1. Introduction
With the thriving of technologies that relate to telecommunications, sensors and networks, the traditional internet with servers, personal computers, and cell phones acting as interconnection entities have been gradually transforming into the Internet of things (IoT), which connects vehicles, electric appliances, even human bodies and aims to realize the interconnection of everything. In order to achieve telemedicine, wireless body area networks (WBANs), for example, which represent the internet of human beings, implant specific sensors on the surface of or even in the body of individuals [
1,
2,
3,
4].
Recently, apart from medical service and health care, WBANs also have the possibility of applications in military and aerospace fields, such as being applied to monitor vital signs of soldiers or astronauts and to implement first aid treatments. During routine training, WBANs could guard trainees by means of collecting training data and adjusting the training intensity. In military actions, WBANs could assist in developing attackers and defenders’ strategies through monitoring body postures of both our armies and the opponents. On battlefields, WBANs could contribute to communications between soldiers as well as to data deliveries to commanders in the base. In addition, WBANs could provide help in monitoring physical status and positions of soldiers by embedding monitor sensors into military uniforms. Generally speaking, WBANs play an essential role in enhancing the accuracy, survivability, and connectivity in virtually every aspect of military operations. In addition, WBANs could be deployed along with astronauts, and by equipping space capsules with WBAN sensors, important data that concern space research as well as physical status information are transmitted from space to control centers through satellite channels. Such space applications broaden the scope where WBANs may exert themselves.
The WBAN sensors embedded in human bodies can gather a wide range of vital signs, such as heart rates, blood pressures, electroencephalograms (EEGs), electrocardiograms (ECGs), and so forth [
5], and some compressive sensing based methods have already been proposed to deal with such signals [
6,
7]. The WBAN sensors send data they collect to monitoring centers, and thus distant diagnosis could be carried out and proper solutions may be proposed based on the data received. Because the transmission distances of WBAN sensors are limited, commonly, WBANs need the aid of additional typical network infrastructures to transmit data. For example, sensor nodes within WBANs that are distributed in various parts of individual bodies first send the data they collect to mobile phones, computers, satellites, or other types of terminals, and then these terminals transmit these data to monitoring centers or remote databases through Internet or satellite channels. WBANs are also sought after as they have expanded the service scope of traditional medical services that need specific time and workplaces and helped to realize a real-time and mobile mode of medical services.
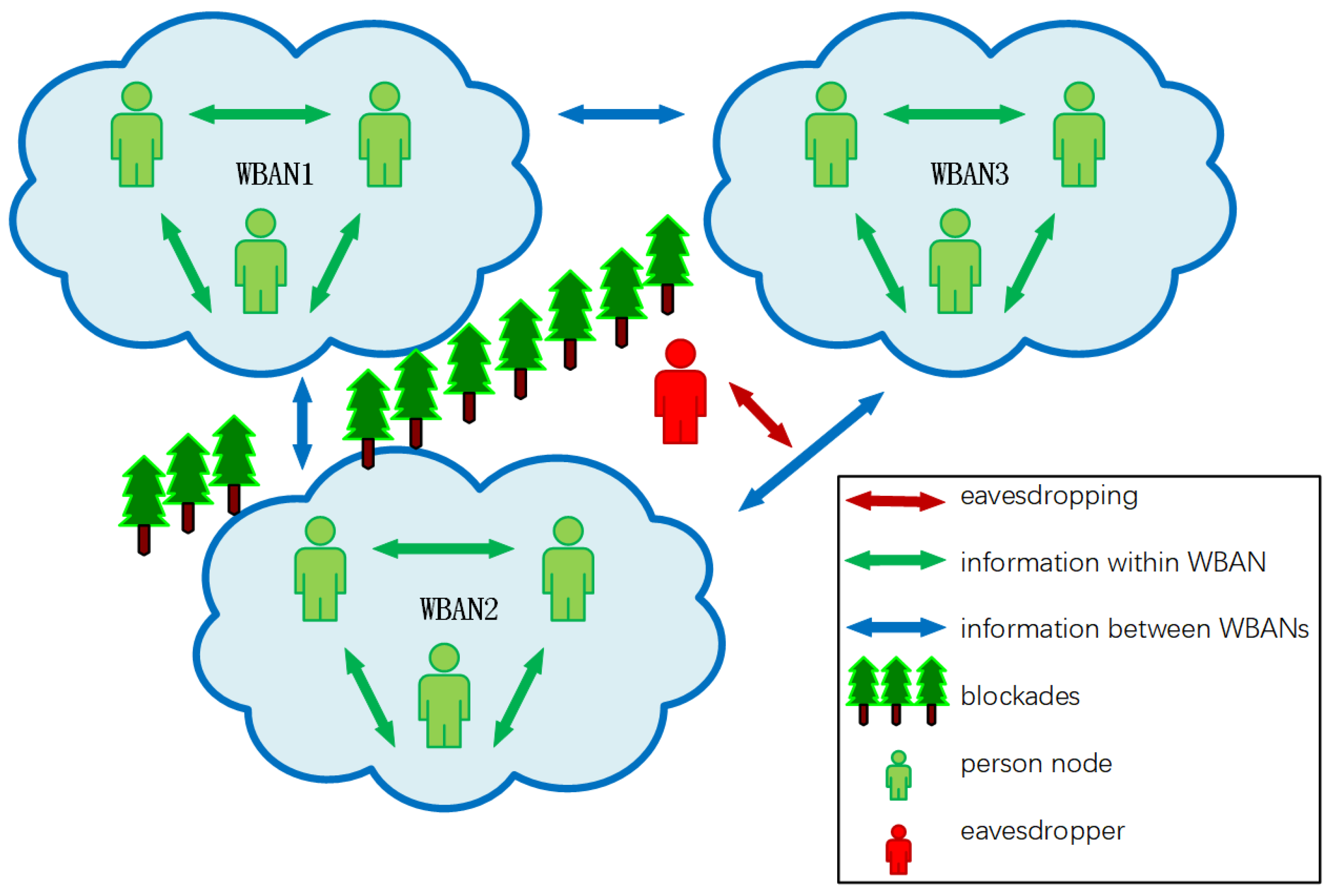
Apart from limited transmission distances, the WBANs that concern military or space technologies and medical applications often have a limited number of participant entities. When accompanied with the extension of application scopes, being applied in occasions such as major sport events, military actions, or disaster rescues, for instance, WBANs are required to be transferred from centralized data communication modes to distributed ones, and therefore body to body networks (BBNs) are gradually formed. BBNs can be regarded as extended WBANs, that is, multiple WBANs are interconnected with each other to generate a BBN. As a result, entities within WBANs could not only interact with other nodes in the same WBAN, but could also communicate across different WBANs, namely, WBANs can communicate with each other.
As shown in
