Abstract
In recent times, Wireless Sensor Networks (WSNs) are becoming more and more popular and are making significant advances in wireless communication thanks to low-cost and low-power sensors. However, since WSN nodes are battery-powered, they lose all of their autonomy after a certain time. This energy restriction impacts the network’s lifetime. Clustering can increase the lifetime of a network while also lowering energy use. Clustering will bring several similar sensors to one location for data collection and delivery to the Base Station (BS). The Cluster Head (CH) uses more energy when collecting and transferring data. The life of the WSNs can be extended, and efficient identification of CH can minimize energy consumption. Creating a routing algorithm that considers the key challenges of lowering energy usage and maximizing network lifetime is still challenging. This paper presents an energy-efficient clustering routing protocol based on a hybrid Mayfly-Aquila optimization (MFA-AOA) algorithm for solving these critical issues in WSNs. The Mayfly algorithm is employed to choose an optimal CH from a collection of nodes. The Aquila optimization algorithm identifies and selects the optimum route between CH and BS. The simulation results showed that the proposed methodology achieved better energy consumption by 10.22%, 11.26%, and 14.28%, and normalized energy by 9.56%, 11.78%, and 13.76% than the existing state-of-art approaches.
1. Introduction
WSNs comprise many low-energy sensors with substantial sink power responsible for establishing paths within specified transmission protocols [1]. WSNs are used in dynamic networks because of their ease of installation and quick synchronization with other sensors. WSN sensors can sense, gather, and send data in real-time [2]. Systematizing sensor networks into clustered frameworks has received much attention recently, resulting in many organizations developing their clustering methods [3].
Clustering is a basic methodology for designing energy-efficient, reliable, and flexible distributed sensor networks. Clustering decreases correspondence overhead, lowering energy consumption and impedance among the SNs [4]. The ultimate objective is to exploit the interaction between the sensors and eliminate the frequent repetition. Combining existing data with data acquired by sensors at CHs, the total amount of data transmitted to the sink may be drastically reduced [5].
While cluster-based sensor network connection and inclusion support protocols had previously been discussed, they have not been organized systematically [6]. Existing approaches for selecting CH nodes are based on various parameters, including the highest residual energy, area of the CH concerning alternate nodes, topological data, and last movement of the SN as a CH [7]. Most of these CH selection approaches ignore the network’s requirement for complete inclusion over long periods [8]. When removing nodes from regions that are sparsely populated with SNs, the passing of an SN issued in a densely populated territory has a lower impact on network inclusion. The importance of each SN to the incorporation endeavor may be quantified using an inclusion-conscious cost metric. This cost metric considers the node’s incredible energy and the inclusion outside its detecting range, measuring the node’s contribution to the network’s inclusion concerns [9].
In this sense, this article looked into the differences between energy-adjusted and inclusion-conscious sensor network association, with a particular focus on clustered WSNs. The traditional method is insufficient for effective CH selection. The main reason is that the node may shift from one cluster area to the other, making it difficult to choose a CH. As a result, the shortest path selection for RN is proposed to solve this problem, allowing data transfer even when the cluster zone changes [10]. Moreover, all these operations must be completed efficiently to avoid wasting the restricted sensor battery life. The sensor’s life cannot be increased by providing external or extra energy since most sensors are placed in difficult-to-reach locations. A network system with too many dead nodes may become paralyzed and unable to function correctly [11]. Therefore, it is not very easy for WSNs to develop energy-balanced and energy-efficient routing algorithms.
The lifespan of a network may be successfully extended by balancing the energy usage of nodes and enhancing energy efficiency. By separating nodes into many clusters, hierarchical clustering methods lengthen the network lifespan [12]. Clustering protocols attempt to identify the best CH set and rotate the function of the CH across all nodes for the optimization of node energy usage. The chosen CHs should significantly influence the clustering protocol’s performance.
Meta-heuristic optimization techniques are the best alternative for selecting appropriate CHs to extend the network’s lifespan. There are also many interesting applications of heuristics in different technical fields such as optimization in electric systems [13] and remote sensing models [14]. However, the algorithms face several common difficulties, such as fast convergence, local search concerns in the fitness function, and increased cost. Meta-heuristic algorithms are preferred when searching for the optimal solution becomes exhausting. Efficient meta-heuristic algorithms must include the solution space where there is a global optimum and develop novel and better solutions. There are meta-heuristic algorithms such as Particle Swarm Optimization (PSO) and Cuckoo Search that strive for global optimization (Exploration) and methods such as Simulated Annealing (SA) and Harmony Search Algorithm (HSA) that are restricted to local optima in the literature. For a better solution, a balance between exploration and exploitation is required. This prompted the combination of two popular meta-heuristic algorithms, MFA and AOA.
This research presents a hybrid Mayfly-Aquila optimization technique for an energy-efficient clustered routing protocol in WSNs to address earlier mentioned difficulties. To minimize energy consumption, this work proposes to include energy consumption as a node choosing the path. For that, the following tasks must be prioritized:
- i.
- The shortest route between BS and CH because of its usage of less energy.
- ii.
- The selection of CH between clusters.
MFA is a new evolving meta-heuristic that has a higher potential for finding the optimum solution than PSO and can identify more optimal solutions. Premature convergence may decrease the eventual solution’s quality in some cases. Combining an algorithm with high exploration skills with another approach with strong exploitation characteristics is possible. The MFA approach successfully explores the search space, whereas the AOA algorithm utilizes and improves existing feature subsets.
The following are the research’s key contributions:
- In the WSN, Mayfly is employed to determine the CH because of its excellent stability and low computing cost. Mayfly chooses the CH in this research based on many objective values, including residual energy, the distance between neighboring nodes, the distance towards the BS, density of the nodes, and node centrality.
- AOA determines the shortest route between CH and BS because of its capability of delivering speed detection of solutions. To address the constraint of the unpredictable convergence time, the AOA is optimized using residual energy, the density of the node, and distance.
- The network lifetime is increased due to the efficient CH selection and optimal path creation for data transmission. Furthermore, by reducing the energy usage of the nodes while transferring data packets, the total number of packets retrieved by the BS is enhanced.
2. Related Works
In this section, the main related works in the area are analyzed to justify the need for the proposed work.
Murugadass, G. and Sivakumar, P. (2020) [15] presented a hybrid approach of Elephant Herding Optimization with a Cultural Algorithm for optimum CH selection (EHO-CA) to increase the lifespan. The advantages of the belief space provided by the cultural algorithm were used to define a separation operator that effectively created different local optimum solutions in the search space in this presented EHO-CA approach. Moreover, the addition of belief space assisted in providing the balance between an ideal exploitation and exploration process and better search abilities in the selection of optimal CH. The presented EHO-CA method improved the distinguishing qualities by combining separation and clan updating operators for optimal selection of CH to increase the network’s lifespan. The limitation of this proposed method was that it required more processing time.
For obtaining an extended network lifespan in sensor networks, Rambabu et al. (2019) [16] proposed a combined Artificial Bee Colony (ABC) and Bacterial Foraging (BF) (ABC-BF) based clustering method. The benefits of Bacterial Foraging Optimization were integrated with this proposed ABC-BFA approach for enhancing the local search ability of the ABC algorithm to achieve maximal exploitation and exploration of the parameters evaluated for the selection of CH. The proposed ABC-BFA approach was assessed in simulations utilizing a percentage of living and dead nodes and throughput using various SNs in the network. However, the packet drop in the proposed technique was high.
Tabatabaei et al. (2019) [17] investigated clustering SN to improve WSN lifespan. The Lion pride optimizer algorithm reduced energy consumption by grouping SN into clusters. For picking the best nodes as CHs, this method used two criteria: battery power range and distance from the sink. The remaining nodes that were not CHs are then joined to the CH closest to them. Clusters were produced in this manner. After clusters were constructed, data routing was facilitated by a direct virtual backbone, which was based in the sink node and made up of CHs. However, from the results, it was identified that the proposed method has a high processing overhead and attained less throughput.
