Investigation of Energy Cost of Data Compression Algorithms in WSN for IoT Applications
Abstract
1. Introduction and Motivation
2. Related Work
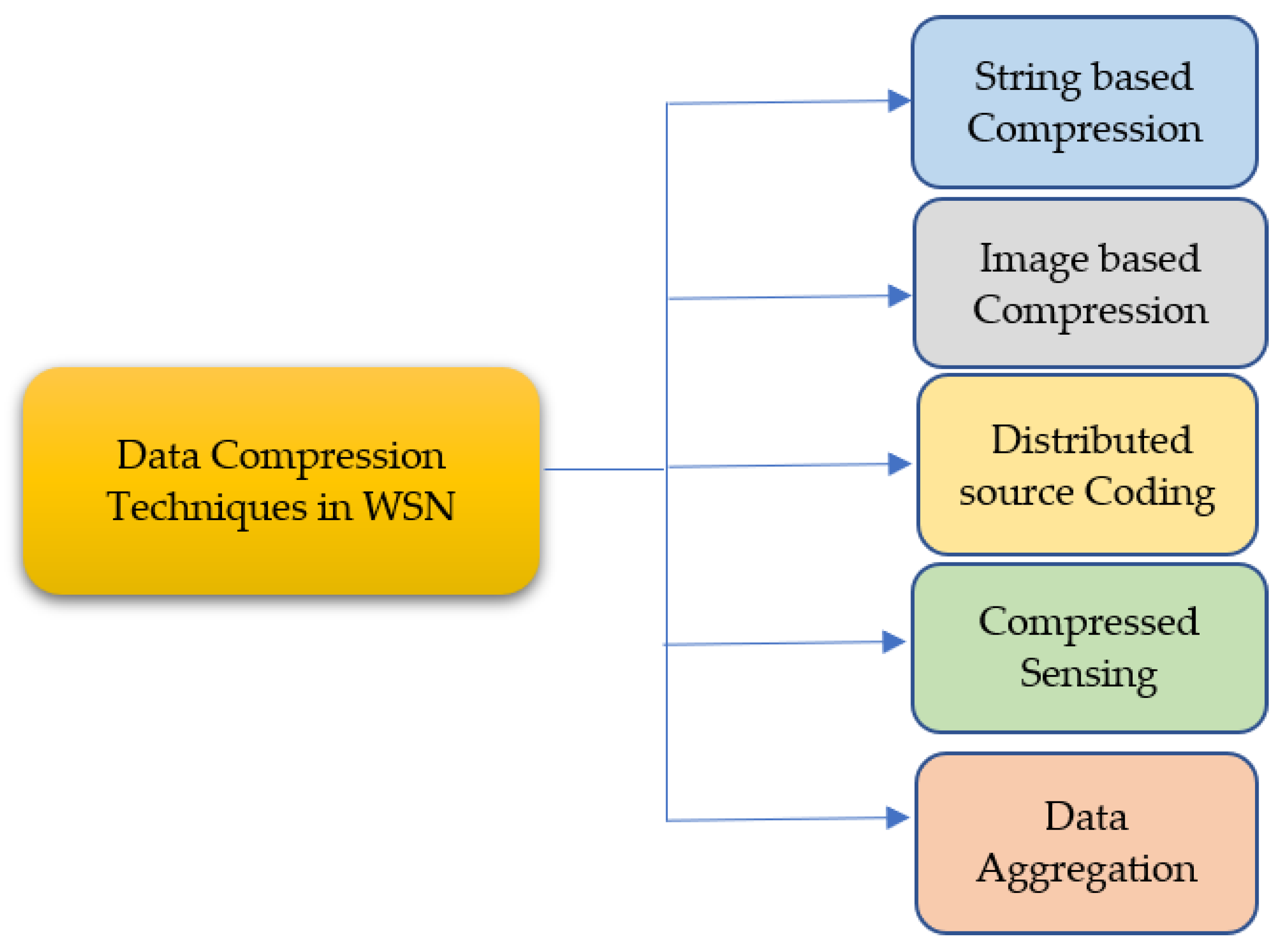
3. Data Compression Techniques
3.1. RLE (Run Length Encoding)
3.2. Adaptive Huffman Encoding
- (a)
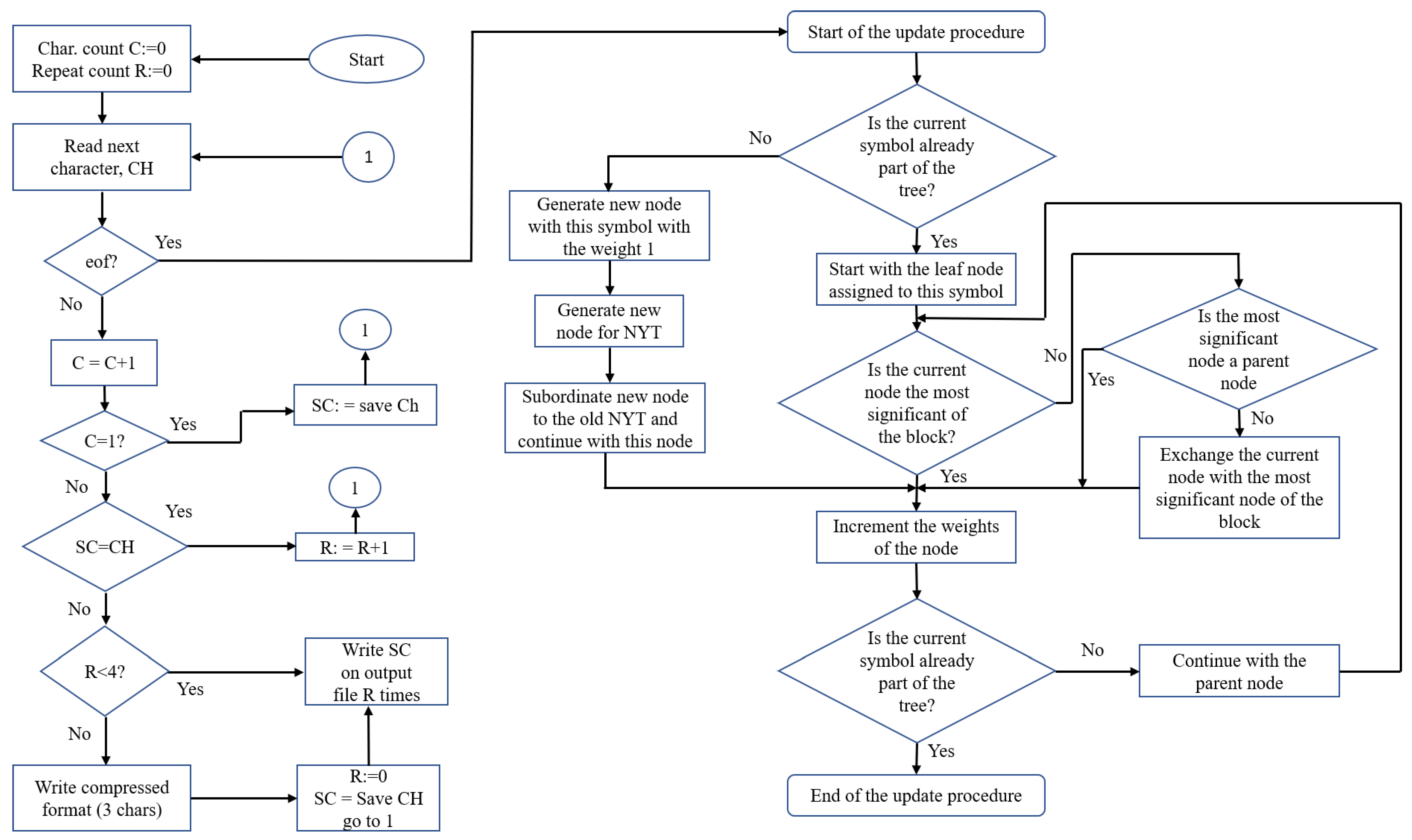
- Encoding Procedure: Initially, there is just one node in the tree at both the encoder and the decoder, which is the NYT node. As a result, the very first symbol that emerges has a predetermined code-word. When encoding a symbol for the second time, we transmit the code for the NYT node, followed by the fixed code for the symbol that was already agreed upon, unless we are dealing with the very first symbol again. By following the Huffman tree from its root to the NYT node, we may retrieve its corresponding code. This notifies the receiver that the Huffman tree does not yet include a node corresponding to the symbol whose code is about to be received. If a symbol has to be encoded and there is an external node in the tree that corresponds to it, a path from the root node to the external node can be used to produce the symbol’s code.