Figure 1, a BBN that consists of three WBANs is used to monitor vital signs of human beings, battlefield environment data, enemy intelligence, and other information, and such information could be exchanged between WBANs or to be sent to remote control centers. At the same time, in the light of the control signals and feedback commands that are transmitted from remote control centers, soldier nodes could be timely administered and arranged, so that efficient military operations are realized. The data gathered by BBNs vary along with the changes in environment and location. The information monitored by BBN sensors, such as human postures and vital signs, is sent by wireless networks and contributes to drawing up operation plans and making decisions, for example, timely evacuation commands could be instructed beforehand as a result of certain discoveries found in data transmitted by BBNs, so as to avoid unnecessary casualties or economic loss.
Moreover, compared with WBANs, BBNs often have larger network scales, longer transmission distances, and wider transmission ranges. Sensor nodes within BBNs not only transmit data caught by themselves, but also forward data collected by other nodes, and such a process causes massive energy consumption. However, BBN sensors are frequently battery-powered, and batteries that are installed on the surface of human bodies or even embedded in the body of individuals are inconvenient to be recharged or replaced. When battery power is exhausted, BBN nodes tend to lose efficiency. Therefore, it is critical to settle energy saving issues when designing data transmission schemes within BBNs, and a practical measure could be to reduce the amount of communication data by compressing the data to be transmitted.
Another difficulty to be overcome is to address eavesdropping problems within BBNs. Because BBNs commonly use wireless transmission technology, network links throughout BBNs may be open and vulnerable to eavesdropping. In particular, such networks are often teeming with private data related to human bodies or confidential information concerning militaries, space technologies, etc. Therefore, in the process of BBN data transmission, an encryption scheme is a must to prevent eavesdroppers from obtaining sensitive information so that the security level of data transmission is enhanced. Furthermore, in order to avoid the potential risk brought by the ownership of a master key that is solely possessed by a single node in the network of the cryptosystem, a certain security protection mechanism is needed. For example, it is necessary to ensure that the secret information carried by original signals will not be disclosed when the person who carries critical data is arrested by enemies. A feasible method is concealing critical information in original signals by means of hierarchical authorization for multilevel receivers. At present, the encryption and compression processes of common schemes are independent. Another issue is, when processing images or videos by sensor nodes within BBNs or WBANs, their storage or computing resources barely meet the requirements of the energy, computing, or other resource consumption level brought by the introduction of classical encryption algorithms. How to accomplish data compression, encryption, and critical information concealment efficiently becomes a burning issue to be addressed.
2. Related Work
This section briefly summarizes the medical and military applications of BBNs, resource consumption and security problems faced by sensor nodes in BBNs, and recent progress in the research of compressive sensing (CS) theory.
In recent years, BBNs have already developed a number of applications for medical services and health care. The CodeBlue project launched by Harvard University attempted to achieve multi-hop transmission through routing nodes in WBANs [
8]. A project called the Advanced Health and Disaster Aid Network [
9], which applied WBANs in disaster rescues, could only allow a rather limited number of sensors taking part in the communication process due to restrictions of the bandwidth. A. Milenkovic et al. proposed a Wearable Health Monitor System [
10], in which a large-scale WBAN for health monitoring was deployed, but the performance of this system was impacted by energy consumption issues.
