In this section, we first evaluate compression savings and encryption efficiency of the IIB–CPE. For the evaluation, we conducted our experiments on two datasets. The Tecnick sampling dataset [
29] comprising 120 true color images with dimensions of 1200 × 1200 and Shenzhen dataset [
30] consisting 400 grayscale images with dimensions of 2048 × 2048. To demonstrate the application of the proposed method, we designed an end-to-end image communication system for PPDL-based image classification. For the classification accuracy, we used the CIFAR datasets [
31]. Both CIFAR–10 and CIFAR–100 consist of 50K training and 10K testing images. For the baseline methods, we implemented compressible PE algorithms proposed in [
10,
11] (Color–EtC), [
13,
14] (GS–EtC), and learnable PE methods, such as learnable encryption (LE) [
5], pixel-based PE (PBE) [
6], chaos-based secure PE (SPBE) [
8], and extended learnable encryption (ELE) [
7]. For the JPEG software, we used the implementation provided in [
32].
4.1. Energy Compaction Analysis
At the core of JPEG is the discrete cosine transform (DCT) [
33], which reduces the data correlation and provides a compact representation of a large amount of information as few data samples. The JPEG standard divides an image into
blocks of pixels, with each block producing 64 coefficients. The DCT–II for a block, where
is the pixel value at position
, is defined as:
where
and
is the corresponding computed DCT value. For the DC coefficient,
and
which gives the average value of pixels in the image block. Therefore, the DC coefficient is independent of the pixel position. The remaining 63 values are AC coefficients that correspond to a progressive increase in frequency in both the horizontal and vertical directions. When the input image is divided into multiple blocks, the DCT can be independently computed for each block. In each calculation, the basis function points remain the same, whereas the pixel values are changed. Therefore, an efficient method is to pre-compute the function points and multiply them by each block to obtain DCT (
D) as
where
is the image data and
is the DCT matrix obtained as
The multiplication of
on the left transforms the rows, and
on the right transforms the columns of
. The product
represented by
is a linear combination of matrix
columns with weights given by matrix
columns. The matrix
with
columns, each with
elements, can be represented in a column–vector form as
, where for
denotes the
th column of
and for
,
denotes
th element of the
th column. The product
is obtained as
, where the
th column of
is
and is defined as a product of matrix
with the
th column of
. It is calculated by
