Decision Feedback Modulation Recognition with Channel Estimation for Amplify and Forward Two-Path Consecutive Relaying Systems
Abstract
:1. Introduction
- For the first time in the lecture, an AMR algorithm for TCRS using an AAF protocol is proposed in this work.
- The proposed algorithm makes use of the a posteriori probabilities that are acquired by the data detector as a priori knowledge to create the a posteriori expectations of the broadcast symbols, which are utilized as training symbols.
- Instead of using different algorithms to predict the channel impulse responses that occur between the source and relays, the source and the destination, and the relays and the destination, we estimate a single parameter called the overall channel impulse response, which includes all these connections.
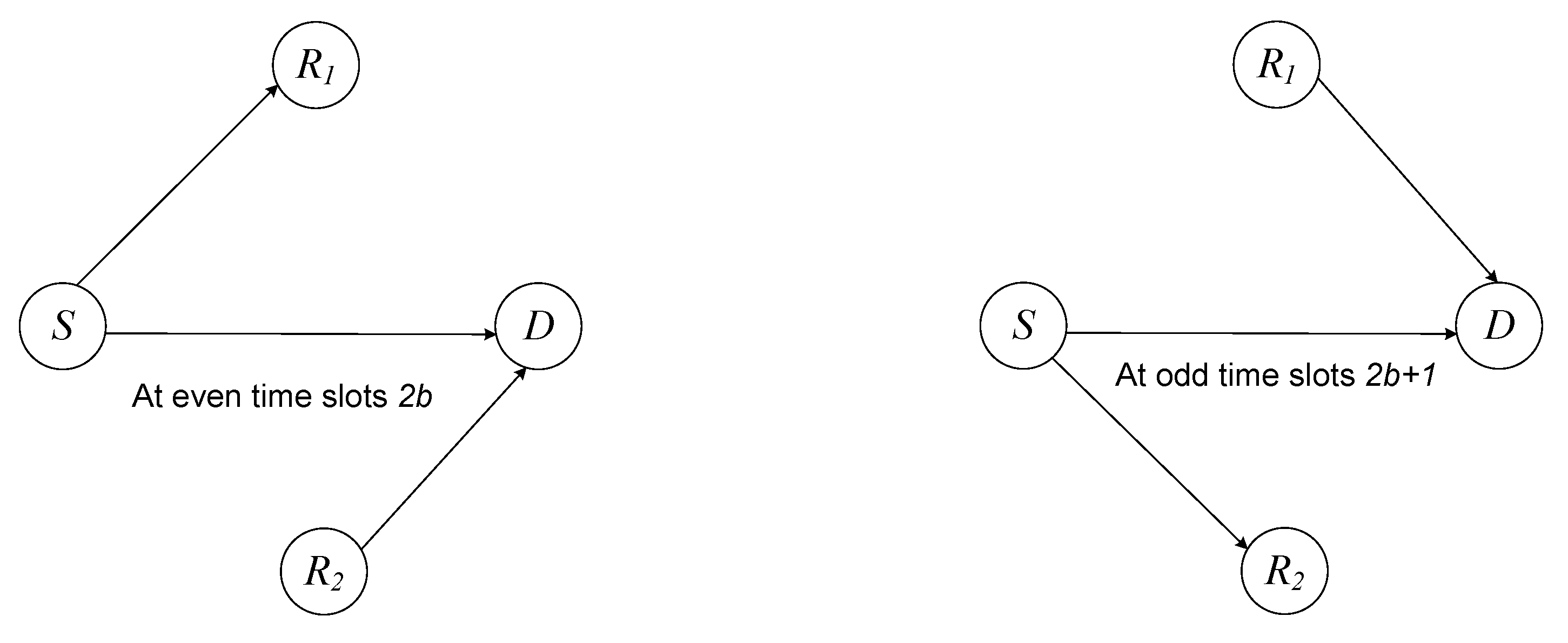
2. System Model
3. Proposed Algorithm
- E-process of the EM algorithm quantifies the expected value of given the existing estimations of the parameters and . In particular, we create the following function [42]Here signifies the average of the information symbols given the modulation type .
4. Practical Discussion
- The issue then arises of how the matrices of and are really computed in reality. Since the expectation function is linear, we produce the matrix by simply replacing each ingredient of with the relevant a posteriori expectation. Typically, the a posteriori expectation of the mth element of the wth vector , , given the modulation scheme is produced as [48]The wth vector is created by concatenating all of these samples. This process is repeated for all unknown information symbols with , 1, . Therefore, the matrix is formed following the same way as reported in (15) with the use of instead of .
