Abstract
Healthcare is an important medical topic in recent years. In this study, the novelty we propose is the intelligent healthcare system using an inequality-type optimization mathematical model with signal-to-noise ratio (SNR) and wavelet-domain low-frequency amplitude adjustment techniques to hide patients’ confidential data in their electrocardiogram (ECG) signals. The extraction of the hidden patient information also utilizes the low-frequency amplitude adjustment. The detailed steps of establishing the system are as follows. To integrate confidential patient data into ECG signals, we first propose a nonlinear model to optimize the quality of ECG signals with the embedded patients’ confidential data including patient name, patient birthdate, date of medical treatment, and medical history. Then, we apply Simulated Annealing (SA) to solve the nonlinear model such that the ECG signals with embedded patients’ confidential data have good SNR, good root mean square error (RMSE), and high similarity. In other words, the distortion of the PQRST complexes and the ECG shape caused by the embedded patients’ confidential data is very small, and thus the quality of the embedded ECG signals meets the requirements of physiological diagnostics. In the terminals, one can receive the ECG signals with the embedded patients’ confidential data. In addition, the embedded patients’ confidential data can be received and extracted without the original ECG signals. The experimental results confirm the efficiency that our method maintains a high quality of each ECG signal with the embedded patient confidential data. Moreover, the embedded confidential data shows a good robustness against common attacks.
1. Introduction
In recent years, the technology of Internet of Things (IoT), in which sensors are connected to the network to transmit important sensor information, has gradually matured [1,2,3,4,5,6,7]. Moreover, supporting medical treatment by IoT is even more important [8,9]. The electrocardiogram (ECG) represents the electrical activity of the human heart so that the ECG can be used as a reference for the analysis of cardiac pathology and the diagnosis of the cardiovascular system. Therefore, the ECG is a significant piece of bio-information which needs to be protected and transmitted in the hospital network, and it is necessary to apply the information hiding technology of ECG to protect patients’ rights and information.
Research on protecting ECG information through watermarking or masking techniques remains an important topic. Kong al. [10] and Engin et al. [11] proposed a method of simple data masking of ECG signals, but the method is not blind. Zheng and Qian [12,13] proposed a method to indicate wavelet-domain ECG data in complex non-QRS frames to ensure the recovery of practically undistorted ECG signals. Kuar et al. [14] used a blind masking method to present the secure transmission of ECG signals in wireless networks. Ibaida et al. [15] improved the LSB (Least Significant Bit) watermarking technique and applied this upgraded approach to embed health information into ECG signals. Ibaida et al. [16] announced a watermarking approach to hide patient biomedical information in ECG signals to ensure the integrity of the patient–ECG connection, which is convenient for a wearable health monitoring platform. Nonetheless, it is hard to select the embedding site.
Authors in [17,18] apply a discrete wavelet transform (DWT) with seven-level decomposition to transform the ECG signal and combine the synchronization code with a watermark embedded in the low-frequency sub-band of level 7 to get better Signal-to-Noise ratio (SNR) and bit error rate (BER). However, the quality of all watermarked ECG signals degrades when increasing the embedding strength. Furthermore, Guo and Zhou [18] proposed a model with blind detection by single-channel electromyography. Dey et al. [19] designed watermarks by reversible binary bits and embedded the watermarks into the PPG signal and extracted them based on an error prediction algorithm. Dey et al. [20] embedded the binary watermarked image into the ECG signal proposed so as to obtain a novel session-based blind watermarking method. However, both methods [19] and [20] have the drawback of not being blind. Ayman and Ibrahim [21] established a wavelet-based information-hiding technique that combines encryption and scrambling to protect patients’ confidential data. To protect patient rights and information, transform-domain single-coefficient quantization is administered to ECG digital watermark encryption technology [22,23]. By this practice, the distortion in the PQRST complexes and the amplitude of ECG signal is very small. Jero et al. [24,25] utilized curvelet transformation to determine coefficients for storing diagnostic information. The novelty in their method is the use of curvelet transformation, suitable selection for locating watermark, and a threshold judgement concept. In [26], the original time-frequency watermarking scheme is realized with a lead-independent beat-to-beat adaptive data container design. The authors demonstrated six wavelets, six encoding bit depth values, and two watermark content types to catch the necessary conditions for the watermarked ECG to fit International Electrotechnical Commission (IEC) performance requirements. Sanivarapu et al. [27] announced a wavelet-based watermarking procedure for the patient information hidden in the ECG as a QR image. First, they converted the 1D ECG signal into a 2D ECG image using the Pan–Tompkins algorithm and used a wavelet transform to decompose the 2D ECG image. Then, they decomposed the wavelet detail coefficient and the QR image using QR decomposition for incorporating the data. The concepts proposed in [28] are single-sample quantification, ECG watermarking, and threshold-based compression, which reduce data size while ensuring patient data confidentiality and authenticity.
Since patients’ confidential data including patient name, patient birthdate, date of medical treatment, and medical history have the right to personal privacy, the hospital and related personnel must respect and protect patients’ confidential data during network transmission or telemedicine in the hospital to prevent leaked, stolen, or even misappropriated data. Accordingly, we design a useful information-hiding technique to embed patients’ confidential data into ECG signals in this study. In other words, we propose a new technique to hide patients’ confidential data in ECG signals. Since ECG has high accuracy requirements, especially PQRST waves [29], we rewrite the signal-to-noise ratio (SNR) and the low-frequency amplitude embedding rule as a performance index and constraint so as to obtain an optimized model for embedding sensitive patients’ confidential data including patient name, patient birthdate, date of medical treatment, and medical history attached with patient bed into ECGs. The optimization model is processed by simulated annealing (SA) algorithms, and the results are applied to incorporate the confidential patient data for satisfying better signal-to-noise ratio (SNR), root mean square error (RMSE), and similarity. Consequently, the distortion of PQRST complexes and ECG amplitude is very low, so that the embedded confidential data can fit the requirements of physiological diagnostics. Through network transmission, the ECG with confidential data embedded can be received at the other end and the confidential data can be extracted without the original ECG. In addition, the embedded confidential data shows a good robustness against common attacks.
2. Preliminaries
In this section, we recall the knowledge we need to use in the later section: discrete wavelet transformation (DWT) and simulated annealing (SA).
2.1. Discrete Wavelet Transformation (DWT)
The discrete wavelet transformation using scaling and shifting parameters is defined by
Moreover, and provide that
From a multi-resolution analysis of and the subspaces represents the orthogonal differences of the above. The orthogonal relations give the existence of sequences and which conform to
where and are low-pass and high-pass filters, respectively. In the following work, the host digital audio signal , represents the sampling of the original audio signal at the nth sampling time, and the orthogonal Haar wavelet basis is utilized to realize the DWT of the host digital audio signal by filter bank [30,31].