- (b)
- Update Procedure: To perform the update method, the nodes must be arranged in a predetermined order. Using node numbers, this order is maintained.
4. Hybrid Model for Run Length Encoding with Adaptive Huffman Encoding
4.1. Hybrid Run Length Encoding with Adaptive Huffman Encoding (H-RLEAHE) Algorithm
4.2. Hybrid Algorithm
| Algorithm 1: H-RLEAHE Compression Algorithm |
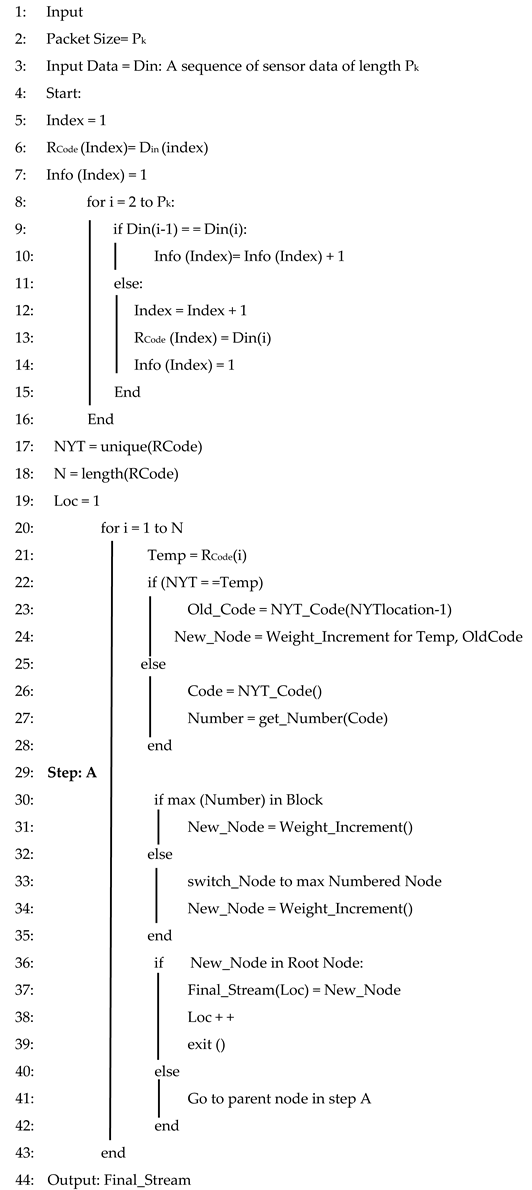 |
| Algorithm 2: Decompression algorithm for H-RLEAHE |
 |
5. Performance Measures and Analysis
- A.
- Compression Ratio (CR): The compression algorithms factor is the ratio of the size of the uncompressed data in bits (buc) to the size of the compressed data in bits (bc) [43].
- B.
- Compression Time (CT): The time it takes to compress the original data [43].
- C.
- Consumption of CPU resources or power used during data compression: An investigation on data compression’s impact on energy use.
- D.
- Transmission cost: The amount of energy consumed to transmit compressed data.
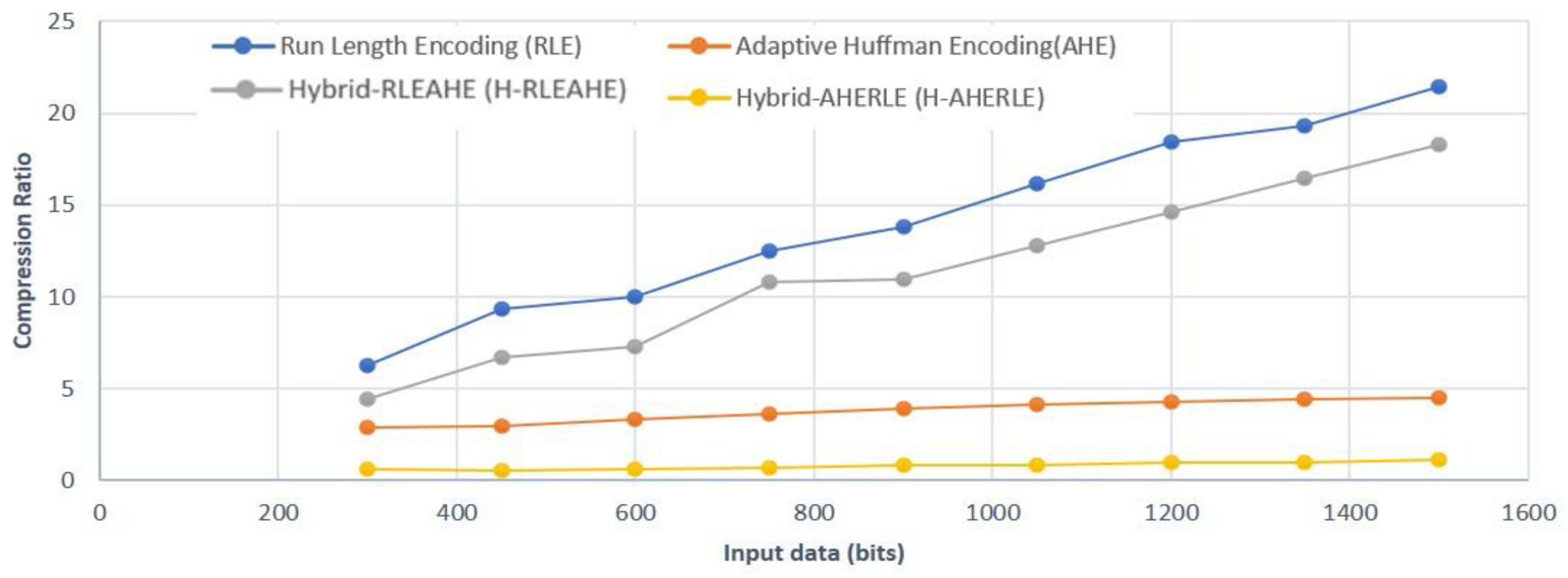
Analysis of RLE, AHE, H-RLEAHE and H-AHERLE Algorithm
- (a)
- CPU cost for RLE is formulated as in Equation (4)where L1 is the compressed data of RLE and compressed bits is 70 bits, CPU cost is 0.00018731 J and transmission cost is is 1.61 10−5 J. RLE algorithim uses two addition operators and one comparison operator.
- (b)
- CPU cost for AHE is formulated as in Equation (5)where L1 is the compressed data of AHE and compressed data is 330 bits, CPU cost is 0.0017029 J and transmission cost is × 30 bits is 7.59 10−5 J. In Equation (5) there are 9 addition operators 4 subtratctions, 1 multiplication, 1 division and 14 comaprison operators.
- (c)
- CPU cost for H-RLEAHE is formulated as in Equation (6)where L1 is the compressed data of RLE, the is the compressed data of H-RLEAHE and data compressed is 82, CPU cost is 0.00025543 J and transmission cost is 82 bits is 1.886 10−5 J. From equation 6 we can observe that there are two addition operators, one compariosn, 23 addition operators, 4 subtractions, 1 division and multiplication and 1 compariosn operators.
- (d)
- CPU cost for H-AHERLE is formulated as in Equation (7)where L1 is the compressed data of AHE, is the compressed data of H-AHERLE and data compressed is 1360, CPU cost is 0.0019502 J and transmission cost is 1360 bits is 0.0003128 J. Operators used in Equation (7) is 23 additions, 4 subtractions, 1 multiplication and division, and 1 comparison. It can be clearly seen that the transmission cost and CPU cost for RLE is better than the other data compression algorithms.
6. Network Setup and Scenario Analysis
- Consider all sensor nodes to be stationary.
- The study assumes that the data gathered from source IoT nodes is destined for a single BS.
- SNs that have similar processing and communication capabilities are considered homogeneous. It also takes into account the fact that all SNs have the same initial energy.
- The x and y coordinates of SNs released randomly are always in the topological region.
- Applying Euclidean distance, the separation between two near-neighboring SNs is calculated.
