Video Watermarking Algorithm Based on NSCT, Pseudo 3D-DCT and NMF
Abstract
:1. Introduction
2. Related Theories
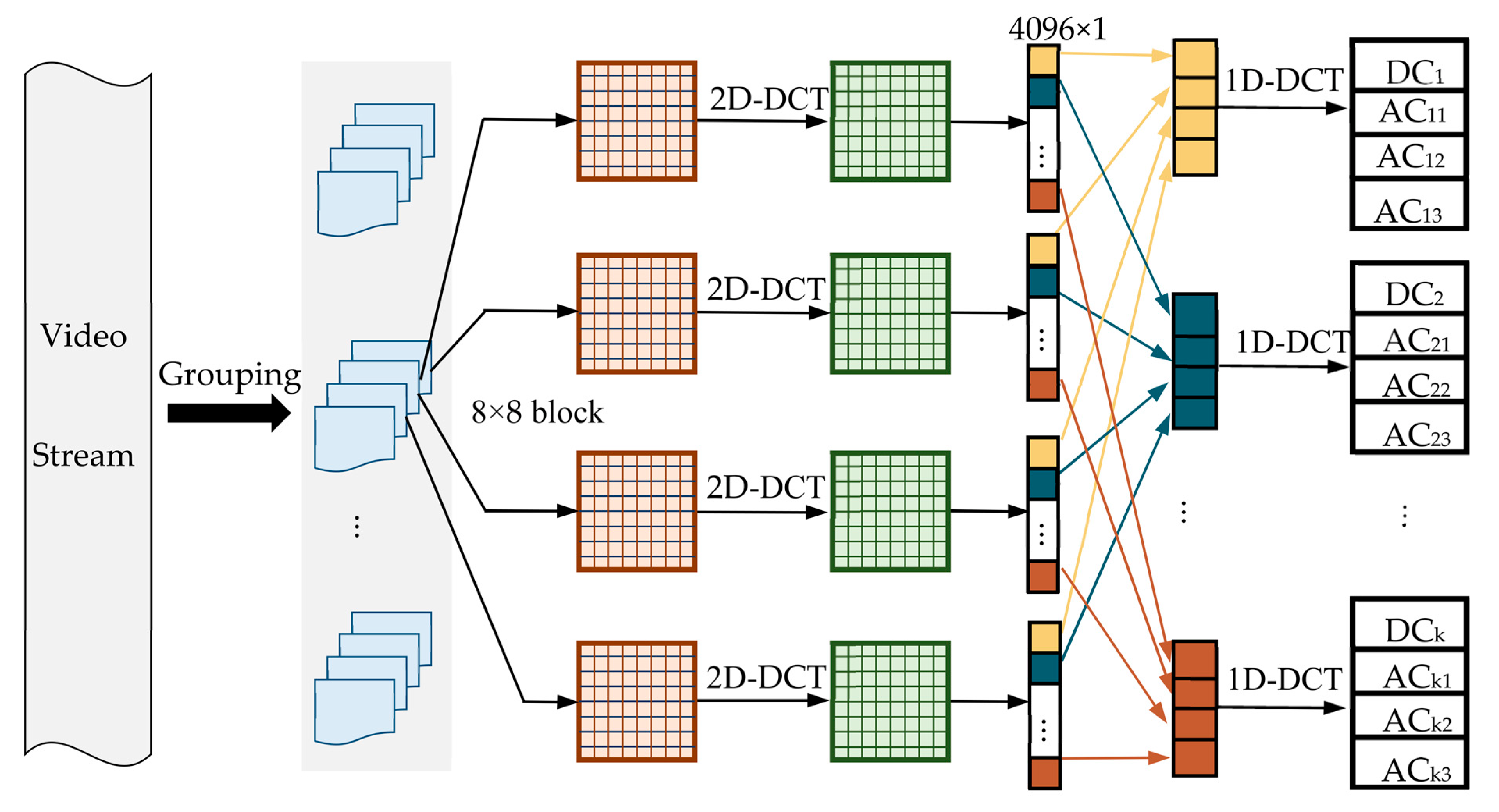
2.1. Pseudo 3D-DCT of Images
- (1)
- Divide every four keyframes into a group, where each frame is a sub-block of , and perform a 2D-DCT on each of these blocks.
- (2)
- The DC coefficients of sub-blocks at the same position in each group are connected along the time axis to form a sequence, upon which 1D-DCT is carried out. The result is the pseudo 3D-DCT coefficient.
2.2. NMF Decomposition of Images
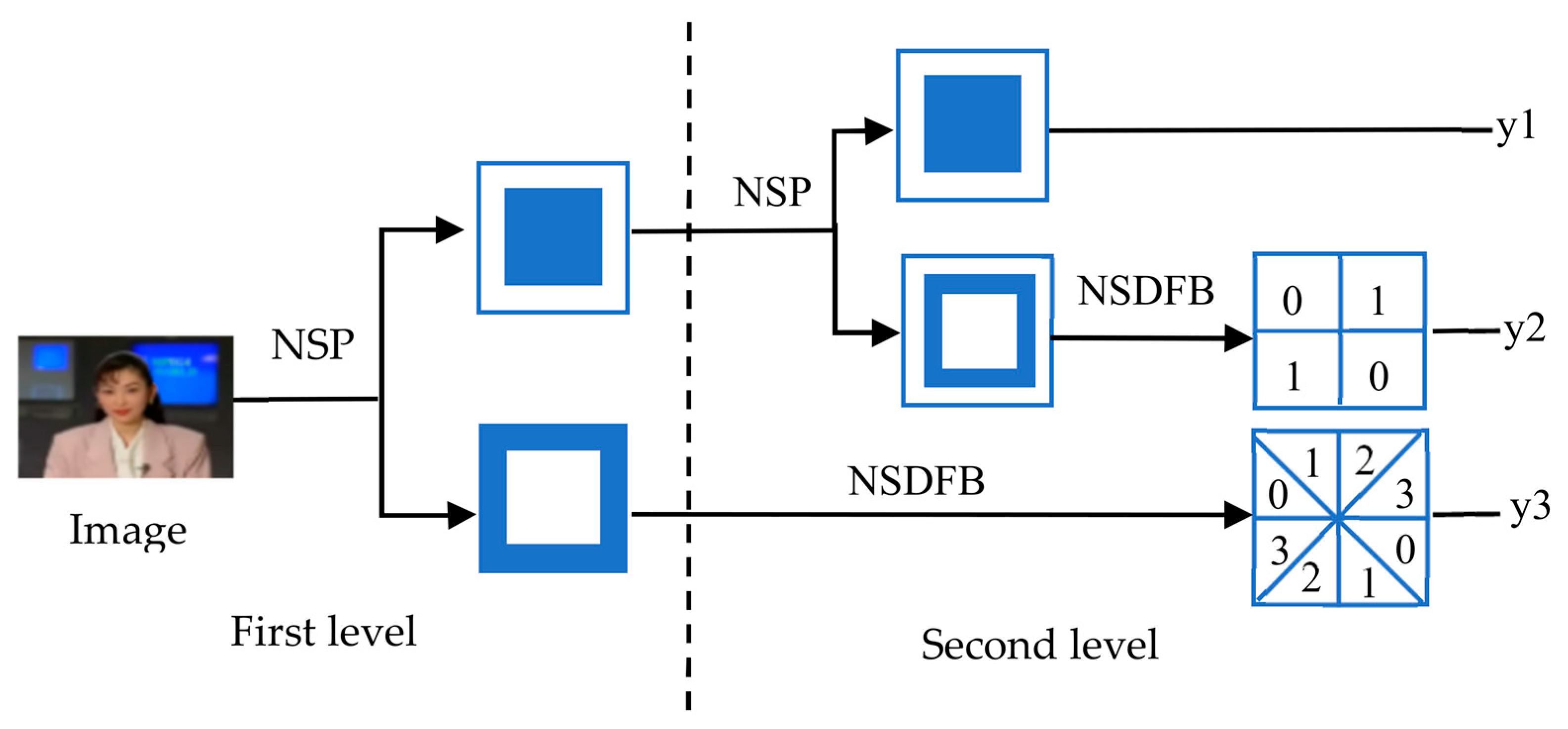
2.3. NSCT of Images
3. Video Watermark Embedding Algorithm and Embedding Intensity Selection
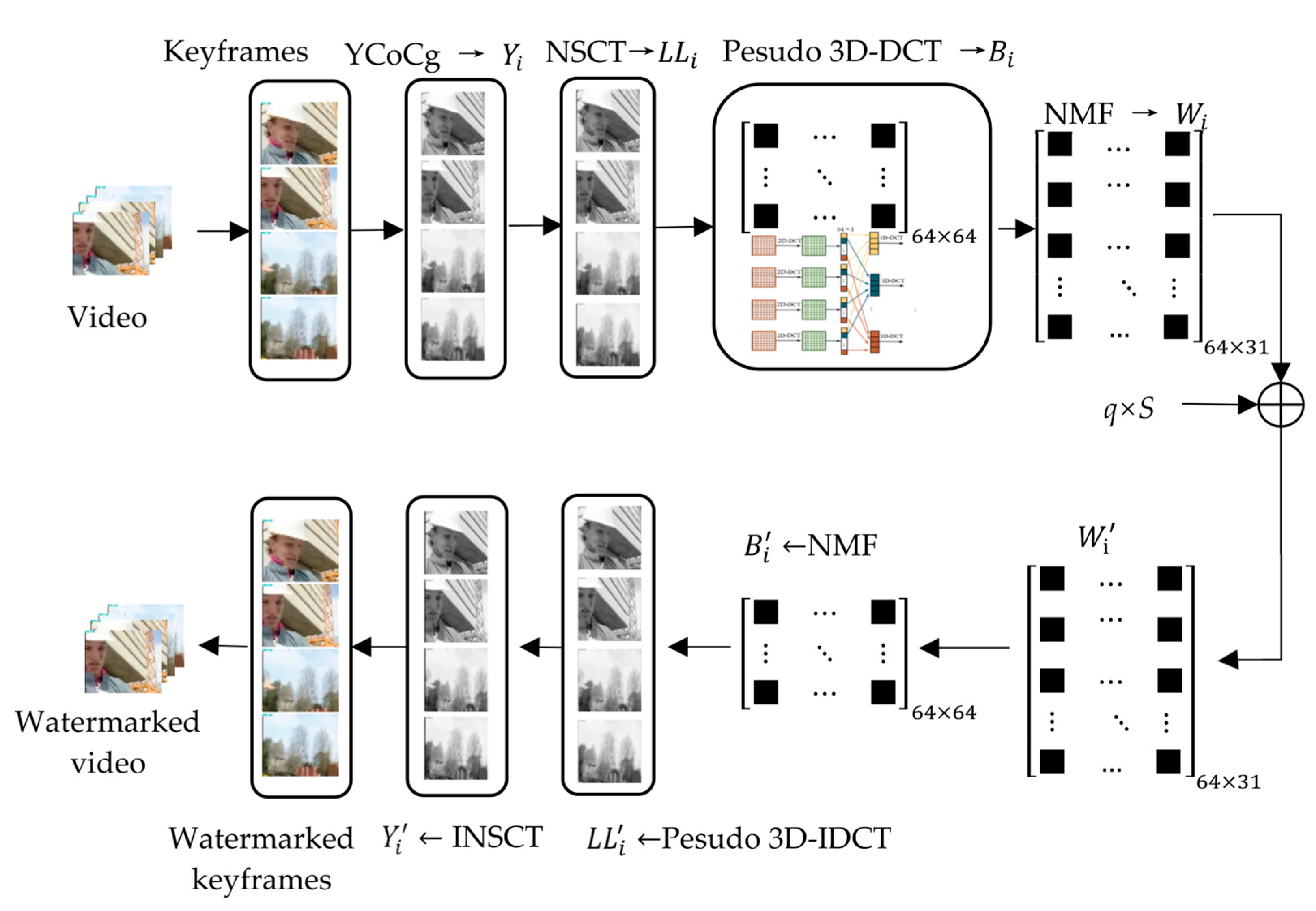
3.1. Video Watermark Embedding Algorithm
- (1)
- Extract the keyframe of the video and save the frame number as the key.
- (2)
- Transform the keyframe image into YCoCg color space, and group its Y components into a group every four frames.
- (3)
- Perform two-level NSCT on four Y-component graphs of the group, denoted as = , and take their low-frequency sub-bands, denoted as = , where , respectively, are the low-frequency sub-bands of the two-level NSCT of the four Y-component graphs.
- (4)
- In the pseudo 3D-DCT of , the DC coefficient matrix with the DC coefficient raised dimension is denoted as .
- (5)
- NMF with was performed on the matrix of group i, and the basis matrix was saved. The decomposition error is:where is the error matrix; and are the basis matrix and coefficient matrix after NMF, respectively.
- (6)
- The encrypted watermark S is additive embedded into to obtain a new basis matrix . The embedding method is:where is the embedding strength of the watermark.
- (7)
- Synthesize , , into a non-negative matrix:
- (8)
- Perform inverse pseudo 3D-DCT on the to obtain the low-frequency sub-band containing the watermark, and then perform inverse NSCT to obtain the brightness component containing the watermark .
- (9)
- is combined with Co and Cg components to obtain a watermarked keyframe image.
- (10)
- Place the keyframe back into the video according to the frame number to obtain the video sequence embedded with a watermark.
