Enhanced Authenticated Key Agreement for Surgical Applications in a Tactile Internet Environment
Abstract
1. Introduction
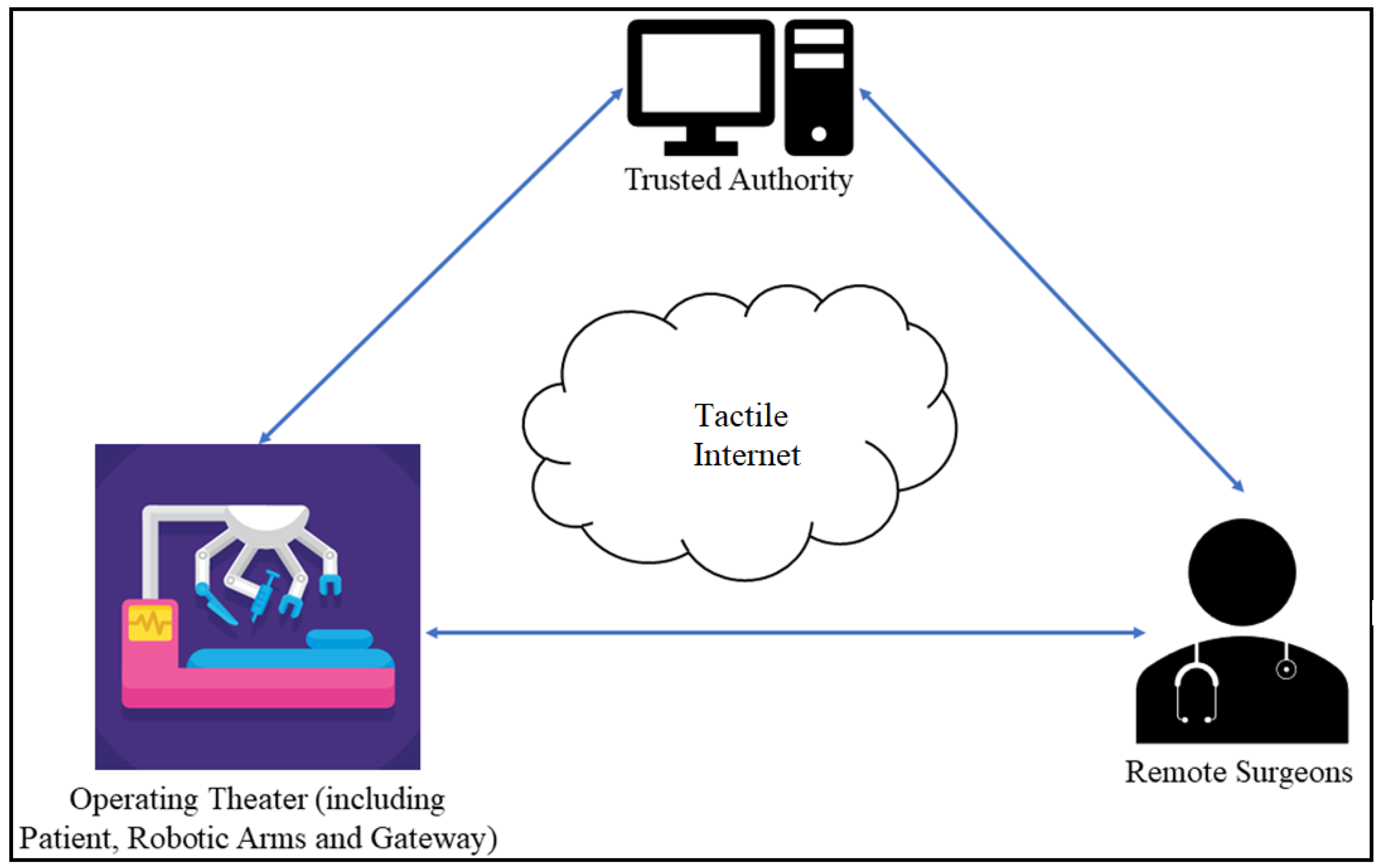
1.1. The Model of a Tactile Internet Remote Surgery Application
1.2. Related Works
1.3. Our Motivation
1.4. Our Contributions
1.5. Organization of Paper
2. Preliminary
2.1. Review of the Scheme of Kamil et al.
| Notation | Description |
|---|---|
| Trusted authority | |
| Gateway | |
| Robotic arm | |
| Remote surgeon | |
| | Identity of gateway Identity of robotic arm |
| Concatenation operation | |
| Timestamp at instant | |
| Allowable network transmission delay | |
| Bitwise exclusive OR (XOR) operation | |
| Hash function | |
| Session key | |
| Adversary |
2.1.1. Gateway and Robotic Arm Registration Phase
2.1.2. User Registration Phase
2.1.3. User Login Phase
2.1.4. Authentication and Key Agreement Phase
2.1.5. Password Updating Phase
2.1.6. Dynamic Robotic Arm Addition Phase
2.1.7. Revocation Phase
2.2. Limitations of the Authenticated Key Agreement Proposed by Kamil et al.
2.2.1. Failure to Resist Robotic Arm Compromise Attacks
