In-Vehicle Communication Cyber Security: Challenges and Solutions
Abstract
1. Introduction
- What are the main components of in-vehicle network?
- Why there is a need to secure in-vehicle network environment?
- Which are the main approaches for securing the in-vehicle network?
- What kind of challenges exist in securing the in-vehicle network?
- Where the future research on in-vehicle cybernetics will move forward?
- In-vehicle communication network architecture is presented considering key components, interfaces, and related technologies.
- The protocols for in-vehicle communication have been classified based on their characteristics, and usage type.
- Security solutions for in-vehicle communication have been critically reviewed considering machine learning, cryptography, and port centric techniques.
- A multi-layer secure framework is also developed as a protocol and use case independent in-vehicle communication solution.
- Finally, open challenges, and future dimension of research for in-vehicle communication cyber security is highlighted as observation and recommendation.
2. Architecture and Components of In-Vehicular System
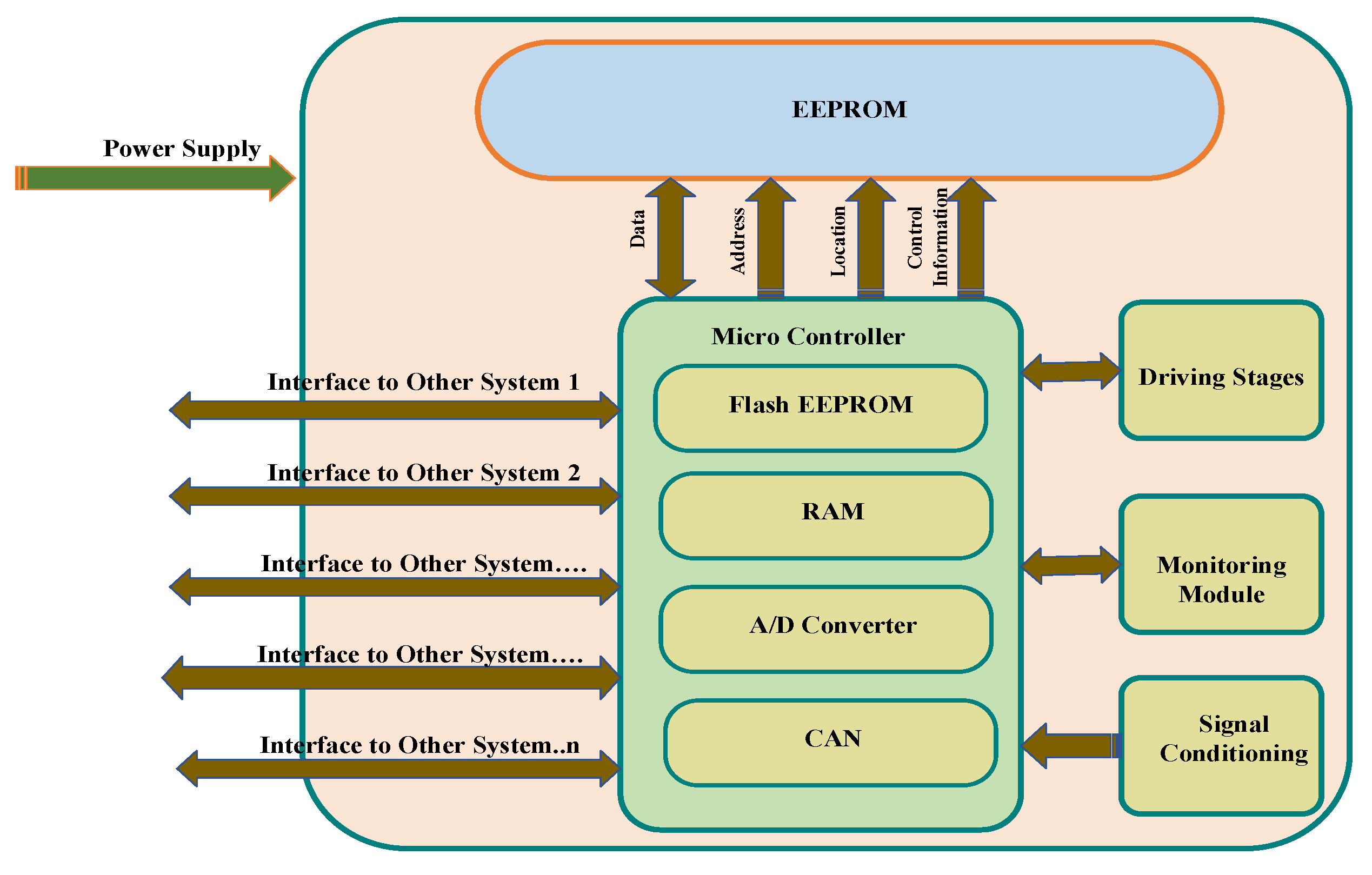
2.1. Internal Configuration of Electronic Control Units
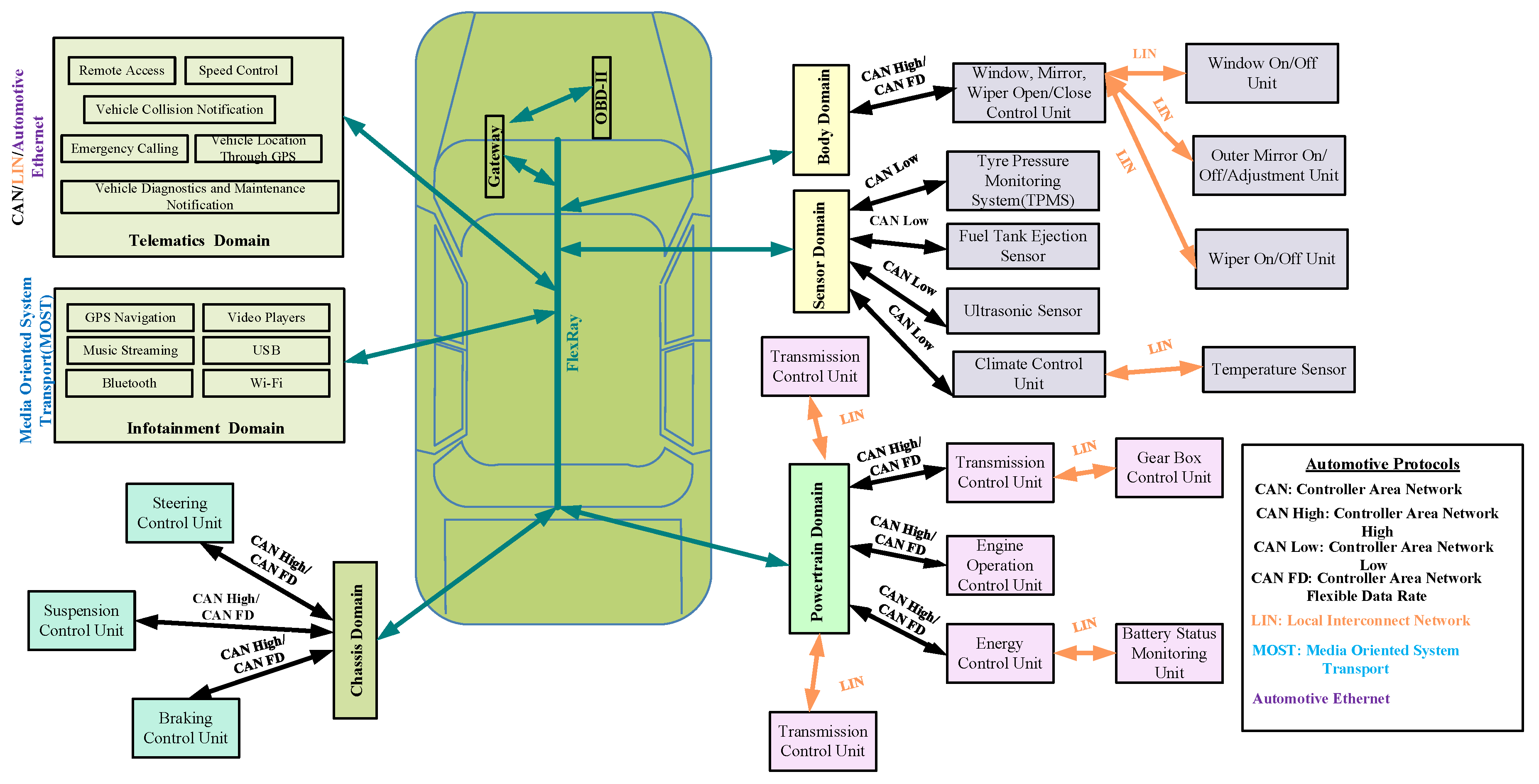
2.2. In-Vehicle Network Architecture
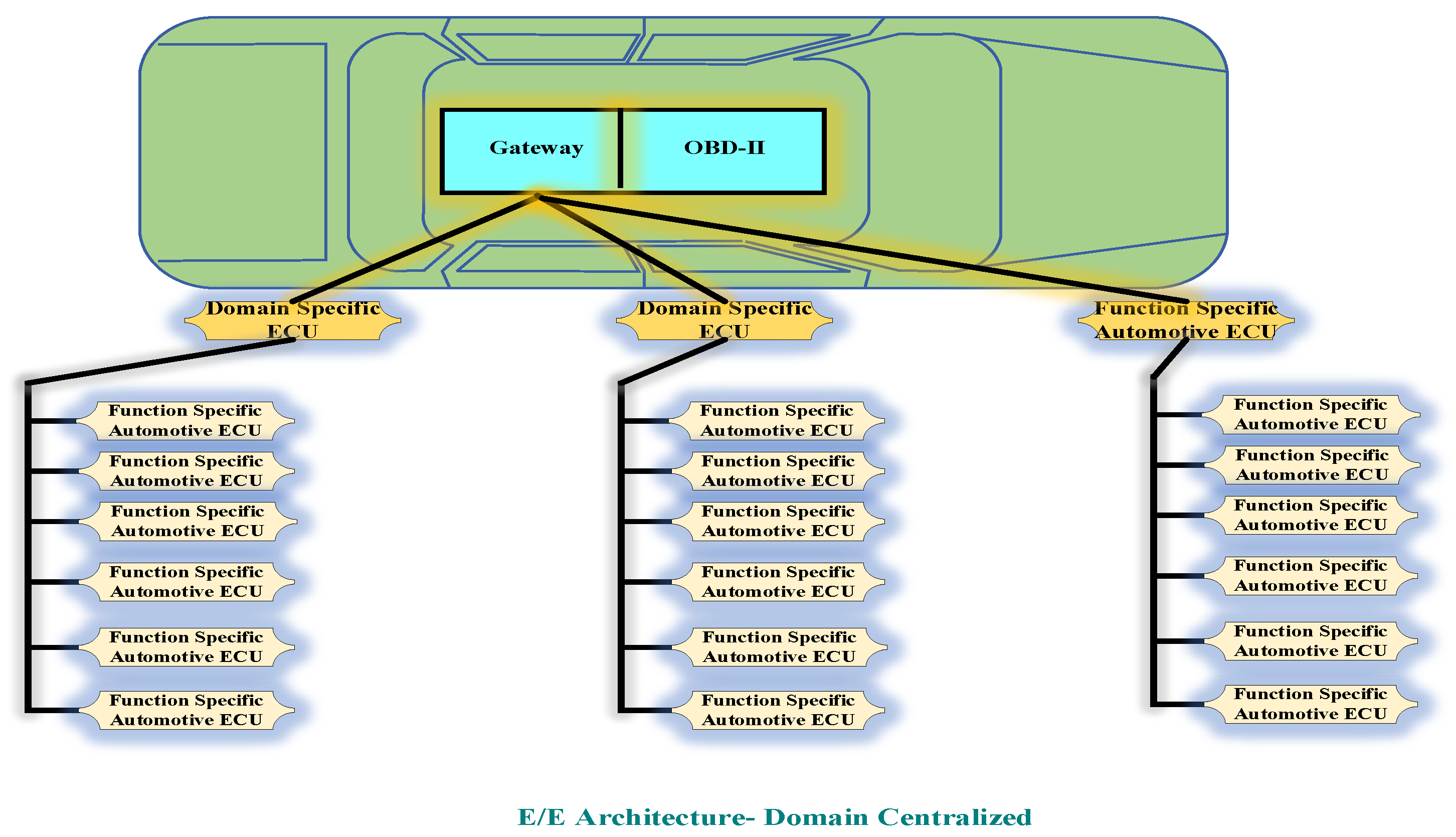
2.3. Classification of In-Vehicle Network Architecture
3. Classifications and Characteristics of In-Vehicle Automotive Protocols
3.1. Controller Area Network (CAN)
3.2. Local Interconnect Network (LIN)
3.3. FlexRay Protocol
3.4. Media-Oriented Systems Transport (MOST)
3.5. Automotive Ethernet
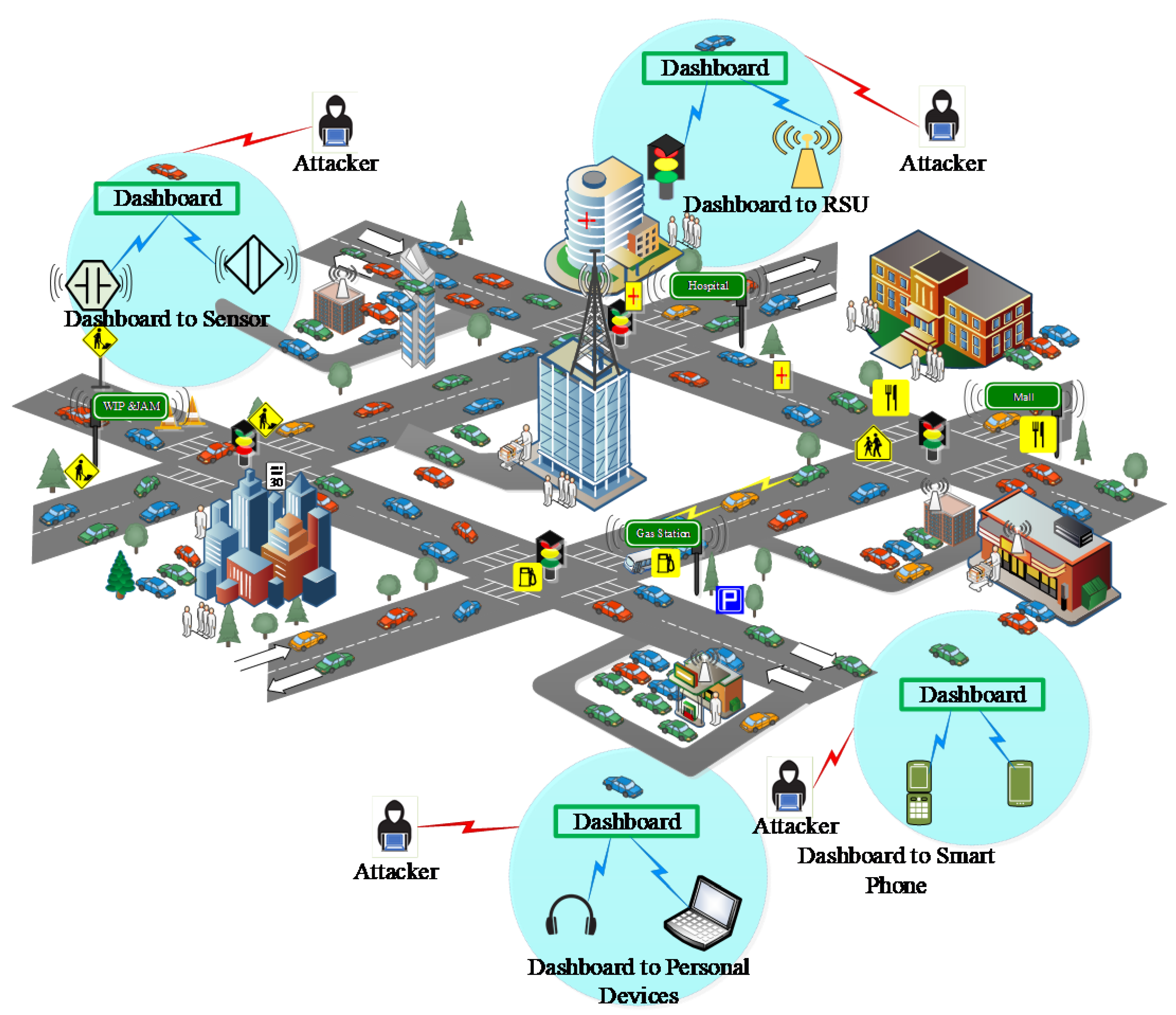
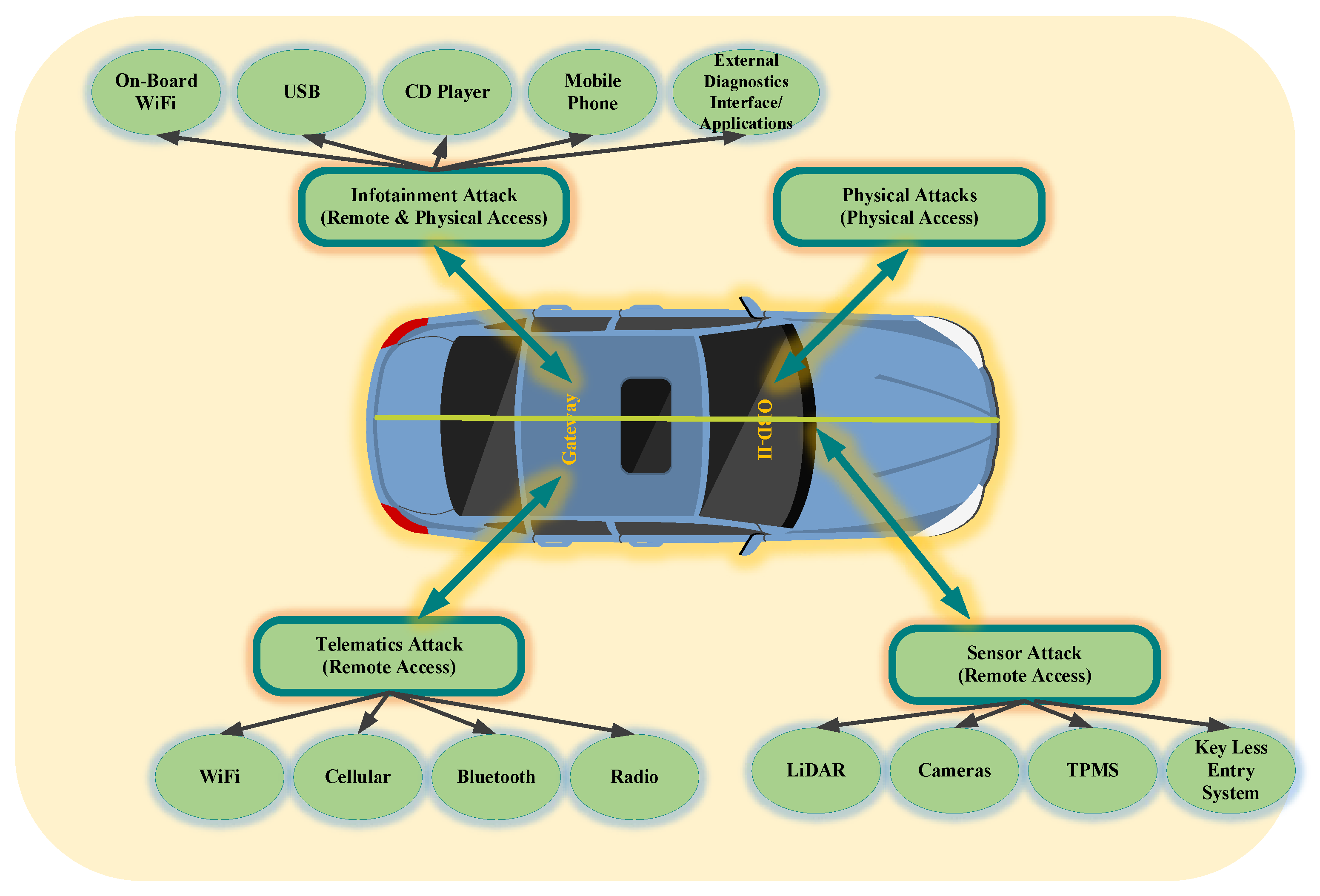
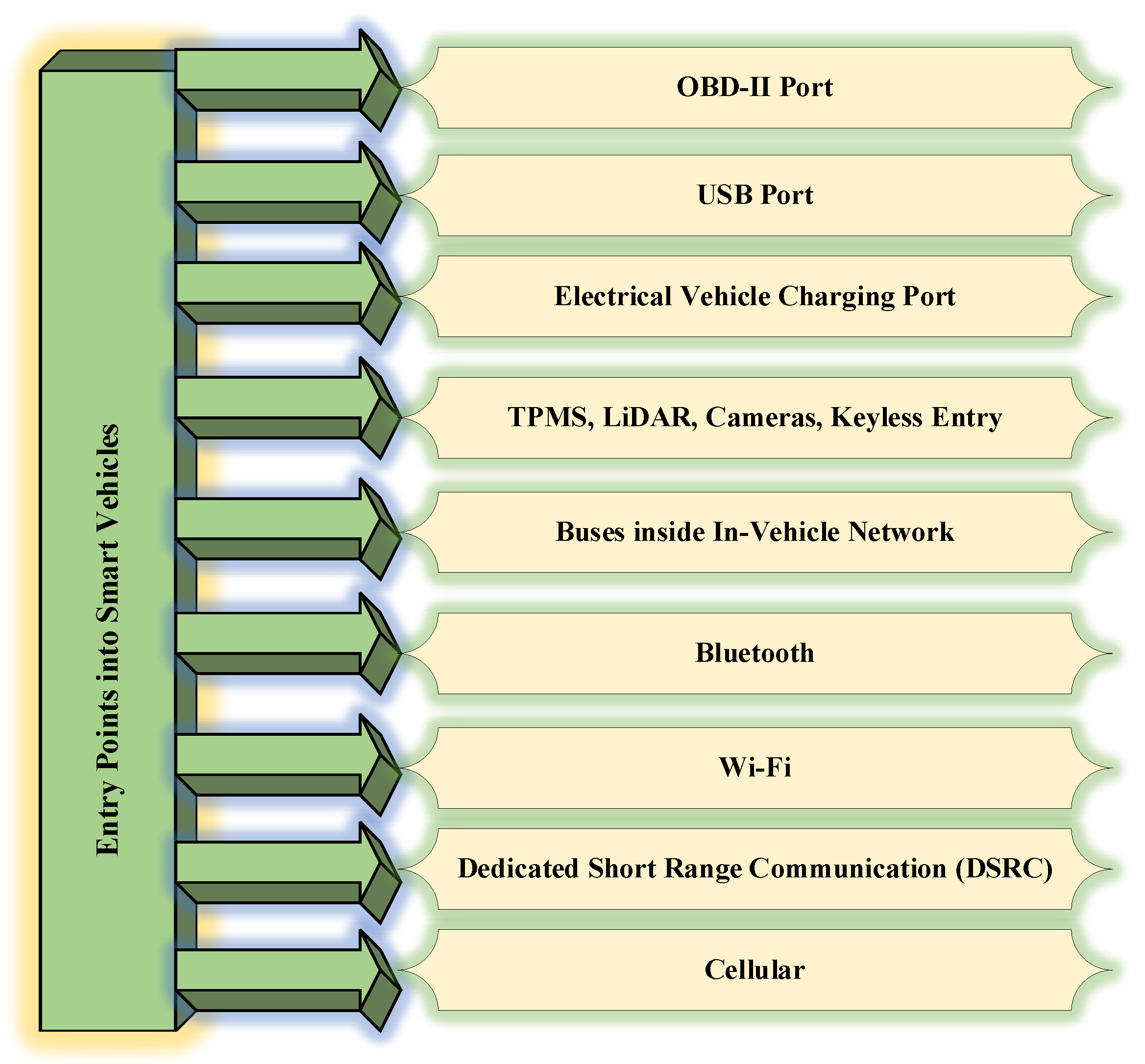
4. Classification of Attacks on In-Vehicle Network System for Possible Entry Points
4.1. Entry points to Smart Vehicles
4.1.1. OBD-II Port
4.1.2. USB and Charging Ports
4.1.3. Tire Pressure Monitoring System (TPMS), LiDAR and Keyless Entry Ports
4.1.4. Buse Network Ports
4.1.5. Vehicular Communication Ports
4.2. Corrective Mechanisms to Port Threats
5. Comprehensive Survey of Security Solutions for In-Vehicle Network