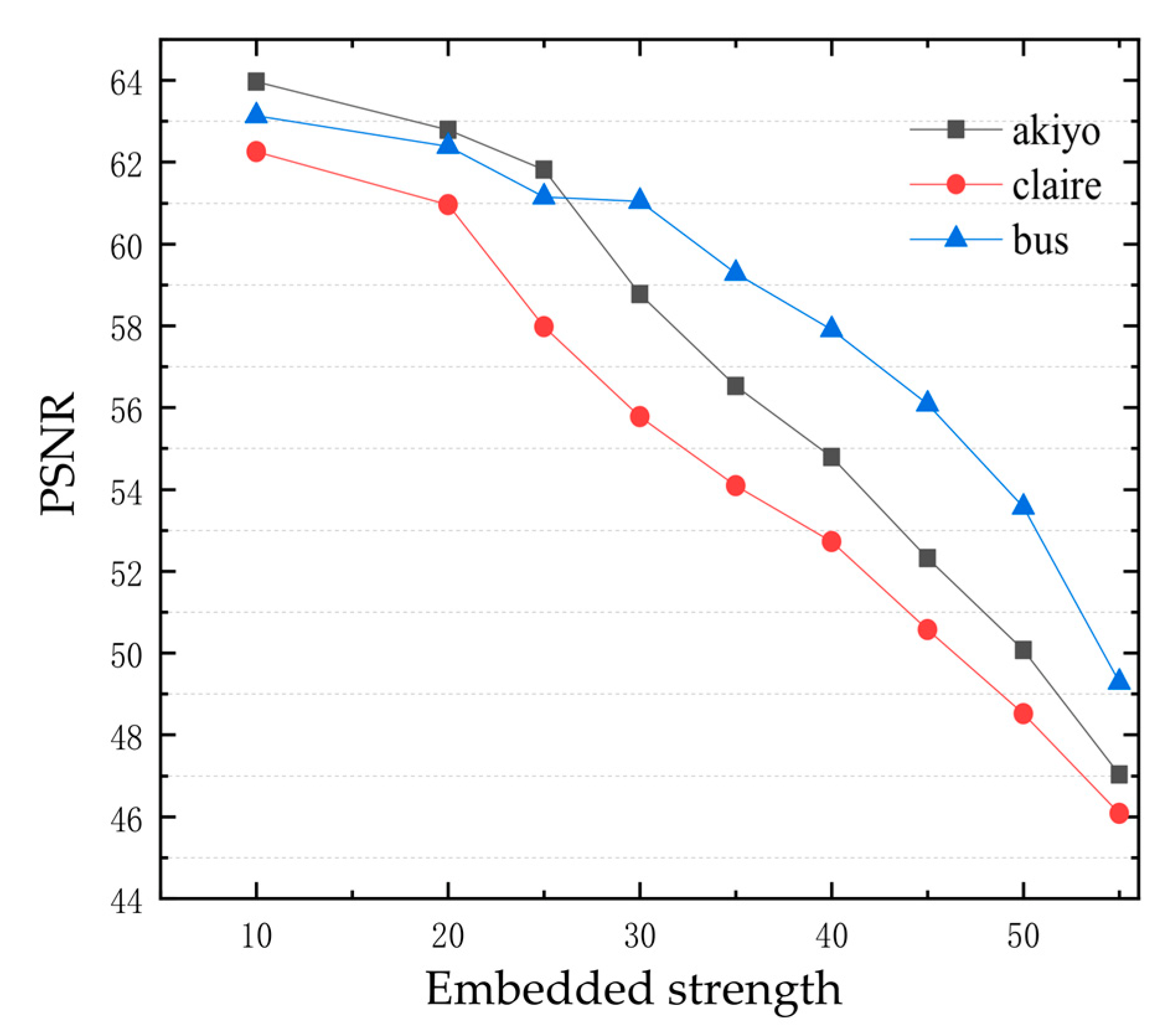
3.2. Watermark Embedding Strength Choice
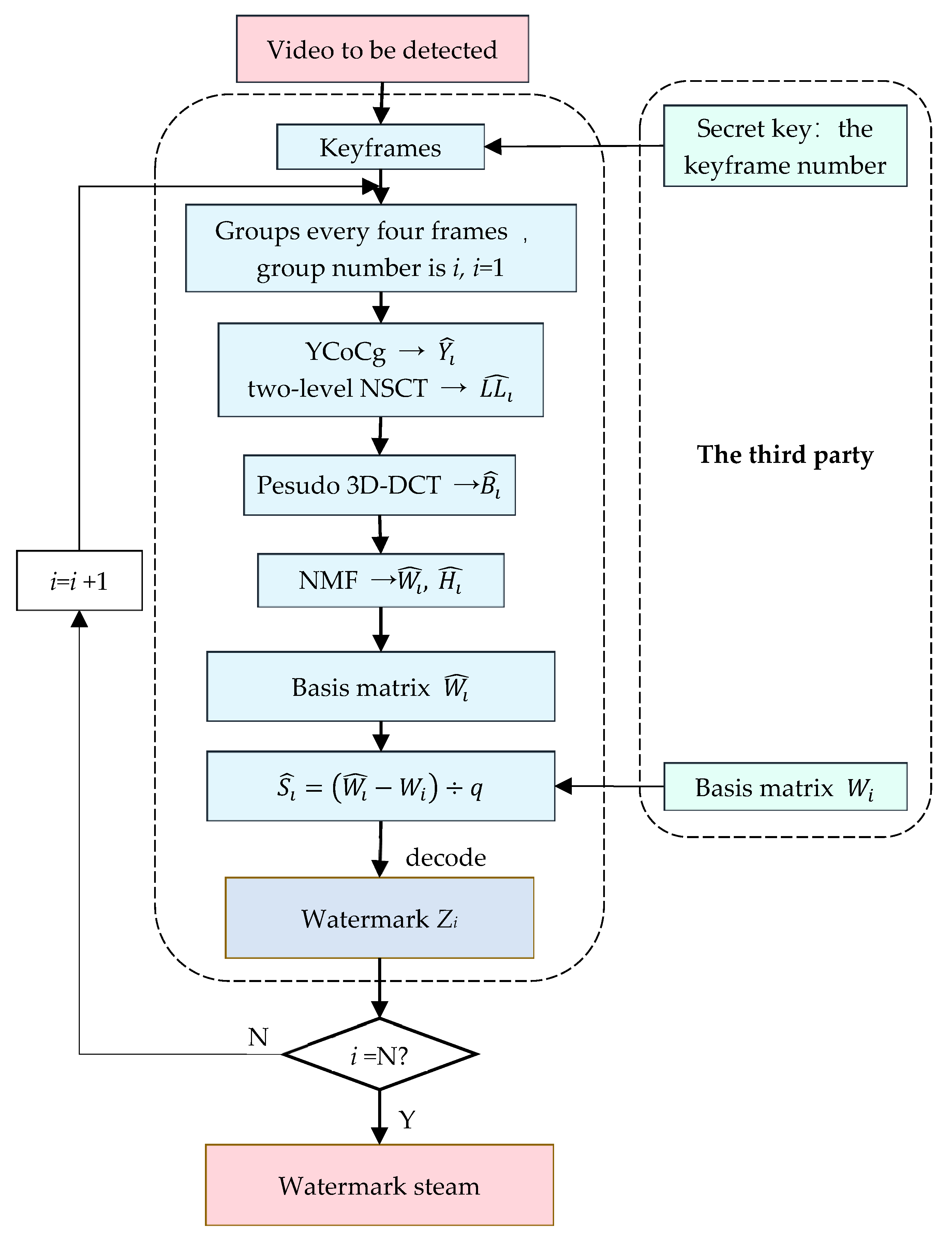
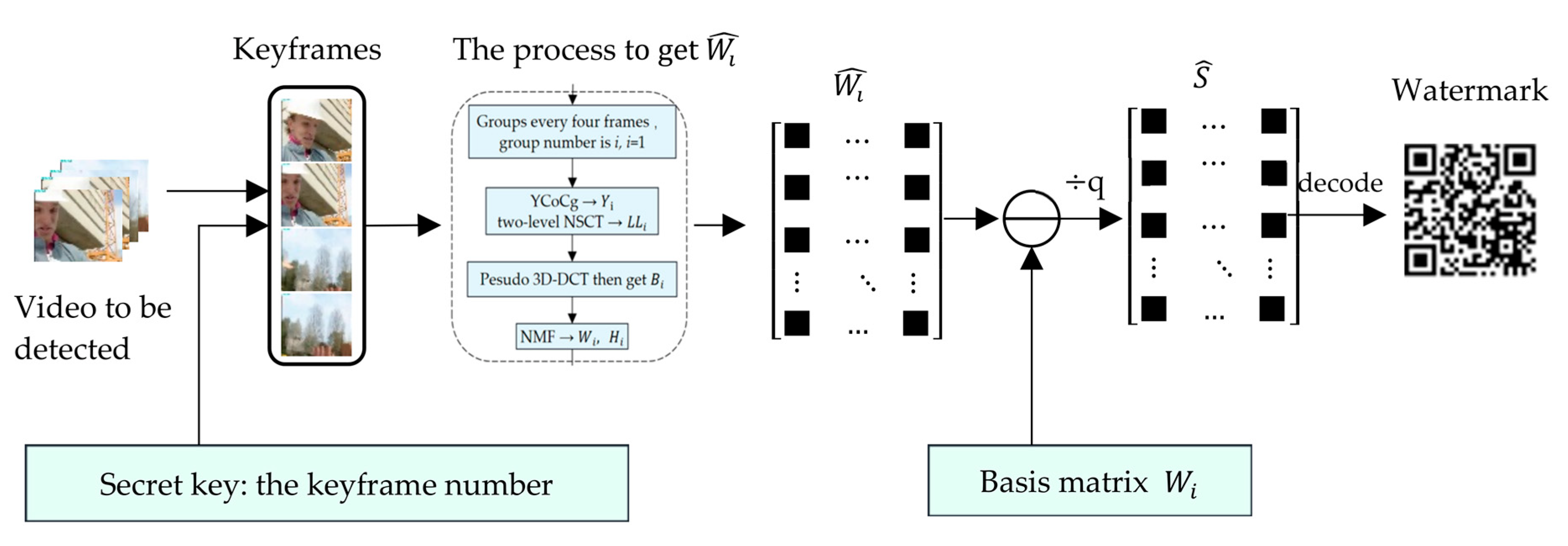
4. Video Watermark Extraction Algorithms
- (1)
- Find the video keyframe according to the frame number saved by the key.
- (2)
- According to the video watermark embedding algorithm, the NMF of the of group i is decomposed into:where and are the basis matrix and coefficient matrix of , respectively.
- (3)
- Using the saved base matrix , extract watermark from as:
- (4)
- Decrypt to obtain copyright watermark information , which can be used for copyright authentication.