6.1. Results and Discussion
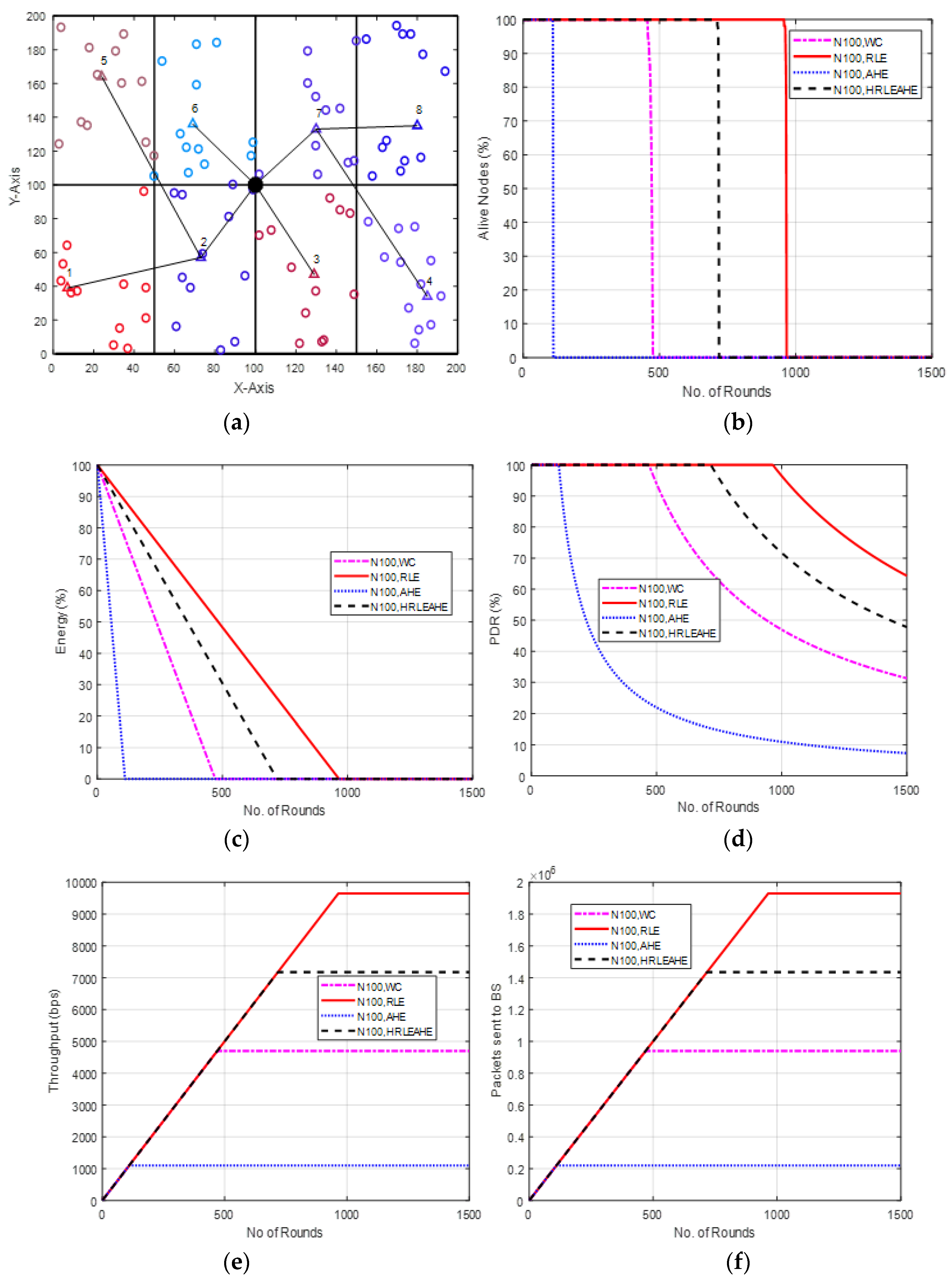
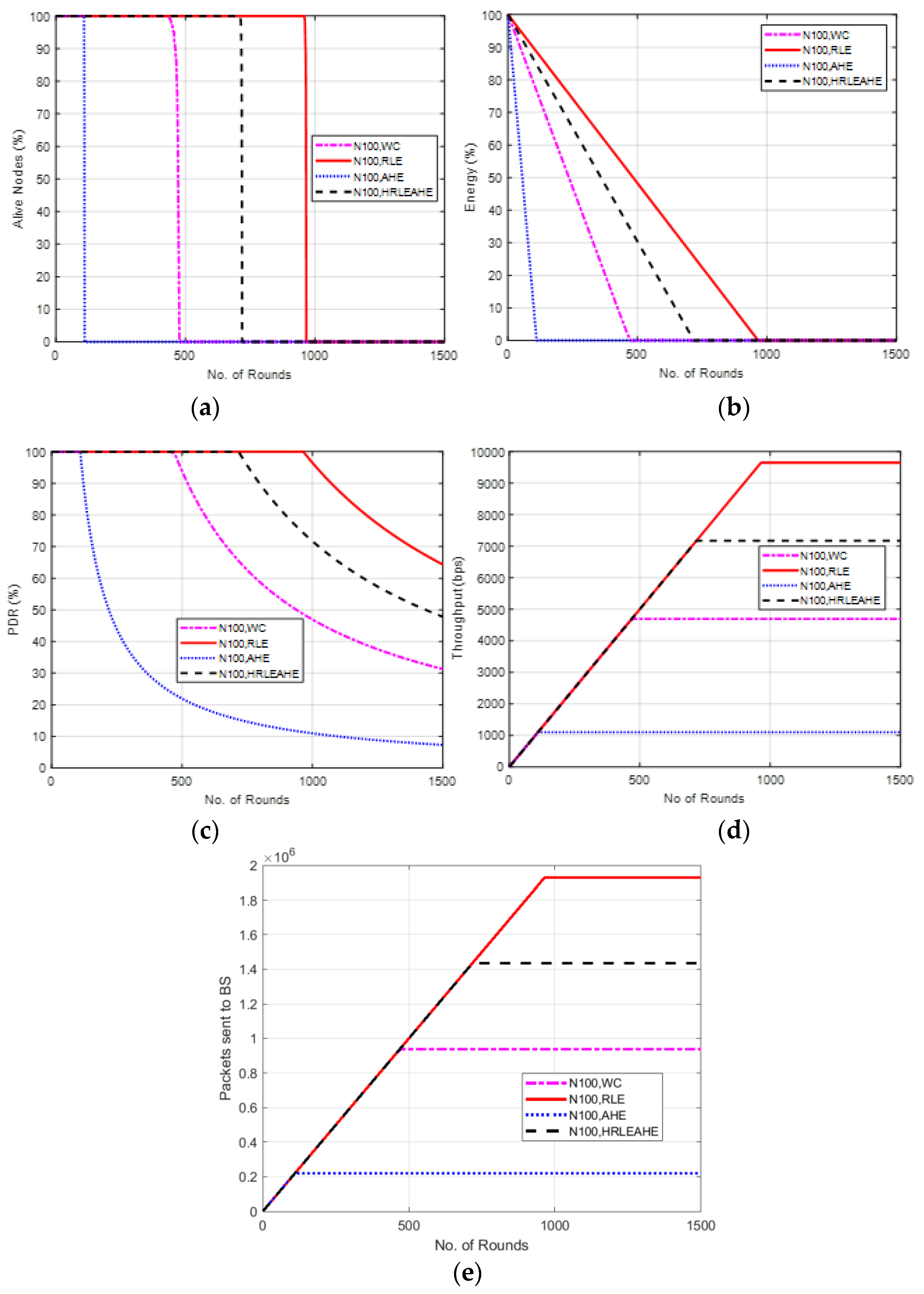
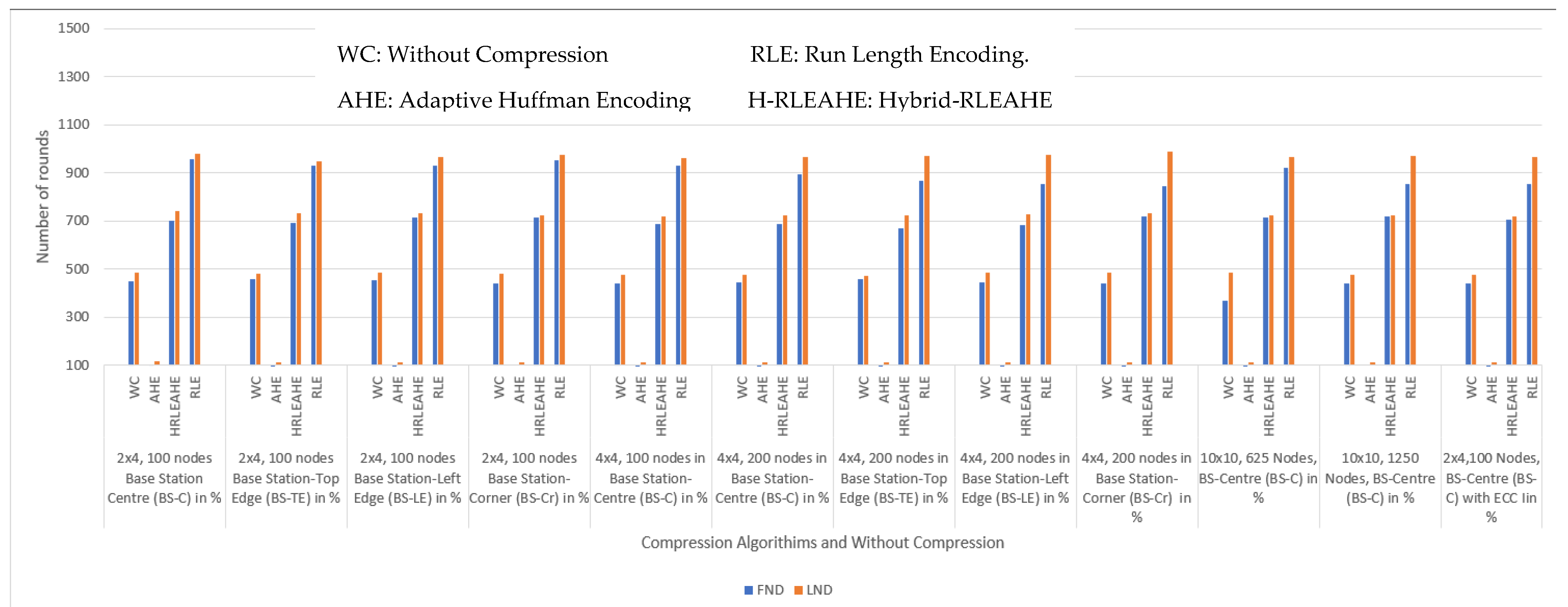
6.2. Case Study 1-1: 2 × 4, 100 Nodes, BS at Center
6.3. Case Study 1-2: 2 × 4, 100 Nodes, BS at Top Edge
6.4. Case Study 1-3: 2 × 4, 100 Nodes, BS at Left Edge
6.5. Case Study 1-4: 2 × 4 Grids, 100 Nodes, BS at Corner
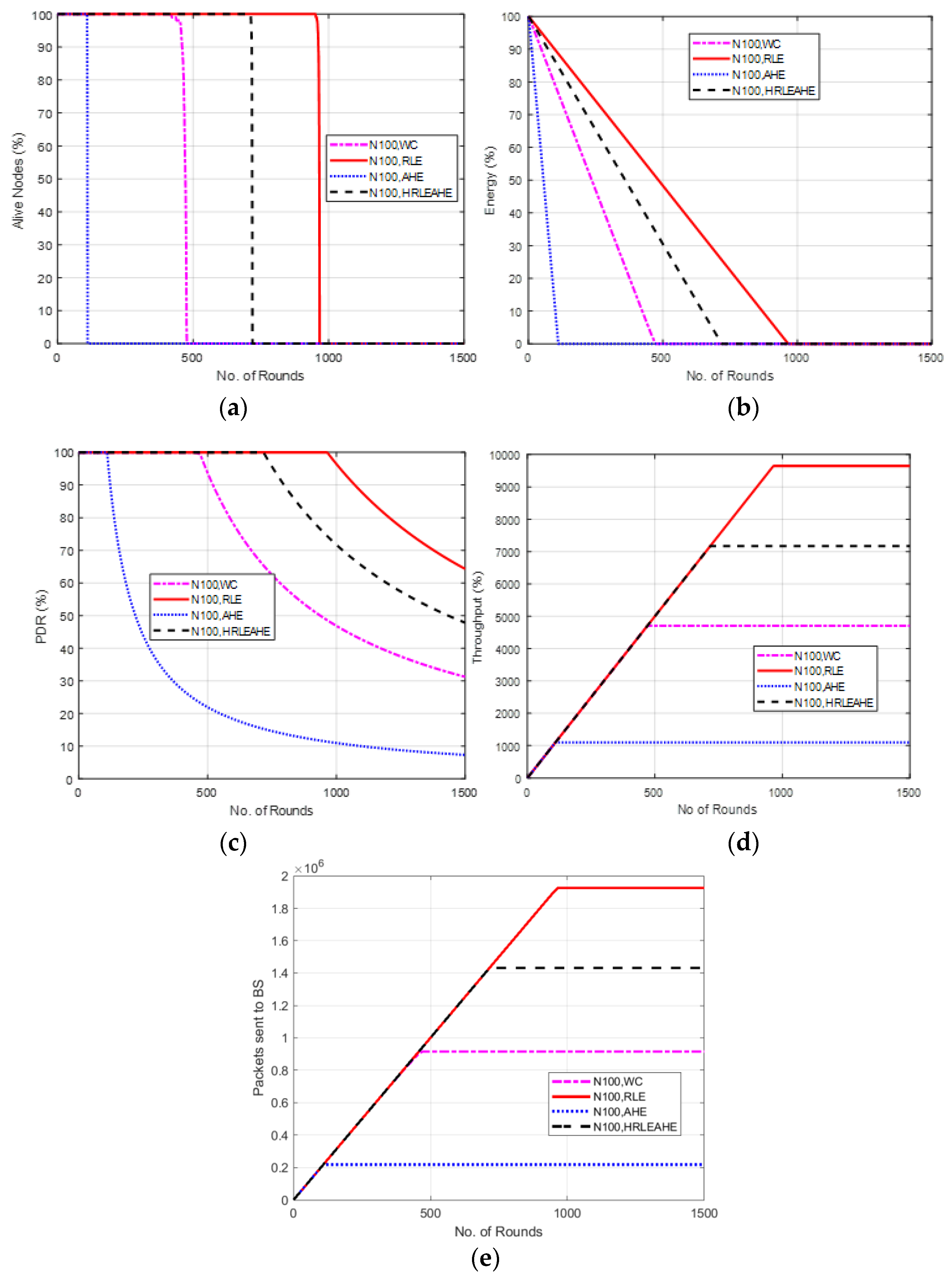
6.6. Case Study 2: 4 × 4 Grids, 100 Nodes, BS at Center
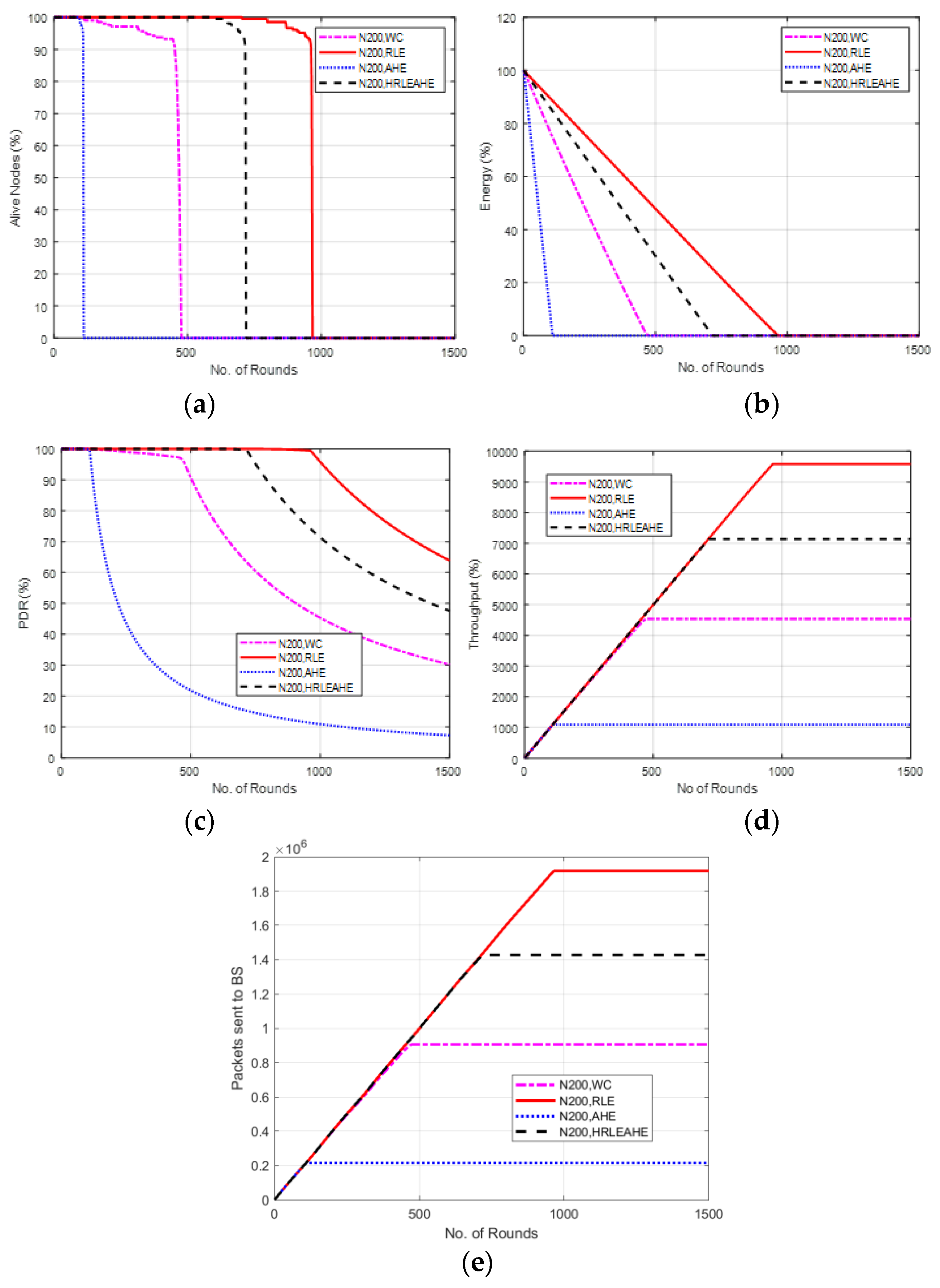
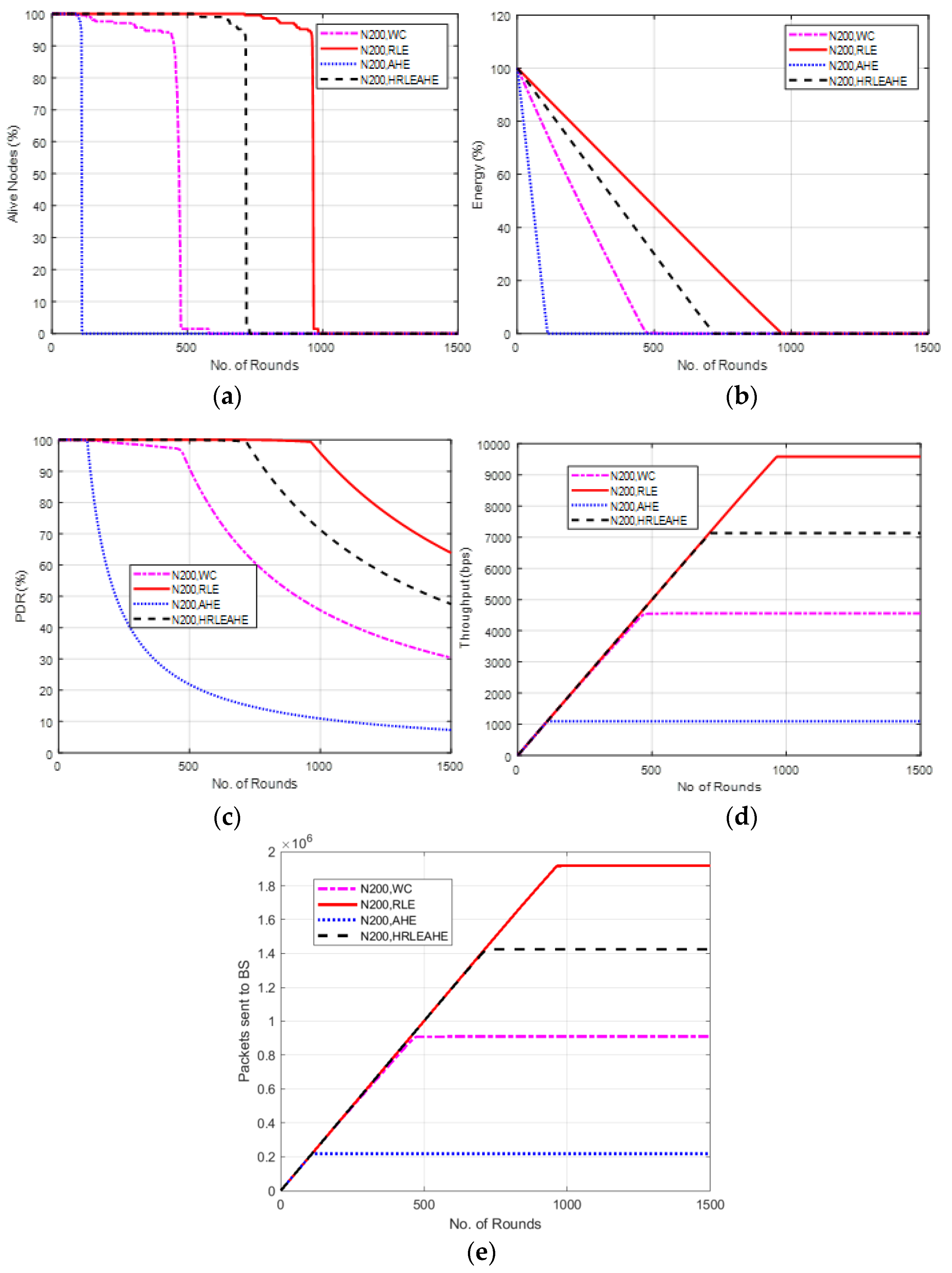
6.7. Case Study 3-1: 4 × 4, 200 Nodes, BS at Center
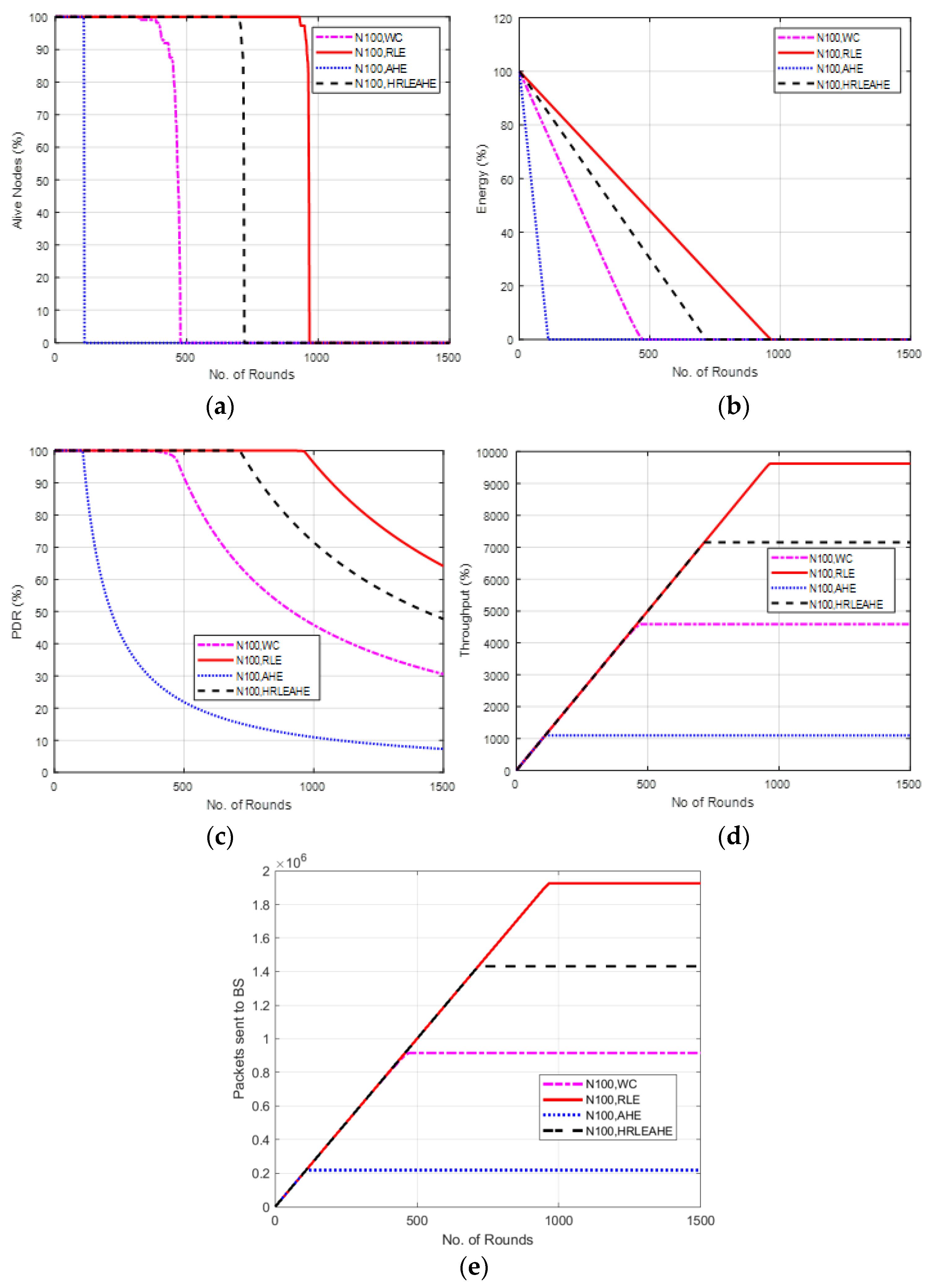
6.8. Case Study 3-2: 4 × 4, 200 Nodes, BS at Top Edge
6.9. Case Study 3-3: 4 × 4, 200 Nodes, BS at Left Edge
6.10. Case Study 3-4: 4 × 4, 200 Nodes, BS at Corner
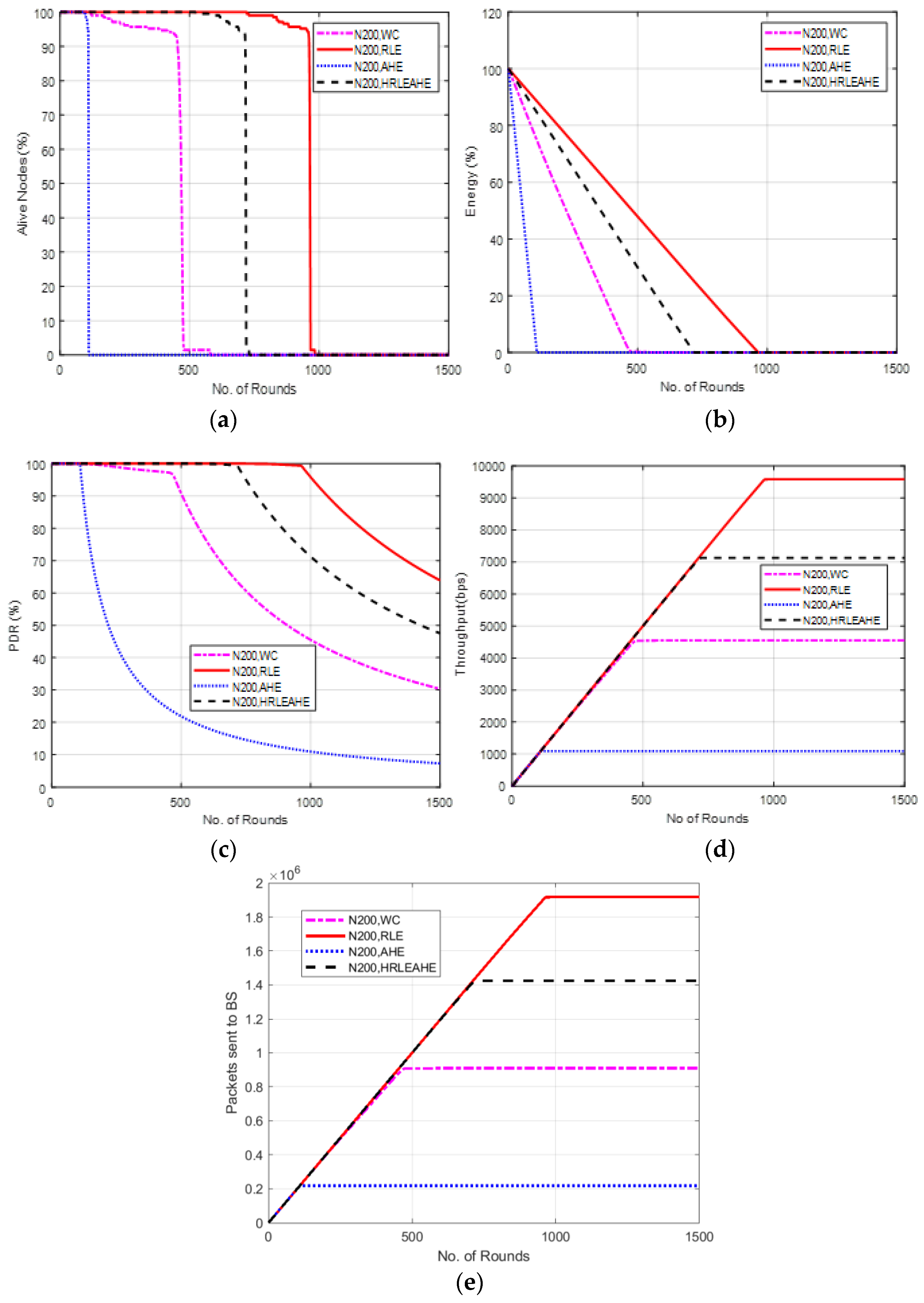
6.11. Case Study 4: 10 × 10, 650 Nodes, BS at Center
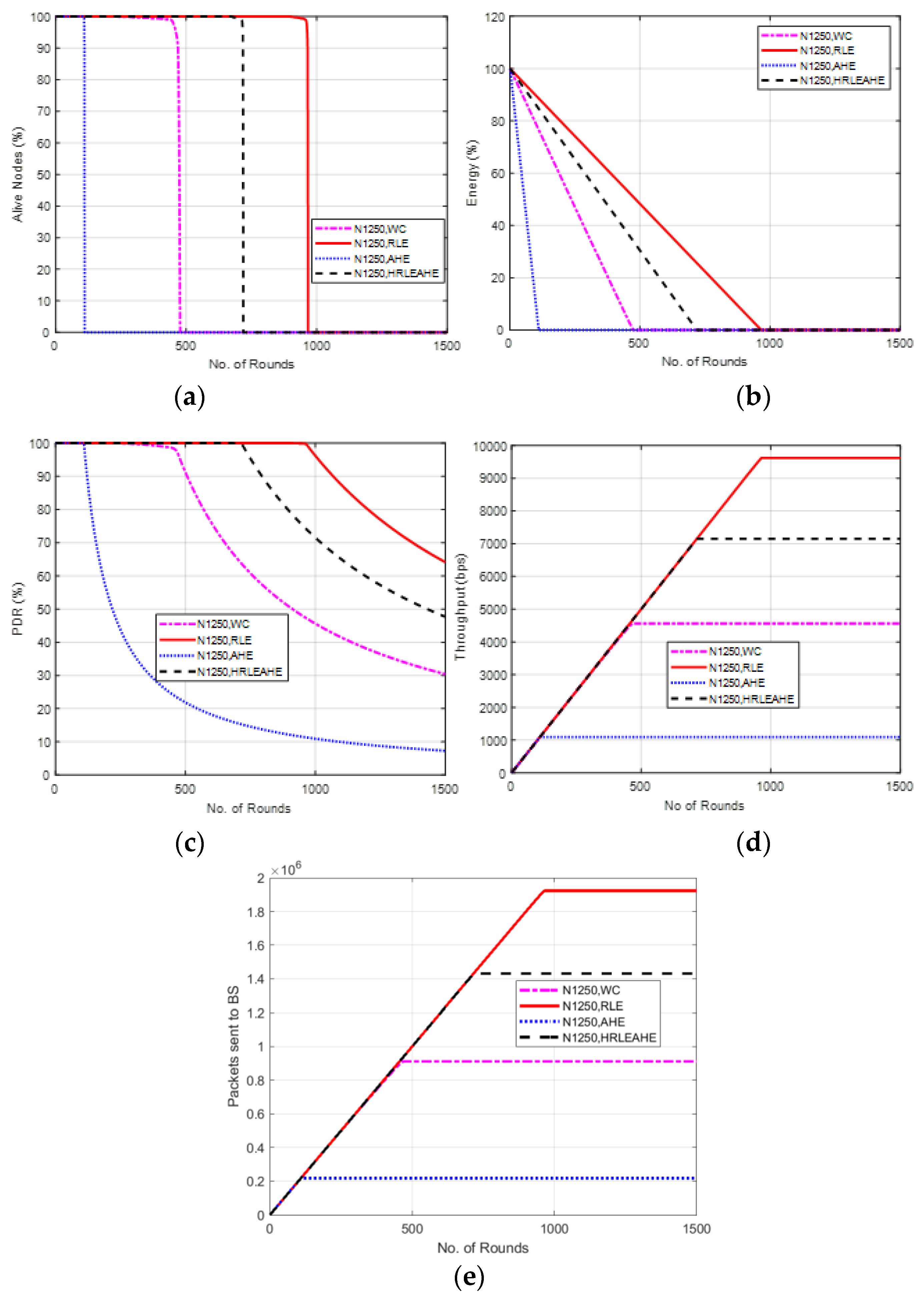
6.12. Case Study 5: 10 × 10, 1250 Nodes, BS at Center
6.13. Case Study 6: Study of Data Compression with Elliptic Curve Cryptography (ECC) for 2 × 4, 100 Nodes, BS at the Center
7. Comparative Analysis with Respect to Alive Nodes
8. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Majid, M.; Habib, S.; Javed, A.R.; Rizwan, M.; Srivastava, G.; Gadekallu, T.R.; Lin, J.C.-W. Applications of Wireless Sensor Networks and Internet of Things Frameworks in the Industry Revolution 4.0: A Systematic Literature Review. Sensors 2022, 22, 2087. [Google Scholar] [CrossRef]
- Lin, J.C.-W.; Wu, J.M.-T.; Fournier-Viger, P.; Djenouri, Y.; Chen, C.-H.; Zhang, Y. A Sanitization Approach to Secure Shared Data in an IoT Environment. IEEE Acess 2019, 7, 25359–25368. [Google Scholar] [CrossRef]
- Dâmaso, A.; Freitas, D.; Rosa, N.; Silva, B.; Maciel, P. Evaluating the Power Consumption of Wireless Sensor Network Applications Using Models. Sensors 2013, 13, 3473–3500. [Google Scholar] [CrossRef]
- Sefuba, M.; Walingo, T. Energy-efficient medium access control and routing protocol for multihop wireless sensor networks. IET Wirel. Sens. Syst. 2018, 8, 99–108. [Google Scholar] [CrossRef]
- Yemeni, Z.; Wang, H.; Ismael, W.M.; Wang, Y.; Chen, Z. Reliable spatial and temporal data redundancy reduction approach for WSN. Comput. Netw. 2020, 185, 107701. [Google Scholar] [CrossRef]
- Kumar, S.; Chaurasiya, V.K. A Strategy for Elimination of Data Redundancy in Internet of Things (IoT) Based Wireless Sensor Network (WSN). IEEE Syst. J. 2018, 13, 1650–1657. [Google Scholar] [CrossRef]
