A Comprehensive Collection and Analysis Model for the Drone Forensics Field
Abstract
:1. Introduction
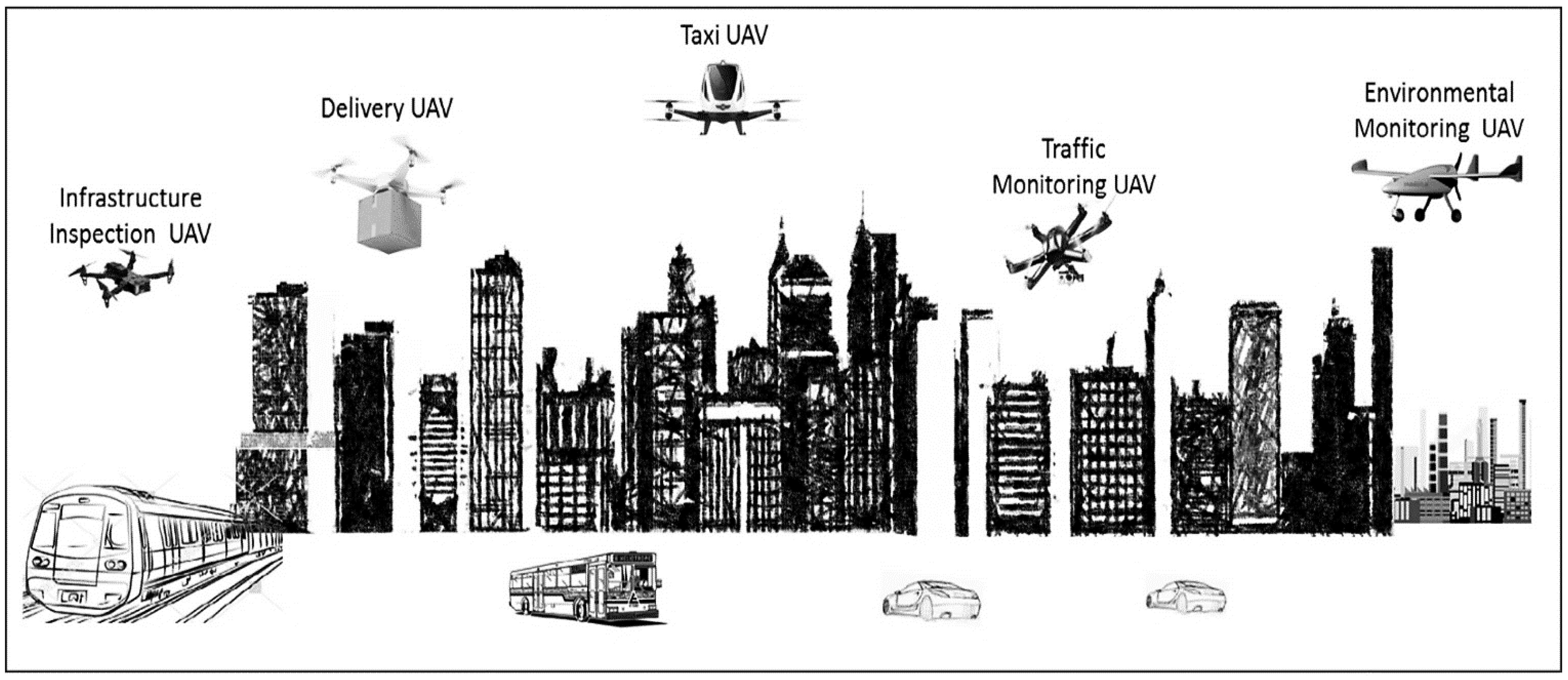
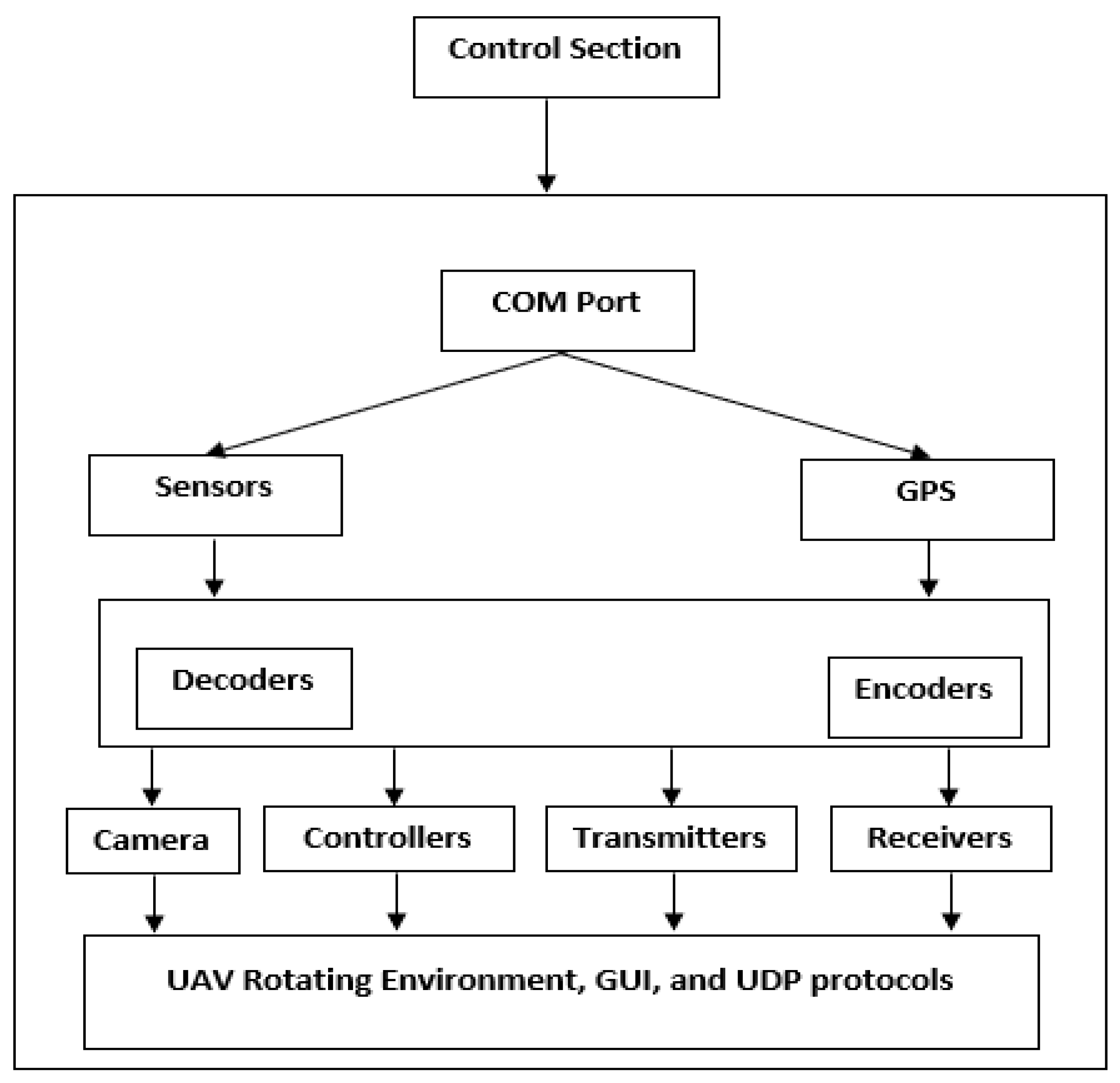
2. Background and Related Work
2.1. Drone Forensic Models and Frameworks
2.2. Machine Learning Techniques Used in the Drone Forensics Field
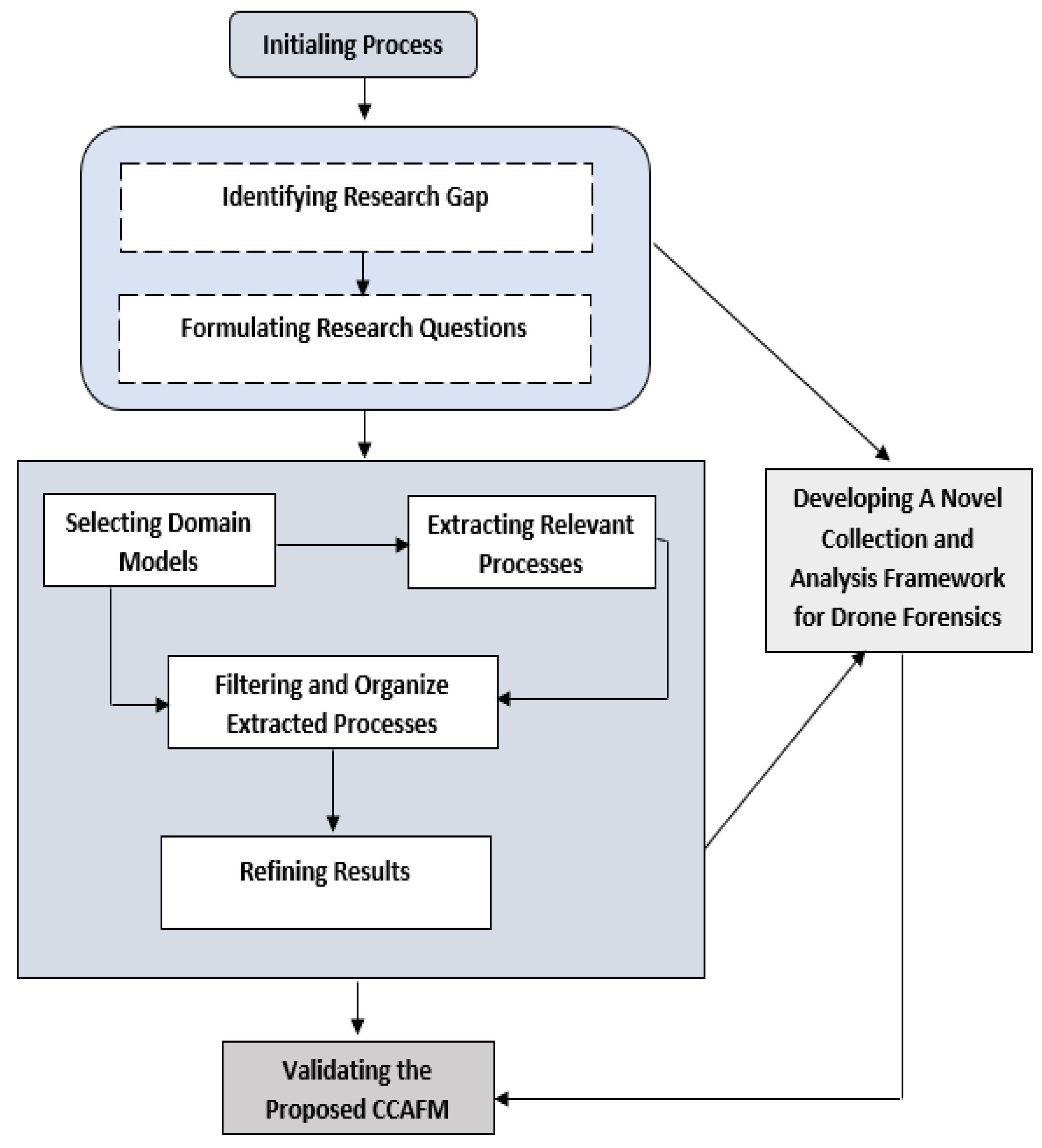
3. Methodology for Developing and Validating CCAFM
- Phase 1: Identifying and selecting the domain models
- Phase 2: Extracting the processes for relevant investigations
- Phase 3: Filtering and organizing the extracted processes
- Phase 4: Proposing a comprehensive collection and analysis forensic model
- Phase 5: Validating the proposed model
3.1. Phase 1: Identifying and Selecting the Domain Models
| ID. | Models References | Year | Authors | Description of the Model |
|---|---|---|---|---|
| 1. | [20] | 2015 | Mhatre et al. | They offered a tool using Java-FX to visualize the real-time flight control. Their designed tool is not directly applicable to the DF field; however, it can create efficient connections between a drone and its controller to transfer data. In addition, this tool can display sensor parameters, including GPS, IMU, and altitude for pilots, which provides a great level of safety for flights |
| 2. | [24] | 2016 | Horsman | This study offered an initial assessment of UAV devices, emphasizing the issues caused by this equipment to the digital forensic experts and law enforcement examinations. They provided an investigation of a Parrot Bebop drone and a study of the mobile tools used to pilot it, namely Galaxy and an iPhone 6, both using the Parrot’s offered UAVs flight routing product “FreeFlight3”. |
| 3. | [26] | 2016 | Mohan | In this study, the author analyzed the drones’ vulnerabilities and applications and their relationships with issues that generally arise in the cybersecurity domain. They asserted that if a drone is hacked and abused by opponents, serious risks or consequences may arise. That study primarily focused on identifying the benefits of using drones in numerous conditions, from employing these devices as children’s toys to using them as mass destruction weapons. |
| 4. | [19] | 2016 | Kovar, Dominguez, and Murph | The authors discussed all components of a drone. They all emphasized the use of the Linux operating system and its potential to gather evidence on the Linux file system. Note that to work properly, drones need to use an OS. |
| 5. | [85] | 2016 | Maarse et al. | Researchers tried to evaluate DRFs with the purpose of DJI Phantom 2 commonly. They assessed the drone’s software and hardware and reviewed how they can be used to apply DRFs. Their results achieved the creation of a principle in the dedication and range of DRFs |
| 6. | [25] | 2016 | Procházka | Authors attempted to integrate the visualizing data recovered from drones with a non-forensic approach. They designed an application to visualize the log parameters from flight data. However, only a small number of drones were evaluated in their study. The scope of this working on the Parrot AR Drone 2.0. |
| 7. | [29] | 2017 | Prastya, Riadi, and Luthfi | The researchers comprehensively discussed how the GPS coordinates could be used as location evidence while examining the crimes committed with the help of a drone. They attempted not only to extract the system logs but also to visualize GPS coordinates on maps, where the web-based third-party platforms were used to plot the flight paths. |
| 8. | [27] | 2017 | Jain, Rogers, and Matson | The authors proposed a 12-phase forensic framework to offer an innovative approach to the systematic investigation of UAVs. Wide-ranging tests were carried out on five commercial UAVs, for instance, the Parrot AR Drone 2.0, to identify the relationships amongst various components. They also executed an experiment to validate their developed framework. All the UAVs tested in the study were modified by adding and removing some parts. These modifications were done to try to check whether the framework involved all of the various elements in any basic commercial UAV and to examine whether it could be applied to a comprehensive UAV analysis. They found out that an important issue that does not allow for mitigating the attacks effectively is the deficiency of law enforcement training processes in UAVs. None of the UAVs were exposed to forensic analyses; however, an effective framework was finally constructed, which applied to the ex-amination and analysis of the stages involved. |
| 9. | [28] | 2017 | Clark et al. | In this study, the authors were the first researchers that comprehensively analyzed the DJI Phantom 3 Standard. The examined UAV was flown towards two different sites. Then, the collected data were separated into three parts: controller, drone, and phone/tablet. Eventually, they explored two types of files of interest: the “.dat” files produced by the UAV and the “.txt” files produced by the DJI GO application. The files were first subjected to the decryption and decodification processes; after that, the information about the GPS locations, flight status, Wi-Fi connections, remote control, motors, etc., was extracted. When the obtained data were analyzed, and the proprietary file structures were well-understood, the researchers developed the DROP tool for the analysis of the evidentiary files. Additionally, they developed a forensically sound open-source drone open-source parser (DROP) tool. |
| 10. | [86] | 2017 | Bucknell and Bassindal | The authors analyzed the effects of a quadcopter’s downwash to know whether it can affect the retaining of material evidence in crime events. |
| 11. | [30] | 2017 | Llewellyn | The authors attempted to explore the flight data correlation among drones, SD cards, and mobile phones. Finding a connection between a drone and a suspect significantly facilitates criminal inspections. The application of specific software to private UAV devices could lead to the provision of many digital items such as GPS timestamps and waypoints, several connected satellites, barometer, pitch, roll, battery status, azimuth, distance, photos, and videos. |