This representation simplifies the change in the product matrix elements with respect to weight. For example, in Equation (4), the weights belong to an image distribution, which has the intrinsic property of being highly correlated; thus, the adjacent pixels have smaller differences. Therefore, swapping the pixel positions in a block by intra block processing has a smaller effect on the product of the two matrices. As an example, we extracted an 8 × 8 block from the Lena image, where the vertical and horizontal correlation factors are
and
, respectively. The DCT transformations of the original, conventional PE, and IIB–CPE images are shown in
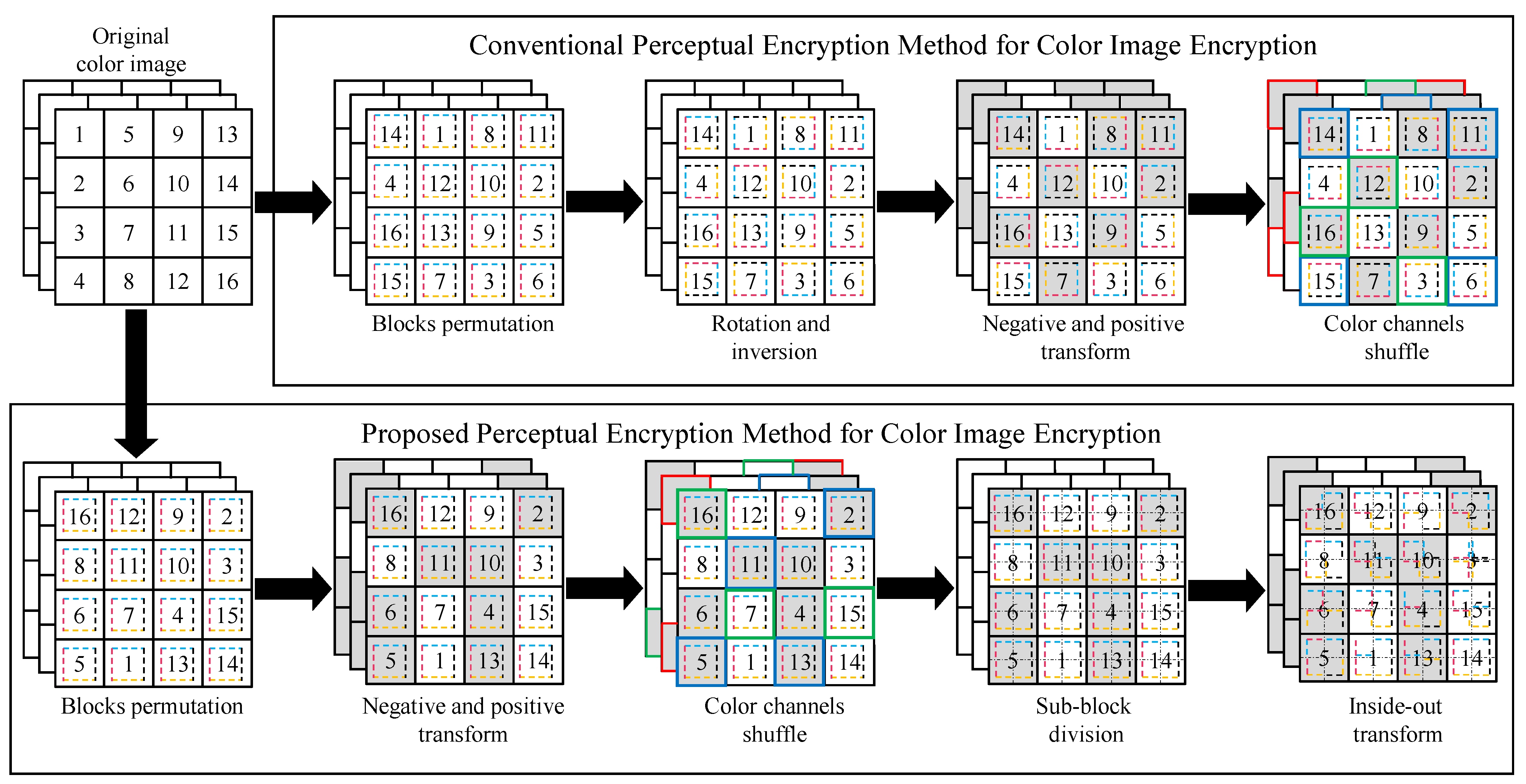
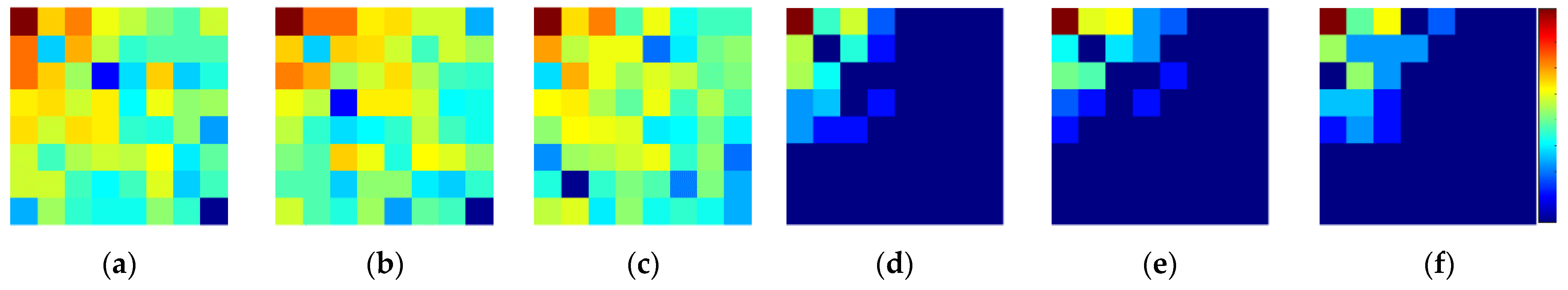
Figure 5a,c. The PE image is obtained by 90° rotation of the whole block, whereas the IIB–CPE is obtained by first dividing the block into 4 × 4 sub-blocks and then randomly and independently rotating and inverting each sub-block.
Figure 5b illustrates that the transformation of the entire block only changes the DCT coefficient positions, while their values remain the same as those of the original image. On the other hand, the sub-block processing results in DCT coefficients with values slightly different from the plain image, as shown in
Figure 5c. However, the transformation in the JPEG algorithm is followed by a quantization step, to reduce each coefficient value obtained in Equation (2) [
34]. The reduction amount is controlled by a quantization table
, which is defined by a quality factor
. The JPEG standard provides two quantization tables
for
, one for each image component. The standard tables can be used to construct different quantization tables corresponding to different quality factors. The element
of a quantization table
for a quality factor
is defined as
where the function
ensures that the elements in Equation (5) remain integers and are between 1 to 255 as required by the standard recommendation. The function is defined as
The DCT coefficients computed in Equation (2) can be quantized by dividing each value
by the corresponding quantization element
as
where function
rounds a value to the closest smallest integer and
is the quantized value. Since the quantization reduces the values to small integers, the difference in the DCT coefficients resulting from the sub–block processing was significantly reduced in the JPEG quantization step, as shown in
Figure 5d–f. In fact, the number of zeros at the end of the zigzag scan remains the same and can be encoded as the JPEG end-of-block (EOB) identifier in a manner similar to the plain image. Therefore, the IIB–CPE has little impact on the energy compaction of the DCT and it allows the quantizer to discard high-frequency coefficients without introducing any visual distortion in the recovered image.
