Rule-Based Detection of False Data Injections Attacks against Optimal Power Flow in Power Systems
Abstract
1. Introduction
2. Background and Related Work
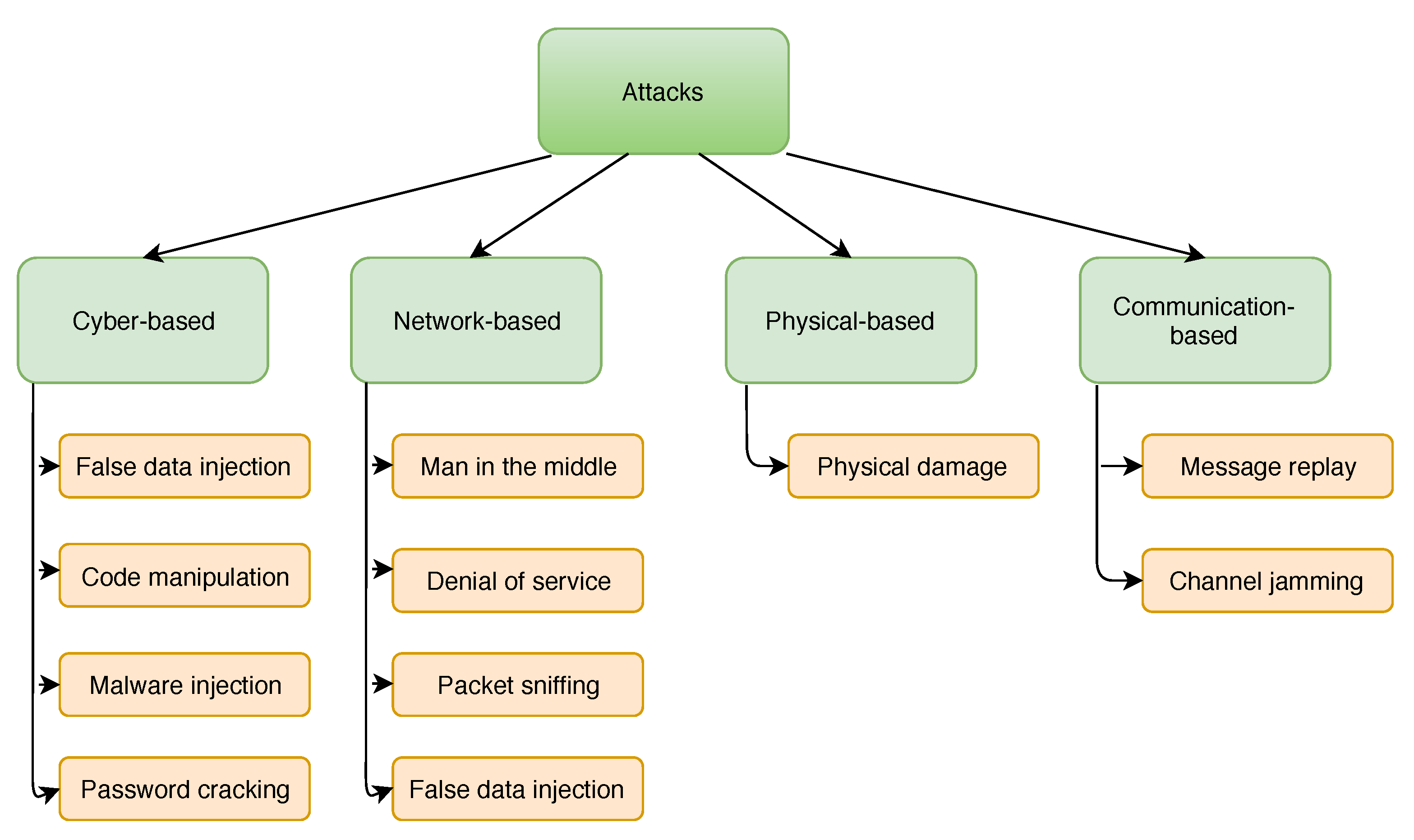
2.1. Attacks on Power Systems