| 12. | [32] | 2017 | Barton and Azhar | The researchers in this study used Windows and Kali (a Linux distribution) as forensic workstations to conduct the needed analyses on A.R Drone and DJI Phantom 3. Different open-source tools such as Geo-Player have been used primarily to visualize the data related to the flight path. Due to the absence of a proper built environment, including a package manager, configuration tools, and a compiler within the UAV system, this option entails making a serious change to the data existing in the UAV. For that reason, it was terminated in favor of the logical level acquisition. This was carried out by mounting a forensic mass storage device onto a UAV; then, the existing files were copied entirely from the mounted “/ data” partition using the “cp” command. |
| 13. | [31] | 2017 | A. L. P. S. Renduchintala, Albehadili, and Javaid | The authors tried to examine the key log boundaries of the independent UAV. They suggested comprehensive forensic software for the drone design with initial findings. |
| 14. | [87] | 2018 | Bouafif et al. | In this study, the authors utilized digital forensics to the Parrot A.R Drone 2.0. They delivered a dialogue on various common statements and file structures and then tried to imagine the trip path with the aid of Google Earth. |
| 15. | [23] | 2018 | Roder, Choo, and Le-Khac | The authors presented a set of rules for drone examinations in this study. They tried to discern the direction to conduct a drone forensic examination with the purpose of the DJI Phantom 3 drone as a real scenario. |
| 16. | [33] | 2018 | Maune | The authors offered their own set of guidelines in this regard. To end with, they explained how their procedures could be effectively implemented when analyzing a drone forensically. They employed DJI Phantom 3 drone as their case study. A key limitation in UAV forensics is that there is not any confirmed forensically useful tool (this indeed recommends a direction for future research). For example, the subsequent logical step is the creation of different parsing tools that can analyze original data and make available readable and reliable information. In addition, UAVs are expected to attain the capacity needed for being properly integrated with radio communication services in the future. |
| 17. | [34] | 2018 | Benzarti, Triki, and Korbaa | In this study, a novel architecture was introduced using the ID-based Signcryption to guarantee the authentication process and privacy preservation. In the initial step, the authors defined the key elements that the architecture relies on. After that, they investigated the interactions between these elements to explore how the process goes on. Next, they elaborated on their proposed authentication scheme. Thus, the RFID tags were applied to tracking the drones and the temporary identity to preserve privacy. In addition, they simulated the calculation of the average renewal of temporary identity by testing the drones’ different times and speeds. |
| 18. | [88] | 2018 | Gülataş and Baktır | The essential major log parameters of the autonomous drone were analyzed, and it was suggested to employ comprehensive software architecture related to drone forensics with preliminary results. The researchers expected that their developed software could provide a user-friendly graphical user interface (GUI) based on which the users could extract and investigate the onboard flight information. In addition, they claimed their findings would contribute to the body of the drone forensics field by designing a new tool that greatly helps run investigations effectively on criminal deeds executed with the help of drones. |
| 19. | [36] | 2018 | Dawam, Feng, and Li | The authors attempted to identify the potential cyber-physical security threats and address the current challenges attributed to UAV security before a time in the future when UAVs are the predominant vehicles used by ordinary people. Furthermore, in that study, there is a suggestion about using a certain method that can be applied effectively to examining large-scale cyber-security attack vectors of such systems concerning four classes of systems, which are highly important to UAV operations. Furthermore, the authors elaborated on the contributions of their findings and suggested the appropriate ways to defend against such attacks. |
| 20. | [37] | 2018 | Esteves, Cottais, and Kasmi | In this paper, authors designed arbitrary software and then applied it to a locked target to gain access to the device’s interior sensors and logs with the help of neutralization and hardening strategies to predict the effectiveness. |
| 21. | [89] | 2018 | Shi et al. | The authors discussed the overall legal processes that need to be taken into action to collect drones from the crime scene and investigate them in the laboratory. |
| 22. | [90] | 2018 | Guvenc et al. | In this study, a model was introduced for collecting and documenting digital data from the flight items and the related mobile devices to aid investigators in forensically examining two common drone systems, i.e., the Mavic Air and DJI Spark. |
| 23. | [91] | 2018 | Ding et al. | The authors conducted a preliminary forensic analysis on the Parrot Bebop, known as the only UAV similar to the Parrot AR Drone 2.0. |
| 24. | [35] | 2019 | A. Renduchintala et al. | The researchers made a forensic analysis of a captured UAV. Security forces may capture suspected UAVs using different techniques or tools such as a shotgun; these devices may break into private properties. It is necessary to determine what software/hardware modules are used to examine a UAV. After that, the investigator needs to perform three activities: gathering accessible evidence, providing the chain of custody, and analyzing the media/artifact loaded on the UAV. The increasing incidence of unlawful utilization of UAVs reflects legal ambiguity and uncertainty in the existing aviation regulations. This problem has resulted in the shortage of evidence and fundamental standards. |