5. Experimental Results and Analysis
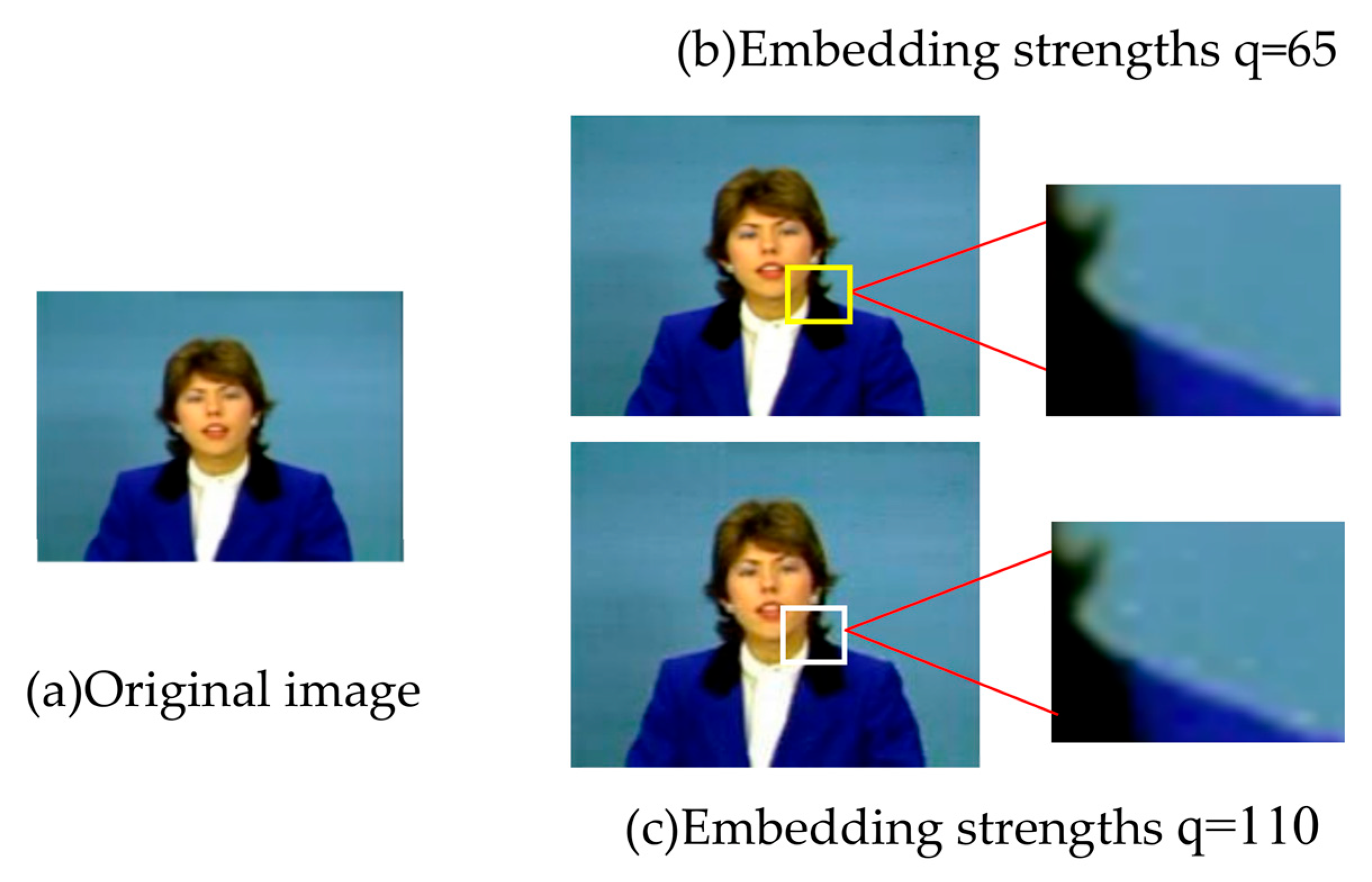
5.1. Invisibility Experiment Results and Analysis
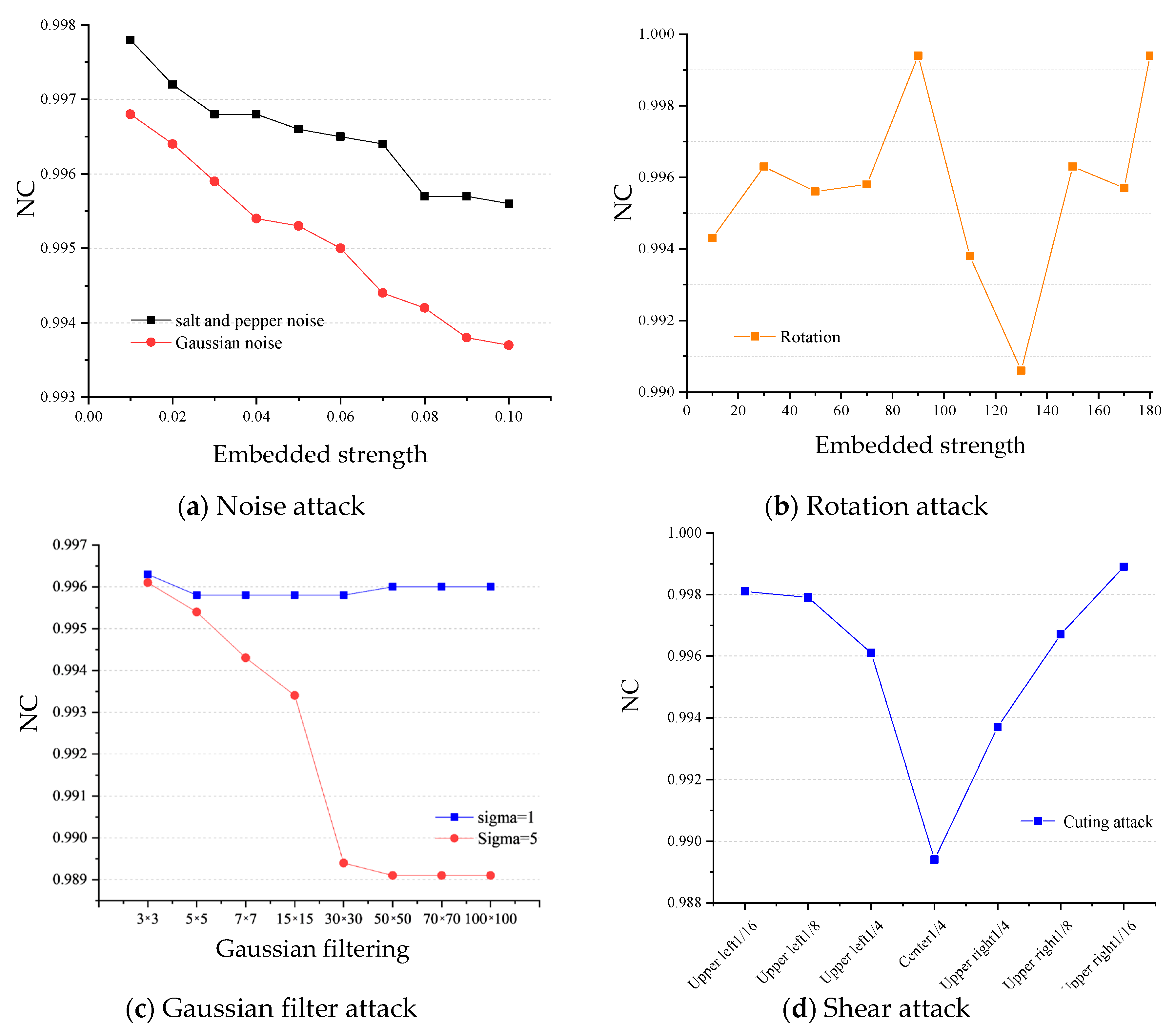
5.2. Robustness of Experimental Results and Analysis
- (1)
- Noise attack. The added attack intensity is Gaussian and salt and pepper noise in the range of 0–0.1. The experimental results are shown in Figure 10a. It can be seen from the results in the figure that, under the noise attack, the NC values of the watermark extracted from the video keyframes are above 0.99, indicating that the algorithm has strong anti-noise