2.2.2. Failure to Resist Stolen Verifier Attacks
2.2.3. Failure to Execute Correctly
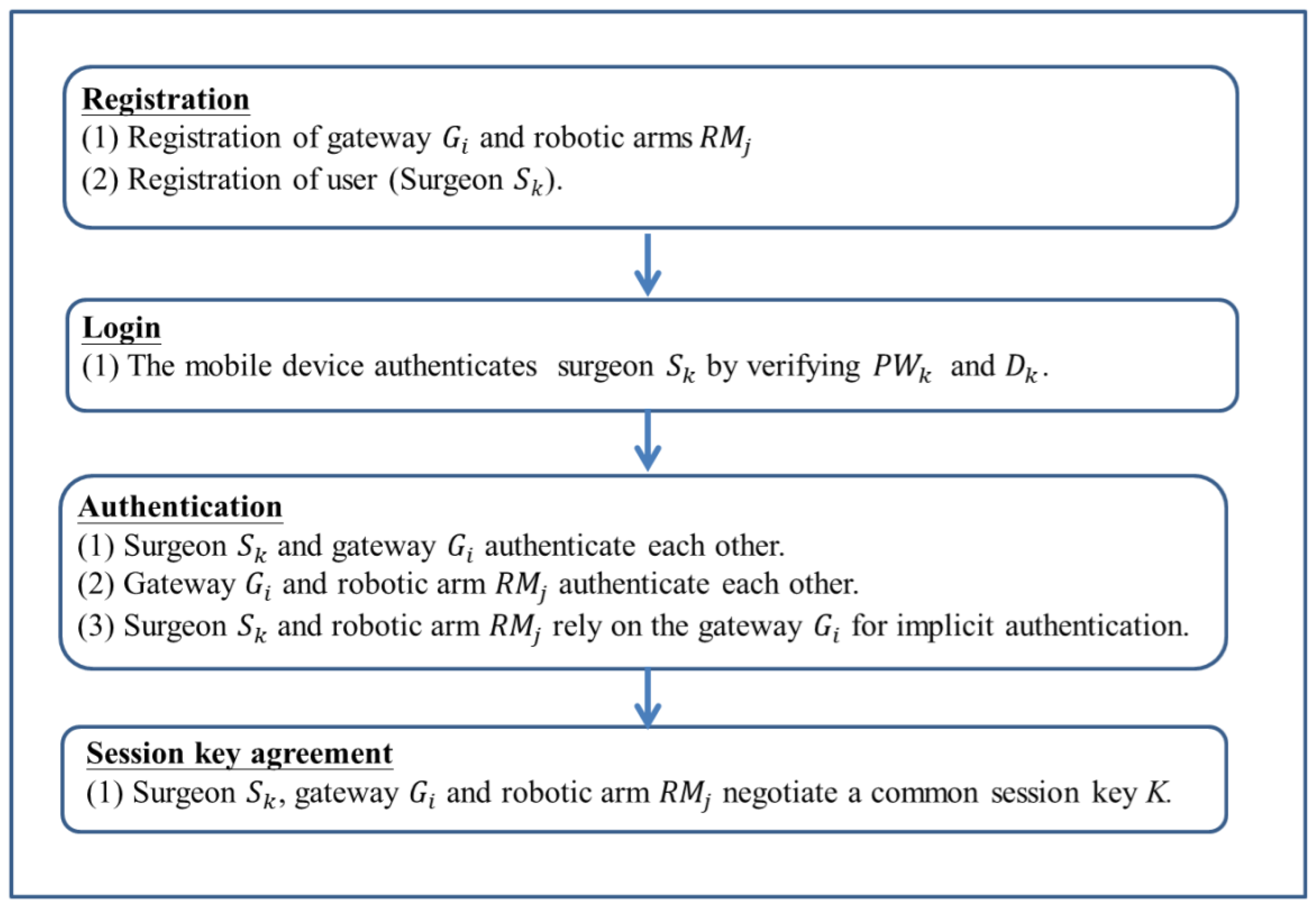
3. Enhanced Authenticated Key Agreement Scheme for Tactile Internet Environment
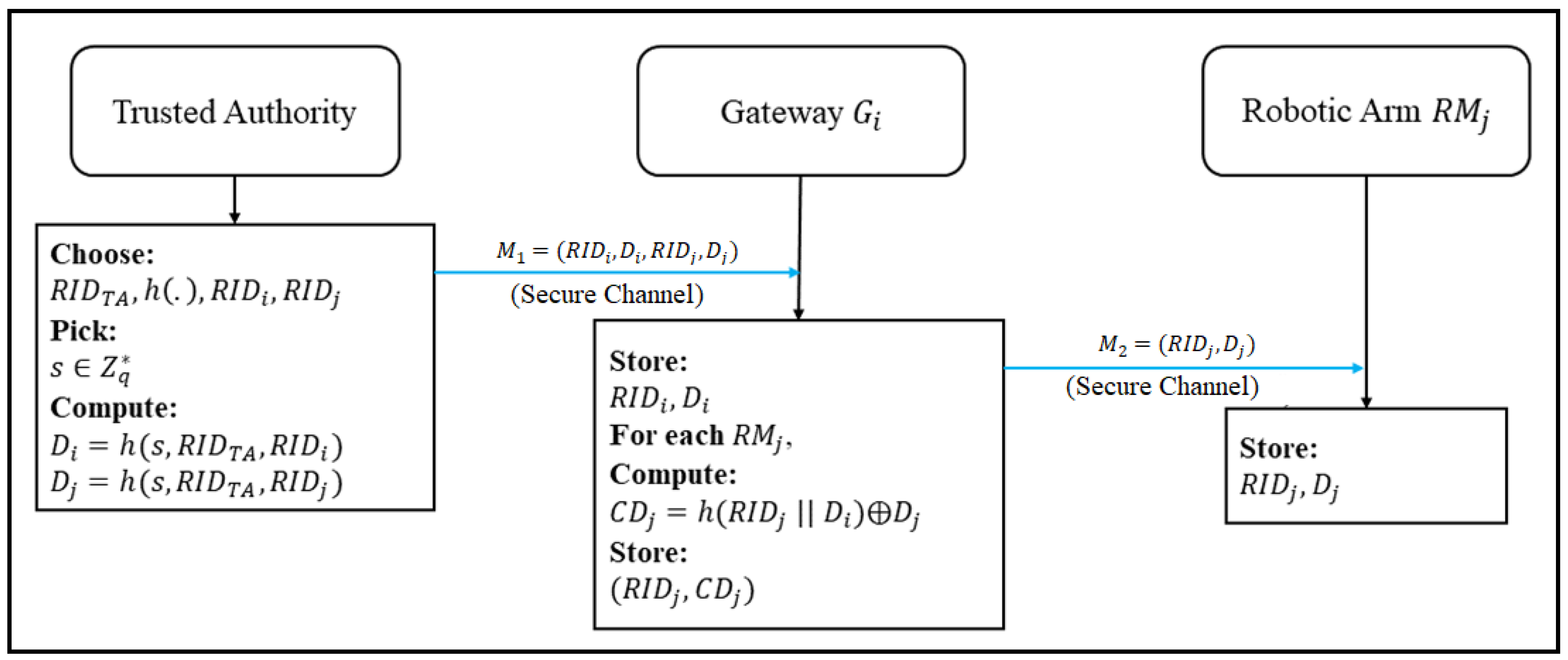
3.1. Registration Phase of Gateway and Robotic Arms
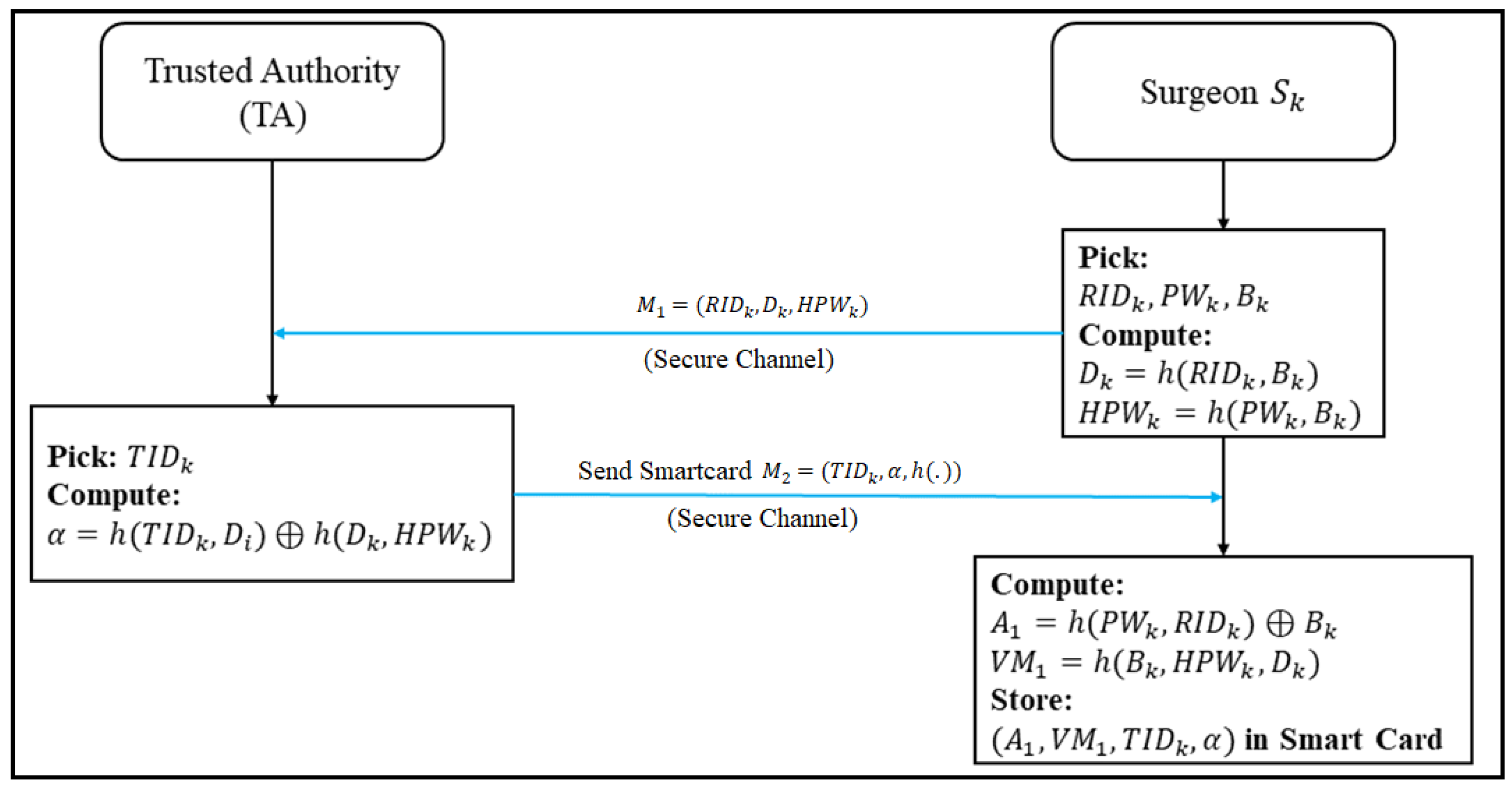
3.2. User Registration Phase
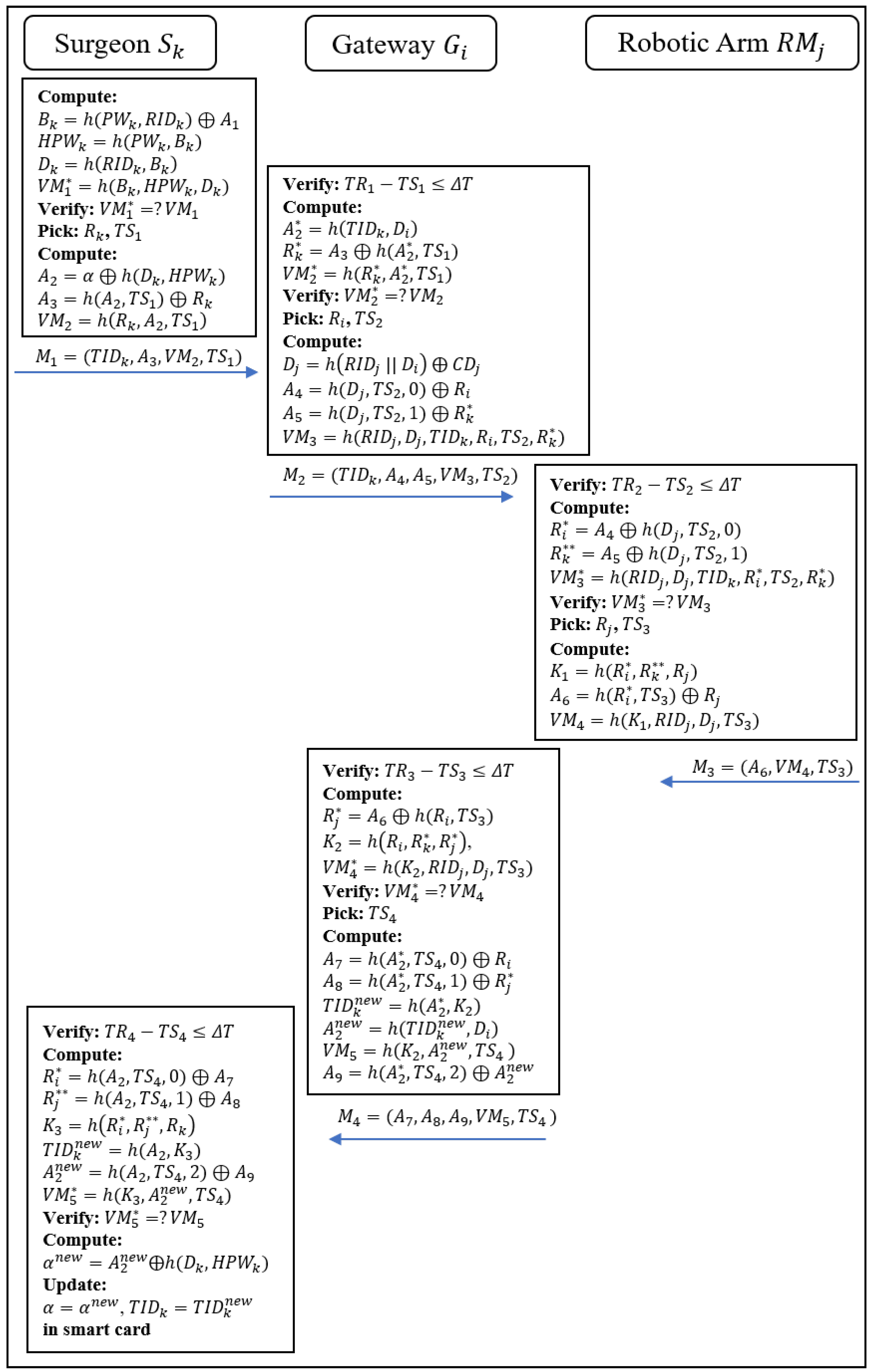
3.3. Login, Authentication, and Session Key Agreement Phase
4. Security and Performance Analysis
4.1. Authentication Proof of the Proposed Scheme Using BAN Logic
4.1.1. Inference Rules of BAN Logic
4.1.2. Goals of Authentication and Key Agreement
4.1.3. Idealized Form
4.1.4. Assumptions
4.1.5. Verification
4.2. Security Analysis
4.2.1. Resistance to Robotic Arm Compromise Attacks
4.2.2. Resistance to Stolen Verifier Attacks
4.3. Functionality Comparison
4.4. Performance Comparisons
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Maier, M.; Chowdhury, M.; Rimal, B.P.; Van, D.P. The tactile internet: Vision, recent progress, and open challenges. IEEE Commun. Mag. 2016, 54, 138–145. [Google Scholar] [CrossRef]