There are also a number of research achievements in military applications of BBNs. At Walter Reed Army Medical Center (WRAMC), research on supplementary treatments involving cell phones as tools for diabetes treatment was conducted [
11], and this could have a profound impact on the outcome of remedies for the elderly and patients with diabetes or other chronic diseases by introducing WBANs in remote health monitoring. Emeka E. Egbogah et al. proposed a cost-efficient data transmission method to meet the demands of monitoring soldiers’ vital signs [
12]. This method reduced the energy consumption of WBANs worn by soldiers through the means of formulating and solving two optimization problems.
Currently, WBANs and BBNs offer new possibilities for improving the performance of individuals and teams in terms of military operations. For instance, WBANs could play a fundamental role in preventing critical information from being stolen by enemies [
13]. In this paper, in order to avoid threats generated by the single node problem, a group of sensors were deployed to collect important information about the circumstances and nearby new actions, and, at the team level, the information gathered by sensors could enable commanders to coordinate tasks with team members. Singh D. et al. visualized a military health service platform and designed a model based on semantic edge [
14]. Salayma M et al. proposed a new military medical application that could assess the level of soldier fatigue and combat readiness, so as to protect staff in uniform [
15].
Aiming at secure and efficient data transmission within BBNs, some solutions are raised. Several energy harvesting methods are proposed in [
16,
17,
18,
19]. Energy harvesting means that nodes within BBNs collect or generate power from human bodies or other sources to supplement the batteries of sensors. The batteries may be charged by bioenergy or energies generated from body heat, vibration, or friction of movement, etc. However, such energy harvesting functions always add specific circuits to the hardware of BBN sensors, such as energy collectors or power management circuits. In this way, the costs of sensor nodes are increased, which may be detrimental to widespread deployment of BBNs. For energy saving, Zhang C et al. proposed a novel medium access control (MAC) protocol with the function of reducing power consumption [
20]. In [
21,
22,
23], efficient routing protocols suitable for BBNs were designed, and several energy optimization and control algorithms were proposed in [
24,
25].
To account for security, there have been several proposed schemes. S. Al-Janabi et al. presented a solution for encryption and authentication processes in the link layer of BBNs and proposed a security suite based on IEEE 802.15.6 standard [
26]. X. Liu et al. offered an information security management system for WBANs to ensure data confidentiality and integrity [
27]. A key generation method that introduced attributes of wireless channels of BBNs was raised in [
28]. L. Wu et al. purveyed an anonymous authentication method for BBNs, which could resist man-in-the-middle attacks [
29]. Finally, in [
30], H. Zhu et al. applied homomorphic encryption to BBNs to realize data collection and query without the neglect of privacy protection.
The following paragraphs contain a brief introduction of the main research progress in (compressive sensing) CS. CS theory is a signal sampling and compression theory that was first proposed by Tao in 2006 [
31,
32,
33]. Once put forward, this theory has been widely used in telecommunications, networks, signal processing, radars, aviation, biomedical applications, etc. CS does not merely address the problem of data compression. It also achieves data encryption simultaneously. Such characteristics may meet the requirements of data compression and encryption of sensor networks. Noticeably, CS can realize data compression and encryption in solely one step [
34,
35,
36]. Peng et al. improved the generation process of the measurement matrix and enhanced the security level of data transmission by introducing chaotic systems, but concealing critical information was not considered [
37]. Mehmet Yamaç et al. combined CS and data hiding, although their scheme has not achieved the acme of perfection in terms of resisting statistical attacks [
38].
To the best of our knowledge, research on BBNs commonly considers data security, energy efficiency, and critical information concealment issues separately. Although a proportion of existing CS based schemes could accomplish data encryption and compression at the same time, or could realize efficient data transmission to a certain extent, they did not address the problems that concerns critical information concealment.
According to the characteristics of BBNs and the above-mentioned issues to be settled, this paper proposes a secure and efficient data transmission method based on the chaotic CS model and there are three main contributions.
(1) For the purpose of achieving energy efficiency, it should be considered that the capacity of batteries installed on BBN sensors is fairly limited, and recharging or replacing these batteries are often not convenient, especially when the batteries have been implanted into human bodies. And because of the expansion of network scales, the complexity of natural or external environments, or the huge volume of data to be transmitted, power of BBN batteries may consume fast. So, energy saving issues become a must while designing data transmission schemes applied in BBNs. Based on CS theory, this paper gives an efficient data transmission method, which completes data compression, encryption and critical information concealment simultaneously.
(2) For the purpose of realizing transmission security, it should be considered that the majority of data transmitted in BBNs may contain confidential sections, especially when the data concern vital signs of human beings or personal information. Especially, while being applied to medical care or military affairs, BBNs highly probably transmit a substantial amount of data involving critical or private information. On the one hand, under complex circumstances of the real world, open links may be vulnerable to be eavesdropped, which may lead to critical information leaking or other problems. Moreover, even if data are transmitted solely in internal channels, secure data transmission scheme is also imperative, since data may be forwarded several times and these processes may generate many copies of original signals involving critical information. Based on chaos theory, this paper designs a novel secure data transmission method, which could enhance the security level of data transmission by breaking the statistical patterns of original data, providing large key space and sensitivity of the initial values, etc.
