Towards a Security Reference Architecture for NFV
Abstract
:1. Introduction
- Self-sufficiency: the software is no longer linked to the hardware. As a result, they will evolve independently of one another.
- Flexibility and speed: by decoupling software from hardware, it is possible to reassign and share infrastructure resources, allowing different functions to be performed at different times. As a result, network operations and their connections may be deployed more quickly and with greater flexibility.
- Scalability: in regular legacy network systems, Telcos have to be up to date with new network standards and requirements, which requires time, planning, and money. However, in NFV, decoupling software from hardware allows for dynamically scaling the actual performance of virtualized network functions with finer granularity and minimal effort.
- Reduced energy consumption: with the ability to scale up or down resources, Telcos will be able to reduce the OPEX needed to run network devices. Similarly, energy consumption at the customer end will be reduced significantly due to not having to install dedicated hardware to deliver network functions.
- Speed to set-up the network: the deployment and configuration of network services is much faster in NFV.
2. Background
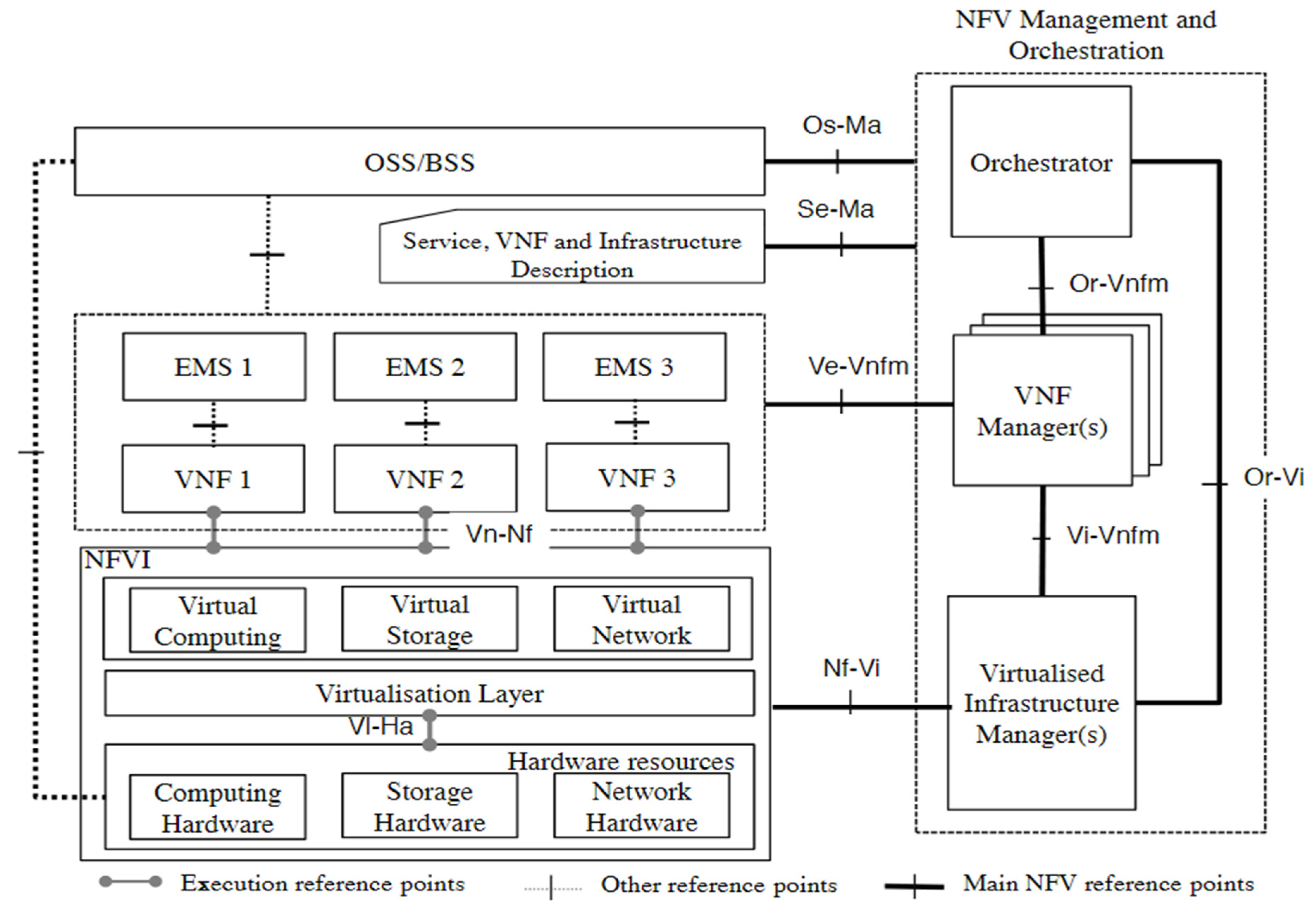
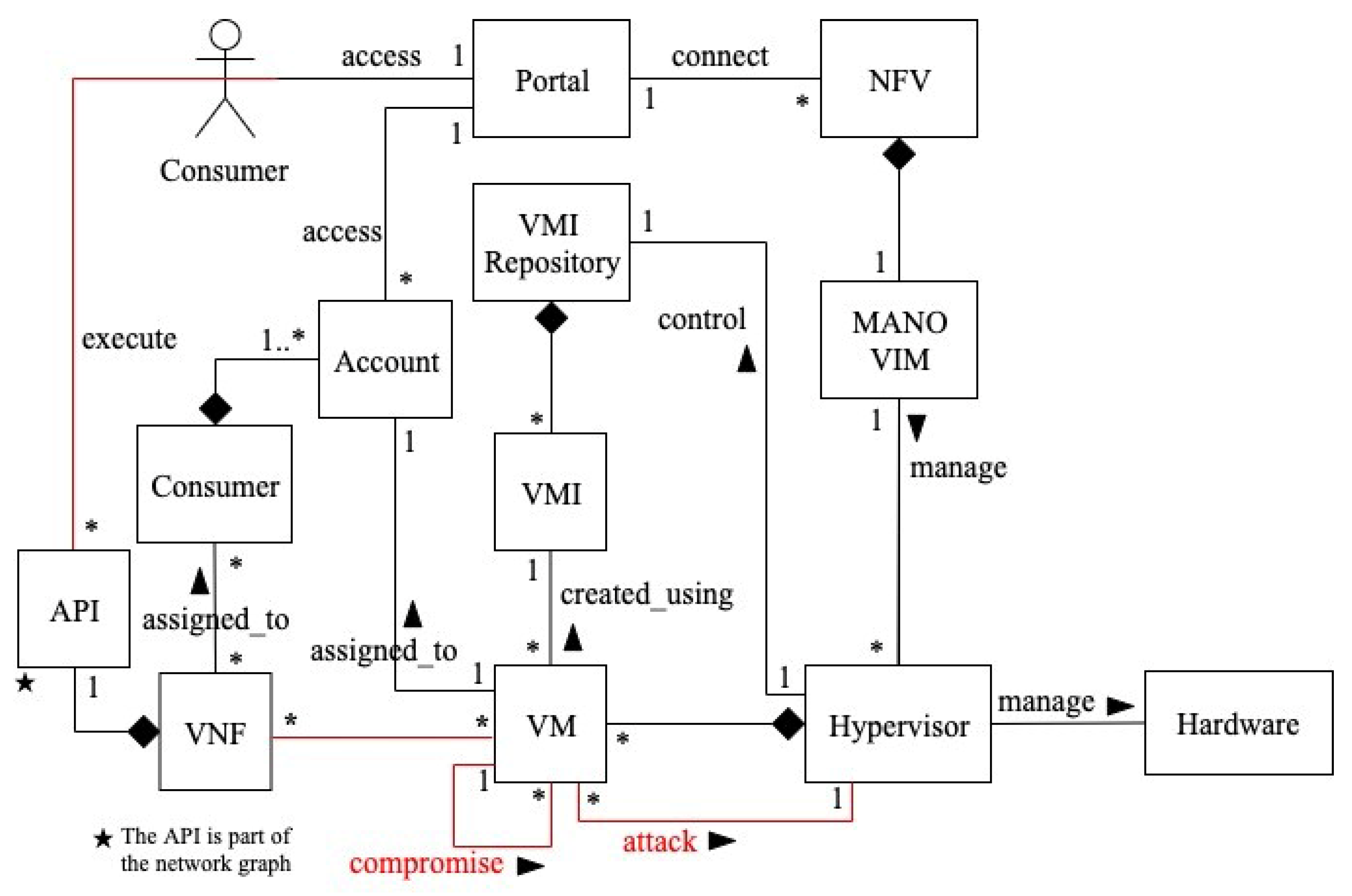
2.1. NFV Architecture
- Virtual infrastructure manager (VIM): is responsible for managing and controlling the interaction of the VNFs with the NFVI resources. The VIM performs resource management functions, such as keeping an inventory of software as well as management and orchestration of resources. The VIM is also responsible for collecting and logging information to check for faults, as well as collecting information for the purpose of capacity planning, performance monitoring, and performance optimization [3].