ability, especially under the salt and pepper noise attack, for which the NC values are above 0.995. To a certain extent, it can be shown that the resistance of the algorithm to salt and pepper noise is better than to Gaussian noise.
- (2)
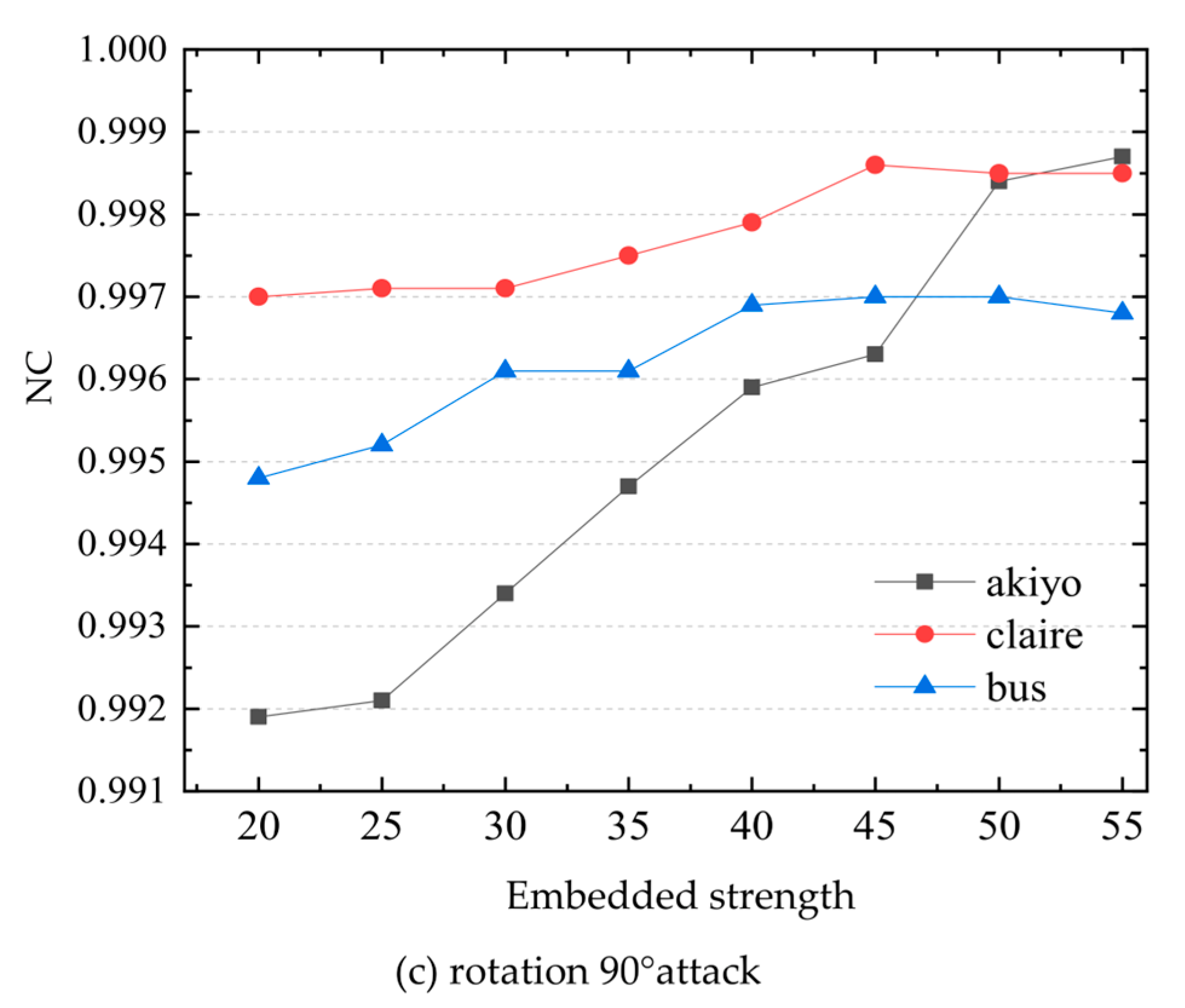
- Rotation attack. The added attack is a rotation of 15° in the range of 10–180°, and the result is shown in Figure 10b. It can be seen from the figure that even under a large rotation attack, the NC value of most of the watermarks can still be maintained at about 0.98, indicating that the algorithm has good robustness to rotation attacks.
