1. Introduction
Due to the advancement in Information and Communication Technology (ICT), Autonomous Vehicles (AVs) enter the commercial market and progress toward full autonomy. Connected and Autonomous Vehicles (CAVs) combine the features of AVs and Connected Vehicles (CVs), providing more benefits than their individual functionalities. CAVs are equipped with smart cameras, sensors, control systems, and automated applications. Some practical applications of CVs include traffic and congestion control, fleet management, and onboard device-assisted multimedia systems [
1]. In order to support the Advanced Driver Assistance Systems (ADAS), the automobile industry has focused on the research and development of CAVs, particularly Vehicle-to-Everything (V2X) communication. Therefore, most developed countries continue to improve their Intelligent Transportation Systems (ITS) in order to manage people, autonomous vehicles, and roads using cutting-edge technologies [
2]. ITS enable road monitoring, traffic control, vehicular communication, smart decisions during emergency situations, etc. With regard to the future of ITS, traffic management and road safety applications play an essential role in the control of traffic congestion and the reduction of accidents [
3].
The Vehicular Ad Hoc Network (VANET) is regarded as one of the fundamental architectures of ITS since it provides valuable services. A VANET is a collection of moving or stationary vehicles connected via a wireless network. They manage intelligent traffic and provide real-time information as well as event collections. Initially, the main objective of VANET was to speed up the development and use of self-driving cars by providing reliable communication with the help of ITS. Nevertheless, it has evolved into a special kind of networking architecture that allows CAVs to communicate with each other and the road infrastructure. In VANET, CAVs are responsible for sending, receiving, and relaying information through V2X communication channels [
4]. VANET delivers information and entertainment services known as infotainment, which requires ultra-reliable and low-latency communication models. VANET is adopted to improve road safety, control traffic congestion, regulate data flow, and facilitate emergency services through the reliable and timely dissemination of alerts and warnings. It also allows CAVs to check the weather and play music and videos on the way [
5].
VANET inherits the features of the Mobile Ad Hoc Network (MANET) and is based on Telecommunication Control Protocol/Internet Protocol TCP/IP standards [
6]. TCP/IP is a widely adopted communication standard for wired and wireless communications. For instance, the technologies used in the Internet of Things (IoT) and Internet of Vehicles (IoV) depend heavily on the underlying TCP/IP standards [
7]. Multiple radio access methods, including Wireless in Vehicular Environments (WAVE), Dedicated Short Range Communications (DSRC), Long-Term Evolution Vehicle-to-Everything (LTE-V2X), and Cellular Vehicle-to-Everything (C-V2X), all operate under the TCP/IP standards [
8]. However, the TCP/IP paradigm in VANET for the distribution of large amounts of data is challenging. In other words, TCP/IP-based communication cannot meet the requirements of a VANET due to the vehicles’ frequent mobility and the dense environments [
9].
Furthermore, security warnings and beacon messages that need timely communication necessitate a latency-free system. Moreover, quick content delivery, vehicle mobility management, a robust traffic management system, and adaptive routing render the TCP/IP infrastructure infeasible and make it complicated to meet the quality of service needs of various applications. Other obstacles include unstable communication between vehicles as a result of continuous changes in the networks as well as network instability. It is challenging to maintain dedicated pathways between source and destination vehicles in a TCP/IP-based VANET due to the mobility of vehicles [
10].
On the other hand, a Named Data Network (NDN) is designed under the umbrella of Information-Centric Networking (ICN) [
11]. NDN is a content-oriented architecture that has the potential to replace IP-based architecture in the near future. In the NDN, the data can be accessed according to their name/content/prefix rather than their IP address (host location) [
12,
13]. The content’s name is a key element in NDN-based communication in contrast to the IP address. Due to the benefits of NDN over traditional IP-based networking, new designs have been created to implement the VANET by using the NDN architecture [
14]. Named Data Network (NDN)-enabled VANET is known as Vehicular NDN (VNDN), which has emerged as a viable data distribution option for connected vehicles (cars) [
15]. Instead of safeguarding a communication connection, NDN encrypts data. However, it lacks defenses against Denial of Service (DoS) and Distributed-DoS (DDoS) attacks [
16]. The flooding effect of interest packets is one of the DDoS attacks in VNDN in which the attacker sends many bogus requests and prevents total submissions from legitimate vehicles. This study is motivated by a desire to mitigate the data packet broadcast storms of unregulated and unwanted traffic over VNDN.