- VNF manager (VNFM): is responsible for managing and monitoring the VNF through the element management system (EMS), which includes scaling, changing operations, and adding new resources to the VNF, as well as communicating the states of VNFs to the other functional blocks that create the NFV architecture.
- Orchestrator: provides the necessary resources and networks needed to set up cloud-based services and applications, including the use of different virtualization software as well as hardware [15].
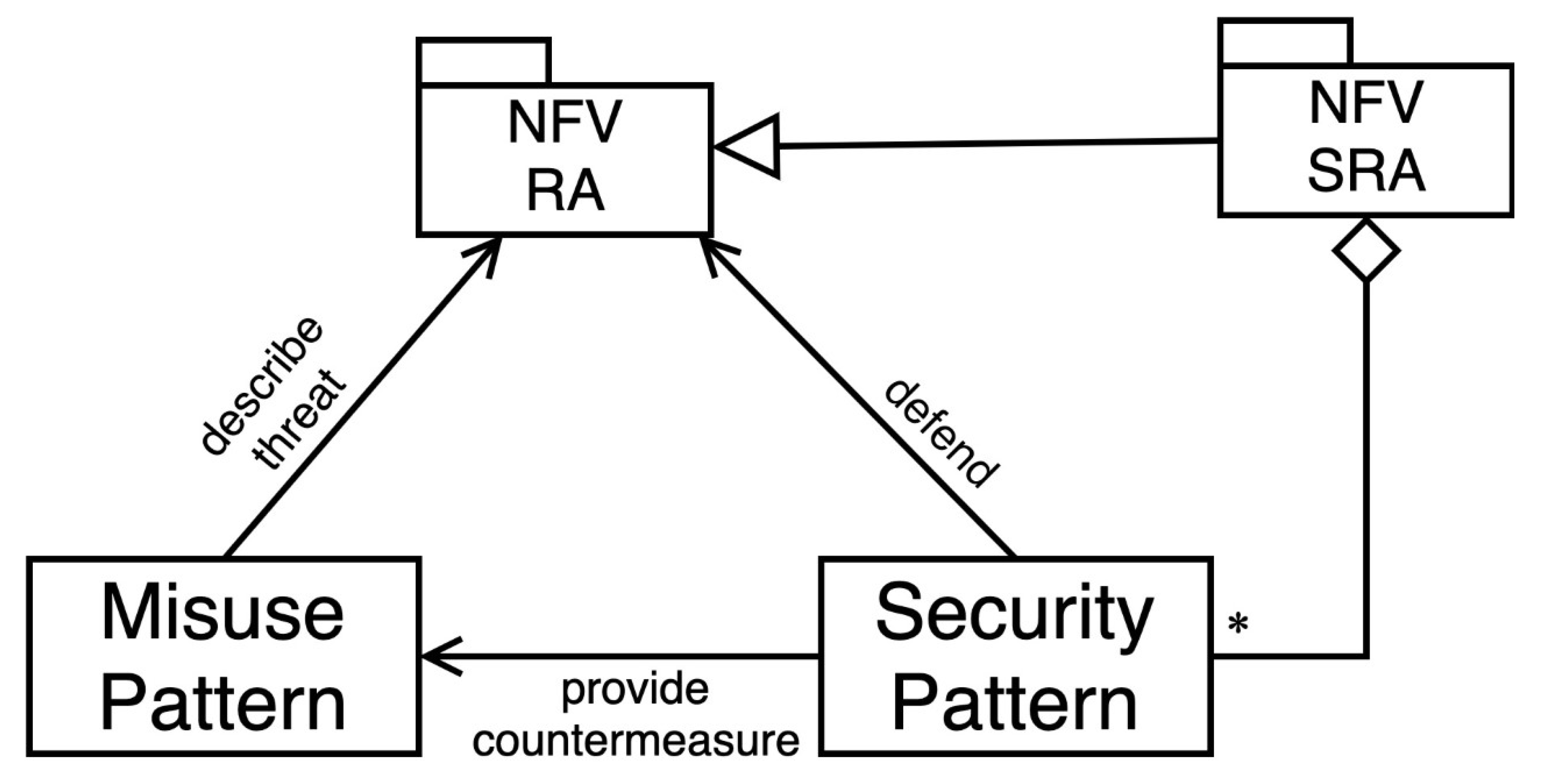
2.2. Patterns and Reference Architectures
3. A Security Reference Architecture for NFV
3.1. Finding Threats through Misuse Activities
3.2. A Misuse Pattern for Privilege-Escalation-Based Misuses
- VMs can send any type of hypercalls, whether they are legitimate or malicious, to the hypervisor.
- Hypercalls are low-level kernel requests for processing and resource access, and distinguishing genuine from malicious hypercalls can be challenging.
- Because the network service is hosted in a sharable environment, if one VNF is compromised, the other co-resident VNFs may be affected.
- The emergence of new attacks like return-oriented programming (ROP) attack, which allow attackers to change data in the hypervisor that modifies VM privilege levels.
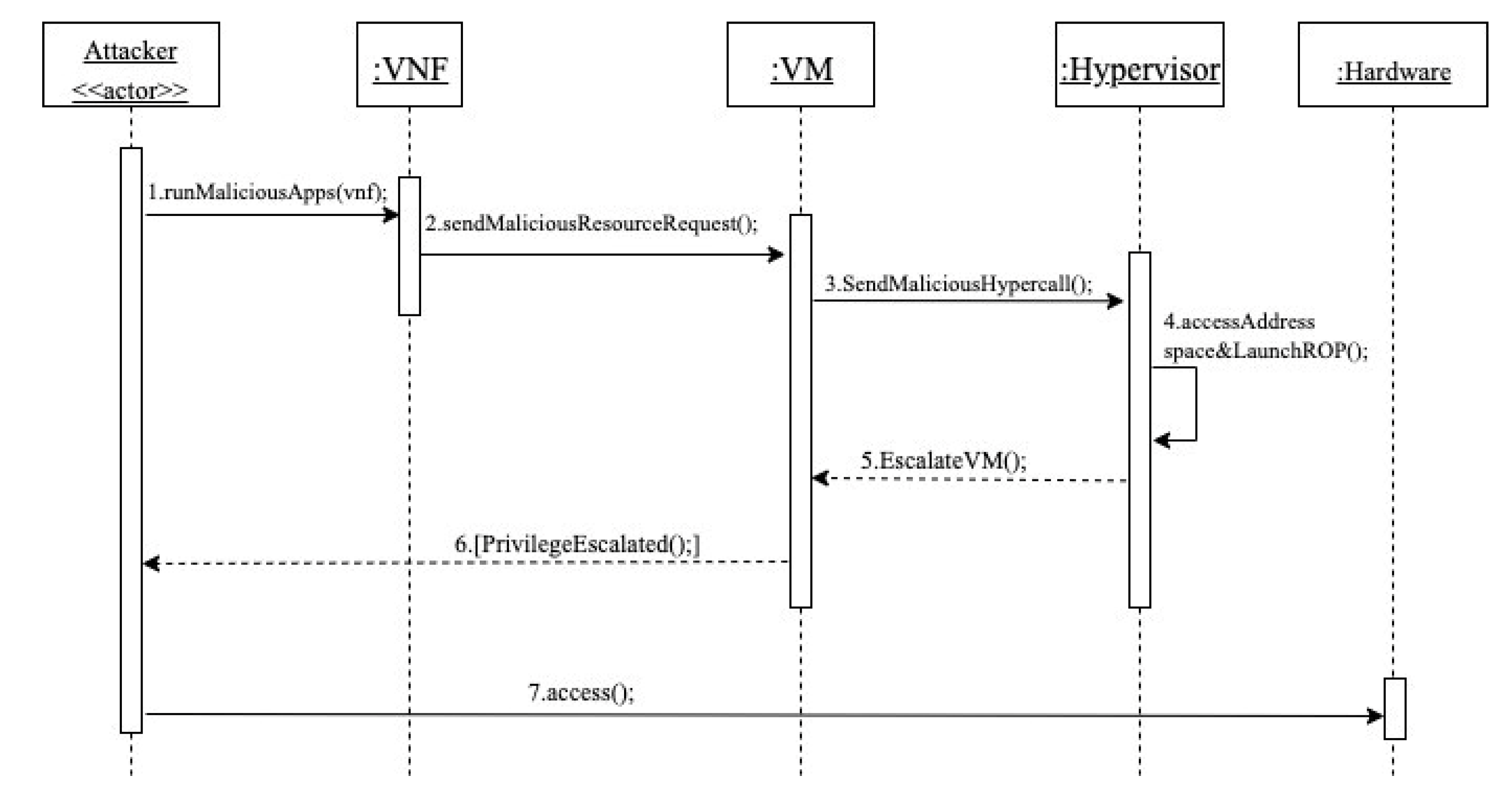
- The attacker first runs a malicious application in his VNF.