| 25. | [38] | 2019 | Fitwi, Chen, and Zhou | The researchers designed an innovative scheme called distributed, agent-based secure mechanism for IoD and smart grid sensors monitoring (DASMIS). Their aim was to test a hybrid of peer-to-peer (P2P) and client-server (C/S) network architecture with reduced protocol overheads for immediate and bandwidth-efficient communication. Each node within this system is assigned with an initial status and provided with a python-based agent that can scan and detect in read-only node-IDs, node MAC address, system calls made, node IP address, all running system programs and applications, installed applications, and modifications. The agent securely authenticates the nodes, puts communications in a coded form, and approves inter-node access. This can prevent and detect different attacks, e.g., modification, masquerading, and DoS attacks. In addition, it can execute data encryption and hashing, and it reports the changes to other peer nodes and the server that is located at the C&C center. |
| 26. | [39] | 2019 | Jones, Gwinnett, and Jackson | The authors attempted to facilitate the processes such as generating, analyzing, validating, and optimizing data to trace evidence recovery. To do this, they introduced and explained the approach adopted for solving this problem considering the target fiber retrieval context using self-adhesive tapes. |
| 27. | [40] | 2019 | Salamh and Rogers | The authors attempted to adapt digital forensic processes to enhance drone incident response plans by implementing the drone forensic analysis process. The authors in that study provided more detailed information about the developed Drone Forensics and Incident Response Plan. They resulted in the fact that the Federal Aviation Administration (FAA) can update what unmanned aerial systems (UAS) require based on two classifications of UAS. In addition, they performed an inclusive review of the existing literature. They found out that it lacks research concentrating on incident responses and forensic analysis frameworks designed specifically for remotely piloted aerial systems. Then, they attempted to bridge this gap. |
| 28. | [41] | 2019 | Esteves | The researchers introduced the concept of “electromagnetic watermarking” as a technique exploiting the IEMI impacts to embed a watermark into civilian UAVs so that forensic tracking could be done well. |
| 29. | [42] | 2019 | J. L. Esteves, E. Cottais, and C. Kasmi | In this study, many aircraft accident investigators and drone forensics investigators were surveyed to find out how they employ forensic models to carry out forensic analyses on drones. The authors analyzed the data using the chi-square test of independence; it revealed no significant connection between the drone investigations of the groups of respondents and the techniques they use to perform UAS forensics. |
| 30. | [92] | 2019 | Le Roy et al. | A new method was introduced to accurately and quickly determine whether a drone is lying on the ground or in the sky. These results are attained just by eavesdropping on the radio traffic and processing it using standard machine learning techniques (instead of using any active approach). The authors in that study asserted that if the network traffic is classified properly, the exact status of a drone could be accurately determined using the overall operating system of ArduCopter (for instance, several DJI and Hobbyking vehicles). Furthermore, a lower bound was created on the detection delay when using the aforementioned method. It was confirmed that their proposed solution could discriminate against a drone’s state (moving or steady) with approximately 0.93 SR in 3.71 s. |
| 31. | [43] | 2019 | Sciancalepore et al. | The authors proposed using only the encrypted communication traffic between the drone and the remote controller to determine the drone’s status (flying or at rest). A drone equipped with ArduCopter firmware was used to collect the data. Without using the contents of the encrypted packet, six features were produced (inter-arrival time, packet size, mean and standard deviation computed over a certain number of samples of inter-arrival time and packet size). Three different classifiers, i.e., decision tree, random forest, and neural networks, were used to classify data (decision tree, random forest, and neural networks). The random forest classifier yielded superior results for drone detection. |
| 32. | [44] | 2020 | Lakew Yihunie, Singh, and Bhatia | The researchers assessed and discussed the security vulnerabilities of Parrot Mambo FPV and Eachine E010 drones. They then suggested proper countermeasures to enhance their resilience against possible attacks. The findings showed that Parrot Mambo FPV was vulnerable to de-authentication and FTP service attacks, while Eachine E010 was susceptible to radio frequency (RF) replay and custom-made controller attacks. |
3.2. Phase 2: Extracting the Processes for Relevant Investigations
- Abstracts, related work, conclusions, and titles were excluded. The investigation process was extracted either from the main textual model or the diagram.
- The investigation process should be associated with the analysis and collection processes.
- There should be an activity, definition, or task in the investigation process with which the purpose and meaning of the process can be recognized.
- The investigation processes unrelated to the conducting processes of collection and analysis were excluded.
- The implicit and explicit investigation processes should be included in the models.