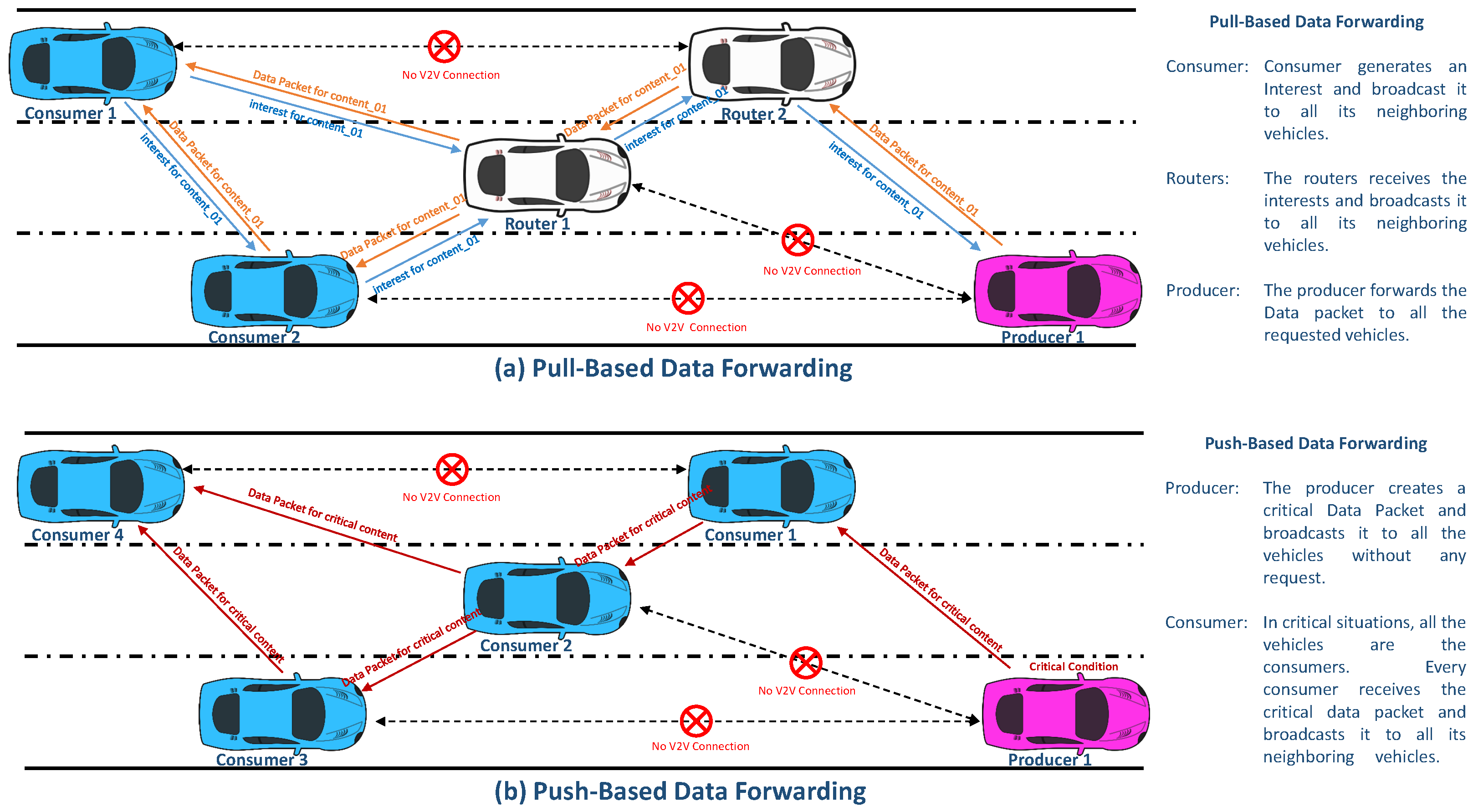
In VNDN, vehicles may be consumers, producers, or intermediate vehicles. By design, VNDN supports only a pull-based communication model in which a consumer vehicle creates an interest packet and broadcasts it on the network [
17]. The intermediate vehicles forward the interest packet to other vehicles in the network until it reaches the producer. After receiving the interest packet, the vehicle (producer) of the content or an intermediate vehicle that has stored the requested content in its cache responds with the data packet. The data packet of the requested content is sent to the consumer vehicle simply by broadcasting it to all the nearby vehicles [
18]. In order to realize critical situations such as accidents, bad weather conditions, and traffic jams, it is essential for the critical data packets to be transmitted in a push-based manner [
19,
20]. In push-based data forwarding scenarios, a vehicle (producer) generates a critical data packet and transmits it to all the vehicles (consumers) without their requests. A push-based data forwarding scheme is thus required to be designed in VNDN. To the best of our knowledge, some researchers have offered content retrieval solutions based on a push-based strategy for naive NDN, but not for VNDN [
21]. For instance, the authors of [
22] suggested a distributed push-based caching management scheme called Push-Based Traffic-Aware Distributed Cache (P-TAC) in NDN. When interest is received, a Content Store (CS) in P-TAC requests one of its neighbors to store the content on its behalf.
Similarly, the authors of [
23] provided a system to enable push-based Internet of Things (IoT) traffic based on three situations. The authors adopted three distinct scenarios in order to manage various sorts of IoT traffic, such as interest notification, unsolicited data, and virtual interest polling. In [