- Using the malicious application, a malicious resource request is sent as a hypercall.
- The malicious hypercall is forwarded to the hypervisor through the VM.
- The hypervisor receives the malicious hypercall request and fulfills it. In this case, the malicious application accesses the hypervisor address space and launches an ROP attack. The result of the ROP is escalating the privilege of the attacker’s VM by changing the is_privilege value from 0 to 1.
- The hypervisor escalates the VM privilege level.
- The attacker is notified that the VM has successfully been escalated.
- The attacker is now able to illegally access hardware resources.
- The attacker is able to compromise the system and its data because he is able to illegally access hardware resources.
- The attacker can completely disrupt the network services (DoS), preventing NFV consumers from using the service.
- Escalating the privilege of the attacker’s VM enables him to perform hypervisor operations such as directly accessing hardware resources and jeopardizing the system servers, creating, starting, stopping, migrating, and terminating victims’ VMs.
- The attacker may be a competitor in the network service market and aims to damage the reputation of the NFV provider as their service has been disrupted and will appear to have security issues.
- Using security schemes including hypercalls control and authenticated hypercalls that help to verify the authenticity of hypercalls [31].
3.3. A Misuse Pattern for Compromising VMs via Virtual Machine Escape
- The hypervisor is a software that includes various components, such as: drivers, schedulers, and hypercalls table. The security of hypervisor is difficult to maintain due to its design complexity [32].
- The hypervisor is one of the most critical components in the virtualization environment since it mediates the virtualized instances and hardware. As a result, a faulty hypervisor configuration can lead to a number of vulnerabilities that attackers can use to launch attacks, such as VM escape [33].
- VMs are interconnected with the host OS through the hypervisor; if there is a lack of isolation, attackers will be able to break into the host OS.
- The existence of many vulnerabilities that lead to VM escape proves that the virtualized environment is not robust enough even if these vulnerabilities have already been patched.
- Hypervisors send and receive hypercalls from VMs. These hypercalls are low-level requests for basic processing and resource access and it is difficult to differentiate between legitimate and malicious hypercalls; therefore, attackers can take advantage to send malicious requests to the hypervisor.
- The network service is hosted on a shared environment; if a VNF is compromised, that may affect the other co-resident VNFs.
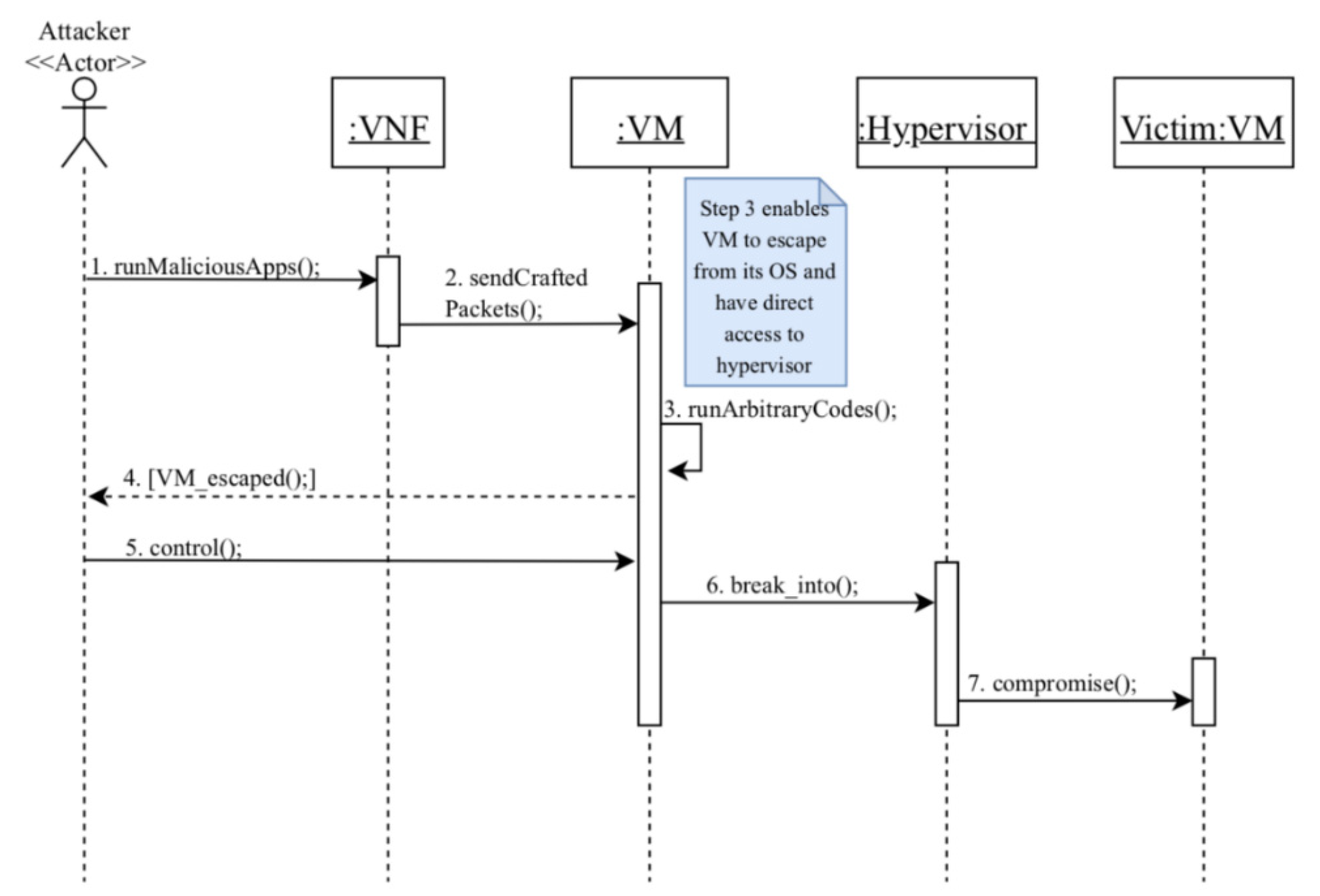
- The attacker first runs a malicious application in his VNF and compromises it by gaining access to the VM’s operating system.
- Using the compromised VNF, the attacker sends a crafted network packet to the VM in order to exploit a heap overflow.
- Arbitrary codes are executed on the hypervisor resulting in a VM escape. These codes enable the attacker to gain access to the host OS.
- The attacker is notified that the VM has successfully escaped from hypervisor control.
- As a result, the attacker can now control the VM.
- The attacker can read/write the hypervisor data through the controlled VM.
- Now, the attacker is able to compromise the victim’s VM using the controlled hypervisor.
3.4. A Misuse Pattern for Distributed Denial-of-Service Attack in NFV
- NFV is a recent technology, and its security infrastructure has not been tested enough in the wild, which raises the possibility that vulnerabilities may lead to several threats including denial of service.