- Kshirsagar, R.V.; Jirapure, A.B. A fault tolerant approach to extend network life time of wireless sensor network. In Proceedings of the 2015 International Conference on Advances in Computing, Communications and Informatics, Kochi, India, 10–13 August 2015; pp. 993–998. [Google Scholar] [CrossRef]
- Rajesh, L.; Reddy, C.B. Efficient wireless sensor network using nodes sleep/active strategy. In Proceedings of the International Conference on Inventive Computation Technologies (ICICT), Coimbatore, India, 26–27 August 2016; Volume 2, pp. 1–4. [Google Scholar]
- Jayasankar, U.; Thirumal, V.; Ponnurangam, D. A survey on data compression techniques: From the perspective of data quality, coding schemes, data type and applications. J. King Saud Univ. Comput. Inf. Sci. 2021, 33, 119–140. [Google Scholar] [CrossRef]
- Le, T.L.; Vo, M.-H. Lossless Data Compression Algorithm to Save Energy in Wireless Sensor Network. In Proceedings of the 4th International Conference on Green Technology and Sustainable Development (GTSD), Ho Chi Minh City, Vietnam, 23–24 November 2018; pp. 597–600. [Google Scholar]
- Chen, C.; Zhang, L.; Tiong, R.L.K. A new lossy compression algorithm for wireless sensor networks using Bayesian predictive coding. Wirel. Netw 2020, 26, 5981–5995. [Google Scholar] [CrossRef]
- Wu, M.; Tan, L.; Xiong, N. Data prediction, compression, and recovery in clustered wireless sensor networks for environmental monitoring applications. Inf. Sci. 2016, 329, 800–818. [Google Scholar] [CrossRef]
- Aanchal, A.; Kumar, S.; Kaiwartya, O.; Abdullah, A.H. Green computing for wireless sensor networks: Optimization and Huffman coding approach. Peer Peer Netw. Appl. 2017, 10, 592–609. [Google Scholar] [CrossRef]
- Sheltami, T.; Musaddiq, M.; Shakshuki, E. Data compression techniques in Wireless Sensor Networks. Futur. Gener. Comput. Syst. 2016, 64, 151–162. [Google Scholar] [CrossRef]
- Zhou, B.; Jin, H.; Zheng, R. A Parallel High Speed Lossless Data Compression Algorithm in Large-Scale Wireless Sensor Network. Int. J. Distrib. Sens. Netw. 2015, 11, 795353. [Google Scholar] [CrossRef]
- Lungisani, B.A.; Lebekwe, C.K.; Zungeru, A.M.; Yahya, A. Image Compression Techniques in Wireless Sensor Networks: A Survey and Comparison. IEEE Access 2022, 10, 82511–82530. [Google Scholar] [CrossRef]
- Manikandan, S.; Chinnadurai, M. Effective Energy Adaptive and Consumption in Wireless Sensor Network Using Distributed Source Coding and Sampling Techniques. Wirel. Pers. Commun. 2021, 118, 1393–1404. [Google Scholar] [CrossRef]