24], the authors created a system for secure sensing using NDN-enabled sensors. The authors regarded an environmental sensing device as a producer. When new material becomes accessible, the sensor alerts the consumer’s application for it to broadcast an interest packet and retrieve the content. All of these methods need customer interest before they can start exchanging content, which creates too much latency in NDN-based communication.
Concerning the current forwarding strategies that enable push-based critical data forwarding in the NDN environment, the critical data packets are broadcast and transferred without proper procedures. As a result, critical data dissemination creates a broadcast storm effect in push-based NDN communication. In terms of mitigating the critical data broadcast storm effect, the research is at its initial phase, and comprehensive research is required on this particular topic. The only research that exists on the mitigation of the critical data broadcast storm effect is presented in [
25], which was applied in IoT-based NDN communication. Therefore, we propose a novel scheme based on a fuzzy logic approach to mitigate the critical data broadcast storm. The proposed scheme is the first research work of its kind. We designed a fuzzy logic approach, applied it in VNDN, and reduced the broadcast storm effect resulting from the broadcasting of the critical data packets. In this regard, we assumed critical situations, and the critical data packets were transmitted through a push-based mode of communication. Our proposed model can be used as a starting point for future push-based communication in which the critical data packets are disseminated in the VNDN environment.
The rest of the paper is structured as follows.
Section 2 explains the Vehicular Named Data Networking (VNDN) architecture to understand the context. The push-based data forwarding procedure used in VNDN is illustrated in
Section 3.
Section 4 demonstrates the proposed push-based data forwarding scheme with fuzzy logic. The simulation environment and results are discussed in
Section 5. Finally,
Section 6 concludes the paper.