Through the development of the Rider-Cat Swarm Optimization (RCSO) algorithm for beginning communication in SN, Shyjith et al. (2021) [18] built a platform for data transfer in WSN. The proposed RCSO method, which incorporated the ROA in the CSO algorithm, was used to build the CHs of the WSN nodes, and the CHs aid communication with the ideal CH, determined using the fitness function. The network was first established with initial energy, and the node mobility was regulated using the mobility model. During the setup phase, the CHs for data transmission from the nodes to the BS were determined using the clustering algorithm, which was created by determining the best threshold and CHs using the proposed RCSO method. Following the selection of the CHs, data transfer from the CH to the BS commenced. However, this method did not consider the Quality of Service (QoS) metric.
Poonguzhali and Ananthamoorthy (2020) [19] proposed a novel routing protocol based on Ant Colony Optimization (ACO) and HSA with optimum parameter selection. This research looked at how to send packets quicker without sacrificing data quality. The results demonstrated that the proposed strategy is more effective than other ways of increasing the network’s energy efficiency. However, the limitation of this work was that it only allowed for a meta-heuristic approach, which may have restricted utility in recovering prior network routing parameters.
Wang et al. (2020) [20] investigated the topic of reducing WSN energy consumption and proposed an energy-efficient routing protocol relying on an enhanced ABC algorithm. This research employed the modified ABC method to optimize the fuzzy C-means clustering and pick the optimal CH. In addition, this article employed a polling control access method based on busy/idle nodes, which conserved energy and improved network throughput. According to the simulation findings, the proposed method performed well in energy usage balance, power efficiency, network lifespan, network stability duration, and network throughput. Nevertheless, the developed algorithm could only be used in fixed networks.
Hassan et al. (2020) [21] proposed an enhanced energy-efficient clustering protocol to increase the lifetime of WSN-based IoT networks by addressing clustering structure issues that decrease protocol performance. By optimizing the clustering structure, the proposed technique lowered and balanced the power usage of nodes. As a result, the presented protocol was declared viable for networks with a longer lifespan requirement. In addition, the proposed method used a novel goal function to choose CHs in ideal locations. Though, uncertainty is a big concern with this model.
Al Mazaideh and Levendovszky (2021) [22] developed a method for determining the optimal values of direct detection of paradigm elements by multiple objective genetic algorithms. It was discovered that adjusting these factors will optimize energy efficiency while reducing the likelihood of reconstruction error. The proposed method achieved a fair balance between these two goals. They also devised a compressive sensing approach to conserve energy by decreasing the length of the sensing vector. When the proposed algorithms were evaluated to the performance of typical cluster selection algorithms, it was discovered that they had greater energy efficiency. However, the complexity of this technique was high.
Osamy et al. (2020) [23] introduced the hybrid Chicken Swarm- GA (CSGA) clustering algorithm, in which the CSO algorithm was updated to optimize the energy utilisation in WSNs, to enhance network lifespan. CSGA used a hierarchal order approach. The population was separated into three groups and then sorted according to fitness values to choose the finest nodes that function as CHs every round. To enhance population variety, CSGA used crossover and mutation mechanisms. In addition, the fitness function was created to reduce the overall amount of energy spent and the total number of times the chosen set of nodes worked as CHs. However, this method failed to address the network heterogeneity.
To tackle the optimal data transmission routing path in WSNs, Zhang et al. (2021) [24] proposed a unique and efficient Robust ACO (RACO) method based on ACO. The proposed method comprehensively considers power consumption, node distance, and connection security, improving ACO’s heuristic value. Furthermore, the numerical testing revealed that the RACO approach was resilient and improved network overhead performance without raising network design, operation, or communication. However, the proposed method has a higher computational cost.
To prolong the lifetime of heterogeneous WSNs, Li et al. (2020) [25] developed a Modified GA (MGA). In contrast to prior studies, MGA represented solutions using two-level organized chromosomes. The value of this chromosome was that it represented the exact scheduling of each set and the detailed energy allotment of each sensor. For the generation of the initial population, a greedy strategy was used. This approach has a temporal complexity. However, it considerably increases the pace of searching. Forward and backward mutation procedures were created as unique mutation operations. The forward mutation ensures chromosomal variety, whereas the backward mutation can aid in efficiently leaping out of local optima. However, scalability and mobility were not provided in this approach.
Li et al. (2019) [26] proposed a unique Load Balancing Ant-based routing protocol (LBAR) for WSNs. Under the limits of a limited energy supply, LBAR aimed to balance energy consumption, extend network lifetime, and speed up route-finding convergence. In the development of LBAR, a pseudo-random method was used to find routes, which speeds up the search for an efficient route and considers the energy balance. Furthermore, the pheromone trail updating mechanism took energy and path length information into account, resulting in a network lifespan extension. However, this method was unable to determine the cluster technique’s optimality.
Elsmany et al. (2019) [27] introduced the energy-efficient Scalable Routing Technique (SRA), a flexible, low-energy, and adaptive clustering hierarchical routing algorithm to sustain network lifespan despite network size growth. To minimize the stress on CH, SRA implemented a three-layer hierarchy structure and used multi-hop broadcast for intra-cluster communication. In this work, SRA was compared to different WSN routing schemes using network performance as a function of network size changes. According to simulation data, SRA outperformed benchmarking techniques through load balancing and energy efficiency for WSNs. However, this proposed method did not analyze the computational time and complexity.
Zhou et al. (2019) [28] presented Privacy-Preserving Data Aggregation (PPDA), a new aggregating technique that is both energy-efficient and secure. A sensor network was structured into an aggregation tree, and the leaf nodes of the tree were connected to form multiple chains, according to the proposed strategy. It reduced the number of leaf nodes in the basic aggregation tree. The simulation study findings revealed that the proposed algorithm is more efficient when compared to conventional aggregation techniques while maintaining superior privacy protection. PPDA performed well in terms of efficiency and accuracy of aggregation outputs. However, this technique was unable to develop a data aggregation model to reduce duplicate data.
It has been discovered that a great deal of effort has gone into controlling CH selection and improving data transfer across SN while the sink is moving. However, there has been a sprinkling of research that has concentrated on both aspects at the same time using any hybrid strategy. Using a hybrid method to combine the best features of both optimization techniques to obtain the best network performance.
3. Proposed MFA-AOA Algorithm
CHs are chosen using a formula based on the node’s various properties in traditional protocols. Even though these approaches are easy and simple to apply, they do not consider suitable criteria for choosing CHs. Although metaheuristic-based methods are more efficient in picking optimal CHs than classical techniques, they suffer from high time and computational difficulties since an iterative algorithm must be used to identify CHs at each round. The three categories mentioned above all have the disadvantage of not being application-specific. Therefore, the controllable parameters cannot be adaptively altered to meet the application’s needs. Though these procedures may provide acceptable results in certain situations, their effectiveness may be compromised in others. Furthermore, most present protocols do not use adequate criteria for selecting CHs (during the clustering phase) and forwarders (during the multi-hop routing phase). The proposed MFA-AOA is offered to address the problems mentioned earlier.