5.1. Related Existing Surveys
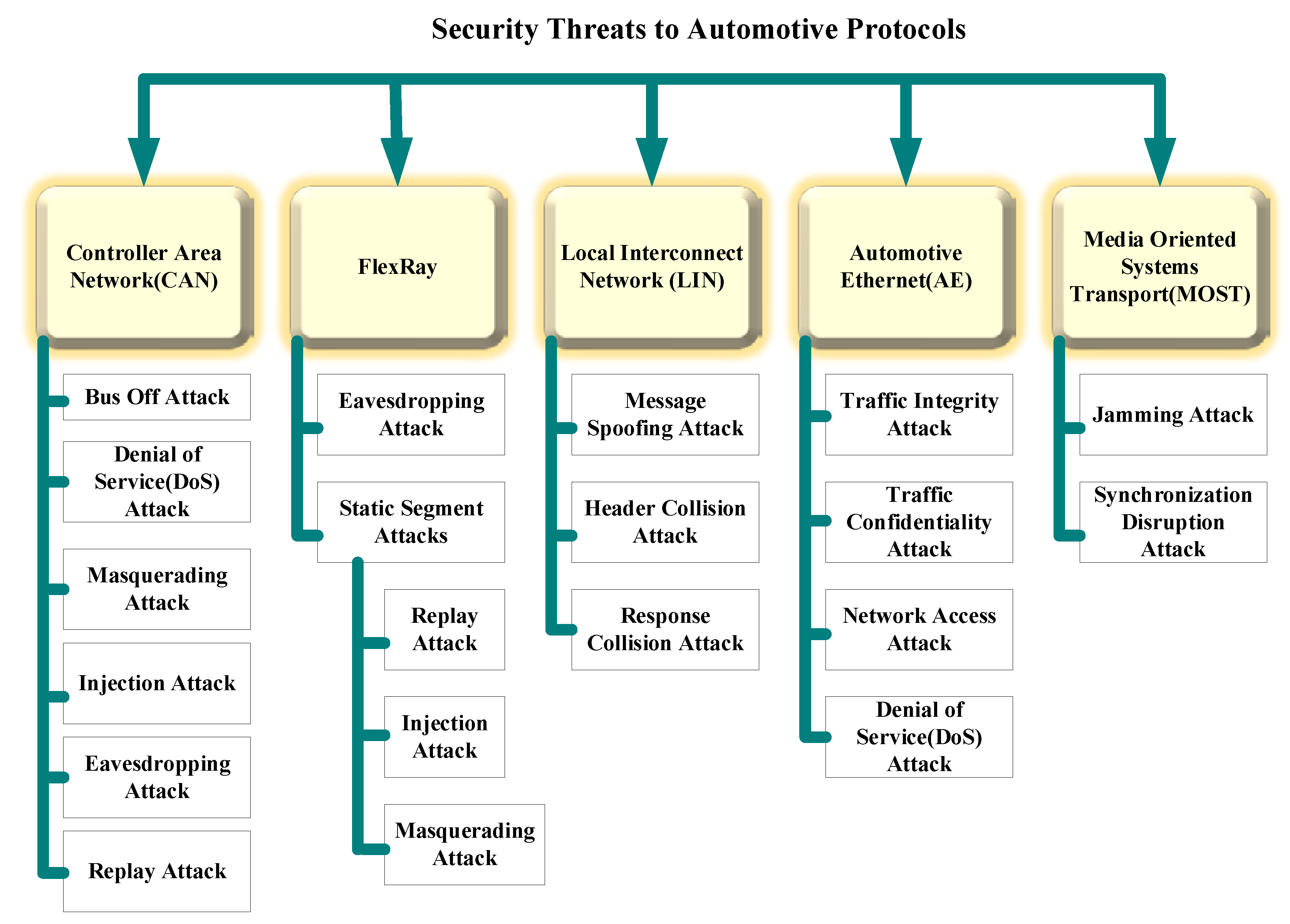
5.2. Security Threats to In-Vehicular Protocols and Countermeasures
5.2.1. CAN-Centric Security Threats
Survey of Security Solutions Based on Machine Learning Algorithms
Survey of Security Solutions Based on Cryptography Techniques
5.2.2. Security Threats—FlexRay
5.2.3. Security Threats—Local Interconnect Network (LIN)
5.2.4. Security Threats—Automotive Ethernet (AE)
5.2.5. Security Threats—Media-Oriented Systems Transport (MOST)
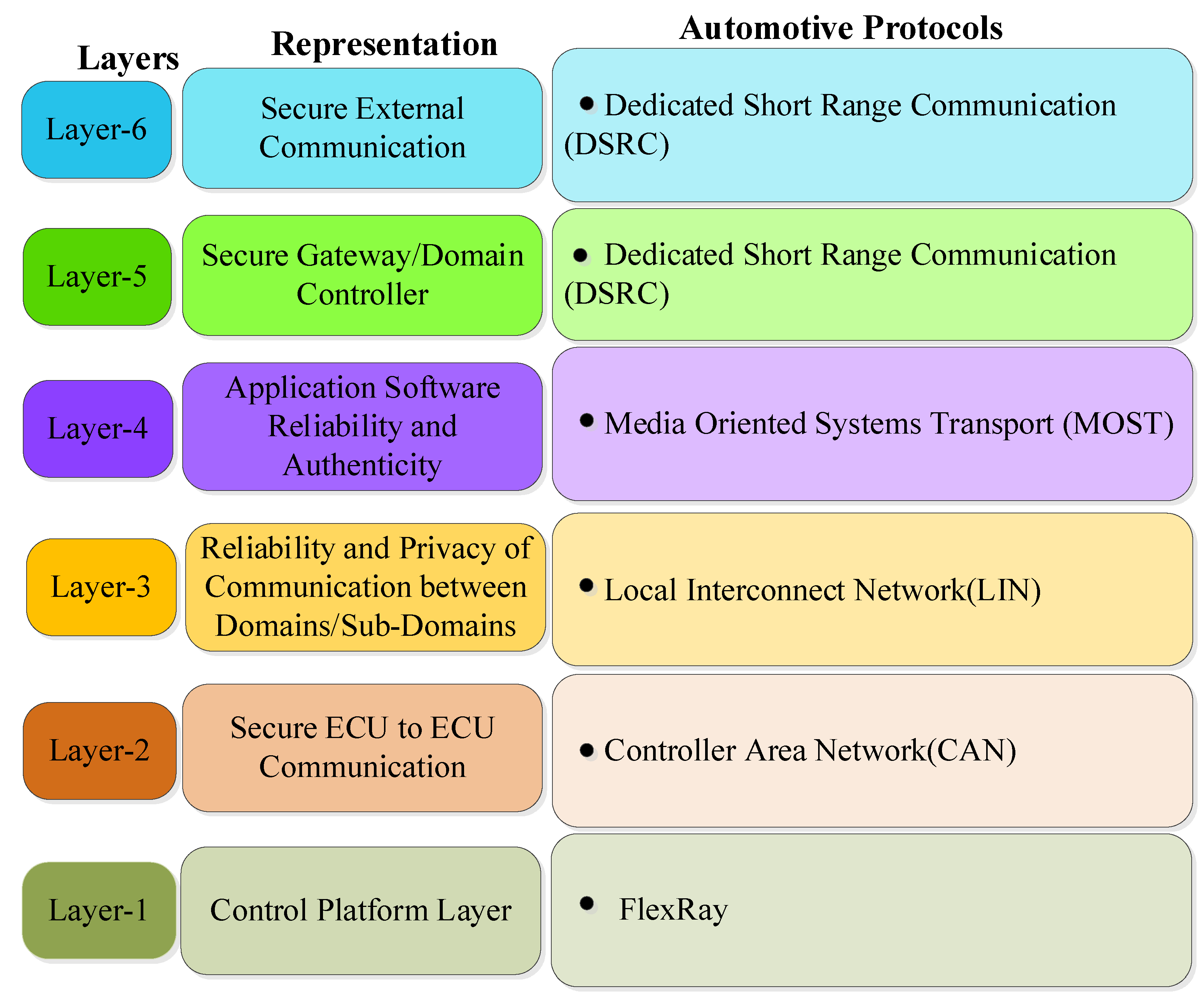
6. Multi-Layered Security Framework
6.1. Control Platform Layer
6.2. Secure ECU to ECU Communication in In-Vehicle Network
6.3. Reliability and Privacy of Communication between Domains/Sub-Domains in In-Vehicle Network
- ○
- Message authentication system: Cryptographic certificate is used to ensure an authenticated sender and message integrity. This certificate is added to all messages in the network.
- ○
- Encryption: Messages are encrypted inside the vehicles to guard against loss of data and identity theft since messages are distributed with several different ECUs.