- We are going to proceed with the widely held premise that the data symbols are not linked with one another. Therefore, the approximate computation for is as follows [34]
- In light of (30), computing the probability of for each modulation scheme is essential for the proposed recognition process. When we examine (4) and (11) more closely, we come to the conclusion that each information symbol is collected at the endpoint twice: once through the source-destination connection and once via the relay-destination route. As a result, the corresponding transmission structure may be thought of as being comparable to a convolutional encoder that only has a single memory component. A bank of N Bahl, Cocke, Jelinek, and RavivBCJR algorithms is used to create the optimum data detection, which is accomplished by employing a method that is similar to the one described in the earlier works of [38,39].
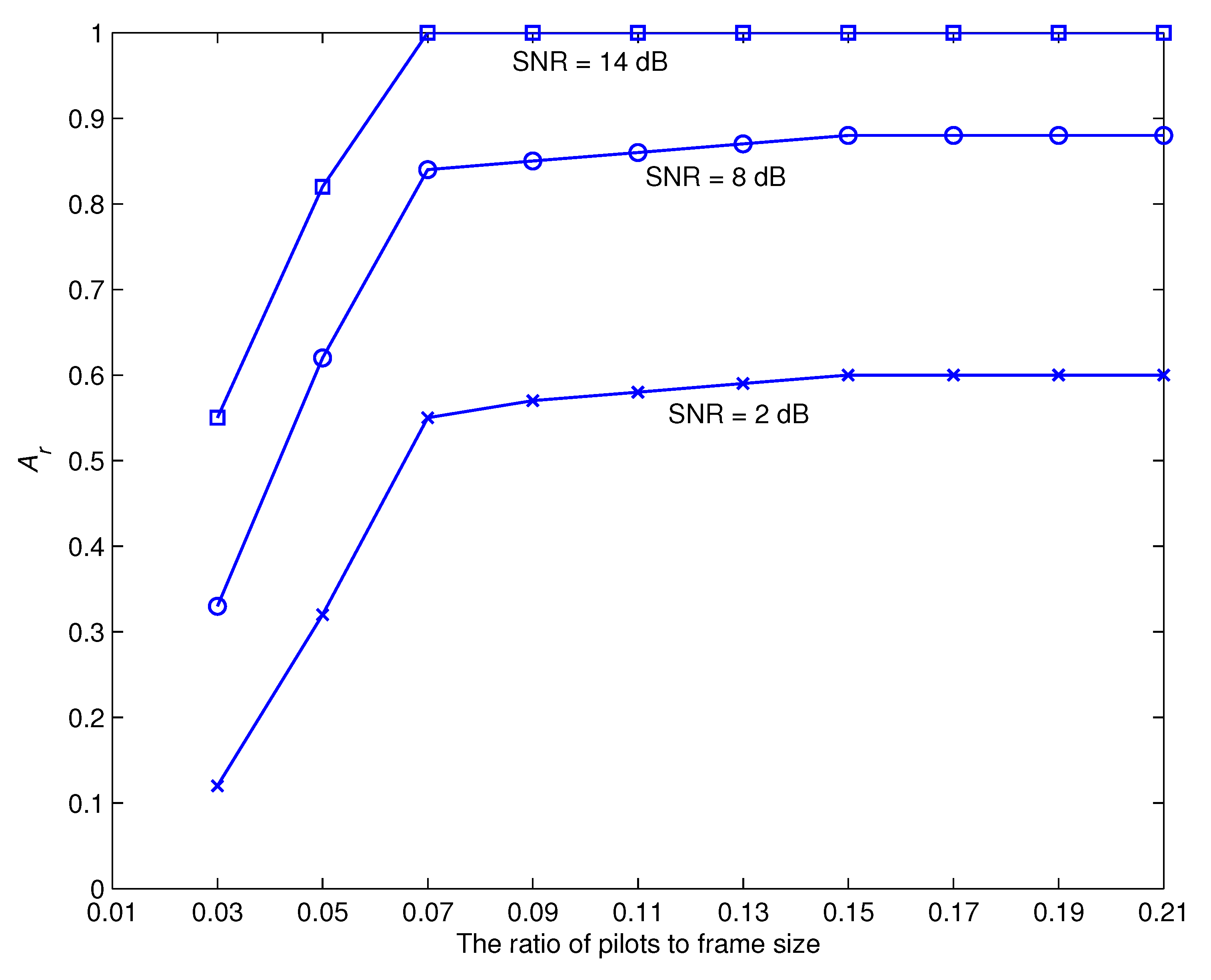
- In order to kick off the recognition and estimation processes, a small number of pilot symbols are included into the data symbols. As a result, the proposed approach is able to get preliminary estimations of the channel coefficient and the chosen modulation scheme. It is generally known that the accuracy of the evaluation will improve in proportion to the number of utilized pilots. Nevertheless, extending the length of the pilot symbols not only reduces the amount of energy that is allocated for the transfer of information but also slows down the data rate. As a consequence of this, the ratio between the specified amount of pilot symbols and the amount of the information symbols has to be sustained at a level that is as low as possible. This is accomplished by using the method that has been described, which refines the original estimations via a process of iterative improvement. We make use of the output of the demodulation procedure to compute the a posteriori expectations of the information symbols, which are then applied to the proposed recognizer and estimator as if they were pilot symbols.