(3) For the purpose of enhancing flexibility, the proposed method considers from two aspects. For data senders, the proposed method can flexibly control the proportion and the quantity of sections to be concealed which may contain critical information, according to different scenarios and application requirements. For example, the transmitted information can be concealed completely by senders without affecting the data recovery quality. In addition, senders could select independently only one or more sections to be concealed. For the data receivers, the information they could obtained varied according to their authorization levels. For instance, the receivers with the restricted authorization could only achieve the very part of data without critical information, while the receivers with the full authorization could recovery nearly intact original information.
5. Feasibility Analysis
This section contains two parts. First, we demonstrate the feasibility of the proposed method theoretically. Because the reconstruction process of full-authorized receivers is rather similar to the reconstruction process of traditional compressive sensing, in this section, we only discuss the feasibility of the reconstruction of restricted-authorized receivers. In the second part, we conduct experiments to verify that the proposed method is practically feasible.
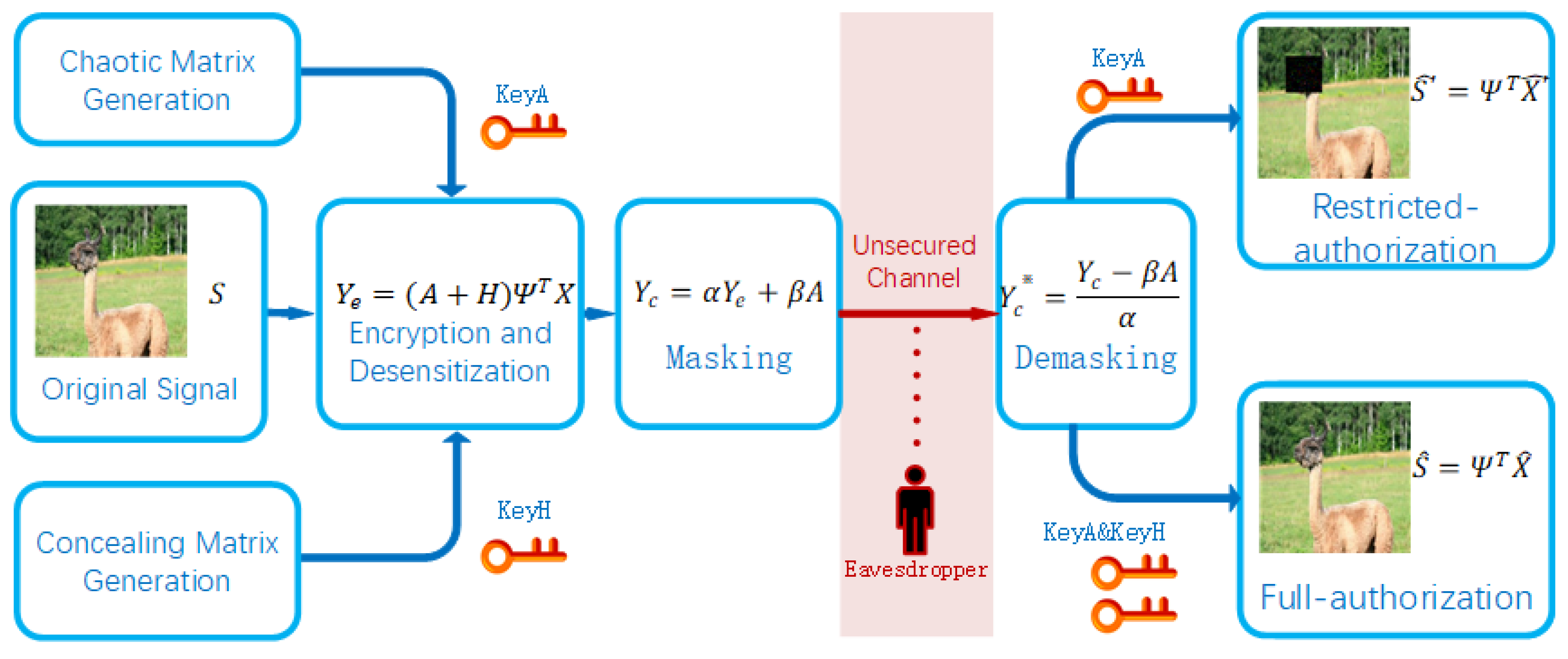
To explicitly explain the processes of critical information concealment and retrieval, we expand Equation (
9) in the following way, and assume that
is the element that involves critical information.
Let
, then Equation (
19) can be rewritten as follows:
To further simplify the discussion, we assume that all
, so we get,
where
,
. When restricted-authorized receivers use the OMP algorithm with the input
and
A, they obtain the signal
as a result.
For the normal case, if at least one
, then Equation (
21) could be rewritten as,
where
, and, as explained in [
45], no reduction in the reconstruction can be achieved when the noise added to the measurement matrix is not arbitrarily large. Clearly, the boundedness characteristic of chaotic systems is an additional prerequisite of the successful reconstruction of signal
.