- The urgency to adopt NFV services may have let NFVPs focus more on profits without hardening the security of their infrastructure including the DNS server configurations [35].
- The network service is hosted on a shared environment running on top of VMs; if a VNF is compromised due to misconfiguration, malware infection, or by exploiting a vulnerability in an old version of software running on it, a huge amount of traffic can be generated from the compromised VNF and sent to other co-resident VNFs running on the same hypervisor or even on different hypervisors, or to DNSs [36].
- The NFV environment provides network functions with a higher degree of flexibility and configuration possibilities than traditional architectures; therefore, there are more ways to misconfigure the network functions, which increases the attack surface and opens new avenues to compromise the system [37].
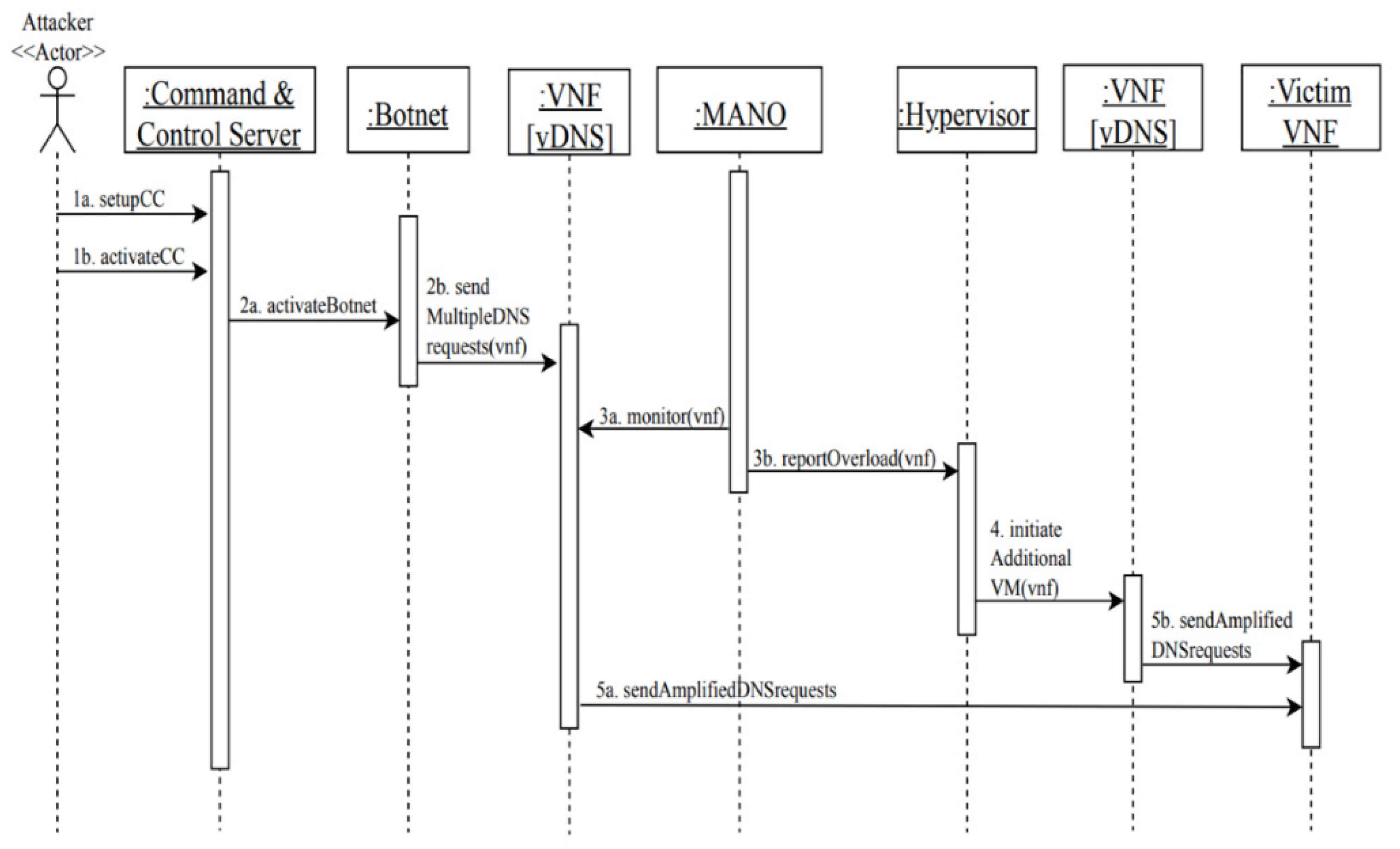
- The elasticity of the NFV environment enables network resources to rapidly scale up or down. In case of the DNS amplification DDoS attack, attackers can take advantage of this property to amplify the attack when multiple vDNSs will be created due to the traffic load and will produce a huge number of DNS replies to the victim. This scenario is possible in NFV environments, and we demonstrate it in later sections.
- Domain name systems, especially public DNSs, are designed to respond to any request where an attacker can turn a few DNS requests into much larger payloads. Attackers can leverage this amplification effect to launch a DDoS attack.
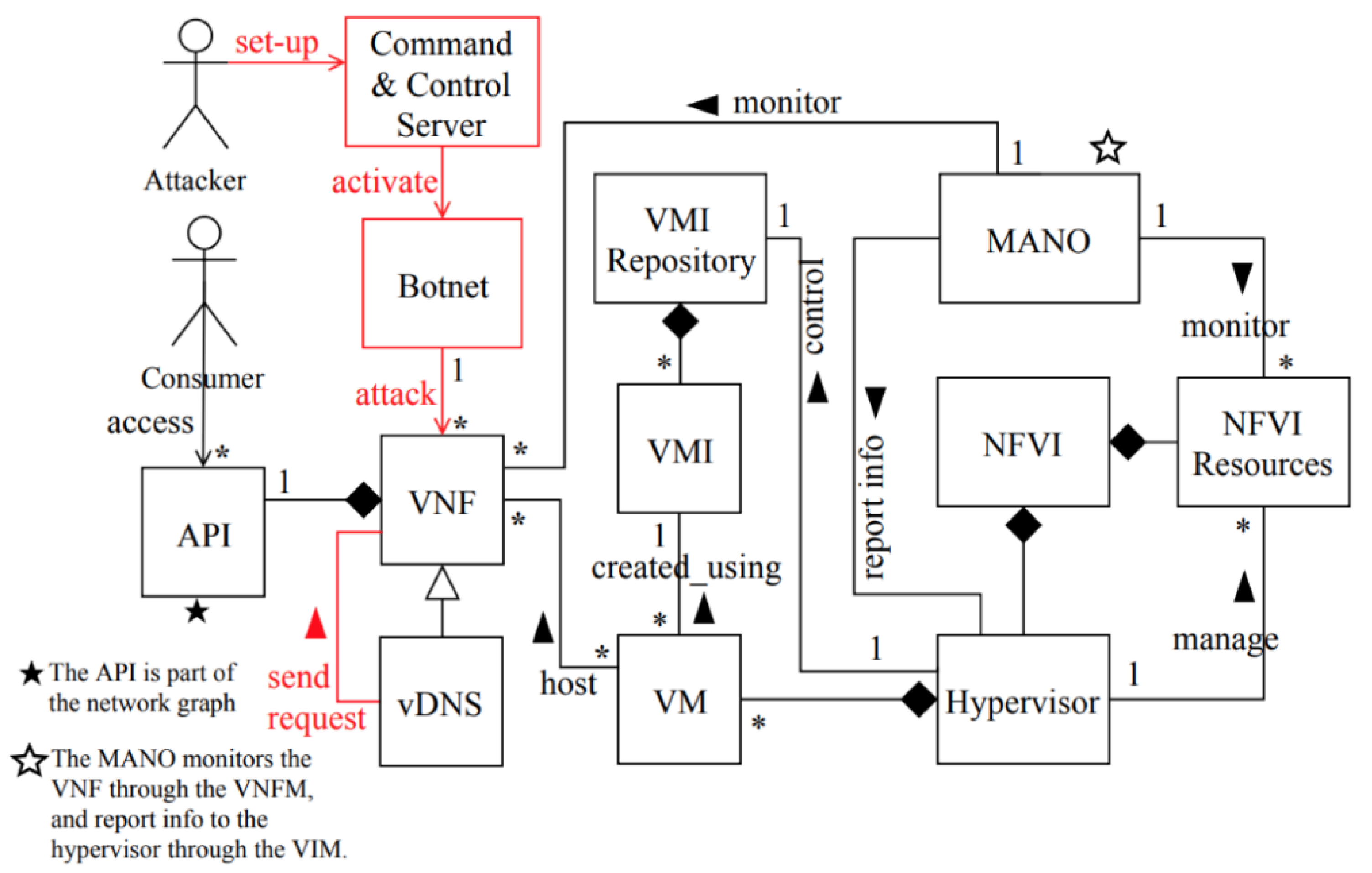
- The attacker first sets up the command-and-control server (CC) and activates it.
