P4G2Go: A Privacy-Preserving Scheme for Roaming Energy Consumers of the Smart Grid-to-Go
Abstract
1. Introduction
- Define the G2Go concept and present its functional, security and privacy requirements. To the best of our knowledge, this is the first time a scenario for roaming energy consumers is being proposed by the literature.
- Propose P4G2Go, a privacy-preserving scheme designed for the G2Go concept based on well-established security and privacy-preserving technologies.
- Assess P4G2Go’s performance and qualitatively reason about its security and privacy properties. For this purpose, we have implemented the main components of P4G2Go including the Idemix anonymous credential system.
2. Related Work
3. The G2Go Concept
3.1. Definition and Participants
3.2. Security Model
- (1)
- Smart meters convey consumption readings and they are trustful. However, a malicious software injected after the proper deployment of the smart meter may try to obtain the readings or convey false information to aggregators.
- (2)
- Aggregators follow the honest-but-curious model, which is what most related works on privacy-preserving aggregation depend on. According to this model, aggregators securely send valid and accurate energy consumption data without discarding or tampering the transmitted messages, but they may try to deduce information from the received messages.
- (3)
- UR also follows the honest-but-curious model in the sense that they properly execute the involved protocols, but they are curious and may try to read the data received from other nodes in order to gain information. We assume that different UR may collude and combine legitimately acquired information in order to link the activities of the Consumer.
- (4)
- The UH follows strict protocol procedures and is trusted by both UR and the Consumer.
3.3. Security and Privacy Requirements
3.3.1. Security Requirements
- (S1)
- Data confidentiality: Consumption data must be available only to the responsible Utility and the Consumer. No entities may collude to gain information in order to track a Consumer’s activity.
- (S2)
- Data integrity and authenticity: All data exchanged between the participating entities should be protected against alteration and replication. Each entity should be in a position to verify the source of the data received.
- (S3)
- Non-repudiation: No Consumer should be able to deny their actions.
- (S4)
- Authorization and access control: Access to the roaming service is granted only to legitimate Consumers registered at the Utilities that participate in the scenario.
- (S5)
- Accountability: A Consumer should be held accountable for their actions.
- (S6)
- Physical protection: Smart grid components should incorporate protection mechanisms to prevent being tampered with by adversaries with physical access.
3.3.2. Privacy Requirements
- (P1)
- Identity privacy: Consumer’s true identity should only be known to their UH. UR authenticates Consumers only by their pseudonyms, and it should not be possible for adversaries to identify a Consumer by monitoring the grid.
- (P2)
- Location privacy: There should be no way for colluding UR entities to track the trajectory of Consumers.
- (P3)
- Unlinkability: Guarantees that different charging sessions from the same Consumer cannot be linked to each other.
- (P4)
- Minimum data disclosure: Guarantees that suppliers should access Consumer’s data limited to the minimum required to bill them.
- (P5)
- Privacy-preserving data aggregation: Aggregation of consumption data should happen in a secure and privacy-preserving manner that protects Consumer’s individual consumptions from being disclosed or modified by unauthorized parties, and prohibits the linkage of a property with a specific energy usage. Also, the end result of the consumption data aggregation should be computed correctly in order to charge the Consumer.
