Abstract
Missing tag incidents are common in RFID-enabled supply-chain and warehousing scenarios due to cargo theft and employee error operations, which may lead to serious economic losses or potential safety hazards. On the premise of ensuring the accuracy of missing tag detection, this paper aims to improve the time efficiency in an integrated RFID system. Unlike prior work focusing on detecting missing items from a large number of homogeneous tags that are monitored by a single reader, one integrated RFID system possesses multiple readers to communicate with the heterogeneous tags, which have different categorical attributes. In addition, the prior work required repeating the execution several times to capture the missing tags in assorted categories, which is of low time efficiency. Thus, a protocol called Multi-reader Missing Tag Detection (MMTD) is proposed to capture the missing tag quickly and reliably, which can detect missing tags from different categories in a parallel manner and is much more time-efficient than previous work. MMTD has two major advantages compared to prior work: (i) It leverages the knowledge of the spatial distribution of tags to divide up a difficult detection task into several lightweight tasks, which are shared by multiple readers. (ii) It personalizes the time frame of the reader based on the tag population to optimize the utilization of the communication channel. The final simulation results reveal that MMTD is the best in time-efficiency among the comparison protocols, and MMTD outperforms the other missing tag detection protocols by at least in the Integrated RFID scenarios.
1. Introduction
Radio Frequency Identification (RFID) technology has helped shape many aspects of our daily lives. For example, the items are attached with tags to quickly inventory in a warehouse and pay conveniently in an unattended supermarket. Missing tag detection is a valuable and important problem in RFID research. According to a recent survey [1,2], the American retail industry has lost $46.8 billion from the missing items in 2017. To avoid significant economic loss, the system manager wants to detect missing items as quickly as possible. Thus, time-efficiency is a critical metric in the evaluation of execution performance.
The related protocols can be classified into two groups: missing tag detection [3,4,5,6,7,8], and missing tag identification [9,10,11,12]. The former concentrates on detecting the number of missing tags with the principle of probability and statistics. Once a missing tag is detected, the reader will terminate the time frame immediately and raise a warning message [13,14]. The latter focuses on continuously obtaining the exact missing tags list. It will check the existence of each tag one by one in a deterministic manner. Compared with missing tag detection, the latter typically takes more time to obtain the exact ID of each missing tag. To balance accuracy and time-efficiency, the above two schemes are often integrated to be used simultaneously. Specifically, we can first apply a lightweight probabilistic tag detection scheme to continuously monitor the missing tags. Once a missing tag is found, we can further adopt the deterministic tag identification scheme to obtain the complete ID.
This paper aims to improve the time-efficiency of missing tag detection in integrated RFID systems. Although many protocols have been proposed, they simply apply a single reader to monitor one category of tags [3,7,15]. However, the reading range of a reader (even equipped with multiple antennas) is limited [16]. Therefore, in integrated RFID systems, many readers are deployed to ensure communication between readers and all tags. Thus, tags in the same category may be monitored by several readers and each reader covering parts of several categories. Some authors take the multi-reader and multi-category scenarios into consideration, but ignore the distribution of the tags and just set the uniform parameters for all readers [6]. Due to the differentiated spatial distribution of the tags, the uniform reader settings will result in more invalid slots and decrease detection efficiency. Therefore, personalizing the parameter settings of the reader is extremely important for improving the execution speed of missing tag detection.
2. Proposed Approach
To improve the time-efficiency in complex multi-reader and multi-category RFID scenarios, we propose a Multi-reader Missing Tag Detection (MMTD) protocol to parallelize the non-conflict readers and personalize the parameters of readers according to the tag population. In an integrated RFID system, readers are distributed to continuously investigate the monitoring area and determine if any of the tags are missing. However, reader-to-reader collision (R2Rc) happens when two readers have a duplicate communication area. R2Rc may result in identification failure for the tags, and many anti-conflict protocols are proposed to eliminate the effect of R2Rc [17,18]. In our simulation, we employ the greedy algorithm to group the tags into several isolation batches, which ensures that the tags in the same batch are free of collisions. As shown in Figure 1, the reader will be grouped into two batches labeled with black and red. During the tag querying process, we will activate readers according to their batch ordering.
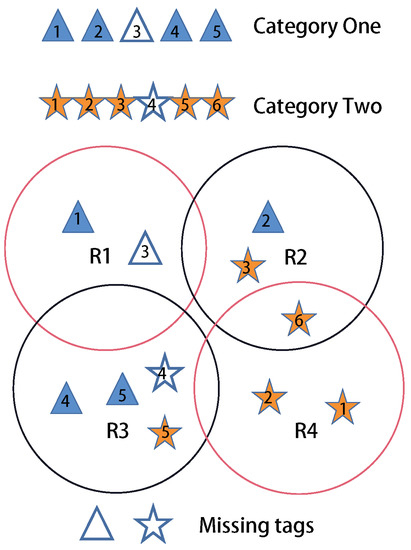
Figure 1.
System model.
MMTD can efficiently detect missing tags through the following three phases. First, each reader estimates the category size in its monitoring region and groups the tag categories with similar sizes for parallel missing tag detection. Second, since the categories in one group have similar sizes, the reader can adopt uniform parameter settings to detect missing tags in its region simultaneously. The reader repeats the above operation multiple times to detect missing tags in different groups. Finally, each reader can obtain a set of absent tags for each category, which contains both the extraterritorial tags and parts of the missing tags. The intersections of the absent sets are truly missing tags detected in the RFID system. For the first and second phases we can consult the paper [6]. However, this paper addresses the missing tag detection under the precondition that only one reader in the RFID system is used. We concentrate on the individuation of readers, here, we personalize the time frame of readers based on the tag population to optimize the utilization of the communication channel. Previous work commonly assumed that multiple readers operate simultaneously and execute the same parameters; therefore, these protocols are low detection accuracy and inefficient, due to the identification failure being led by R2Rc and these protocols do not take the differences between the tasks undertaken by readers into consideration. In MMTD, a difficult detection task is divided up and shared with the readers. The main challenges of this paper are demonstrated in the following content. The first challenge is to ensure sufficient detection accuracy for each category of tags and optimize the time-efficiency of MMTD’s. The second challenge is to dynamically adjust and determine the termination of MMTD to accommodate the diversity of category sizes in integrated RFID systems. Therefore, we summarize the main contributions of MMTD as follows: first, MMTD personalizes the parameters of readers to achieve higher execution speed in detection of missing tag; second, MMTD optimizes the broadcast frame size of each reader with sufficient theoretical analysis to balance both accuracy and time-efficiency; finally, we evaluate the performance of our MMTD through the extensive comparisons, and the results indicate that MMTD meets the required detection accuracy and that the execution speed is at least faster than the other related protocols.