4.2. Compression Analysis
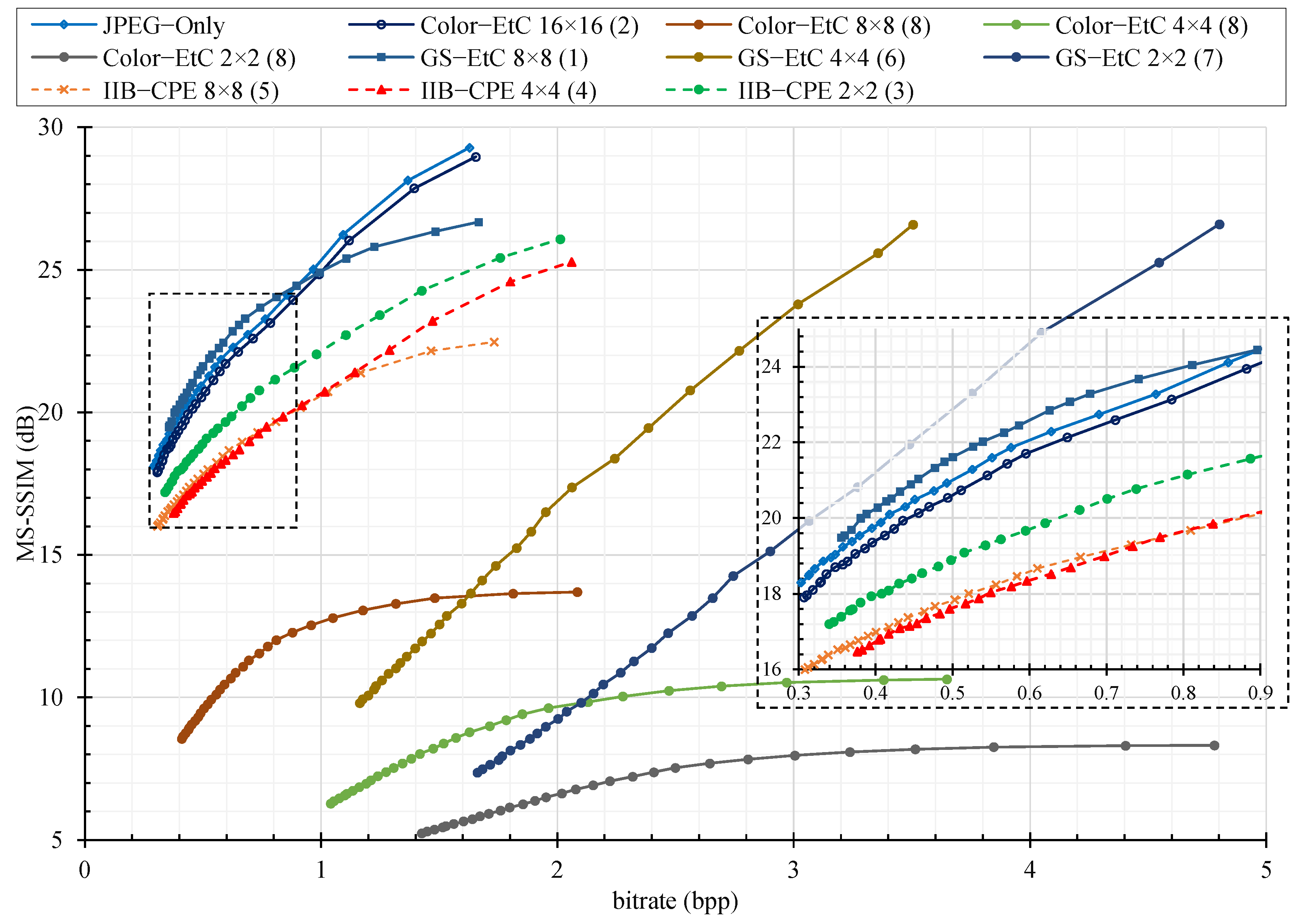
For compression analysis, we plotted the rate distortion (RD) curve as shown in
Figure 6,
Figure 7 and
Figure 8 for color image compression without chroma subsampling, color image compression with 4:2:0 subsampling ratio, and grayscale images, respectively. The y-axis is the recovered image quality represented as a multiscale structural similarity index measure (MS–SSIM) in dB against the compression savings given as the bitrate on the x–axis. The RD curves are for the JPEG quality factors of 70–100. To compare the RD curves, we used Bjøntegaard delta (BD) measures [
35], where the BD rate difference is the percent difference between two bitrates of the equivalent quality, and the BD quality difference is the average dB difference for the equivalent bandwidth. Instead of peak signal-to-noise ratio (PSNR), as used in the conventional literature, the BD rate difference is computed for a better image quality measure such as MS–SSIM [
36]. Note that the value of MS–SSIM (M) is
Table 1 summarizes the rate savings and image quality differences of PE methods and JPEG-compressed images using BD measures for the RD curves presented in
Figure 6,
Figure 7 and
Figure 8. First, we considered the JPEG algorithm for color images compression without chroma subsampling. The results show that the proposed IIB–CPE (8 × 8) preserves the compression savings of color–EtC (16 × 16), while outperforming GS–EtC by almost 15%. However, there is a 3% datarate difference as compared to compression of the original images. The main reason is that the DC coefficients in adjacent blocks have higher correlation and the JPEG algorithm treats them differently to the AC coefficients. The DC coefficients in adjacent blocks are differentially pulse code modulated (DPCM) with each other and their prediction errors are entropy-encoded. In the proposed scheme, the permutation step disrupts this correlation, and compression savings that could have been achieved by the DPCM are lost. On the other hand, for smaller sub-block sizes such as (4 × 4) and (2 × 2), there is an increment in the image size across all methods. However, compared to conventional PE methods, where the file size drastically increases, the proposed method is still able to deliver compression savings. For example, to achieve the highest-quality image (that is,