- (3)
- Shearing attack. The added attack is to cut 1/16, 1/8 and 1/4 in the upper left and upper right corners, and 1/4 in the center. The experimental results are shown in Figure 10c. The experimental results show that, due to the characteristics of the pseudo 3D-DCT and NMF algorithms, the algorithm also shows good robustness to shearing attacks.
- (4)
- Filter attack. The added attack is Gaussian filtering with different window sizes and scales of Sigma = 1 and Sigma = 5. The experimental results are shown in Figure 10d. It can be seen from the figure that the mean values of the NC extracted from the watermark are above 0.98, and the algorithm has strong robustness to filtering attacks under various window sizes.
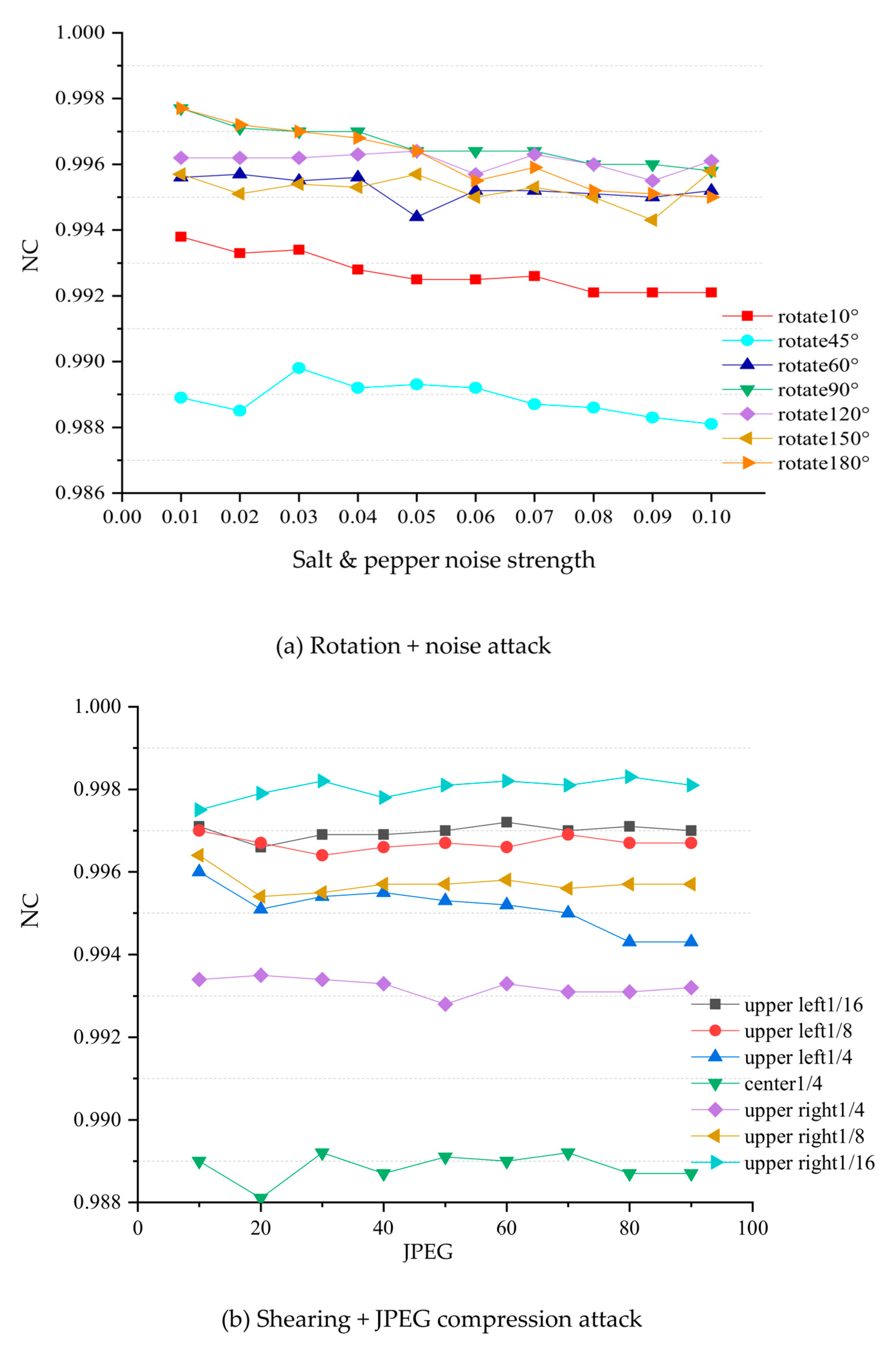
- (5)
- Combination attack. In this paper, three combined attacks of rotation plus salt and pepper noise, JPEG compression plus cropping, and Gaussian filtering and Gaussian noise under different windows were selected for experiments, and the results are shown in Figure 11. From the experimental results, for the first combined attack, most of the watermark NC values extracted by the algorithm in this paper are above 0.90, which has a good anti-attack ability for the combined attack, and the algorithm is more sensitive to rotation attacks than salt and pepper noise. For the second combined attack, the algorithm in this paper has strong robustness under small-scale cropping and JPEG compression attacks, the extracted watermark NC values can reach more than 0.98, and the sensitivity to cropping attacks is higher than that of JPEG compression. For the third combined attack, the NC values of the watermark extracted by the algorithm in this paper under different window Gaussian filtering and Gaussian noise attacks are all above 0.90, which indicates good resistance, and that it is sensitive to both Gaussian filtering and Gaussian noise attack.
