Prevention of Cyber Security with the Internet of Things Using Particle Swarm Optimization
Abstract
:1. Introduction
1.1. Primary Literature Exploration
1.2. Proposed Methodology
1.3. Objectives
2. System Model: Pre-Processing
2.1. Data Cleaning and Normalization
2.2. Discretization and Integration of Data
2.3. Feature Selection
3. Analysis Using AI Optimization Procedure
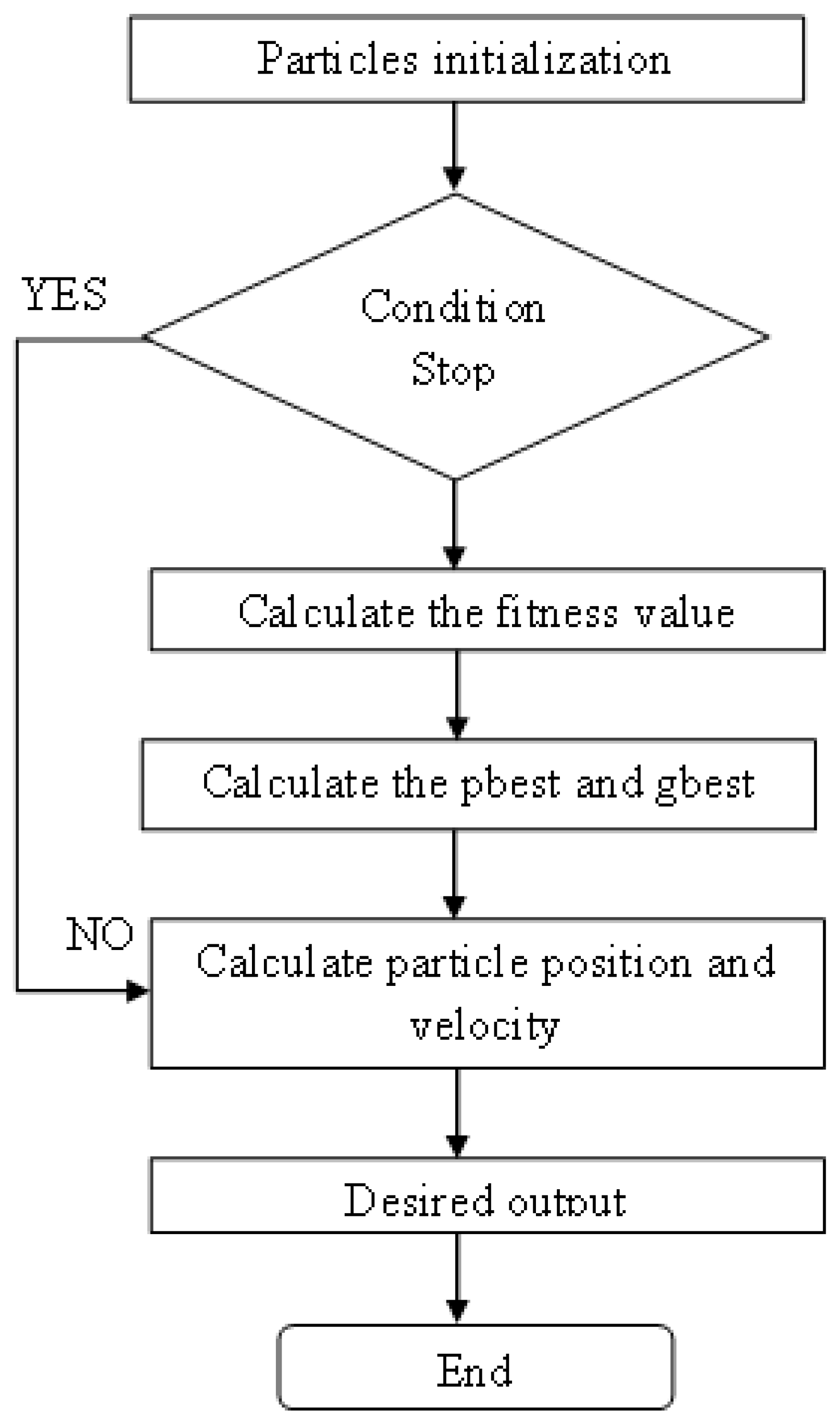
3.1. Particle Swarm Optimization
3.2. Ant Colony Optimization
3.3. Genetic Algorithm
4. Dataset
Outcomes
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Liu, X.; Liu, Y.; Liu, A.; Yang, L.T. Defending on–off attacks using light probing messages in smart sensors for industrial communication systems. IEEE Trans. Ind. Inf. 2018, 14, 3801–3811. [Google Scholar] [CrossRef]
- Patil, R.; Dudeja, H.; Modi, C. Designing an efficient security framework for detecting intrusions in virtual network of cloud computing. Comput. Secur. 2019, 85, 402–422. [Google Scholar] [CrossRef]
- Mirjalili, S.; Wang, G.G.; Coelho, L.D.S. Binary optimization using hybrid particle swarm optimization and gravitational search algorithm. Neural Comput. Appl. 2014, 25, 1423–1435. [Google Scholar] [CrossRef]
- Mazini, M.; Shirazi, B.; Mahdavi, I. Anomaly network-based intrusion detection system using a reliable hybrid artificial bee colony and AdaBoost algorithms. J. King Saud. Univ. Comput. Inf. Sci. 2018, 31, 541–553. [Google Scholar] [CrossRef]
- Huda, R.K.; Banka, H. Efficient feature selection and classification algorithm based on PSO and rough sets. Neural Comput. Appl. 2018, 31, 4287–4303. [Google Scholar] [CrossRef]
- Aljuhani, A.; Alharbi, T.; Taylor, B. Mitigation of Application Layer DDoS Flood Attack Against Web Servers. J. Inf. Secur. Cybercrimes Res. 2019, 2, 83–95. [Google Scholar] [CrossRef]
- Fadlil, A.; Riadi, I.; Aji, S. Review of detection DDOS attack detection using naive bayes classifier for network forensics. Bull. Electr. Eng. Inform. 2017, 6, 140–148. [Google Scholar] [CrossRef]
- Casola, V.; de Benedictis, A.; Rak, M.; Villano, U. Toward the automation of threat modeling and risk assessment in iot systems. Int. Things 2019, 7, 100056. [Google Scholar] [CrossRef]
- Cagnazzo, M.; Hertlein, M.; Holz, T.; Pohlmann, N. Threat modeling for mobile health systems. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), Barcelona, Spain, 15–18 April 2018; pp. 314–319. [Google Scholar]
- Elmasry, W.; Akbulut, A.; Zaim, A.H. Evolving deep learning architectures for network intrusion detection using a double PSO metaheuristic. Comput. Netw. 2020, 168, 107042. [Google Scholar] [CrossRef]
- Khadidos, A.O.; Shitharth, S.; Khadidos, A.O.; Sangeetha, K.; Alyoubi, K.H. Healthcare Data Security Using IoT Sensors Based on Random Hashing Mechanism. J. Sens. 2022, 2022, 8457116. [Google Scholar] [CrossRef]