) when using the smallest block size of (2 × 2), the bitrate of IIB–CPE is 4.6 bpp, whereas for conventional Color–EtC and GS–EtC methods, the bitrate is 10.4 and 8.9 bpp, respectively. The bitrate of conventional PE methods is in fact an increment from the original image size.
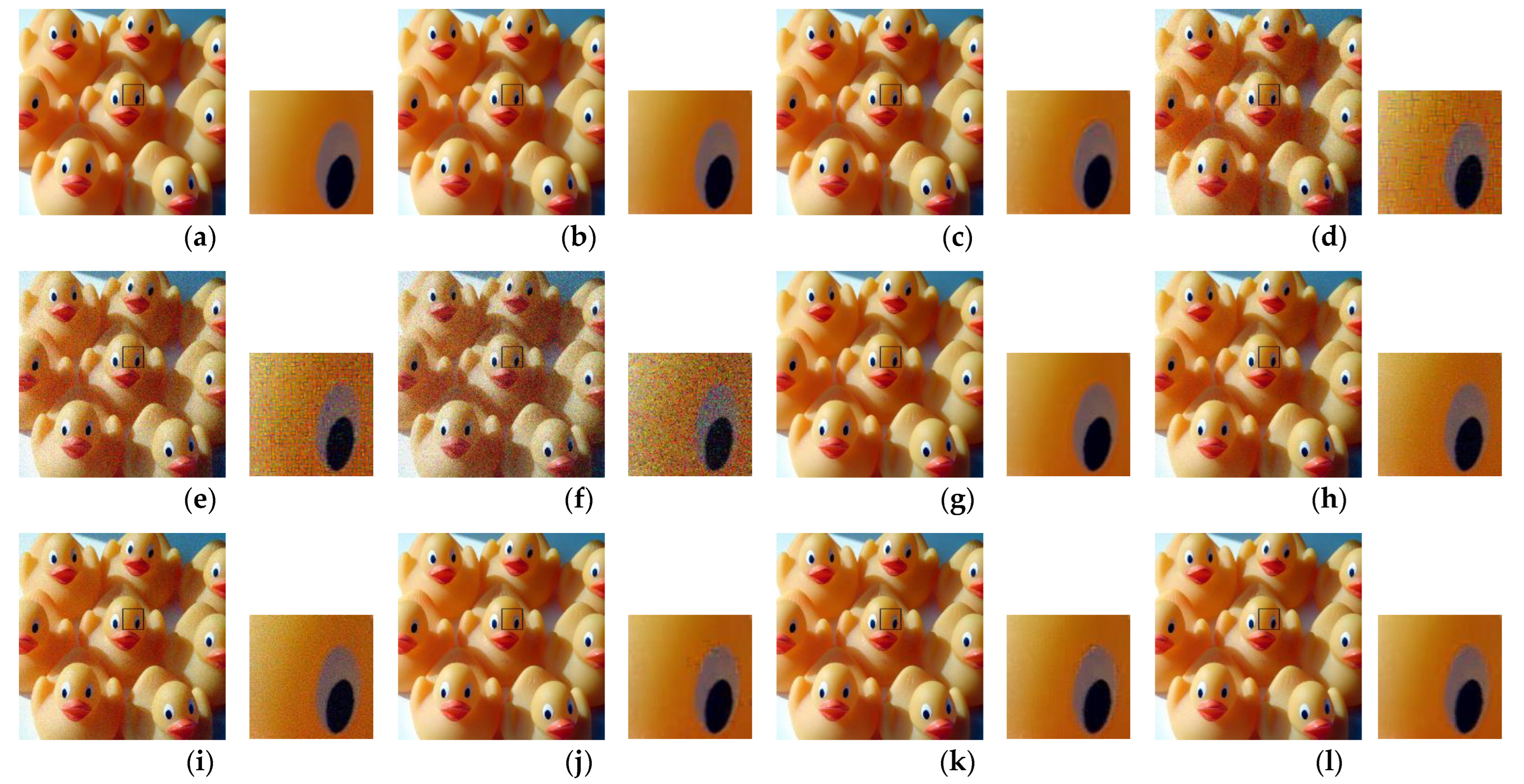
Second, we considered the JPEG algorithm for color image compression with a subsampling ratio of 4:2:0. The JPEG encoder performs chroma sub-sampling (such as 4:2:0) on a block size of 16 × 16. Therefore, when the images are encrypted with a block size smaller than the standard specified size, then the resulting (8 × 8) blocks in color components will consist of pixels from different blocks. Such pixels have low correlation and performing interpolation on them to recover the original image resolution results in block artifacts (Type I). In addition, when the luminance component (Y) is shuffled with either of the chrominance components (Cb or Cr) as a result of the channel shuffling step, then during encoding, this block is treated as a chrominance component. Based on human color perception capabilities, the JPEG algorithm processes the chrominance components differently to the luminance. For example, the chrominance component resolution is reduced during the subsampling step and the values are represented with fewer bits during the quantization step. Therefore, when a block that belongs to the luminance component undergoes this processing, then, regardless of its size, the block is recovered with blur distortion (Type II). For visual inspection,
Figure 9 shows images recovered from PE encryption methods with different block sizes. For the conventional Color–EtC method, when 16 × 16 block size is used, then the Type II distortion appears in the regions where there is an abrupt change in the pixels values. Images encrypted with block sizes smaller than 16 × 16 have both Type I and Type II distortions. Since, in the GS–EtC method, the chroma subsampling is performed before encryption, no block artifacts are visible. However, for smaller block sizes, there is visible distortion as a result of the quantization step. On the other hand, for the proposed IIB–CPE method, only Type II distortion appears in the similar regions to that of the Color–EtC (16 × 16) method. The proposed method preserved the correlation among the adjacent pixels within a block, as discussed in
