An Intelligent Automated System for Detecting Malicious Vehicles in Intelligent Transportation Systems
Abstract
:1. Introduction
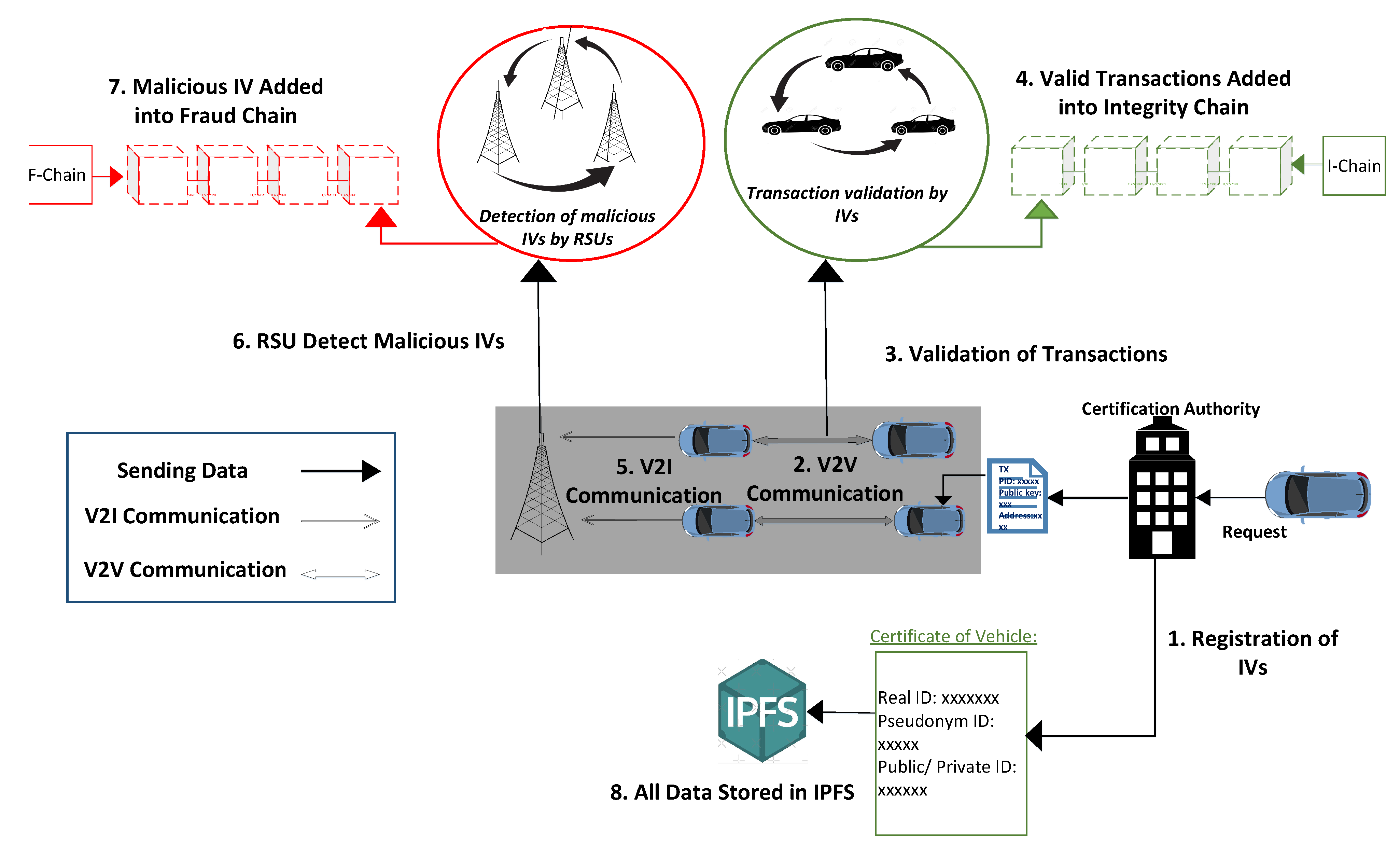
- In the proposed work, a secure and efficient communication model based on blockchain is proposed. The proposed model addresses some main communication issues such as lack of coordination between IVs, validation of transactions, and detection of malicious IVs in a VN.
- The proposed model also helps manage the storage problem efficiently and promotes secure communication.
- CA is used for the authentication of IVs and provides trustworthiness for the communication of IVs.
- The multi-chain concept is introduced, where the integrated network entities are stored in the Legitimate Chain (L-chain), and all fraudulent entities are stored in the Fraud Chain (F-chain). In addition, the multi-chain concept also solves the intensive data problem.
- An encryption technique is used to validate the transactions (data).
- Furthermore, two attacker models, selfish mining and Sybil attack are also implemented to protect the system from blockchain attacks.
2. Related Work and Problem Statement
| Addressed Problems | Proposed Solutions | Strengths | Limitations |
|---|---|---|---|
| Security and privacy preservation problems [10] | Proposed an authentication protocol for privacy preservation | Outperforms in terms of delay, throughput and packet dropping rate | Does not consider the storage problem |
| Privacy, authentication, and communication problems in VANETs [11] | Traceable decentralized framework is proposed | Achieved conditional privacy for anonymous vehicles | Large number of events affect the efficiency of the network |
| Malicious nodes broadcast forged messages and trust inconsistency [12] | An active detection trust mechanism is proposed for the VANETs | Identitify the malicious behavior of EVs | Proposed mechanism has high computational costs |
| Problem of illusion attacks [13] | An Applied Intelligence AppLied Intelligence in bloCkchaIn VANET (ALICIA) is proposed | Novel validation scheme | Low-level metrics in ALICIA |
| Inefficient Energy trading [14] | Proposed a fog computing-based V2V energy trading architecture | Improved PBFT | System’s efficiency is threatened |
| Centralized storage and data validation problems [15] | Proposed a reputation system for ITS | Secure data sharing | Validation of information is based on users |