2.2. Simulated Annealing (SA)
Simulated annealing (SA) is an artificial intelligence algorithm that utilizes a random way to approximate the global optimal value of a given function. The SA algorithm is derived from the principle of solid annealing. The solid is heated to a sufficient temperature, and then slowly cooled. During heating, the internal particles of the solid become disordered as the temperature rises, and the internal energy increases., but gradually tend to order, reach equilibrium at each temperature, and finally reach the ground state at room temperature. Then the internal energy is reduced to a minimum. According to the Metropolis criterion, the probability that a particle tends to equilibrium at temperature T is e − ΔE/(kT), where E is the internal energy at temperature T, ΔE is the change number, and k is the Boltzmann constant. Using solid annealing to simulate the combinatorial optimization problem, the internal energy E is simulated as the objective function value f, and the temperature T is evolved into the control parameter t, that is, the simulated annealing algorithm for solving the combinatorial optimization problem is obtained: starting from the initial solution i and the initial value of the control parameter t, the iteration of “generate new solution calculate difference of objective function accept or discard” is repeated for the current solution, the t value gradually decays, and the current solution at the end of the algorithm is the approximate optimal solution obtained. The annealing process is controlled by the cooling schedule (Cooling Schedule), including the initial value t of the control parameters and its decay factor Δt, the number of iterations at each t value, and the stopping condition [32]. The implementation of the SA algorithm is easy due to its simple concept and calculation.
3. Proposed Method
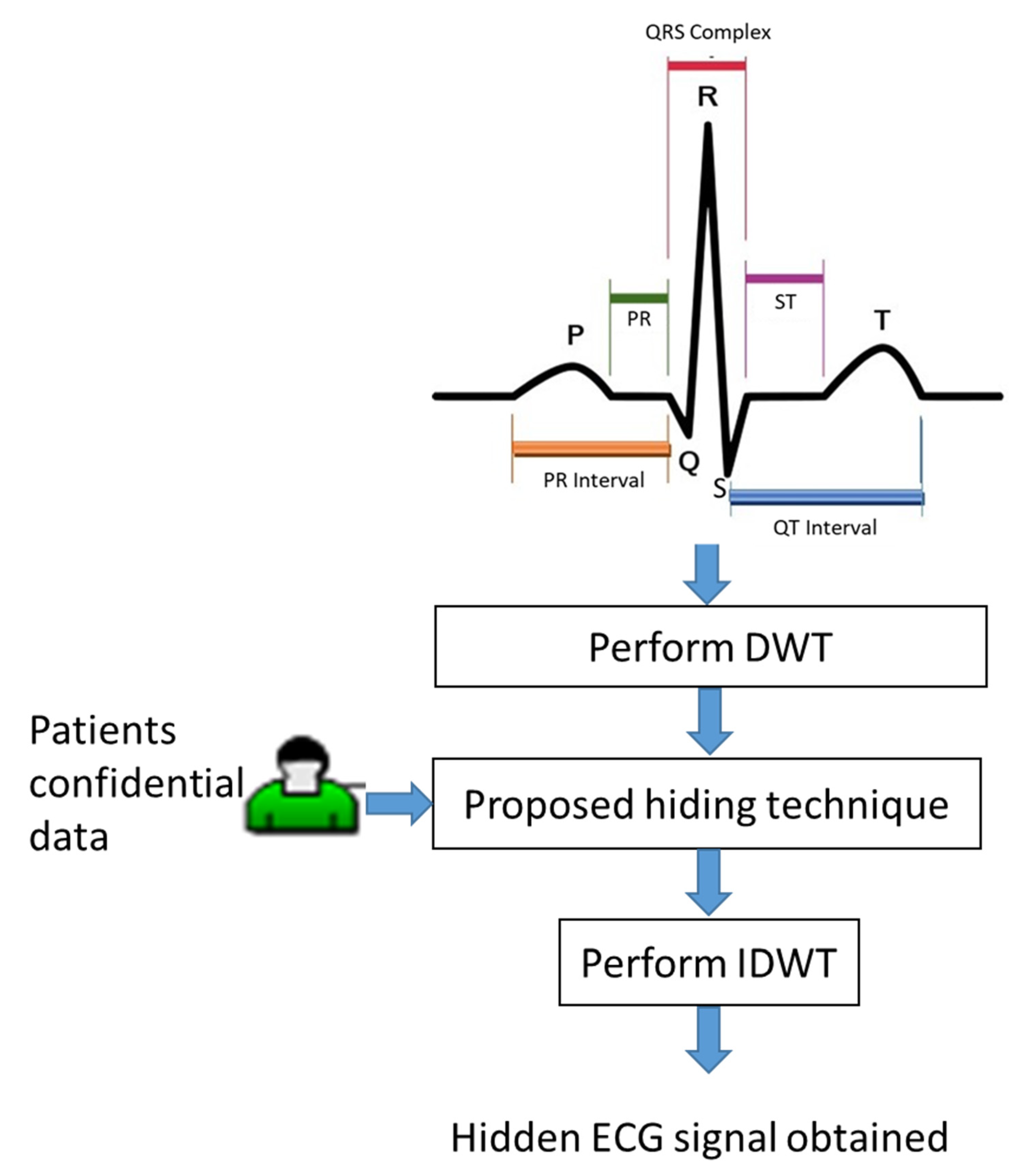
The electrocardiogram wave of electrocardiogram (ECG) signals was named by the Dutch physiologist W. Einthoven (the inventor of the ECG). He classified one cardiac cycle into P, Q, R, S, and T complex waves, which are shown in the ECG pattern at the top of Figure 1. Due to the fact that the ECG diagnosis is dependent on the PQRST waves [19], we have to avoid the shape distortion of these waveforms when we add patients’ confidential data including patient name, patient birthdate, date of medical treatment, and medical history into ECG signals. Accordingly, we propose an optimization model to maximize the quality of the embedded ECG signals under low-frequency amplitude modification. As the flowchart shows in Figure 1, we give the details of patients’ confidential data embedding in the following subsections.
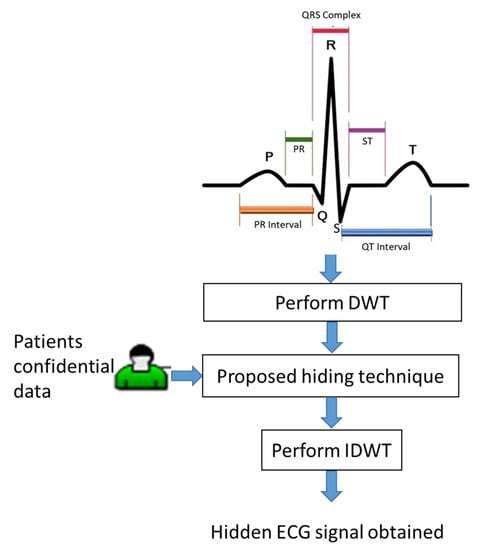
Figure 1.
A flowchart of the proposed embedding method.