4. P4G2Go Technologies and Architectural Overview
4.1. P4G2Go Technologies
4.1.1. Idemix
4.1.2. Trusted Execution Environment (TEE)
4.1.3. MASKER
4.1.4. Fast Identity Online 2 (FIDO2)
4.2. P4G2Go Architecture
5. P4G2Go Operations
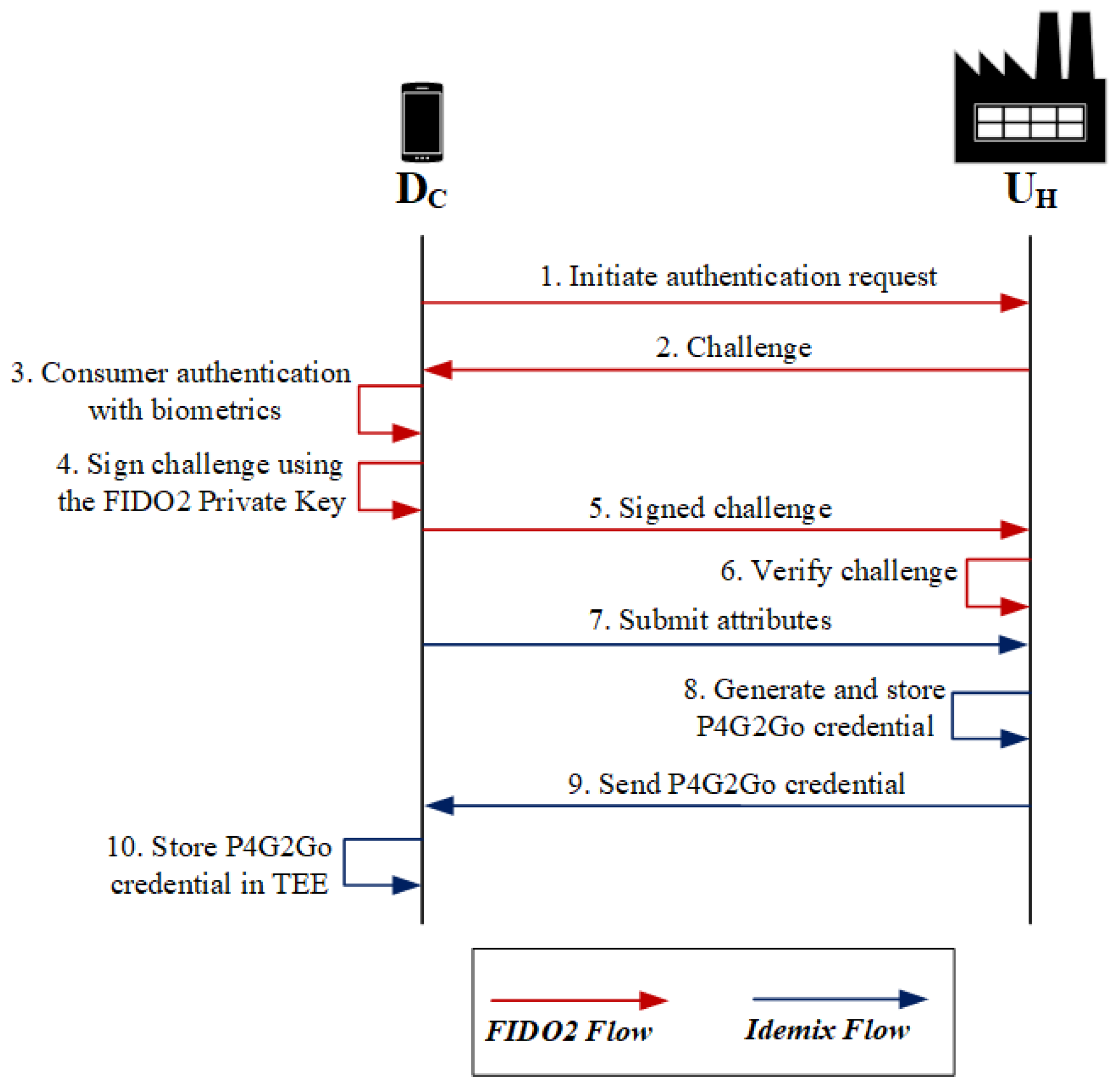
5.1. Credential Issuance
5.2. Credential Verification and Privacy-Preserving Data Aggragation
5.3. Billing and Payment
6. Performance Evaluation
7. Security and Privacy Analysis
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Fang, X.; Misra, S.; Xue, G.; Yang, D. Smart grid—The new and improved power grid: A survey. IEEE Commun. Surv. Tutor. 2011, 14, 944–980. [Google Scholar] [CrossRef]
- Vacation Rentals. Homes, Experiences & Places—Airbnb. Available online: https://www.airbnb.com/ (accessed on 27 February 2021).