- Through the command-and-control server, the attacker activates the botnet and sends attack commands to the botnet to launch a high number of DNS requests to a vDNS.
- Meanwhile, the MANO is monitoring the VNF and realizes that the traffic load is higher than the normal threshold and reports it to the hypervisor.
- As a response to the high traffic load on the vDNS, the hypervisor initiates additional VMs to scale-up additional vDNSs to accommodate more requests.
- Accordingly, amplified DNS requests are recursively sent from the vDNSs to the victims’ web servers, which results in service unavailability or disruption.
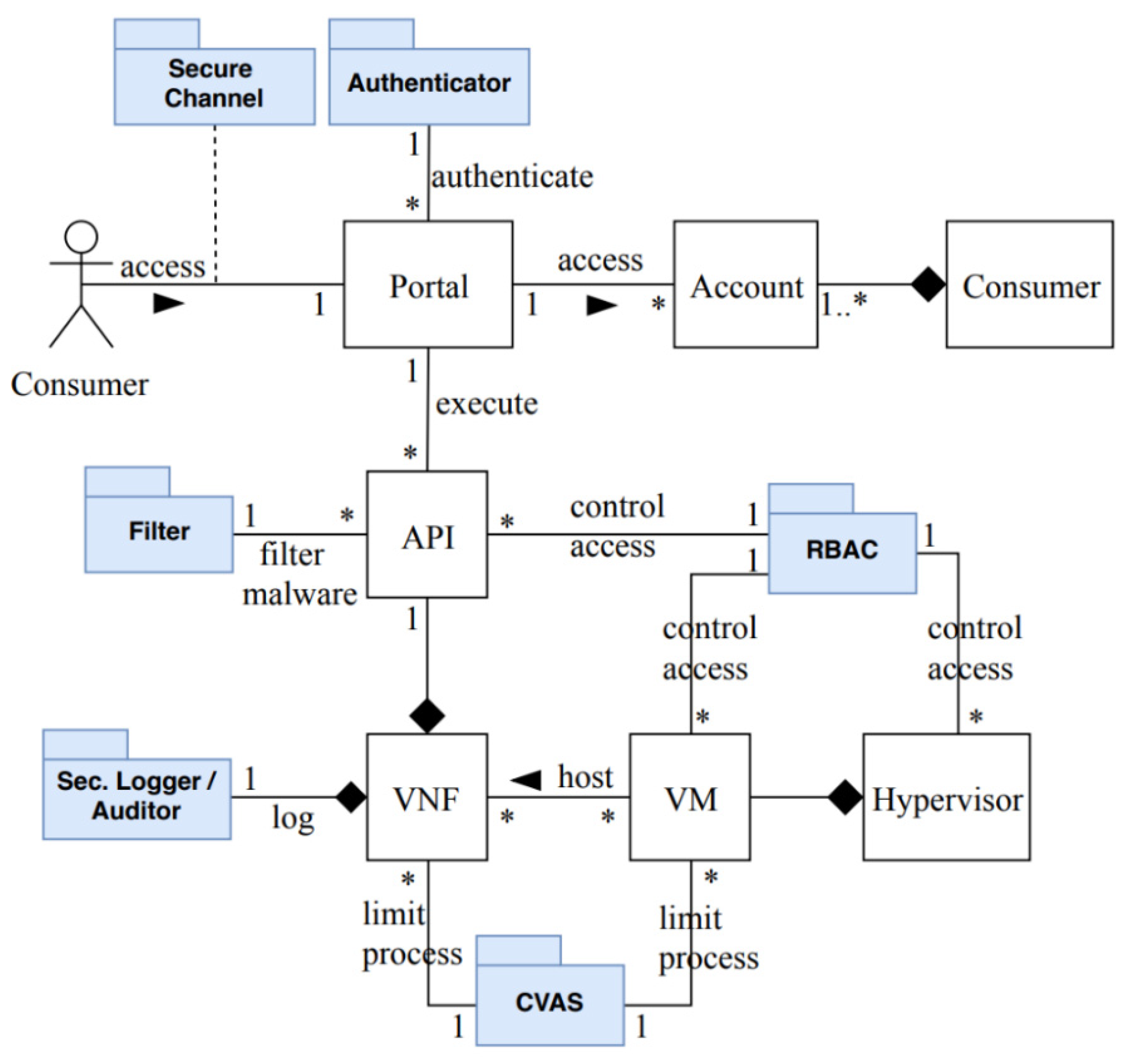
3.5. Securing the NFV Service
3.5.1. Security Evaluation of the Security Reference Architecture of NFV
4. Validation of SRAs
5. Related Work
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Chiosi, M.; Clarke, D.; Willis, P.; Reid, A.; Feger, J.; Bugenhagen, M.; Khan, W.; Cui, C.; Deng, H.; Chen, C. Network Functions Virtualisation (NFV): Network Operator Perspectives on Industry Progress. In Proceedings of the SDN & OpenFlow World Congress, Düsseldorf, Germany, 14–17 October 2013. [Google Scholar]
- ETSI. Network Functions Virtualisation (NFV); Infrastructure Overview; ETSI: Sophia Antipolis, France, 2015. [Google Scholar]
- ETSI. Network Functions Virtualisation (NFV); Architectural Framework; ETSI: Sophia Antipolis, France, 2014. [Google Scholar]
- Milenkoski, A.; Jaeger, B.; Raina, K.; Harris, M.; Chaudhry, S.; Chasiri, S.; David, V.; Liu, W. Security Position Paper: Network Function Virtualization; Cloud Security Alliance-Virtualization Working Group, 2016; Available online: https://cloudsecurityalliance.org/artifacts/security-position-paper-network-function-virtualization/ (accessed on 30 April 2022).