3.3. Phase 3: Filtering and Organizing the Extracted Processes
3.4. Phase 4: Proposing a Comprehensive Collection and Analysis Forensic Model
3.5. Phase 5: Validating the Proposed Comprehensive Collection Analysis and Forensic Model
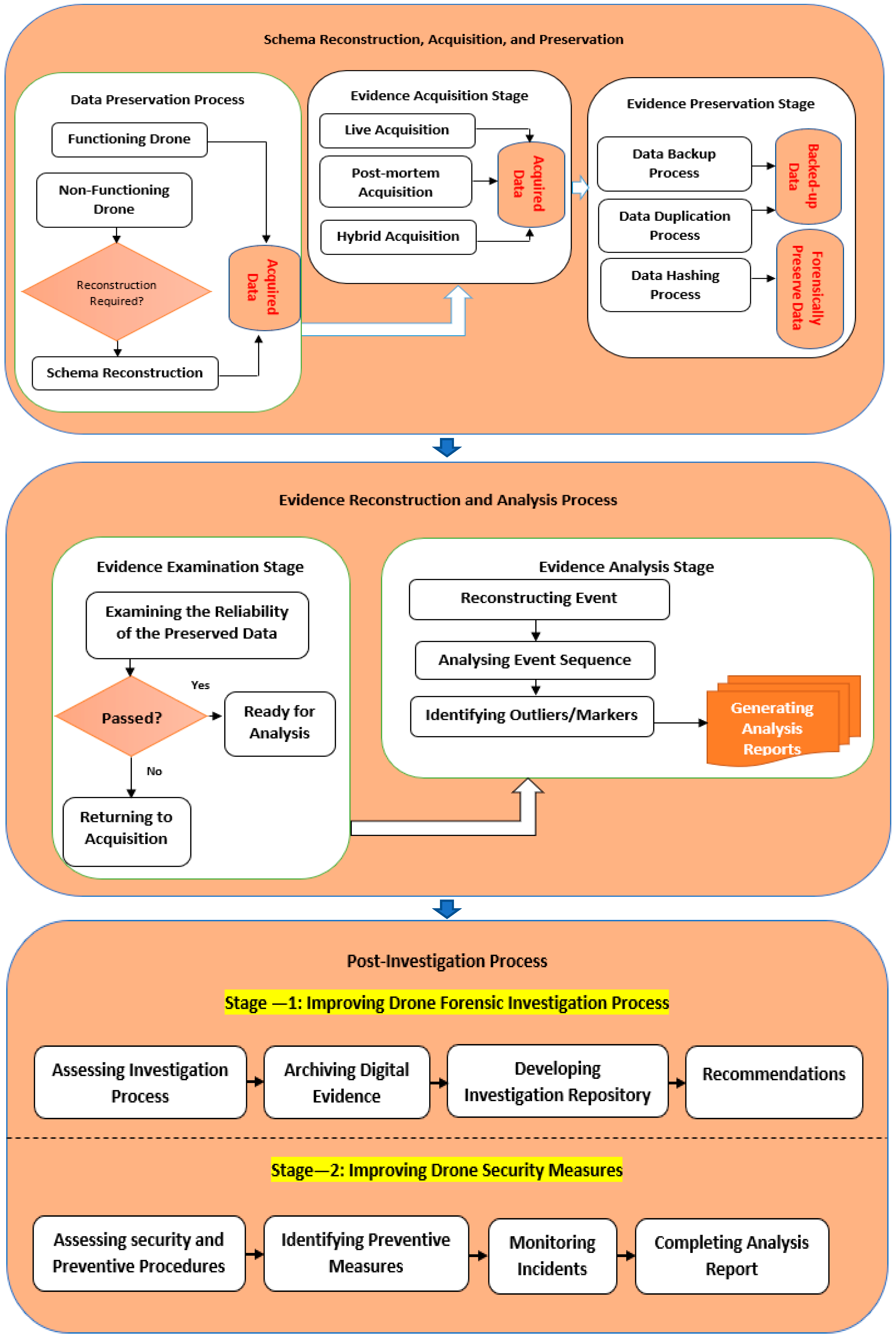
4. Discussion
4.1. Preservative A: Harmonized Perspective
- Acquisition and preservation process: It allows volatile and nonvolatile items to be collected from the suspect drone and preserved based on the trusted forensic techniques mainly using the collection and preservation process. It has three main stages: schema reconstruction, data acquisition, and data preservation. Prior to attempting to conduct any investigation, the investigator would need to ascertain the state of the database. In this regard, the preparatory process can be evoked. In this process, the investigator would need to verify if the drone would require a schema reconstruction process. Drone schema reconstruction is a major technical process implemented when the drone structure is either corrupted, damaged, or altered in such a way that the functionality of the drone cannot be ascertained. In such conditions, schema reconstruction techniques will be required to re-align the raw data in the drone to the metadata of the database. This could be techniques against localized data alteration, alteration to the sequence of blocks of data, and manipulation carried out on the links between blocks of data [82,95,96]. Upon an accurate schema reconstruction, the process of evidence acquisition can be evoked. Volatile and nonvolatile data can be acquired using the data acquisition stage with trusted forensic tools. It has three stages: a dead acquisition stage, a hybrid acquisition stage, and a live acquisition stage. The dead acquisition stage means that data are copied from the system investigated without the system itself, while in the hybrid acquisition stage, key elements of both dead and live acquisition methods are combined to offer the advantages of both options. The live acquisition stage is preferred to prevent the missing of volatile data. In the live acquisition stage, data are acquired in the case of system analysis while the investigation is being done. It is a usual dead acquisition after the live acquisition of the volatile data. Acquired data are the output of this stage. In the acquired data, preservation is needed to protect integrity and confidentiality against tampering. Hashing and backup methods are used in the data preservation stage to keep the reliability of the acquired data, and any modification of acquired data could be prevented. The integrity of data can be kept by hashing and backing up the acquired data from the data acquisition stage. Hashing ensures that the data will not be changed by the drone forensics techniques used to hash the acquired data. It also assures that the transferred acquired data between the destination and source is reliable. Moreover, an exact copy of the acquired data utilized as a second copy for the tampered original data is provided in the backup. Therefore, reconstruction and analysis activities are conducted to transfer the copy of the hashed acquired data to the forensic workstation through secure channels.
- Analysis and reconstruction: In this phase, the events causing an incident to acquired data (including user drone activities, existing SQL execution history, and retracing past systems) are examined, constructed, and analyzed. There are two stages in this mode: data examination and data reconstruction. In the data examination stage, it is ensured that acquired data are not altered and remain authentic. Thus, the investigation team’s first mission is to use such examination tools to examine if the data collected are authentic. However, the modification of the acquired data requires the investigation team to bring another clean acquired data from the first acquired data.
4.2. Preservative B: Awareness Perspective
- Improving the drone investigation process: the investigation process can be improved in the future, and the output and reliability of the drone investigation can be enhanced by gathering the output of the preservation and collection processes and analyses as well as the reconstruction process. It includes a set of procedures:
- Assessing the process of investigation: A reliable investigation can be guaranteed by carefully examining the existing drone forensics’ workstation, i.e., investigation team, tools, procedures, guidelines, models, methods, labs, and policies. The investigation team should have enough qualifications and high experience to perform the stages of the investigation. To preserve high productivity, the investigation team needs to be continuously trained and updated. The center of any investigation is the forensic tools, which should be carefully selected by senior investigators. The selection of improper investigation tools may result in the failed stages of the investigation and lost evidence. A reliable and clear investigation can be assumed by assessing and updating the existing investigation policies, guidelines, and procedures.
- Archiving the digital pieces of evidence: All the incident-related data will be deleted with the exemption of digital evidence that will be securely archived for further legal purposes.
- Developing the investigation repository: All the investigation stages are kept with an investigation repository, allowing practitioners to quickly access the previous investigations information and use it again for similar cases.
- Recommendations: The weakness of the existing forensic workstations can be improved by translating the assessment at step 1 to new guidelines.
- Improving the drone security measures: There is a need for enabled and audited security measures, such as access control for the mitigation of the drone breaches. This stage aims to improve the security measures for the prevention of drone incidents. It involves several procedures:
- Assessing preventive security procedures: The integrity, confidentiality, and availability of the information systems are protected based on the security measures as significant components. To accomplish the security objectives, it is necessary to continuously assess the preventive security procedures. Thus, the data should be kept secure by reassessing and improving the current drone security measures such as IDS, access control, auditing feature, and firewalls. On the other hand, all CCAFM processes are subject to the laws of countries in terms of privacy when acquiring information. In fact, this is one of the biggest challenges facing investigators. Some laws do not allow data to be collected without permission from the authorities. For example, there is a need to strike a balance between what is acceptable for private use and what is not. Currently, there are laws being created by both state and federal agencies. Many of these laws revolve around the first and fourth amendments. In particular, the need to know the location of the drone when it is recording is critical for privacy. Some states are simply banning them outright, while others are more focused on what is allowed and what is not. One example is laws against drones carrying weapons. The state of Connecticut, USA, proposed a law to restrict/prohibit putting guns on drones after a man posted a video of his drone flying with a gun and shooting. Thus, all the processes of the proposed CCAFM should follow the laws of the state where the crime happened in terms of privacy.
- Identifying preventive measures: It may prove dangerous someday to see no preventive measures in the drone system for monitoring outsider or insider attacks. Thus, preventive drone measures must be enabled and assessed continuously to keep data secure.