| Storage issue [16] | Proposed system exploits benefits of IPFS | Provide monetary incentives to active EVs | Consensus mechanism uses high computational power |
| Inefficient energy trading and security issues [17] | Proposed an incentive scheme based on blockchain for energy trading | Enhance the security level | Distributed architecture for data storage is missing |
| Trust, authentication, and access control problems [18] | Multiple smart contracts are proposed | Detection of misbehavior | Difficult to manage revolutionary mobile communication |
| Address the problem of peak hours charges [19] | Proposed a framework for secure and efficient energy trading | Incentive mechanism for the motivation of EVs | An action to prevent against various attacks is missing |
| Address the charging problem of roaming vehicles [20] | Proposed an architecture that provides charging services to roaming vehicles | Fair and unified billing solution | High computational power is used |
| Problem of uncertainty and randomness of EV charging and discharging [21] | Proposed a blockchain-based trading model for Peer to Peer (P2P) transactions among EVs | Reduce the electricity purchaser cost | Face difficulty dealing with dense network |
| Growing energy demand issue in EV sector [22] | Proposed different charging strategies for EVS | Modify the load profile and reduce the cost | Work only for economic perspective |
| Addressed the problems of insecure communication and lack of privacy in VANETs [23] | Proposed an efficient mechanism for privacy preservation, aggregation of signature, and batch verification | Reduce the risk of privacy disclosure | However, because of the high cost, it cannot maintain the batch verification |
| Addressed the security and privacy issues in energy trading models [24] | An account generation technique is proposed | Provides a fault-tolerant and reliable data storage | Scalability issue when the number of EVs are increased. |
| Address the trust issues [25] | Proposed a blockchain-based Trusted Data Management scheme | Provides data protection and mutual authentication | Designing a uniform data format is still missing |
| Address the security issues [26] | Proposed a mechanism to deal with the security issue | Provides secrecy and protection to the control system | High maintenance cost |