- Schaad, A.; Binder, D. Ml-supported identification and prioritization of threats in the ovvl threat modelling tool. In Data and Applications Security and Privacy XXXIV; Singhal, A., Vaidya, J., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 274–285. [Google Scholar]
- Sion, L.; van Landuyt, D.; Wuyts, K.; Joosen, W. Privacy risk assessment for data subject-aware threat modeling. In Proceedings of the 2019 IEEE Security and Privacy Workshops (SPW), San Francisco, CA, USA, 19–23 May 2019; pp. 64–71. [Google Scholar]
- Malik, A.J.; Khan, F.A. A hybrid technique using binary particle swarm optimization and decision tree pruning for network intrusion detection. Clust. Comput. 2018, 21, 667–680. [Google Scholar] [CrossRef]
- Garg, S.; Batra, S. Fuzzified cuckoo based clustering technique for network anomaly detection. Comput. Electr. Eng. 2018, 71, 798–817. [Google Scholar] [CrossRef]
- Moustafa, N.; Creech, G.; Sitnikova, E.; Keshk, M. Collaborative anomaly detection framework for handling big data of cloud computing. In Proceedings of the 2017 Military Communications and Information Systems Conference (MilCIS), Canberra, Australia, 14–16 November 2017; pp. 1–6. [Google Scholar]
- Khadidos, A.O.; Manoharan, H.; Selvarajan, S.; Khadidos, A.O.; Alyoubi, K.H.; Yafoz, A. A Classy Multifacet Clustering and Fused Optimization Based Classification Methodologies for SCADA Security. Energies 2022, 15, 3624. [Google Scholar] [CrossRef]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.; Du, X.; Guizani, M. A survey of machine and deep learning methods for internet of things (IoT) security. arXiv 2018, arXiv:1807.11023. [Google Scholar] [CrossRef]
- Chaabouni, N.; Mosbah, M.; Zemmari, A.; Sauvignac, C.; Faruki, P. Network Intrusion Detection for IoT Security based on Learning Techniques. IEEE Commun. Surv. Tutor. 2019, 21, 2671–2701. [Google Scholar] [CrossRef]
- Farivar, F.; Haghighi, M.S.; Jolfaei, A.; Alazab, M. Artificial intelligence for detection, estimation, and compensation of malicious attacks in nonlinear cyber-physical systems and industrial IoT. IEEE Trans. Ind. Inf. 2020, 16, 2716–2725. [Google Scholar] [CrossRef]
- Setiawan, B.; Djanali, S.; Ahmad, T. Increasing accuracy and completeness of intrusion detection model using fusion of normalization, feature selection method and support vector machine. Int. J. Intell. Eng. Syst. 2019, 12, 378–389. [Google Scholar] [CrossRef]
- Kuzlu, M.; Fair, C.; Guler, O. Role of Artificial Intelligence in the Internet of Things (IoT) cybersecurity. Discov. Internet Things 2021, 1, 7. [Google Scholar] [CrossRef]
- McDermott, D.; Isaacs, J.P.; Petrovski, A.V. Evaluating awareness and perception of botnet activity within consumer internet-of-things (IoT) networks. Informatics 2019, 6, 8. [Google Scholar] [CrossRef]