2. Vehicular Named Data Networking (VNDN)
The Information-Centric Network (ICN) project called Named Data Networking (NDN) is a new architecture designed to upgrade traditional TCP and IP networks to content-based networks. The primary purpose of the modification of the network is to make it easier for data packets in a communication network to refer to their content names instead of their destination IP addresses [
26]. Recently, most research has focused on integrating vehicular communication with the NDN architecture, known as Vehicular Named Data Networking (VNDN). In other words, VNDN is an application class of VANETs and NDN in which a group of vehicles is connected through the On-Board Units (OBUs) and obtains access to a centralized data network. An OBU allows vehicles to process, store, and communicate with each other. In addition, OBUs can be connected wirelessly with or without Road Side Units (RSUs), enabling them to form ad hoc, dispersed, and self-organized networks. The major objectives of VANET using the NDN architecture are the rigorous exchange of information and the effort to increase road safety while improving the driving experience. In VNDN, vehicles can communicate and exchange interest and data packets via V2V and V2RSUs [
27]. If a consumer vehicle needs any content, it generates a request (interest) with the name of the content and broadcasts it on the network. The intermediate vehicles rebroadcast the interest until it reaches the data producer. Once the interest packet reaches a node/vehicle that possesses the requested data, i.e., the name of the interest is the same as the name of the data or a prefix of the name of the data, the data are sent to the requested consumer vehicle. Since there are no source and destination addresses in a VNDN packet, the intermediate vehicles use the name and prefix in the Content Store (CS), Pending Interest Table (PIT), and Forwarding Information Base (FIB) to exchange interest and data packets [
28].
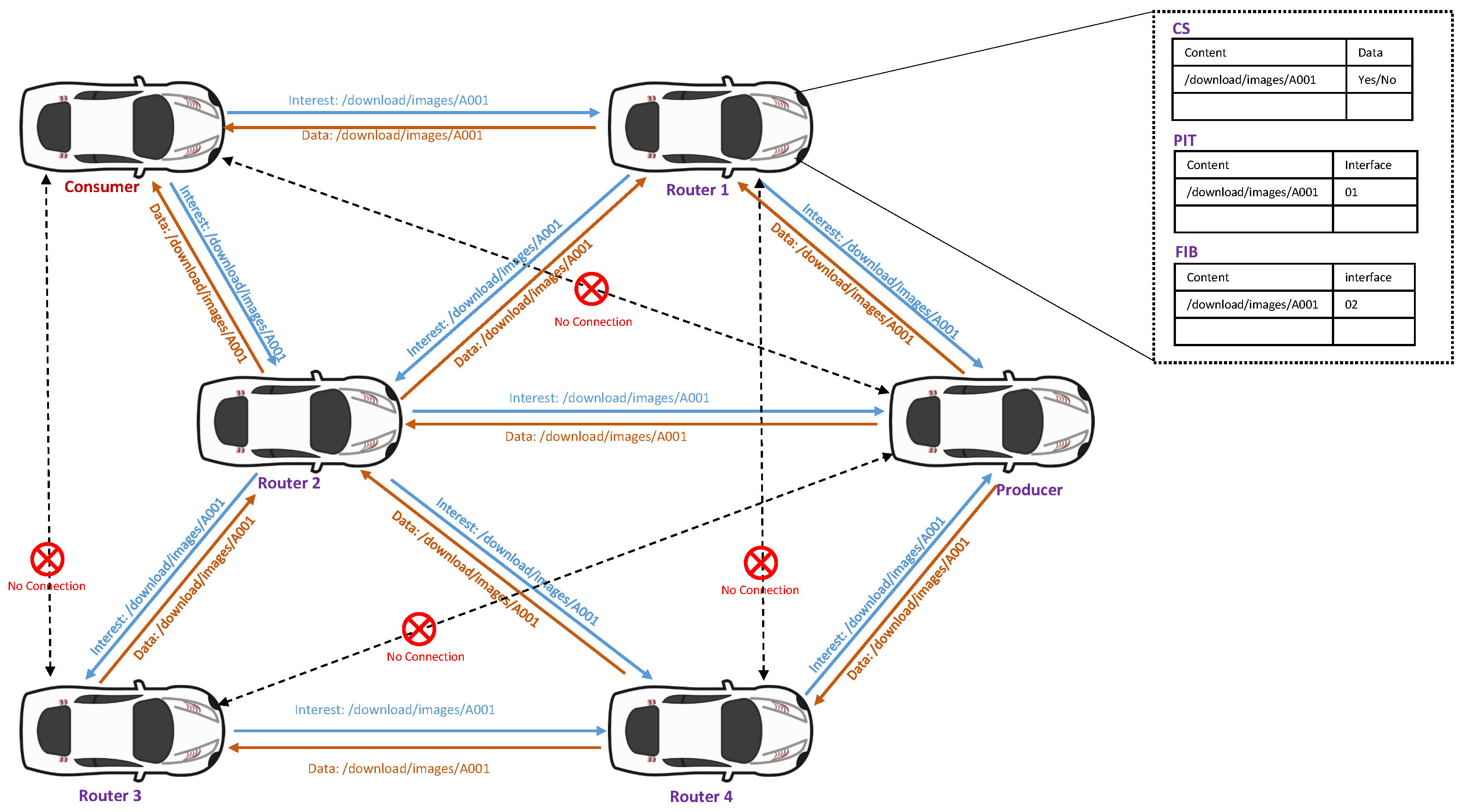
Figure 1 demonstrates the general method used in the VNDN-based architecture, where the third layer makes use of a content name instead of an IP address.