By altering the components, an optimization strategy is utilized to reduce or maximize a function’s output. All viable options for this problem are referred to as possible solutions, and the best is referred to as the optimal solution. All swarm intelligence algorithms are population-based, which means that their iterative approach improves the position of individuals in the population and, as a result, their progress toward better positions. The network model, energy model, Mayfly optimization description, and Aquila optimization technique are all covered in this section. Figure 1 depicts the construction of the WSN. The following factors are used to develop the network model:
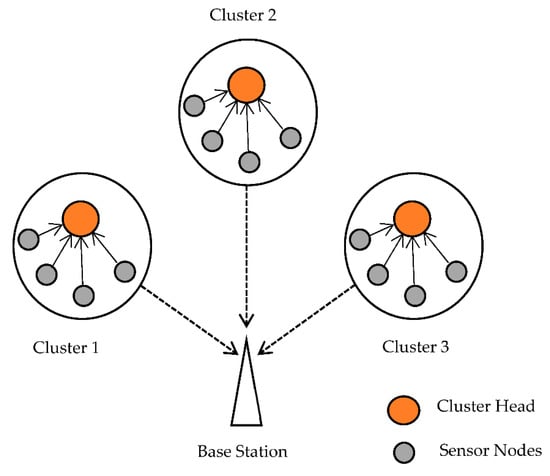
Figure 1.
Construction of WSN.
- All SNs starting energy and process time in a WSN are comparable.
- The Euclidean distance formula is used to compute the distance between the sensors
- The SNs are placed in the sensing region at random, and their position remains constant after installation
- The SNs send information to BS regarding the reserve energy and distance. An efficient CH selection method is used to choose CHs for all SNs based on that data. The routing procedure is then employed to find the optimal path between the CHs and the BS [29].
3.1. Energy Model
A 1st order radio model computes the transmitter and receiver energy. Equations (1) and (2) represent the amount of energy used to send and collect bit packets over a given distance [30].
where is the amount of energy released at the transmitter /receiver and denotes the threshold distance. The following Equation (3) is used to compute the threshold distance.
where and are the amplification energies for the free space and multipath model , respectively. The transmitter amplifier type determines these factors.
3.2. Mayfly Algorithm
A mathematical concept based on mayfly social behavior is named the mating process. Mayflies are considered adults in this method when they hatch from the egg, and only the fittest mayfly survives. The ideal solution to the issue is represented by the location of every mayfly in the search space. Each mayfly’s position in search space symbolizes a possible solution to the problem. Based on the fitness function, this algorithm identifies the optimal position, referred to as the best CH. This mathematical model considers nuptial dance and mayfly movement within a certain range. In addition, it determines the crossover value among mayflies to arrive at the ideal place.
Two sets of mayflies are first produced randomly and positioned in problem space as a potential solution signified by a dimensional vector. The velocity of a mayfly is defined as a variation in its location while evaluating fitness function Each mayfly’s flight path is in a dynamic direction. Each mayfly’s location is modified to the best () position attained by any mayfly in the swarm before (). The best position is chosen as the basis for CH selection. The mayfly selects the best CH for all sensors based on node degree and centrality and the distance to its neighbors [31].
3.2.1. Position of Male Mayflies
Male and female mayflies are initialized independently. Every mayfly modifies its position in response to its individual and its neighbors’ experiences. It is considered that the mayfly’s present location is and that the search space is designated as at time . When velocity is added to the present location, position changes. It may be expressed as:
Here, velocity .
and are positive attraction constraints. is the optimal position of mayfly had ever visited. Here, is the distance between male and female mayflies, is the gravity coefficient and is a fixed visibility coefficient. can be determined using minimization problems as follows:
Similarly, at time step , can be given as:
where, is the first mayfly in the swarm and is the total number of male mayflies.
3.2.2. Movement of Female Mayflies
Male and female attraction is depending on the effectiveness of the existing solution. The best performing male attracts the best forming female, and so on until all partners are found. Moreover, the updated position for female mayflies can be expressed as follows:
where, is the present female mayfly position. The best female attracts the best male and the second best female to the second best male when considering female mayflies, velocity can be determined. The modified equation for a female’s velocity is:
where is the velocity of element female mayflies at time , is the fitness value of female mayfly location, is the fitness value of male mayfly location, the is the location of the female mayfly in dimension at time , is the element of the location of the male mayfly in dimension at time , is the earlier determined attraction constant, is the gravity coefficient, is the Cartesian separation between the male and female mayflies, and is a random number between [−1, 1]. In the scenario where a female is not attracted to a male , then is a random walk coefficient. Here is the present iteration number and is a random value Є [0, 1].
3.2.3. Crossover
By initially recognizing a male mayfly and subsequently a female mayfly, a crossover operation happens. Best males breed with best females, and selection is based on fitness value. The equation below illustrates the offspring that result from a crossover.
This selection may be made at random or in accordance with the fitness function. Here, the male stands in for the male father and the female for the female parent. A value at random inside a certain range is called . Offspring velocities are initially set to zero.
3.3. Aquila Algorithm
One of the most studied birds in the world is the Aquila, which is famous for its hunting bravery. Male Aquila’s caught a lot more prey when they hunted alone. Aquila uses their speed and strong nails to hunt other animals. [32]. The Aquila optimization algorithm, which is a population-based technique, starts with a population of candidate solutions (Y), which is created randomly between the upper limit and lower bound of the given problem. The best-obtained solution is roughly selected as optimal in every iteration process.
In AOA, the optimization begins the improvement processes by producing a predetermined random population of potential solutions. The search criteria of the AO examine the reasonable locations of the best-obtained solution or the near-optimal solution through the repetition trajectory. The number of iterations needed by AO to reach the ideal solution is relatively low. It is clear from the solution’s trajectory that its magnitude and frequency are high in the initial iterations. They have almost totally vanished in recent versions. This demonstrates AOA’s strong ability for exploration in the early iterations and its strong ability for exploitation in the last iterations. This behavior indicates that there is a good likelihood that AOA will find the optimal solution.
Four different procedures are used to catch the prey in the Aquila algorithm [33].
3.3.1. Approach 1: Extended Exploration
Initially, the Aquila recognizes the prey’s position and flies around looking for it.
where denotes the individual’s location at iteration . The best location at the current iteration is represented by . The mean locations of all individuals at the current iteration are represented by .
where denotes the location of the individual at iteration , and is the swarm population size. denotes the maximum permitted iteration number, while is the random number in a Gaussian distribution between 0 and 1. Based on this condition, if , the exploration phases will be activated; else, the exploitation phases will be carried out, and the AOA algorithm can switch from exploration phases to exploitation phases utilising different behaviours.
3.3.2. Approach 2: Narrowed Exploration
The next approach is narrowed exploration. Continuing with the exploration technique, the Aquila would fly surrounding the prey and ready the land once it located it.
where denotes the dimensionality of the problems to be solved. stands for Levy flights, which are computed as follows:
where , are random values between 0 and 1, and p = 0.01 is a constant parameter. is determined in the following way:
where is a fixed value of 1.5. Γ indicates the gamma function. At the current iteration, represents a randomly picked candidate. The spiral form is represented by x and y, which are computed as follows:
where is a fixed value ranging from 1 to 20 and is a small value fixed to 0.00464. is an array of integer numbers ranging from 1 to the whole length of the issues. The number ω = 0.004 is a constant.
3.3.3. Approach 3: Extended Exploitation
When the Aquila fails to detect the target during the exploitation operation, they may re-initialize themselves; they then update their locations using the equation below.
The definitional domain of the presented issue is [,]. and are two little fixed integers.
3.3.4. Approach 4: Narrowed Exploitation
When the Aquila comes near the prey, they use the following equation to restrict their exploitation.
The AO’s different tracking motions during the session are represented by , which is computed using Equation (24). The flight slope of the AO utilized to follow the prey during the escape from the starting position to the final position (), which is derived using Equation (25), is represented by by decreasing values from 2 to 0. is a quality function that is employed to optimize the search plan, and it is derived using the equation below.