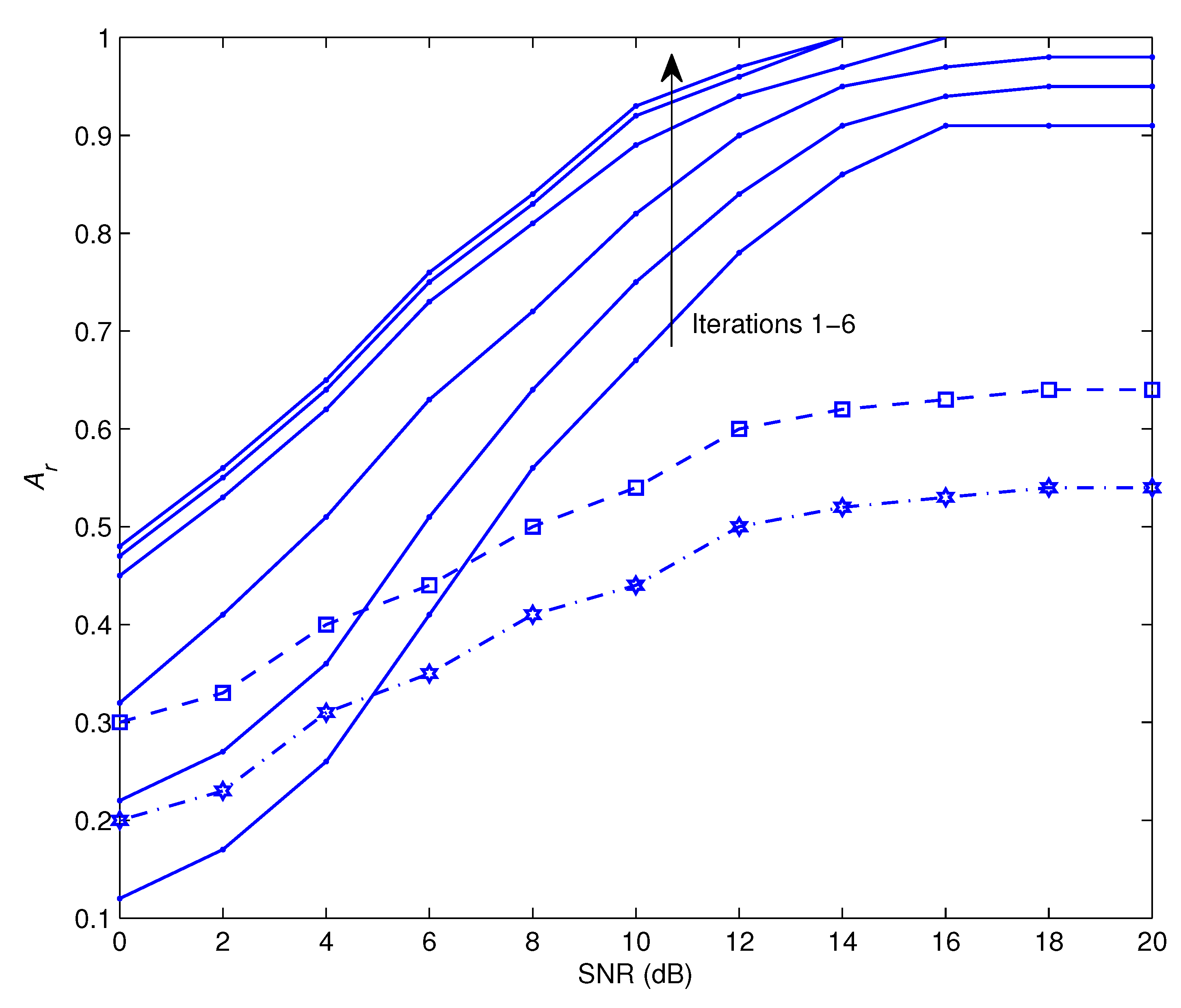
- It is worth noting that the quality of modulation recognition is strengthened by using a powerful error-correcting code to provide accurate feedback to the proposed technique. Furthermore, increasing the number of pilot symbols speeds up the suggested method’s convergence.
- The computational cost of the proposed AMR approach is examined by computing the number of needed floating point operations (fp) [15,50]. Multiplying two complex numbers needs 6 fp, whereas adding them only involves two fp. The study in the previous section shows that the required number of fp per iteration is roughly stated as . Assuming and with a processor speed of 10 Terafp per second, the processing time is 2 nanoseconds, which is sufficient for practical uses.