- Shafiq, A.; Ayub, M.F.; Mahmood, K.; Sadiq, M.; Kumari, S.; Chen, C.-M. An Identity-Based Anonymous Three-Party Authenticated Protocol for IoT Infrastructure. J. Sens. 2020, 2020, 8829319. [Google Scholar] [CrossRef]
- Simsek, M.; Aijaz, A.; Dohler, M.; Sachs, J.; Fettweis, G. 5G-enabled tactile internet. IEEE J. Sel. Areas Commun. 2016, 34, 460–473. [Google Scholar] [CrossRef]
- Fettweis, G.P. The tactile internet: Applications and challenges. IEEE Veh. Technol. Mag. 2014, 9, 64–70. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Biswas, G.P.; Khan, M.K.; Kumar, N. A robust and anonymous patient moni-toring system using wireless medical sensor networks. Future Gener. Comput. Syst. 2018, 80, 483–495. [Google Scholar] [CrossRef]
- Wu, F.; Li, X.; Sangaiah, A.K.; Xu, L.; Kumari, S.; Wu, L.; Shen, J. A lightweight and robust two-factor authentication scheme for personalized healthcare systems using wireless medical sensor networks. Future Gener. Comput. Syst. 2018, 82, 727–737. [Google Scholar] [CrossRef]