- Monitoring incidents: The post-incident activities have been closely monitored since the reappearance of threat actors. We suggest that a security log hawk should analyze the security information and event monitoring (SIEM) data to see any signs of indicators tripping associated with the previous incident.
- Completing an analysis report: The incident will be documented to augment additional security measures and improve the incident response plan to prevent such security events in the future. The report needs to answer the following questions: how logging is done, what are the intrusion detection systems (IDS), what is logged, and what are the forensic acquisition, reconstruction, preparation, and analyzing methods, and tools.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Mohamed, N.; Al-Jaroodi, J.; Jawhar, I.; Idries, A.; Mohammed, F. Unmanned aerial vehicles applications in future smart cities. Technol. Forecast. Soc. Chang. 2020, 153, 119293. [Google Scholar] [CrossRef]
- Yu, K.-P.; Tan, L.; Aloqaily, M.; Yang, H.; Jararweh, Y. Blockchain-enhanced data sharing with traceable and direct revocation in IIoT. IEEE Trans. Ind. Inform. 2021, 17, 7669–7678. [Google Scholar] [CrossRef]
- Yu, K.; Arifuzzaman, M.; Wen, Z.; Zhang, D.; Sato, T. A key management scheme for secure communications of information centric advanced metering infrastructure in smart grid. IEEE Trans. Instrum. Meas. 2015, 64, 2072–2085. [Google Scholar]
- Tan, L.; Yu, K.; Shi, N.; Yang, C.; Wei, W.; Lu, H. Towards secure and privacy-preserving data sharing for covid-19 medical records: A blockchain-empowered approach. IEEE Trans. Netw. Sci. Eng. 2021, 9, 271–281. [Google Scholar] [CrossRef]
- Tan, L.; Yu, K.; Ming, F.; Cheng, X.; Srivastava, G. Secure and resilient artificial intelligence of things: A HoneyNet approach for threat detection and situational awareness. IEEE Consum. Electron. Mag. 2021, 11, 69–78. [Google Scholar] [CrossRef]
- Tan, L.; Yu, K.; Lin, L.; Cheng, X.; Srivastava, G.; Lin, J.C.-W.; Wei, W. Speech emotion recognition enhanced traffic efficiency solution for autonomous vehicles in a 5G-enabled space-air-ground integrated intelligent transportation system. IEEE Trans. Intell. Transp. Syst. 2021, 23, 2830–2842. [Google Scholar] [CrossRef]
- Awan, S.; Ahmed, S.; Ullah, F.; Nawaz, A.; Khan, A.; Uddin, M.I.; Alharbi, A.; Alosaimi, W.; Alyami, H. IoT with blockchain: A futuristic approach in agriculture and food supply chain. Wirel. Commun. Mob. Comput. 2021, 2021, 5580179. [Google Scholar] [CrossRef]
- Li, H.; Yu, K.; Liu, B.; Feng, C.; Qin, Z.; Srivastava, G. An efficient ciphertext-policy weighted attribute-based encryption for the internet of health things. IEEE J. Biomed. Health Inform. 2021, 26, 1949–1960. [Google Scholar] [CrossRef] [PubMed]
- Saif, A.; Dimyati, K.; Noordin, K.A.; C, D.G.; Shah, N.S.M.; Abdullah, Q.; Mohamad, M. An efficient energy harvesting and optimal clustering technique for sustainable postdisaster emergency communication systems. IEEE Access 2021, 9, 78188–78202. [Google Scholar] [CrossRef]
- Feng, C.; Liu, B.; Guo, Z.; Yu, K.; Qin, Z.; Choo, K.-K.R. Blockchain-based cross-domain authentication for intelligent 5g-enabled internet of drones. IEEE Internet Things J. 2021, 9, 6224–6238. [Google Scholar] [CrossRef]
- Feng, C.; Liu, B.; Yu, K.; Goudos, S.K.; Wan, S. Blockchain-empowered decentralized horizontal federated learning for 5G-enabled UAVs. IEEE Trans. Ind. Inform. 2021, 18, 3582–3592. [Google Scholar] [CrossRef]
- Ullah, F.; Pun, C.-M. The Role of Internet of Things for Adaptive Traffic Prioritization in Wireless Body Area Networks. In Healthcare Paradigms in the Internet of Things Ecosystem; Elsevier: Amsterdam, The Netherlands, 2021; pp. 63–82. [Google Scholar]
- Feng, C.; Yu, K.; Aloqaily, M.; Alazab, M.; Lv, Z.; Mumtaz, S. Attribute-based encryption with parallel outsourced decryption for edge intelligent IoV. IEEE Trans. Veh. Technol. 2020, 69, 13784–13795. [Google Scholar] [CrossRef]
- Ding, F.; Zhu, G.; Alazab, M.; Li, X.; Yu, K. Deep-learning-empowered digital forensics for edge consumer electronics in 5G HetNets. IEEE Consum. Electron. Mag. 2020, 11, 42–50. [Google Scholar] [CrossRef]
- Ding, F.; Yu, K.; Gu, Z.; Li, X.; Shi, Y. Perceptual enhancement for autonomous vehicles: Restoring visually degraded images for context prediction via adversarial training. IEEE Trans. Intell. Transp. Syst. 2021, 23, 9430–9441. [Google Scholar] [CrossRef]
- Al-Dhaqm, A.; Ikuesan, R.; Kebande, V.; Razak, S.; Ghabban, F. Research Challenges and Opportunities in Drone Forensics Models. Electronics 2021, 10, 1519. [Google Scholar] [CrossRef]
- Ding, F.; Zhu, G.; Li, Y.; Zhang, X.; Atrey, P.K.; Lyu, S. Anti-forensics for face swapping videos via adversarial training. IEEE Trans. Multimed. 2021, 24, 3429–3441. [Google Scholar] [CrossRef]
- Zhou, Z.; Dong, X.; Li, Z.; Yu, K.; Ding, C.; Yang, Y. Spatio-Temporal Feature Encoding for Traffic Accident Detection in VANET Environment. IEEE Trans. Intell. Transp. Syst. 2022, 1–10. [Google Scholar] [CrossRef]
- Kovar, D.; Dominguez, G.; Murphy, C. UAV (aka drone) Forensics. In Proceedings of the SANS DFIR Summit, Austin, TX, USA, 23–24 June 2016; pp. 23–24. [Google Scholar]
- Mhatre, V.; Chavan, S.; Samuel, A.; Patil, A.; Chittimilla, A.; Kumar, N. Embedded video processing and data acquisition for unmanned aerial vehicle. In Proceedings of the 2015 International Conference on Computers, Communications, and Systems (ICCCS), Kanyakumari, India, 2–3 November 2015; pp. 141–145. [Google Scholar]
- Yu, K.; Tan, L.; Lin, L.; Cheng, X.; Yi, Z.; Sato, T. Deep-learning-empowered breast cancer auxiliary diagnosis for 5GB remote E-health. IEEE Wirel. Commun. 2021, 28, 54–61. [Google Scholar] [CrossRef]
- Yu, K.; Tan, L.; Mumtaz, S.; Al-Rubaye, S.; Al-Dulaimi, A.; Bashir, A.K.; Khan, F.A. Securing critical infrastructures: Deep-Learning-Based threat detection in IIoT. IEEE Commun. Mag. 2021, 59, 76–82. [Google Scholar] [CrossRef]
- Roder, A.; Choo, K.-K.R.; Le-Khac, N.-A. Unmanned aerial vehicle forensic investigation process: Dji phantom 3 drone as a case study. arXiv 2018, arXiv:1804.08649. [Google Scholar]
- Horsman, G. Unmanned aerial vehicles: A preliminary analysis of forensic challenges. Digit. Investig. 2016, 16, 1–11. [Google Scholar] [CrossRef]
- Procházka, T. Capturing, Visualizing, and Analyzing Data from Drones. Bachelor Thesis, Charles University, Staré Město, Czech Republic, 2016. [Google Scholar]
- Mohan, M. Cybersecurity in Drones; Utica College: Utica, NY, USA, 2016. [Google Scholar]
- Jain, U.; Rogers, M.; Matson, E.T. Drone forensic framework: Sensor and data identification and verification. In Proceedings of the 2017 IEEE Sensors Applications Symposium (SAS), Glassboro, NY, USA, 13–15 March 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Clark, D.R.; Meffert, C.; Baggili, I.; Breitinger, F. DROP (DRone open source parser) your drone: Forensic analysis of the DJI phantom III. Digit. Investig. 2017, 22, S3–S14. [Google Scholar] [CrossRef]
- Prastya, S.E.; Riadi, I.; Luthfi, A. Forensic Analysis of Unmanned Aerial Vehicle to Obtain GPS Log Data as Digital Evidence. Int. J. Comput. Sci. Inf. Secur. 2017, 15, 280–285. [Google Scholar]
- Llewellyn, M. DJI Phantom 3-Drone Forensic Data Exploration; Edith Cowan University: Perth, Australia, 2017. [Google Scholar]
- Renduchintala, A.L.P.S.; Albehadili, A.; Javaid, A.Y. Drone Forensics: Digital Flight Log Examination Framework for Micro Drones. In Proceedings of the 2017 International Conference on Computational Science and Computational Intelligence (CSCI), Las Vegas, NV, USA, 14–16 December 2017; pp. 91–96. [Google Scholar] [CrossRef]
- Barton, T.E.A.; Bin Azhar, M.H. Forensic analysis of popular UAV systems. In Proceedings of the 2017 Seventh International Conference on Emerging Security Technologies (EST), Canterbury, UK, 6–8 September 2017; pp. 91–96. [Google Scholar] [CrossRef]
- Maune, K.G. A Project Completed as Part of the Requirements for BSc (Hons) Computer Forensic Investigation. 2018. Available online: https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.1025.4878&rep=rep1&type=pdf (accessed on 3 March 2021).