- ○
- Detection of intrusion: The corrective mechanism should use the cryptographic accelerators and security subsystems integrated with the microcontroller to guard against threats.
- ○
- Validation at ECU level: In the vehicle network, ECU’s validity is checked first at the start of the engine and also afterwards at specified time intervals.
6.4. Application Software Reliability and Authenticity
6.5. Secure Gateway /Domain Controller
6.6. Secure External Communication
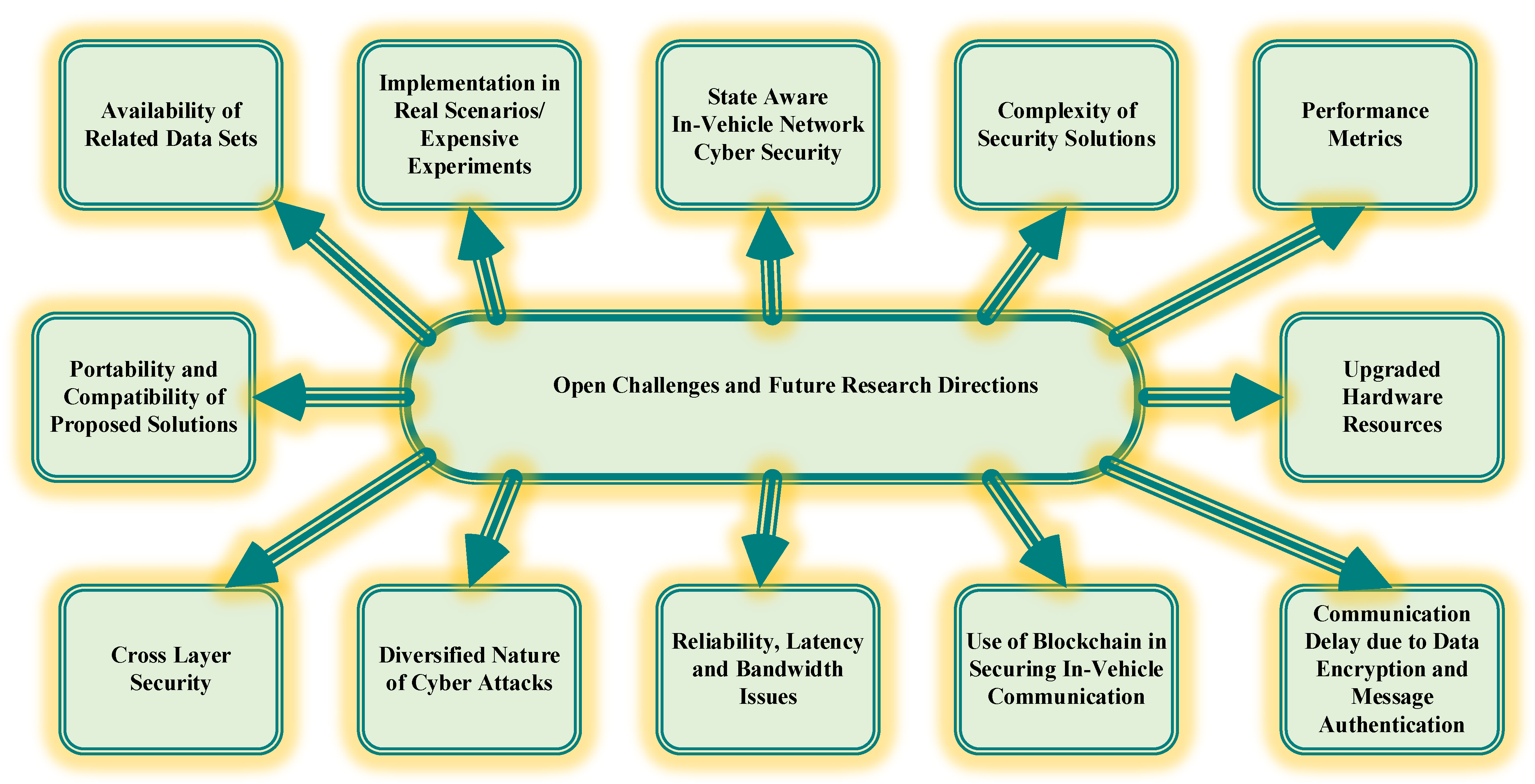
7. Open Challenges and Future Research Directions
7.1. Availability of Related Data Sets
7.2. Implementation in Real Scenarios/Expensive Experiments
7.3. State Aware In-Vehicle Network Cyber Security
7.4. The Complexity of Security Solutions
7.5. Performance Metrics
7.6. Portability and Compatibility of Proposed Solutions
7.7. Upgraded Hardware Resources
7.8. Cross-Layer Security
7.9. Diversified Nature of Cyber Attacks
7.10. Use of Blockchain in Securing In-Vehicle Communication
7.11. Reliability, Latency and Bandwidth Issues
7.12. Communication Delay Due to Data encryption and Message Authentication
8. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Kaiwartya, O.; Abdullah, A.H.; Cao, Y.; Altameem, A.; Prasad, M.; Lin, C.T.; Liu, X. Internet of vehicles: Motivation, layered architecture, network model, challenges, and future aspects. IEEE Access 2016, 4, 5356–5373. [Google Scholar] [CrossRef]
- Song, H.M.; Kim, H.K. Self-supervised anomaly detection for in-vehicle network using noised pseudo normal data. IEEE Trans. Veh. Technol. 2021, 70, 1098–1108. [Google Scholar] [CrossRef]
- Kang, S.; Seong, J.; Lee, M. Controller area network with flexible data rate transmitter design with low electromagnetic emission. IEEE Trans. Veh. Technol. 2018, 67, 7290–7298. [Google Scholar] [CrossRef]
- Lee, Y.S.; Kim, J.H.; Jeon, J.W. FlexRay and Ethernet AVB synchronization for high QoS automotive gateway. IEEE Trans. Veh. Technol. 2016, 66, 5737–5751. [Google Scholar] [CrossRef]
- Kong, W.; Luo, Y.; Qin, Z.; Qi, Y.; Lian, X. Comprehensive fault diagnosis and fault-tolerant protection of in-vehicle intelligent electric power supply network. IEEE Trans. Veh. Technol. 2019, 68, 10453–10464. [Google Scholar] [CrossRef]
- Zhang, L.; Yang, F.; Lei, Y. Tree-based intermittent connection fault diagnosis for controller area network. IEEE Trans. Veh. Technol. 2019, 68, 9151–9161. [Google Scholar] [CrossRef]
- Iorio, M.; Reineri, M.; Risso, F.; Sisto, R.; Valenza, F. Securing SOME/IP for in-vehicle service protection. IEEE Trans. Veh. Technol. 2020, 69, 13450–13466. [Google Scholar] [CrossRef]
- Choi, W.; Jo, H.J.; Woo, S.; Chun, J.Y.; Park, J.; Lee, D.H. Identifying ecus using inimitable characteristics of signals in controller area networks. IEEE Trans. Veh. Technol. 2018, 67, 4757–4770. [Google Scholar] [CrossRef]
- Jeong, W.; Han, S.; Choi, E.; Lee, S.; Choi, J.W. CNN-based adaptive source node identifier for controller area network (CAN). IEEE Trans. Veh. Technol. 2020, 69, 13916–13920. [Google Scholar] [CrossRef]
- Xie, G.; Yang, L.T.; Liu, Y.; Luo, H.; Peng, X.; Li, R. Security enhancement for real-time independent in-vehicle CAN-FD messages in vehicular networks. IEEE Trans. Veh. Technol. 2021, 70, 5244–5253. [Google Scholar] [CrossRef]
- Kaiwartya, O.; Kumar, S. Cache agent-based geocasting in VANETs. Int. J. Inf. Commun. Technol. 2015, 7, 562–584. [Google Scholar] [CrossRef]
- Moulahi, T.; Zidi, S.; Alabdulatif, A.; Atiquzzaman, M. Comparative Performance Evaluation of Intrusion Detection Based on Machine Learning in In-Vehicle Controller Area Network Bus. IEEE Access 2021, 9, 99595–99605. [Google Scholar] [CrossRef]
- Zhang, L.; Ma, D. A Hybrid Approach Toward Efficient and Accurate Intrusion Detection for In-Vehicle Networks. IEEE Access 2022, 10, 10852–10866. [Google Scholar] [CrossRef]
- Kumar, S.; Singh, K.; Kumar, S.; Kaiwartya, O.; Cao, Y.; Zhou, H. Delimitated anti jammer scheme for Internet of vehicle: Machine learning based security approach. IEEE Access 2019, 7, 113311–113323. [Google Scholar] [CrossRef]
- He, Y.; Jia, Z.; Hu, M.; Cui, C.; Cheng, Y.; Yang, Y. The Hybrid Similar Neighborhood Robust Factorization Machine Model for Can Bus Intrusion Detection in the In-Vehicle Network. IEEE Trans. Intell. Transp. Syst. 2021, 1, 1–9. [Google Scholar] [CrossRef]
- Lo, W.; Alqahtani, H.; Thakur, K.; Almadhor, A.; Chander, S.; Kumar, G. A hybrid deep learning based intrusion detection system using spatial-temporal representation of in-vehicle network traffic. Veh. Commun. 2022, 35, 100471. [Google Scholar] [CrossRef]
- Carvajal-Roca, I.E.; Wang, J.; Du, J.; Wei, S. A Semi-Centralized Dynamic Key Management Framework for In-Vehicle Networks. IEEE Trans. Veh. Technol. 2021, 70, 10864–10879. [Google Scholar] [CrossRef]
- Kohnhäuser, F.; Püllen, D.; Katzenbeisser, S. May. Ensuring the safe and secure operation of electronic control units in road vehicles. In Proceedings of the 2019 IEEE Security and Privacy Workshops (SPW), San Francisco, CA, USA, 19–23 May 2019; pp. 126–131. [Google Scholar]
- Walrand, J.; Turner, M.; Myers, R. An architecture for in-vehicle networks. IEEE Trans. Veh. Technol. 2021, 70, 6335–6342. [Google Scholar] [CrossRef]
- Apostu, S.; Burkacky, O.; Deichmann, J.; Doll, G. Automotive Software and Electrical/Electronic Architecture: Implications for OEMs. 2019. Available online: https://www.mckinsey.com/industries/automotive-and-assembly/our-insights/automotive-software-andelectrical-electronic-architecture-implications-for-oems (accessed on 16 July 2022).
- Jiang, S. Vehicle e/e Architecture and Its Adaptation to New Technical Trends; Technical Report; SAE Technical Paper: Warrendale, PA, USA, 2019. [Google Scholar]
- Zerfowski, D.; Lock, A. Functional Architecture and E/E-Architecture–A Challenge for the Automotive Industry. In 19. Internationales Stuttgarter Symposium; Springer: Berlin/Heidelberg, Germany, 2019; pp. 909–920. [Google Scholar]
- Butzkamm, C.; Brand, K. E/E Architecture in the HARRI Innovation Platform. Atzelektronik Worldw. 2020, 15, 18–24. [Google Scholar] [CrossRef]
- Freddie Holmes, J.H.; Moreton, J. Zonal E/E Architectures the Cornerstone of Future Mobility Development. 2021. Available online: https://www.automotiveworld.com/articles/zonal-e-e-architectures-the-cornerstone-of-future-mobility-development (accessed on 15 July 2022).