- Are Hosts Allowed to ‘Spring’ Utility Bills on Guests? Available online: https://airhostsforum.com/t/are-hosts-allowed-to-spring-utility-bills-on-guests/122 (accessed on 27 February 2021).
- Electricity Payment on Consumption. Available online: https://community.withairbnb.com/t5/Hosting/electricity-payment-on-consumption/td-p/8931 (accessed on 27 February 2021).
- As a Host, How Does One Go about Charging Extra for Water and Electricity When It Is Applicable? Available online: https://community.withairbnb.com/t5/Help/Extra-charges-for-water-and-electricity/td-p/72432 (accessed on 27 February 2021).
- Farao, A.; Rubio, J.E.; Alcaraz, C.; Ntantogian, C.; Xenakis, C.; Lopez, J. SealedGRID: A Secure Interconnection of Technologies for Smart Grid Applications. In Critical Information Infrastructures Security. CRITIS 2019; Nadjm-Tehrani, S., Ed.; Lecture Notes in Computer Science; Springer: Cham, Germany, 2020; Volume 11777. [Google Scholar]
- MBO Partners. COVID-19 and the Rise of the Digital Nomad; White Report; MBO Partners: Herndon, VA, USA, 2020. [Google Scholar]
- Laurent, L. WFH in Greece or Barbados? The Fight for Covid’s Digital Nomads. Bloomberg.com, Bloomberg, 16 November 2020. Available online: www.bloomberg.com/opinion/articles/2020-11-16/greece-or-barbados-the-tax-fight-for-covid-s-wfh-nomads-begins (accessed on 27 February 2021).
- Hermann, I.; Paris, C.M. Digital Nomadism: The nexus of remote working and travel mobility. Inf. Technol. Tour. 2020, 22, 329–334. [Google Scholar] [CrossRef]
- Erkin, Z.; Troncoso-Pastoriza, J.R.; Lagendijk, R.L.; Pérez-González, F. Privacy-preserving data aggregation in smart metering systems: An overview. IEEE Signal Process. Mag. 2013, 30, 75–86. [Google Scholar] [CrossRef]
- Karopoulos, G.; Ntantogian, C.; Xenakis, C. MASKER: Masking for privacy-preserving aggregation in the smart grid ecosystem. Comput. Secur. 2018, 73, 307–325. [Google Scholar] [CrossRef]
- Gabay, D.; Akkaya, K.; Cebe, M. Privacy-preserving authentication scheme for connected electric vehicles using blockchain and zero knowledge proofs. IEEE Trans. Veh. Technol. 2020, 69, 5760–5772. [Google Scholar] [CrossRef]
- Camenisch, J.; Lysyanskaya, A. An efficient system for non-transferable anonymous credentials with optional anonymity revocation. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Innsbruck, Austria, 6–10 May 2001; pp. 93–118. [Google Scholar]
- Veseli, F.; Serna, J. Evaluation of privacy-ABC technologies-a study on the computational efficiency. In Proceedings of the IFIP International Conference on Trust Management, Darmstadt, Germany, 18–22 July 2016; pp. 63–78. [Google Scholar]
- FIDO2: WebAuthn & CTAP, Moving the World Beyond Passwords. Available online: https://fidoalliance.org/fido2 (accessed on 27 February 2021).