- Benzarti, S.; Triki, B.; Korbaa, O. Privacy preservation and drone authentication using Id-Based Signcryption. Front. Artif. Intell. Appl. 2018, 303, 226–239. [Google Scholar] [CrossRef]
- Renduchintala, A.; Jahan, F.; Khanna, R.; Javaid, A.Y. A comprehensive micro unmanned aerial vehicle (UAV/Drone) forensic framework. Digit. Investig. 2019, 30, 52–72. [Google Scholar] [CrossRef]
- Dawam, E.S.; Feng, X.; Li, D. Autonomous Arial Vehicles in Smart Cities: Potential Cyber-Physical Threats. In Proceedings of the 2018 IEEE 20th International Conference on High Performance Computing and Communications; IEEE 16th International Conference on Smart City; IEEE 4th International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Exeter, UK, 28–30 June 2018; IEEE: New York, NY, USA, 2018; pp. 1497–1505. [Google Scholar]
- Esteves, J.L.; Cottais, E.; Kasmi, C. Unlocking the Access to the Effects Induced by IEMI on a Civilian UAV. In Proceedings of the 2018 International Symposium on Electromagnetic Compatibility (EMC EUROPE), Amsterdam, The Netherlands, 27–30 August 2018; pp. 48–52. [Google Scholar]
- Fitwi, A.; Chen, Y.; Zhou, N. An Agent-Administrator-Based Security Mechanism for Distributed Sensors and Drones for Smart Grid Monitoring; SPIE: Philadelphia, PA, USA, 2019; p. 11018. [Google Scholar] [CrossRef]
- Jones, Z.V.; Gwinnett, C.; Jackson, A.R. The effect of tape type, taping method and tape storage temperature on the retrieval rate of fibres from various surfaces: An example of data generation and analysis to facilitate trace evidence recovery validation and optimisation. Sci. Justice 2019, 59, 268–291. [Google Scholar] [CrossRef]
- Salamh, F.E.; Rogers, M. Drone Disrupted Denial of Service Attack (3DOS): Towards an Incident Response and Forensic Analysis of Remotely Piloted Aerial Systems (RPASs). In Proceedings of the 2019 15th International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 704–710. [Google Scholar]
- Esteves, J.L. Electromagnetic Watermarking: Exploiting IEMI effects for forensic tracking of UAVs. In Proceedings of the 2019 International Symposium on Electromagnetic Compatibility-EMC EUROPE, Barcelona, Spain, 2–6 September 2019; pp. 1144–1149. [Google Scholar] [CrossRef]
- Mei, N. Unmanned Aircraft Systems Forensics Framework an Approach to Unmanned Aircraft Systems Forensics Framework. Ph.D. Thesis, Capitol Technology University, South Laurel, MD, USA, 2019. [Google Scholar]
- Sciancalepore, S.; Ibrahim, O.A.; Oligeri, G.; Di Pietro, R. Detecting drones status via encrypted traffic analysis. In Proceedings of the ACM Workshop on Wireless Security and Machine Learning, Miami, FL, USA, 14 May 2019; pp. 67–72. [Google Scholar] [CrossRef]
- Yihunie, F.L.; Singh, A.K.; Bhatia, S. Assessing and Exploiting Security Vulnerabilities of Unmanned Aerial Vehicles. Smart Innov. Syst. Technol. 2020, 141, 701–710. [Google Scholar] [CrossRef]
- Mistry, N.R.; Sanghvi, H.P. Drone forensics: Investigative guide for law enforcement agencies. Int. J. Electron. Secur. Digit. Forensics 2021, 13, 334–345. [Google Scholar] [CrossRef]
- Yang, C.-C.; Chuang, H.; Kao, D.-Y. Drone Forensic Analysis Using Relational Flight Data: A Case Study of DJI Spark and Mavic Air. Procedia Comput. Sci. 2021, 192, 1359–1368. [Google Scholar] [CrossRef]
- Alotaibi, F.M.; Al-Dhaqm, A.; Al-Otaibi, Y.D. A Novel Forensic Readiness Framework Applicable to the Drone Forensics Field. Comput. Intell. Neurosci. 2022, 2022, 1–13. [Google Scholar] [CrossRef]
- Atkinson, S.; Carr, G.; Shaw, C.; Zargari, S. Drone Forensics: The Impact and Challenges. In Digital Forensic Investigation of Internet of Things (IoT) Devices; Springer: Berlin/Heidelberg, Germany, 2021; pp. 65–124. [Google Scholar]
- Lan, J.K.W.; Lee, F.K.W. Drone Forensics: A Case Study on DJI Mavic Air 2. In Proceedings of the 2022 24th International Conference on Advanced Communication Technology (ICACT), Virtual Conference, 13–16 February 2022; pp. 291–296. [Google Scholar]
- Husnjak, S.; Forenbacher, I.; Peraković, D.; Cvitić, I. UAV Forensics: DJI Mavic Air Noninvasive Data Extraction and Analysis. In Proceedings of the 5th EAI International Conference on Management of Manufacturing Systems, Krynica-Zdrój, Poland, 5–7 October 2022; pp. 115–127. [Google Scholar]
- Parghi, P.; Dhamija, R.; Agrawal, A.K. Innovative Approach to Onboard Media Forensic of a Drone. In IOT with Smart Systems; Springer: Berlin/Heidelberg, Germany, 2022; pp. 307–314. [Google Scholar]
- Alhussan, A.A.; Al-Dhaqm, A.; Yafooz, W.M.S.; Emara, A.-H.M.; Razak, S.B.A.; Khafaga, D.S. A Unified Forensic Model Applicable to the Database Forensics Field. Electronics 2022, 11, 1347. [Google Scholar] [CrossRef]
- Alhussan, A.A.; Al-Dhaqm, A.; Yafooz, W.M.S.; Razak, S.B.A.; Emara, A.-H.M.; Khafaga, D.S. Towards Development of a High Abstract Model for Drone Forensic Domain. Electronics 2022, 11, 1168. [Google Scholar] [CrossRef]
- Bertino, E.; Kantarcioglu, M.; Akcora, C.G.; Samtani, S.; Mittal, S.; Gupta, M. AI for Security and Security for AI. In Proceedings of the Eleventh ACM Conference on Data and Application Security and Privacy, Virtual, 26–28 April 2021; pp. 333–334. [Google Scholar]
- Nadkarni, P.M.; Ohno-Machado, L.; Chapman, W.W. Natural language processing: An introduction. J. Am. Med. Inform. Assoc. 2011, 18, 544–551. [Google Scholar] [CrossRef]
- Murphy, R.R. Introduction to AI robotics; MIT Press: Cambridge, MA, USA, 2019. [Google Scholar]
- Abdallah, A.; Maarof, M.A.; Zainal, A. Fraud detection system: A survey. J. Netw. Comput. Appl. 2016, 68, 90–113. [Google Scholar] [CrossRef]
- Kulik, S.D. Neural network model of artificial intelligence for handwriting recognition. J. Theor. Appl. Inf. Technol. 2015, 73, 1–10. [Google Scholar]
- Voronin, V.V.; Marchuk, V.I.; Semenishchev, E.A.; Makov, S.V.; Creutzburg, R. Digital inpainting with applicataions to forensic image processing. Electron. Imaging 2016, 28, 1–7. [Google Scholar]
- Oladipo, F.; Ogbuju, E.; Alayesanmi, F.S.; Musa, A.E. The State of the Art in Machine Learning-Based Digital Forensics. SSRN 2020. [Google Scholar] [CrossRef]
- Alhawiti, K.M. Advances in artificial intelligence using speech recognition. Int. J. Comput. Inf. Eng. 2015, 9, 1432–1435. [Google Scholar]
- Bithas, P.S.; Michailidis, E.T.; Nomikos, N.; Vouyioukas, D.; Kanatas, A.G. A survey on machine-learning techniques for UAV-based communications. Sensors 2019, 19, 5170. [Google Scholar] [CrossRef]
- Hachimi, M.; Kaddoum, G.; Gagnon, G.; Illy, P. Multi-stage jamming attacks detection using deep learning combined with kernelized support vector machine in 5g cloud radio access networks. In Proceedings of the 2020 International Symposium on Networks, Computers and Communications (ISNCC), Montreal, QC, Canada, 20–22 October 2020; pp. 1–5. [Google Scholar]