Section 3.2.1; therefore, it avoids the Type I distortion. The Type II distortion is reduced when using a larger value for the JPEG quality factor, as shown in
Figure 10.
For the compression savings when using chroma subsampling, it can be seen in
Table 1 that GS–EtC with block size 8 × 8 has achieved better performance than the compared methods. For block size 8 × 8, the method has an improved bitrate compared with that of the plain images. The reason for this is that GS–EtC uses a single quantization table (for example, the standard luminance table in our simulations); therefore, in the low-bitrate region, it has achieved better image quality, as shown in
Figure 7. The Color–EtC with block size 16 × 16 has a 6% difference in the bitrate with negligible difference in the image quality. However, for both Color–EtC and GS–EtC, the performance gain is reduced significantly with the smaller block size. On the other hand, the proposed method has a higher bitrate requirement than the conventional methods. However, it is still able to deliver compression savings across different blocks sizes with a negligible difference in image quality. For the proposed method, there is an opposite trend between the measures and the block sizes. This occurs because when using sub-blocks of smaller sizes for intra block processing, then the correlation is better preserved within the block.
As discussed in
Section 2, existing PE methods have a prerequisite of color image as an input for better security. As opposed to conventional methods, the encryption efficiency of proposed method is independent of input image representation because of the intra block processing. Therefore, we have also evaluated compression efficiency of existing EtC and IIB–CPE methods on grayscale images.
Table 1 summarizes the rate savings and image quality differences of PE methods and JPEG-compressed images using BD measures on grayscale images. Note that since the input are grayscale images with only one channel, Color–EtC and GS–EtC can be implemented with the same algorithm and are together referred to as ‘EtC’ method in
Figure 8 and
Table 1. The results show that for IIB–CPE with sub-block sizes of 4 × 4 and 2 × 2 has acceptable degradation in compression savings, whereas conventional EtC methods were unable to preserve compression savings for smaller blocks sizes.