- Ahmad, I.; Kumar, T.; Liyanage, M.; Okwuibe, J.; Ylianttila, M.; Gurtov, A. Overview of 5G Security Challenges and Solutions. IEEE Commun. Stand. Mag. 2018, 2, 36–43. [Google Scholar] [CrossRef] [Green Version]
- Correa Chica, J.C.; Imbachi, J.C.; Botero Vega, J.F. Security in SDN: A Comprehensive Survey. J. Netw. Comput. Appl. 2020, 159, 102595. [Google Scholar] [CrossRef]
- Madi, T.; Alameddine, H.A.; Pourzandi, M.; Boukhtouta, A. NFV Security Survey in 5G Networks: A Three-Dimensional Threat Taxonomy. Comput. Netw. 2021, 197, 108288. [Google Scholar] [CrossRef]
- Fernandez, E.B.; Hamid, B. A pattern for network functions virtualization. In Proceedings of the 20th European Conference on Pattern Languages of Programs (EuroPLoP ’15), Kaufbeuren, Germany, 8–12 July 2015; pp. 1–9. [Google Scholar]
- Alwakeel, A.M.; Alnaim, A.K.; Fernandez, E.B. A Survey of Network Function Virtualization Security. In Proceedings of the IEEE SoutheastCon 2018, St. Petersburg, FL, USA, 19–22 April 2018. [Google Scholar]
- Fernandez, E.B. Security Patterns in Practice: Designing Secure Architectures Using Software Patterns; John Wiley & Sons: Hobokon, NJ, USA, 2013. [Google Scholar]
- Alnaim, A.K.; Alwakeel, A.M.; Fernandez, E.B. A Misuse Pattern for NFV based on Privilege Escalation. In Proceedings of the 8th Asian Conference on Pattern Languages of Programs, Irsee, Germany, 3–7 July 2019. [Google Scholar]
- Alnaim, A.K.; Alwakeel, A.M.; Fernandez, E.B. A Misuse Pattern for Compromising VMs via Virtual Machine Escape in NFV. In Proceedings of the 14th International Conference on Availability, Reliability and Security (ARES 2019), Canterbury, UK, 26–29 August 2019. [Google Scholar]
- Alnaim, A.K.; Alwakeel, A.M.; Fernandez, E.B. A Misuse Pattern for Distributed Denial-of-Service Attack in Network Function Virtualization. In Proceedings of the 26th PLoP’19, Ottawa, ON, Canada, 7–10 October 2019. [Google Scholar]
- Basilier, H.; Darula, M.; Wilke, J. Virtualizing network services—The telecom cloud. Ericsson Rev. 2014, 91, 1–9. [Google Scholar]
- SdxCentral. 2017 NFV Report Series Part I Foundations of NFV: NFV Infrastructure and VIM; SdxCentral: Santa Clara, CA, USA, 2017. [Google Scholar]
- ETSI. Network Functions Virtualisation (NFV); Infrastructure; Hypervisor Domain; ETSI: Sophia Antipolis, France, 2015. [Google Scholar]
- ETSI. Network Functions Virtualisation (NFV); Virtual Network Functions Architecture; ETSI: Sophia Antipolis, France, 2014. [Google Scholar]
- Buschmann, F.; Meunier, R.; Rohnert, H.; Sommerland, P.; Stal, M. Pattern-Oriented Software Architecture Volume 1: A System of Patterns; Wiley: New York, NY, USA, 1996. [Google Scholar]
- Fernandez, E.; Pelaez, J.; Larrondo-Petrie, M. Attack Patterns: A New Forensic and Design Tool. In Advances in Digital Forensics III; Springer: New York, NY, USA, 2007; pp. 345–357. [Google Scholar]
- Avgeriou, P. Describing, Instantiating and Evaluating a Reference Architecture: A Case Study. Default J. 2003, 342, 1–24. [Google Scholar]
- Braz, F.A.; Fernandez, E.B.; VanHilst, M. Eliciting security requirements through misuse activities. In Proceedings of the 2008 19th International Workshop on Database and Expert Systems Applications, Turin, Italy, 1–5 September 2008; pp. 328–333. [Google Scholar]
- NIST National Vulnerability Database—CVE-2011-1583. Available online: https://nvd.nist.gov/vuln/detail/CVE-2011-1583#match-1664916 (accessed on 3 October 2021).
- Ding, B.; Wu, Y.; He, Y.; Tian, S.; Guan, B.; Wu, G. Return-Oriented Programming Attack on the Xen Hypervisor. In Proceedings of the 2012 Seventh International Conference on Availability, Reliability and Security, Prague, Czech Republic, 20–24 August 2012; pp. 479–484. [Google Scholar]
- Reynaud, F.; Aguessy, F.-X.; Bettan, O.; Bouet, M.; Conan, V. Attacks against Network Functions Virtualization and Software-Defined Networking: State-of-the-art. In Proceedings of the 2016 IEEE NetSoft Conference and Workshops (NetSoft), Seoul, Korea, 6–10 June 2016; pp. 471–476. [Google Scholar]
- Xen Project. Xen Security Advisory. 2011. Available online: http://old-list-archives.xenproject.org/archives/html/xen-devel/2011-05/msg00483.html (accessed on 15 November 2021).
- Onarlioglu, K.; Bilge, L.; Lanzi, A.; Balzarotti, D.; Kirda, E. G-Free: Defeating Return-Oriented Programming through Gadget-Less Binaries. In Proceedings of the 26th Annual Computer Security Applications Conference on (ACSAC 2010), Austin, TX, USA, 6–10 December 2010; p. 49. [Google Scholar]
- Jiang, J.; Jia, X.; Feng, D.; Zhang, S.; Liu, P. HyperCrop: A Hypervisor-Based Countermeasure for Return Oriented Programming; Springer: Berlin/Heidelberg, Germany, 2011; pp. 360–373. [Google Scholar]
- Ding, B.; He, Y.; Wu, Y.; Lin, Y. HyperVerify: A VM-assisted Architecture for Monitoring Hypervisor Non-Control Data. In Proceedings of the 2013 IEEE Seventh International Conference on Software Security and Reliability Companion, Gaithersburg, MD, USA, 18–20 June 2013; pp. 26–34. [Google Scholar]
- Cheng, Y.; Zhou, Z.; Yu, M.; Ding, X.; Deng, R.H. ROPecker: A Generic and Practical Approach for Defending against ROP Attacks. In Proceedings of the 2014 Network and Distributed System Security Symposium, San Diego, CA, USA, 23–26 February 2014. [Google Scholar]
- Shuo, T.; Yeping, H.; Baozeng, D. Prevent Kernel Return-Oriented Programming Attacks Using Hardware Virtualization; Springer: Berlin/Heidelberg, Germany, 2012; pp. 289–300. [Google Scholar]
- Hoang, C.; Hoang, C.; Le, H. Protecting Xen hypercalls Intrusion Detection/Prevention in a Virtualization Environment; The University of British Colombia: Vancouver, BC, Canada, 2009. [Google Scholar]
- Jansen, W.A. Cloud Hooks: Security and Privacy Issues in Cloud Computing. In Proceedings of the 2011 44th Hawaii International Conference on System Sciences, Kauai, HI, USA, 4–7 January 2011; pp. 1–10. [Google Scholar]
- Ali, M.; Khan, S.U.; Vasilakos, A.V. Security in cloud computing: Opportunities and challenges. Inf. Sci. 2015, 305, 357–383. [Google Scholar] [CrossRef]
- Lal, S.; Taleb, T.; Dutta, A. NFV: Security Threats and Best Practices. IEEE Commun. Mag. 2017, 55, 211–217. [Google Scholar] [CrossRef]
- SecurityTrails. 8 Tips to Prevent DNS Attacks. Available online: https://securitytrails.com/blog/8-tips-to-prevent-dns-attacks (accessed on 16 September 2021).
- Huang, D.; Chowdhary, A.; Pisharody, S. Software-Defined Networking and Security: From Theory to Practice; CRC Press: Boca Rotan, FL, USA, 2018. [Google Scholar]
- Pillaipakam, D. Building a Secure DNS Architecture for NFV|Light Reading. Available online: https://www.lightreading.com/nfv/nfv-strategies/building-a-secure-dns-architecture-for-nfv/a/d-id/720711 (accessed on 12 December 2021).
- Syed, M.H.; Fernandez, E.B.; Moreno, J. A misuse Pattern for DDoS in the IoT. In Proceedings of the 23rd European Conference on Pattern Languages of Programs (EuroPLoP ’18), Irsee, Germany, 4–8 July 2018; pp. 1–5. [Google Scholar]
- Fernandez, E.B.; Monge, R.; Hashizume, K. Building a security reference architecture for cloud systems. Requir. Eng. 2016, 21, 225–249. [Google Scholar] [CrossRef]
- ETSI. Network Functions Virtualisation (NFV) Release 3; Security; Security Management and Monitoring Specification; ETSI: Sophia Antipolis, France, 2017. [Google Scholar]
- ETSI. Network Functions Virtualisation (NFV) Release 3; Security; System Architecture Specification for Execution of Sensitive NFV Components; ETSI: Sophia Antipolis, France, 2017. [Google Scholar]
- ETSI. Network Functions Virtualisation (NFV); NFV Security; Cataloguing Security Features in Management Software; ETSI: Sophia Antipolis, France, 2015. [Google Scholar]
- OpenStack. OpenStack Security Guide. Available online: https://docs.openstack.org/security-guide/ (accessed on 9 May 2021).