- Bandur, V.; Selim, G.; Pantelic, V.; Lawford, M. Making the case for centralized automotive e/e architectures. IEEE Trans. Veh. Technol. 2021, 70, 1230–1245. [Google Scholar] [CrossRef]
- Di Natale, M.; Zeng, H.; Giusto, P.; Ghosal, A. Understanding and Using the Controller Area Network Communication Protocol: Theory and Practice; Springer Science & Business Media: Berlin, Germany, 2012. [Google Scholar]
- Ruff, M. October. Evolution of local interconnect network (LIN) solutions. In Proceedings of the 2003 IEEE 58th Vehicular Technology Conference. VTC 2003-Fall (IEEE Cat. No. 03CH37484), Orlando, FL, USA, 6–9 October 2003; Volume 5, pp. 3382–3389. [Google Scholar]
- Shaw, R.; Jackman, B. An introduction to FlexRay as an industrial network. In Proceedings of the 2008 IEEE International Symposium on Industrial Electronics, Cambridge, UK, 30 June 2008–2 July 2008; pp. 1849–1854. [Google Scholar]
- Sumorek, A.; Buczaj, M. New elements in vehicle communication “media oriented systems transport” protocol. Teka Kom. Motoryz. I Energetyki Rol. 2012, 12, 275–279. [Google Scholar]
- Hank, P.; Müller, S.; Vermesan, O.; Van Den Keybus, J. Automotive ethernet: In-vehicle networking and smart mobility. In Proceedings of the 2013 Design, Automation & Test in Europe Conference & Exhibition, Grenoble, France, 18–22 March 2013; pp. 1735–1739. [Google Scholar]
- Klinedinst, D.; King, C. On Board Diagnostics: Risks and Vulnerabilities of the Connected Vehicle; CERT Coordination Center: Pittsburgh, PA, USA, 2016. [Google Scholar]
- Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; Savage, S.; Koscher, K.; Czeskis, A.; Roesner, F.; Kohno, T. Comprehensive experimental analyses of automotive attack surfaces. In Proceedings of the 20th USENIX Security Symposium (USENIX Security 11), San Francisco, CA, USA, 10–12 August 2011. [Google Scholar]
- Gottumukkala, R.; Merchant, R.; Tauzin, A.; Leon, K.; Roche, A.; Darby, P. Cyber-physical system security of vehicle charging stations. In Proceedings of the 2019 IEEE Green Technologies Conference (GreenTech), Lafayette, LA, USA, 3–6 April 2019; pp. 1–5. [Google Scholar]
- Cao, Y.; Xiao, C.; Cyr, B.; Zhou, Y.; Park, W.; Rampazzi, S.; Chen, Q.A.; Fu, K.; Mao, Z.M. Adversarial sensor attack on lidar-based perception in autonomous driving. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 2267–2281. [Google Scholar]
- Miller, C.; Valasek, C. Adventures in automotive networks and control units. Def. Con. 2013, 21, 15–31. [Google Scholar]
- Li, X.; Yu, Y.; Sun, G.; Chen, K. Connected vehicles’ security from the perspective of the in-vehicle network. IEEE Netw. 2018, 32, 58–63. [Google Scholar] [CrossRef]
- Nakhila, O.; Dondyk, E.; Amjad, M.F.; Zou, C. User-side wi-fi evil twin attack detection using ssl/tcp protocols. In Proceedings of the 2015 12th Annual IEEE Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2015; pp. 239–244. [Google Scholar]
- Wu, X.; Subramanian, S.; Guha, R.; White, R.G.; Li, J.; Lu, K.W.; Bucceri, A.; Zhang, T. Vehicular communications using DSRC: Challenges, enhancements, and evolution. IEEE J. Sel. Areas Commun. 2013, 31, 399–408. [Google Scholar]
- Ivanov, I.; Maple, C.; Watson, T.; Lee, S. Cyber security standards and issues in V2X communications for Internet of Vehicles. In Proceedings of the Living in the Internet of Things: Cybersecurity of the IoT—2018, London, UK, 28–29 March 2018. [Google Scholar]
- Kim, S.; Shrestha, R. In-vehicle communication and cyber security. In Automotive Cyber Security; Springer: Gateway East, Singapore, 2020; pp. 67–96. [Google Scholar]
- Zeng, W.; Khalid, M.A.; Chowdhury, S. In-vehicle networks outlook: Achievements and challenges. IEEE Commun. Surv. Tutor. 2016, 18, 1552–1571. [Google Scholar] [CrossRef]
- Nowdehi, N.; Lautenbach, A.; Olovsson, T. In-vehicle CAN message authentication: An evaluation based on industrial criteria. In Proceedings of the 2017 IEEE 86th Vehicular Technology Conference (VTC-Fall), Toronto, ON, Canada, 24–27 September 2017; pp. 1–7. [Google Scholar]
- Groza, B.; Murvay, P.S. Security solutions for the controller area network: Bringing authentication to in-vehicle networks. IEEE Veh. Technol. Mag. 2018, 13, 40–47. [Google Scholar] [CrossRef]
- Avatefipour, O.; Malik, H. State-of-the-art survey on in-vehicle network communication (CAN-Bus) security and vulnerabilities. arXiv 2018, 1802, 01725. [Google Scholar]
- Bozdal, M.; Samie, M.; Jennions, I. A survey on can bus protocol: Attacks, challenges, and potential solutions. In Proceedings of the 2018 International Conference on Computing, Electronics & Communications Engineering (iCCECE), Southend, UK, 16–17 August 2018; pp. 201–205. [Google Scholar]
- Tomlinson, A.; Bryans, J.; Shaikh, S.A. September. Towards viable intrusion detection methods for the automotive controller area network. In Proceedings of the 2nd ACM Computer Science in Cars Symposium, Munich, Germany, 13–14 September 2018; pp. 1–9. [Google Scholar]
- Le, V.H.; den Hartog, J.; Zannone, N. Security and privacy for innovative automotive applications: A survey. Comput. Commun. 2018, 132, 17–41. [Google Scholar] [CrossRef]
- Young, C.; Zambreno, J.; Olufowobi, H.; Bloom, G. Survey of automotive controller area network intrusion detection systems. IEEE Des. Test 2019, 36, 48–55. [Google Scholar] [CrossRef]
- Gmiden, M.; Gmiden, M.H.; Trabelsi, H. Cryptographic and Intrusion Detection System for automotive CAN bus: Survey and contributions. In Proceedings of the 2019 16th International Multi-Conference on Systems, Signals & Devices (SSD), Istanbul, Turkey, 21–24 March 2019; pp. 158–163. [Google Scholar]
- Wu, W.; Li, R.; Xie, G.; An, J.; Bai, Y.; Zhou, J.; Li, K. A survey of intrusion detection for in-vehicle networks. IEEE Trans. Intell. Transp. Syst. 2019, 21, 919–933. [Google Scholar] [CrossRef]
- Lokman, S.F.; Othman, A.T.; Abu-Bakar, M.H. Intrusion detection system for automotive Controller Area Network (CAN) bus system: A review. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 1–17. [Google Scholar] [CrossRef]
- Bozdal, M.; Samie, M.; Aslam, S.; Jennions, I. Evaluation of can bus security challenges. Sensors 2020, 20, 2364. [Google Scholar] [CrossRef] [PubMed]
- El-Rewini, Z.; Sadatsharan, K.; Selvaraj, D.F.; Plathottam, S.J.; Ranganathan, P. Cybersecurity challenges in vehicular communications. Veh. Commun. 2020, 23, 100214. [Google Scholar] [CrossRef]
- Sun, X.; Yu, F.R.; Zhang, P. A survey on cyber-security of connected and autonomous vehicles (CAVs). IEEE Trans. Intell. Transp. Syst. 2021, 23, 6240–6259. [Google Scholar] [CrossRef]
- Karopoulos, G.; Kambourakis, G.; Chatzoglou, E.; Hernández-Ramos, J.L.; Kouliaridis, V. Demystifying In-Vehicle Intrusion Detection Systems: A Survey of Surveys and a Meta-Taxonomy. Electronics 2022, 11, 1072. [Google Scholar] [CrossRef]
- Choi, W.; Joo, K.; Jo, H.J.; Park, M.C.; Lee, D.H. Voltageids: Low-level communication characteristics for automotive intrusion detection system. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2114–2129. [Google Scholar] [CrossRef]
- Carsten, P.; Andel, T.R.; Yampolskiy, M.; McDonald, J.T. In-vehicle networks: Attacks, vulnerabilities, and proposed solutions. In Proceedings of the 10th Annual Cyber and Information Security Research Conference, Oak Ridge, TN, USA, 7–9 April 2015; pp. 1–8. [Google Scholar]
- Liu, J.; Zhang, S.; Sun, W.; Shi, Y. In-vehicle network attacks and countermeasures: Challenges and future directions. IEEE Netw. 2017, 31, 50–58. [Google Scholar] [CrossRef]
- Mundhenk, P.; Steinhorst, S.; Lukasiewycz, M.; Fahmy, S.A.; Chakraborty, S. Lightweight authentication for secure automotive networks. In Proceedings of the 2015 Design, Automation & Test in Europe Conference & Exhibition (DATE), Grenoble, France, 9–13 March 2015; pp. 285–288. [Google Scholar]
- Song, H.M.; Kim, H.R.; Kim, H.K. Intrusion detection system based on the analysis of time intervals of CAN messages for in-vehicle network. In Proceedings of the 2016 International Conference on Information Networking (ICOIN), Kota Kinabalu, Malaysia, 13–15 January 2016; pp. 63–68. [Google Scholar]
- Kang, M.J.; Kang, J.W. Intrusion detection system using deep neural network for in-vehicle network security. PLoS ONE 2016, 11, e0155781. [Google Scholar] [CrossRef]
- Ghaleb, F.A.; Zainal, A.; Rassam, M.A.; Mohammed, F. An effective misbehavior detection model using artificial neural network for vehicular ad hoc network applications. In Proceedings of the 2017 IEEE Conference on Application, Information and Network Security (AINS), Miri, Malaysia, 13–14 November 2017; pp. 13–18. [Google Scholar]
- Jagielski, M.; Jones, N.; Lin, C.W.; Nita-Rotaru, C.; Shiraishi, S. Threat detection for collaborative adaptive cruise control in connected cars. In Proceedings of the 11th ACM Conference on Security & Privacy in Wireless and Mobile Networks, Stockholm, Sweden, 18–20 June 2018; pp. 184–189. [Google Scholar]
- Seo, E.; Song, H.M.; Kim, H.K. GIDS: GAN based intrusion detection system for in-vehicle network. In Proceedings of the 2018 16th Annual Conference on Privacy, Security and Trust (PST), Belfast, Ireland, 28–30 August 2018; pp. 1–6. [Google Scholar]
- Ferdowsi, A.; Challita, U.; Saad, W.; Mandayam, N.B. Robust deep reinforcement learning for security and safety in autonomous vehicle systems. In Proceedings of the 2018 21st International Conference on Intelligent Transportation Systems (ITSC), Maui, HI, USA, 4–7 November 2018; pp. 307–312. [Google Scholar]
- Zhu, K.; Chen, Z.; Peng, Y.; Zhang, L. Mobile edge assisted literal multi-dimensional anomaly detection of in-vehicle network using LSTM. IEEE Trans. Veh. Technol. 2019, 68, 4275–4284. [Google Scholar] [CrossRef]
- Eziama, E.; Jaimes, L.M.; James, A.; Nwizege, K.S.; Balador, A.; Tepe, K. Machine learning-based recommendation trust model for machine-to-machine communication. In Proceedings of the 2018 IEEE International Symposium on Signal Processing and Information Technology (ISSPIT), Louisville, KY, USA, 6–8 December 2018; pp. 1–6. [Google Scholar]