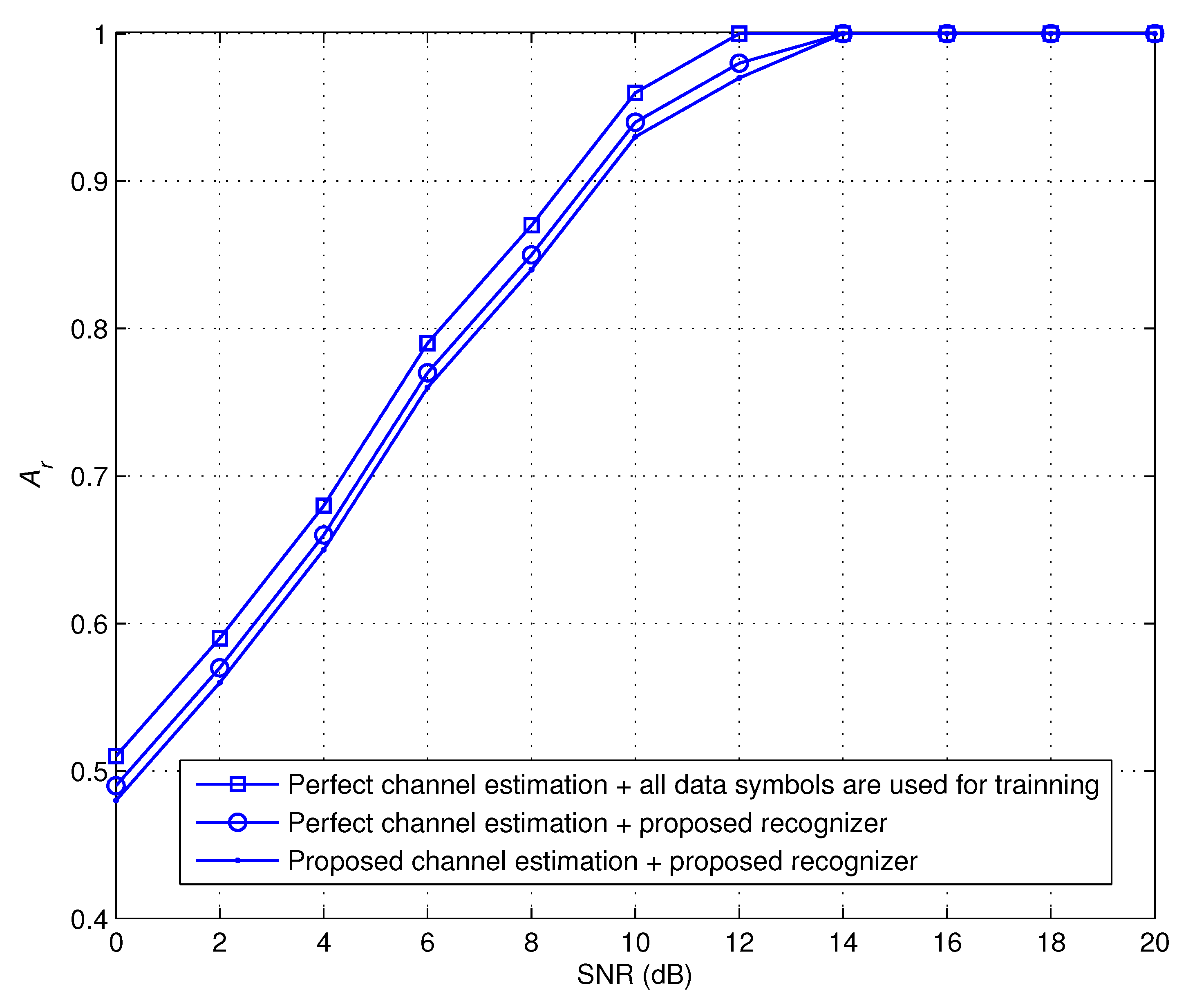
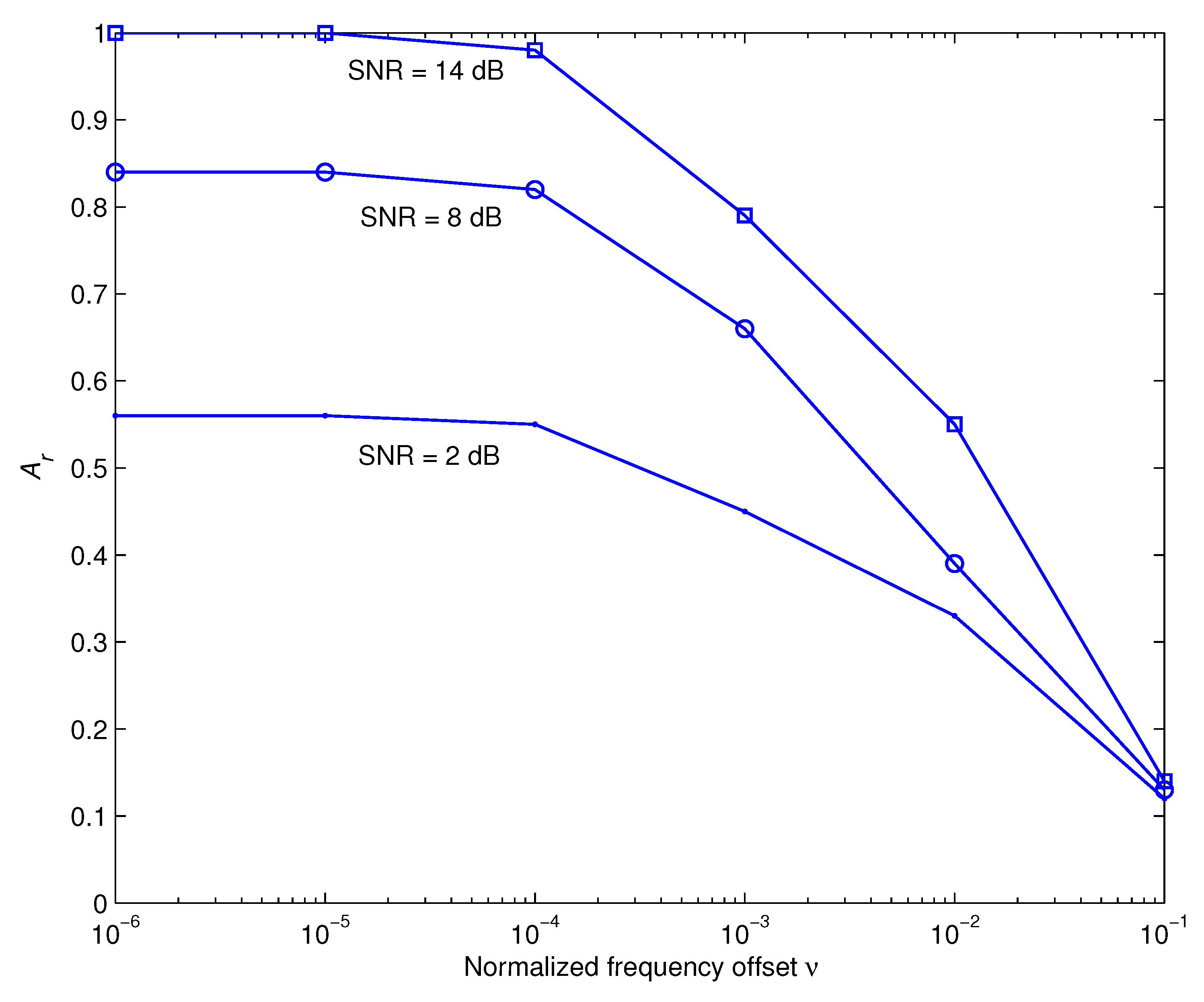
5. Simulation Results
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Candal-Ventureira, D.; González-Castaño, F.J.; Gil-Castiñeira, F.; Fondo-Ferreiro, P. Coordinated Allocation of Radio Resources to Wi-Fi and Cellular Technologies in Shared Unlicensed Frequencies. IEEE Access 2021, 9, 134435–134456. [Google Scholar] [CrossRef]
- Dobre, O.A. Signal Identification for Emerging Intelligent Radios: Classical Problems and New Challenges. IEEE Instrum. Meas. Mag. 2015, 18, 11–18. [Google Scholar] [CrossRef]
- Marey, M.; Mostafa, H. Turbo Modulation Identification Algorithm for OFDM Software-Defined Radios. IEEE Commun. Lett. 2021, 25, 1707–1711. [Google Scholar] [CrossRef]
- Marey, M.; Mostafa, H. Code-Aided Modulation Classification Algorithm for Multiuser Uplink SC-FDMA Systems. IEEE Wirel. Commun. Lett. 2021, 10, 1023–1027. [Google Scholar] [CrossRef]
- Marey, M.; Dobre, O.A. Blind Modulation Classification Algorithm for Single and Multiple-Antenna Systems Over Frequency-Selective Channels. IEEE Signal Process. Lett. 2014, 21, 1098–1102. [Google Scholar]
- Xing, Z.; Gao, Y. A Modulation Classification Algorithm for Multipath Signals Based on Cepstrum. IEEE Trans. Instrum. Meas. 2020, 69, 4742–4752. [Google Scholar] [CrossRef]
- Serbes, A.; Cukur, H.; Qaraqe, K. Probabilities of False Alarm and Detection for the First-Order Cyclostationarity Test: Application to Modulation Classification. IEEE Commun. Lett. 2020, 24, 57–61. [Google Scholar] [CrossRef]
- Zheng, J.; Lv, Y. Likelihood-Based Automatic Modulation Classification in OFDM with Index Modulation. IEEE Trans. Veh. Technol. 2018, 67, 8192–8204. [Google Scholar] [CrossRef]
- Gupta, R.; Kumar, S.; Majhi, S. Blind Modulation Classification for Asynchronous OFDM Systems Over Unknown Signal Parameters and Channel Statistics. IEEE Trans. Veh. Technol. 2020, 69, 5281–5292. [Google Scholar] [CrossRef]
- He, Y.; Evans, J.S. Adaptive Opportunistic Spatial Modulation for Boosting Transmit Diversity. IEEE Trans. Commun. 2022, 70, 4286–4298. [Google Scholar] [CrossRef]
- Bobrov, E.; Kropotov, D.; Lu, H.; Zaev, D. Massive MIMO Adaptive Modulation and Coding Using Online Deep Learning Algorithm. IEEE Commun. Lett. 2022, 26, 818–822. [Google Scholar] [CrossRef]
- Dobre, O.A.; Abdi, A.; Bar-Ness, Y.; Su, W. A Survey of Automatic Modulation Classification Techniques: Classical Approaches and New Developments. IET Commun. 2007, 1, 137–156. [Google Scholar] [CrossRef]
