bitcoin/bitcoin (accessed on 10 November 2022).
- Ben-Sasson, E.; Bentov, I.; Horesh, Y.; Riabzev, M. Scalable Zero Knowledge with No Trusted Setup. In Advances in Cryptology—CRYPTO 2019; Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), LNCS; Springer: Cham, Switzerland, 2019; Volume 11694, pp. 701–732. [Google Scholar] [CrossRef]
- Mikuz, M.; Stanic, M.O.; Kos, M.; Vute, M.; Goebl, R.; Waltl, C. Evalvacija Slovenskih Muzejev 2006–2008—Part 1; Ministry of Culture of Republic of Slovenia: Lubljana, Slovenia; Wien, Austria; Manama, Bahrain, 2010.
- Smartphone Subscriptions Worldwide 2027 | Statista. Available online: https://www.statista.com/statistics/330695/number-of-smartphone-users-worldwide/ (accessed on 8 September 2022).





| archeology | 3,800,000 |
| history | 1,700,000 |
| ethnology | 150,000 |
| fine arts and crafts | 400,000 |
| geology and natural history | 300,000 |
| science and technology | 10,000 |
| other | 200,000 |
| TOTAL | 6,560,000 |
| Computing Keys (mJ) | Signing (mJ) | Verification (mJ) | Number of Transactions/yr | Energy Costs/yr | |
| TBC | 60 (160 b) | 4.6 (160 b) | 0.7 (160 b) | 83,950,000 | ∞ |
| HeriLedger | 5184 | ~0 | 2591 | 10,000 | 5184 mJ × 10,000 = 51,840 J |
| current ledger size | Ledger growth/yr | quantum. comp. resistance | privacy with accountability | the rest of properties | |
| TBC | 400 GB | ~60 GB | NO | NO | ND (no difference) |
| HeriLedger | 27 MB | 10,000 × 4 KB ≈ 40 KB | YES | YES | ND (no difference) |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Trček, D. HeriLedger—A New Generation of Blockchains for Cultural Heritage Preservation. Sensors 2022, 22, 8913. https://doi.org/10.3390/s22228913
Trček D. HeriLedger—A New Generation of Blockchains for Cultural Heritage Preservation. Sensors. 2022; 22(22):8913. https://doi.org/10.3390/s22228913
Chicago/Turabian StyleTrček, Denis. 2022. "HeriLedger—A New Generation of Blockchains for Cultural Heritage Preservation" Sensors 22, no. 22: 8913. https://doi.org/10.3390/s22228913
APA StyleTrček, D. (2022). HeriLedger—A New Generation of Blockchains for Cultural Heritage Preservation. Sensors, 22(22), 8913. https://doi.org/10.3390/s22228913