2.1. Content Store (CS)
A Content Store (CS) is one of the important data structures used in VNDN-based communication. CS temporarily stores the data packets when it receives from the producers or intermediate vehicles. In VNDN-based communication, data packets are meaningful and need to be stored in a cache, i.e., CS, which can be forwarded to the consumer upon request. In order to maintain the updated version, the most recently used data packet can replace the old one. The vehicle checks the data packet in its CS when an interest packet is received.
2.2. Pending Interest Table (PIT)
Pending Interest Table (PIT) is another data structure of the VNDN architecture. PIT contains all the requested interest packets received and forwarded in the search for a data packet. Each PIT records the name or prefix of the data carried by the interest packet of its incoming and outgoing interface(s). After successfully delivering the data packet, the entry is removed from the PIT table.
2.3. Forwarding Information Base (FIB)
Forwarding Information Base (FIB) is a data structure used in the VNDN architecture. FIB generates a routing table that links content names to interfaces. A name-prefix-based routing protocol populates the FIB, which might have many output interfaces for each prefix.
2.4. Consumer Vehicle
In VNDN, any node/vehicle that generates an interest packet (request) for any content or information is called a consumer vehicle. Based on this NDN forwarding strategy, a consumer initiates an interest packet and broadcasts it to all the neighboring vehicles. The data packet will be received if the interest is fulfilled by the intermediate vehicles or the producer. The consumer vehicle is hence the data requester in a VNDN system.
2.5. Producer Vehicle
The node or vehicle that contains the original data in its depository is the producer in the VNDN. When an interest packet (request) is received at the producer, a data packet is prepared after matching the name or prefix of the content. The data are then forwarded to the consumer through the same path that the interest packet has traversed.
3. Push-Based Data Forwarding in VNDN
The VNDN basically supports a pull-based architecture in which communication is initiated by a consumer node/vehicle. However, in vehicular communication, there might be some critical situations in which push-based communication should be applied. These critical situations may include the broadcast of traffic information, advertisements, and critical alerts, among others.
Figure 2 demonstrates a comparison of the pull-based and push-based data forwarding mechanisms in VNDN.
A VNDN is represented by the undirected graph
, where
V is the collection of vertices and
indicates the links that connect the vehicles at time
t.
V denotes the connected vehicles in the network, such as
,
,
, …,
.
p is the producer that contains the original content, and
c is the consumer that intends to obtain that content. The symbol
O refers to an object of the content that has two different kinds of chunks: the non-critical chunks consist of
,
,
, …,
, while the critical chunks include
,
,
, …,
. Using Equation (
1), we can calculate the total transfer time for the data packet in a pull-based VNDN system [
19]. We assume that the size of every chunk, regardless of the class, is the same and is denoted by
.
where
and
represent the latency and transfer rate for data chunks, whereas
and
represent the latency and transfer rate for interest packets.
is the distance between two nodes (vehicles).
represents the status of the network at the moment when a producer broadcasts the data content.
defines the condition of the network at the moment when an interest packet is broadcast.
represents the network status at the moment when a chunk of the data content is disseminated.
and
represent the length of interest and data packets, respectively.
indicates the time required for a node/vehicle to forward the data packet to its nearby nodes/vehicles.