5.3. Comparative Experimental Analysis
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Agarwal, H.; Husain, F. Development of payload capacity enhanced robust video watermarking scheme based on symmetry of circle using lifting wavelet transform and SURF. J. Inf. Secur. Appl. 2021, 59, 102846. [Google Scholar] [CrossRef]
- Sun, J.; Jiang, X.; Liu, J.; Zhang, F.; Li, C. An Anti-Recompression Video Watermarking Algorithm in Bitstream Domain. Tsinghua Sci. Technol. 2021, 26, 154–162. [Google Scholar] [CrossRef]
- Xuecheng, S.; Zheming, L.; Zhe, W.; Yongliang, L. A geometrically robust multi-bit video watermarking algorithm based on 2-D DFT. Multimed. Tools Appl. 2021, 80, 13491–13511. [Google Scholar]
- Sahu, A.K. A logistic map based blind and fragile watermarking for tamper detection and localization in images. J. Ambient. Intell. Humaniz. Comput. 2021, 237902713. [Google Scholar] [CrossRef]
- Munir, R. A Secure Fragile Video Watermarking Algorithm for Content Authentication Based on Arnold Cat Map. In Proceedings of the 4th International Conference on Information Technology (InCIT), IEEE, Bangkok, Thailand, 24–25 October 2019; pp. 32–37. [Google Scholar]
- Arab, F.; Zamani, M.; Poger, S.; Manigault, C.; Yu, S. A Framework to Evaluate the Performance of Video Watermarking Techniques. In Proceedings of the 2nd International Conference on Information and Computer Technologies (ICICT), Kahului, HI, USA, 14–17 March 2019; pp. 114–117. [Google Scholar]
- Ahuja, R.; Singh Bedi, S. Video watermarking scheme based on IDR frames using MPEG-2 structure. Int. J. Inf. Comput. Secur. 2019, 11, 585–603. [Google Scholar] [CrossRef]
- Ahuja, R.; Sharma, M.; Haque, M.J. A Compressed domain Based Robust and Imperceptible Digital Video Watermarking Scheme. In Proceedings of the Sixth International Conference on Parallel, Distributed and Grid Computing (PDGC), Waknaghat, India, 6–8 November 2020; pp. 313–317. [Google Scholar]
- Sun, Y.; Wang, J.; Huang, H.; Chen, Q. Research on scalable video watermarking algorithm based on H.264 compressed domain. Opt. Int. J. Light Electron Opt. 2020, 227, 165911. [Google Scholar] [CrossRef]
- Li, C.; Yang, Y.; Liu, K.; Tian, L. A Semi-Fragile Video Watermarking Algorithm Based on H.264/AVC. Wirel. Commun. Mob. Comput. 2020, 2020, 8848553. [Google Scholar] [CrossRef]
- Dhevanandhini, G.; Yamuna, G. An effective and secure video watermarking using hybrid technique. Multimed. Syst. 2021, 27, 953–967. [Google Scholar] [CrossRef]
- Gaj, S.; Sur, A.; Bora, P.K. Prediction mode based H. 265/HEVC video watermarking resisting re-compression attack. Multimed. Tools Appl. 2020, 79, 18089–18119. [Google Scholar] [CrossRef]
- Darabkh, K.A.; Al-Sheikh, R.M.; Haddad, R.F.; Khalifeh, A.F. Scene Change Based Video Watermarking Algorithm. In Proceedings of the International Conference on Innovation and Intelligence for Informatics, Computing and Technologies (3ICT), Sakheer, Bahrain, 20–21 December 2020; pp. 1–6. [Google Scholar]
- Sun, W.; Zhao, H.; Zhang, X.; Sun, Y.; Liu, X.; Lv, X.; Fan, D. Zero-watermarking Algorithm for Audio and Video Matching Verification. Optim. Algorithms Dyn. Syst. 2022, 7, 8390–8407, (Accepted, SCI Source Journal). [Google Scholar] [CrossRef]
- Fan, D.; Li, Y.; Gao, S.; Wang, G.; Chi, C.; LV, C. A Novel Zero Watermark Optimization Algorithm Based on Gabor Transform and Discrete Cosine Transform. Concurr. Comput. Pract. Exp. 2020, 34, e5689. [Google Scholar] [CrossRef]
- Sharma, C.; Amandeep, B.; Sobti, R.; Kumar Lohani, T.; Shabaz, M. A secured frame selection based video watermarking technique to address quality loss of data: Combining graph based transform, singular valued decomposition, and hyperchaotic encryption. Secur. Commun. Netw. 2021, 2021, 5536170. [Google Scholar] [CrossRef]
- Fu, Y. Robust image watermarking scheme based on 3D-DCT. 2009 Sixth International Conference on Fuzzy Systems and Knowledge Discovery, IEEE, Tianjin, China, 14–16 August 2009; pp. 437–441. [Google Scholar]
- Yiming, L.; Chongxiong, Z. Video zero-watermarking algorithm in pseudo 3D-DCT domain. Electron. Meas. Technol. 2019, 42, 157–161+166. [Google Scholar]
- Huang, H.Y.; Yang, C.H.; Hsu, W.H. A video watermarking algorithm based on pseudo 3D DCT. IEEE Symposium on Computational Intelligence for Image Processing, Nashville, TN, USA, 30 March–2 April 2009; pp. 76–81. [Google Scholar]
- Li, D.; Cui, L.H. Robust Animation Zero Watermarking Based on Visual Cryptography and Complete Complementary Code. Lect. Notes Electr. Eng. 2017, 474, 60–65. [Google Scholar]
- Liu, X. Research on Digital Watermarking Algorithm for Audio and Video Matching. Master’s Thesis, Shandong University of Science and Technology, Qingdao, China, 2020. [Google Scholar]
- Li, D.; Yang, S.; Zuo, Y.; Zheng, Z.; Cui, L. Animation Zero Watermarking Algorithm Based on Edge Feature. In Lecture Notes in Electrical Engineering; Springer: Cham, Switzerland, 2018; Volume 518, pp. 565–571. [Google Scholar]
- Cox, I.J.; Kilina, J.; Leighton, T.; Shamoon, T. Secure spread spectrum watermarking for multimedia. IEEE Trans. Image Processing 1997, 6, 1673. [Google Scholar] [CrossRef]
- Huang, J.W.; Shi, Y.Q.; Shi, Q. Embedding Image Watermarks in DC Components. IEEE Trans. Circuits Syst. Video Technol. 2000, 10, 974–979. [Google Scholar] [CrossRef] [Green Version]