- El-Malek, A.A.; Zummo, S. A Bandwidth-Efficient Cognitive Radio with Two-Path Amplify-and-Forward Relaying. IEEE Wirel. Commun. Lett. 2015, 4, 66–69. [Google Scholar] [CrossRef]
- Yucek, T.; Arslan, H. OFDM Signal Identification and Transmission Parameter Estimation for Cognitive Radio Applications. In Proceedings of the IEEE Military Communications Conference, Boston, MA, USA, 19–21 October 1998; pp. 4056–4060. [Google Scholar]
- Marey, M.; Mostafa, H. Soft-Information Assisted Modulation Recognition for Reconfigurable Radios. IEEE Wirel. Commun. Lett. 2021, 10, 745–749. [Google Scholar] [CrossRef]
- Idris, S.; Karunathilake, T.; Förster, A. Survey and Comparative Study of LoRa-Enabled Simulators for Internet of Things and Wireless Sensor Networks. Sensors 2022, 22, 5546. [Google Scholar] [CrossRef]
- Hakim, G.P.N.; Habaebi, M.H.; Toha, S.F.; Islam, M.R.; Yusoff, S.H.B.; Adesta, E.Y.T.; Anzum, R. Near Ground Pathloss Propagation Model Using Adaptive Neuro Fuzzy Inference System for Wireless Sensor Network Communication in Forest, Jungle and Open Dirt Road Environments. Sensors 2022, 22, 3267. [Google Scholar] [CrossRef] [PubMed]
- Liu, K.; Xiang, X.; Yin, L. Radio Frequency Database Construction and Modulation Recognition in Wireless Sensor Networks. Sensors 2022, 22, 5715. [Google Scholar] [CrossRef]
- Yan, X.; Zhang, Y.; Rao, X.; Wang, Q.; Wu, H.C.; Wu, Y. Novel Cooperative Automatic Modulation Classification Using Vectorized Soft Decision Fusion for Wireless Sensor Networks. Sensors 2022, 22, 1797. [Google Scholar] [CrossRef] [PubMed]
- Markovic, G.B.; Sokolovic, V.S.; Dukic, M.L. Distributed Hybrid Two-Stage Multi-Sensor Fusion for Cooperative Modulation Classification in Large-Scale Wireless Sensor Networks. Sensors 2019, 19, 4339. [Google Scholar] [CrossRef] [PubMed]
- Zheng, S.; Qi, P.; Chen, S.; Yang, X. Fusion Methods for CNN-Based Automatic Modulation Classification. IEEE Access 2019, 7, 66496–66504. [Google Scholar] [CrossRef]
- Stankovic, V.; Host-Madsen, A.; Xiong, Z. Cooperative Diversity for Wireless Ad Hoc Networks. IEEE Signal Process. Mag. 2006, 23, 37–49. [Google Scholar] [CrossRef]
- Xiao, Y.; Jin, X.; Shen, Y.; Guan, Q. Joint Relay Selection and Adaptive Modulation and Coding for Wireless Cooperative Communications. IEEE Sens. J. 2021, 21, 25508–25516. [Google Scholar] [CrossRef]
- Lv, L.; Zhou, F.; Chen, J.; Al-Dhahir, N. Secure Cooperative Communications with an Untrusted Relay: A NOMA-Inspired Jamming and Relaying Approach. IEEE Trans. Inf. Forensics Secur. 2019, 14, 3191–3205. [Google Scholar] [CrossRef]