On the other hand, Equation (
2) can be used in the push-based communication model to calculate the total transfer time for critical data packets [
19].
where,
and
represent the latency and transfer rate for the chunks of the critical data content.
indicates the distance between two nodes (vehicles).
denotes the status of the network at the moment when a producer broadcasts the critical data content.
is the network status at the time when a producer transmits a chunk of critical data content.
indicates the size of the critical data content.
is the time required for a node/vehicle to forward the critical data packet to its nearby nodes/vehicles.
5. Simulation Environment and Results
The NS-3 and ndnSIM tools were used to implement the proposed scheme and analyze the performance. In addition to the traditional NDN structures, Simulation for Urban Mobility (SUMO) was employed to obtain the vehicle movements [
31]. For a fair comparison, the simulations employed the same configuration, network configuration, Physical and MAC layer parameters, and mobility model. A total of 600 vehicles were considered moving at different speed rates. The length of the observed area was 300 m, and a three-lane road was considered. The remaining simulation settings are listed in
Table 2.
In addition, a random number of vehicles (producers) were dispersed evenly over the network, and each vehicle randomly generated a critical data packet during the experiment. Every vehicle exchanged its location with all its neighbors through a pilot message.
Figure 6 shows the total number of critical data packets transmitted over each iteration with respect to the number of vehicles. We can observe that the naive scheme transmitted a massive number of critical data packets, while the proposed scheme transmitted a lower number of critical data packets. In the naive scheme, all the vehicles participate in broadcasting the critical data packets once it receives the data packets. As a result, every vehicle receives multiple copies of the same critical data packet. On the other hand, the proposed scheme allows only the CH to broadcast the critical data packet to all the vehicles in the cluster. Therefore, the proposed scheme transmits fewer data packets than the naive method.
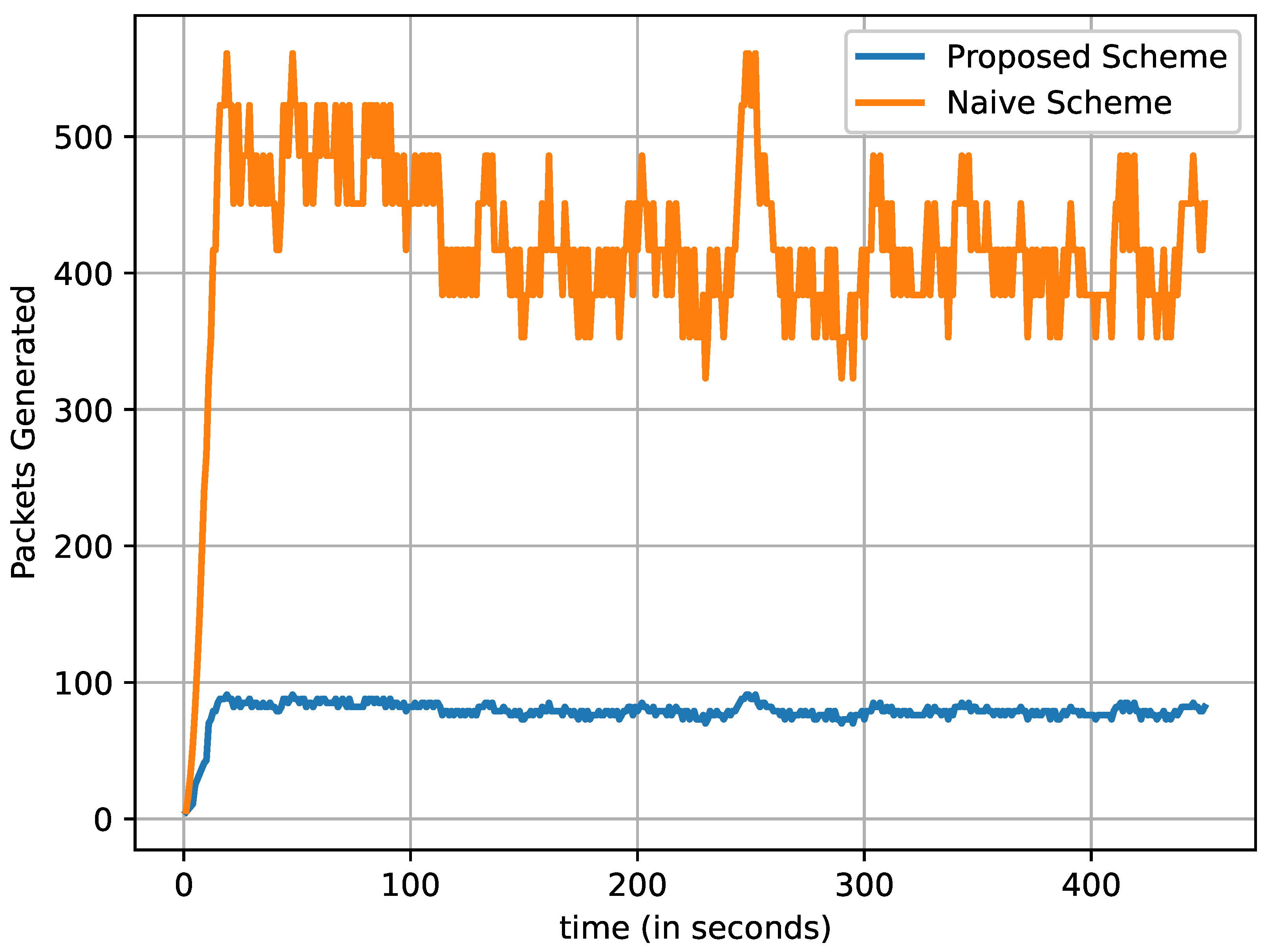
In