3.4. Proposed Method
The proposed method works based on the characteristics of two algorithms: one for selecting the CH and the other for network routing. First, the Mayfly algorithm identifies appropriate sensors and Aquila determines the best path between the CH and the BS. Following that, the CHs send the data obtained to the BS through the path generated by the Aquila algorithm. Figure 2 illustrates the overall procedure of the proposed technique. The proposed MFA-AOA optimization approach has a powerful hybrid algorithmic framework based on the behavior of the mayfly and Aquila. The best results are attained when this technique is paired with a routing protocol.
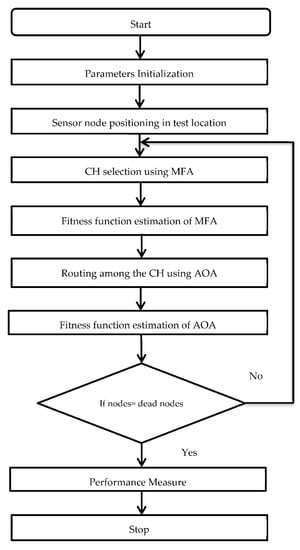
Figure 2.
Flowchart of the proposed MFA-AOA.
Cluster maintenance is one of the most critical stages in this analysis for balancing the load amongst clusters. Due to inter-cluster communication, clusters closer to the BS consume too much energy. Therefore, the cluster maintenance stage is necessary to prevent node failure. It increases the lifespan of data transmission from the SN to the BS. The MFA algorithm is re-initialized to cluster the network if the CH’s residual energy exceeds the threshold level. The CHs are then chosen using the clustering technique, and the AOA is utilized to find the routing path between the CHs and the BS. The MFA algorithm is used in this proposed technique to conduct an effective CH selection. The CHs are chosen based on five criteria: node level, node density, distance from neighbors, distance from the BS, and residual energy. These characteristics are used to choose the best CH from the available nodes.
3.4.1. Evaluation of MFA Fitness Function
The best CH is chosen from the network’s collection of sensors using the identical fitness function of MFA. To avoid using a dead node as a CH during the clustering process, the residual energy taken into account by the fitness function is used. The next step is to choose the best CH to reduce the nodes’ energy consumption using the distance between the nodes and the distance from the potential CH to the BS. The node degree is taken into account when choosing the CH with the lowest normal nodes in order to keep the node for the next rounds. Additionally, the cluster members’ transmission distances to CH are reduced due to the enhanced centrality of the cluster member. The fitness factors have been optimised for the best possible outcomes. The developed model fitness function is for minimising the energy usage and thereby extends network lifespan. The fitness function initialization parameters taken into account for CH selections are explained in the following sections.
3.4.2. Residual Energy
CH chooses its primary factor depending on the remaining energy in each round. The CH rotation is based on the nodes’ residual energy, which results in energy distribution across the network. Maximum energy is used to pick CH in this proposed network. This metric represents the ratio of residual energy to the total energy. It can be expressed as follows:
where stands for the maximum number of nodes. stands for residual energy, while stands for total energy spent. Decreased value of possibility of picking that node as CH gets minimal.
3.4.3. Distance
The distance between nodes and BS determines the amount of energy consumed. Although the separation across the node and the BS are shorter, each node consumes more energy. Conversely, when the distance between the node and the BS is small, every node’s energy consumption is small. As a result, routing protocols use the distance factor as a primary measuring metric. The following is an example of a distance factor:
The distance between the node and BS are represented by .The average distance between node and BS are represented by . For CH selection, this fitness measure should be at its maximum.
3.4.4. Rate of Energy Consumption
or the energy consumption rate is a key component in determining whether a node is suitable for CH selection. It is the difference between the node’s starting energy and the residual energy of the node after the first round. The variation between initial and residual energy is considered in the computation. As a result, is measured and compared to the voltage threshold. If the computed value is lesser than the threshold value, that node is designated as CH. Otherwise, the node remains a member node. The is computed as follows:
denotes the present location energy value of the node in the preceding round and indicates the energy used by the node in the current round. When the number of iterations increases by one, the energy from the last round becomes the new round’s beginning energy. The node with the minimum energy within the cluster is not considered while computing the average threshold value of ECR. A node that uses a lot of energy is not suitable for CH selection.
3.4.5. Node Degree
It describes the number of SNs associated with each CH. The CHs with higher clusters lose their energy over longer periods of time, hence the CHs with fewer sensors are chosen. Equation (29) expresses the node degree.
where denotes the number of SNs.
3.4.6. Node Centrality
Node centrality describes how far a node is from its neighbours.
where denotes the number of neighboring SNs.
Each objective value is given a weight value. In this instance, a single objective function replaces the multiple objectives. are the weighted values. The Equation (32) depicts the single objective function.
The fitness function equation of MFA is as follows:
where, .
The values of are 0.33, 0.25, 0.20, 0.12 and 0.1 respectively. To prevent the node failure as a CH, the is given consideration for taking residual energy as a higher priority. Then, the and are given second and third priority concerns to locate the CH from the BS with the shortest distance possible, hence minimising energy loss. The node degree is specified as the fourth priority to choose the CH with the lowest node degree . In order to strengthen the connection between the CH and cluster members, the node centrality is also given final priority.
To determine the optimal solution, the fitness values of the updated and initial mayflies are compared. After analyzing each fitness value, the best mayfly in the present location is selected as CH. The optimum fireflies’ fitness value is also compared to the to achieve the optimal solution.
3.5. Routing Using the Aquila Algorithm
Data transmission to the BS in a clustered WSN is energy-efficient due to suitable routing between CHs. After figuring out the best paths for every CH in the network, this study uses AOA, as explained in Section 3.3, to identify the best routes for sending raw data to BS.
3.5.1. Initialization
Each Aquila in AOA-based routing reflects a path from each CH that the MFA has chosen to the BS, which is defined as the prey area. Each Aquila has a dimension equal to the number of CHs chosen by MFA. Every Aquila position in the network is initialised in the solution vector to represent a subsequent SN towards the BS. Assuming represents the Aquila in the network, each Aquila’s position is assigned at random SNs from CHs.
3.5.2. Fitness Function for Routing
The fitness function uses three factors to determine the best path from CH to BS. The first constraint determines the distance between CH and SN, the second determines the distance between SNs and BS, and the third determines the residual energy of SNs. Below are the derivations of these three parameters.
- (a)
- Distance between CH and Sensor nodes:
stands for a function that calculates the distance between the CH and its chosen SNs at random. Equation (33) contains the derivation of this function.
where represents sensor node of CH.
- (b)
- Distance between SNs and BS:
A function called is used to calculate the separation between the SNs and BS that were chosen at random. It is energy-efficient to send data from CH to BS over SNs if the distance between those two devices is kept to a minimum. This function’s derivation is provided in Equation (34).
- (c)
- Residual energy of SNs:
The function is used to determine the residual energy of the subsequent SNs. If SNs have enough remaining energy, it would be advantageous to be selected as SN by a CH. Using Equation (35), the residual energy of SNs is computed as:
As the overall fitness function is a minimization problem, the calculation of , which reflects a minimization of , is done using Equation (36).
The concluding fitness function combining the parameter functions described in Equations (33)–(35) is regarded as a minimization problem and is determined using Equation (37), which is also a minimization problem.
3.5.3. Updating AOA
As stated in Section 3.3, AOA employs four processes to identify the optimal solution. Equation (11) is utilised in the expanded exploration phase to update the locations of the AOA, and Equation (37) is employed to compute fitness. The process is carried out until the iteration stopping requirement is not met if the updated population’s fitness is higher than the previous one. Equations (13), (21) and (22) are also used to update the locations in the other three stages of narrowed exploration, extended exploitation, and narrowed exploitation. The top positions are determined using the best fitness value for each phase. The best optimal path to the BS is discovered once all AOA iterations have been completed. This energy-efficient channel enables sending aggregated data to the BS.