3.1. Perform DWT and Binary Bits
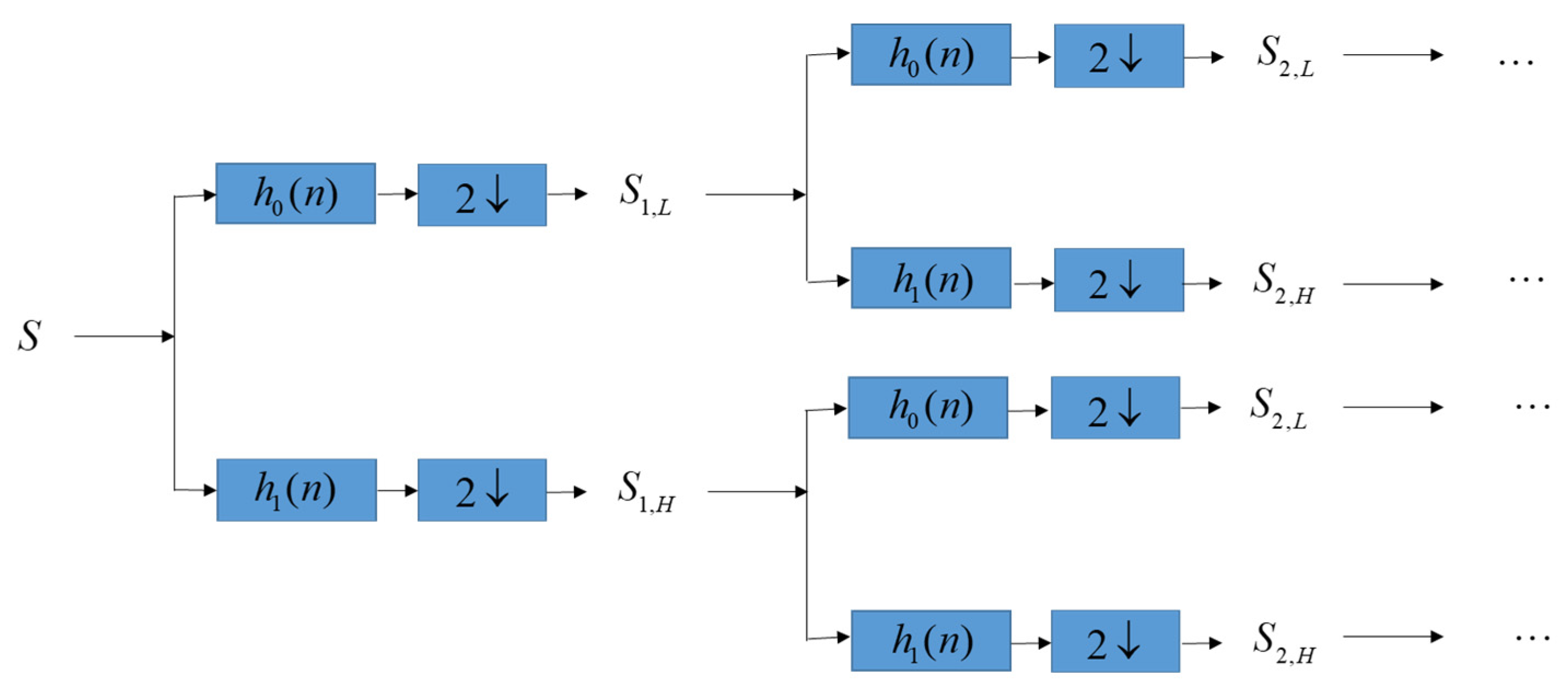
Let S denote an ECG signal, and cut S into several segments. Without generality, each segment has the same length n sample points. We then perform DWT decomposition on each segment to get high-frequency sub-band Sj,H and low-frequency sub-band Sj,L in different level j = 1,2,3,…, as shown in Figure 2. At the same time, patients’ confidential data including patient name, patient birthdate, date of medical treatment, and medical history is converted to be the binary bits since binary bits B can be easily hidden into the lowest-frequency sub-band of DWT.
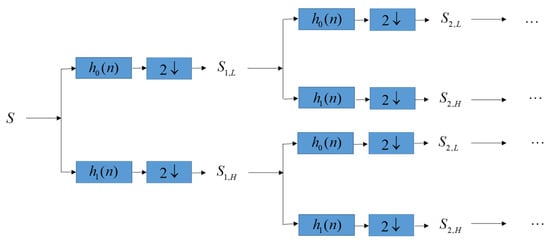
Figure 2.
Perform DWT decomposition on each segment to obtain low-frequency sub-band Sj,L and high-frequency sub-band Sj,H in different level j = 1,2,3,….
3.2. Proposed Patient Confidential Data Hiding Technique
Since the energy and quality of a signal are concentrated in the low frequency, the high frequency is susceptible to noise interference and can be easily removed or filtered without affecting the quality of the signal. Therefore, the binary bits are usually embedded in low frequencies to prevent them from being removed, filtered out, or interfered with by noise. In order to define a better threshold when embedding and extracting the binary bits in low frequencies, original audio signal of length is firstly segmented by frames, and then k-level DFT is realized on each frame. Therefore, the total number of lowest-frequency coefficients in each frame is and the mean of these coefficients is
Then, two thresholds are defined by
and
where is the embedding strength. Finally, the binary bit of value 0 or 1 is embedded into low frequencies by the following rules.
where is the embedded DWT low-frequency coefficient corresponding to original DWT coefficient .
3.3. Enhance Performance by the Proposed Optimization Model
Generally, the shape of an ECG signal is distorted when embedding patient confidential data. In order to lessen the distortion of the ECG shape, we take the maximum of the SNR which is defined by
where means the original ECG signal sample points and means the unknown embedded (or modified) ECG signal sample points. Since we realize the DWT using orthogonal wavelet bases, the SNR can be rewritten as
From the perspective of SNR maximization, we plan to evaluate the unidentified values of using the following optimization models.
- If the bit is embedded into , is modified to by
- If the bit is embedded into , is modified to by
3.4. Solving the Proposed Optimization Model by SIMULATED Annealing (SA)
Since Equations (13a)–(13d) form an optimization model, we apply the Simulated Annealing (SA) solver to approximately find the optimal solutions of . At each point in time, SA stochastically selects a solution that is in sight of the current solution, measures its quality, and then decides to move toward it or to continue with the current solution according to either one of two probabilities between which it chooses on the basis of the fact that the new solution is better or worse than the current one. During the search for the optimal solution, the temperature gradually drops from an initial positive number to zero and affects both probabilities: at each step, the probability of moving toward a better new solution is either kept to 1 or is altered towards a positive value; on the other hand, the probability of moving to a worse new solution is progressively altered towards zero. In this section, SA is applied to approximate the optimal solution of the proposed optimization model. The clear process of SA in solving our proposed optimization model will be listed in the following steps:
Step 1. Given the initial value of parameters, including initial solution C0, initial temperature T0, final temperature Tf, cooling rate r, and iteration number D for each temperature, , where .
Step 2. For each d=1…, D at a temperature T, repeat the following:
(1) Randomly generate a new solution and evaluate the difference between current solution and the new solution (neighbors) .
(2) The probability of going from the current solution to a new solution (neighbors) is given by an acceptance probability function that depends on and T.
In case , the probability function is equal to 1, indicating that the current solution S is replaced by the new solution S’. In case , the current solution S is replaced by the new solution S’ when the probability function is bigger than a threshold .
Step 3. When Step 2 is complete, the temperature T is lowered by a cooling rate r to a new temperature T = rT.
Step 4. Check if the temperature T comes to the final temperature Tf to break off simulated annealing.
After using SA to integrate the essential bodily functions of the patient into the ECG signal S, an integrated ECG signal is obtained in each case.