| Address the repudiation issue [27] | Proposed a blockchain-based fair non-repudiation scheme | Smart contract is implemented to resolve the disputes | Reputation system for service providers is missing |
| High computational power requirement and privacy [28] | Proposed a lightweight blockchain-based model for V2G network | Negotiate between the vehicle and grid at less cost | Designing the blockchain layer in proposed framework is an issue |
| Imbalance distribution of assets [29] | A novel configuration mechanism to serve the objective of deploying distributed assets | Automation is achieved | Size of memory is not calculated |
| Address the authentication problem [30] | Proposed a key agreement protocol for the authentication | Reduce the time of authentication | Unable to deal with damage of data |
| Address the privacy problem during the charging of EVs [31] | Proposed a decentralized privacy-preserving charging scheme based on blockchain and fog computing | Blockchain is deployed on fog computing nodes | Only theoretical analysis is provided |
| Address the problem of privacy in sellers [32] | A double auction mechanism is proposed | Case studies are provided to show the effectiveness of proposed model | Off-chain payment can cause disputes |
| Security problems in vehicular systems [35] | Proposed a secure charging system based on blockchain | Energy allocation mechanism to allocate the limited renewable energy for EVs | Latency issue |
| Storage problem [36] | Proposed an efficient data sharing scheme | Consensus and signature mechanism guaranteed the data security | Current storage mechanisms need to be revised to handle the growing size of blockchain |
| Addressed the internal and external adversarial attacks [38] | Develop a consensus protocol termed as Proof of Reputation (PoR) for the security | Implemented secure energy delivery | Computationally expensive |
| Inefficient charging issue [39] | a new system of EV charging based on consortium blockchain is proposed | Provided convenient charging services for EVs | Scalability issue |
| Security threats of data and the leakage of privacy [41] | Proposed a system of consortium blockchain-enabled framework | Analyze the efficiency and security of proposed model | Computational Overhead |
| Issues of communication and insecure transactions [43] | Proposed adopting blockchain expertise in Real-Time Applications (RTA) | Achieved secure communication and create decentralized cloud computing platform | No assessment mechanism for unreliable source |