- Krikidis, I.; Thompson, J.S.; Mclaughlin, S.; Goertz, N. Max-min Relay Selection for Legacy Amplify-and-Forward Systems with Interference. IEEE Trans. Wirel. Commun. 2009, 8, 3016–3027. [Google Scholar] [CrossRef]
- Kim, Y.G.; Beaulieu, N.C. Exact BEP of Decode-and-Forward Cooperative Systems with Multiple Relays in Rayleigh Fading Channels. IEEE Trans. Veh. Technol. 2015, 64, 823–828. [Google Scholar] [CrossRef]
- Wan, H.; Høst-Madsen, A.; Nosratinia, A. Compress-and-Forward Via Multilevel Coding and Trellis Coded Quantization. IEEE Commun. Lett. 2021, 25, 1163–1167. [Google Scholar] [CrossRef]
- Zhang, Z.; Long, K.; Vasilakos, A.V.; Hanzo, L. Full-Duplex Wireless Communications: Challenges, Solutions, and Future Research Directions. Proc. IEEE 2016, 104, 1369–1409. [Google Scholar] [CrossRef]
- Zhong, C.; Suraweera, H.A.; Zheng, G.; Krikidis, I.; Zhang, Z. Wireless Information and Power Transfer with Full Duplex Relaying. IEEE Trans. Commun. 2014, 62, 3447–3461. [Google Scholar] [CrossRef]
- Laneman, N.; Tse, D.; Wornell, G. Cooperative Diversity in Wireless Networks - Efficient Protocols and Outage Behavior. IEEE Trans. Inf. Theory 2004, 50, 3062–3080. [Google Scholar] [CrossRef]
- Luo, C.; Gong, Y.; Zheng, F. Full Interference Cancellation for Two-Path Relay Cooperative Networks. IEEE Trans. Veh. Technol. 2011, 60, 343–347. [Google Scholar] [CrossRef]
- Li, L.; Poor, H.; Hanzo, L. Non-Coherent Successive Relaying and Cooperation: Principles, Designs, and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 1708–1737. [Google Scholar] [CrossRef]
- Marey, M. Solving IQ Mismatch Problem for Two-Path Successive Relaying OFDMA Uplink Systems with Direct Conversion Transceivers. IEEE Wirel. Commun. Lett. 2019, 8, 33–36. [Google Scholar] [CrossRef]
- Marey, M.; Mostafa, H. Iterative Channel Estimation Algorithm for Downlink MC-CDMA Systems with Two-Path Successive Relaying Transmission. IEEE Commun. Lett. 2019, 23, 668–671. [Google Scholar] [CrossRef]
- Wicaksana, H.; Ting, S.; Ho, C.; Chin, W.; Guan, Y. AF Two-Path Half Duplex Relaying with Inter-Relay Self Interference Cancellation: Diversity Analysis and its Improvement. IEEE Trans. Wirel. Commun. 2009, 8, 4720–4729. [Google Scholar] [CrossRef]
- Rankov, B.; Wittneben, A. Spectral Efficient Protocols for Half Duplex Fading Relay Channels. IEEE J. Sel. Areas Commun. 2007, 25, 379–389. [Google Scholar] [CrossRef]
- Fan, Y.; Thompson, C.W.J.; Poor, H. Recovering Multiplexing Loss through Successive Relaying Using Repetition Coding. IEEE Trans. Wirel. Commun. 2007, 6, 4484–4493. [Google Scholar] [CrossRef]