3.5. Perform Inverse Discrete Wavelet Transform (IDWT)
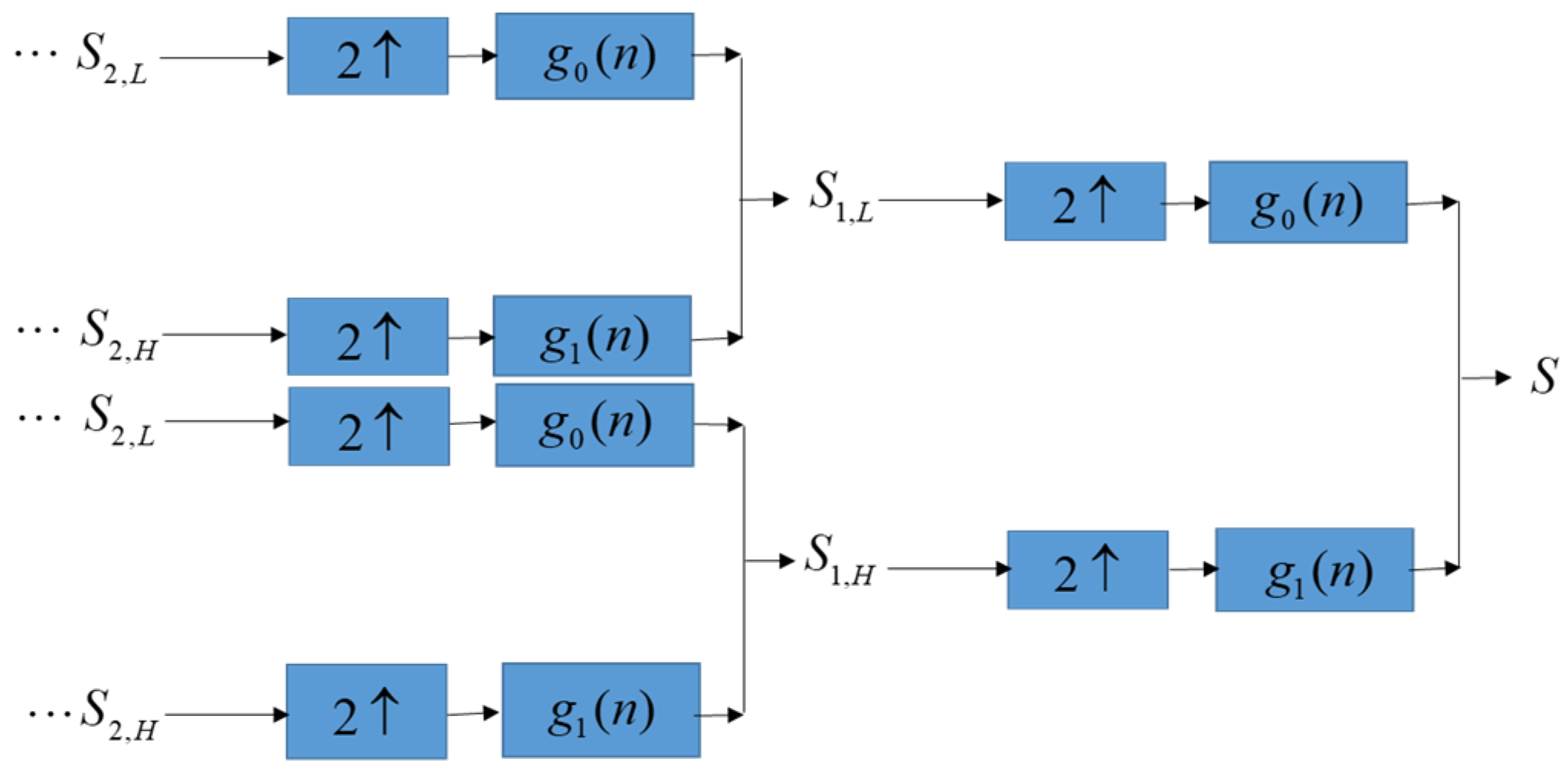
After the solution of the optimization model is obtained by SA, the patients’ confidential data is embedded into the lowest-frequency coefficients of DWT of ECGs along with the binary bits. Next, we perform inverse discrete wavelet transform (IDWT), as shown in Figure 3, to obtain the embedded ECGs and transfer the embedded ECGs to end devices over the network. The end devices that receive embedded ECGs use the extraction method in the next section to extract the binary bits to obtain patients’ confidential data.
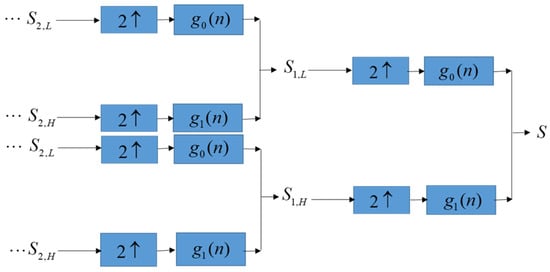
Figure 3.
Inverse discrete wavelet transform.
3.6. Extraction Method
When extracting the patients’ confidential data, we segment the test audio into several frames and then implement DWT on each frame in the same manner as in the embedding process. Suppose n consecutive absolute values are the optimal-embedded coefficients. We extract the binary bits B by using the following rules:
- If , the extracted bit is .
- If , the extracted bit is .
3.7. Architecture of the Proposed Confidential Data Communication System
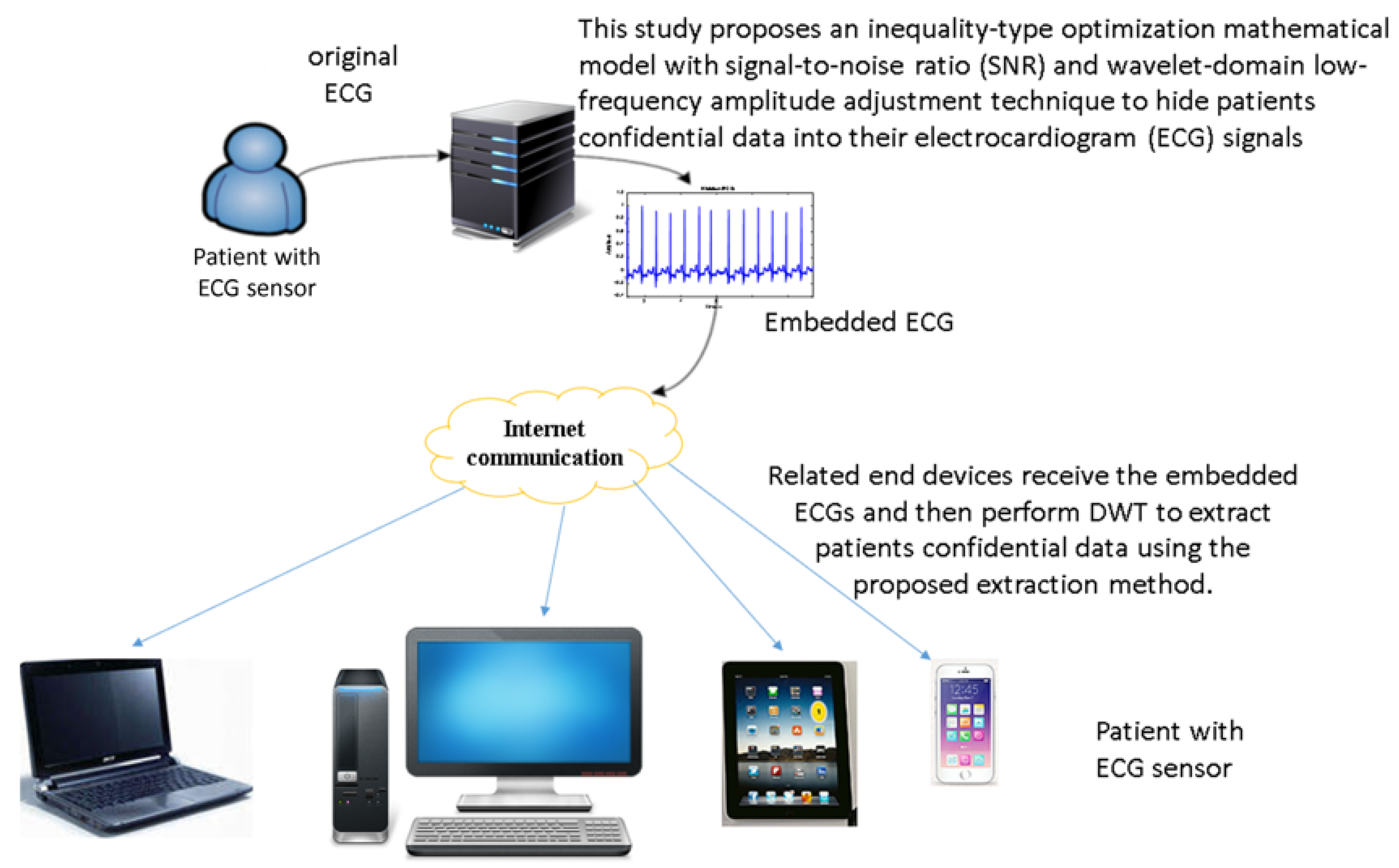
Figure 4 shows the architecture of the proposed intelligent confidential data communication system. First, we obtain patients Electrocardiogram (ECG) from the ECG sensor module or website in [33,34]. Next, by Section 3.1, Section 3.2, Section 3.3, Section 3.4 and Section 3.5, we first embed the patients’ confidential data including patient name, patient birthdate, date of medical treatment, and medical history attached with patient bed into the ECG signals in the wavelet domain by the proposed hiding method. Then, the embedded ECGs are transmitted to related end devices through internet connections. At the end devices, the optimal-embedded patients’ confidential data are extracted after receiving the embedded ECGs and performing DWT on the embedded ECGs.