Algorithm 1 shows the pseudo-code for the proposed hybrid clustering algorithm in MFA-AOA. Initially, a random population is created and split into two groups: (MFA) and (AOA). The whole populations of MFA and AOA ( and ) are assessed by the suggested multi-objective function during each iteration of MFA-AOA. The two populations and are then shuffled and reassembled into new and populations, which are then chosen at random. The procedure is continued until it reaches the maximum number of iterations. When the proposed MFA-AOA is finished, the algorithm’s global best solution is decoded to find the relevant CHs.
| Algorithm 1: Proposed hybrid MFA-AOA Algorithm |
| #MFA optimization |
| initialize population of male mayflies |
| initialize population of female mayflies |
| Calculate the fitness and update |
| Find |
| Update male mayfly’s velocity using Equation (4) |
| Update female mayfly’s velocity using Equation (8) |
| Perform crossover using Equation (9) |
| Distinct male and female mayfly |
| Replace the worst solution with the latest one |
| Compute the fitness function of the best mayfly using Equation (32) |
| Update |
| End while |
| Return |
| #AOA optimization |
| initialize population of : |
| While |
| Calculate fitness and update |
| For (i = 1:M) |
| IF |
| Update by using Equation (11) #Extended Exploration |
| Else; |
| Update by using Equation (13) #Narrowed Exploration |
| End If |
| Compute the fitness value of using Equation (37) |
| Update |
| End For |
| Else: |
| For (i = 1:M) |
| IF |
| Update by using Equation (21) # Extended Exploitation |
| Else; |
| Update by using Equation (22) # Narrowed Exploitation |
| End If |
| Compute the fitness value of using Equation (37) |
| End For |
| Else if |
| End while |
| Return |
| Post-process results and discussions |
BS constantly monitors the remaining energy of the nodes to prevent node failure during data transmission. The AOA method finds the best transmission path from the SN to the BS through CH. It finds the shortest way to lower the nodes’ energy consumption. This MFA and AOA-based optimum CH selection and route development created an energy-efficient WSN. As a result, an energy-efficient WSN is utilized to increase the total number of packets transferred to the BS at data transmission, extending the network lifetime. Algorithm 1 shows the pseudo-code for the proposed hybrid MFA-AOA algorithm.
4. Results and Discussion
The proposed MFA-AOA optimized protocol, as well as the existing Hybrid Red Deer-Simulated Annealing (RDSA) [34], Genetic Algorithm-PSO (GAPSO) [35], Clan Separator Elephant Herding Optimization operator (CSEHO) [36], and Moth Flame-GA (MFGA) [37] techniques, are tested using MATLAB 2019b. The simulation setup consists of 500 SNs distributed randomly in a network area of 1500 × 1500 square meters, with one sink node at 500 m. Three thousand five hundred rounds were employed in the implementation process. In addition, Table 1 shows the simulation setup used to implement the proposed MFA-AOA optimized protocol.

Table 1.
Simulation parameters of the proposed MFA-AOA protocol.
The proposed MFA-AOA optimized protocol and the existing RDSA [34], GAPSO [35], CSEHO [36], and MFOGA [37] techniques are first examined in terms of network lifetime, energy usage, throughput, and packet delay with SN density.
Figure 3 and Figure 4 show the comparison of the proposed MFA-AOA optimized routing protocol with existing protocols in terms of network lifespan, energy usage, and density of SN. Since it included the advantages of MFA into the AOA for determining the superior nodes of the network as CH, the network lifespan of the proposed MFA-AOA optimized protocol and the existing methods demonstrate a better life with a systematic increment of SNs. Furthermore, this dominance of the proposed MFA-AOA optimized protocol is achieved by replacing MFA’s searching phase with AOA’s hunting phase throughout the search space to preserve the trade-off between exploitation and exploration.
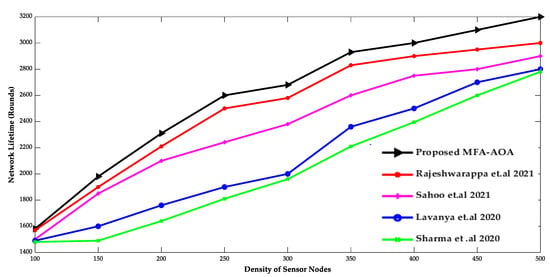
Figure 3.
Density of sensor nodes vs. Network Lifetime [34,35,36,37].
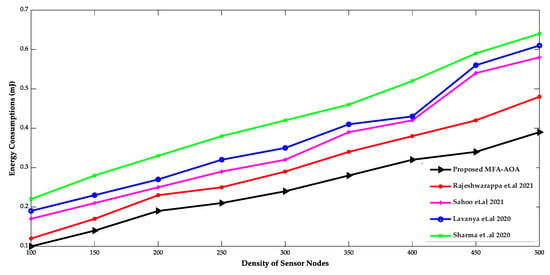
Figure 4.
Density of sensor nodes vs. Energy consumption [34,35,36,37].
The proposed MFA-AOA optimized protocol and the existing schemes’ energy consumptions are shown to grow consistently as SN density increases. However, because it comprises different techniques that combine candidate solutions into prospective offspring solutions, the proposed MFA-AOA optimized protocol can sustain energy consumption. This analysis of future offspring focused on identifying and eliminating the worst solutions that avoid the least critical SNs from being chosen as CHs. The proposed MFA-AOA optimized protocol enhances network lifespan by 9.78%, 11.24%, and 14.25% with varied density of SNs, compared to the RDSA [34], GAPSO [35], CSEHO [36], and MFOGA [37] techniques. With different densities of SNs, the proposed MFA-AOA optimized routing protocol reduces energy consumption by 10.22%, 11.26%, and 14.28%, which is better than the existing systems.
Figure 5 and Figure 6 compare proposed MFA-AOA optimized protocols with existing protocols in terms of throughput and packet delaying of SN densities. The proposed MFA-AOA optimized protocol’s throughput is verified to be superior to the RDSA [34], GAPSO [35], CSEHO [36], and MFOGA [37] techniques with scaling increases in the density of SNs. Furthermore, this capacity of the proposed protocol is improved proportionally because of the benefits of hunting, which assisted in better CH selection and prevented packet drop to an expected level.
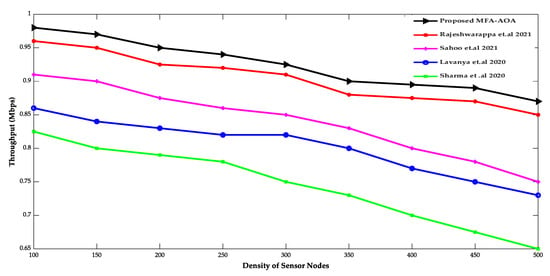
Figure 5.
Density of sensor nodes vs. throughput [34,35,36,37].
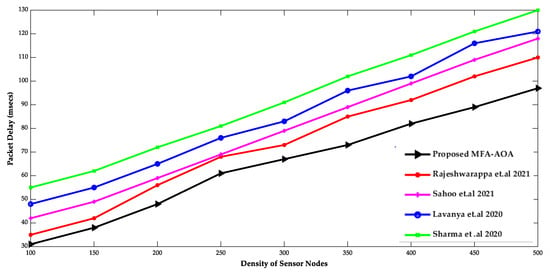
Figure 6.
Density of sensor nodes vs. Packet Delay [34,35,36,37].