- Wang, Y.; Geng, X.; Zhang, F.; Ruan, J. An Immune Genetic Algorithm for Multi-Echelon Inventory Cost Control of IoT Based Supply Chains. IEEE Access 2018, 6, 8547–8555. [Google Scholar] [CrossRef]
- Han, J.; Jeon, Y.; Kim, J. Security considerations for secure and trustworthy smart home system in the IoT environment. In Proceedings of the 2015 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 28–30 October 2015; pp. 1116–1118. [Google Scholar] [CrossRef]
- Kraijak, S.; Tuwanut, P. A survey on IoT architectures, protocols, applications, security, privacy, real-world implementation and future trends. In Proceedings of the 11th International Conference on Wireless Communications, Networking and Mobile Computing (WiCOM 2015), Shanghai, China, 21–23 September 2015; pp. 1–6. [Google Scholar]
- Jun, Y.; Craig, A.; Shafik, W.; Sharif, L. Artificial Intelligence Application in Cybersecurity and Cyberdefense. Wirel. Commun. Mob. Comput. 2021, 2021, 3329581. [Google Scholar] [CrossRef]
- Suroor, N.; Hassan, S.I. Identifying the factors of modern-day stress using machine learning. Int. J. Eng. Sci. Technol. 2017, 9, 229–234. [Google Scholar]
- Akojwar, S.; Kshirsagar, P. A Novel Probabilistic-PSO Based Learning Algorithm for Optimization of Neural Networks for Benchmark Problems. Wseas Trans. Electron. 2016, 7, 79–84. [Google Scholar]
- Shamshirband, S.; Anuar, N.B.; Kiah, M.L.M.; Patel, A. An appraisal and design of a multi -agent system based cooperative wireless intrusion detection computational intelligence technique. Eng. Appl. Artif. Intell. 2013, 26, 2105–2127. [Google Scholar] [CrossRef]
- Alabbas, A.R.; Hassnawi, L.A.; Ilyas, M.; Pervaiz, H.; Abbasi, Q.H.; Bayat, O. Performance enhancement of safety message communication via designing dynamic power control mechanisms in vehicular ad hoc networks. Comput. Intell. 2021, 37, 1286–1303. [Google Scholar] [CrossRef]
- Galeano-Brajones, J.; Carmona-Murillo, J.; Valenzuela-Valdés, J.F.; Luna-Valero, F. Detection and mitigation of DoS and DDoS attacks in iot-based stateful SDN: An experimental approach. Sensors 2020, 20, 816. [Google Scholar] [CrossRef]
- Qi, B.W. Analysis on the Application of artificial Intelligence in classroom. J. Phys. Conf. Ser. 2019, 1345, 402–420. [Google Scholar]
- Sarker, I.H.; Furhad, M.H.; Nowrozy, R. AI-Driven Cybersecurity: An Overview, Security Intelligence Modeling and Research Directions. SN Comput. Sci. 2021, 2, 1–18. [Google Scholar] [CrossRef]
- Bao, H.; He, H.; Liu, Z.; Liu, Z. Research on information security situation awareness system based on big data and artificial intelligence technology. In Proceedings of the 2019 international conference on robots intelligent system (ICRIS), Haikou, China, 15–16 June 2019; pp. 318–322. [Google Scholar]