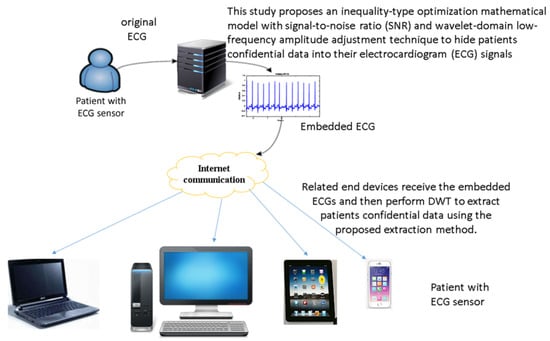
Figure 4.
Architecture of the proposed intelligent patients’ confidential data communication system.
4. Experiments and Discussion
In experiments, we use the ECG data obtained from the website in [33,34] to simulate the proposed method for each ECG signal with a length of 4096 samples represented by 16-bit. Since the 5-level Haar DWT is performed on the ECG signal, the lowest-frequency sub-band in level 5 has 128 coefficients. The embedding strength is set to 2000 and 4000 for n = 2 and n = 4, respectively. Experimental results and discussion are listed in the following.
Without generality, the superiority of the proposed method is judged by signal to noise ratio (SNR) and similarity, which are formulated as follows:
where and denote original ECG signal sample point and embedded ECG signal sample point. The higher the SNR and the similarity, the smaller the distortion of the embedded signal, that is to say, the higher the SNR and the similarity, the better the quality of the embedded signal.