Similarly, the proposed MFA-AOA optimized protocol achieves significantly lower packet latency. The selection of prospective CH in the network was always ensured by categorizing solutions and creating important offspring solutions. As a result, the proposed MFA-AOA optimized protocol enhances throughput by 11.36%, 12.79%, and 14.45%, respectively, when compared to the RDSA [34], GAPSO [35], CSEHO [36], and MFOGA [37] techniques. Furthermore, with variable densities of SNs, the proposed MFA-AOA optimized protocol reduces packet latency by 9.27%, 10.34%, and 12.78%, which is better than the existing systems. The proposed MFA-AOA optimized protocol, as well as the RDSA [34], GAPSO [35], CSEHO [36], and MFOGA [37] techniques, are compared in terms of the number of living and dead SNs, throughput, and mean residual energy over several rounds.
The comparison of the number of living SNs and the number of dead SNs deployed in the network of the proposed MFA-AOA optimized protocol and the RDSA [34], GAPSO [35], CSEHO [36], and MFOGA [37] techniques are shown in Figure 7 and Figure 8. As the network’s energy is saved by choosing only the possible SNs as CH throughout the clustering process, the proposed MOA-AOA optimized routing protocol is superior to the state-of-art schemes in terms of the number of alive nodes maintained. This selection technique eliminates unnecessary clustering because the worse SNs are not picked as CH nodes. It keeps the network’s energy at a reasonable level by preventing wasteful energy-draining in the SN. As a result, the proposed MFA-AOA protocol maintains the number of living nodes by 12.54%, 13.63%, and 15.28%, respectively, compared to the RDSA [34], GAPSO [35], CSEHO [36], and MFOGA [37] techniques. Furthermore, the proposed MFA-AOA protocol reduces the number of dead nodes by 11.46%, 13.28%, and 14.63% with varied rounds, which is superior to the existing methods.
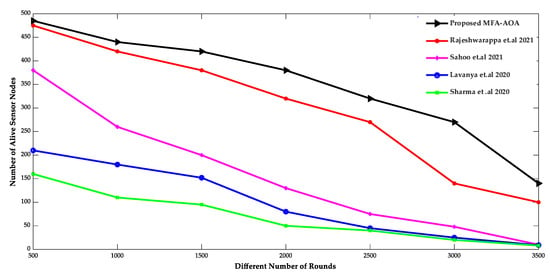
Figure 7.
Different Number of Rounds vs. Alive sensor nodes [34,35,36,37].
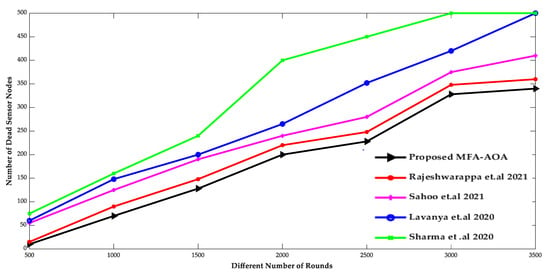
Figure 8.
Different Number of Rounds vs. Dead sensor nodes [34,35,36,37].
Figure 9 and Figure 10 show the comparison of throughput and mean residual energy of the proposed MFA-AOA optimized protocol as well as the RDSA [34], GAPSO [35], CSEHO [36], and MFOGA [37] techniques with different rounds.
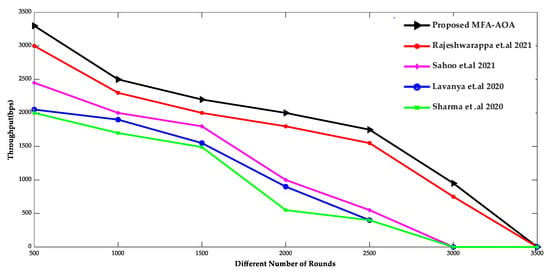
Figure 9.
Different Number of Rounds vs. Throughput [34,35,36,37].
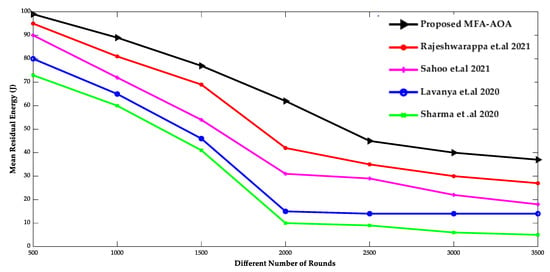
Figure 10.
Different Number of Rounds vs. Mean Residual Energy [34,35,36,37].
The proposed MFA-AOA strategy outperforms the other schemes in terms of throughput because the local search ability initiated by MFA into AOA allows for enhanced CH selection. MFA’s local search capability is also essential to minimize local points of optimization problem and stagnation to the maximum level, regardless of the number of implementation cycles performed. As a result, the proposed MFA-AOA protocol enhances throughput by 8.52%, 10.98%, and 12.69%, respectively, compared to the existing techniques. In addition, the mean residual energy of the proposed MFA-AOA protocol improves by 9.56%, 11.78%, and 13.76% with a varied number of rounds, which is superior to the benchmarked methods.
Figure 11 shows the convergence rate of the proposed MFA-AOA algorithm for 100 nodes. The performance of MFA, AOA, and hybrid MFA-AOA is calculated at the 15th iteration. Hybrid MFA-AOA provides an optimal path with the minimum time consumption compared to the individual MFA and AOA algorithm performances.
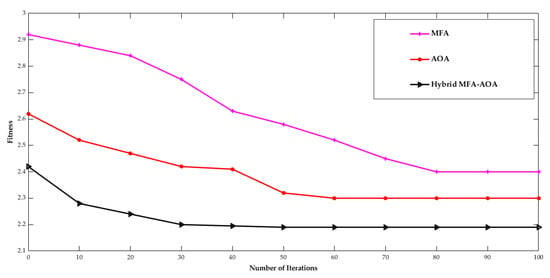
Figure 11.
Number of iterations vs. Fitness.
Moreover, the number of rounds until the first node death, half of the node death, and the last node death in the network are explored, and the proposed MFA-AOA protocol is compared with the existing state-of-art methods [34,35,36,37].
From Figure 12, the proposed MFA-AOA protocol experiences the first node death at round 3400, whereas the first SN death of the compared techniques occurs between rounds 2695 and 3200. The adaptive technique included by MFA into the basic AOA scheme throughout the exploitation process is primarily responsible for the proposed MFA-AOA protocol’s remarkable performance.
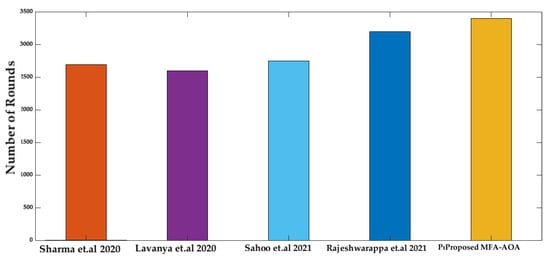
Figure 12.
Number of rounds until first node death [34,35,36,37].
Figure 13 shows that the proposed MFA-AOA protocol is estimated to be half of the node’s death by round 4250, whereas the other techniques have half of the node’s death between 3520 and 3892 rounds. The proposed AOA protocol’s critical performance is achieved by including a flexible exploitation mechanism that varies based on the potentiality of solutions found during the mating phase. Furthermore, Figure 14 shows that the proposed AOA protocol’s last node death occurs at 4450 rounds, whereas the compared schemes occur between 3500 and 4126 rounds.
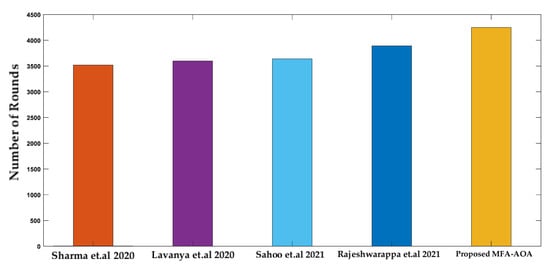
Figure 13.
Number of rounds until half nodes death [34,35,36,37].