- Han, W.; Xiao, Y. Privacy preservation for V2G networks in smart grid: A survey. Comput. Commun. 2016, 91, 17–28. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L.A.; Janicke, H.; Jiang, J.; Shu, L. A systematic review of data protection and privacy preservation schemes for smart grid communications. Sustain. Cities Soc. 2018, 38, 806–835. [Google Scholar] [CrossRef]
- Kim, M.; Park, K.; Yu, S.; Lee, J.; Park, Y.; Lee, S.W.; Chung, B. A secure charging system for electric vehicles based on blockchain. Sensors 2019, 19, 3028. [Google Scholar] [CrossRef]
- Zhang, Y.; Zou, J.; Guo, R. Efficient privacy-preserving authentication for V2G networks. Peer Peer Netw. Appl. 2020, 1–13. [Google Scholar] [CrossRef]
- Bansal, G.; Naren, N.; Chamola, V.; Sikdar, B.; Kumar, N.; Guizani, M. Lightweight mutual authentication protocol for V2G using physical unclonable function. IEEE Trans. Veh. Technol. 2020, 69, 7234–7246. [Google Scholar] [CrossRef]
- Su, Y.; Shen, G.; Zhang, M. A novel privacy-preserving authentication scheme for V2G networks. IEEE Syst. J. 2019, 14, 1963–1971. [Google Scholar] [CrossRef]
- Kaveh, M.; Martín, D.; Mosavi, M.R. A lightweight authentication scheme for V2G communications: A PUF-based approach ensuring Cyber/Physical security and Identity/Location privacy. Electronics 2020, 9, 1479. [Google Scholar] [CrossRef]
- Au, M.H.; Liu, J.K.; Fang, J.; Jiang, Z.L.; Susilo, W.; Zhou, J. A New Payment System for Enhancing Location Privacy of Electric Vehicles. IEEE Trans. Veh. Technol. 2014, 63, 3–18. [Google Scholar] [CrossRef]
- Schwerdt, R.; Nagel, M.; Fetzer, V.; Gräf, T.; Rupp, A. P6V2G: A privacy-preserving V2G scheme for two-way payments and reputation. Energy Inform. 2019, 2, 32. [Google Scholar] [CrossRef]
- Höfer, C.; Petit, J.; Schmidt, R.; Kargl, F. POPCORN: Privacy-preserving charging for eMobility. In Proceedings of the 2013 ACM Workshop on Security, Privacy and Dependability for CyberVehicles, Berlin, Germany, 4 November 2013; pp. 37–48. [Google Scholar]
- Mustafa, M.A.; Zhang, N.; Kalogridis, G.; Fan, Z. Roaming electric vehicle charging and billing: An anonymous multi-user protocol. In Proceedings of the 2014 IEEE International Conference on Smart Grid Communications (SmartGridComm), Venice, Italy, 3–6 November 2014; pp. 939–945. [Google Scholar]
- Shuaib, K.; Barka, E.; Abdella, J.A.; Sallabi, F. Secure charging and payment protocol (SCPP) for roaming plug-in electric vehicles. In Proceedings of the 2017 4th International Conference on Control, Decision and Information Technologies (CoDIT), Barcelona, Spain, 5–7 April 2017; pp. 173–178. [Google Scholar]
- Zelle, D.; Springer, M.; Zhdanova, M.; Krauß, C. Anonymous charging and billing of electric vehicles. In Proceedings of the 13th International Conference on Availability, Reliability and Security (ARES 2018), Hamburg, Germany, 27–30 August 2018; pp. 1–10. [Google Scholar]
- Saxena, N.; Grijalva, S.; Chukwuka, V.; Vasilakos, A.V. Network security and privacy challenges in smart vehi-cle-to-grid. IEEE Wirel. Commun. 2017, 24, 88–98. [Google Scholar] [CrossRef]
- Fazouane, M.; Kopp, H.; van der Heijden, R.W.; Le Métayer, D.; Kargl, F. Formal verification of privacy properties in electric vehicle charging. In Proceedings of the International Symposium on Engineering Secure Software and Systems (ESSoS 2015), Milan, Italy, 4–6 March 2015; pp. 17–33. [Google Scholar]