- Shitharth, S.; Kshirsagar, P.R.; Praveen, B.; Khaled, K.; Omar, A. An Innovative Perceptual Pigeon Galvanized Optimization (PPGO) Based Likelihood Naïve Bayes (LNB) Classification Approach for Network Intrusion Detection System. IEEE Access 2022, 10, 46424–46441. [Google Scholar] [CrossRef]
- Holzinger, A.; Plass, M.; Holzinger, K.; Crişan, G.C.; Pintea, C.M.; Palade, V. Towards interactive machine learning (IML): Applying ant colony algorithms to solve the traveling salesman problem with the human-in-the-loop approach. In Availability, Reliability, and Security in Information Systems; Buccafurri, F., Holzinger, A., Kieseberg, P., Tjoa, A.M., Weippl, E., Eds.; Springer: Cham, Switzerland, 2016; pp. 81–95. [Google Scholar]
- Sudhir, G.; Akojwar, P.; Kshirsagar, R. Performance Evolution of Optimization Techniques for Mathematical Benchmark Functions. Int. J. Comput. 2016, 1, 231–236. [Google Scholar]
- Wiafe, I.; Koranteng, F.N.; Obeng, E.N.; Assyne, N.; Wiafe, A.; Gulliver, S.R. Artificial Intelligence for Cybersecurity: A Systematic Mapping of Literature. IEEE Access 2020, 8, 146598–146612. [Google Scholar]
- Dilek, S.; Çakır, H.; Aydın, M. Applications of Artificial Intelligence Techniques to Combating Cyber Crimes: A Review. Int. J. Artif. Intell. Appl. 2015, 6, 6. [Google Scholar] [CrossRef]
- Padmaja, M.; Shitharth, S.; Prasuna, K.; Chaturvedi, A.; Kshirsagar, P.R.; Vani, A. Grow of Artificial Intelligence to Challenge Security in IoT Application. Wirel. Pers. Commun. 2021. [Google Scholar] [CrossRef]
- Shitharth, S.; Prasad, K.M.; Sangeetha, K.; Kshirsagar, P.R.; Babu, T.S.; Alhelou, H.H. An Enriched RPCO-BCNN Mechanisms for Attack Detection and Classification in SCADA Systems. IEEE Access 2021, 9, 156297–156312. [Google Scholar] [CrossRef]
- Mahdi, K.; Kazuaki, N.; Yuki, H.; Naoko, N.; Noboru, B. Model Inversion Attack by Integration of Deep Generative Models: Privacy-Sensitive Face Generation From a Face Recognition System. IEEE Trans. Inf. Forensics Secur. 2022, 17, 357–372. [Google Scholar]











| Reference | Data Technique Used | Type of Algorithm | Objectives |
|---|---|---|---|
| [22] | Internet of Things | Artificial Intelligence | Cyber security operations with high network gateways |
| [27] | Layering procedure using Internet of Things | Artificial Intelligence | Compatibility of transportation applications with cyber security |
| [33] | - | Artificial Intelligence | Intelligent interactive devices for smart home applications with cyber security |
| [34] | Intrusion detection | Artificial Intelligence | Better service for cyber security operation and intelligent management |
| [39] | Pathway management | Artificial Intelligence | Increasing the secured operations for industrial applications |