The rest of this paper is organized as follows. Section 3 elaborates on the advantages and disadvantages of related work on missing tag detection. Section 4 presents the system model and problem definition. Section 5 describes MMTD in detail and optimizes the parameters of readers. Section 6 conducts extensive simulation and evaluates the performance of MMTD. Section 7 is the conclusion of this paper.
3. Relate Work
RFID researchers have made great contributions to RFID development, and these works include the estimation of RFID tags [19,20,21], missing tag detection [3,6,7,8,22,23] and missing tags identification [9,10,12].
3.1. Estimation of RFID Tags
The estimation of RFID tags is to obtain a non-absolute value of the number of tags with the required accuracy. Zero-One Estimator (ZOE) [19] can achieve an accurate value of the number of tags with a high time-efficiency. In ZOE, only a small portion of tags are demanded to respond to the reader’s inquiry, and the cardinality of tags is inferred by measuring the ratio of busy (idle) slots. However, in an integrated RFID system, ZOE has to operate the estimations category-by-category. The Simultaneous Estimation for Multi-category RFID system (SEM) [20] exploits a new decoding mechanism that separates the single tag reply message from the combined signal in one slot, and estimates the category size by calculating the ratio of empty slots in the time frame. The RFID Estimation scheme with Blocker tags (REB) is the first estimation scheme that is designed for the privacy protection, REB imports the blocker tags, and calculates the population size of genuine tags by computing the ratio of empty slots and singleton slots in a time frame. Physical Layer Cardinality Estimation for large-scale RFID system (PLACE) [21] can obtain the number of tags in one slots through the signal of physical layer, and estimate the population size of tags by calculating the ratio of various collision slots. However, PLACE is designed based on the GNURario/USRP platform. The physical layer signals are difficult to achieve with commercial RFID systems. In this paper, we adopt the SEM method to estimate the population size of tags. SEM is designed for multi-category RFID system, and the simulations verify that it has excellent performance.
3.2. Missing Tag Detection
In the Efficient Missing-tag Detection protocol (EMD) [8] that Luo et al. proposed, the sampling method allows for a small ratio of tags participating in polling ID from reader to tags. In the Trusted Reader Protocol (TRP) [7], the frame slots are optimized and the missing tags can be detected by comparing the expected slots with actual slots. In the RFID monitoring protocol with unexpected tags (Run) [3] that Shahzad et al. proposed, multiple Aloha frames are used to detect the missing tag with unexpected tags existing. The Multi-seed Missing tag detection protocol (MSMD) [22] adopts the sampling and multi-hash methods to select the singleton slots in frames, if a singleton slot is transformed into empty, the missing tag event is existing. They all assume that one tag category and a single reader in work scenarios. Improving the time-efficiency and satisfying the accuracy of requirements are critical demands for an integrated RFID system. Liu et al. proposed the Simultaneous Missing Tag Detection protocol (SMTD) [6] for multiple categories RFID systems. SMTD decodes the combined signal of tag responses to detect if they are missing tags. However, in an integrated RFID system, where the readers of SMTD share uniform parameters, the distribution of tags and the individuation of readers are neglected.
3.3. Missing Tags Identification
Zhang et al. [10] uses the empty slots, singleton slots, that the particular tags should map into, to find missing tags. Yu et al. proposed the point-to-multipoint protocol (P2M) [9], in P2M, each tag chooses one slot to map, and the number of slots is . By optimizing the Q, P2M can achieve the minimum time-cost of missing tag identification. Vector-based Missing Key tag Identification protocol (VEKI) [12] needs to be executed multiple rounds, and the reader broadcasts an expected vector that is computed by the back-end server to tags. The missing tag will be determined by comparing the status of slots between an expected vector and actual frame slots.
4. System Model and Problem Definition
4.1. System Model
In an integrated RFID system such as Figure 1, a mass of tags belonging to multiple categories are distributed in the monitoring area. The tags have their respective IDs, and each ID is classified into two parts: category ID and member ID. Category ID is a binary string, and as an identifier, represents that a tag belongs to a certain category. In the binary string, one bit is 1, and all other bits are 0 s. Member ID indicates that a tag is a member of one particular category. Multiple readers are carefully deployed across the entire monitoring area to ensure communication between readers and tags.
The execution of MMTD is compatible with the ALOHA protocol, and we assume that all tag IDs are stored on a central server. Only one hash function is required for execution, and the data is stored in the tags’ memory. In one execution frame, the parameters including the frame size and a random hash seed are sent to tags by reader, once the tags receive the parameters, they will determine which slot to respond to. We classify the frame slots into two types: singleton slot and non-singleton slot. In singleton slot, only one tag maps into, and we represent it as 1; in non-singleton slot, there are no tag maps into or multiple tags map into, we represent it as 0.
To perform a fair simulation, we set the parameters as follows: The transmission rate of down-link is 53 Kb/s, while the transmission rate of up-link is 26.5 Kb/s. The duration time between the execution of two slots is 302 ms [6,24]. Following the assumptions made in previous missing tag detection schemes [3], we assume that there are no errors during wireless transmitting–receiving. We implemented our simulator using MATLAB.
4.2. Problem Definition
In an integrated RFID system, we assume that U readers are carefully deployed in the monitoring area to ensure that each tag can communicate with at least one reader. N tags are expected to be located in the monitoring area and distributed into categories . The number of tags in each category is , . In actuality, there are missing tags in the i-th category. For the i-th category, the number of present tags is .