- Shuaib, K.; Barka, E.; Abdella, J.A.; Sallabi, F.; Abdel-Hafez, M.; Al-Fuqaha, A. Secure plug-in electric vehicle (PEV) charging in a smart grid network. Energies 2017, 10, 1024. [Google Scholar] [CrossRef]
- Saxena, N.; Choi, B.J. Authentication scheme for flexible charging and discharging of mobile vehicles in the V2G net-works. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1438–1452. [Google Scholar] [CrossRef]
- Tao, M.; Ota, K.; Dong, M.; Qian, Z. AccessAuth: Capacity-aware security access authentication in federat-ed-IoT-enabled V2G networks. J. Parallel Distrib. Comput. 2018, 118, 107–117. [Google Scholar] [CrossRef]
- Liu, D.; Li, D.; Liu, X.; Ma, L.; Yu, H.; Zhang, H. Research on a cross-domain authentication scheme based on consortium blockchain in V2G networks of smart grid. In Proceedings of the 2018 2nd IEEE Conference on Energy Internet and Energy System Integration (EI2), Beijing, China, 20–22 October 2018; pp. 1–5. [Google Scholar]
- Gope, P.; Sikdar, B. An efficient privacy-preserving authentication scheme for energy internet-based vehicle-to-grid communication. IEEE Trans. Smart Grid 2019, 10, 6607–6618. [Google Scholar] [CrossRef]
- Mármol, F.G.; Sorge, C.; Ugus, O.; Pérez, G.M. Do not snoop my habits: Preserving privacy in the smart grid. IEEE Commun. Mag. 2012, 50, 166–172. [Google Scholar] [CrossRef]
- Abdallah, A.; Shen, X. Security and Privacy in Smart Grid; Springer International Publishing AG: Cham, Switzerland, 2018. [Google Scholar]
- Zhang, Y.; Gjessing, S.; Liu, H.; Ning, H.; Yang, L.T.; Guizani, M. Securing vehicle-to-grid communications in the smart grid. IEEE Wirel. Commun. 2013, 20, 66–73. [Google Scholar] [CrossRef]
- Liu, J.; Xiao, Y.; Li, S.; Liang, W.; Chen, C.P. Cyber security and privacy issues in smart grids. IEEE Commun. Surv. Tutor. 2012, 14, 981–997. [Google Scholar] [CrossRef]
- Kalogridis, G.; Efthymiou, C.; Denic, S.Z.; Lewis, T.A.; Cepeda, R. Privacy for smart meters: Towards undetectable appliance load signatures. In Proceedings of the 2010 First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 232–237. [Google Scholar]
- Efthymiou, C.; Kalogridis, G. Smart grid privacy via anonymization of smart metering data. In Proceedings of the 2010 first IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 238–243. [Google Scholar]
- Chen, L.; Zhou, J.; Chen, Y.; Cao, Z.; Dong, X.; Choo, K.K.R. PADP: Efficient Privacy-preserving Data Aggregation and Dynamic Pricing for Vehicle to Grid Networks. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Camenisch, J.; Van Herreweghen, E. Design and implementation of the idemix anonymous credential system. In Proceedings of the 9th ACM Conference on Computer and Communications Security (CCS ’02), Washington, DC, USA, 18–22 November 2002; pp. 21–30. [Google Scholar]
- Koutroumpouchos, N.; Ntantogian, C.; Xenakis, C. Building Trust for Smart Connected Devices: The Challenges and Pitfalls of TrustZone. Sensors 2021, 21, 520. [Google Scholar] [CrossRef] [PubMed]
- FIDO Security Reference. FIDO Alliance. Available online: https://fidoalliance.org/specs/fido-v2.0-rd-20180702/fido-security-ref-v2.0-rd-20180702.html (accessed on 27 February 2021).