| [40,41,42,43] | Deep generative model | Deep learning | Face recognition with a clone detection mechanism |
| Proposed | Internet of Things and cloud management | Artificial Intelligence | Building smart homes with enhanced cyber security features |
| KDD Dataset | Abnormal | Normal | Total | ||
|---|---|---|---|---|---|
| DOS | Probing | U2R | |||
| Training data | 55,967 | 12,378 | 75 | 70,656 | 139,076 |
| Test data | 7590 | 3021 | 220 | 9823 | 20,654 |
| Algorithm | Attacks | Accuracy (%) | Precision (%) | Recall (%) | F-Measure (%) |
|---|---|---|---|---|---|
| GA | DOS | 98.90 | 98.90 | 94.90 | 96.89 |
| Probe | 84.78 | 91.89 | 68.12 | 70.01 | |
| U2R | 99.90 | 99.78 | 99.67 | 99.21 | |
| ACO | DOS | 98.89 | 97.95 | 95.87 | 98.45 |
| Probe | 86.23 | 88.92 | 84.54 | 83.67 | |
| U2R | 99.87 | 99.05 | 82.76 | 88.94 | |
| PSO | DOS | 99.50 | 99.93 | 99.54 | 99.65 |
| Probe | 86.78 | 88.90 | 86.98 | 84.81 | |
| U2R | 99.98 | 99.67 | 99.01 | 98.34 |
| F1 | F2 | h | Accuracy |
|---|---|---|---|
| 0.8 | 0.6 | 1.0 | 98.45 |
| 0.8 | 0.6 | 0.9 | 97.73 |
| 0.8 | 0.6 | 1.0 | 98.12 |
| 0.7 | 0.6 | 1.0 | 98.09 |
| 0.6 | 0.5 | 1.0 | 99.46 |
| Particles | Iterations | Accuracy | Precision | F-Measure |
|---|---|---|---|---|
| 2500 | 25 | 97.90 | 97.89 | 97.12 |
| 2500 | 26 | 98.06 | 97.03 | 97.56 |
| 2500 | 27 | 98.45 | 96.43 | 96.49 |
| 2500 | 28 | 98.23 | 97.63 | 98.62 |
| 2500 | 29 | 99.56 | 99.54 | 99.32 |
| 2500 | 30 | 97.96 | 97.87 | 97.51 |
| Features | Accuracy | Precision | F-Measure |
|---|---|---|---|
| 10 | 99.45 | 99.03 | 99.89 |
| 12 | 98.09 | 97.46 | 97.43 |
| 15 | 98.83 | 98.03 | 98.69 |
| 18 | 98.23 | 98.67 | 97.52 |
| 20 | 97.12 | 97.23 | 98.86 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alterazi, H.A.; Kshirsagar, P.R.; Manoharan, H.; Selvarajan, S.; Alhebaishi, N.; Srivastava, G.; Lin, J.C.-W. Prevention of Cyber Security with the Internet of Things Using Particle Swarm Optimization. Sensors 2022, 22, 6117. https://doi.org/10.3390/s22166117
Alterazi HA, Kshirsagar PR, Manoharan H, Selvarajan S, Alhebaishi N, Srivastava G, Lin JC-W. Prevention of Cyber Security with the Internet of Things Using Particle Swarm Optimization. Sensors. 2022; 22(16):6117. https://doi.org/10.3390/s22166117
Chicago/Turabian StyleAlterazi, Hassan A., Pravin R. Kshirsagar, Hariprasath Manoharan, Shitharth Selvarajan, Nawaf Alhebaishi, Gautam Srivastava, and Jerry Chun-Wei Lin. 2022. "Prevention of Cyber Security with the Internet of Things Using Particle Swarm Optimization" Sensors 22, no. 16: 6117. https://doi.org/10.3390/s22166117
APA StyleAlterazi, H. A., Kshirsagar, P. R., Manoharan, H., Selvarajan, S., Alhebaishi, N., Srivastava, G., & Lin, J. C.-W. (2022). Prevention of Cyber Security with the Internet of Things Using Particle Swarm Optimization. Sensors, 22(16), 6117. https://doi.org/10.3390/s22166117