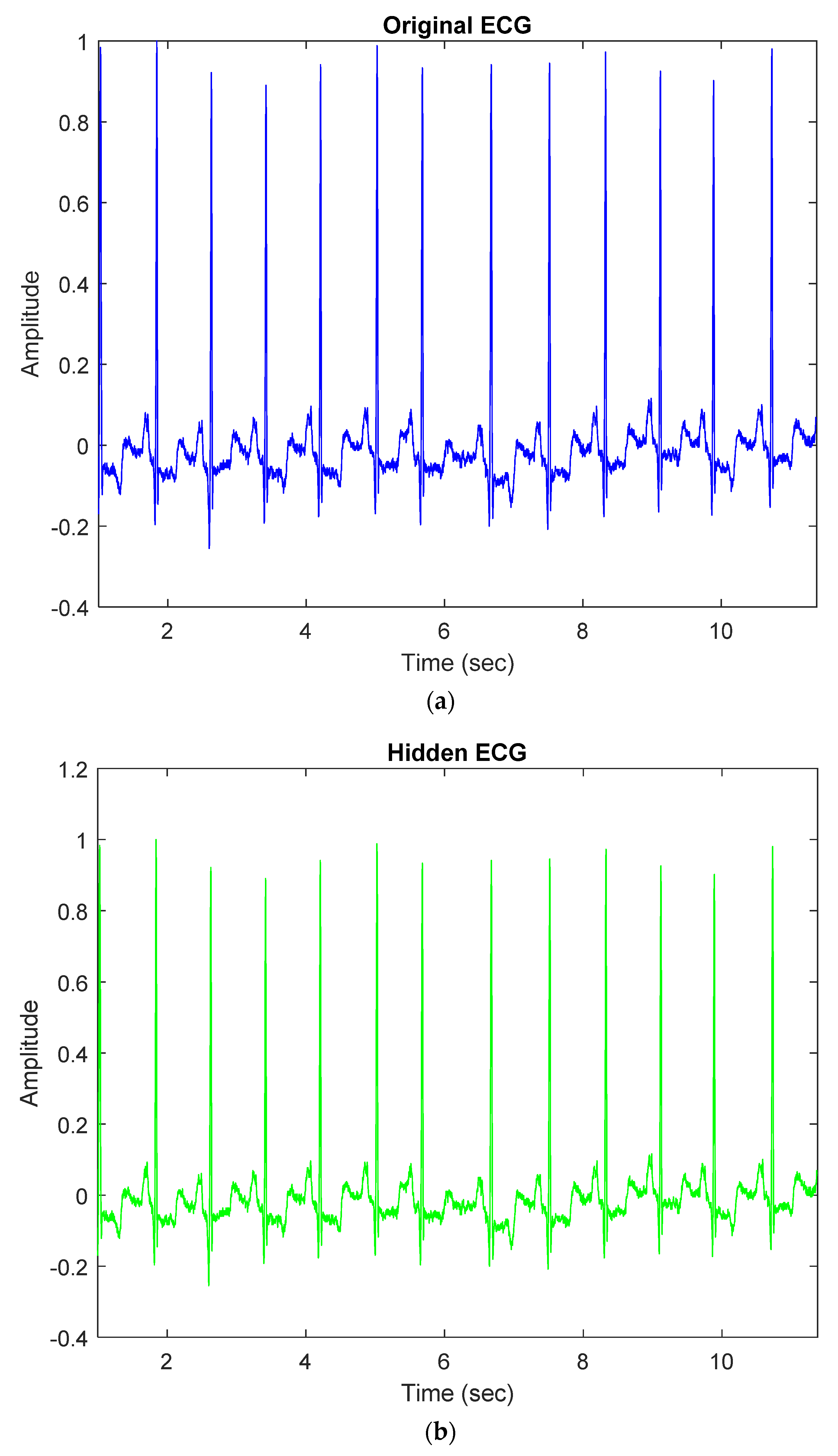
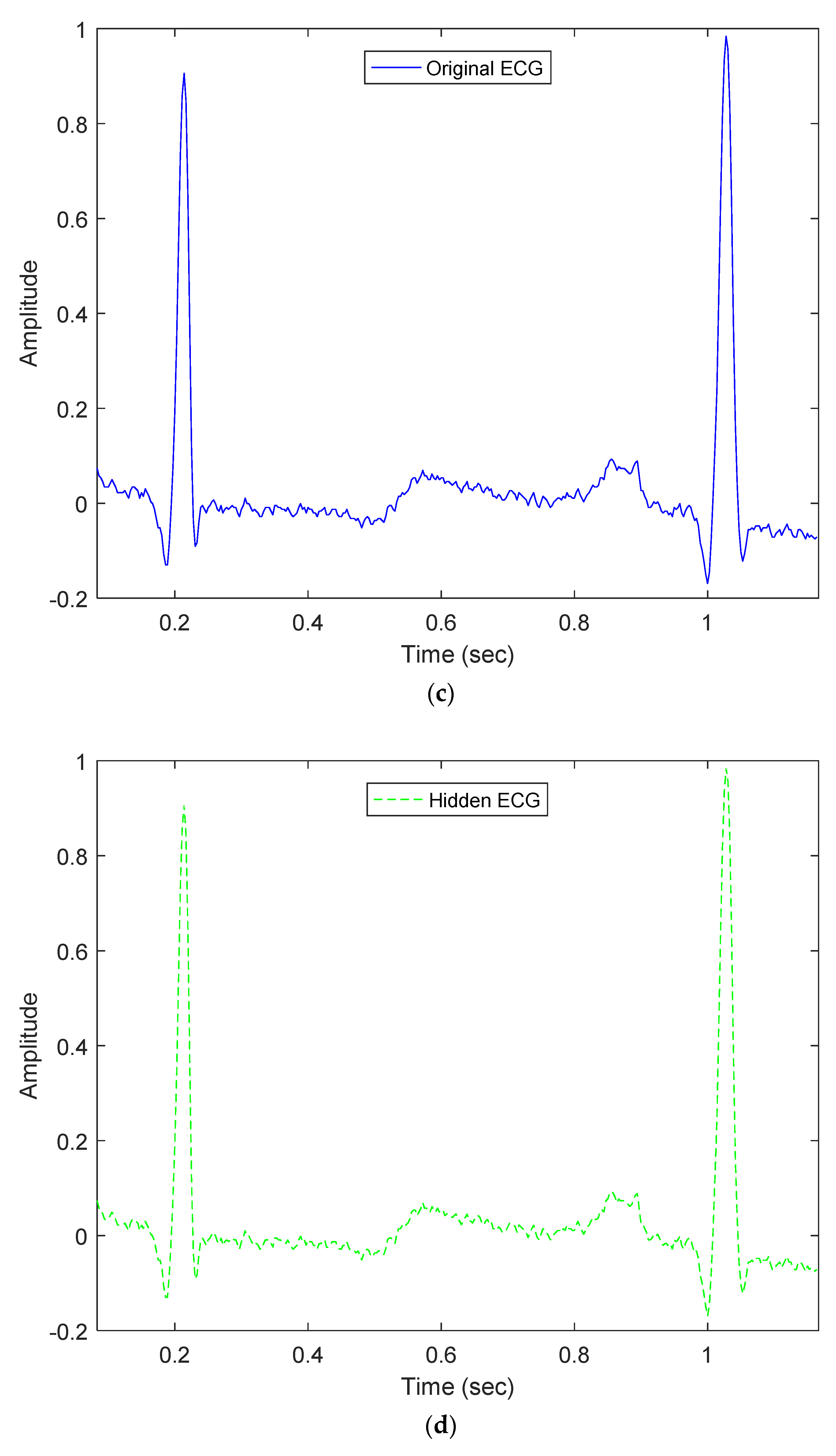
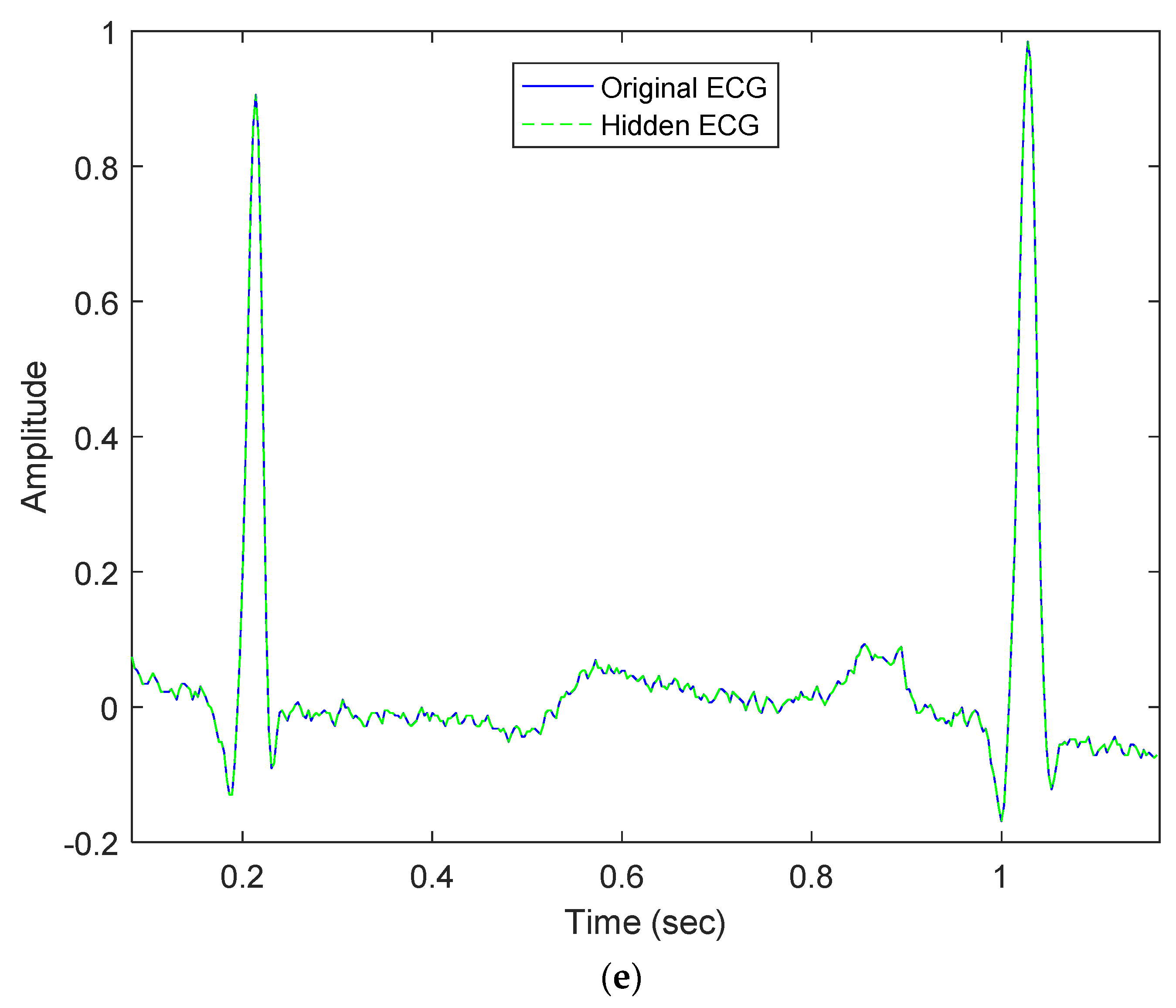
Our proposed method embeds patients’ confidential data into their ECG signals with minimal distortion and then enables each hidden ECG signal to be of good quality. For example, Figure 3a demonstrates the original ECG signal without patients’ confidential data, and Figure 3b demonstrates the hidden ECG signal with patients’ confidential data using the proposed embedding technique in DWT 5-level decomposition. In Figure 5c,d, the blue curve represents the original ECG signals and the green curve represents the optimal-embedded ECG signals in the case of embedding strength = 4000 and n = 4. Figure 5e shows that they are almost indistinguishable visually.