- Panos, C.; Malliaros, S.; Ntantogian, C.; Panou, A.; Xenakis, C. A security evaluation of FIDO’s UAF protocol in mobile and embedded devices. In Proceedings of the 28th International Tyrrhenian Workshop on Digital Communication (TIWDC 2017), Palermo, Italy, 18–20 September 2017; pp. 127–142. [Google Scholar]
- Papadamou, K.; Zannettou, S.; Chifor, B.; Teican, S.; Gugulea, G.; Caponi, A.; Recupero, A.; Pisa., C.; Bianchi, G.; Gevers, S.; et al. Killing the Password and Preserving Privacy with Device-Centric and Attribute-based Authentication. IEEE Trans. Inf. Forensics Secur. 2019, 15, 2183–2193. [Google Scholar] [CrossRef]
- Benzi, F.; Anglani, N.; Bassi, E.; Frosini, L. Electricity smart meters interfacing the households. IEEE Trans. Ind. Electron. 2011, 58, 4487–4494. [Google Scholar] [CrossRef]
- FIDO2 Server. Community Edition Provided by StrongKey. Available online: https://github.com/StrongKey/fido (accessed on 21 February 2021).
- MASKER Implementation. Available online: https://github.com/gkarop/masker (accessed on 27 February 2021).
- Dataset of Hourly Electricity Consumptions from the European Network of Transmission System Operators for Electricity. Available online: https://www.entsoe.eu/data/data-portal/consumption/Pages/default.aspx (accessed on 27 February 2021).
- LOCUST, An Open Source Load Testing Tool. Available online: https://locust.io (accessed on 27 February 2021).
- Paquin, C.; Zaverucha, G. U-Prove Cryptographic Specification; Version 1.1; Technical Report; Microsoft Corporation: Redmond, WA, USA, 2011. [Google Scholar]
- Vullers, P.; Alpár, G. Efficient selective disclosure on smart cards using idemix. In Proceedings of the IFIP Working Conference on Policies and Research in Identity Management (IDMAN 2013), London, UK, 8–9 April 2013; pp. 53–67. [Google Scholar]
- Ekberg, J.E.; Kostiainen, K.; Asokan, N. The untapped potential of trusted execution environments on mobile devices. IEEE Secur. Priv. 2014, 12, 29–37. [Google Scholar] [CrossRef]
- Karopoulos, G.; Xenakis, C.; Tennina, S.; Evangelopoulos, S. Towards trusted metering in the smart grid. In Proceedings of the 2017 IEEE 22nd International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Lund, Sweden, 19–21 June 2017; pp. 1–5. [Google Scholar]
- European Commission. Best Available Techniques Reference Document, for the Cyber-Security and Privacy of the 10 Minimum Functional Requirements of the SMART Metering Systems, Smart-Grid Task Force Stakeholder Forum; European Commission: Brussels, Belgium, 2016. [Google Scholar]
- ENISA. Smart Grid Security. In Annex II. Security Aspects of the Smart Grid; ENISA: Iraklion, Greece, 2012; Available online: https://www.enisa.europa.eu/topics/critical-information-infrastructures-and-services/smart-grids/smart-grids-and-smart-metering/ENISA_Annex%20II%20-%20Security%20Aspects%20of%20Smart%20Grid.pdf (accessed on 5 April 2021).
- Finster, S.; Baumgart, I. Privacy-aware smart metering: A survey. IEEE Commun. Surv. Tutor. 2014, 16, 1732–1745. [Google Scholar] [CrossRef]
- W3C, Decentralized Identifiers (DIDs) V1.0. Available online: https://www.w3.org/TR/did-core/ (accessed on 5 April 2021).
- Lodder, M.; Khovratovich, D. Anonymous Credentials 2.0. 2019. Available online: https://bit.ly/3dSvUKG (accessed on 5 April 2021).