- RedHat. Red Hat Solution for Network Functions Virtualization; RedHat: Raleigh, NC, USA, 2022. [Google Scholar]
- Alwakeel, A.M.; Alnaim, A.K.; Fernandez, E.B. A Reference Architecture for Network Function Virtualization. Ph.D. Thesis, Florida Atlantic University, Boca Raton, FL, USA, 2022. [Google Scholar]
- Pattaranantakul, M.; He, R.; Song, Q.; Zhang, Z.; Meddahi, A. Nfv security survey: From use case driven threat analysis to state-of-the-art countermeasures. IEEE Commun. Surv. Tutor. 2018, 20, 3330–3368. [Google Scholar] [CrossRef]
- Farris, I.; Taleb, T.; Khettab, Y.; Song, J. A survey on emerging SDN and NFV security mechanisms for IoT systems. IEEE Commun. Surv. Tutor. 2019, 21, 812–837. [Google Scholar]
- Wu, X.; Hou, K.; Leng, X.; Li, X.; Yu, Y.; Wu, B.; Chen, Y. State of the art and research challenges in the security technologies of network function virtualization. IEEE Internet Comput. 2020, 24, 25–35. [Google Scholar] [CrossRef]
- Basile, C.; Valenza, F.; Lioy, A.; Lopez, D.R.; Perales, A.P. Adding Support for Automatic Enforcement of Security Policies in NFV Networks. IEEE/ACM Trans. Netw. 2019, 27, 707–720. [Google Scholar] [CrossRef] [Green Version]
- Alhebaishi, N.; Wang, L.; Jajodia, S. Modeling and mitigating security threats in network functions virtualization (NFV). In Proceedings of the IFIP Annual Conference on Data and Applications Security and Privacy, Calgary, AB, Canada, 25–26 June 2020; Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Cham, Switzerland, 2020; pp. 3–23. [Google Scholar]
- Shameli-Sendi, A.; Jarraya, Y.; Pourzandi, M.; Cheriet, M. Efficient Provisioning of Security Service Function Chaining Using Network Security Defense Patterns. IEEE Trans. Serv. Comput. 2016, 12, 534–549. [Google Scholar] [CrossRef]
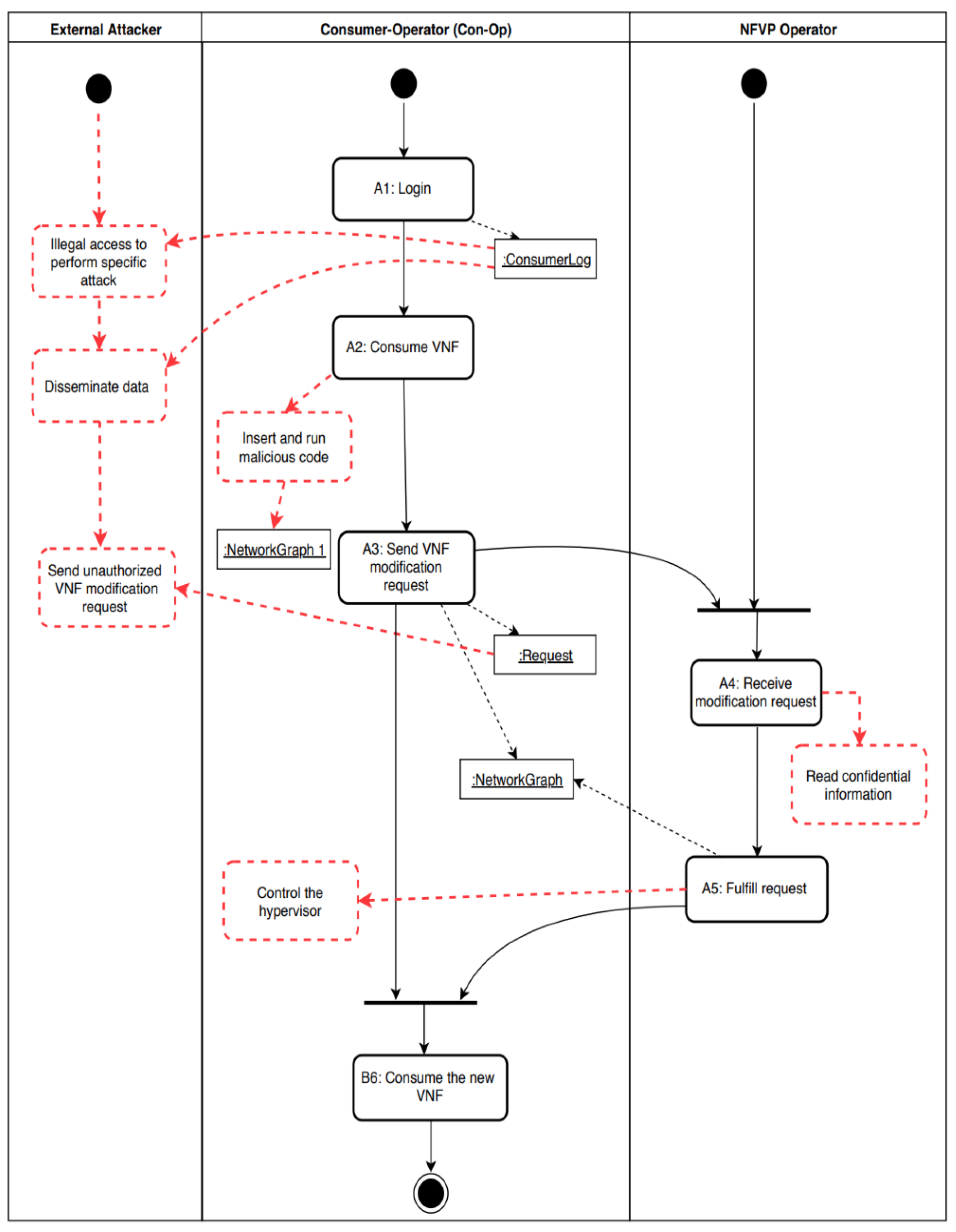
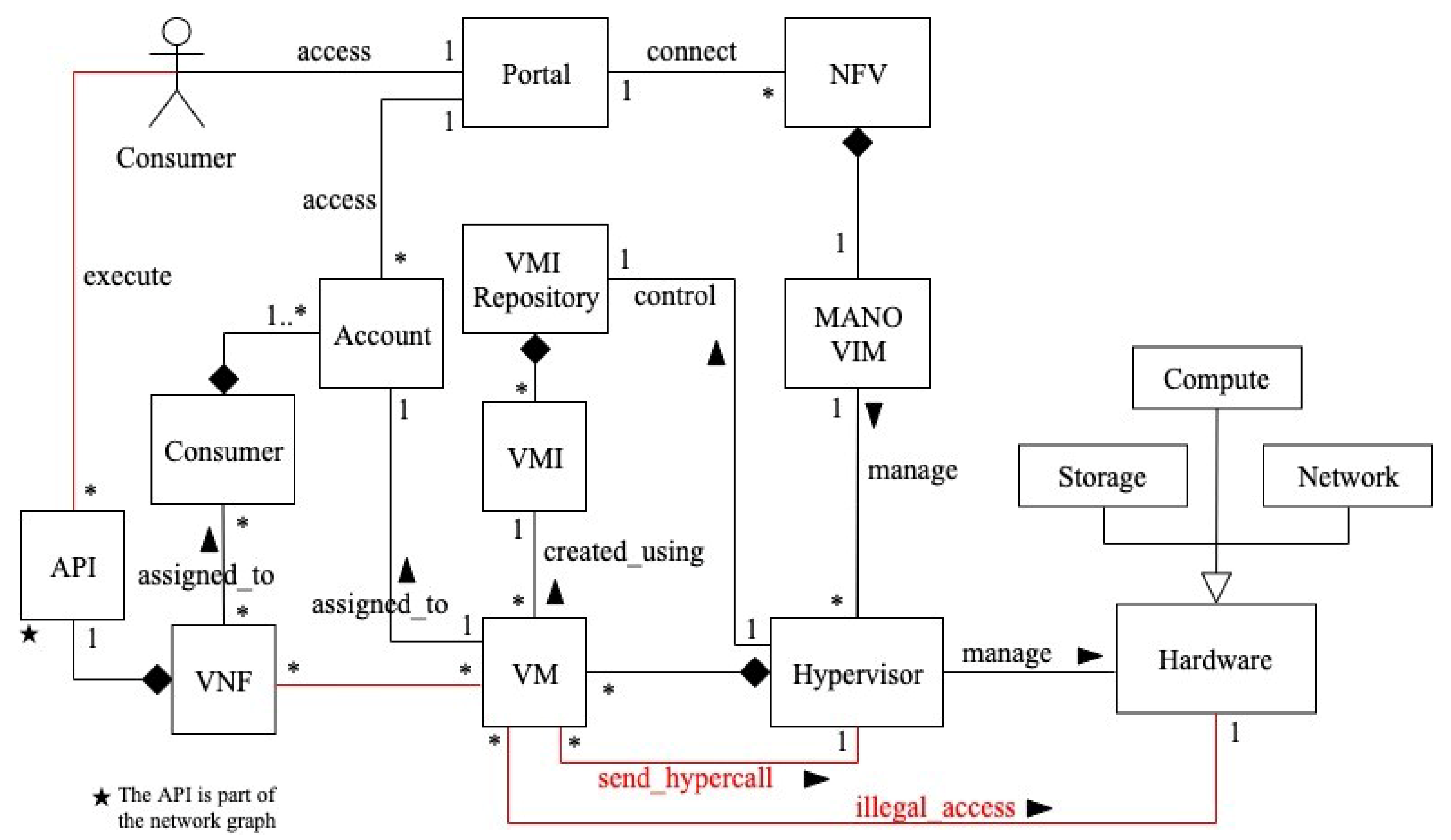
| Actor | Action | Threat Number | Sec. Attr. CO/IN/AV/AC | Source AIn/UIn/Out | Description |
|---|---|---|---|---|---|
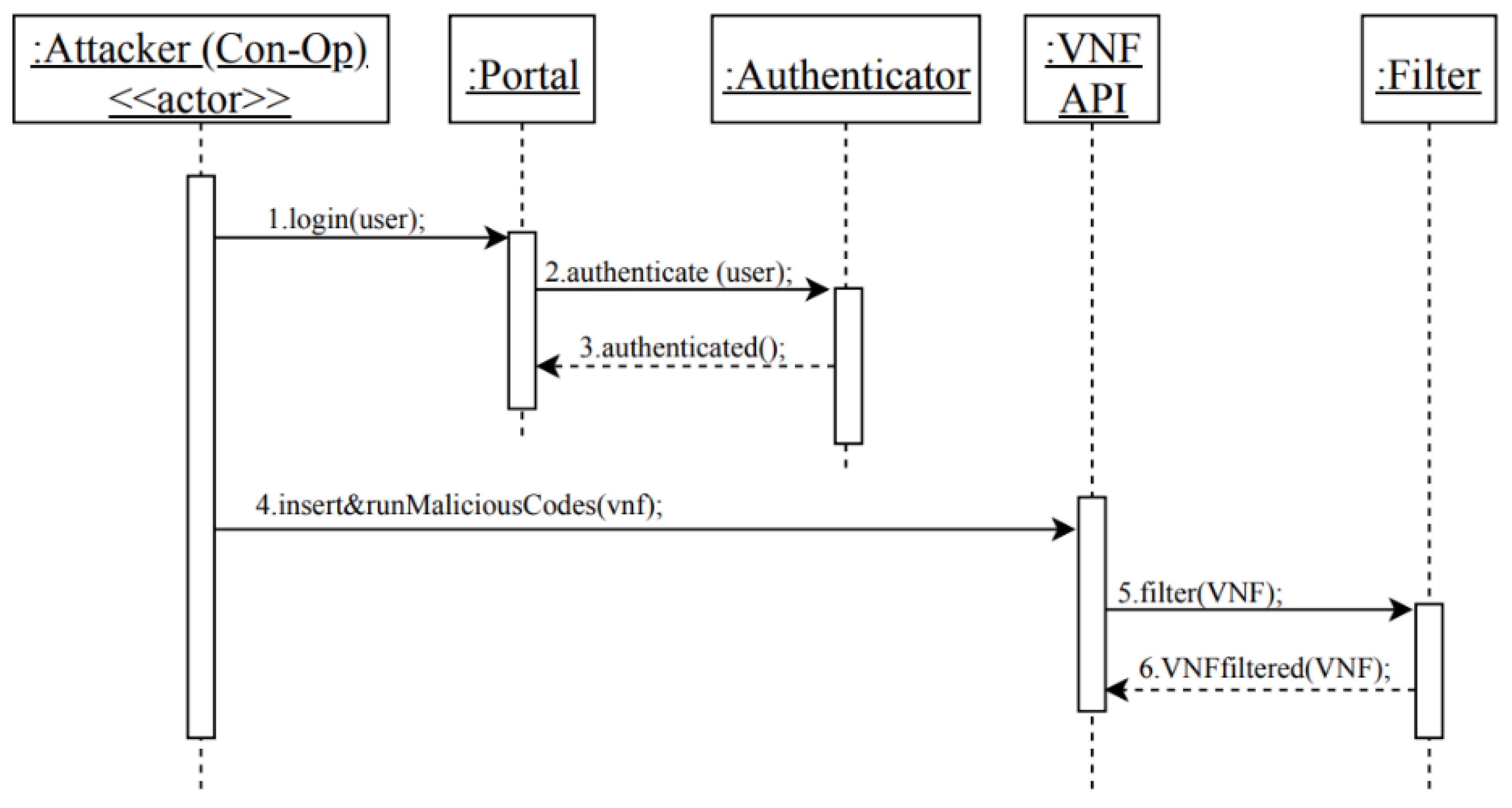
| Con-Op | A1. Login | T1 | CO | Out | An external attacker illegally accesses the system to perform specific attacks, such as modify the network |
| T2 | CO | Out | An external attacker disseminates Con-Op’s data. | ||
| A2. Consume VNF | T3 | IN | AIn | The Con-Op inserts and runs malicious codes within the VNF. | |
| A3. Send VNF modification request | T4 | IN | Out | An external attacker modifies the Con-Op requests while in transit. | |
| T5 | AV | AIn/Out | The Con-Op overwhelms the system with requests to make the service unavailable (DoS). | ||