- Fute, E.T.; Kamdjou, H.M.; El Amraoui, A.; Nzeukou, A. DDCA-WSN: A Distributed Data Compression and Aggregation Approach for Low Resources Wireless Sensors Networks. Int. J. Wirel. Inf. Netw. 2022, 29, 80–92. [Google Scholar] [CrossRef]
- Masoum, A.; Meratnia, N.; Havinga, P.J. A Distributed Compressive Sensing Technique for Data Gathering in Wireless Sensor Networks. Procedia Comput. Sci. 2013, 21, 207–216. [Google Scholar] [CrossRef]
- Alemdar, A.; Ibnkahla, M. Wireless sensor networks: Applications and challenges. In Proceedings of the 9th International Symposium on Signal Processing and Its Applications, Sharjah, United Arab Emirates, 12–15 February 2007; pp. 1–6. [Google Scholar]
- Khriji, S.; Chéour, R.; Goetz, M.; El Houssaini, D.; Kammoun, I.; Kanoun, O. Measuring energy consumption of a wireless sensor node during transmission: Panstamp. In Proceedings of the IEEE 32nd International Conference on Advanced Information Networking and Applications (AINA), Krakow, Poland, 16–18 May 2018; pp. 274–280. [Google Scholar]
- Lin, M.-B.; Lee, J.-F.; Jan, G. A Lossless Data Compression and Decompression Algorithm and Its Hardware Architecture. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2003, 14, 499–510. [Google Scholar] [CrossRef]
- Abo-Zahhad, M.; Rajoub, B.A. An effective coding technique for the compression of one-dimensional signals using wavelet transforms. Med. Eng. Phys. 2002, 24, 185–199. [Google Scholar] [CrossRef]
- Kattan, A. Universal intelligent data compression systems: A review. In Proceedings of the 2nd Computer Science and Electronic Engineering Conference (CEEC), Colchester, UK, 8–9 September 2010; pp. 1–10. [Google Scholar]
- Cristiano, M.; Ivanil, A.; Bonatti, S.; Peres, P.L.D. Adaptive Run Length Encoding method for the compression of electrocardiograms. Med. Eng. Phys. 2013, 35, 145–153. [Google Scholar]
- David, A.; Maluf, P.; Tran, B.; Tran, D. Effective Data Representation and Compression in Ground Data Systems. In Proceedings of the IEEE Aerospace Conference, Big Sky, MT, USA, 1–8 March 2008; pp. 1–7. [Google Scholar]
- Qian, S.-E.; Bergeron, M.; Cunningham, I.; Gagnon, L.; Hollinger, A. Near lossless data compression onboard a hyperspectral satellite. IEEE Trans. Aerosp. Electron. Syst. 2006, 42, 851–866. [Google Scholar] [CrossRef]