| Central server for IoVs that creates security issues [47] | Introduced a Secure and Highly Efficient Practical Byzantine Fault Tolerance (SG-PBFT) | Reduced the burden on the central server and minimized the possibility of single-node threats | Required highest Cost |
Research Gap and Problem Statement
3. System Model
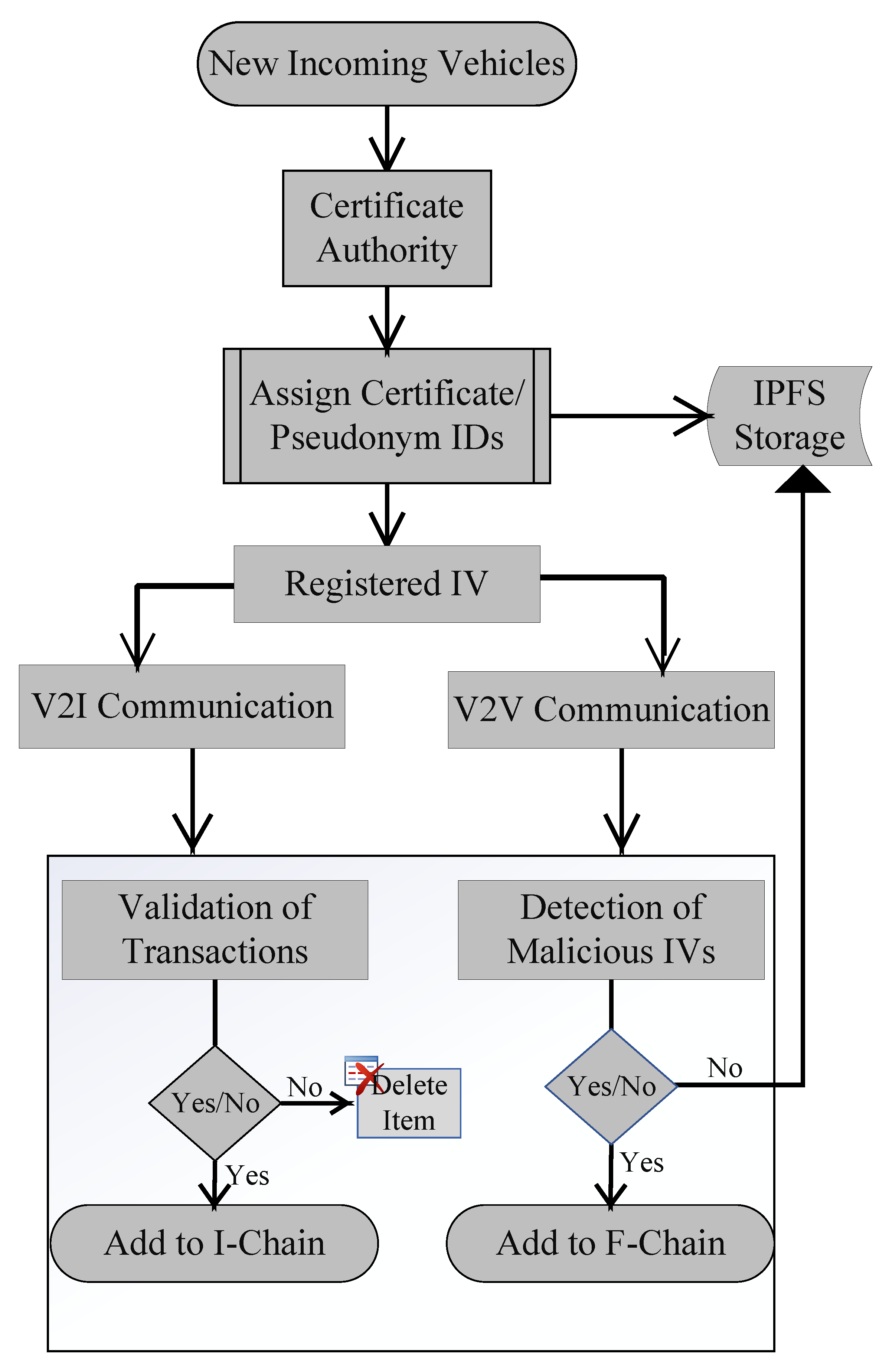
3.1. Registration of IVs
Analysis of Algorithm 1 (Registration and Validation of IVs)
| Algorithm 1: Registration and Validation of IVs. |
|
3.2. Secure Communication
Analysis of Algorithm 2 (Authentication of IVs)
| Algorithm 2: Authentication of IVs. |
|
3.3. Efficient Storage Management through IPFS
3.4. Branching of Data
3.5. Detection of Malicious IVs
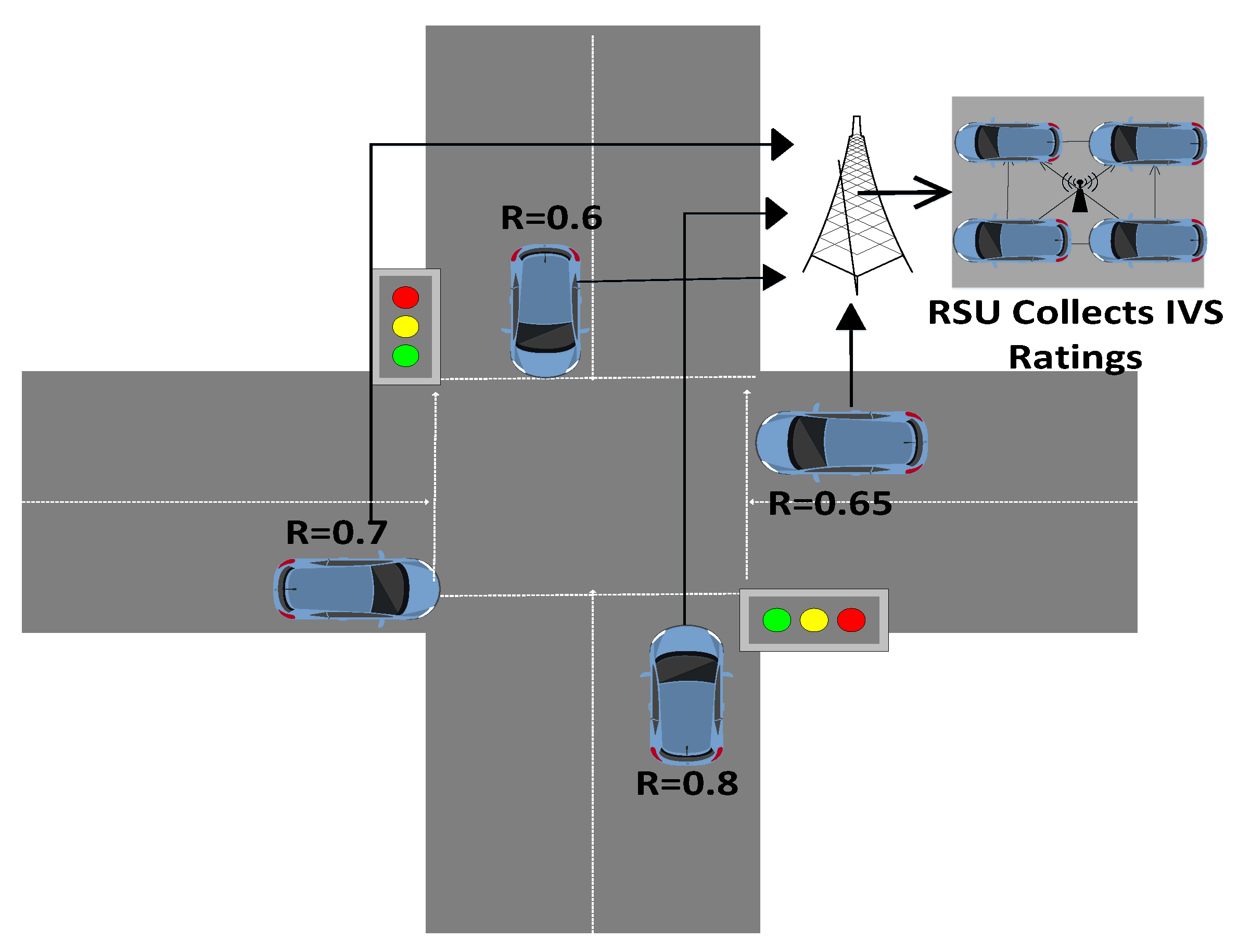
3.6. Intersection Scenario
| Algorithm 3: Assign Reputation to IVs. |
|
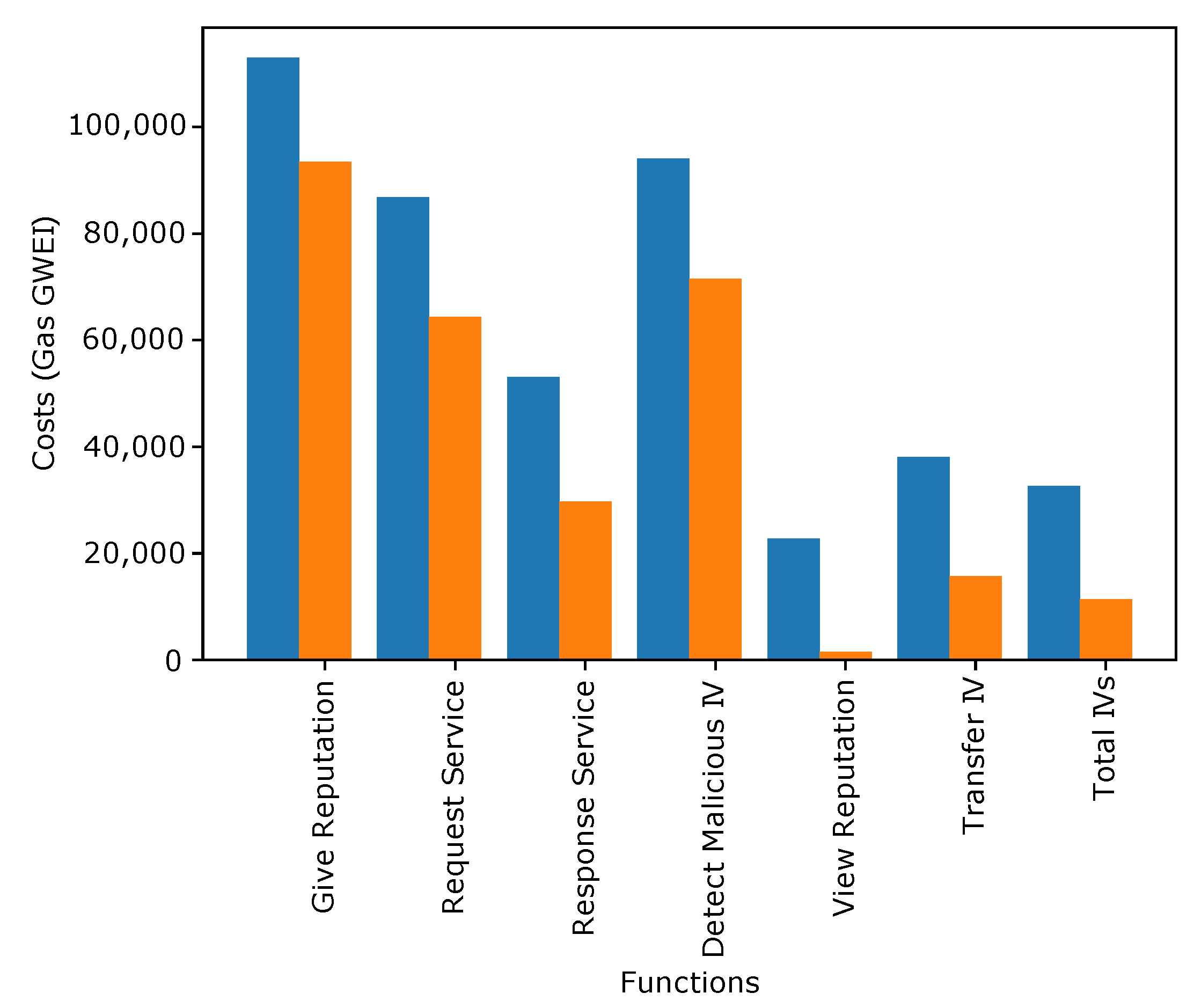
4. Results and Discussion
5. Security Analysis
5.1. Smart Contract-Based Attacks
5.1.1. Types of Smart Contract Attacks
5.1.2. Security Features
5.2. Blockchain-Based Attacks
5.2.1. Selfish Mining Attack
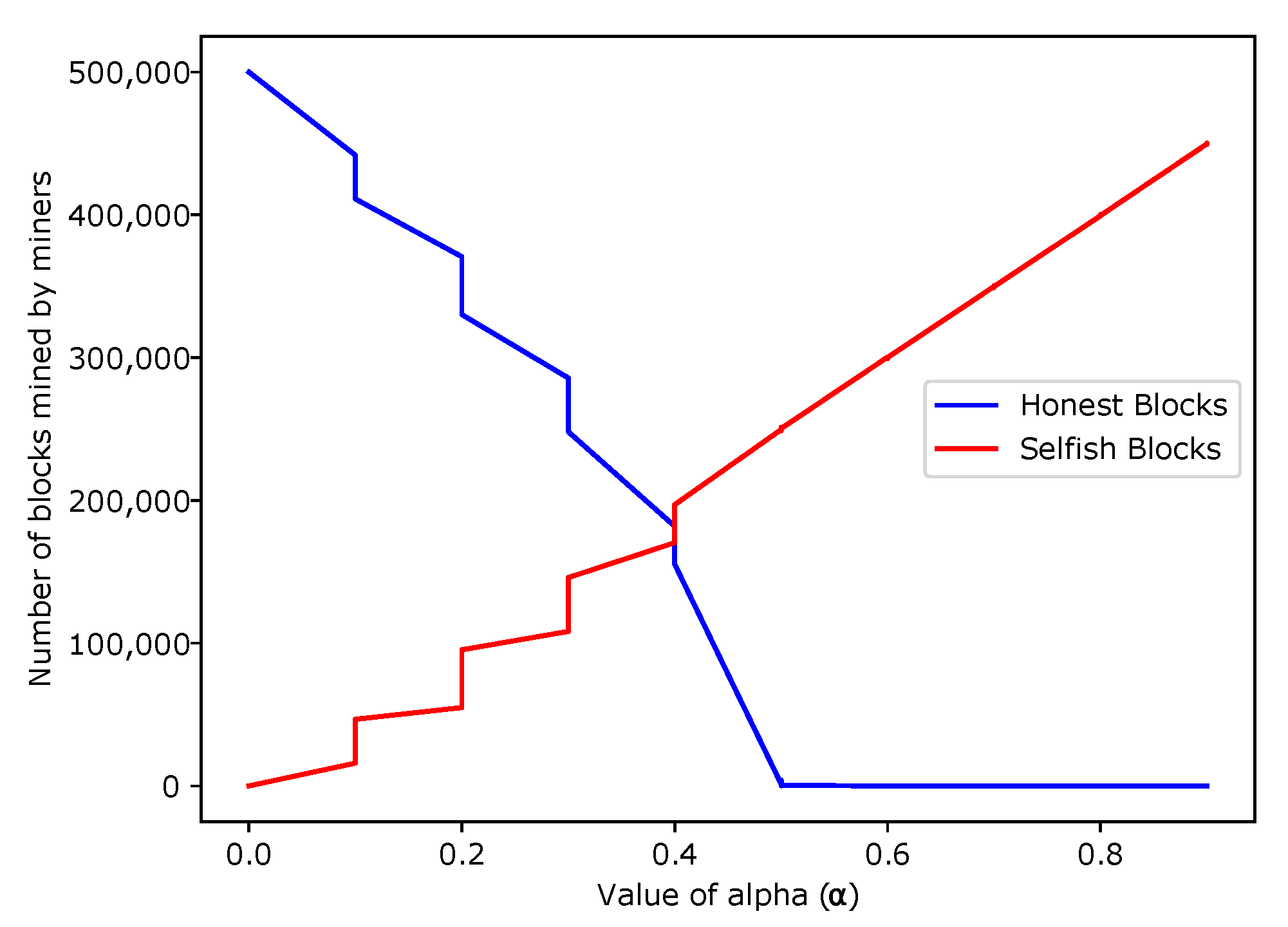
- Probability of occurrence of attack:The probability of a selfish mining attack depends on several variables, including computing capacity and selfish mining power. During the attack, orphan blocks are generated, indicating that the attack has occurred. As the probability of selfish mining increases, the number of orphan blocks also increases. The high number of orphan blocks is used as evidence of the existence of selfish miners. Simulation results show the proportional relationship between orphan blocks and the probability of attack.
- Total revenue calculation:Selfish miners in the network initially create forks in the blockchain and connect the fake blocks in the blockchain. These fake blocks get control of the network and gain revenue.
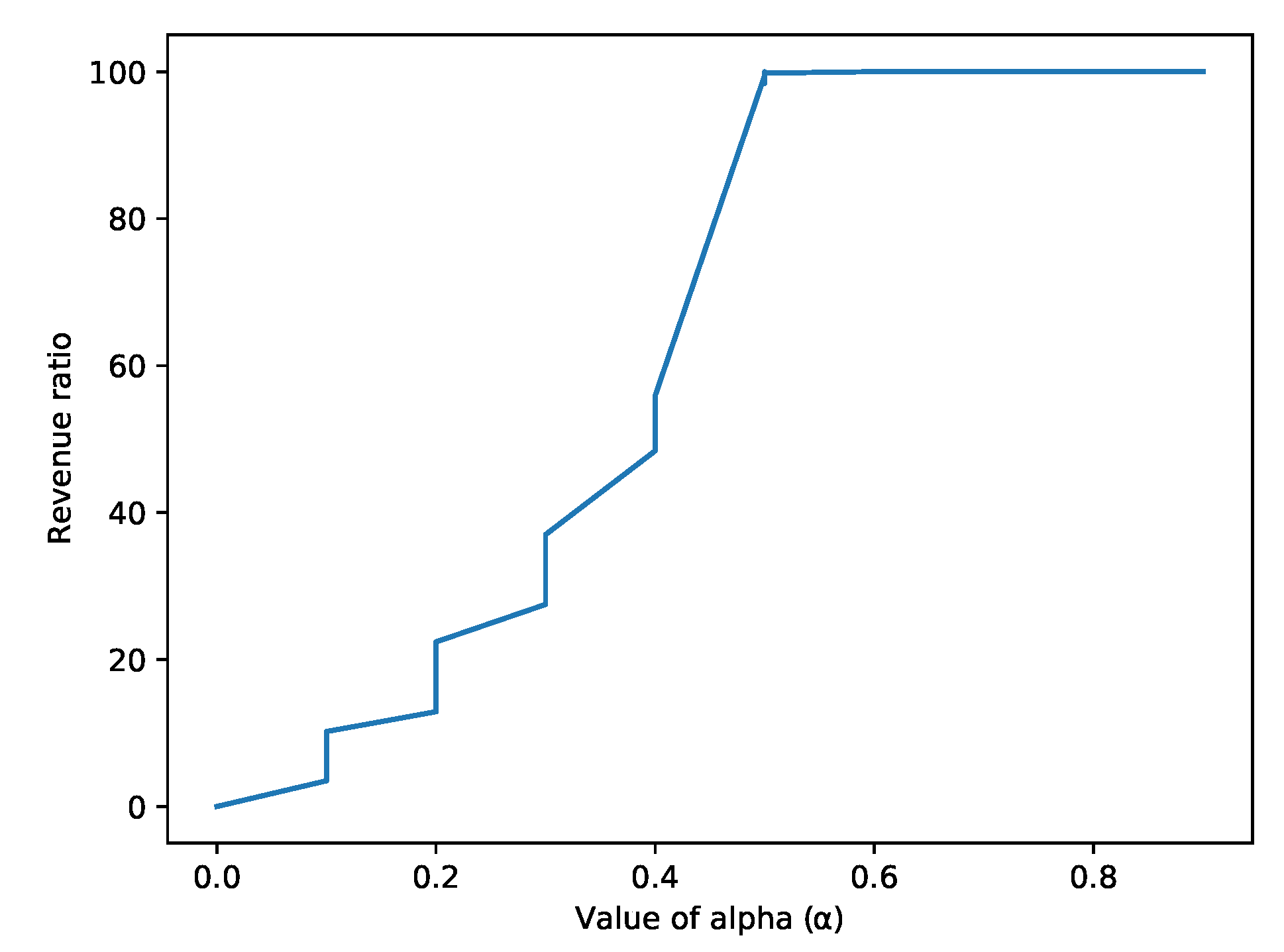
- Profit and loss ratio:
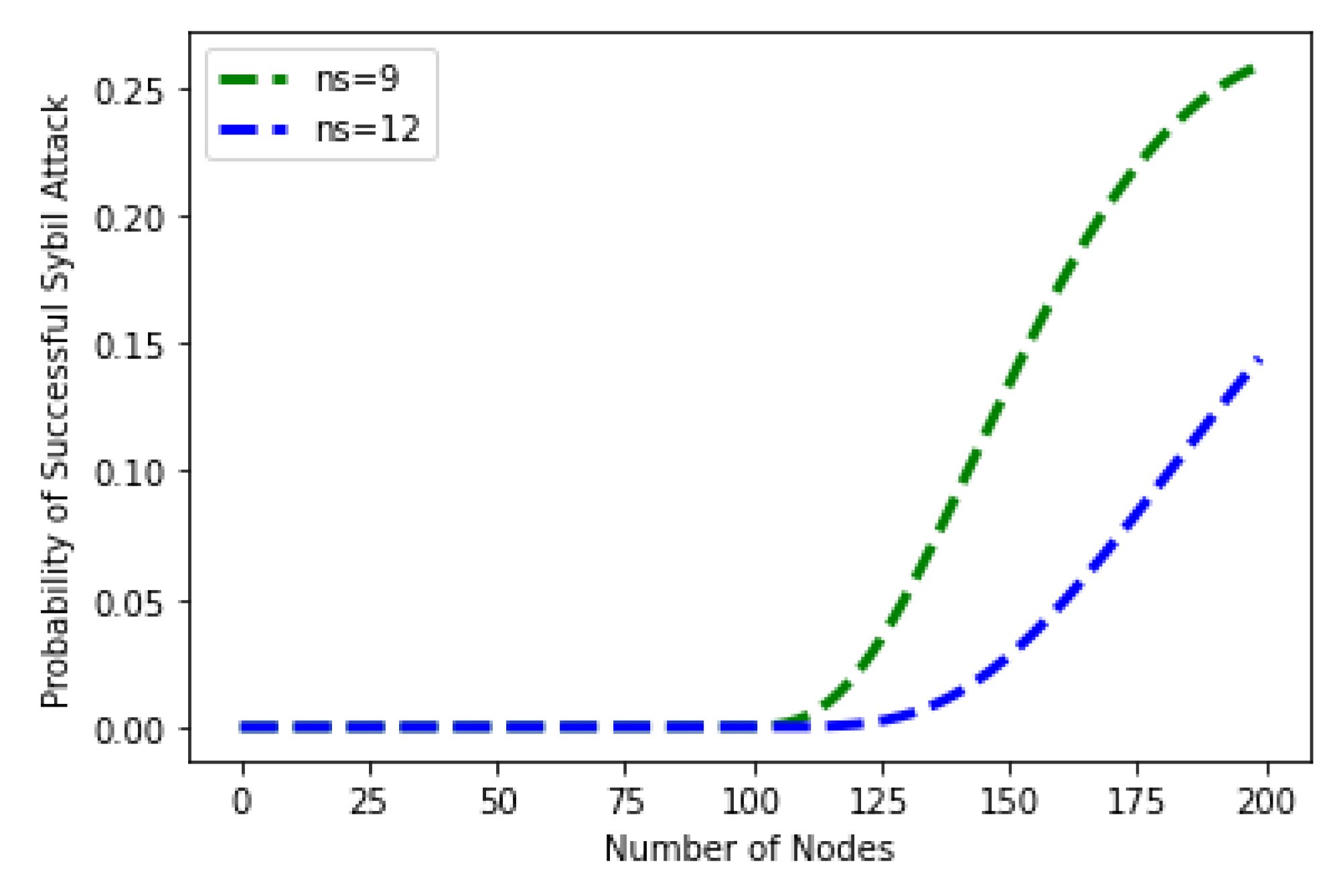
5.2.2. Sybil Attack
- N: number of population
- M: number of successful items from the population
- n: number of successful items from the sample
- c: computational power of sample
- N*: number of items in the sample
6. Conclusions
7. Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AI | Artificial Intelligent |
| AES | Advanced Encryption Standard |
| aFPR | automatic Frequency Restoration Reserve |