- Luo, P.; Wang, B.; Li, T.; Tian, J. ADS-B anomaly data detection model based on VAE-SVDD. Comput. Secur. 2021, 104, 102213. [Google Scholar] [CrossRef]
- Xiao, L.; Xie, C.; Min, M.; Zhuang, W. User-centric view of unmanned aerial vehicle transmission against smart attacks. IEEE Trans. Veh. Technol. 2017, 67, 3420–3430. [Google Scholar] [CrossRef]
- Hoang, T.M.; Duong, T.Q.; Tuan, H.D.; Lambotharan, S.; Hanzo, L. Physical layer security: Detection of active eavesdropping attacks by support vector machines. IEEE Access 2021, 9, 31595–31607. [Google Scholar] [CrossRef]
- Ahn, H. Deep learning based anomaly detection for a vehicle in swarm drone system. In Proceedings of the 2020 International Conference on Unmanned Aircraft Systems (ICUAS), Athens, Greece, 1–4 September 2020; pp. 557–561. [Google Scholar]
- Jeong, S.; Bito, J.; Tentzeris, M.M. Design of a novel wireless power system using machine learning techniques for drone applications. In Proceedings of the 2017 IEEE Wireless Power Transfer Conference (WPTC), Taipei, Taiwan, 10–12 May 2017; pp. 1–4. [Google Scholar]
- Sciancalepore, S.; Ibrahim, O.A.; Oligeri, G.; Di Pietro, R. PiNcH: An effective, efficient, and robust solution to drone detection via network traffic analysis. Comput. Netw. 2020, 168, 107044. [Google Scholar] [CrossRef]
- Nemer, I.; Sheltami, T.; Ahmad, I.; Yasar, A.U.-H.; Abdeen, M.A.R. RF-based UAV detection and identification using hierarchical learning approach. Sensors 2021, 21, 1947. [Google Scholar] [CrossRef]
- Shoufan, A.; Al-Angari, H.M.; Sheikh, M.F.A.; Damiani, E. Drone pilot identification by classifying radio-control signals. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2439–2447. [Google Scholar] [CrossRef]
- Park, J.; Kim, Y.; Seok, J. Prediction of information propagation in a drone network by using machine learning. In Proceedings of the 2016 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Korea, 19–21 October 2016; pp. 147–149. [Google Scholar]
- Al-Dhaqm, A.; Razak, S.; Ikuesan, R.A.; Kebande, V.R.; Othman, S.H. Face Validation of Database Forensic Investigation Metamodel. Infrastructures 2021, 6, 13. [Google Scholar] [CrossRef]
- Kebande, V.R.; Ikuesan, R.A.; Karie, N.M. Review of Blockchain Forensics Challenges. In Blockchain Security in Cloud Computing; Springer: Berlin/Heidelberg, Germany, 2022; pp. 33–50. [Google Scholar]
- Kim, J.; Kim, M.-Y.; Kwon, H.; Kim, J.-W.; Im, W.-Y.; Lee, S.M.; Kim, K.; Kim, S.J. Active Machine Learning Adversarial Attack Detection in the User Feedback Process. Forensic Sci. Int. Rep. 2020, 3, 36908–36923. [Google Scholar] [CrossRef]
- Al-Dhaqm, A.; Razak, S.; Othman, S.H.; Choo, K.-K.R.; Glisson, W.B.; Ali, A.; Abrar, M. CDBFIP: Common database forensic investigation processes for Internet of Things. IEEE Access 2017, 5, 24401–24416. [Google Scholar] [CrossRef]
- Kebande, V.R.; Karie, N.M.; Choo, K.R.; Alawadi, S. Digital forensic readiness intelligence crime repository. Secur. Priv. 2021, 4, e151. [Google Scholar] [CrossRef]
- Al-Dhaqm, A.; Razak, S.A.; Ikuesan, R.A.; Kebande, V.R.; Siddique, K. A Review of Mobile Forensic Investigation Process Models. IEEE Access 2020, 8, 173359–173375. [Google Scholar] [CrossRef]
- Makura, S.; Venter, H.S.; Kebande, V.R.; Karie, N.M.; Ikuesan, R.A.; Alawadi, S. Digital forensic readiness in operational cloud leveraging ISO/IEC 27043 guidelines on security monitoring. Secur. Priv. 2021, 4, e149. [Google Scholar] [CrossRef]
- Philomin, S.; Singh, A.; Ikuesan, A.; Venter, H. Digital forensic readiness framework for smart homes. In Proceedings of the International Conference on Cyber Warfare and Security, Albany, NY, USA, 17–18 March 2022. [Google Scholar] [CrossRef]
- Kebande, V.R.; Ikuesan, R.A. Virtual sensor forensics. In Proceedings of the 2nd International Conference on Intelligent and Innovative Computing Applications, Plaine Magnien, Mauritius, 24–25 September 2020. [Google Scholar] [CrossRef]
- Al-Dhaqm, A.; Razak, S.A.; Siddique, K.; Ikuesan, R.A.; Kebande, V.R. Towards the Development of an Integrated Incident Response Model for Database Forensic Investigation Field. IEEE Access 2020, 8, 145018–145032. [Google Scholar] [CrossRef]
- Kelly, S.; Pohjonen, R. Worst practices for domain-specific modeling. IEEE Softw. 2009, 26, 22–29. [Google Scholar] [CrossRef]
- Al-Dhaqm, A.; Razak, S.A.; Othman, S.H.; Ali, A.; Ghaleb, F.A.; Rosman, A.S.; Marni, N. Database forensic investigation process models: A review. IEEE Access 2020, 8, 48477–48490. [Google Scholar] [CrossRef]
- Maarse, M.; Sangers, L.; van Ginkel, J.; Pouw, M. Digital forensics on a DJI Phantom 2 Vision+ UAV. Univ. Amst. 2016, 1, 22. [Google Scholar]
- Bucknell, A.; Bassindale, T. An investigation into the effect of surveillance drones on textile evidence at crime scenes. Sci. Justice 2017, 57, 373–375. [Google Scholar] [CrossRef]
- Bouafif, H.; Kamoun, F.; Iqbal, F.; Marrington, A. Drone Forensics: Challenges and New Insights. In Proceedings of the 2018 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 26–28 February 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Gülataş, İ.; Baktır, S. Unmanned aerial vehicle digital forensic investigation framework. J. Nav. Sci. Eng. 2018, 14, 32–53. [Google Scholar]
- Shi, X.; Yang, C.; Xie, W.; Liang, C.; Shi, Z.; Chen, J. Anti-drone system with multiple surveillance technologies: Architecture, implementation, and challenges. IEEE Commun. Mag. 2018, 56, 68–74. [Google Scholar] [CrossRef]
- Guvenc, I.; Koohifar, F.; Singh, S.; Sichitiu, M.L.; Matolak, D. Detection, tracking, and interdiction for amateur drones. IEEE Commun. Mag. 2018, 56, 75–81. [Google Scholar] [CrossRef]
- Ding, G.; Wu, Q.; Zhang, L.; Lin, Y.; Tsiftsis, T.A.; Yao, Y.-D. An amateur drone surveillance system based on the cognitive Internet of Things. IEEE Commun. Mag. 2018, 56, 29–35. [Google Scholar] [CrossRef]
- Le Roy, F.; Roland, C.; Le Jeune, D.; Diguet, J.-P. Risk assessment of SDR-based attacks with UAVs. In Proceedings of the 2019 16th International Symposium on Wireless Communication Systems (ISWCS), Oulu, Finland, 27–30 August 2019; pp. 222–226. [Google Scholar] [CrossRef]
- Caro, M.F.; Josyula, D.P.; Cox, M.T.; Jiménez, J.A. Design and validation of a metamodel for metacognition support in artificial intelligent systems. Biol. Inspired Cogn. Archit. 2014, 9, 82–104. [Google Scholar] [CrossRef]
- Bogen, A.C.; Dampier, D.A. Preparing for Large-Scale Investigations with Case Domain Modeling. In Proceedings of the 5th Annual Digital Forensic Research Workshop, DFRWS 2005, New Orleans, LA, USA, 17–19 August 2005. [Google Scholar]