- Chandrakar, P.A. Secure Remote User Authentication Protocol for Healthcare Monitoring Using Wireless Medical Sensor Networks. Int. J. Ambient Comput. Intell. 2019, 10, 96–116. [Google Scholar] [CrossRef]
- Kaur, K.; Garg, S.; Kaddoum, G.; Guizani, M. Secure authentication and key agreement protocol for tactile internet-based tele-surgery ecosystem. In Proceedings of the ICC 2020—2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Nykvist, C.; Larsson, M.; Sodhro, A.H.; Gurtov, A. A lightweight portable intrusion detection communication system for auditing applications. Int. J. Commun. Syst. 2020, 33, e4327. [Google Scholar] [CrossRef]
- Bolton, T.; Dargahi, T.; Belguith, S.; Al-Rakhami, M.; Sodhro, A. On the Security and Privacy Challenges of Virtual Assistants. Sensors 2021, 21, 2312. [Google Scholar] [CrossRef]
- Kamil, I.A.; Ogundoyin, S.O. A lightweight mutual authentication and key agreement protocol for remote surgery application in Tactile Internet environment. Comput. Commun. 2021, 170, 1–18. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Lee, J.H. User authentication in a tactile internet based remote surgery environment: Security issues, challenges, and future research directions. Pervasive Mob. Comput. 2019, 54, 71–85. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R.M. A logic of authentication. Proc. R. Soc. Lond. A Math. Phys. Sci. 1989, 426, 233–271. [Google Scholar]
- Guo, H.; Xu, Y.G.T.; Zhang, X.; Ye, J. A secure and efficient three-factor multigateway authenti-cation protocol for wireless sensor networks. Ad Hoc Netw. 2019, 95, 101965. [Google Scholar] [CrossRef]
- Soni, P.; Pal, A.K.; Islam, S.H. An improved three-factor authentication scheme for patient monitoring using WSN in remote health-care system. Comput. Methods Programs Biomed. 2019, 182, 105054. [Google Scholar] [CrossRef] [PubMed]
- Li, X.; Peng, J.; Obaidat, M.S.; Wu, F.; Khan, M.K.; Chen, C. A secure three-factor user authentica-tion protocol with forward secrecy for wireless sensor network systems. IEEE Syst. J. 2020, 4, 39–50. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Lee, J.-H.; Sherratt, R.S. Enhanced three-factor security protocol for consumer USB mass storage devices. IEEE Trans. Consum. Electron. 2014, 60, 30–37. [Google Scholar] [CrossRef]