- Sherazi, H.H.R.; Iqbal, R.; Ahmad, F.; Khan, Z.A.; Chaudary, M.H. DDoS attack detection: A key enabler for sustainable communication in internet of vehicles. Sustain. Comput. Inform. Syst. 2019, 23, 13–20. [Google Scholar] [CrossRef]
- Khanapuri, E.; Chintalapati, T.; Sharma, R.; Gerdes, R. Learning-based adversarial agent detection and identification in cyber physical systems applied to autonomous vehicular platoon. In Proceedings of the 2019 IEEE/ACM 5th International Workshop on Software Engineering for Smart Cyber-Physical Systems (SEsCPS), Montreal, QC, Canada, 28–28 May 2019; pp. 39–45. [Google Scholar]
- Song, H.M.; Woo, J.; Kim, H.K. In-vehicle network intrusion detection using deep convolutional neural network. Veh. Commun. 2020, 21, 100198. [Google Scholar] [CrossRef]
- Xiao, J.; Wu, H.; Li, X. Internet of things meets vehicles: Sheltering in-vehicle network through lightweight machine learning. Symmetry 2019, 11, 1388. [Google Scholar] [CrossRef]
- Guo, J.; Li, X.; Liu, Z.; Ma, J.; Yang, C.; Zhang, J.; Wu, D. TROVE: A context-awareness trust model for VANETs using reinforcement learning. IEEE Internet Things J. 2020, 7, 6647–6662. [Google Scholar] [CrossRef]
- Katragadda, S.; Darby, P.J.; Roche, A.; Gottumukkala, R. Detecting low-rate replay-based injection attacks on in-vehicle networks. IEEE Access 2020, 8, 54979–54993. [Google Scholar] [CrossRef]
- Rasheed, I.; Hu, F.; Zhang, L. Deep reinforcement learning approach for autonomous vehicle systems for maintaining security and safety using LSTM-GAN. Veh. Commun. 2020, 26, 100266. [Google Scholar] [CrossRef]
- Lin, Y.; Chen, C.; Xiao, F.; Avatefipour, O.; Alsubhi, K.; Yunianta, A. An Evolutionary Deep Learning Anomaly Detection Framework for In-Vehicle Networks—CAN Bus. IEEE Trans. Ind. Appl. 2020, 1, 1–14. [Google Scholar] [CrossRef]
- Hossain, M.D.; Inoue, H.; Ochiai, H.; Fall, D.; Kadobayashi, Y. LSTM-based intrusion detection system for in-vehicle can bus communications. IEEE Access 2020, 8, 185489–185502. [Google Scholar] [CrossRef]
- D’Angelo, G.; Castiglione, A.; Palmieri, F. A cluster-based multidimensional approach for detecting attacks on connected vehicles. IEEE Internet Things J. 2020, 8, 12518–12527. [Google Scholar] [CrossRef]
- Loukas, G.; Vuong, T.; Heartfield, R.; Sakellari, G.; Yoon, Y.; Gan, D. Cloud-based cyber-physical intrusion detection for vehicles using deep learning. IEEE Access 2017, 6, 3491–3508. [Google Scholar] [CrossRef]
- Zhang, J.; Li, F.; Zhang, H.; Li, R.; Li, Y. Intrusion detection system using deep learning for in-vehicle security. Ad Hoc Netw. 2019, 95, 101974. [Google Scholar] [CrossRef]
- Lokman, S.F.; Othman, A.T.; Musa, S.; Abu Bakar, M.H. Deep contractive autoencoder-based anomaly detection for in-vehicle controller area network (CAN). In Progress in Engineering Technology; Springer: Cham, Switzerland, 2019; pp. 195–205. [Google Scholar]
- Avatefipour, O.; Al-Sumaiti, A.S.; El-Sherbeeny, A.M.; Awwad, E.M.; Elmeligy, M.A.; Mohamed, M.A.; Malik, H. An intelligent secured framework for cyberattack detection in electric vehicles’ CAN bus using machine learning. IEEE Access 2019, 7, 127580–127592. [Google Scholar] [CrossRef]
- Yang, Y.; Duan, Z.; Tehranipoor, M. Identify a spoofing attack on an in-vehicle CAN bus based on the deep features of an ECU fingerprint signal. Smart Cities 2020, 3, 17–30. [Google Scholar] [CrossRef]
- Li, X.; Hu, Z.; Xu, M.; Wang, Y.; Ma, J. Transfer learning based intrusion detection scheme for Internet of vehicles. Inf. Sci. 2021, 547, 119–135. [Google Scholar] [CrossRef]
- Al-Saud, M.; Eltamaly, A.M.; Mohamed, M.A.; Kavousi-Fard, A. An intelligent data-driven model to secure intravehicle communications based on machine learning. IEEE Trans. Ind. Electron. 2019, 67, 5112–5119. [Google Scholar] [CrossRef]
- Aldhyani, T.H.; Alkahtani, H. Attacks to automatous vehicles: A deep learning algorithm for cybersecurity. Sensors 2022, 22, 360. [Google Scholar] [CrossRef]
- Nilsson, D.K.; Larson, U.E.; Jonsson, E. Efficient in-vehicle delayed data authentication based on compound message authentication codes. In Proceedings of the 2008 IEEE 68th Vehicular Technology Conference, Calgary, AB, Canada, 21–24 September 2008; pp. 1–5. [Google Scholar]
- Van Herrewege, A.; Singelee, D.; Verbauwhede, I. CANAuth-a simple, backward compatible broadcast authentication protocol for CAN bus. In Proceedings of the ECRYPT Workshop on Lightweight Cryptography, Louvain-la-Neuve, Belgium, 28–29 November 2011; Volume 2011, p. 20. [Google Scholar]
- Hazem, A.; Fahmy, H.A. Lcap-a lightweight can authentication protocol for securing in-vehicle networks. In Proceedings of the 10th Escar Embedded Security in Cars Conference, Berlin, Germany, 28–29 November 2012; Volume 6, p. 172. [Google Scholar]
- Groza, B.; Murvay, S.; Herrewege, A.V.; Verbauwhede, I. LiBrA-CAN: A lightweight broadcast authentication protocol for controller area networks. In Proceedings of the International Conference on Cryptology and Network Security, Darmstadt, Germany, 12–14 December 2012; pp. 185–200. [Google Scholar]
- Lin, C.W.; Sangiovanni-Vincentelli, A. Cyber-security for the controller area network (CAN) communication protocol. In Proceedings of the 2012 International Conference on Cyber Security, Alexandria, VA, USA, 14–16 December 2012; pp. 1–7. [Google Scholar]
- Han, K.; Weimerskirch, A.; Shin, K.G. Automotive cybersecurity for in-vehicle communication. IQT Q. 2014, 6, 22–25. [Google Scholar]
- Ueda, H.; Kurachi, R.; Takada, H.; Mizutani, T.; Inoue, M.; Horihata, S. Security authentication system for in-vehicle network. SEI Tech. Rev. 2015, 81, 5–9. [Google Scholar]
- Fassak, S.; El Idrissi, Y.E.H.; Zahid, N.; Jedra, M. A secure protocol for session keys establishment between ECUs in the CAN bus. In Proceedings of the 2017 International Conference on Wireless Networks and Mobile Communications (WINCOM), Rabat, Morocco, 1–4 November 2017; pp. 1–6. [Google Scholar]
- Noureldeen, P.; Azer, M.A.; Refaat, A.; Alam, M. Replay attack on lightweight CAN authentication protocol. In Proceedings of the 2017 12th International Conference on Computer Engineering and Systems (ICCES), Cairo, Egypt, 19–20 December 2017; pp. 600–606. [Google Scholar]
- Tashiro, A.; Muraoka, H.; Araki, S.; Kakizaki, K.I.; Uehara, S. A secure protocol consisting of two different security-level message authentications over CAN. In Proceedings of the 2017 3rd IEEE International Conference on Computer and Communications (ICCC), Chengdu, China, 13–16 December 2017; pp. 1520–1524. [Google Scholar]
- Lu, Z.; Wang, Q.; Chen, X.; Qu, G.; Lyu, Y.; Liu, Z. LEAP: A lightweight encryption and authentication protocol for in-vehicle communications. In Proceedings of the 2019 IEEE Intelligent Transportation Systems Conference (ITSC), Auckland, New Zealand, 27–30 October 2019; pp. 1158–1164. [Google Scholar]
- Wang, Q.; Sawhney, S. VeCure: A practical security framework to protect the CAN bus of vehicles. In Proceedings of the 2014 International Conference on the Internet of Things (IOT), Cambridge, MA, USA, 6–8 October 2014; pp. 13–18. [Google Scholar]
- Ansari, M.R.; Yu, S.; Yu, Q. IntelliCAN: Attack-resilient controller area network (CAN) for secure automobiles. In Proceedings of the 2015 IEEE International Symposium on Defect and Fault Tolerance in VLSI and Nanotechnology Systems (DFTS), Amherst, MA, USA, 12–14 October 2015; pp. 233–236. [Google Scholar]
- Woo, S.; Jo, H.J.; Kim, I.S.; Lee, D.H. A practical security architecture for in-vehicle CAN-FD. IEEE Trans. Intell. Transp. Syst. 2016, 17, 2248–2261. [Google Scholar] [CrossRef]
- Radu, A.I.; Garcia, F.D. LeiA: A lightweight authentication protocol for CAN. In Proceedings of the European Symposium on Research in Computer Security, Heraklion, Greece, 28–30 September 2016; pp. 283–300. [Google Scholar]
- King, Z. Investigating and securing communications in the Controller Area Network (CAN). In Proceedings of the 2017 International Conference on Computing, Networking and Communications (ICNC), Silicon Valley, CA, USA, 26–29 January 2017; pp. 814–818. [Google Scholar]
- Farag, W.A. CANTrack: Enhancing automotive CAN bus security using intuitive encryption algorithms. In Proceedings of the 2017 7th International Conference on Modeling, Simulation, and Applied Optimization (ICMSAO), Sharjah, United Arab Emirates, 4–6 April 2017; pp. 1–5. [Google Scholar]
- Siddiqui, A.S.; Gui, Y.; Plusquellic, J.; Saqib, F. Secure communication over CANBus. In Proceedings of the 2017 IEEE 60th International Midwest Symposium on Circuits and Systems (MWSCAS), Boston, MA, USA, 06–09 August 2017; pp. 1264–1267. [Google Scholar]
- Gui, Y.; Siddiqui, A.S.; Saqib, F. Hardware based root of trust for electronic control units. In Proceedings of the SoutheastCon 2018, St. Petersburg, FL, USA, 19–22 April 2018; pp. 1–7. [Google Scholar]
- Carel, G.; Isshiki, R.; Kusaka, T.; Nogami, Y.; Araki, S. Design of a message authentication protocol for CAN FD based on chaskey lightweight MAC. In Proceedings of the 2018 Sixth International Symposium on Computing and Networking Workshops (CANDARW), Takayama, Japan, 27–30 November 2018; pp. 267–271. [Google Scholar]
- Woo, S.; Moon, D.; Youn, T.Y.; Lee, Y.; Kim, Y. Can id shuffling technique (cist): Moving target defense strategy for protecting in-vehicle can. IEEE Access 2019, 7, 15521–15536. [Google Scholar] [CrossRef]
- Agrawal, M.; Huang, T.; Zhou, J.; Chang, D. CAN-FD-Sec: Improving security of CAN-FD protocol. In Security and Safety Interplay of Intelligent Software Systems; Springer: Cham, Switzerland, 2018; pp. 77–93. [Google Scholar]
- Zhang, M.; Masrur, A. Improving timing behavior on encrypted CAN buses. In Proceedings of the 2019 IEEE 25th International Conference on Embedded and Real-Time Computing Systems and Applications (RTCSA), Hangzhou, China, 18–21 August 2019; pp. 1–6. [Google Scholar]
- Jo, H.J.; Kim, J.H.; Choi, H.Y.; Choi, W.; Lee, D.H.; Lee, I. Mauth-can: Masquerade-attack-proof authentication for in-vehicle networks. IEEE Trans. Veh. Technol. 2019, 69, 2204–2218. [Google Scholar] [CrossRef]