- Al-Dhaqm, A.; Razak, S.A.; Dampier, D.A.; Choo, K.-K.R.; Siddique, K.; Ikuesan, R.A.; Alqarni, A.; Kebande, V.R. Categorization and organization of database forensic investigation processes. IEEE Access 2020, 8, 112846–112858. [Google Scholar] [CrossRef]
- Adedayo, O.M.; Olivier, M.S. Schema reconstruction in database forensics. IFIP Adv. Inf. Commun. Technol. 2014, 433, 101–116. [Google Scholar] [CrossRef]
| No | Similar Processes |
|---|---|
| 1. | Collecting Drone Data |
| 2. | Drone Evidence Collection |
| 3. | Collection Drone Process |
| 4. | Drone Items Collection |
| 5. | Drone Data Extraction Process |
| 6. | Starting of Investigation |
| 7. | Drone Metadata Gathering |
| 8. | Drone Data Collection |
| 9. | Collecting Drone Files |
| 10. | Drone Item Collection |
| 11. | Collection process |
| 12. | Collection of Drone Nonvolatile Items |
| 13. | Collection of Drone Volatile Items |
| 14. | Drone Item Collection |
| 15. | Collection Suspect Drone System |
| 16. | Drone Collection and Preservation Process |
| 17. | Collection of Drone Process |
| 18. | Execution of Drone Data |
| 19. | Collection, Preservation |
| 20. | Drone Item Collection |
| 21. | Drone Items Collection |
| 22. | Reconstructing Drone Events |
| 23. | Restoring Drone Integrity |
| 24. | Drone Media Analysis |
| 25. | Timeline Creation of Drone Data |
| 26. | Drone Data Recovery |
| 27. | Search String |
| 28. | Drone Artifact Analysis |
| 29. | Financial and Business Data Analysis |
| 30. | Drone Restoration and Searchability |
| 31. | Investigation on Drone Data Collected |
| 32. | Drone Artifact Analysis |
| 33. | Rebuilding of Drone Data |
| 34. | Reconstruction of Drone Events |
| 35. | Drone Forensic Analysis |
| 36. | Analysis of Anti-forensic Drone Attacks, Analysis of Drone Attack |
| 37. | Reconstructing Drone Evidence |
| 38. | Reconstruction Process |
| 39. | Analysis Process |
| 40. | Reconstructing Drone Volatile Items |
| 41. | Recovering Drone Schema |
| 42. | Analysis of Drone Stages |
| No | Similar Processes |
|---|---|
| 1. | Collecting Drone Data |
| 2. | Drone Evidence Collection |
| 3. | Drone Collection process |
| 4. | Drone Item Collection |
| 5. | Drone Data Extraction Process |
| 6. | Starting the Investigation |
| 7. | Drone Metadata Gathering |
| 8. | Drone Data Collection |
| 9. | Collecting Drone Files |
| 10. | Drone Item Collection |
| 11. | Drone Collection Process |
| 12. | Collection of Drone Nonvolatile Items |
| 13. | Collection of Drone Volatile Items |
| 14. | Drone Items Collection |
| 15. | Collection Suspect Drone System |
| 16. | Collection and Preservation |
| 17. | Drone Collection process |
| 18. | Execution of Drone Data |
| 19. | Collection, Preservation |
| 20. | Drone Items Collection |
| 21. | Drone Items Collection |
| No | Similar Processes |
|---|---|
| 1 | Reconstructing Drone Data |
| 2 | Restoring Drone Integrity |
| 3 | Drone Media Analysis |
| 4 | Timeline Creation of Drone Data |
| 5 | Drone Data Recovery |
| 6 | Search String |
| 7 | Drone Artifact Analysis |
| 8 | Financial and Business Data Analysis |
| 9 | Drone Restoration and Searchability |
| 10 | Investigation on Drone Data Collected |
| 11 | Drone Artifact Analysis |
| 12 | Reconstruction of Drone Data |
| 13 | Reconstruction of the Drone Events |
| 14 | Drone Forensic Analysis |
| 15 | Analysis of Anti-forensic Attacks, Analysis of Drone Attacks |
| 16 | Reconstructing Drone Evidence |
| 17 | Reconstruction Process |
| 18 | Drone Analysis Process |
| 19 | Reconstructing Drone Volatile Items |
| 20 | Recovering Drone Schema |
| 21 | Analysis of Drone Stages |
| ID | Processes in the Compared Models | Processes in the Proposed Model | ||
|---|---|---|---|---|
| Collection and Preservation | Reconstruction and Analysis | Post-Investigation | ||
| 1. | Collecting Drone Data | ✓ | ✓ | × |
| 2. | Drone Evidence Collection | ✓ | ✓ | × |
| 3. | Collection Process | ✓ | ✓ | × |
| 4. | Drone Items Collection | ✓ | ✓ | × |
| 5. | Drone Data Extraction Process | ✓ | ✓ | × |
| 6. | Starting the Investigation | ✓ | ✓ | × |
| 7. | Drone Metadata Gathering | ✓ | ✓ | × |
| 8. | Drone Data Collection | ✓ | ✓ | × |
| 9. | Collecting Drone Files | ✓ | ✓ | × |
| 10. | Drone Items Collection | ✓ | ✓ | × |
| 11. | Drone Collection Process | ✓ | ✓ | × |
| 12. | Collection of Drone Nonvolatile Items | ✓ | ✓ | × |
| 13. | Collection of Drone Volatile Items | ✓ | ✓ | × |
| 14. | Drone Items Collection | ✓ | ✓ | × |
| 15. | Collection of Suspect Drone System | ✓ | ✓ | × |
| 16. | Collection and Preservation | ✓ | ✓ | × |
| 17. | Drone Collection Process | ✓ | ✓ | × |
| 18. | Execution of Drone Data | ✓ | ✓ | × |
| 19. | Collection, Preservation | ✓ | ✓ | × |
| 20. | Drone Items Collection | ✓ | ✓ | × |
| 21. | Drone Items Collection | ✓ | ✓ | × |
| 22. | Reconstructing Drone Data | ✓ | ✓ | × |
| 23. | Restoring Drone Integrity | ✓ | ✓ | × |
| 24. | Drone Media Analysis | ✓ | ✓ | × |
| 25. | Timeline Creation of Drone Data | ✓ | ✓ | × |
| 26. | Drone Data Recovery | ✓ | ✓ | × |
| 27. | Search String | ✓ | ✓ | × |
| 28. | Drone Artifact Analysis | ✓ | ✓ | × |
| 29. | Financial and Business Data Analysis | ✓ | ✓ | × |
| 30. | Drone Restoration and Searchability | ✓ | ✓ | × |
| 31. | Investigation on Drone Data Collected | ✓ | ✓ | × |
| 32. | Drone Artifact Analysis | ✓ | ✓ | × |
| 33. | Rebuilding of Drone Data | ✓ | ✓ | × |
| 34. | Reconstruction of the Drone Events | ✓ | ✓ | × |
| 35. | Drone Forensic Analysis | ✓ | ✓ | × |
| 36. | Analysis of Anti-forensic Attacks, Analysis of Drone Attack | ✓ | ✓ | × |
| 37. | Reconstructing Drone Evidence | ✓ | ✓ | × |
| 38. | Reconstruction Drone Process | ✓ | ✓ | × |
| 39. | Drone Analysis Process | ✓ | ✓ | × |
| 40. | Reconstructing Drone Volatile Items | ✓ | ✓ | × |
| 41. | Recovering Drone Schema | ✓ | ✓ | × |
| 42. | Analysis of Drone Stages | ✓ | ✓ | × |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alotaibi, F.M.; Al-Dhaqm, A.; Al-Otaibi, Y.D.; Alsewari, A.A. A Comprehensive Collection and Analysis Model for the Drone Forensics Field. Sensors 2022, 22, 6486. https://doi.org/10.3390/s22176486
Alotaibi FM, Al-Dhaqm A, Al-Otaibi YD, Alsewari AA. A Comprehensive Collection and Analysis Model for the Drone Forensics Field. Sensors. 2022; 22(17):6486. https://doi.org/10.3390/s22176486
Chicago/Turabian StyleAlotaibi, Fahad Mazaed, Arafat Al-Dhaqm, Yasser D. Al-Otaibi, and Abdulrahman A. Alsewari. 2022. "A Comprehensive Collection and Analysis Model for the Drone Forensics Field" Sensors 22, no. 17: 6486. https://doi.org/10.3390/s22176486
APA StyleAlotaibi, F. M., Al-Dhaqm, A., Al-Otaibi, Y. D., & Alsewari, A. A. (2022). A Comprehensive Collection and Analysis Model for the Drone Forensics Field. Sensors, 22(17), 6486. https://doi.org/10.3390/s22176486