| ALICIA | AppLied Intelligence in bloCkchaIn VANET |
| ANN | Artificial Neural Networks |
| BMS | Battery Management system |
| BlockTDM | Blockchain-based Trusted Data Management scheme |
| CA | Certificate Authority |
| D2D | Device to Device |
| DHT | Distributed Hash Table |
| DSRC | Dedicated Short Range Communication |
| DPoS | Delegate Proof of Stake |
| EVs | Electric Vehicles |
| F-Chain | Fraud Chain |
| IDs | Identifications |
| I-Chain | Integrity Chain |
| IIoT | Industrial Internet of Things |
| IoT | Internet of Things |
| IoVs | Internet of Vehicles |
| IPFS | InterPlanetary File System |
| IVs | Intelligent Vehicles |
| ITS | Intelligent Transport System |
| LDB | Locally Dynamic Blockchain |
| LNSC | Lighting Network Smart Contract |
| PBFT | Practical Byzantine Fault Tolerance |
| P2P | Peer to Peer |
| PoD | Proof of Driving |
| PoR | Proof of Reputation |
| RSUs | Roadside Units |
| SG-PBFT | secure and highly efficient PBFT |
| SDN | Software Defined Network |
| SWM | Social Welfare Maximization |
| TA | Trusted Authority |
| VANET | Vehicular Ad hoc Networks |
| VEN | Vehicular Energy Network |
| VSN | Vehicular Social Networks |
| V2G | Vehicle to Grid |
| V2I | Vehicle to Infrastructure |
| V2V | Vehicle to Vehicle |
| V2X | Vehicle to Everything |
| VN | Vehicular Network |
References
- Liu, C.; Chai, K.K.; Zhang, X.; Lau, E.T.; Chen, Y. Adaptive blockchain-based electric vehicle participation scheme in smart grid platform. IEEE Access 2018, 6, 25657–25665. [Google Scholar] [CrossRef]
- Waheed, A.; Shah, M.A.; Mohsin, S.M.; Khan, A.; Maple, C.; Aslam, S.; Shamshirband, S. A Comprehensive Review of Computing Paradigms, Enabling Computation Offloading and Task Execution in Vehicular Networks. IEEE Access 2022, 10, 3580–3600. [Google Scholar] [CrossRef]
- Aslam, S.; Michaelides, M.P.; Herodotou, H. Internet of ships: A survey on architectures, emerging applications, and challenges. IEEE Internet Things J. 2020, 7, 9714–9727. [Google Scholar] [CrossRef]
- Bunsen, T.; Pierpaolo, C.; Marine, G.; Leonardo, P.; Sacha, S.; Renske, S.; Jacopo, T.; Jacob, T. Global EV Outlook 2018: Towards Cross-MODAL Electrification; International Energy Agency: Paris, France, 2018. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Decentralized Business Review, 21260. 2008. Available online: https://www.debr.io/article/21260-bitcoin-a-peer-to-peer-electronic-cash-system (accessed on 13 June 2022).