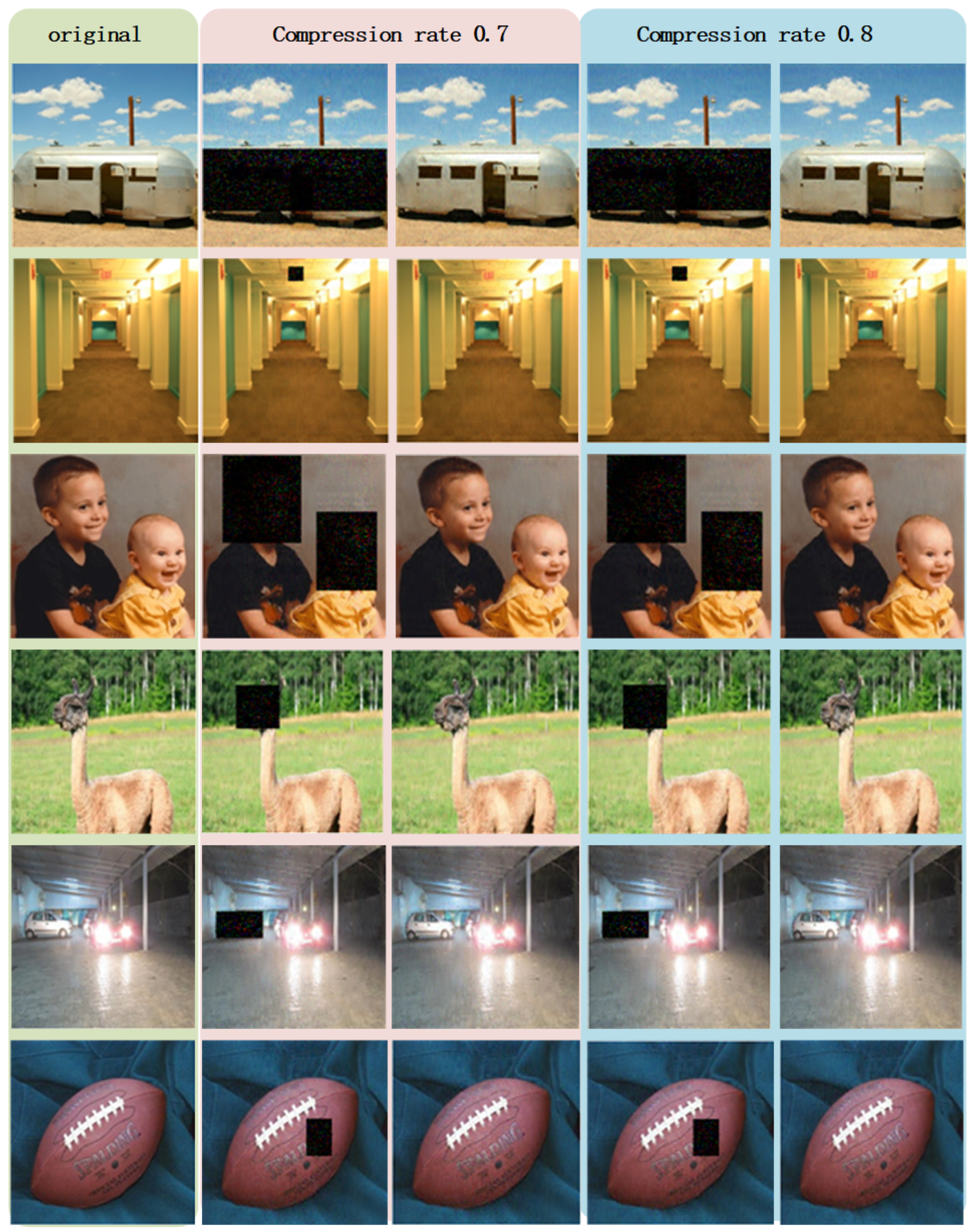
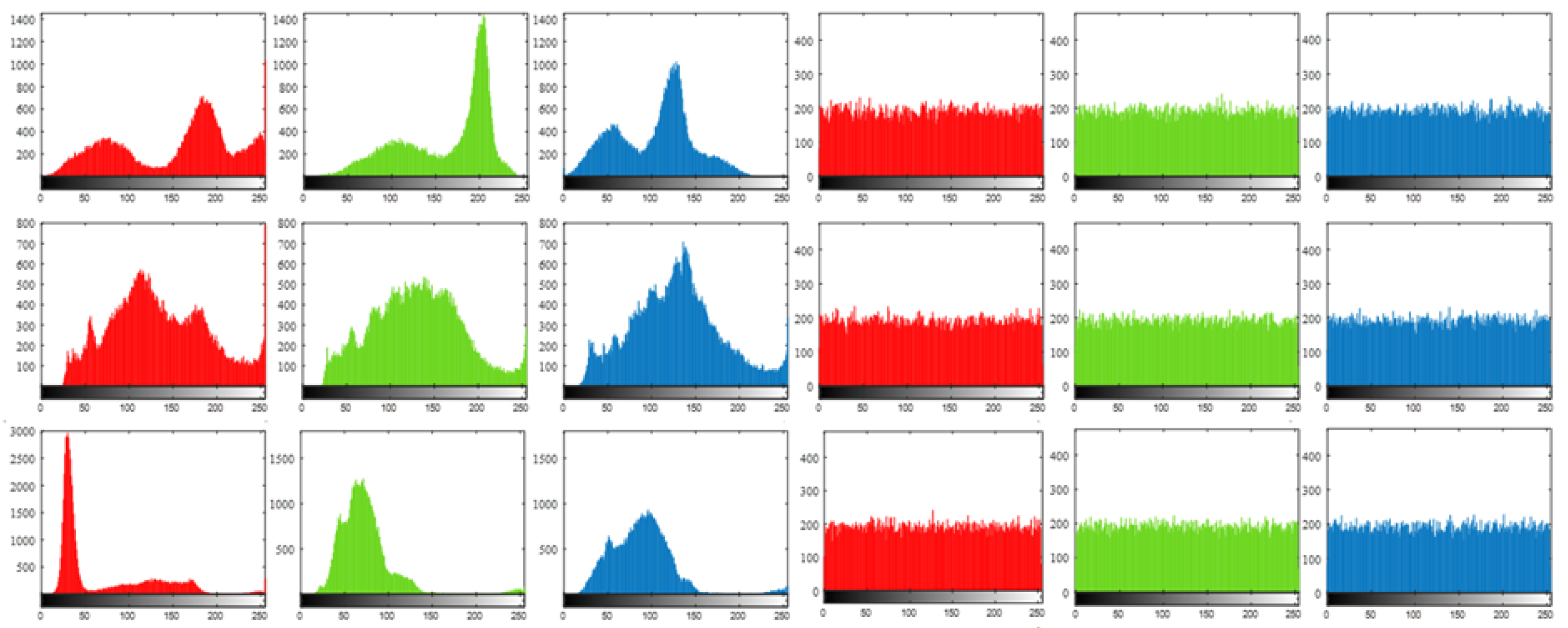
We conduct a substantial number of experiments to verify the feasibility of the proposed method from a practical perspective. The results of several experiments using pictures from MATLAB R2020b image library are reported in
Figure 3, along with the values of peak signal-to-noise ratios (PSNRs, dB) recorded in
Table 1.
By observing the second and fourth columns of
Figure 3, it is crystal clear that the assumed critical information in the original images is concealed, and other information contained in the original signals is reconstructed successfully. Simultaneously, from the third and fifth columns of
Figure 3, we can obtain vivid reconstructions of the entire image without any concealment.
The PSNR values that are calculated based on pixels of the original images and the reconstructed images from red, green, and blue channels are listed in