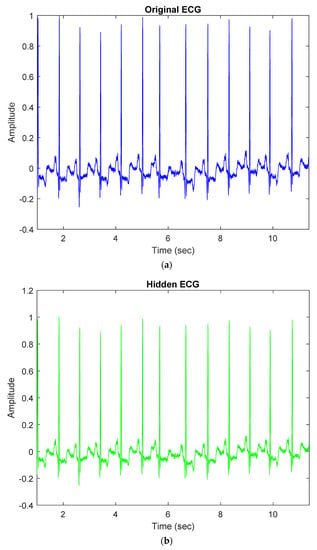
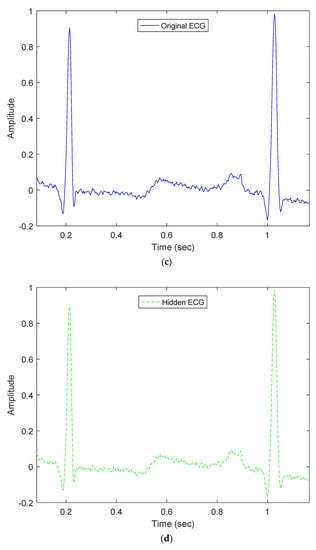
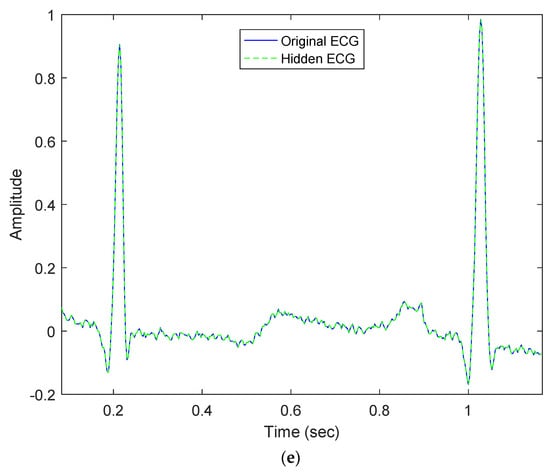
Figure 5.
Comparison between original ECG signal and embedded ECG signal for dataset ID 1; (a) Original ECG signal; (b) Hidden ECG signal; (c) Original ECG between 0.09 and 1.09 (s); (d) Hidden ECG between 0.09 and 1.09 (s); (e) Waveform comparison between 0.09 and 1.09 (s).
Moreover, as shown in Table 1, the main drawback in methods in [22,23,28] is that the SNR, which represents the quality of each embedded ECG signals, decreases significantly with the increase of the embedding strength Q. Since SA is applied to optimize the quality of each embedded ECG signal, we improve the disadvantage that the quality of each embedded ECG signal greatly decreases with increasing the embedding strength . In other words, our method maintains a good SNR (i.e., good quality) with sufficient hidden capacity for each embedded ECG signal regardless of the increase in the embedding strength .

Table 1.
Experimental results of testing amplitude similarity and SNR.
After the embedding, common attacks including re-sampling, low-pass filtering, and noise interference are utilized to test the robustness of the embedded patients’ confidential data. The test methods and average BER results are explained as follows.
(1) Low-pass filtering: Low-pass filter is a kind of signal processing so as to give easy passage to low-frequency signals and difficult passage to high-frequency signals. By the BER information in Table 2, one can find that the robustness of the proposed method against the low-pass filter attack with a cutoff frequency of 3000 Hz and 6000 Hz is significantly higher than the methods in [9,22,23,28].

Table 2.
BER (%) IN THE LOW-PASS FILTERING ATTACK.
(2) Noise interference: Gaussian noise is a common noise for audio and other signals. Table 3 lists the experimental results of adding Gaussian noise with various noise intensities to the embedded and compressed audio signal. In common noise intensities −40 dB and −30 dB, the robustness of the proposed method is significantly higher than the methods in [9,22,23,28].

Table 3.
BER (%) IN THE GAUSSIAN NOISE ATTACK.
(3) Re-sampling: Resampling converts an audio signal from a given sample rate to a different sample rate. Upsampling or interpolation increases the sampling rate, and downsampling or decimation decreases the sampling rate. Both can be accomplished using integer-valued interpolation or decimation factors. In the proposed method, the embedded-compressed audio signal is first decimated from 44,100 Hz to 22,050 Hz and then interpolated to the original 44100 Hz. This step is repeated two more times from 44,100 Hz to 11,025 Hz and 8000 Hz, then back to 44,100 Hz. The BER during the resampling attack is shown in Table 4. BER information shows that the proposed embedding method leads to lower BER and better robustness.

Table 4.
BER (%) IN THE RE-SAMPLING ATTACK.
We performed all experiments above using patients’ Electrocardiogram (ECG) data from the website in [33,34]. With the exception of a few patients with damaged ECGs, most of the ECGs were successfully tested by our proposed method.
5. Conclusions
Based on the proposed optimization model and SA algorithm, patients’ confidential data are embedded into ECG signals using DWT lowest-frequency amplitude embedding method. After testing the ECG dataset using the proposed embedding method, the difference between the embedded ECG signal and the original ECG signal is so small that it is almost negligible enough to be suitable for physiological diagnosis. Furthermore, the proposed method improves the disadvantage that the quality of each embedded ECG signal greatly decreases with the increase of the embedded strength ε. On the terminal device, the user can transmit the received embedded ECG through the Internet and then accurately extract the embedded patient’s confidential data by performing DWT on the embedded ECGs received.