| NFVP Operator | A4. Receive modification request | T6 | CO | AIn/UIn | The NFVP Operator collects confidential information. |
| A5. Fulfill request | T7 | CO/IN | AIn | The Con-Op compromises the hypervisor in unauthorized manner, which results to accomplish the attacker’s malicious goals, such as controlling the hypervisor, modify VM privilege, or VM escape. |
| Threat Number | Description | Defense Mechanism |
|---|---|---|
| T1 | An external attacker illegally accesses the system to perform specific attacks, such as modify the network. | Authenticator |
| T2 | An external attacker disseminates Con-Op’s data. | Security logger/auditor |
| T3 | The Con-Op inserts and runs malicious codes within the VNF. | Filter module |
| T4 | An external attacker modifies the Con-Op requests while in transit. | Secure channel |
| T5 | The Con-Op overwhelms the system with requests to make the service unavailable (DoS). | CVAS, traffic filtering and detection mechanisms |
| T6 | The NFVP operator collects confidential information. | Security logger/auditor |
| T7 | The Con-Op compromises the hypervisor in unauthorized manner, which accomplishes the attacker’s malicious goals, such as controlling the hypervisor, modifying VM privilege, or VM escape. | Patching the hypervisor |
| Components | VNF | VM | Hypervisor | API | VIM | Authenticator | Filter | Sec. Log/Auditor | RBAC | CVAS | Sec. Channel | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Frameworks | ||||||||||||
| The NFV SRA | ||||||||||||
| NFV SRA | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| Industry NFV Frameworks Used to Compare with our SRA | ||||||||||||
| ETSI Security Framework | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| CSA Security Framework | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| Red Hat Platform | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alnaim, A.K.; Alwakeel, A.M.; Fernandez, E.B. Towards a Security Reference Architecture for NFV. Sensors 2022, 22, 3750. https://doi.org/10.3390/s22103750
Alnaim AK, Alwakeel AM, Fernandez EB. Towards a Security Reference Architecture for NFV. Sensors. 2022; 22(10):3750. https://doi.org/10.3390/s22103750
Chicago/Turabian StyleAlnaim, Abdulrahman Khalid, Ahmed Mahmoud Alwakeel, and Eduardo B. Fernandez. 2022. "Towards a Security Reference Architecture for NFV" Sensors 22, no. 10: 3750. https://doi.org/10.3390/s22103750
APA StyleAlnaim, A. K., Alwakeel, A. M., & Fernandez, E. B. (2022). Towards a Security Reference Architecture for NFV. Sensors, 22(10), 3750. https://doi.org/10.3390/s22103750