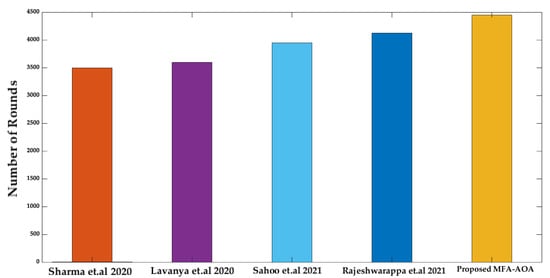
Figure 14.
Number of rounds until last node death [34,35,36,37].
This extraordinary capacity of the proposed AOA protocol can be seen owing to the policy implemented for keeping the degree of exploration and exploitation at a predictable level irrespective of the number of rounds in implementation. The suggested AOA’s significant performance is mostly due to the numerous selections of random sample solutions generated from the same cluster in which the commander solution exists and from the remaining clusters in the network. Due to the great searching efficiency of MFA combined with the dynamic exploratory character of AOA, it can be stated that the proposed hybrid MFA-AOA algorithm outperforms other existing algorithms.
In comparison to the standardised schemes employed for the investigation, Table 2 shows the best, worst, mean, median, and standard deviation in the time complexity of the proposed MFA-AOA protocol. The findings clearly demonstrated that the presented MFA-AOA, when measured in terms of best, worst, median, and SD in time complexity, is superior since it included the benefits of MFA and AOA in the optimal CH and path selection, hence reducing the difficulty incurred in CH selection.

Table 2.
Time complexity comparison of proposed MFA-AOA with existing schemes.
5. Conclusions
For ensuring lifespan enhancement and energy stability in WSNs, the MFA-AOA optimized method was presented in this paper: a combination of the global optimization capabilities of the MFA optimization method with the local optimization ability of AOA. This inclusion of AOA in MFA aids in achieving a balance between exploration and exploitation in the selection of CH for long-term energy stability. Meta-heuristic qualities of MFA and AOA are inherited in this clustering algorithm for locating essential CHs and the best BS placement to improve energy efficiency. In comparison to the existing RDSA, GAPSO, CSEHO, and MFOGA methods, the simulation results of the proposed MFA-AOA-based routing protocol enhanced network lifespan by 9.78%, 11.24%, and 14.25%.
Furthermore, with different densities of SNs, the proposed MFA-AOA routing protocol reduces energy consumption by 10.22%, 11.26%, and 14.28%, which is better than the existing methods. Furthermore, it increased the median number of living nodes by 12.54%, 13.63%, and 15.28%, respectively, while maintaining median normalized energy of 9.56%, 11.78%, and 13.76%, which was superior to the existing schemes. Therefore, it has been determined that the proposed MFA-AOA should be used to endorse practical issues as part of the future scope of work. Furthermore, optimization techniques based on self-adaptive approaches may be employed to address the network’s energy consumption problem.
Author Contributions
Conceptualization, G.N.; Formal analysis, S.K.; Funding acquisition, R.P.d.P. and M.W.; Methodology, S.K.; Software, G.N.; Supervision, R.P.d.P. and M.W.; Validation, R.P.d.P. and M.W. All authors have read and agreed to the published version of the manuscript.
Funding
The authors acknowledge contributions to this project from the Rector of the Silesian University of Technology under a proquality grant no. 09/010/RGJ22/0068.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
| Symbols | Meanings |
| Transmitter | |
| Receiver | |
| Number of bits | |
| Distance | |
| Amount of energy | |
| Threshold distance | |
| Energies for the free space | |
| Multipath model | |
| Fitness function | |
| Best position | |
| First mayfly in the swarm | |
| N | total number of male mayflies |
| Male mayfly’s present location | |
| Search space | |
| Time | |
| Velocity | |
| Updated position of male mayfly | |
| Positive attraction constraints | |
| Optimal position of mayfly had ever visited | |
| Distance between male and female mayflies | |
| Gravity coefficient | |
| Fixed visibility coefficient | |
| Female mayfly’s present location | |
| Updated position of female mayfly | |
| Fitness value of female mayfly location | |
| Fitness value of male mayfly location | |
| The location of the female mayfly in dimension k | |
| element of the location of the male mayfly in dimension k | |
| Cartesian separation between the male and female mayflies | |
| Random number between [−1, 1] | |
| Random walk coefficient | |
| present iteration number | |
| Random value Є [0, 1]. | |
| Value at random inside a certain range | |
| individual’s location at iteration | |
| Best location at the current iteration | |
| Mean locations of all individuals at the current iteration | |
| Location of the individual at iteration | |
| Swarm population size | |
| Maximum permitted iteration number | |
| Random number in a Gaussian distribution between 0 and 1 | |
| E | Dimensionality of the problems |
| Levy flights | |
| Fixed value of 1.5 | |
| Γ | Gamma function |
| Randomly picked candidate | |
| x and y | Spiral form |
| Fixed value ranging from 1 to 20 | |
| Constant 0.00464. | |
| Array of integer numbers | |
| ω | Constant 0.004 |
| Two little fixed integers | |
| Tracking motions | |
| Flight slope of the AO | |
| Q | Quality function |
| Maximum number of nodes. | |
| Residual energy, | |
| Total energy spent | |
| Distance between the node and BS | |
| Average distance between . node and BS | |
| Energy consumption rate | |
| Present location energy value of the node in the preceding round | |
| Number of Sensor nodes | |
| Number of neighboring Sensor nodes | |
| Weighted values | |
| . | 0.33, 0.25, 0.20, 0.12 and 0.1 |
| Aquila in the network | |
| Sensor node of CH | |
| Separation between the SNs and BS | |
| Residual energy of the subsequent SNs |
References
- Verma, U.S.; Gupta, N. Wireless Sensor Network Path Optimization Using Sensor Node Coverage Area Calculation Approach. Wirel. Pers. Commun. 2021, 116, 91–103. [Google Scholar] [CrossRef]
- Singh, O.; Rishiwal, V.; Chaudhry, R.; Yadav, M. Multi-objective optimisation in WSN: Opportunities and challenges. Wirel. Pers. Commun. 2021, 121, 127–152. [Google Scholar] [CrossRef]
- Kamble, A.A.; Patil, B.M. Systematic analysis and review of path optimisation techniques in WSN with mobile sink. Comput. Sci. Rev. 2021, 41, 100412. [Google Scholar] [CrossRef]
- Panag, T.S.; Dhillon, J.S. Predator–prey optimisation based clustering algorithm for wireless sensor networks. Neural Comput. Appl. 2021, 33, 11415–11435. [Google Scholar] [CrossRef]
- Jubair, A.M.; Hassan, R.; Aman, A.H.M.; Sallehudin, H.; Al-Mekhlafi, Z.G.; Mohammed, B.A.; Alsaffar, M.S. Optimisation of Clustering in Wireless Sensor Networks: Techniques and Protocols. Appl. Sci. 2021, 11, 11448. [Google Scholar] [CrossRef]