We use to represent the threshold value of expected missing tags. Let be the probability that the readers can detect the missing event of the i-th category. The definition of missing tag detection is demonstrated as follows.
Definition 1.
For the i-th category, the number of the expected present tags is , the population size of missing tags is , the optimum missing tag detection is at least one missing tag is found in a minimum execution time with the detection probability , if , where is the probability of detection requirement of the i-th category.
However, in an integrated RFID system, U readers are deployed to monitor the tags which are attached to items. Thus, the tags outside the monitoring area of one reader will be determined as missing tags. However, the determined missing tags by one reader are not true missing tags.
Definition 2.
(The true missing tags). U readers are deployed with overlaps in an integrated RFID system. For the i-th category, after multiple turns of detection, each reader obtains a set of missing tags that are determined by itself. The true missing tags set , where is the missing tags set which are obtained by the j-th reader.
Thus, if the set S is empty, all expected tags present in the monitoring RFID system, whereas if there is at least one tag in the set S, the missing tag event is detected. As shown in Figure 1, for category one, the reader obtains a missing tag set which contains . contains . contains . considers all tags in category one are missing. The intersection of missing tag set S contains only one missing tag . The is truly missing. The main notations used in this paper are shown in Table 1.

Table 1.
Main notations used in the paper.
5. The Proposed MMTD Protocol
5.1. Protocol Design
We do not know whether all tags can exchange information with readers. In MMTD, the operations that are executed on each reader are similar to those in the simultaneous missing tag detection plus category clustering (SMTD + CC) protocol [6]. The SMTD+CC protocol is disembodied because it simply assumes that there is only one reader in an RFID system.
As shown in Figure 2, based on Manchester encoding, the combined signal received by the reader can be decoded into category vectors. We can obtain three category vectors from the actual time frame by decoding, which represent the mapping of each category. The number of tags for each category can be obtained through an estimation method in the monitoring area of one reader. For example, SEM [20] decodes the combined signal of multiple categories into categorized independence signals, and calculates the proportion of empty slots to estimate the population size of each category. The missing event will be issued at the end of the iterative operation by comparing the category vectors and the expected time frame. For example, the first slot should be 1 according to the expected time frame, but in category-1 vector, it is 0 in actuality, so we can determine that this tag is missing.
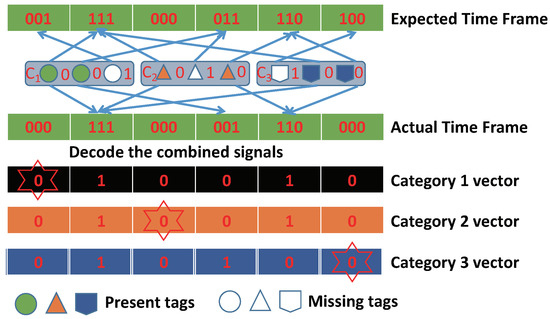
Figure 2.
The decoding of received combined signal.
The traditional missing tag detection method is category by category for an integrated RFID system; this method is low time-efficient. MMTD designs a characteristic tag ID and adopts the parallel detection method to improve the time-efficiency. However, the setting of broadcast frame size is a problem that directly affects the detection efficiency. As known to us, in a single category RFID system, the detection efficiency is highest when the broadcast frame size is equal to the population size of tags. However, there are different population sizes in different categories within an integrated RFID system. They adopt the same broadcast frame size, more collision slots will present if the population size of a category is far greater than the broadcast frame size, whereas more empty slots will present if the population size of the category is far less than the broadcast frame size. These non-optimal solutions result in low utilization of slots in the missing tag detection. Thus, MMTD groups the similar population sizes of categories into one batch and sets the same parameters to the members of the batch. The parameters include the broadcast frame size and the random seed.
In order to obtain a higher time-efficiency, MMTD clusters the categories into multiple groups. We name this method for CG. CG is a k- clustering algorithm, k is the number of clustering groups, is the average. The cluster objects are , where . As shown in Figure 3, we assume that there are 10 categories monitored by one reader, and the number of tags in each category are 800, 900, 1200, 1400, 1550, 2200, 2400, 2550, 2800, 3000, respectively. The broadcast frame size in one batch is the average population size of tags in one category.
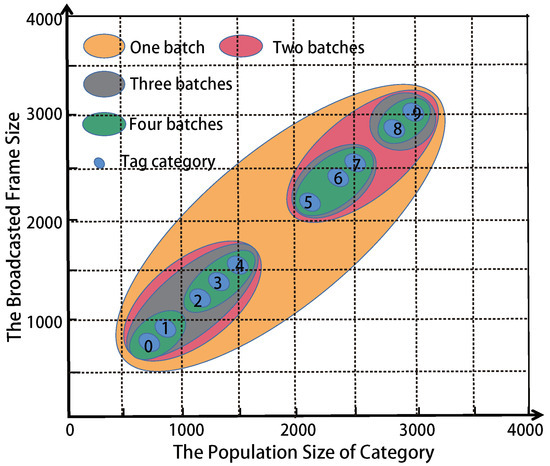
Figure 3.
Category clustering.
For example, if the k is 3, the categories will be clustered into 3 batches: , , and . Their broadcast frame sizes are 1170, 2383, 2900, respectively. However, we do not know the number of tags in each category under the monitoring of every reader. Thus, the optimal k is a variable for each reader. Before MMTD execution, the optimal k value will be obtained by simulation.
Specifically, in MMTD detection, each tag also selects a pseudo-random time slot to send its category identifier (category ID), and each reader can decode a frame occupation vector for each category. For each tag in category , on reader , we use the hash parameters and its ID to calculate the location in a given time frame. If the corresponding bit in the frame occupation vector is 0, we know that this tag is missing; it will be added into the missing tag set , which is initialized as an ∅. After several rounds of tag detection operations, the set may contain the actual missing tags and the tags that are covered by other readers. To obtain the real missing tag set for category , we calculate . This means that a tag is identified as missing if and only if it is recognized as missing by all readers. In this case, the missing tag event for category is found, where . To meet the requirement of detection accuracy for each category, we must perform a sufficient number of detection rounds on each reader . The detection rounds required by category on reader are represented by .