Table 1. From these figures, we surmise that, although the values of PSNR varies due to the difference between images and compression rates, all the PSNR values exceed 30 dB, which could be regarded as a benchmark for acceptable image reconstruction qualities.
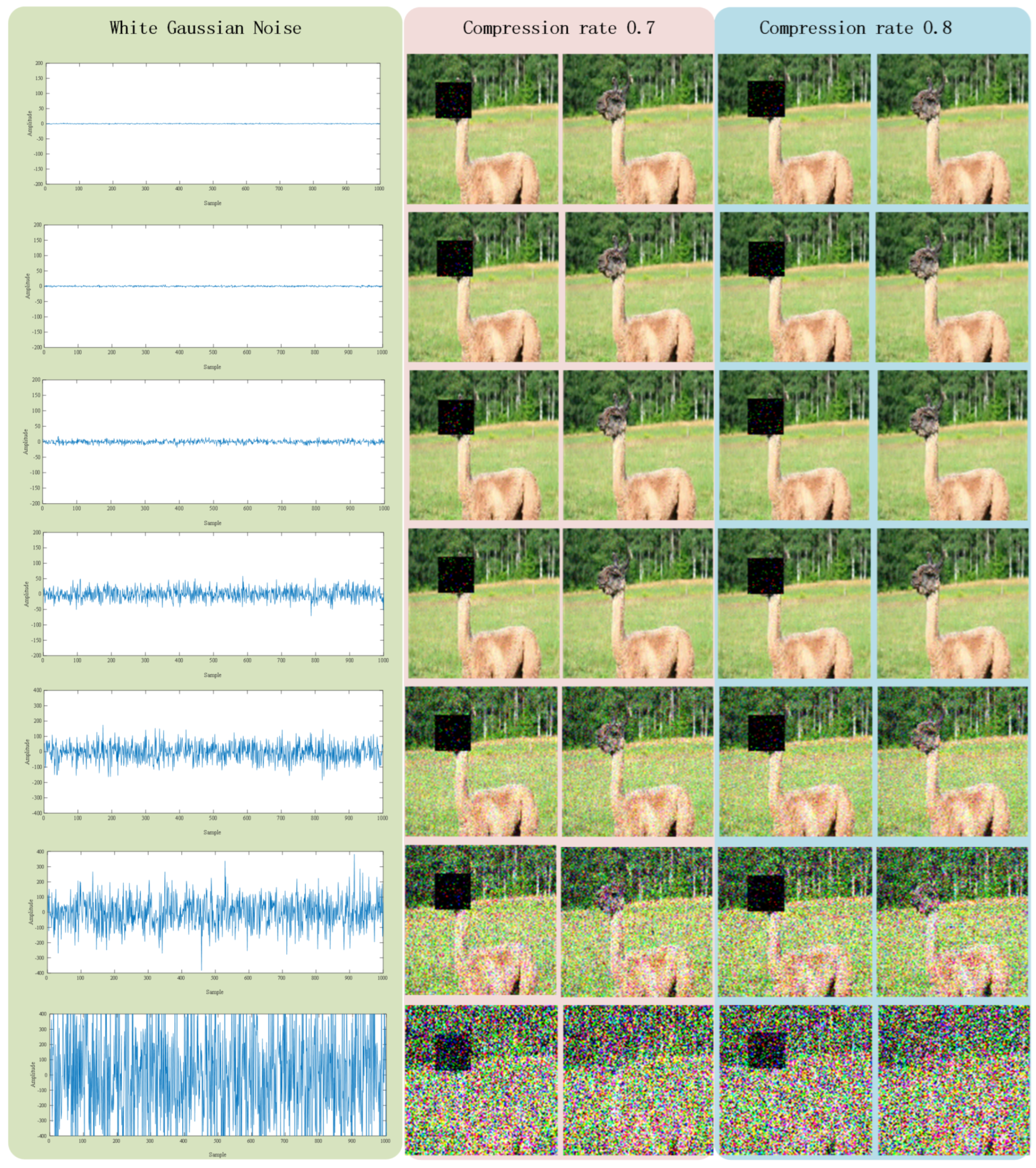
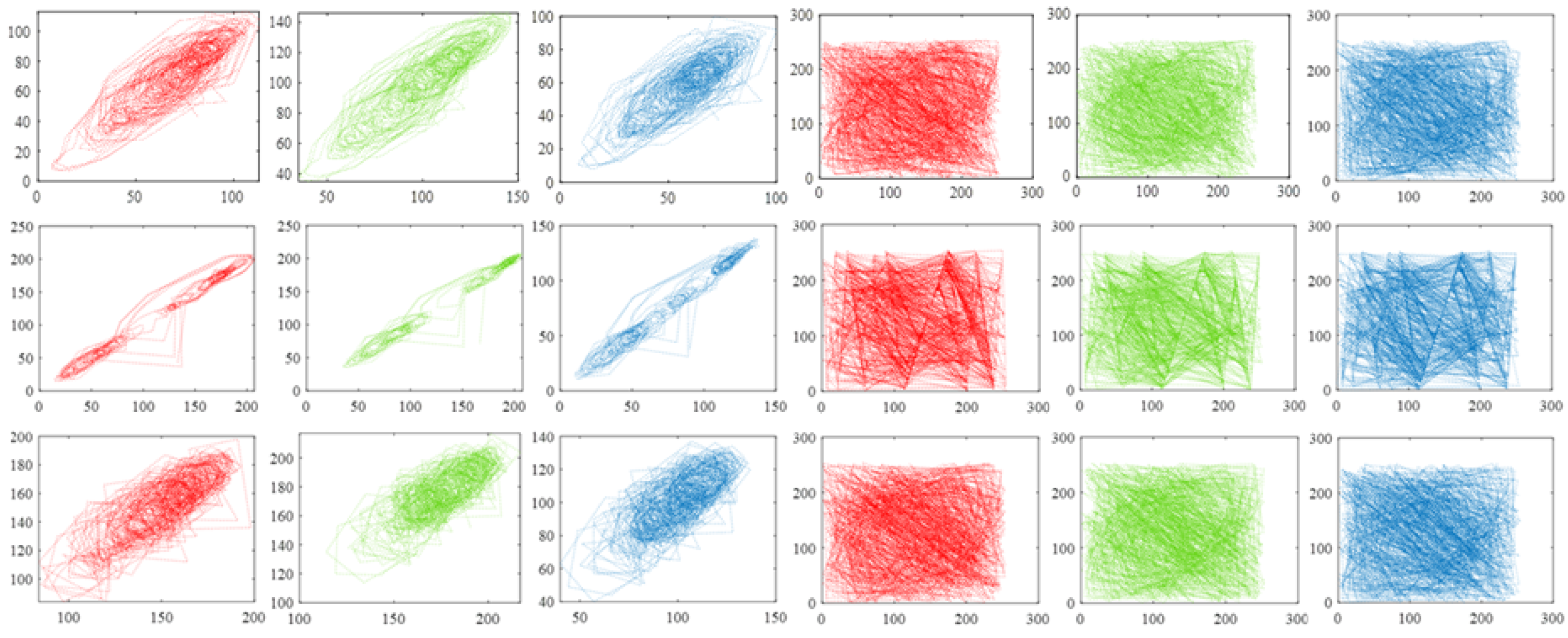
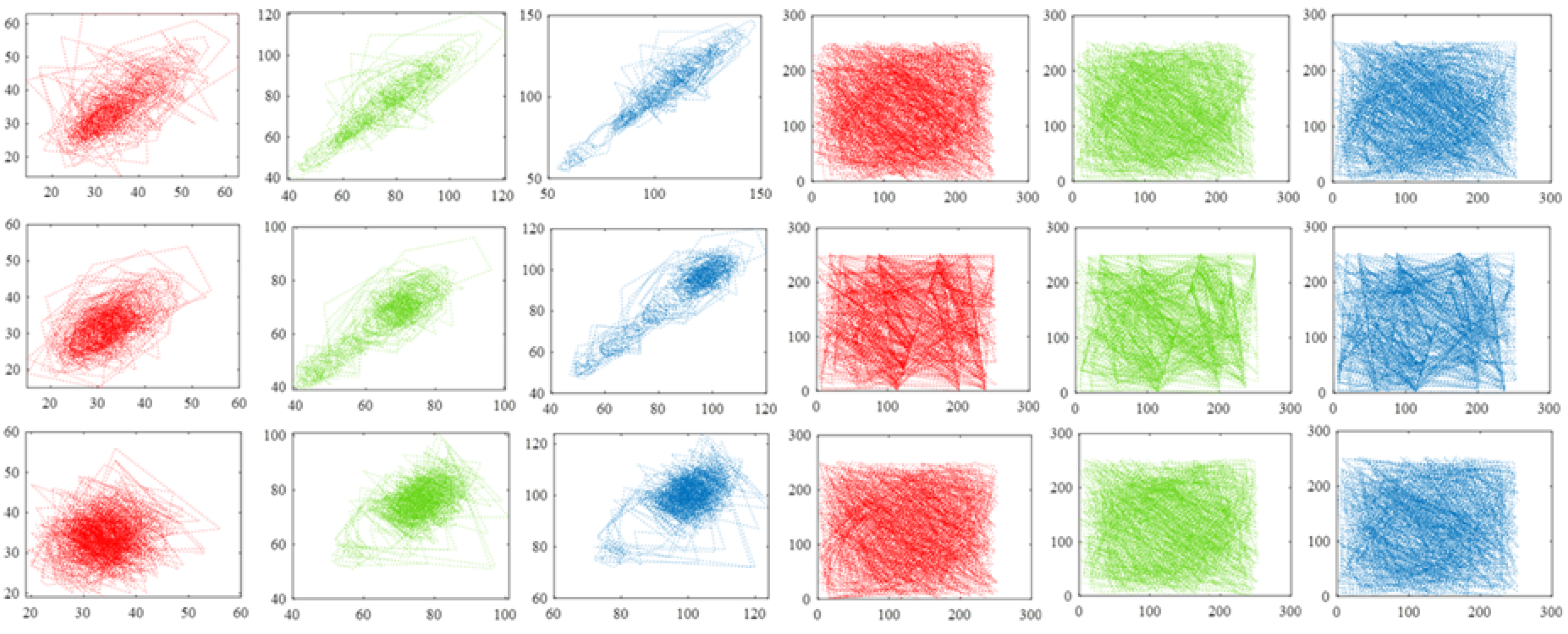
From
Figure 4, we see that flexibility is achieved in terms of concealing portions and the number of concealed sections, and the related PSNR values in
Table 2 all exceed 30 dB, which represents an acceptable quality of image reconstruction.
9. Conclusions
In this paper, we propose a secure and efficient BBN data transmission method that could accomplish critical information concealment and retrieval. Generally, BBN sensors are resource constrained, and CS-based methods are naturally suitable for these sensors, as CS can accomplish data compression