4.3. Encryption Analysis
Several statistical tests, for example, histogram analysis, correlation analysis, and entropy analysis, usually assess the security of encryption algorithms. These tests are commonly used for analysis of full encryption techniques, where an attacker tries to discover details of the algorithm. However, different from full encryption algorithms, the goal of perceptual encryption cryptanalysis is to recover a better-quality image out of the unencrypted data and their semantics [
37]. The compressible PE preserves correlation of the original images on a bock level, which may be vulnerable to the jigsaw puzzle solver attack proposed in [
20]. It is a ciphertext-only attack (COA) where the main goal is to reconstruct the original image fully or partially from the cipher image by exploiting the correlation that exist in each block. To demonstrate robustness against the attack, we extended the jigsaw puzzle attack to accommodate sub-block processing. The proposed jigsaw puzzle solver reconstructs the original image in two steps. First, correct orientations of sub-blocks in an entire block are recovered. For this purpose, the cipher image can be treated as a type of jigsaw puzzle where only orientation of the pieces are unknown. Here, the change in orientation is a result of the combination of rotation and inversion transformations, which is given by a composite function as
The function
rotates a piece where
and the function
flips a piece, where
and H: horizontal flip, V: vertical flip, and HV: horizontal flip followed by vertical flip. For the composite function, the rotation function
or
in order to avoid collision. The orientation can be recovered by minimizing the total sum of the cost across the boundaries of any two given pieces. The cost is a pairwise compatibility between two pieces calculated as the Mahalanobis Gradient Compatibility (MGC) measure proposed in [
23]. For example, for two pieces
and
, the compatibility between top of
and bottom of
is represented as
. The minimum compatibility of the two pieces for the proposed solver is given as
Since the positions of the sub-blocks are not changed, each sub-block is compared only with its neighbor in the block. Once the sub-blocks’ orientation is recovered, the next step is to solve the puzzle for the transformation performed on the entire blocks. Note that the recovery of the sub-blocks’ orientation with respect to their neighbors in a block does not necessarily guarantee the correct orientation of the entire block. Therefore, the entire block has the transformation of
and has an additional function
that applies negative–positive transformation on a block, where
and
being transformation is applied. The overall transformations on a block
can be defined by a composite function as
and the minimum compatibility in Equation (8) for two blocks
and
becomes:
The position of each block is changed because of the permutation step in the encryption; therefore, the compatibility of each block should be computed with every other block in the puzzle. Finally, the calculated compatibility scores are then used to solve the puzzle by using a constrained minimal spanning tree algorithm proposed in [
23]. The following measures proposed in [
23,
38] were investigated in this study to show the robustness against the jigsaw puzzle solver attacks:
Direct comparison (
Dc): measures the ratio of blocks in the correct position in the recovered image. Let
be the original image,
the recovered image,
the
th piece, and
the total number of pieces, then
is given by
Neighbor comparison (
Nc)
: measures the ratio of correctly joined pairwise blocks. For the recovered image
with
boundaries among the pieces and
being the
th boundary,
is given by
Largest component comparison (
Lc): measures the ratio of the largest joined blocks that have correct pairwise adjacencies with other blocks in the component. For a recovered image
the
is given by
where
is the number of partially correct assembled regions,
and
is number of blocks in the
th assembled area. The scores,
where a larger value indicates a better reconstruction of the cipher image. For the robustness analysis, 20 images were randomly chosen from the Tecnick dataset. First, we encrypted the images and then assembled them using the jigsaw puzzle solver.
Table 2 summarizes the average
and
scores of those 20 images. The smaller score value of the proposed method is attributed to intra block processing, which reduces the efficiency of the compatibility measure used by the jigsaw puzzle solver.