Figure 7, we can observe that the total number of critical data packets are generated and transmitted over time. It is noteworthy that the number of data packets by vehicles (producers) increases with respect to time. After starting the simulation, only one vehicle generates a critical data packet and transmits it. When the time reaches the 10th second, two vehicles generate critical data packets and transmit them, and the process continues. On the 100th second, about 98,000 and 18,000 critical data packets are observed to have been generated and transmitted by the naive and proposed schemes, respectively. The difference gets larger as the vehicles producing critical data packets increase. After 200 s, the total generated and transmitted data packets by the naive and proposed schemes rise to almost 350,000 and 6500, respectively. Therefore, the total number of transmitted critical data packets is multiplied by the number of vehicles that produce the critical data packets. The results show that the proposed scheme clearly transmitted fewer critical data packets than the naive method.
Figure 8 indicates the efficiency of the proposed and naive schemes. Efficiency is calculated by using Equation (
10). We can observe that the efficiency of the proposed scheme is higher than the efficiency of the naive method. As the number of vehicles increases, the efficiency decreases. The straight line indicates that the number of vehicles remained almost the same due to the SUMO tool.
In
Figure 9, we observe that the number of critical data packets increases linearly with time. However, the number of vehicles is distributed randomly by applying the Poisson point distribution with a mean value of twenty (
). The proposed scheme broadcasts a much lower number of critical data packets. On the other hand, the naive scheme broadcasts a massive number of critical data packets. The main reason is that only the CHs in the proposed scheme are responsible for broadcasting the critical data packets to every member vehicle within a cluster. However, in a naive method, every vehicle broadcasts the critical data packets and causes the broadcast storm during push-based data dissemination. Therefore, the proposed scheme mitigates the broadcast storm effect during push-based data forwarding within a VNDN environment.
Figure 10 demonstrates the total number of data packets broadcast with respect to the vehicles’ density. As the number of vehicles increases, the number of total data packets broadcast increases as well. The ratio between the proposed and naive schemes rises as the number of vehicles increases. In the naive method, the broadcast of critical data packets is directly proportional to the number of vehicles. In contrast, in the proposed scheme, the number of critical data packets is proportional to the number of clusters and CHs. As vehicles’ density increases, the number of clusters and CHs increases. As a result, the effect of the broadcast storm is mitigated because the CHs are responsible for broadcasting the critical data packets.