- Xu, K.; Zhao, Z.; Luo, Y.; Hui, G.; Hu, L. An energy-efficient clustering routing protocol based on a high-QoS node deployment with an inter-cluster routing mechanism in WSNs. Sensors 2019, 19, 2752. [Google Scholar] [CrossRef]
- Kim, D.; Yun, J.; Kim, D. An Energy-Efficient Secure Forwarding Scheme for QoS Guarantee in Wireless Sensor Networks. Electronics 2020, 9, 1418. [Google Scholar] [CrossRef]
- Yao, Y.; Hu, S.; Li, Y.; Wen, Q. A Node Deployment Optimization Algorithm of WSNs Based on Improved Moth Flame Search. IEEE Sens. J. 2022, 22, 10018–10030. [Google Scholar] [CrossRef]
- Sharma, N.; Singh, B.M.; Singh, K. QoS-based energy-efficient protocols for wireless sensor network. Sustain. Comput. Inform. Syst. 2021, 30, 100425. [Google Scholar] [CrossRef]
- Agarkhed, J.; Dattatraya, P.Y.; Patil, S. Multi-QoS constraint multipath routing in cluster-based wireless sensor network. Int. J. Inf. Technol. 2021, 13, 865–876. [Google Scholar] [CrossRef]
- Fang, W.; Zhang, W.; Yang, W.; Li, Z.; Gao, W.; Yang, Y. Trust management-based and energy efficient hierarchical routing protocol in wireless sensor networks. Digit. Commun. Netw. 2021, 7, 470–478. [Google Scholar] [CrossRef]
- Shagari, N.M.; Salleh, R.B.; Ahmedy, I.; Idris, M.Y.I.; Murtaza, G.; Ali, U.; Modi, S. A two-step clustering to minimise redundant transmission in wireless sensor network using sleep-awake mechanism. Wirel. Netw. 2022, 28, 2077–2104. [Google Scholar] [CrossRef]
- Woźniak, M.; Sikora, A.; Zielonka, A.; Kaur, K.; Hossain, M.S.; Shorfuzzaman, M. Heuristic Optimization of Multipulse Rectifier for Reduced Energy Consumption. IEEE Trans. Ind. Inform. 2021, 18, 5515–5526. [Google Scholar] [CrossRef]
- Basak, H.; Kundu, R.; Singh, P.K.; Ijaz, M.F.; Woźniak, M.; Sarkar, R. A union of deep learning and swarm-based optimization for 3D human action recognition. Sci. Rep. 2022, 12, 5494. [Google Scholar] [CrossRef] [PubMed]
- Murugadass, G.; Sivakumar, P. A hybrid elephant herding optimisation and cultural algorithm for energy-balanced cluster head selection scheme to extend the lifetime in WSNs. Int. J. Commun. Syst. 2020, 33, e4538. [Google Scholar] [CrossRef]
- Rambabu, B.; Reddy, A.V.; Janakiraman, S. A hybrid artificial bee colony and bacterial foraging algorithm for optimised clustering in wireless sensor network. Int. J. Innov. Technol. Explor. Eng. 2019, 8, 2186–2190. [Google Scholar]
- Tabatabaei, S.; Rajaei, A.; Rigi, A.M. A novel energy-aware clustering method via lion pride optimiser algorithm (LPO) and fuzzy logic in wireless sensor networks (WSNs). Wirel. Pers. Commun. 2019, 108, 1803–1825. [Google Scholar] [CrossRef]
- Shyjith, M.B.; Maheswaran, C.P.; Reshma, V.K. Optimised and dynamic selection of cluster head using energy efficient routing protocol in WSN. Wirel. Pers. Commun. 2021, 116, 577–599. [Google Scholar] [CrossRef]
- Poonguzhali, P.K.; Ananthamoorthy, N.P. Improved energy efficient WSN using ACO based HSA for optimal cluster head selection. Peer-to-Peer Netw. Appl. 2020, 13, 1102–1108. [Google Scholar] [CrossRef]
- Wang, Z.; Ding, H.; Li, B.; Bao, L.; Yang, Z. An energy efficient routing protocol based on improved artificial bee colony algorithm for wireless sensor networks. IEEE Access 2020, 8, 133577–133596. [Google Scholar] [CrossRef]
- Hassan, A.A.H.; Shah, W.M.; Habeb, A.H.H.; Othman, M.F.I.; Al-Mhiqani, M.N. An improved energy-efficient clustering protocol to prolong the lifetime of the WSN-based IoT. IEEE Access 2020, 8, 200500–200517. [Google Scholar] [CrossRef]
- Al Mazaideh, M.; Levendovszky, J. A multi-hop routing algorithm for WSNs based on compressive sensing and multiple objective genetic algorithm. J. Commun. Netw. 2021, 23, 138–147. [Google Scholar] [CrossRef]
- Osamy, W.; El-Sawy, A.A.; Salim, A. CSOCA: Chicken swarm optimisation based clustering algorithm for wireless sensor networks. IEEE Access 2020, 8, 60676–60688. [Google Scholar] [CrossRef]
- Zhang, Z.; Li, J.; Xu, N. Robust optimisation based on ant colony optimisation in the data transmission path selection of WSNs. Neural Comput. Appl. 2021, 33, 17119–17130. [Google Scholar] [CrossRef]
- Li, J.; Luo, Z.; Xiao, J. A hybrid genetic algorithm with bidirectional mutation for maximising lifetime of heterogeneous wireless sensor networks. IEEE Access 2020, 8, 72261–72274. [Google Scholar] [CrossRef]
- Li, X.; Keegan, B.; Mtenzi, F.; Weise, T.; Tan, M. Energy-efficient load balancing ant based routing algorithm for wireless sensor networks. IEEE Access 2019, 7, 113182–113196. [Google Scholar] [CrossRef]
- Elsmany, E.F.A.; Omar, M.A.; Wan, T.C.; Altahir, A.A. EESRA: Energy efficient scalable routing algorithm for wireless sensor networks. IEEE Access 2019, 7, 96974–96983. [Google Scholar] [CrossRef]
- Zhou, L.; Ge, C.; Hu, S.; Su, C. Energy-efficient and privacy-preserving data aggregation algorithm for wireless sensor networks. IEEE Internet Things J. 2019, 7, 3948–3957. [Google Scholar] [CrossRef]
- Bhattacharyya, T.; Chatterjee, B.; Singh, P.K.; Yoon, J.H.; Geem, Z.W.; Sarkar, R. Mayfly in harmony: A new hybrid meta-heuristic feature selection algorithm. IEEE Access 2020, 8, 195929–195945. [Google Scholar] [CrossRef]
- Barshandeh, S.; Masdari, M.; Dhiman, G.; Hosseini, V.; Singh, K.K. A range-free localisation algorithm for IoT networks. Int. J. Intell. Syst. 2021. [Google Scholar] [CrossRef]
- Lizy, P.J.; Indra, N.C. Metaheuristic energy efficient protocol for heterogeneous WSN. Mater. Today Proc. 2021, in press. [Google Scholar] [CrossRef]
- Abualigah, L.; Yousri, D.; Abd Elaziz, M.; Ewees, A.A.; Al-Qaness, M.A.; Gandomi, A.H. Aquila optimiser: A novel meta-heuristic optimisation algorithm. Comput. Ind. Eng. 2021, 157, 107250. [Google Scholar] [CrossRef]
- Zhao, J.; Gao, Z.M.; Chen, H.F. The Simplified Aquila Optimization Algorithm. IEEE Access 2022, 10, 22487–22515. [Google Scholar] [CrossRef]
- Rajeswarappa, G.; Vasundra, S. Red Deer and Simulation Annealing Optimization Algorithm-Based Energy Efficient Clustering Protocol for Improved Lifetime Expectancy in Wireless Sensor Networks. Wirel. Pers. Commun. 2021, 121, 2029–2056. [Google Scholar] [CrossRef]
- Sahoo, B.M.; Pandey, H.M.; Amgoth, T. GAPSO-H: A hybrid approach towards optimising the cluster based routing in wireless sensor network. Swarm Evol. Comput. 2021, 60, 100772. [Google Scholar] [CrossRef]
- Lavanya, N.; Shankar, T. Hybrid based energy efficient cluster head selection using camel series elephant herding optimisation algorithm in WSN. Int. J. Adv. Comput. Sci. Appl. 2020, 11. [Google Scholar]
- Sharma, R.; Vashisht, V.; Singh, U. eeTMFO/GA: A secure and energy efficient cluster head selection in wireless sensor networks. Telecommun. Syst. 2020, 74, 253–268. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).