In addition, to demonstrate the robustness against brute-force attacks, we analyzed the keyspace of the encryption algorithms. The algorithms consisted of four keys: permutation key
, rotation and inversion key
, negative–positive transformation key
, and color-channel shuffling key
. The
represented as
and
, shows transformation on a block and sub-block level, respectively. For an image
with
pixels divided into non-overlapping blocks of the same size
pixels, the number of blocks
in each color channel is given by
For intra block processing, when each block of dimension
pixels is divided into smaller blocks of size
, the number of sub blocks
is given by
The keyspace
for the conventional Color–EtC scheme based on Equation (14) can be derived as:
The keyspace
for the conventional GS–EtC scheme can be derived similarly to Equation (16) without the last term
as the methods lack color-channel shuffling step:
The number of blocks is three times the number of blocks used in the color–EtC scheme. The reason is that the GS–EtC scheme concatenates all the three color channels blocks in a single channel, thereby, it transforms each block independent of its color component. When considering the smallest allowable block sizes such as (16 × 16) in Color–EtC schemes and (8 × 8) in GS–EtC schemes then, the number of blocks in GS–EtC are further increased by a factor of four. The keyspace in Equation (17) becomes
The keyspace
for the proposed scheme based on Equations (14) and (15) can be derived as:
For inter block processing, both Color–EtC and IIB–CPE methods have the same keyspace. However, the intra block processing increases the key size of the IIB–CPE by a factor of
. More specifically, when the sub-block size is chosen as
then the increment factor
. On the other hand, the GS–EtC methods represent a color input as pseudo grayscale image; therefore, they have larger keyspace than proposed method. However, color image as an input is a prerequisite for GS–EtC methods. Therefore, when the input is a grayscale image, then the achieved encryption efficiency of GS–EtC methods diminishes and proposed method gains advantage of a larger keyspace. For example, as mentioned in
Section 3, for grayscale image encryption, all of the conventional EtC methods (Color–EtC, Extended EtC and GS–EtC methods) can be implemented in the same steps. Therefore, their keyspace
can be derived as:
Since the images are compressed by the JPEG standard in grayscale mode, the smallest block size of (8 × 8) can be used. On the other hand, the keyspace
of IIB–CPE for grayscale image encryption can be derived by omitting the last term in Equation (19) as:
For inter block processing, both conventional EtC and IIB–CPE methods have the same keyspace. However, the intra block processing increases the key size of the IIB–CPE in the similar way as discussed for color image encryption. Therefore, it can be seen that the encryption efficiency of proposed method is independent of input image representation because of the intra block processing.
For the completeness of security analysis, it is necessary to show robustness of the proposed method against known-plaintext (KPA) and chosen-plaintext attack (CPA). Similar to the conventional EtC methods, the proposed scheme is robust against KPA because of the use of different keys for encryption of each image. Since the proposed method is a symmetric encryption scheme and does not need to disclose any information about the key, it can resist CPA.
4.4. Application: Privacy-Preserving Deep Learning
In contrast to the centralized paradigm, a decentralized system (e.g.,
Federated learning (FL) [
39]
where algorithm is distributed instead of data gathering) relying on the principle of remote executions and distributed data storage provides an infrastructural approach to security and confidentiality [
40]. However, a decentralized system does not fully guarantee privacy. For example, a lack of encryption puts the data and algorithm parameters at risk of being stolen or tampered with, and reconstruction of data from the model weights is also possible [
41]. In addition, a limited computational capacity or a small amount of data at a node may affect the quality of the results [
41]. In this regard, data manipulation techniques, such as differential privacy (DP) [
42] and secure aggregation techniques, such as homomorphic encryption (HE) [
43], can provide security in FL. However, DP can degrade the data and may reduce the accuracy of the model, especially in domains with limited data, for example, medical imaging [
41]. The main challenge in implementing HE is the computational cost and requirement of a specifically designed algorithm to enable computation in the encryption domain [
41]. Similarly, secure multiparty computation (SMPC) [
44] has the disadvantage of communication overhead.
As an application of the IIB–CPE scheme, we propose an end-to-end image communication system for privacy-preserving deep learning-based image classification. The proposed system considers a secure and efficient transmission of images to a remote location, thereby,
end-to-end, and enables classification in the encryption domain without the need for decryption, thereby,
privacy-preserving deep learning. For classification performance, we used the PyramidNet [
45] model of 110 layers in depth and a widening factor of α = 270 with ShakeDrop regularization [
46]. The model was trained for 300 epochs using Stochastic Gradient Descent (GSD) with the Nesterov accelerated gradient and momentum method. The momentum of 0.9, weight decay of 0.0001, and batch size of 128 were used during training. The initial learning rates were set to 0.1 for CIFAR10 and 0.5 for CIFAR100 datasets, which were then decayed by a factor of 0.1 at 150 and 225 epochs.