| Notation | Abbreviation |
|---|---|
| Entity believes statement | |
| has jurisdiction over statement | |
| once said | |
| sees | |
| Formula is encrypted by key | |
| and communicate via shared key | |
| sends the message (), and receives it | |
| is freshly generated |
| Security Attribute | [11] | [5] | [6] | [7] | [14] | [15] | [16] | Our AKA |
|---|---|---|---|---|---|---|---|---|
| Provision of strong anonymity | O | O | X | O | X | O | O | O |
| Provision of session key establishment | O | - | O | - | O | O | O | O |
| Provision of perfect forward secrecy | O | O | O | O | O | O | O | O |
| Resistance to replay attacks | O | X | X | O | O | O | X | O |
| Resistance to impersonation attacks | O | X | O | O | O | O | O | O |
| Resistance to offline user login credentials guessing attack | O | X | O | O | O | O | O | O |
| Resistance to insider attacks | O | - | O | O | O | O | O | O |
| Resistance to mobile device loss attacks | O | X | O | O | O | O | O | O |
| Resistance to denial of service attacks | O | O | O | O | O | O | O | O |
| Resistance to robotic arm compromise attacks | X | X | O | O | O | O | O | O |
| Resistance to stolen verifier attacks | X | O | O | X | O | X | X | O |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, T.-F.; Ye, X.; Chen, W.-Y.; Chang, C.-C. Enhanced Authenticated Key Agreement for Surgical Applications in a Tactile Internet Environment. Sensors 2022, 22, 7941. https://doi.org/10.3390/s22207941
Lee T-F, Ye X, Chen W-Y, Chang C-C. Enhanced Authenticated Key Agreement for Surgical Applications in a Tactile Internet Environment. Sensors. 2022; 22(20):7941. https://doi.org/10.3390/s22207941
Chicago/Turabian StyleLee, Tian-Fu, Xiucai Ye, Wei-Yu Chen, and Chi-Chang Chang. 2022. "Enhanced Authenticated Key Agreement for Surgical Applications in a Tactile Internet Environment" Sensors 22, no. 20: 7941. https://doi.org/10.3390/s22207941
APA StyleLee, T.-F., Ye, X., Chen, W.-Y., & Chang, C.-C. (2022). Enhanced Authenticated Key Agreement for Surgical Applications in a Tactile Internet Environment. Sensors, 22(20), 7941. https://doi.org/10.3390/s22207941