- Mun, H.; Han, K.; Lee, D.H. Ensuring safety and security in CAN-based automotive embedded systems: A combination of design optimization and secure communication. IEEE Trans. Veh. Technol. 2020, 69, 7078–7091. [Google Scholar] [CrossRef]
- Groza, B.; Popa, L.; Murvay, P.S. Highly efficient authentication for CAN by identifier reallocation with ordered CMACs. IEEE Trans. Veh. Technol. 2020, 69, 6129–6140. [Google Scholar] [CrossRef]
- Youn, T.Y.; Lee, Y.; Woo, S. Practical sender authentication scheme for in-vehicle CAN with efficient key management. IEEE Access 2020, 8, 86836–86849. [Google Scholar] [CrossRef]
- Lenard, T.; Bolboacă, R.; Genge, B.; Haller, P. MixCAN: Mixed and backward-compatible data authentication scheme for controller area networks. In Proceedings of the 2020 IFIP Networking Conference (Networking), Paris, France, 22–26 June 2020; pp. 395–403. [Google Scholar]
- Ma, B.; Yang, S.; Zuo, Z.; Zou, B.; Cao, Y.; Yan, X.; Zhou, S.; Li, J. An Authentication and Secure Communication Scheme for In-Vehicle Networks Based on SOME/IP. Sensors 2022, 22, 647. [Google Scholar] [CrossRef]
- Mousa, A.R.; NourElDeen, P.; Azer, M.; Allam, M. Lightweight authentication protocol deployment over FlexRay. In Proceedings of the 10th International Conference on Informatics and Systems, Giza, Egypt, 9–11 May 2016; pp. 233–239. [Google Scholar]
- Gu, Z.; Han, G.; Zeng, H.; Zhao, Q. Security-aware mapping and scheduling with hardware co-processors for flexray-based distributed embedded systems. IEEE Trans. Parallel Distrib. Syst. 2016, 27, 3044–3057. [Google Scholar] [CrossRef]
- Han, G.; Zeng, H.; Li, Y.; Dou, W. SAFE: Security-aware flexray scheduling engine. In Proceedings of the Conference on Design, Automation & Test in Europe, Dresden, Germany, 24–28 March 2014. [Google Scholar]
- Perrig, A.; Tygar, J.D. TESLA broadcast authentication. In Secure Broadcast Communication; Springer: Boston, MA, USA, 2003; pp. 29–53. [Google Scholar]
- Deng, J.; Yu, L.; Fu, Y.; Hambolu, O.; Brooks, R.R. Security and data privacy of modern automobiles. In Data Analytics for Intelligent Transportation Systems; Elsevier: New York, NY, USA, 2017; pp. 131–163. [Google Scholar]
- Takahashi, J.; Aragane, Y.; Miyazawa, T.; Fuji, H.; Yamashita, H.; Hayakawa, K.; Ukai, S.; Hayakawa, H. Automotive attacks and countermeasures on lin-bus. J. Inf. Processing 2017, 25, 220–228. [Google Scholar] [CrossRef][Green Version]
- Kiravuo, T.; Sarela, M.; Manner, J. A survey of Ethernet LAN security. IEEE Commun. Surv. Tutor. 2013, 15, 1477–1491. [Google Scholar] [CrossRef]
- Lin, C.-W.; Yu, H. INVITED: Cooperation or Competition? Coexistence of Safety and Security in Next-Generation Ethernet-Based Automotive Networks. In Proceedings of the 53rd ACM/EDAC/IEEE Design Automation Conference, Austin, TX, USA, 5–9 June 2016. [Google Scholar]
- Wolf, M.; Weimerskirch, A.; Paar, C. Security in automotive bus systems. In Workshop on Embedded Security in Cars; Escrypt GmbH: Bochum, Germany, 2004; pp. 1–13. [Google Scholar]
- Pekaric, I.; Sauerwein, C.; Haselwanter, S.; Felderer, M. A taxonomy of attack mechanisms in the automotive domain. Comput. Stand. Interfaces 2021, 78, 103539. [Google Scholar] [CrossRef]
- Guan, T.; Han, Y.; Kang, N.; Tang, N.; Chen, X.; Wang, S. An overview of vehicular cybersecurity for intelligent connected vehicles. Sustainability 2022, 14, 5211. [Google Scholar] [CrossRef]




| In-Vehicle Network Communication Protocols | Domain | Bandwidth | Salient Features | Drawbacks | Topology | Standard | Cabling | Max. Nodes Supported | Messaging |
|---|---|---|---|---|---|---|---|---|---|
| Controller Area Network (CAN) | Powertrain, Body Control | 125 Kbps–1 Mbps | Low cost | Less Bandwidth | Star, Ring, Linear bus | ISO 11898 | UTP | 30 | Multi-Master |
| Local Interconnect Network (LIN) | Simple Applications (Less Time Critical) | 125 Kbps–1 Mbps | Low cost | Low Speed | Liner bus | ISO 17987 | 1-Wire Cabling | 16 | Master-Slave |
| FlexRay | Advanced Chassis Control | Up to 10 Mbps | High Speed | High Cost | Star, Linear bus, hybrid | ISO 17458 | UTP | 22 | Multi-Master |
| Media-Oriented Systems Transport (MOST) | Infotainment Applications | Up to 150 Mbps | High Speed | High Cost | Ring | ISO 21806 | UTP and Optical | 64 | Streams/Cyclic Frames |
| Automotive Ethernet | High Bandwidth Applications | Up to 100 Mbps | High Speed | High Cost | Star, Linear bus | ISO 21111 | UTP | Based on Switch ports | Based on IP |
| Focused Area | Algorithm Used for Detection | Adversary Model | Robustness | Strength | Weakness | Complexity Level | Accuracy in Detection (%) |
|---|---|---|---|---|---|---|---|
| CAN Bus | Time Intervals-based Framework for Analysis [60] | Denial of Service Attack | High | Lightweight IDS | No provision of Sequence Analysis | Low | >90 |
| CAN Bus | Deep Neural Network [61] | Intrusion Detection System | High | Effective Class Discrimination | Extensive Data Set is required for learning | High | >90 |
| VANET Applications | Artificial Neural Network [62] | Misbehavior Detection System | High | Effective Data Analysis and Feature Extraction before building Classifier | Lack of Comprehensive Detection Mechanism | High | >90 |
| Connected Vehicle | Physical-based constraints and Machine Learning Algorithm [63] | Manipulation of Data | Medium | Collaborative Adaptive Cruise Control Attack Analysis | Unable to find dependencies in hidden states | High | 90% for velocity and Position change attack |
| CAN Bus | Generative Adversarial Networks based on Deep Learning [64] | Fuzzy Attack, Denial of Service Attack, Spoofing Attack | High | Real time IDS for In-Vehicle Network | Lack of Efficiency in distinguishing other type of Anomalous Traffic | High | >90 |
| Autonomous Vehicle | Long Short-Term Memory and Reinforcement Learning [65] | Cyber Physical Attack | High | Effective extraction of temporal features using LSTM | Extensive Data Set for learning | High | Not Available |
| CAN Bus | Long Short-Term Memory [66] | Flood Attack, Replay Attack, Spoofing Attack | Medium | Multi-Dimensional Anomaly Detection Model | Issues of Random Weight Initializations | High | >80 |
| Machine to Machine Communication | Five machine learning approaches, namely K-Nearest Neighbor, Linear and Radial Support Vector Machine, model based on Decision Tree, model based on Naive Bayes, and finally model based on Random Forest [67] | Trust Computation | Medium | Comparative Analysis of machine learning-based trust models | Issues in finding the optimality in trust boundaries | High | Not Available |
| Internet of Vehicles | Fuzzy and Q-Learning [68] | Distributed Denial of Service Attack | High | Self-Learning Capability | Unable to Provide Efficient Protection Against other Types of Attacks | High | Not Available |
| Autonomous Vehicle | Convolutional Neural Network and Fully Connected Deep Neural Network [69] | Platoon Attack | High | Effective Performance with Time Series Classification | Scalability Issues | High | >90 |
| CAN Bus | Deep Convolutional Neural Network [70] | Spoofing, Denial of Service, Fuzzy | Medium | Experiment is Performed on the Real Vehicle | Semantic Features are not considered for further detecting the unknown attack | High | >80 |
| CAN Bus | Recurrent Neural Network [71] | Impersonation, Denial of Service, Fuzzy | High | Vehicle status can be monitored in real time without domain knowledge | Issues with long sequences | High | >90 |
| VANET | Reinforcement Learning [72] | Trust Computation | High | Model for evaluating the reliability of information | Issue of overloading of states resulting into diminishing output | High | 90% |
| CAN Bus | Intrusion Detection based on Frequency Analysis [73] | Replay Attack | Medium | Model can be adaptable to different Automotive Manufacturer | No consideration about different vehicle states | Medium | Not Available |
| Autonomous Vehicle | Long-Term Short-Term Memory, Generative Adversarial Network, Reinforcement Learning [74] | Cyber Physical Attack | High | Model can Extract Features from huge data sets | No consideration for non-linear modelling with dynamics | High | Not Available |
| CAN Bus | Deep Learning [75] | Impersonation, Denial of Service, Fuzzy | Medium | Sequential Patterns Analysis for Detecting the Change in Traffic Behavior | No consideration for other Cyber Attacks | High | >80 |
| CAN Bus | Long Short-Term Memory [76] | Spoofing, Denial of Service, Fuzzy | Medium | CAN data sets are collected from real Vehicle | Experiment is conducted in offline mode, no consideration for other unknown attacks | High | >90 |
| CAN Bus | Cluster-based learning algorithm and Data Driven algorithm [77] | RPM Attack, Fuzzy Attack, GEAR Attack, Denial of Service Attack | High | Data driven model with classification based on unsupervised approach | No consideration about self adaptability feature and other attack types | High | >90 |
| CAN Bus, Cloud-based IDS | Deep Learning [78] | Malware, Denial of Service, Command Injection | Medium | Mathematical Modelling and Testbed Experiment on Robotic Vehicle | No consideration against physical jamming threat | High | >85 |
| CAN Bus | Deep Learning [79] | Replay, Spoofing | High | Experiment is conducted on the real data acquired from the physical vehicle | No Comparative Analysis with other Deep Learning Schemes | High | >95 |
| CAN Bus | Deep Contractive Autoencoders [80] | Fuzzy, Impersonation, Denial of Service | Medium | Three different Vehicles are utilized for AN Data Collection and Discriminating the Anomalies. | Lack of Efficiency in distinguishing other type of Anomalous Traffic | High | >90 |
| CAN Bus | Machine Learning [81] | Spoofing, Denial of Service, Fuzzy | High | Simulation is performed on the real data collected from licensed vehicle | Support Vector Machine underperform with more noisy data set | High | >90 |
| CAN Bus | Long-Term Short-Term Memory and Recurrent Neural Network [82] | Spoofing | High | Authentication based on finger print signals | No provision for optimization of FPGA Accelerator | High | >95 |