2.2. Detection of False Data Injection Attacks
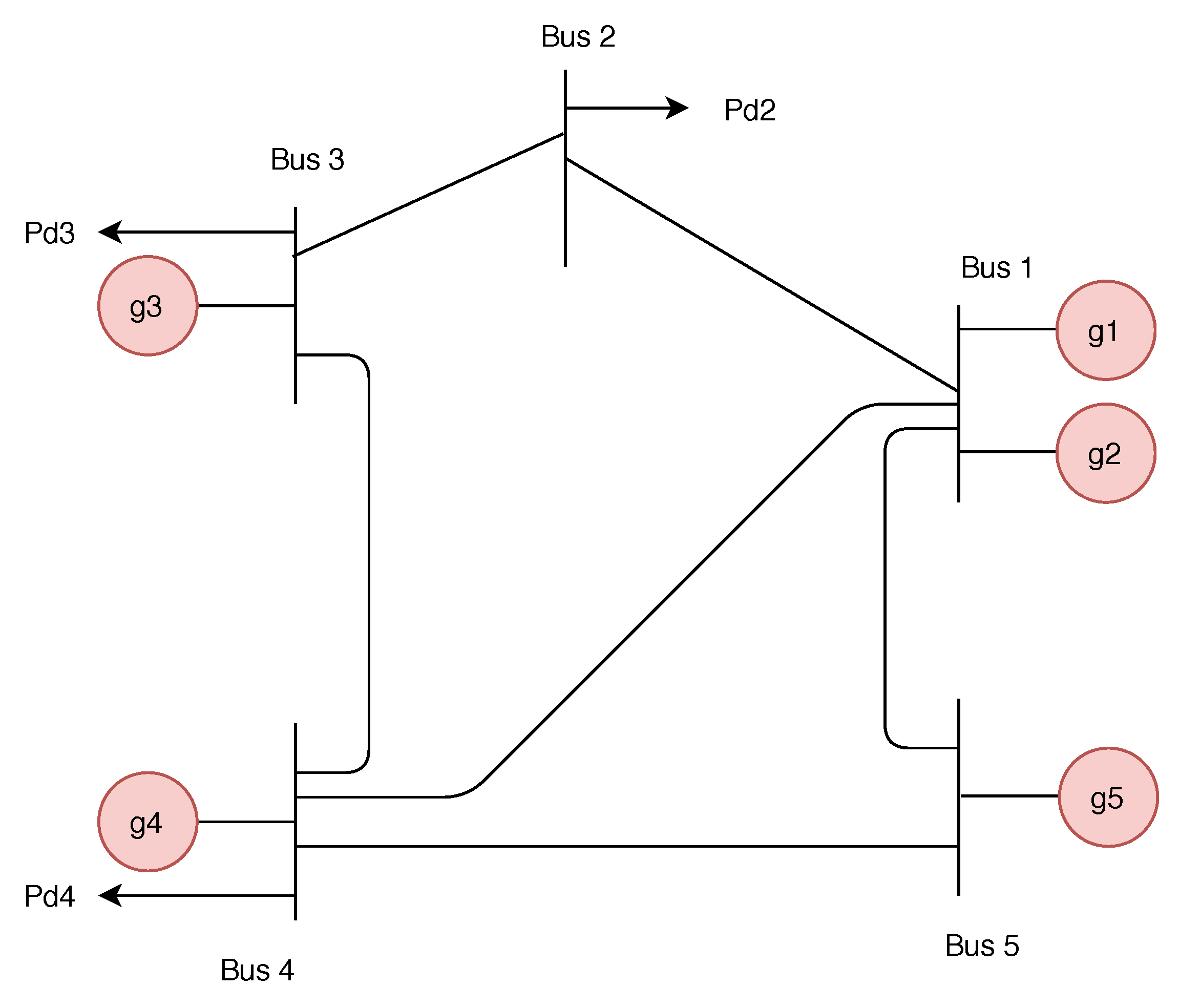
2.3. Bus System Model
2.4. The Energy Management System
2.5. The Optimal Power Flow Problem
2.6. Metaheuristics
2.6.1. Simulated Annealing