- Kiely, A.; Klimesh, M. The ICER Progressive Wavelet Image Compressor. IPN Prog. Rep. 2003, 42, 14–46. [Google Scholar]
- Logeswaran, R. Fast Two-Stage Lempel-Ziv Lossless Numeric Telemetry Data Compression Using a Neural Network Predictor. J. Univers. Comput. Sci. 2004, 10, 1199–1211. [Google Scholar]
- Rong, C.D.; Hong, L.J.; Yong, Z.G. Algorithm design for launch vehicle telemetry data compression. J. Astronaut. 2001, 22, 12–17. [Google Scholar]
- Chan, H.L.; Siao, Y.C.; Chen, S.W. Wavelet-based ECG compression by bit-field preserving and running length encoding. Comput. Methods Programs Biomed. 2008, 90, 1–8. [Google Scholar] [CrossRef] [PubMed]
- Steinwandt, R.; Villányi, V.I. A one-time signature using run-length encoding. Inf. Process. Lett. 2008, 108, 179–185. [Google Scholar] [CrossRef]
- Stabno, M.; Wrembel, R. RLH: Bitmap compression technique based on run-length and Huffman encoding. Inf. Syst. 2009, 34, 400–414. [Google Scholar] [CrossRef]
- Korpela, E.; Forsten, J.; Hamalainen, A.; Ruoskanen, J.; Eskelinen, P. A Hardware Signal Processing Platform for Sensor Systems. IEEE Aerosp. Electron. Syst. Mag. 2006, 21, 22–25. [Google Scholar] [CrossRef]
- Nunez, J.; Jones, S. Lossless data compression programmable hardware for high-speed data networks. In Proceedings of the IEEE International Conference on Field-Programmable Technology, Hong Kong, China, 16–18 December 2002; pp. 290–293. [Google Scholar] [CrossRef]
- Kao, C.-F.; Huang, S.-M.; Huang, I.-J. A Hardware Approach to Real-Time Program Trace Compression for Embedded Processors. IEEE Trans. Circuits Syst. I: Regul. Pap. 2007, 54, 530–543. [Google Scholar] [CrossRef]
- Hashempour, H.; Lombardi, F. Application of Arithmetic Coding to Compression of VLSI Test Data. IEEE Trans. Comput. 2005, 54, 1166–1177. [Google Scholar] [CrossRef]
- Lam, S.M.I.; Fahmy, S. Energy-efficient provenance transmission in large-scale wireless sensor networks. In Proceedings of the 2011 IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networksm, Lucca, Italy, 20–24 June 2011; pp. 1–6. [Google Scholar]
- Wang, Y.C. Data compression techniques in wireless sensor networks. Pervasive Comput. 2012, 61, 75–77. [Google Scholar]
- Capo-Chichi, E.P.; Guyennet, H.; Friedt, J. K-RLE: A New Data Compression Algorithm for Wireless Sensor Network. In Proceedings of the 2009 Third International Conference on Sensor Technologies and Applications, Athens, Greece, 18–23 June 2009; pp. 502–507. [Google Scholar] [CrossRef]