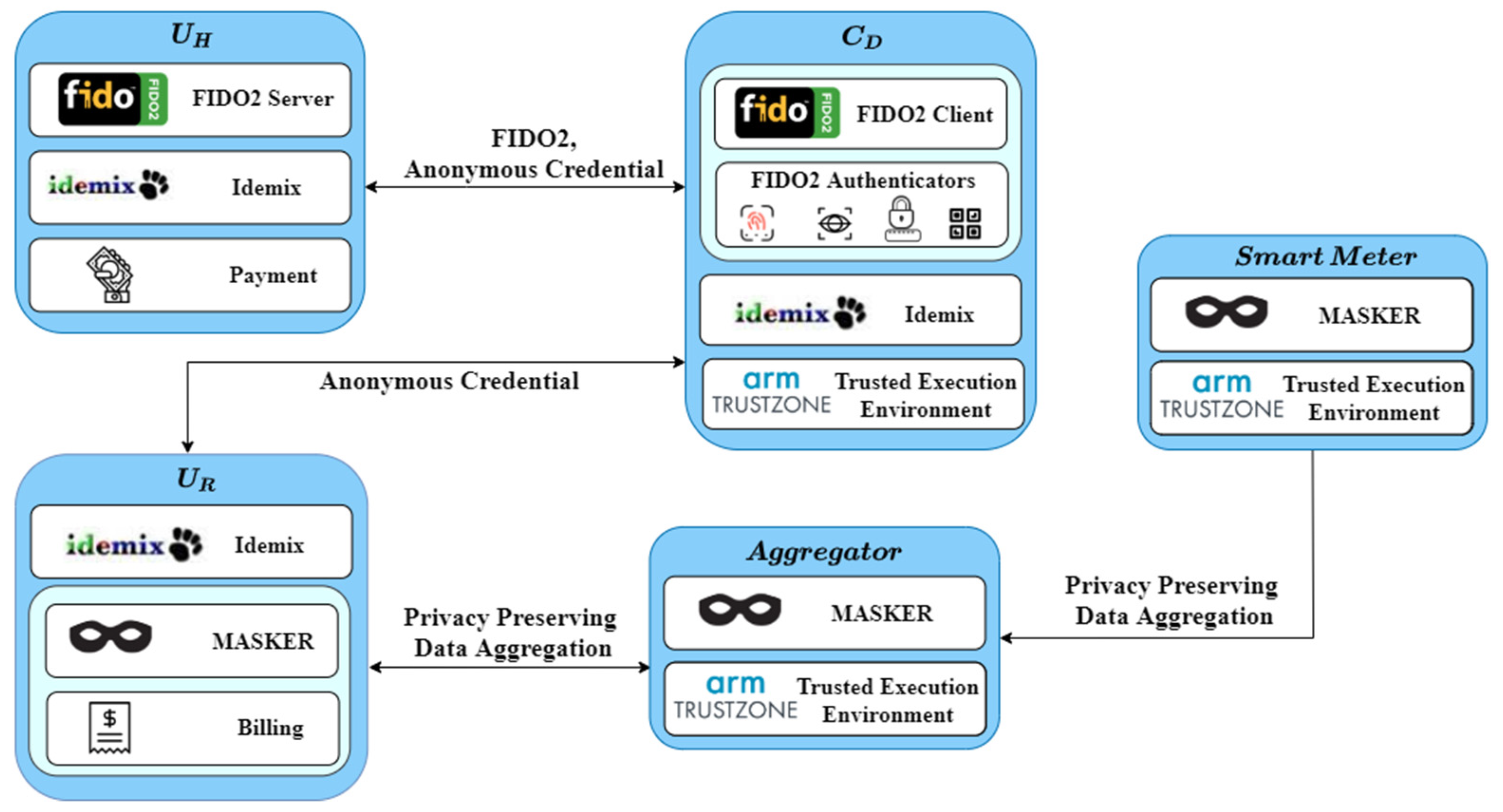


| Entity | Description |
|---|---|
| Consumer | A roaming energy consumer. |
| UH | Is under contract to supply the Consumer with energy. Issues P4G2Go credentials to its customers. |
| UR | Is under contract to supply the rented property with energy. Verifies roaming consumers’ P4G2Go credentials. |
| DC | Consumer’s mobile device. |
| Smart meter | Is bound with a property and measures the occupants’ energy consumption. Conveys the consumption readings to its corresponding aggregator. |
| Aggregator | Aggregates the consumption readings received by smart meters. Sends valid and accurate energy consumption data to its corresponding Utility. |
| Attributes | Description |
|---|---|
| PKUH | The public key of UH. |
| PKUH(NH) | The NH encrypted with the public key of the UH. |
| Consumer details | Various requirements depending on access control policies (e.g., the Consumer must be over 18). |
| Type of consumer | Individual, corporate. |
| Type of appliances | Need for high energy consumption equipment, charging electric vehicles, etc. |
| Discounts | Special offers for the Consumer. |
| UH | The UH of the Consumer. |
| Lifetime | The expiration date of the credential. |
| Entity | Setup |
|---|---|
| UH, UR | -Intel Core i5-4590 CPU at 3.30 GHz, 8 GB RAM (Download: 90.44 Mbps; Upload: 93.32 Mbps) |
| DC | -Xiaomi Redmi Note 5, Octa-core, 2000 MHz, ARM Cortex-A53, 64-bit, Android 9 (Download: 12.9 Mbps; Upload: 1.1 Mbps) |
| Smart meter, Aggregator | -Raspberry Pi v1 (a single-core 700 MHz CPU, and 512 MB–400 MHz RAM) (Download: 6.9 Mbps; Upload: 0.5 Mbps) |
| P4G2Go Processes | Average Duration (in Seconds) |