- Khosravy, M.; Nakamura, K.; Hirose, Y.; Nitta, N.; Babaguchi, N. Model Inversion Attack by Integration of Deep Generative Models: Privacy-Sensitive Face Generation from a Face Recognition System. IEEE Trans. Inf. Forensics Secur. 2022, 17, 357–372. [Google Scholar] [CrossRef]
- Bahga, A.; Madisetti, V.K. Blockchain platform for industrial internet of things. J. Softw. Eng. Appl. 2016, 9, 533. [Google Scholar] [CrossRef] [Green Version]
- Lin, D.; Tang, Y. Blockchain Consensus Based User Access Strategies in D2D Networks for Data-Intensive Applications. IEEE Access 2018, 6, 72683–72690. [Google Scholar] [CrossRef]
- Khan, S.; Amin, M.B.; Azar, A.T.; Aslam, S. Towards interoperable blockchains: A survey on the role of smart contracts in blockchain interoperability. IEEE Access 2021, 9, 116672–116691. [Google Scholar] [CrossRef]
- Akhter, A.F.M.; Ahmed, M.; Shah, A.F.M.; Anwar, A.; Zengin, A. A Secured Privacy-Preserving Multi-Level Blockchain Framework for Cluster Based VANET. Sustainability 2021, 13, 400. [Google Scholar] [CrossRef]
- Zheng, D.; Jing, C.; Guo, R.; Gao, S.; Wang, L. A traceable blockchain-based access authentication system with privacy preservation in VANETs. IEEE Access 2019, 7, 117716–117726. [Google Scholar] [CrossRef]
- Li, F.; Guo, Z.; Zhang, C.; Li, W.; Wang, Y. ATM: An Active-Detection Trust Mechanism for VANETs Based on Blockchain. IEEE Trans. Veh. Technol. 2021, 70, 4011–4021. [Google Scholar] [CrossRef]
- Maskey, S.R.; Badsha, S.; Sengupta, S.; Khalil, I. ALICIA: Applied Intelligence in blockchain based VANET: Accident Validation as a Case Study. Inf. Process. Manag. 2021, 58, 102508. [Google Scholar] [CrossRef]
- Sun, G.; Dai, M.; Zhang, F.; Yu, H.; Du, X.; Guizani, M. Blockchain-Enhanced High-Confidence Energy Sharing in Internet of Electric Vehicles. IEEE Internet Things J. 2020, 7, 7868–7882. [Google Scholar] [CrossRef]
- Hîrţan, L.A.; Dobre, C.; González-Vélez, H. Blockchain-based reputation for intelligent transportation systems. Sensors 2020, 20, 791. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Khalid, A.; Iftikhar, M.S.; Almogren, A.; Khalid, R.; Afzal, M.K.; Javaid, N. A blockchain based incentive provisioning scheme for traffic event validation and information storage in VANETs. Inf. Process. Manag. 2021, 58, 102464. [Google Scholar] [CrossRef]
- Chaudhary, R.; Jindal, A.; Aujla, G.S.; Aggarwal, S.; Kumar, N.; Choo, K.K.R. BEST: Blockchain-based secure energy trading in SDN-enabled intelligent transportation system. Comput. Secur. 2019, 85, 288–299. [Google Scholar] [CrossRef]
- Sultana, T.; Almogren, A.; Akbar, M.; Zuair, M.; Ullah, I.; Javaid, N. Data sharing system integrating access control mechanism using blockchain-based smart contracts for IoT devices. Appl. Sci. 2020, 10, 488. [Google Scholar] [CrossRef] [Green Version]
- Zhou, Z.; Wang, B.; Dong, M.; Ota, K. Secure and efficient vehicle-to-grid energy trading in cyber physical systems: Integration of blockchain and edge computing. IEEE Trans. Syst. Man Cybern. Syst. 2019, 50, 43–57. [Google Scholar] [CrossRef]
- Yaqub, R.; Ahmad, S.; Ali, H. AI and Blockchain Integrated Billing Architecture for Charging the Roaming Electric Vehicles. IoT 2020, 1, 22. [Google Scholar] [CrossRef]
- Liu, H.; Zhang, Y.; Zheng, S.; Li, Y. Electric vehicle power trading mechanism based on blockchain and smart contract in V2G network. IEEE Access 2019, 7, 160546–160558. [Google Scholar] [CrossRef]
- Sachan, S.; Deb, S.; Singh, S.N. Different charging infrastructures along with smart charging strategies for electric vehicles. Sustain. Cities Soc. 2020, 60, 102238. [Google Scholar] [CrossRef]
- Ren, Y.; Li, X.; Sun, S.F.; Yuan, X.; Zhang, X. Privacy-preserving batch verification signature scheme based on blockchain for Vehicular Ad-Hoc Networks. J. Inf. Secur. Appl. 2021, 58, 102698. [Google Scholar] [CrossRef]
- Sadiq, A.; Javed, M.U.; Khalid, R.; Almogren, A.; Shafiq, M.; Javaid, N. Blockchain based Data and Energy Trading in Internet of Electric Vehicles. IEEE Access 2020, 9, 7000–7020. [Google Scholar] [CrossRef]
- Zhaofeng, M.; Xiaochang, W.; Jain, D.K.; Khan, H.; Hongmin, G.; Zhen, W. A blockchain-based trusted data management scheme in edge computing. IEEE Trans. Ind. Inform. 2019, 16, 2013–2021. [Google Scholar] [CrossRef]
- Rathee, G.; Sharma, A.; Iqbal, R.; Aloqaily, M.; Jaglan, N.; Kumar, R. A blockchain framework for securing connected and autonomous vehicles. Sensors 2019, 19, 3165. [Google Scholar] [CrossRef] [Green Version]
- Xu, Y.; Ren, J.; Wang, G.; Zhang, C.; Yang, J.; Zhang, Y. A blockchain-based nonrepudiation network computing service scheme for industrial IoT. IEEE Trans. Ind. Inform. 2019, 15, 3632–3641. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Garg, S.; Krishna, D.N.G.; Kaddoum, G.; Jayakody, D.N.K. A blockchain-based framework for lightweight data sharing and energy trading in V2G network. IEEE Trans. Veh. Technol. 2020, 69, 5799–5812. [Google Scholar] [CrossRef]
- AlSkaif, T.; Holthuizen, B.; Schram, W.; Lampropoulos, I.; Van Sark, W. A blockchain-based configuration for balancing the electricity grid with distributed assets. World Electr. Veh. J. 2020, 11, 62. [Google Scholar] [CrossRef]