5.2. Parameters Optimization
We first investigate what is required by each reader to execute a number of frames (denoted as ) to meet the requirement of detection accuracy for each category. Then, we calculate the optimal frame sizes and , which minimize the time cost on reader for category . We use to represent the number of tags in category that are covered by the reader .
5.2.1. Number of Frames
We use to represent the probability that an arbitrary bit in the frame occupation vector of category on reader is 0. The expression of is calculated as follows.
where is the broadcast frame size. However, for some practical reason [24], the frame has to terminate after executing time slots, where [25,26,27] is called the executed frame size. After executing frames with sizes and , the probability that a real-missing tag in category can be detected as absent from reader at least once is as follows:
Hence, we can calculate the probability of a real-missing tag can be discovered as follows:
If tags in category are missing from the system (), the missing tag event can be discovered if and only if at least one of them can be discovered. The corresponding probability is calculated as follows:
To satisfy the detection probability , we must solve the following inequality,
Solving the above inequality, we have:
To save time, we set as follows:
5.2.2. Optimize Frame Size and
The time cost required by reader to satisfy the accuracy of category , denoted as , could be calculated as follows:
on behalf of the slot duration for the reader initializes a -slot time frame with command, and represents the slot duration for the tag replies to the command. Then, we provide sufficient analysis of the frame size of broadcast , and the frame size of execution to make an impact on the time-efficiency of MMTD and propose Theorem 1 to recommend it in the following content.
Theorem 1.
For an arbitrary reader , we assume the number of tags in each category covered by it, denoted as , is known to us. To minimize the detection time , the optimal broadcast frame size should be set to , the optimal executed frame size is , and .
Proof.
We investigate from Equation (9) that when ; when ; when . We discover that the achieves its minimum value when is . Next, in order to optimize the , we obtain the first-order partial derivative against as follows:
where . Then, we obtain the first-order partial derivative of with respect to as follows:
Note that when takes its optimal value of , the is larger than 0. is smaller than 0, so the detection time is a reduction function with respect to . Hence, the should be set to for category on reader . □
The number of tags in different tag categories covered by the same reader are usually different. Thus, different tag categories need to be set differently to optimal frame sizes. Similar to the CC scheme [6], we divide tag categories under a reader into multiple batches according to the required frame sizes. The categories within the same batch share the same average frame size. The best batch division result is that the sum of time cost consumed by all batches is minimized. Note that the batch division process is virtually computed on the server side. After getting the best batch division strategy, missing tag detection is performed batch by batch.
5.2.3. Dynamically Adjusting and Determining Termination
According to Theorem 1, when , and , the detection time of category on reader is minimized. However, as aforementioned, the value of is actually unknown to us. Hence, we will discuss how to configure the frame sizes of MMTD without knowing the value of . At the very beginning, we know nothing about , hence, we simply set and , where is equal to the population size of tags of category in the whole system. Then, we quote the CC protocol [6] to cluster the tag categories into multiple batches. Here, in each batch, the actually used frame sizes are averaged from the optimal frame sizes of all categories in this batch. After executing the first round of missing tag detection for each batch on reader , the obtained frame occupation vectors can also be fed into the SEM algorithm [20] to estimate the value of for each category . For the following rounds of detection, we can use the approximate value estimated from the previous round to optimize the frame sizes and adjust the batch division.
On a reader , a category may belong to different batches in different rounds because the estimated tag cardinality is not entirely accurate. Thus, a category may exploit different frame sizes in different rounds. In addition, it is hard to simply calculate how many rounds are required to satisfy its detection probability. Next, we propose a dynamic determination method that allows us to judge whether a category has met the required detection accuracy at the end of an arbitrary round. Suppose that the reader has performed y rounds of detection for category . In the x-round (), for each category , we obviously know the ratio of bit 0 s in the corresponding frame occupation vector and the actually used frame sizes and . Thus, we can easily calculate the probability that a real-missing tag can be detected out in this round as . The overall probability that a real-missing tag can be detected out through y rounds can be easily given as . If this probability is larger than , the detection process for category on reader can be terminated due to the following reasons. Each reader has the probability to detect a real-missing tag. All U readers will have the probability to detect a certain real-missing tag, it is eventually asserted as a missing tag. At least one of the real-missing tags is detected out, and we will successfully assert the missing event for category . Hence, the probability of successful detection for category can be calculated as , which exactly equals the required probability . This means that the above dynamic termination approach can satisfy the predefined missing tag detection accuracy for each category.
5.3. The Attacks from Physical Layer
As we know, RFID tags are commonly exposed to the outside of the tagged items, and the communication between reader and tags through electromagnetic waves. Thus, the tags are easy to destroy with physical attacks, and the tag identification is vulnerable to electromagnetic interference attacks. These attacks on the physical layer take advantage of the nature of RFID communication, the poor physical securing of RFID devices, and the lack of tensile strain capacities against physical damage. The attacks cause three types damage to RFID devices: permanently disabling damage, temporary damage, and persistent damage. The permanently disabling damage to RFID devices is implemented by tag removal, destructing, and the Kill command issue. The temporary damage adopts the signal shielding method to escape the tag identification. For example, an aluminum bag prevents the communication between reader and tags. The persistent damage is that the adversarial devices are deployed surreptitiously to replace the legitimate RFID reader and tags.
The first two damages can be detected by missing tag detection protocols and artificial reinspection, the killed tags can be recovered by the activate command. However, this persistent damage is hard to detect by the common missing tag detection protocols. Many related protocols concentrated on this damage, they adopted encryption methods to prevent communication between adversarial devices and legitimate devices. For example, Qi et al. [28] proposed an encryption method that overcomes the inefficiency hurdles of CP-ABE [29]. Qi et al. adopted a double encryption paradigm to prevent the malicious intrusion reader and tag information loss with high efficiency. Gope et al. [30] proposed a enhanced protocol based on physically unclonable functions to prevent invasion readers. Though physical security is a concern among researchers, many excellent works have been proposed, and this paper concentrates on the time-efficiency of missing tag detection. Thus, we do not discuss more about physical security information in RFID systems.