2.6.2. Genetic Algorithm
2.6.3. Particle Swarm Optimization
2.6.4. Tabu Search Algorithm
3. Advanced Persistent Threat-Based False Data Injection Attacks
3.1. Methodology
3.1.1. False Data Injection Attacks Plan
3.1.2. FDIA Mitigation
3.2. APT-Based Attack Strategy
3.2.1. Initialization
3.2.2. Optimization Problem
| Algorithm 1: Attack algorithm |
|
3.3. FDIA Targets in the Power Systems
3.4. Minimum Effort FDIA
| Algorithm 2: Minimum effort attack algorithm |
 |
4. Rule-Based Detection System for FDIA
5. Results and Discussions
5.1. Simulation Setup
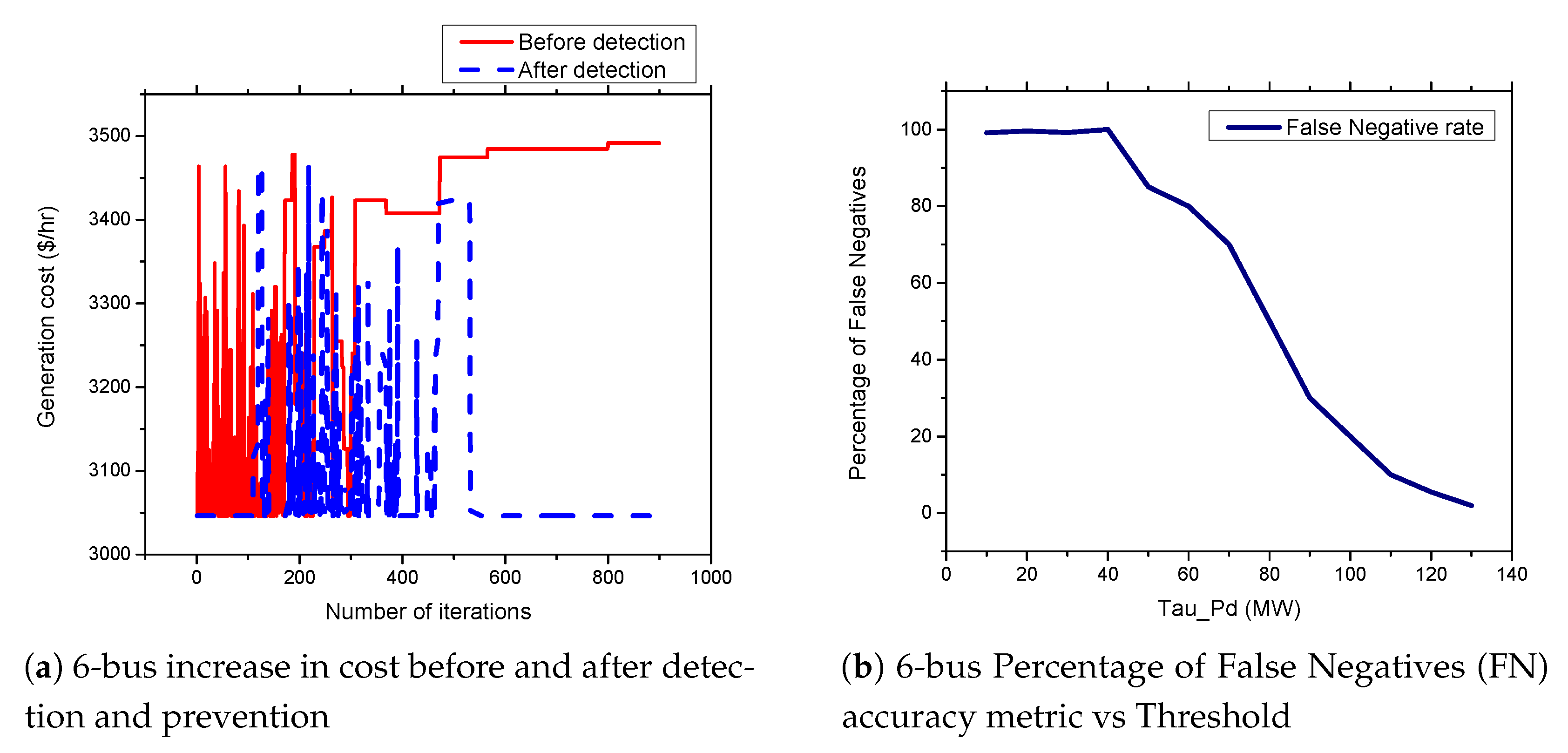
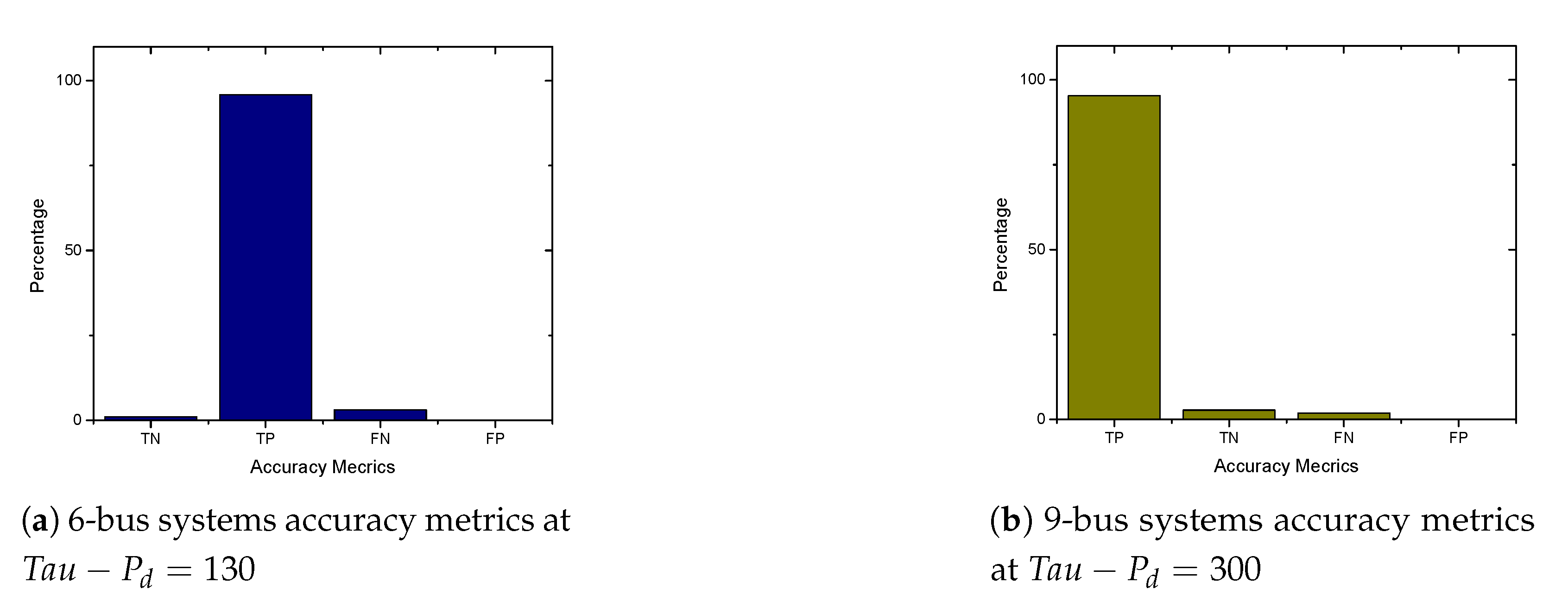
5.2. APT-Based FDIA on IEEE 6 Bus Systems