- Xu, Z.; Liang, W.; Li, K.C.; Xu, J.; Jin, H. A blockchain-based roadside unit-assisted authentication and key agreement protocol for internet of vehicles. J. Parallel Distrib. Comput. 2021, 149, 29–39. [Google Scholar] [CrossRef]
- Li, H.; Han, D.; Tang, M. A Privacy-Preserving Charging Scheme for Electric Vehicles Using Blockchain and Fog Computing. IEEE Syst. J. 2020, 15, 3189–3200. [Google Scholar] [CrossRef]
- Huang, Z.; Li, Z.; Lai, C.S.; Zhao, Z.; Wu, X.; Li, X.; Tong, N.; Lai, L.L. A Novel Power Market Mechanism Based on Blockchain for Electric Vehicle Charging Stations. Electronics 2021, 10, 307. [Google Scholar] [CrossRef]
- Lasla, N.; Al-Ammari, M.; Abdallah, M.; Younis, M. Blockchain based trading platform for electric vehicle charging in smart cities. IEEE Open J. Intell. Transp. Syst. 2020, 1, 80–92. [Google Scholar] [CrossRef]
- Su, Z.; Wang, Y.; Xu, Q.; Fei, M.; Tian, Y.C.; Zhang, N. A secure charging scheme for electric vehicles with smart communities in energy blockchain. IEEE Internet Things J. 2018, 6, 4601–4613. [Google Scholar] [CrossRef] [Green Version]
- Kim, M.; Park, K.; Yu, S.; Lee, J.; Park, Y.; Lee, S.W.; Chung, B. A secure charging system for electric vehicles based on blockchain. Sensors 2019, 19, 3028. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Jiang, Y.; Shen, X.; Zheng, S. An Effective Data Sharing Scheme Based on Blockchain in Vehicular Social Networks. Electronics 2021, 10, 114. [Google Scholar] [CrossRef]
- Umar, J.M.; Rehman, M.; Javaid, N.; Aldegheishem, A.; Alrajeh, N.; Tahir, M. Blockchain-Based Secure Data Storage for Distributed Vehicular Networks. Appl. Sci. 2020, 10, 2011. [Google Scholar]
- Wang, Y.; Su, Z.; Zhang, N. BSIS: Blockchain-based secure incentive scheme for energy delivery in vehicular energy network. IEEE Trans. Ind. Inform. 2019, 15, 3620–3631. [Google Scholar] [CrossRef]
- Fu, Z.; Dong, P.; Ju, Y. An intelligent electric vehicle charging system for new energy companies based on consortium blockchain. J. Clean. Prod. 2020, 261, 121219. [Google Scholar] [CrossRef]
- Oham, C.; Michelin, R.A.; Jurdak, R.; Kanhere, S.S.; Jha, S. B-FERL: Blockchain based framework for securing smart vehicles. Inf. Process. Manag. 2021, 58, 102426. [Google Scholar] [CrossRef]
- Zhou, Z.; Wang, B.; Guo, Y.; Zhang, Y. Blockchain and computational intelligence inspired incentive-compatible demand response in internet of electric vehicles. IEEE Trans. Emerg. Top. Comput. Intell. 2019, 3, 205–216. [Google Scholar] [CrossRef]
- Huang, X.; Xu, C.; Wang, P.; Liu, H. LNSC: A security model for electric vehicle and charging pile management based on blockchain ecosystem. IEEE Access 2018, 6, 13565–13574. [Google Scholar] [CrossRef]
- Jabbar, R.; Kharbeche, M.; Al-Khalifa, K.; Krichen, M.; Barkaoui, K. Blockchain for the internet of vehicles: A decentralized IoT solution for vehicles communication using Ethereum. Sensors 2020, 20, 3928. [Google Scholar] [CrossRef] [PubMed]
- Khan, P.W.; Byun, Y.C. Smart contract centric inference engine for intelligent electric vehicle transportation system. Sensors 2020, 20, 4252. [Google Scholar] [CrossRef] [PubMed]
- Kudva, S.; Badsha, S.; Sengupta, S.; Khalil, I.; Zomaya, A. Towards secure and practical consensus for blockchain based vanet. Inf. Sci. 2021, 545, 170–187. [Google Scholar] [CrossRef]
- Jin, Z.; Wu, R.; Chen, X.; Li, G. Charging guiding strategy for electric taxis based on consortium blockchain. IEEE Access 2019, 7, 144144–144153. [Google Scholar] [CrossRef]
- Xu, G.; Liu, Y.; Xing, J.; Luo, T.; Gu, Y.; Liu, S.; Zheng, X.; Vasilakos, A.V. SG-PBFT: A Secure and Highly Efficient Blockchain PBFT Consensus Algorithm for Internet of Vehicles. arXiv 2021, arXiv:2101.01306. [Google Scholar] [CrossRef]
- Shi, Q.; Zhang, H. Fault diagnosis of an autonomous vehicle with an improved SVM algorithm subject to unbalanced datasets. IEEE Trans. Ind. Electron. 2020, 68, 6248–6256. [Google Scholar] [CrossRef]
- Singh, M.; Kim, S. Blockchain based intelligent vehicle data sharing framework. arXiv 2017, arXiv:1708.09721. [Google Scholar]
- Singh, M.; Kim, S. Branch based blockchain technology in intelligent vehicle. Comput. Netw. 2018, 145, 219–231. [Google Scholar] [CrossRef]
- Rodrigues, J.; Hsing, R.; Chen, M.; Jiao, B. Guest editorial on vehicular communications and applications. J. Netw. Comput. Appl. 2013, 36, 1273–1274. [Google Scholar] [CrossRef]
- Goyat, R.; Kumar, G.; Alazab, M.; Conti, M.; Rai, M.K.; Thomas, R.; Saha, R.; Hoon-Kim, T. Blockchain-based Data Storage with Privacy and Authentication in Internet-of-Things. IEEE Internet Things J. 2020, 9, 14203–14215. [Google Scholar] [CrossRef]
- Ashfaq, T.; Younis, M.A.; Rizwan, S.; Iqbal, Z.; Mehmood, S.; Javaid, N. Consensus Based Mechanism Using Blockchain for Intensive Data of Vehicles. In International Conference on Broadband and Wireless Computing, Communication and Applications; Springer: Cham, Switzerland, 2019; pp. 44–55. [Google Scholar]