5.4. The Detection of R2Rc
R2Rc is reader-to-reader collision, that is to say, two readers communicate with one tag at the same time. The tag receives a combined signal from readers, and the reply from the tag is an error information. The two readers can not decode the tag ID from the error information. Thus, R2Rc is a problem that cannot be ignored in RFID research. How do we determine whether R2Rc exists between two readers? An intuitive approach is tag identification, if two readers obtain the same tag ID, we can determine that the R2Rc exists. The other method is to obtain the Received Signal Strength Indicator (RSSI) from one location to ensure the communication border of one reader. If the communication borders of readers intersect, we can determine that R2Rc exists.
After confirming the relationship between readers and whether the R2Rc exists in any two readers, the next question is how to eliminate the influence of R2Rc. Most existing protocols are designed based on Time Diverse Multiple Access (TDMA), all readers are split into multiple groups, there is no R2Rc in each group, and the groups work at different time frames. For example, the reader scheduling protocol Colorwave [31] groups the readers into many colored nodes, the nodes of the same color can work simultaneously. However, in multiple categories RFID system, they still detect the missing tags category-by-category. This method is low time-efficiency. To minimum the impact of R2Rc, some protocols require that the readers work on different frequency communication channels. However, the communication range of the reader is closely related to the working frequency. The higher the working frequency, the longer the communication distance. Thus, changing the frequency communication channel may result in tag identification failure.
6. Performance Evaluation
In this section, we evaluate the performance of MMTD in two key aspects: detection accuracy and time efficiency. To demonstrate the outstanding performance of the proposed MMTD, we import multiple comparison protocols. The comparison protocols include TRP [7], RUN [3], SSDA, ESSDA [32], EMD [8], and SMTD, SMTD+CC [6]. The slotted ALOHA scheme is their fundamental method, TRP computes the probability of one missing tag mapping into an empty slot; unexpected tags are the impact factor that decreases the time-efficiency for missing tag detection, RUN can accomplish the detection effort with a high time-efficiency in this environment. SSDA and ESSDA detect a transformation that the expected singleton slot is changed into an actual empty slot, to determine whether the mapping tag is missing. However, the utilization of slots is low, because the collision slots are abandoned directly. EMD adopts a higher time-efficient sampling method to reduce the number of response tags; SMTD and SMTD+CC can simultaneously detect missing tags for multi-category through combine-signal decoding.
MMTD is workable in various static tagged applications that have different spatial limitations. In this paper, to give an intuitive demonstration and comparable simulation, an integrated RFID system is built, we set 20 readers monitor a 60 m × 60 m monitoring area. According to the reader scheduling protocols [31], the 20 readers are split into three groups, and they are marked with cyan, red, and black. The locations of readers marked with cyan are , , , , , and , respectively. Their communication radii are 9.0 m, 12.0 m, 15.6 m, 11.4 m, 12.0 m, and 10.8 m, respectively. The locations of readers marked with red are , , , , , , , and , respectively. The corresponding communication radii are 9.0 m, 9.0 m, 9.0 m, 10.2 m, 7.8 m, 13.2 m, 9.6 m, and 8.4 m, respectively. The locations of black readers are , , , , , and , respectively. Their communication radii are 14.4 m, 12.0 m, 12.0 m, 12.0 m, 12.0 m, and 12.0 m, respectively. The distribution of readers as shown in Figure 4. The detection time begins when the first query starts, until the last reader finishes the missing tag detection task.
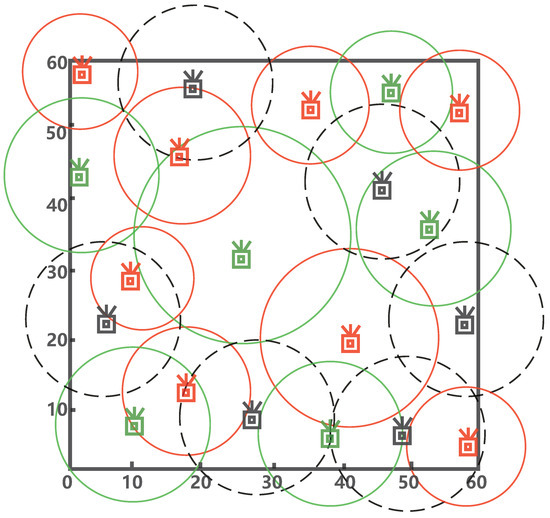
Figure 4.
An example of reader distribution.
In the simulation, we verify that the detection accuracy of our MMTD meets the requirements, and that the execution time of MMTD is shorter than the comparison protocols. We assume that there are 20 readers randomly deployed in the monitoring area to monitor 10 categories of tags. The sizes of category-1 to category-10 are 1500, 2000, 3000, 3500, 8000, 9500, 20,000, 21,000, 22,000, and 23,000, respectively [6]. All of the tags are randomly distributed into the monitoring area, and each tag can be monitored by at least one reader. The number of missing tags in each category is set to 10. In the default setting of MMTD, the threshold on the number of missing tags is 10 and the probability of missing tags detection is 0.95. Since the number of missing tags in every categories reaches the threshold, MMTD should theoretically detect out at least one missing tag in each categories with 0.95 probability.
6.1. Detection Accuracy
To evaluate the detection accuracy of the proposed MMTD protocol, we deploy 20 readers in the monitoring area. The true number of missing tags varied from 8 to 12. We observe in Figure 5a–e that the probability of detection satisfies the requirements when the population size of missing tags equals or exceeds the tolerance threshold of 10 in each category; therefore, the MMTD satisfies the accuracy requirements in multi-category and multi-reader RFID scenarios.
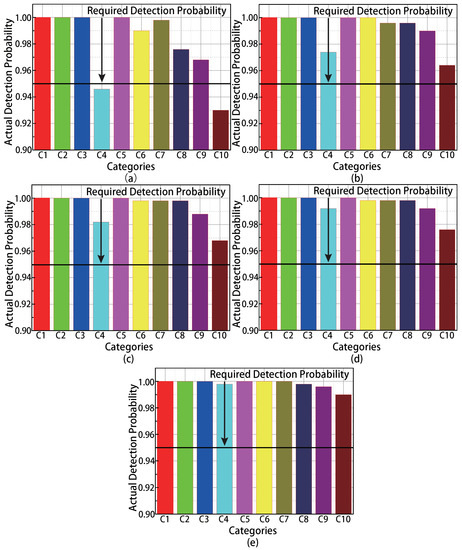
Figure 5.