Author Contributions
Conceptualization, S.-T.C.; methodology, S.-T.C.; software, S.-T.C.; validation, S.-T.C., S.-Y.T. and C.-Y.H.; writing—review and editing, S.-T.C., C.-C.C. and C.-Y.L.; All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Zuo, Z.; Liu, L.; Zhang, L.; Fang, Y. Indoor Positioning Based on Bluetooth Low-Energy Beacons Adopting Graph Optimization. Sensors 2018, 18, 3736. [Google Scholar] [CrossRef] [PubMed]
- Baldini, G.; Dimc, F.; Kamnik, R.; Steri, G.; Giuliani, R.; Gentile, C. Identification of mobile phones using the built-in magnetometers stimulated by motion patterns. Sensors 2017, 17, 783. [Google Scholar] [CrossRef]
- Zhou, C.; Yuan, J.; Liu, H.; Qiu, J. Bluetooth indoor positioning based on RSSI and Kalman filter. Wirel. Pers. Commun. 2017, 96, 4115–4130. [Google Scholar] [CrossRef]
- Zhang, X.; Zhang, S.; Huai, S. Low-Power Indoor Positioning Algorithm Based on iBeacon Network. Complexity 2021, 2021, 8475339. [Google Scholar] [CrossRef]
- Chang, C.-L.; Chang, C.-Y.; Chen, S.-T.; Tu, S.-Y.; Ho, K.-Y. Optimisation-based time slot assignment and synchronisation for TDMA MAC in industrial wireless sensor network. IET Commun. 2019, 13, 2932–2940. [Google Scholar] [CrossRef]
- Chang, C.-L.; Chen, C.-J.; Lee, H.-T.; Chang, C.-Y.; Chen, S.-T. Bounding the Sensing Data Collection Time with Ring-based Routing for Industrial Wireless Sensor Networks. J. Internet Technol. 2020, 21, 673–680. [Google Scholar]
- Chang, C.-L.; Syu, J.-M.; Chang, C.-Y.; Chen, S.-T. Optimization-based Deployment of Beacons for Indoor Positioning Using Wireless Communications and Signal Power Ranking. IET Commun. 2020, 14, 2915–2923. [Google Scholar] [CrossRef]
- Lin, S.-J.; Chen, S.-T. Enhance the perception of easy-to-fall and apply the Internet of Things to fall prediction and protection. J. Healthc. Commun. 2020, 5, 52. [Google Scholar]
- Chen, S.-Y.; Lin, S.-J.; Tsai, M.-C.; Tsai, M.-D.; Tang, Y.-J.; Chen, S.-T.; Wang, L.-H. Patient Confidential Information Transmission Using the Integration of PSO-based Biomedical Signal Steganography and Threshold-based Compression. J. Med. Biol. Eng. 2021, 41, 433–446. [Google Scholar] [CrossRef]
- Kong, X.; Feng, R. Watermarking Medical Signals for Telemedicine. IEEE Trans. Inf. Technol. Biomed. 2001, 5, 195–201. [Google Scholar] [CrossRef]
- Engin, M.; Çidam, O.; Engin, E.Z. Wavelet transformation based watermarking technique for human electrocardiogram (ECG). J. Med. Syst. 2005, 29, 589–594. [Google Scholar] [CrossRef] [PubMed]
- Zheng, K.-M.; Qian, X. Reversible data hiding for electrocardiogram signal based on wavelet transforms. In Proceedings of the International Conference on Computational Intelligence and Security, Suzhou, China, 13–17 December 2008. [Google Scholar]
- Zheng, K.-M.; Tang, L.-W.; Qian, X. Watermarking technology for electrocardiogram signal certification. Comput. Eng. Appl. 2009, 45, 231–233. [Google Scholar]
- Kaur, S.; Farooq, O.; Singhal, R.; Ahuja, B.S. Digital watermarking of ECG data for secure wireless communication. In Proceedings of the International Conference on Recent Trends in Information, Telecommunication and Computing, Kochi, India, 12–13 March 2010. [Google Scholar]
- Ibaida, A.; Khalil, I.; Al-Shammary, D. Embedding Patients Confidential Data in ECG Signal for HealthCare Information System. In Proceedings of the 32nd Annual International Conference of the IEEE EMBS, Buenos Aires, Argentina, 31 August–4 September 2010. [Google Scholar]
- Ibaida, A.; Khalil, I.; van Schyndel, R. A low complexity high capacity ECG signal watermark for wearable sensor-net health monitoring system. In Proceedings of the Computing in Cardiology, Hangzhou, China, 18–21 September 2011. [Google Scholar]
- He, X.; Tseng, K.-K.; Huang, H.-H.; Chen, S.-T.; Tu, S.-Y.; Zeng, F. Wavelet-based Quantization Watermarking for ECG Signals. In Proceedings of the International Conference on Computing, Measurement, Control and Sensor Network, Taiyuan, China, 7–9 July 2012. [Google Scholar]
- Guo, Y.; Zhou, D. Single channel surface electromyography blind recognition model based on watermarking. J. Vib. Control 2012, 18, 42–47. [Google Scholar]
- Dey, N.; Biswas, S.; Roy, A.B.; Das, A.; Chowdhuri, S.S. Analysis of Photoplethysmographic Signals Modified by Reversible Watermarking Technique using Prediction-Error in Wireless Telecardiology. In Proceedings of the First International Conference on Intelligent Infrastructure the 47 th Annual National Convention at COMPUTER SOCIETY of INDIA CSI, Kolkata, India, 1–2 December 2012. [Google Scholar]
- Dey, N.; Mukhopadhyay, S.; Das, A.; Chaudhuri, S.S. Analysis of P-QRS-T Components Modified by Blind Watermarking Technique within the Electrocardiogram Signal for Authentication in Wireless Telecardiology Using DWT. Int. J. Image Graph. Signal Process. 2012, 4, 33–46. [Google Scholar] [CrossRef]
- Ibaida, A.; Khalil, I. Wavelet-Based ECG Steganography for Protecting Patient Confidential Information in Point-of-Care Systems. IEEE Trans. Biomed. Eng. 2013, 60, 3322–3330. [Google Scholar] [CrossRef]
- Tseng, K.-K.; He, X.; Kung, W.-M.; Chen, S.-T.; Liao, M.; Huang, H.-N. Wavelet-based watermarking and compression for ECG signals with verification evaluation. Sensors 2014, 14, 3721–3736. [Google Scholar] [CrossRef]
- Chen, S.-T.; Guo, Y.-J.; Huang, H.-N.; Kung, W.-M.; Tseng, K.-K.; Tu, S.-Y. Hiding Patients Confidential Data in the ECG Signal via Transform-Domain Quantization Scheme. J. Med. Syst. 2014, 38, 54–61. [Google Scholar] [CrossRef]
- Jero, S.E.; Ramu, P.; Ramakrishnan, S. ECG steganography using curvelet transform. Biomed. Signal Process. Control 2015, 22, 161–169. [Google Scholar] [CrossRef]
- Jero, S.E.; Ramu, P. Curvelets-based ECG steganography for data security. Electron. Lett. 2016, 52, 283–285. [Google Scholar] [CrossRef]
- Swierkosz, A.; Augustyniak, P. Optimizing Wavelet ECG Watermarking to Maintain Measurement Performance According to Industrial Standard. Sensors 2018, 18, 3401. [Google Scholar] [CrossRef]
- Sanivarapu, P.V.; Rajesh, K.N.; Reddy, N.V.; Reddy, N. Patient data hiding into ECG signal using watermarking in transform domain. Phys. Eng. Sci. Med. 2020, 43, 213–226. [Google Scholar] [CrossRef]
- Hu, Y.-H.; Li, Y.-H.; Zhao, M. Integration of Information Hiding and Compression for Biomedical Signals. J. Internet Technol. 2019, 20, 975–982. [Google Scholar]
- Electrocardiography. Available online: https://en.wikipedia.org/wiki/Electrocardiography (accessed on 17 September 2022).
- Burrus, C.S.; Gopinath, R.A.; Gao, H. Introduction to Wavelet Theory and Its Application: A primer; Prentice-Hall: Hoboken, NJ, USA, 1998. [Google Scholar]
- Mallat, S. A Wavelet Tour of Signal Processing, 2nd ed.; Academic Press: Cambridge, MA, USA, 1999. [Google Scholar]
- Bouttier, C.; Gavra, I. Convergence Rate of a Simulated Annealing Algorithm with Noisy Observations. J. Mach. Learn. Res. 2019, 20, 127–171. [Google Scholar]
- MIT-BIH Arrhythmia Database Directory, Harvard University-Massachusetts Institute of Technology Division of Health Science and Technology. Available online: https://www.physionet.org/physiobank/database/html/mitdbdir/mitdbdir.htm (accessed on 17 September 2022).
- ECG Heartbeat Categorization Dataset. Available online: https://www.kaggle.com/datasets/shayanfazeli/heartbeat (accessed on 30 September 2022).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).