- Mostafa, H.; Marey, M.; Ahmed, M.; Dobre, O.A. Simplified Maximum-likelihood Detectors for Full-rate Alternate-relaying Cooperative Systems. IET Commun. 2013, 7, 1899–1906. [Google Scholar] [CrossRef]
- Mostafa, H.; Marey, M.; Ahmed, M.H.; Dobre, O.A. Decoding Techniques for Alternate-Relaying Cooperative Systems. EURASIP J. Wirel. Commun. Netw. 2013, 1, 1–13. [Google Scholar] [CrossRef]
- Marey, M.; Mostafa, H.; Alshebeili, S.A.; Dobre, O.A. Iterative Modulation Classification Algorithm for Two-Path Successive Relaying Systems. IEEE Wirel. Commun. Lett. 2021, 10, 2017–2021. [Google Scholar] [CrossRef]
- Marey, M.; Mostafa, H.; Alshebeili, S.A.; Dobre, O.A. Blind Modulation Identification Algorithm For Two-Path Successive Relaying Systems. IEEE Wirel. Commun. Lett. 2021, 10, 2369–2373. [Google Scholar] [CrossRef]
- Feng, X.; Wang, J.; Kuai, X.; Zhou, M.; Sun, H.; Li, J. Message Passing-Based Impulsive Noise Mitigation and Channel Estimation for Underwater Acoustic OFDM Communications. IEEE Trans. Veh. Technol. 2022, 71, 611–625. [Google Scholar] [CrossRef]
- Fernandez, J. Joint Synchronization and Compressive Channel Estimation for Frequency-Selective Hybrid mmWave MIMO Systems. IEEE Trans. Wirel. Commun. 2022, 21, 548–562. [Google Scholar] [CrossRef]
- Marey, M.; Mostafa, H.; Dobre, O.A.; Ahmed, M. Data Detection Algorithms for BICM Alternate-Relaying Cooperative Systems with Multiple-Antenna Destination. IEEE Trans. Veh. Technol. 2016, 65, 3802–3807. [Google Scholar] [CrossRef]
- Marey, M.; Dobre, O.A. Iterative Receiver Design for Uplink OFDMA Cooperative Systems. IEEE Trans. Broadcast. 2016, 62, 936–947. [Google Scholar] [CrossRef]
- Marey, M.; Dobre, O.A.; Inkol, R. Classification of Space-time Block Codes Based on Second-order Cyclostationarity with Transmission Impairments. IEEE Trans. Wirel. Commun. 2012, 11, 2574–2584. [Google Scholar] [CrossRef]
- Marey, M.; Dobre, O.A.; Inkol, R. Cyclostationarity-Based Blind Classification of STBCs for Cognitive Radio Systems. In Proceedings of the IEEE International Conference on Communications, Ottawa, ON, Canada, 10–15 June 2012; pp. 1–6. [Google Scholar]
- Marey, M.; Steendam, H. Novel Data Detection and Channel Estimation Algorithms for BICM OFDMA Uplink Asynchronous Systems in the Presence of IQ Imbalance. IEEE Trans. Wirel. Commun. 2014, 13, 2706–2716. [Google Scholar]