| Internet of Vehicles | Deep Transfer Learning [83] | Flooding, ARP, Impersonation | High | For New Attack type, Model can update without any labelled data requirements | Issue of Negative Transfer | High | >90 |
| CAN Bus | Machine Learning [84] | Denial of Service | Medium | High Search Ability and Avoidance of Premature Convergence | No consideration for other Cyber Attacks | High | >90 |
| CAN Bus | Long Short-Term Memory and Convolutional Neural Network [85] | Replay, Denial of Service, Fuzzy, Spoofing | High | Model is verified with automatic vehicle data sets | No consideration for other attacks types | High | >90 |
| Focused Area | Strength | Approach/Methodology | Weakness | Adversary Model | Key Aspects |
|---|---|---|---|---|---|
| CAN Bus | Delayed Data Authentication for avoiding disruption with real time traffic | CBC-MAC [86] | No provision for MAC calculation with diversified compound sizes | Spoofing, Injection |
|
| CAN Bus | Backward Compatibility, no need to modify existing nodes | Counters, HMAC, Symmetric Key [87] | All nodes must know about pre-shared key before verifying the messages | Replay, Sniffing, Injection, Spoofing | The proposed scheme utilizes HMAC in designing lightweight authentication protocol. |
| CAN Bus | The proposed protocol can be practically deployed in the vehicle without hardware modification | Session Keys, Magic Number [88] | Issues in exchange of authentication data owing bandwidth limitations | Injection, Replay | A lightweight authentication protocol is proposed to CAN bus. |
| CAN Bus | Source authentication is effectively managed | LMAC, MD5 [89] | The proposed scheme works well with only lower number of nodes | Injection, Replay | In the proposed scheme, authentication protocol is designed utilizing MAC mixing and key splitting mechanism. |
| CAN Bus | Proposed solution is software-based and can be easily applied | Secret Keys (Symmetric Pair wise) and MAC [90] | No comparative analysis is provided for testbed experiment | Replay, Masquerade |
|
| CAN Bus | Provide Secure channel for vehicle to external communication | CRC, MAC [91] | No comparative analysis is provided for other types of attacks | Denial of Service | Designing of new secure protocol for CAN. |
| CAN Bus | The proposed centralized security scheme is verified with FPGA board | HMAC, SHA-256 [92] | No comparative analysis is provided for key exchange environment | Spoofing | In the proposed scheme, central authentication framework is designed. |
| CAN Bus | The proposed scheme authenticate ECU with provision of session keys establishment | Session Keys, ECC, HMAC [93] | AVISPA tool is used for Security Validity, other platforms should be used for measuring the efficacy | Authentication of ECU in CAN for providing protection against attacks |
|
| CAN Bus | Simulation is performed using Vector Canoe. | Authentication (Lightweight) [94] | No comparative analysis is provided for other types of attacks | Denial of Service | A new CAN authentication protocol is proposed. |
| CAN Bus | The proposed scheme utilize two different MAC methods. | Key Management, MAC [95] | No comparative analysis is provided for other types of attacks | Replay, Tampering | A new message authentication-based protocol is proposed for CAN. |
| CAN Bus | The proposed scheme requires less memory and speed is high | SHA, RC4, AES-128 [96] | No comparative analysis is provided for other types of attacks | Flood, Replay, Masquerade, Eavesdrop, Brute-force | For authentication and encryption, a new lightweight protocol is proposed for CAN bus. |
| CAN Bus | Proposed scheme has high compatibility with existing architectures and testbed experiment is performed | Symmetric Key, HMAC, Trusted Group [97] | No comparative analysis is provided for other types of attacks | Injection, Sniffing, Spoofing | A practical framework is proposed for solving issue of message authentication. |
| CAN Bus | The proposed scheme has built in fault detection mechanism | CRC, Lightweight Stream Cipher [98] | No comparative analysis is provided for other types of attacks | Masquerade |
|
| CAN Bus | The proposed security scheme provide secure environment for CAN-FD and performance is evaluated with microcontrollers and oftware | SHA-256, AES-128, HMAC [99] | No comparative analysis is provided for other types of attacks | Spoofing, Sniffing, Replay | A security architecture is proposed for developing secure communication environment for CAN-FD. |
| CAN Bus | Backward Compatibility, no need to modify existing nodes | Counter, MAC, 128-bit key [100] | No comparative analysis is provided for other types of attacks | Spoofing, Replay, Injection | An authentication protocol is proposed in which ECUs are allowed to authenticate each other. |
| CAN Bus | Message authentication for CAN bus with the presence of existing constraints | SHA1, HMAC [101] | No comparative analysis is provided for other types of attacks | Replay, Denial of Service | In the proposed scheme, time stamp as well as HMAC are used for the message authentication. |
| CAN Bus | The proposed scheme can change the encrypted messages frequently | Symmetric Key (Dynamically Managed) [102] | No comparative analysis is provided for other types of attacks | Replay |
|
| CAN Bus | The proposed security framework is hardware-based | PUFs, ECDH [103] | No comparative analysis is provided for other types of attacks | Spoofing, Eavesdropping |
|
| CAN Bus | The proposed security model block the compromised data on the receiver as well as sender side simultaneously. | Blacklisting, MAC, Whitelisting [104] | No comparative analysis is provided for other types of attacks | Denial of Service, Man in the Middle |
|
| CAN Bus | The proposed scheme is evaluated on several embedded systems environment | 128-bit key, ChaskeyMAC, Pre-shared [105] | No comparative analysis is provided for other types of attacks | Spoofing, Replay | An authentication protocol is proposed for CAN-FD, utilizing ChaskeyMAC. |
| CAN Bus | In the proposed scheme CAN ID is shuffled using NAS frequently. | HMAC, AES-128, SHA-256, Shuffling-CAN ID, AKEP-2 [106] | No comparative analysis is provided for other types of attacks | Replay, Impersonation | In the proposed scheme, attack surface is dynamically shuffled using one time Id. |
| CAN Bus | Communication security is provided by group-based approach, effective group key management | Keys (Public andPrivate), Gateway-ECU [107] | No comparative analysis is provided for other types of attacks | Spoofing, Sniffing, Replay | A new security architecture is proposed in which Gateway-ECU is used for communication among ECUs. |
| CAN Bus | Experiment is conducted on real hardware. | GHASH, AES-128 [108] | Delay Issue, no comparative analysis is provided for other types of attacks | Sniffing, Replay, Spoofing | In the proposed scheme, encrypted CAN frames are assigned several different priorities for handling the increased delay in the system. |
| CAN Bus | The proposed scheme does not require any changes to existing hardware. | AKEP2, MAC, Session Keys [109] | No comparative analysis is provided for other types of attacks | Denial of Service, Masquerade, Bus-Off | A new authentication protocol is proposed. No need of any hardware modifications. |
| CAN Bus | Design optimization is performed in the proposed scheme for ensuring time critical execution of applications | HMAC 64 bits, Key distribution process based on Diffie-Hellman [110] | No comparative analysis is rovided for other types of attacks | Denial of Service, Injection, Replay, Impersonation, Bus off | The proposed scheme uses HMAC for ensuring security on CAN bus. |
| CAN Bus | Sender nodes are authenticated using software-based mechanism | AES-128, MAC [111] | No comparative analysis is provided for other types of attacks | Concatenation, Injection, Replay | The proposed scheme utilizes the ordered CMAC buffer for authenticating the CAN frames ID. |
| CAN Bus | The proposed scheme has two significant contributions, namely sender authentication and effective key management | MAC, Session Keys [112] | No comparative analysis is provided for other types of attacks | Replay, Impersonation | The proposed scheme is characterized with two features, namely authentication of the sender as well as management of keys. |
| CAN Bus | Overhead of CAN communication is reduced significantly by mixing diversified authentication tags. | SHA-256, MAC, Symmetric Key Cryptography, Bloom Filters [113] | No provision of key distribution and no comparative analysis is provided for other types of attacks | Replay, Man in the Middle | In the proposed scheme, CAN bus data authentication is carried out with the help of Bloom Filters attributes. |
| CAN, Automotive Ethernet | Mutual identity authentication is provided to all communication parties and session key confidentiality is effectively managed | Symmetric Cryptography, Session Keys, AEAD Algorithm [114] | No comparative analysis is provided for other types of attacks | Eavesdropping, Replay, Man in the Middle, Masquerade | The proposed scheme is featured with efficient authentication as well as secure communication. Session keys are updated regularly. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rathore, R.S.; Hewage, C.; Kaiwartya, O.; Lloret, J. In-Vehicle Communication Cyber Security: Challenges and Solutions. Sensors 2022, 22, 6679. https://doi.org/10.3390/s22176679
Rathore RS, Hewage C, Kaiwartya O, Lloret J. In-Vehicle Communication Cyber Security: Challenges and Solutions. Sensors. 2022; 22(17):6679. https://doi.org/10.3390/s22176679
Chicago/Turabian StyleRathore, Rajkumar Singh, Chaminda Hewage, Omprakash Kaiwartya, and Jaime Lloret. 2022. "In-Vehicle Communication Cyber Security: Challenges and Solutions" Sensors 22, no. 17: 6679. https://doi.org/10.3390/s22176679
APA StyleRathore, R. S., Hewage, C., Kaiwartya, O., & Lloret, J. (2022). In-Vehicle Communication Cyber Security: Challenges and Solutions. Sensors, 22(17), 6679. https://doi.org/10.3390/s22176679