- Salomon, D. Data Compression: The Complete Reference; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2004. [Google Scholar]
- Sayood, K. Introduction to Data Compression, 5th ed.; Morgan Kaufmann: Burlington, MA, USA, 2006; pp. 58–65. [Google Scholar]
- Razzaque, M.A.; Bleakley, C.; Dobson, S. Compression in wireless sensor networks: A survey and comparative evaluation. ACM Trans. Sens. Netw. (TOSN) 2013, 10, 1–44. [Google Scholar] [CrossRef]
- Labelled Wireless Sensor Network Data Repository (LWSNDR). Available online: https://home.uncg.edu/cmp/downloads/lwsndr.html (accessed on 20 June 2022).
- Abu Alsheikh, M.; Lin, S.; Niyato, D.; Tan, H.-P. Rate-Distortion Balanced Data Compression for Wireless Sensor Networks. IEEE Sens. J. 2016, 16, 5072–5083. [Google Scholar] [CrossRef]
- Zordan, D.; Martinez, B.; Vilajosana, I.; Rossi, M. To Compress or Not to Compress: Processing vs Transmission Tradeoffs for Energy Constrained Sensor Networking. arXiv 2021, arXiv:1206.2129v1. [Google Scholar]
- Mishra, M.; Gupta, G.S.; Gui, X. Network Lifetime Improvement through Energy-Efficient Hybrid Routing Protocol for IoT Applications. Sensors 2021, 21, 7439. [Google Scholar] [CrossRef] [PubMed]
- Ali, R. Elliptic curve cryptography a new way for encryption. In Proceedings of the 2008 International Symposium on Biometrics and Security Technologies, Isalambad, Pakistan, 23–24 April 2008; pp. 1–5. [Google Scholar]
- Tawalbeh, L.; Mowafi, M.; Aljoby, W. Use of elliptic curve cryptography for multimedia encryption. IET Inf. Secur. 2013, 7, 67–74. [Google Scholar] [CrossRef]
- Reinhardt, A.; Christin, D.; Hollick, M.; Steinmetz, R. On the energy efficiency of lossless data compression in wireless sensor networks. In Proceedings of the 34th Conference on Local Computer Networks, Zurich, Switzerland, 20–23 October 2009; pp. 873–880. [Google Scholar] [CrossRef]
- Giorgi, G. A Combined Approach for Real-Time Data Compression in Wireless Body Sensor Networks. IEEE Sens. J. 2017, 17, 6129–6135. [Google Scholar] [CrossRef]
- Deepu, C.J.; Heng, C.-H.; Lian, Y. A Hybrid Data Compression Scheme for Power Reduction in Wireless Sensors for IoT. IEEE Trans. Biomed. Circuits Syst. 2017, 11, 245–254. [Google Scholar] [CrossRef]
- Ghanmy, N.; Fourati, L.C.; Kamoun, L. Elliptic curve cryptography for WSN and SPA attacks method for energy evaluation. J. Netw. 2014, 9, 2943–2950. [Google Scholar] [CrossRef]