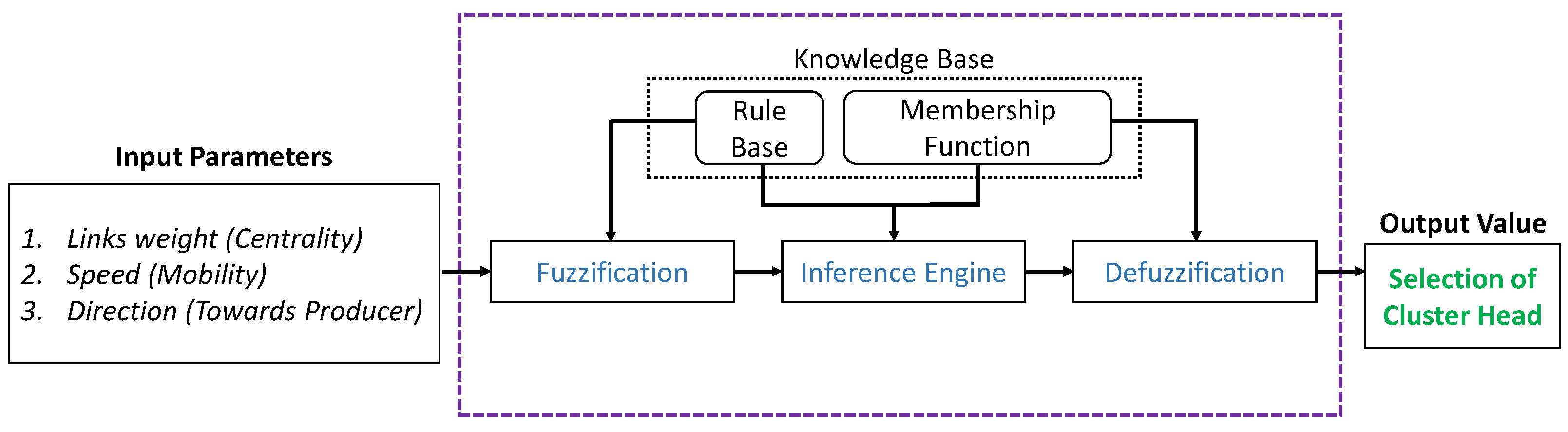
6. Conclusions
In VNDN, pull-based communication is basically supported. When a consumer requires content, it generates an interest packet (request) and broadcasts it to neighboring vehicles. The intermediate vehicles (routers) receive the interest, check the content in their CS, add the content to PIT along with its interface number, and broadcast it to their neighboring vehicles until it reaches the producer. The producer provides the content to the requested consumers using the same route. On the other hand, in push-based forwarding in VNDN, the producer generates critical content and broadcasts it to all the neighboring vehicles without any request; however, this creates a broadcast storm effect in the network. Therefore, we proposed the use of a fuzzy logic scheme to mitigate the broadcast storm effect in push-based data forwarding in VNDN. In our proposed scheme, fuzzy logic was designed to reduce the broadcast storm effect that could occur during the critical data packet broadcast in push-based data forwarding in VNDN. Critical circumstances were considered when a producer broadcast useful information to the rest of the vehicles. We employed the K-means clustering algorithm to divide the vehicles into groups. An Elbow algorithm was used to determine the optimum number of clusters. Then, the CH was selected using fuzzy logic. After the CH selection process, the producer would only forward the critical data packet to the CH. The CH would then exclusively broadcast it to all the member vehicles inside the cluster. In addition, the GW vehicles were responsible for the forwarding of the data packet to the GW vehicles of the neighboring clusters. As a result, the transmitted critical data packets were mitigated efficiently. The results show that the proposed scheme transmitted fewer data packets and reduced the chances of broadcast storms in the VNDN environment. It was also observed that as the number of vehicles increased, the total number of transmitted critical data packets also increased. For instance, if there are 50 vehicles, the total number of transmitted data packets is 1700 and 250 for the naive scheme and the proposed scheme, respectively. In terms of efficiency, the proposed scheme achieved more than efficiency, while the naive method achieved less than efficiency. In future work, we will consider both pull-based and push-based VNDN environments to obtain better results. In addition, efficient Radio Resource Management (RRM) in the VNDN environment is a hot topic to consider for future research.