- Kamvar, S.D.; Schlosser, M.T.; Garcia-Molina, H. The eigentrust algorithm for reputation management in p2p networks. In Proceedings of the 12th International Conference on World Wide Web, Budapest, Hungary, 20–24 May 2003; pp. 640–651. [Google Scholar]
- Buterin, V. Ethereum White Paper: A Next Generation Smart Contract Decentralized Application Platform, First Version; 2014; p. 53. Available online: https://staging.weteachblockchain.org/ (accessed on 20 June 2021).
- Loi, L.; Chu, D.-H.; Olickel, H.; Saxena, P.; Hobor, A. Making smart contracts smarter. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 254–269. [Google Scholar]
- Halo Block, M. How To Use Oyente, A Smart Contract Security Analyzer—Solidity Tutorial. 2020. Available online: https://medium.com/haloblock/how-to-use-oyente-a-smart-contract-security-analyzer-solidity-tutorial-86671be93c4b (accessed on 20 April 2020).
- Ittay, E.; Sirer, E.G. Majority is not enough: Bitcoin mining is vulnerable. In Proceedings of the International Conference on Financial Cryptography and Data Security, Christ Church, Barbados, 3–7 March 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 436–454. [Google Scholar]
- Vanessa, C.; Albuquerque, C.; Jesus, E.; Rocha, A. On the detection of selfish mining and stalker attacks in blockchain networks. Ann. Telecommun. 2020, 75, 143–152. [Google Scholar]
- Grunspan, C.; Pérez-Marco, R. On profitability of selfish mining. arXiv 2018, arXiv:1805.08281. [Google Scholar]
- Landa, R.; Griffin, D.; Clegg, R.G.; Mykoniati, E.; Rio, M. A sybilproof indirect reciprocity mechanism for peer-to-peer networks. In Proceedings of the IEEE INFOCOM, Rio de Janerio, Brazil, 19–25 April 2009; pp. 343–351. [Google Scholar]






| Parameter | Value |
|---|---|
| status | true Transaction mined and execution succeed |
| transaction hash | 0xa4f56,…,b10edd1985594 |
| from | 0x5B38D,…,eddC4 |
| to | VN_Authentication.(constructor) |
| gas | 2507800 gas |
| transaction cost | 2180695 gas |
| execution cost | 2180695 gas |
| hash | 0xa4f5,…,d1985594 |
| input | 0x608…10032 |
| decoded input | {} |
| decoded output | - |
| logs | [] |
| value | 0 wei |
| Parameter | Value |
|---|---|
| status | true Transaction mined and execution succeed |
| transaction hash | 0xe19a,…,dee9d |
| from | 0x5B38,…,dC4 |
| to | Reputation.(constructor) |
| gas | 477940 gas |
| transaction cost | 415600 gas |
| execution cost | 415600 gas |
| input | 0x608…30029 |
| decoded input | {} |
| decoded output | - |
| logs | [] |
| value | 0 wei |
| Parameter | Value |
|---|---|
| status | true Transaction mined and execution succeed |
| transaction hash | 0x5eac1f9ea,…,71b6e139e |
| from | 0xca35b, …, a733c |
| to | Storage.(constructor) |
| gas | 144529 gas |
| transaction cost | 125677 gas |
| execution cost | 125677 gas |
| hash | 0x98933,…, 75f15 |
| input | 0x60806,…,70033 |
| decoded input | { } |
| decoded output | - |
| logs | [] |
| value | 0 wei |
| Limitations | Proposed Solutions | Validations |
|---|---|---|
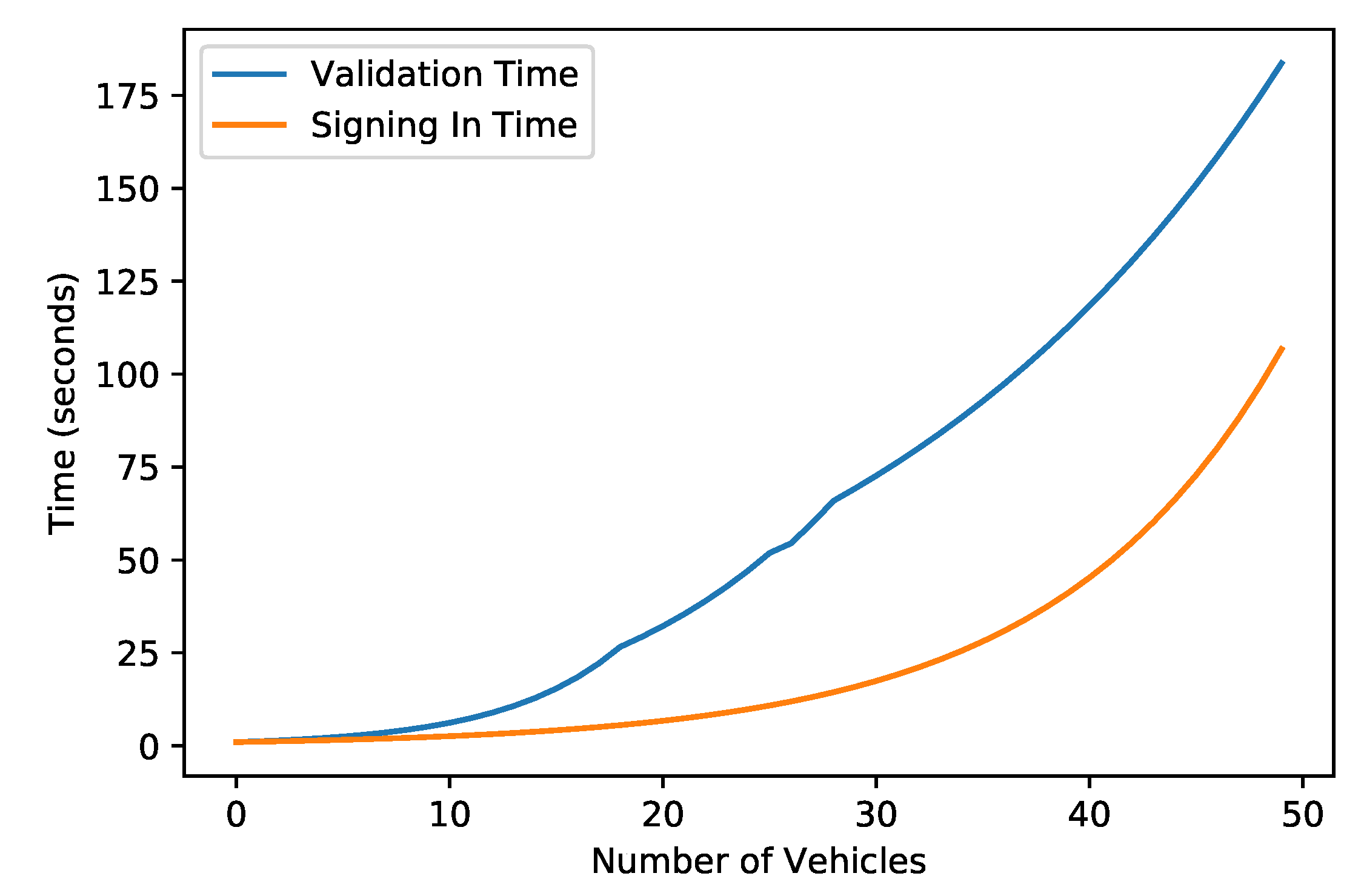
| Intensive data increase the computational power and delay | Division of data into multiple chains | Multi-chains are shown in terms of the relationship between the amount of data generated and time taken, as shown in Figure 9 |
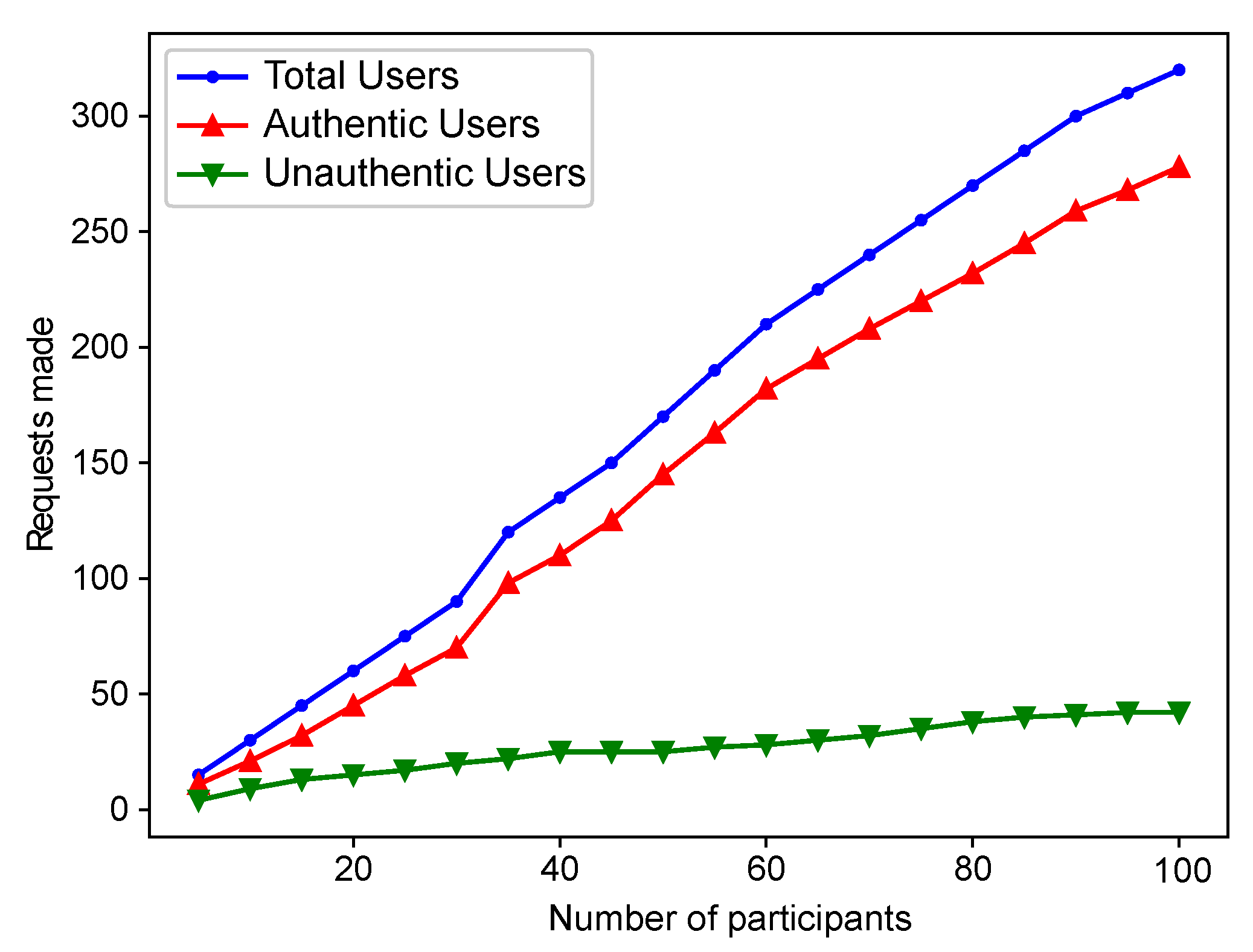
| Insecure communication | Blockchain, CA, authentication process, and AES are used to provide secure communication in the proposed system | Figure 7 shows the relationship between authentic and unauthentic users. |
| Inefficient storage management | Through IPFS, data are not stored on blockchain, only hashes of data are stored on blockchain | Figure 6 shows the results of IPFS storage |
| Road congestion | To tackle the road congestion, intersection criteria are set and followed | Intersection criteria are shown in Figure 10 |
| Validation of transactions | The encryption technique AES is used for the validation of data | Figure 9 shows the computational time used for encryption |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ashfaq, T.; Khalid, R.; Yahaya, A.S.; Aslam, S.; Azar, A.T.; Alkhalifah, T.; Tounsi, M. An Intelligent Automated System for Detecting Malicious Vehicles in Intelligent Transportation Systems. Sensors 2022, 22, 6318. https://doi.org/10.3390/s22176318
Ashfaq T, Khalid R, Yahaya AS, Aslam S, Azar AT, Alkhalifah T, Tounsi M. An Intelligent Automated System for Detecting Malicious Vehicles in Intelligent Transportation Systems. Sensors. 2022; 22(17):6318. https://doi.org/10.3390/s22176318
Chicago/Turabian StyleAshfaq, Tehreem, Rabiya Khalid, Adamu Sani Yahaya, Sheraz Aslam, Ahmad Taher Azar, Tamim Alkhalifah, and Mohamed Tounsi. 2022. "An Intelligent Automated System for Detecting Malicious Vehicles in Intelligent Transportation Systems" Sensors 22, no. 17: 6318. https://doi.org/10.3390/s22176318
APA StyleAshfaq, T., Khalid, R., Yahaya, A. S., Aslam, S., Azar, A. T., Alkhalifah, T., & Tounsi, M. (2022). An Intelligent Automated System for Detecting Malicious Vehicles in Intelligent Transportation Systems. Sensors, 22(17), 6318. https://doi.org/10.3390/s22176318