- Wang, C.-H.; Hu, H.-S.; Zhang, Z.-G.; Guo, Y.-X.; Zhang, J.-F. Distributed energy-efficient clustering routing protocol for wireless sensor networks using affinity propagation and fuzzy logic. Soft Comput. 2022, 26, 7143–7158. [Google Scholar] [CrossRef]
- Rodríguez, A.; Del-Valle-Soto, C.; Velázquez, R. Energy-Efficient Clustering Routing Protocol for Wireless Sensor Networks Based on Yellow Saddle Goatfish Algorithm. Mathematics 2020, 8, 1515. [Google Scholar] [CrossRef]
- Ketshabetswe, K.L.; Zungeru, A.M.; Mtengi, B.; Lebekwe, C.K.; Prabaharan, S.R.S. Data Compression Algorithms for Wireless Sensor Networks: A Review and Comparison. IEEE Access 2021, 9, 136872–136891. [Google Scholar] [CrossRef]




| Parameter | Description |
|---|---|
| Din | A sequence of sensor data |
| Pk | Packet size |
| NYT | Not Yet Transmitted |
| Rcode | Repeat count in RLE |
| Length | Length of the stream |
| Unique | Unique data in the stream |
| Final stream | Output stream packet |
| Loc | Location of the Pointer |
| Info () | Information about the node |
| Operations | Number of CPU Cycles |
|---|---|
| Addition | 184 |
| Subtraction | 177 |
| Multiplication | 395 |
| Division | 405 |
| Comparison | 37 |
| Base station location | 2 × 4, 100 nodes (Centre, left edge, top edge and corner) 4 × 4, 100 nodes 4 × 4, 200 nodes (Centre, left edge, top edge and corner) 10 × 10, 625 nodes 10 × 10, 1250 nodes |
| Number of Rounds | 1500 rounds |
| Case Study | Network Area | Number of Grids | Total Number of Nodes |
|---|---|---|---|
| 1 | 100 m × 100 m | 2 × 4 | 100 |
| 2 | 100 m × 100 m | 4 × 4 | 100 |
| 3 | 200 m × 200 m | 4 × 4 | 200 |
| 4 | 500 m × 500 m | 10 × 10 | 650 |
| 5 | 500 m × 500 m | 10 × 10 | 1250 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mishra, M.; Sen Gupta, G.; Gui, X. Investigation of Energy Cost of Data Compression Algorithms in WSN for IoT Applications. Sensors 2022, 22, 7685. https://doi.org/10.3390/s22197685
Mishra M, Sen Gupta G, Gui X. Investigation of Energy Cost of Data Compression Algorithms in WSN for IoT Applications. Sensors. 2022; 22(19):7685. https://doi.org/10.3390/s22197685
Chicago/Turabian StyleMishra, Mukesh, Gourab Sen Gupta, and Xiang Gui. 2022. "Investigation of Energy Cost of Data Compression Algorithms in WSN for IoT Applications" Sensors 22, no. 19: 7685. https://doi.org/10.3390/s22197685
APA StyleMishra, M., Sen Gupta, G., & Gui, X. (2022). Investigation of Energy Cost of Data Compression Algorithms in WSN for IoT Applications. Sensors, 22(19), 7685. https://doi.org/10.3390/s22197685