while sampling, and this process just needs simple operations of addition and multiplication, which could achieve the aim of reducing energy consumption of sensors during data processing and transmitting. The experimental results show that the proposed methods could compress and encrypt the original data and render different reconstruction results to users in different authorization groups. Namely, users in restricted-authorized groups could only obtain reconstruction results with critical sectors concealed, whereas users in full-authorized groups could reconstruct entire data.
Moreover, in the proposed method, chaotic systems are introduced to generate measurement matrices, so the senders and receivers do not need to transmit the entire measurement matrices to one another, which further saves transmission energy. Specifically, the proposed method could enhance the security level of data transmission by breaking the statistical patterns of original data, providing large key space and sensitivity of the initial values, etc. The key space of the proposed method is discussed, and simulation results show that when even a slight change is applied to the initial value of the chaotic sequences, 10–15 to 10–17, for example, the experimental reconstruction results greatly change.
Last but not least, experimental results also show that the proposed method enables the senders to conceal critical information with flexibility in terms of proportions and quantities of the concealed sectors. In summary, the proposed method realizes the protection of critical information that may be transmitted within BBNs. In the future, the combination of information concealment and semi-tensor compressive sensing could be studied, in order to enhance efficiency and flexibility levels of data transmission catering to the coming requirements of appliances in BBNs and even in IoT.