The relationship between detection accuracy and the number of actual missing tags. (a) 8 missing tags in each category; (b) 9 missing tags in each category; (c) 10 missing tags in each category; (d) 11 missing tags in each category; (e) 12 missing tags in each category.
However, when the tolerance threshold is larger than the number of missing tags, the probability of detection does not always satisfy the required . This is because the actual execution rounds are smaller than the requirements, and this happens when the population size of the category is larger than the broadcast frame size in its batch.
6.2. Time-Efficiency in Multi-Reader Scenarios
In an actual RFID scenario, the distribution area of one category tags may be monitored by multiple readers. Though the burden of each reader is reduced and the size of each frame is decreased, the number of detection frames is increased because each reader needs to satisfy stricter detection accuracy requirements. In this section, we investigate the time-efficiency of MMTD when the various parameters are changed.
6.2.1. Impact of U
The value of U is the number of readers required to be deployed into the monitoring area. We enumerate the U data from 20 to 40. At the moment, the other parameters are the default setting, the and are not workable, because the the population sizes of 10 categories are constant. Two major observations are shown in Figure 6. First, the proposed MMTD protocol is the fastest protocol for changing the number of the readers. For example, the execution time of SMTD+CC is 52.9 s, however, the time required by the MMTD is only 17.9 s when there are 40 readers in the monitoring area. This result indicates that the MMTD runs faster than the RUN protocol. Second, the time consumed by the MMTD reduces as R increases because the burden of the reader decreases. However, the time consumed by other related works is rising, because an increasing number of readers will bring more groups into reader-scheduling.
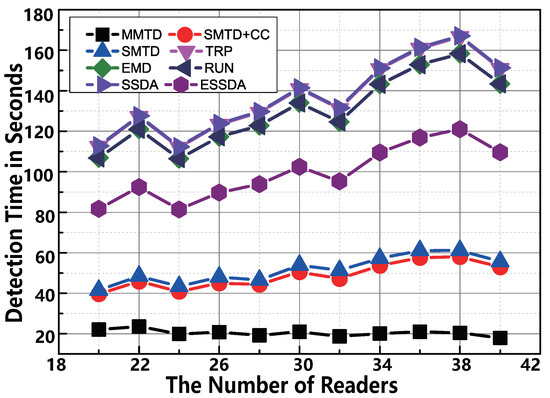
Figure 6.
The comparison of time-efficiency between MMTD and other missing tag detection protocols when the number of readers R is set to be from 20 to 40.
6.2.2. Impact of
The average value in the normal distribution function determines the number of tags directly. In this simulation, we vary the value of from 10,000 to 20,000. That is to say, the number of tags is monotonically increasing. The value of R is 20, and the other parameters are the same as those in the part of “Impact of U”. According to the demonstration of Figure 7, the MMTD protocol has the highest time-efficiency among the comparison protocols. For example, if the data of is 20,000, the time consumption of SMTD + CC is 47.4 s; however, the execution time of the MMTD protocol is only 27.0 s. Moreover, as the increases in each category, the rate of change of the MMTD is much lower than that of the other protocols.
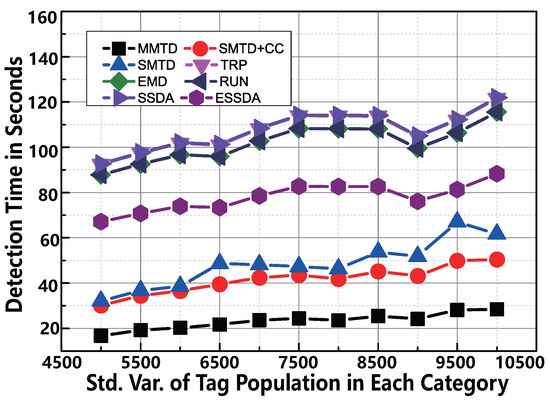
Figure 7.
The comparison of time-efficiency between MMTD and other missing tag detection protocols when is set to be from 5000 to 10,000.
6.2.3. Impact of
With the standard deviation of the function increasing which determines the number of tags, the volatility of the number of tags is monotonically increasing. To make the comparison under different , we vary the value from 5000 to 10,000 in each category in the simulation. The MMTD protocol has the best performance by changing as shown in Figure 8. For example, if the is 10,000, the execution time of SMTD + CC is 50.4 s. However, that of the MMTD is only 28.4 s. This means that our MMTD runs faster than the SMTD+CC protocol. As increases, the MMTD protocol performs much better than other comparison protocols. The reason is that the broadcast frame size of the MMTD is smaller than that of the SMTD + CC, and the ratio of the detection time of the MMTD to the number of broadcast frame size of the MMTD is not positive.
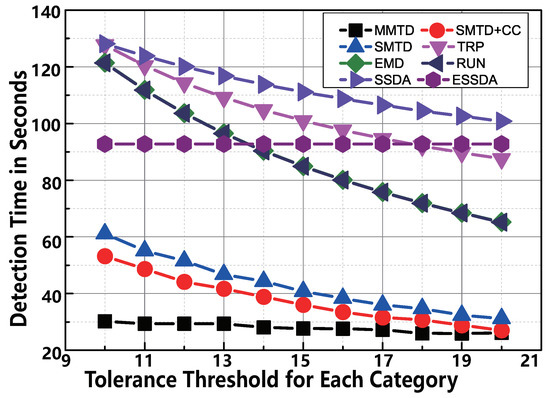
Figure 8.
The comparison of time-efficiency between MMTD and other missing tag detection protocols when is set to be from 10 to 20.