- Marey, M. Low Complexity IQ Mismatch Compensation Algorithm with Channel Awareness for Two-Path Successive Relay Networks. IEEE Commun. Lett. 2018, 22, 1002–1005. [Google Scholar] [CrossRef]
- Marey, M.; Dobre, O.A. Blind Modulation Classification for Alamouti STBC System with Transmission Impairments. IEEE Wirel. Commun. Lett. 2015, 4, 521–524. [Google Scholar] [CrossRef]
- Marey, M.; Guenach, M.; Steendam, H. Code-Aided Channel Tracking and Frequency Offset-Phase Noise Elimination for Multi-Carrier Systems. IEEE Signal Process. Lett. 2008, 15, 657–660. [Google Scholar] [CrossRef]
- Marey, M.; Steendam, H. The Effect of Narrowband Interference on Frequency Ambiguity Resolution for OFDM. In Proceedings of the IEEE Vehicular Technology Conference, Montreal, QC, Canada, 25–28 September 2006; pp. 1–5. [Google Scholar] [CrossRef]
- Bedeer, E.; Marey, M.; Dobre, O.; Baddour, K. Adaptive Bit Allocation for OFDM Cognitive Radio Systems with Imperfect Channel Estimation. In Proceedings of the IEEE Radio and Wireless Symposium, Santa Clara, CA, USA, 15–18 January 2012; pp. 359–362. [Google Scholar] [CrossRef]

| Abbreviation | Definition |
|---|---|
| AMR | Automatic modulation recognition |
| AAF | Amplify-and-forward |
| TCRS | Two-path consecutive relaying systems |
| MIMO | Multiple-input multiple-output |
| ML | Maximum-likelihood |
| EM | Expectation-maximization |
| DA | Data-aided |
| Pilot to Frame Size Ratio | Recognition Accuracy | Iterations Necessary to Converge |
|---|---|---|
| 0.03 | 0.72 | 14 |
| 0.05 | 0.91 | 10 |
| 0.07 | 1 | 6 |
| 0.09 | 1 | 4 |
| 0.11 | 1 | 3 |
| 0.13 | 1 | 2 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Marey, M.; Esmail, M.A.; Mostafa, H. Decision Feedback Modulation Recognition with Channel Estimation for Amplify and Forward Two-Path Consecutive Relaying Systems. Sensors 2022, 22, 6022. https://doi.org/10.3390/s22166022
Marey M, Esmail MA, Mostafa H. Decision Feedback Modulation Recognition with Channel Estimation for Amplify and Forward Two-Path Consecutive Relaying Systems. Sensors. 2022; 22(16):6022. https://doi.org/10.3390/s22166022
Chicago/Turabian StyleMarey, Mohamed, Maged Abdullah Esmail, and Hala Mostafa. 2022. "Decision Feedback Modulation Recognition with Channel Estimation for Amplify and Forward Two-Path Consecutive Relaying Systems" Sensors 22, no. 16: 6022. https://doi.org/10.3390/s22166022
APA StyleMarey, M., Esmail, M. A., & Mostafa, H. (2022). Decision Feedback Modulation Recognition with Channel Estimation for Amplify and Forward Two-Path Consecutive Relaying Systems. Sensors, 22(16), 6022. https://doi.org/10.3390/s22166022