- Lee, D.D.; Seung, H.S. Learning the parts of objects with nonnegative matrix factorization. Nature 1999, 401, 788–791. [Google Scholar] [CrossRef]
- Medimegh, N.; Belaid, S.; Atri, M.; Werghi, N. Statistical 3D watermarking algorithm using non-negative matrix factorization. Multimed. Tools App. 2020, 79, 35–36. [Google Scholar] [CrossRef]
- Chen, Z.; Li, L.; Peng, H.; Liu, Y.; Yang, Y. A novel digital watermarking based on General non-negative matrix factorization. IEEE Trans. Multimed. 2018, 20, 1973–1986. [Google Scholar] [CrossRef]
- Da Cunha, A.L.; Zhou, J.; Do Minh, N. The Nonsubsampled Contourlet Transform: Theory, Design, and Applications. IEEE Trans. Image Processing 2006, 15, 3089–3101. [Google Scholar] [CrossRef] [Green Version]
- Amiri, A.; Mirzakuchaki, S. A digital watermarking method based on NSCT transform and hybrid evolutionary algorithms with neural networks. SN Appl. Sci. 2020, 2, 1669. [Google Scholar] [CrossRef]
- Narasimhulu, C.V. A robust hybrid video watermarking algorithm using NSCT and SVD. In Proceedings of the IEEE International Conference on Power, Control, Signals and Instrumentation Engineering (ICPCSI), Chennai, India, 21–22 September 2017; pp. 1495–1501. [Google Scholar]
- Madenda, S.; Darmayantie, A. Adaptive color space model based on dominant colors for image and video compression performance improvemen. Comput. Opt. 2021, 45, 405–417. [Google Scholar] [CrossRef]
- Jiang, Y.; Cai, M.; Song, C.H. Contourlet domain anti-attack video watermarking algorithm based on SIFT. Comput. Simul. 2018, 35, 314–320. [Google Scholar]
- Sang, J.; Liu, Q.; Song, C.L. Robust video watermarking using a hybrid DCT-DWT approach. J. Electron. Sci. Technol. 2020, 18, 100052. [Google Scholar] [CrossRef]



| Video Name | Video Length (s) | Number of Keyframes Embedded with Watermarks | CPU Time (s) |
|---|---|---|---|
| Akiyo | 10 | 12 | <75 |
| Bus | 5 | 16 | <96 |
| Claire | 10 | 28 | <103 |
| Foreman | 10 | 4 | <25 |
| Video Name | Foreman | Claire | Akiyo | Bus |
|---|---|---|---|---|
| Some video frames with watermark |  |  |  |  |
| PSNR | 47.1679 | 48.1352 | 48.0193 | 49.0118 |
| NC | 1.0000 | 1.0000 | 1.0000 | 1.0000 |
| Attack Type | Attack Parameter | PSNR | NC | Attack Type | Attack Parameter | PSNR | NC |
|---|---|---|---|---|---|---|---|
| Gaussian noise | 0.01 | 20.4067 | 0.9968 | rotation | 10° | 13.5621 | 0.9943 |
| 0.05 | 14.2519 | 0.9950 | 20° | 11.1896 | 0.9939 | ||
| Salt and pepper noise | 0.01 | 24.7449 | 0.9978 | 45° | 8.9730 | 0.9871 | |
| 0.05 | 17.7592 | 0.9966 | JPEG compression | 70 | 40.4686 | 0.9989 | |
| Shearing | Upper left shear 1/3 | 7.1723 | 0.9921 | 30 | 36.8852 | 0.9984 | |
| Down shear 1/3 | 10.0480 | 0.9732 | 5 | 26.7172 | 0.9942 | ||
| Scaling | 1/2 | 40.3844 | 0.9987 | Combined attack | JPEG10 + scaling 1/2 | 31.9584 | 0.9973 |
| 2 | 47.9981 | 0.9996 | Upper left shear 1/16 + Gaussian noise 0.02 | 11.3136 | 0.9945 | ||
| Gaussian filtering | 3 × 3 | 38.5250 | 0.9965 | JPEG10 + salt and pepper noise 0.1 | 17.3147 | 0.9936 | |
| 7 × 7 | 36.5973 | 0.9958 | Median filtering + center shear 1/4 | 9.4794 | 0.9881 | ||
| Recompression | Mpeg4 | 40.978 | 0.9995 | Gaussian filtering 3 × 3 + Mpeg4 compression | 13.6111 | 0.9902 | |
| H.264 | 39.5714 | 0.999 | Scaling 2 + H.264 compression | 20.4327 | 0.9923 |
| Experiment Video | Attack Type | Algorithm [32] Algorithm | Algorithm [33] Algorithm | Proposed Algorithm |
|---|---|---|---|---|
| Foreman | Rotation (10°) | 0.8226 | 0.8209 | 0.9910 |
| Rotation (30°) | 0.8591 | 0.8096 | 0.9941 | |
| Rotation (45°) | 0.8330 | 0.7992 | 0.9884 | |
| Scaling (1/2) | 0.9757 | 0.9290 | 0.9992 | |
| Scaling (2) | 0.6348 | 0.9041 | 0.9995 | |
| Rotation (10°) + Scaling (2) | 0.8591 | 0.8042 | 0.9803 | |
| Rotation (30°) + Scaling (1/2) | 0.8435 | 0.7924 | 0.9909 | |
| Shearing (1/8) | 0.9078 | 0.5292 | 0.9953 | |
| Scaling (1/4) | 0.8070 | 0.3936 | 0.9913 | |
| Scaling (1/2) | 0.6000 | 0.3235 | 0.9309 | |
| Median filtering | 0.9965 | 0.9295 | 0.9972 | |
| Bus | Rotation (10°) | 0.8887 | 0.8562 | 0.9912 |
| Rotation (30°) | 0.7861 | 0.8208 | 0.9911 | |
| Rotation (45°) | 0.7078 | 0.7961 | 0.9871 | |
| Scaling (1/2) | 0.9843 | 0.9473 | 0.9991 | |
| Scaling (2) | 1 | 0.9138 | 0.9996 | |
| Rotation (10°) + Scaling (2) | 0.8904 | 0.8279 | 0.9817 | |
| Rotation (30°) + Scaling (1/2) | 0.7809 | 0.7947 | 0.9851 | |
| Shearing (1/8) | 0.9061 | 0.5945 | 0.9973 | |
| Shearing (1/4) | 0.8157 | 0.4789 | 0.9894 | |
| Shearing (1/2) | 0.5965 | 0.4560 | 0.9477 | |
| Median filtering | 0.9826 | 0.9469 | 0.9965 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fan, D.; Zhang, X.; Kang, W.; Zhao, H.; Lv, Y. Video Watermarking Algorithm Based on NSCT, Pseudo 3D-DCT and NMF. Sensors 2022, 22, 4752. https://doi.org/10.3390/s22134752
Fan D, Zhang X, Kang W, Zhao H, Lv Y. Video Watermarking Algorithm Based on NSCT, Pseudo 3D-DCT and NMF. Sensors. 2022; 22(13):4752. https://doi.org/10.3390/s22134752
Chicago/Turabian StyleFan, Di, Xiao Zhang, Wenshuo Kang, Huiyuan Zhao, and Yingjun Lv. 2022. "Video Watermarking Algorithm Based on NSCT, Pseudo 3D-DCT and NMF" Sensors 22, no. 13: 4752. https://doi.org/10.3390/s22134752
APA StyleFan, D., Zhang, X., Kang, W., Zhao, H., & Lv, Y. (2022). Video Watermarking Algorithm Based on NSCT, Pseudo 3D-DCT and NMF. Sensors, 22(13), 4752. https://doi.org/10.3390/s22134752