6.2.4. Impact of
The tolerance threshold determines the performance of MMTD directly. The smaller means the stricter requirement on detection accuracy. To show the excellent performance of MMTD, we make the comparison between the protocols when we vary the tolerance threshold from 10 to 20 for each category. The number of actual missing tags is equal to . We observe the following in Figure 9. First, the MMTD has the best performance of the protocols. For example, if , the execution time of SMTD + CC is 53.0 s, whereas that of the MMTD protocol is only 30.2 s. This means that our MMTD runs faster than the SMTD + CC protocol. Second, as increases, the time consumption of TRP, EMD, RUN, and SMTD + CC shows a decreasing trend, but this trend is not obvious in terms of MMTD. The reason is that the execution time of all protocols are inversely proportional to the tolerance threshold except for MMTD. The time-cost of the MMTD protocol is only slightly affected by the threshold , as shown in Equation (8).
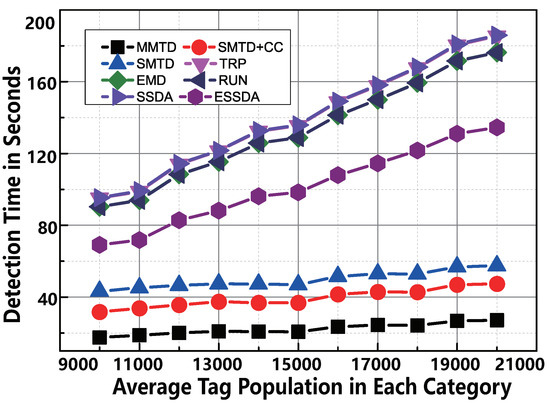
Figure 9.
The comparison of time-efficiency between MMTD and other missing tag detection protocols when is set to be from 10,000 to 20,000.
6.2.5. Impact of
To clarify the comparison, we vary the reliability probability from to in the simulation for each category. The following two observations are made in Figure 10. First, the proposed MMTD protocol exhibits the highest-efficiency among the comparison protocols. For example, when is , the time-execution of SMTD + CC is 92.9 s, whereas that of the MMTD is only 37.7 s. This means that the execution speed of our MMTD runs faster than the SMTD+CC protocol. Second, when the required detection accuracy is higher, the time-cost of all protocols, except for ESSDA and MMTD increases significantly. The reason is that the detection times of the MMTD and ESSDA protocols are slightly affected by .
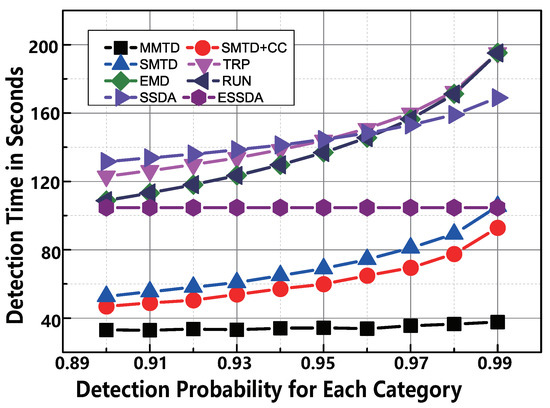
Figure 10.
The comparison of time-efficiency between MMTD and other missing tag detection protocols when is set to be from to .
7. Conclusions
In this paper, we propose a highly efficient method for missing tag detection, which is designed for multi-category and multi-reader RFID scenarios. We make the following key contributions. First, MMTD optimizes the parameters of each reader to personalize the reader’s settings according to the tag populations, while the other protocols often broadcast identical settings by all readers. Second, MMTD proposes a collision elimination algorithm to detect missing tags simultaneously without any conflicts between multiple readers. Third, extensive simulations indicated that the MMTD protocol outperformed similar missing tag detection protocols by at least in the multi-reader scenarios.
Author Contributions
Conceptualization and methodology, K.G.; software and validation, X.X.; investigation, H.Q.; supervision, K.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Informed consent was obtained from all subjects involved in the study.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Lin, K.; Chen, H.; Ai, X.; Shakhov, V.; Ni, L.; Yu, J.; Li, Y. EUMD: Efficient Slot UItilization based Missing Tag Detection with Unknown Tags. J. Netw. Comput. Appl. 2020, 160, 102640. [Google Scholar] [CrossRef]
- Available online: http://fortune.com/2015/06/05/walmart-theft/ (accessed on 20 March 2019).
- Muhammad, S.; Liu, A.X. Expecting the Unexpected: Fast and Reliable Detection of Missing RFID Tags in the Wild. In Proceedings of the 2015 IEEE Conference on Computer Communications, Hong Kong, China, 26 April–1 May 2015. [Google Scholar]
- Lin, K.; Chen, H.; Yan, N.; Li, Z.; Li, J.; Jiang, N. Fast and Reliable Missing Tag Detection for Multiple-Group RFID Systems. IEEE Trans. Ind. Inform. 2021, 18, 2656–2664. [Google Scholar] [CrossRef]
- Zhang, Y.; Chen, S.; Zhou, Y.; Fang, Y. Missing-tag Detection with Unknown Tags. IEEE/ACM Trans. Netw. 2020, 28, 1297–1310. [Google Scholar] [CrossRef]
- Liu, X.; Guo, K.; Liu, Z.; Zhou, X.; Qi, H.; Xue, W. Fast and Accurate Missing Tag Detection for Multi-category RFID Systems. In Proceedings of the 2018 IEEE International Conference on Smart Internet of Things (SmartIoT), Xian, China, 17–19 August 2018. [Google Scholar]
- Tan, C.C.; Sheng, B.; Li, Q. Efficient Techniques for Monitoring Missing RFID Tags. IEEE Trans. Wirel. Commun. 2010, 9, 1882–1889. [Google Scholar] [CrossRef]
- Luo, W.; Chen, S.; Li, T.; Chen, S. Efficient Missing Tag Detection in RFID Systems. In Proceedings of the IEEE INFOCOM, Shanghai, China, 10–15 April 2011. [Google Scholar]
- Yu, J.; Gong, W.; Liu, J.; Chen, L.; Wang, K.; Zhang, R. Missing Tag Identification in Cots RFID Systems: Bridging the Gap between Theory and Practice. IEEE Trans. Mob. Comput. 2018, 19, 130–141. [Google Scholar] [CrossRef]