|---|---|
| Issuing a P4G2Go credential | 1.2 |
| Verifying a P4G2Go credential | 1.65 |
| FIDO2 Authentication | 3.08 |
| MASKER execution on smart meter | 0.05 |
| MASKER execution on aggregator | 0.17 |
| Entity | Technology | Process | CPU Utilization | Memory Consumption |
|---|---|---|---|---|
| UH | FIDO2 | Authentication | 2.6% | 1158 MB |
| Registration | 5% | 1148 MB | ||
| Idemix | Issuance | 26% | 4.76 MB | |
| UR | Idemix | Verification | 28% | 4.78 MB |
| DC | FIDO2 | Authentication | 27% | 61.7 MB |
| Registration | 10% | 60 MB | ||
| Idemix | Issuance | 17% | 4.61 MB | |
| Smart meter | MASKER | Masking readings | 5.1% | 4.8 MB |
| Aggregator | MASKER | Aggregating masked readings | 6.6% | 5 MB |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Farao, A.; Veroni, E.; Ntantogian, C.; Xenakis, C. P4G2Go: A Privacy-Preserving Scheme for Roaming Energy Consumers of the Smart Grid-to-Go. Sensors 2021, 21, 2686. https://doi.org/10.3390/s21082686
Farao A, Veroni E, Ntantogian C, Xenakis C. P4G2Go: A Privacy-Preserving Scheme for Roaming Energy Consumers of the Smart Grid-to-Go. Sensors. 2021; 21(8):2686. https://doi.org/10.3390/s21082686
Chicago/Turabian StyleFarao, Aristeidis, Eleni Veroni, Christoforos Ntantogian, and Christos Xenakis. 2021. "P4G2Go: A Privacy-Preserving Scheme for Roaming Energy Consumers of the Smart Grid-to-Go" Sensors 21, no. 8: 2686. https://doi.org/10.3390/s21082686
APA StyleFarao, A., Veroni, E., Ntantogian, C., & Xenakis, C. (2021). P4G2Go: A Privacy-Preserving Scheme for Roaming Energy Consumers of the Smart Grid-to-Go. Sensors, 21(8), 2686. https://doi.org/10.3390/s21082686