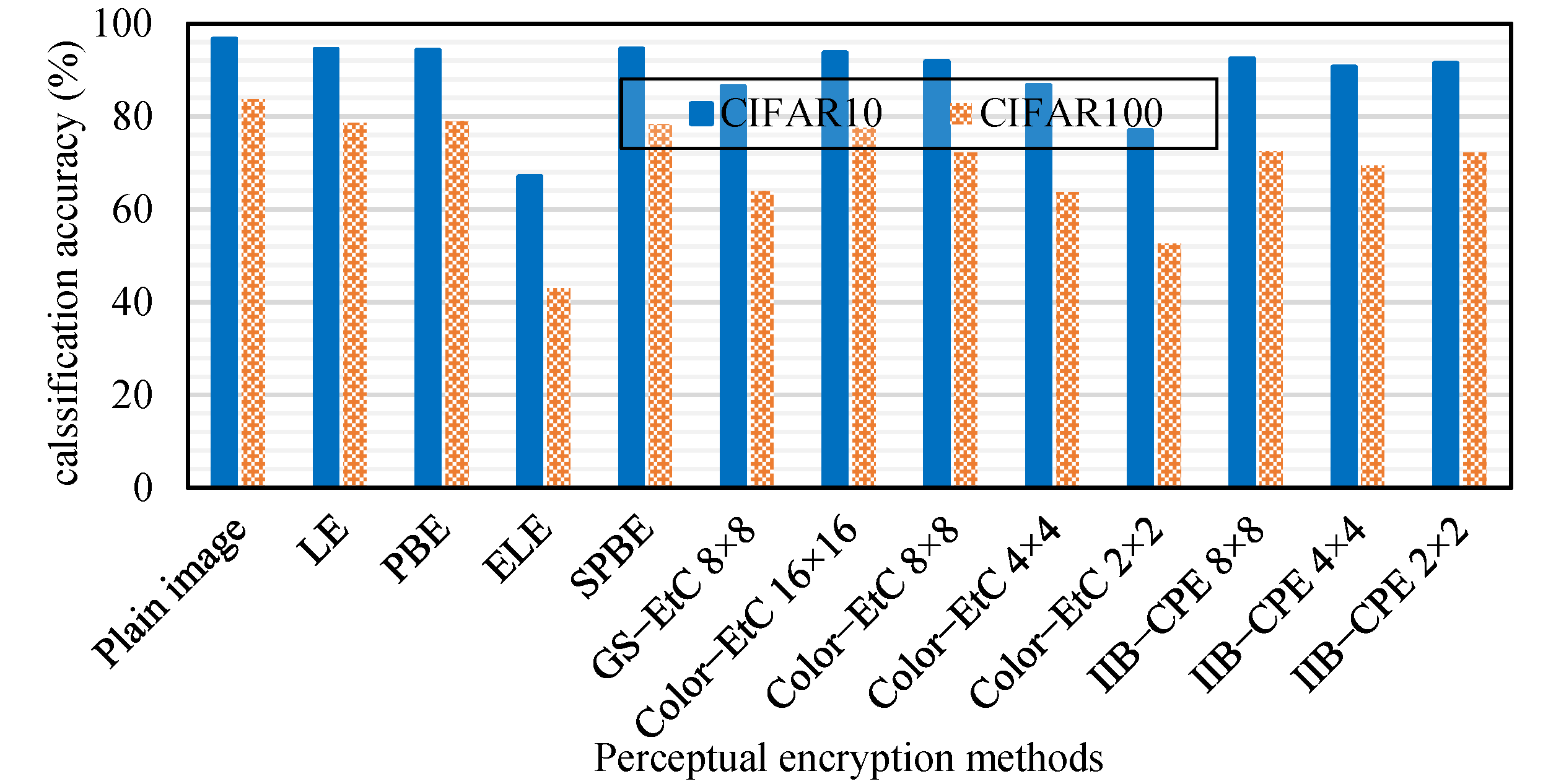
Figure 11 summarizes the classification accuracy of PPDL models. The learnable PE algorithms LE and PBE have the closest accuracy to plain images; however, they are vulnerable to chosen-plaintext attacks, as demonstrated by [
9]. ELE, the most secure PE algorithm, degrades classification accuracy. Among the learnable PE methods, chaos-based SPBE preserved the classification accuracy of plain images while providing a necessary level of security. However, like any other learnable PE method, they do not provide compression savings. In contrast, for compressible PE algorithms, Color–EtC (16 × 16) has the highest accuracy, but its smaller keyspace and larger block size may compromise system security. However, its variant Color–EtC (4 × 4) and conventional GS–EtC (8 × 8) have improved security, but their classification accuracy is reduced, along with compression savings. For the proposed method, when the sub-block size is 8×8, a comparable classification accuracy can be achieved while preserving the compression savings and improving the security of the conventional EtC schemes. Furthermore, for smaller block sizes, there was a slight reduction in the accuracy of the DL model, but improved security strength.
In
Figure 11, the same model and datasets were used for all of the PE methods for fair comparison. In the literature, Color–EtC cipher images were used with two isotropic networks to enable privacy-preserving classification. In their analysis, the best accuracy scores of 87.89% and 92.76% were achieved on the CIFAR 10 dataset for vision transformer (ViT–16) [
47] and ConvMixer [
48], respectively. For the same encryption method (Color–EtC (16 × 16)), our PPDL model achieved almost 6% and 1% better accuracy than ViT and ConvMixer, respectively. However, the main advantage of using ConvMixer is the smaller number of parameters than in the proposed method. On the other hand, when the images were encrypted with the proposed IIB–CPE method, then the achieved accuracy was up to 5% better than the ViT model and almost 2% less than ConvMixer across different smaller block sizes. As mentioned earlier, the use of larger block size makes the Color–EtC method vulnerable to the COA attack. Therefore, the IIB–CPE based PPDL has the main advantage of better security.