- Zhang, R.; Liu, Y.; Zhang, Y.; Sun, J. Fast Identification of the Missing Tags in a Large RFID System. In Proceedings of the IEEE SECON, Nashville, TN, USA, 17–20 March 2011. [Google Scholar]
- Wang, Y.; Liu, J.; Wang, X.; Chen, X.; Yan, Y.; Chen, L. Time-efficient Missing Tag Identification in an Open RFID System. ACM Trans. Sens. Netw. 2020, 16, 1–27. [Google Scholar] [CrossRef]
- Chen, H.; Wang, Z.; Xia, F.; Li, Y.; Shi, L. Efficiently and Completely Identifying Missing Key Tags for Anonymous RFID Systems. IEEE Internet Things J. 2017, 5, 2915–2926. [Google Scholar] [CrossRef]
- Chen, H.; Xue, G.; Wang, Z. Efficient and Reliable Missing Tag Identification for Large-scale RFID Systems with Unknown Tags. IEEE Internet Things J. 2017, 4, 736–748. [Google Scholar] [CrossRef]
- Tan, H.; Choi, D.; Kim, P.; Pan, S.; Chung, I. An Efficient Hash-based RFID Grouping Authentication Protocol Providing Missing Tags Detection. J. Internet Technol. 2018, 19, 481–488. [Google Scholar]
- Liu, H.; Zhang, R.; Chen, L.; Yu, J.; Liu, J.; An, J. On Fast and Reliable Missing Event Detection Protocol for Multitagged RFID Systems. IEEE Internet Things J. 2020, 7, 10324–10335. [Google Scholar] [CrossRef]
- Jia, X.; Bolic, M.; Feng, Y.; Gu, Y. An Efficient Dynamic Anti-Collision Protocol Mobile RFID Tags Identification. IEEE Commun. Lett. 2019, 23, 620–623. [Google Scholar] [CrossRef]
- Mbacke, A.A.; Mitton, N.; Rivano, H. A Survey of RFID Readers Anticollision Protocols. IEEE J. Radio Freq. Identif. 2018, 2, 38–48. [Google Scholar] [CrossRef]
- Amadou, I.; Mitton, N.; Sarma, S.E. HAMAC: High Adaptive MAC Protocol for Dense RFID Reader-to-reader Networks. In Proceedings of the of AdHocNets, San Remo, Italy, 1–2 September 2015. [Google Scholar]
- Zheng, Y.; Li, M. ZOE: Fast Cardinality Estimation for Large-scale RFID Systems. In Proceedings of the The 32nd IEEE International Conference on Computer Communications, Turin, Italy, 14–19 April 2013. [Google Scholar]
- Liu, X.; Li, K.; Liu, A.X.; Guo, S.; Wang, A.L.; Xie, X.; Wu, J. Multi-category RFID Estimation. IEEE/ACM Trans. Netw. 2017, 25, 264–277. [Google Scholar] [CrossRef]
- Hou, Y.; Ou, J.; Zheng, Y.; Li, M. PLACE: Physical Layer Cardinality Estimation for Large-scale RFID Systems. IEEE/ACM Trans. Netw. 2015, 24, 2702–2714. [Google Scholar] [CrossRef][Green Version]
- Luo, W.; Chen, S.; Li, T.; Qiao, Y. Probabilistic Missing-tag Detection and Energy-time Tradeoff in Large-scale RFID Systems. In Proceedings of the Thirteenth ACM International Symposium on Mobile Ad Hoc Networking and Computing—MobiHoc, New York, NY, USA, 11–14 June 2012. [Google Scholar]
- Han, W.; Liu, W.; Zhang, K.; Li, Z.; Liu, Z. A Protocol for Detecting Missing Target Tags in RFID Systems. J. Netw. Comput. Appl. 2019, 132, 40–48. [Google Scholar] [CrossRef]
- Shahzad, M.; Liu, A.X. Fast and Accurate Estimation of RFID Tags. IEEE/ACM Trans. Netw. 2015, 23, 241–254. [Google Scholar] [CrossRef]
- Liu, X.; Xiao, B.; Li, K.; Wu, J.; Liu, A.; Qi, H.; Xie, X. Rfid Cardinality Estimation with Blocker Tags. In Proceedings of the 2015 IEEE Conference on Computer Communications (INFOCOM), Hong Kong, China, 26 April–1 May 2015. [Google Scholar]
- Shahzad, M.; Liu, A.X. Probabilistic Optimal Tree Hopping for RFID Identification. IEEE/ACM Trans. Netw. 2015, 23, 796–809. [Google Scholar] [CrossRef]
- Shahzad, M.; Liu, A.X. Every Bit Counts: Fast and Scalable RFID Estimation. In Proceedings of the 18th Annual International Conference on Mobile Computing and Networking—MobiCom, Istanbul, Turkey, 22–26 August 2012. [Google Scholar]
- Qi, S.; Zheng, Y.; Li, M.; Liu, Y.; Qiu, J. Scalable Industry Data Access Control in RFID-enabled Supply Chain. IEEE/ACM Trans. Netw. 2016, 24, 3551–3564. [Google Scholar] [CrossRef]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy Attributebased Encryption. In Proceedings of the IEEE Symposium on Security and Privacy, Oakland, CA, USA, 20–23 May 2007. [Google Scholar]
- Gope, P.; Lee, J.; Quek, T.Q.S. Lightweight and practical anonymous authentication protocol for RFID systems using physically unclonable functions. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2831–2843. [Google Scholar] [CrossRef]
- Waldrop, J.; Engels, D.W.; Sarma, S.E. Colorwave: An Anticollision Algorithm for the Reader Collision Problem. In Proceedings of the IEEE International Conference on Communications, Anchorage, AK, USA, 11–15 May 2003; Volume 2, pp. 1206–1210. [Google Scholar]
- Li, Z.; He, C. Optimal Scheduling-based RFID Reader-to-reader Collision Avoidance Method using Artificial Immune System. Appl. Soft Comput. 2013, 13, 2557–2568. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).