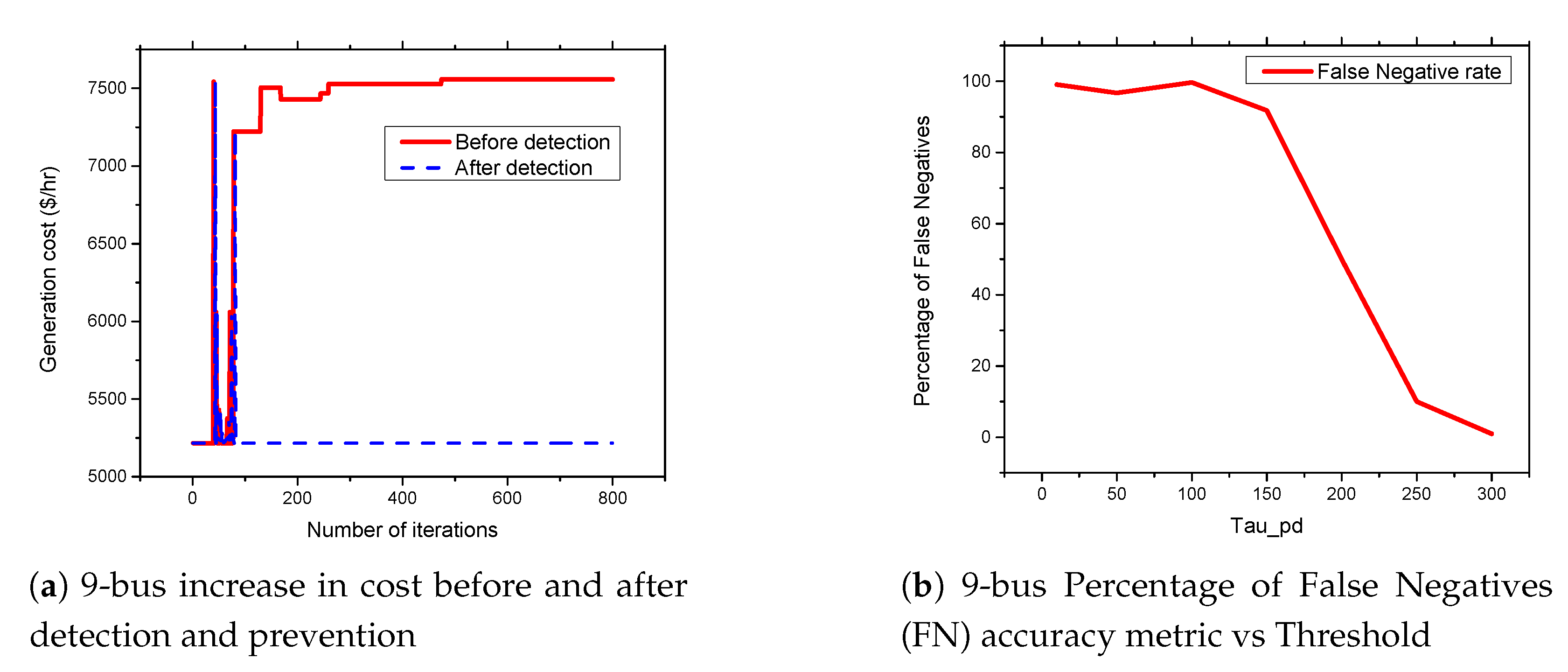
5.3. APT-Based FDIA on IEEE 9-Bus System
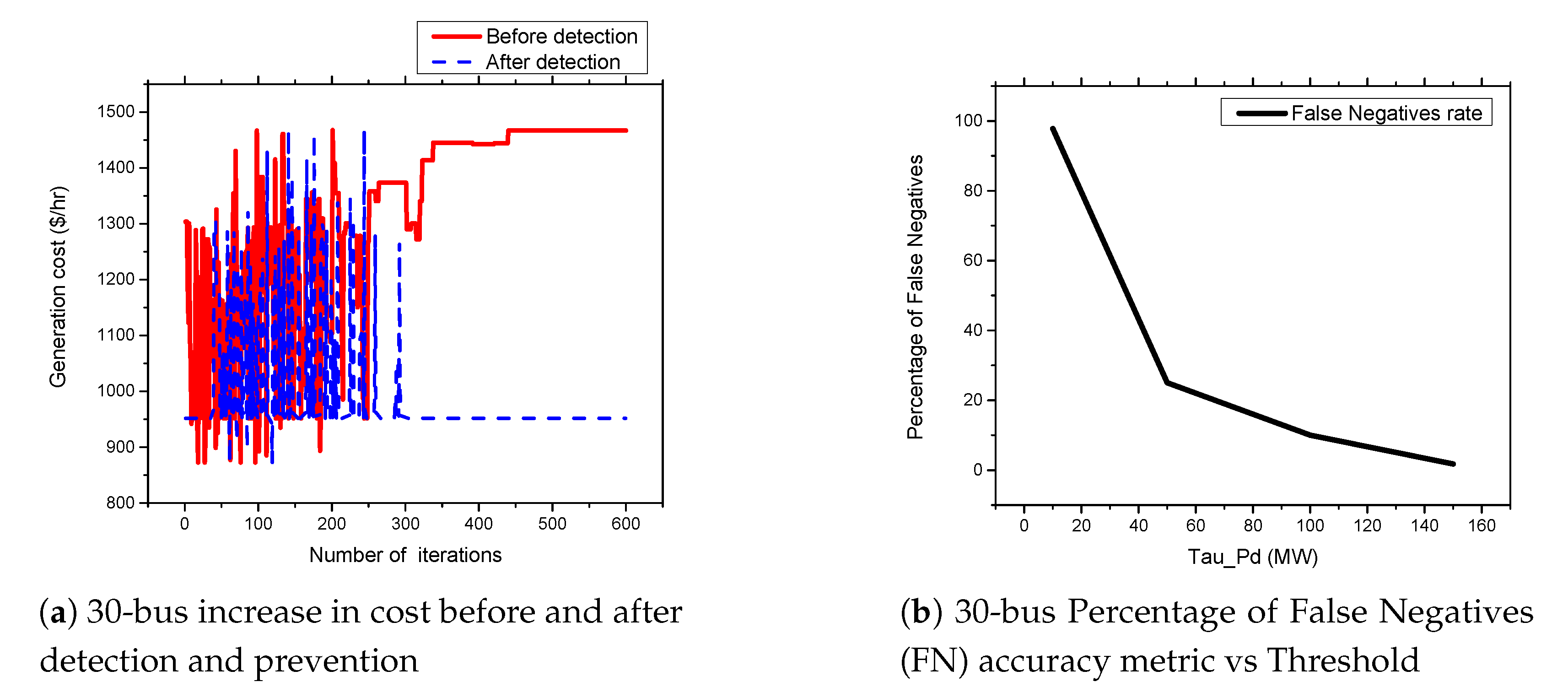
5.4. APT-Based FDIA on IEEE 30-Bus System
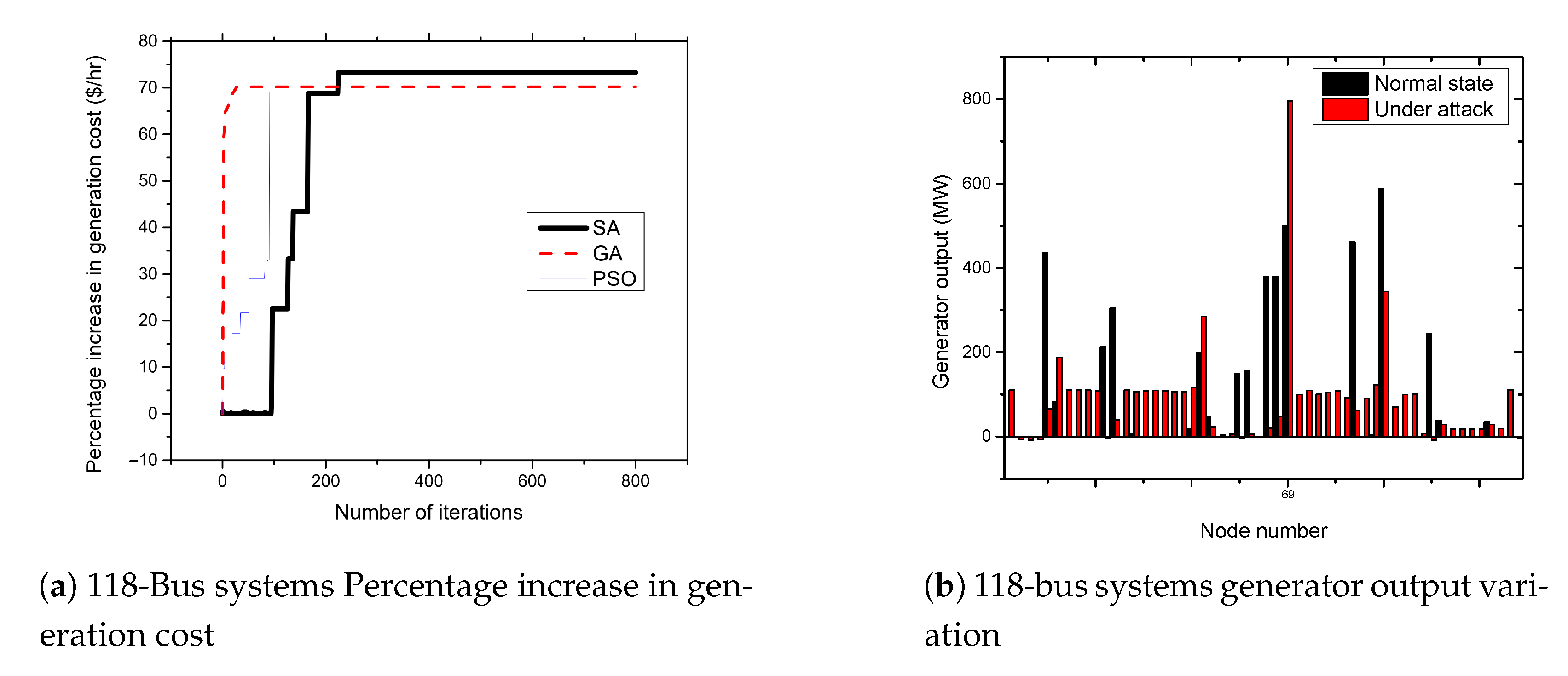
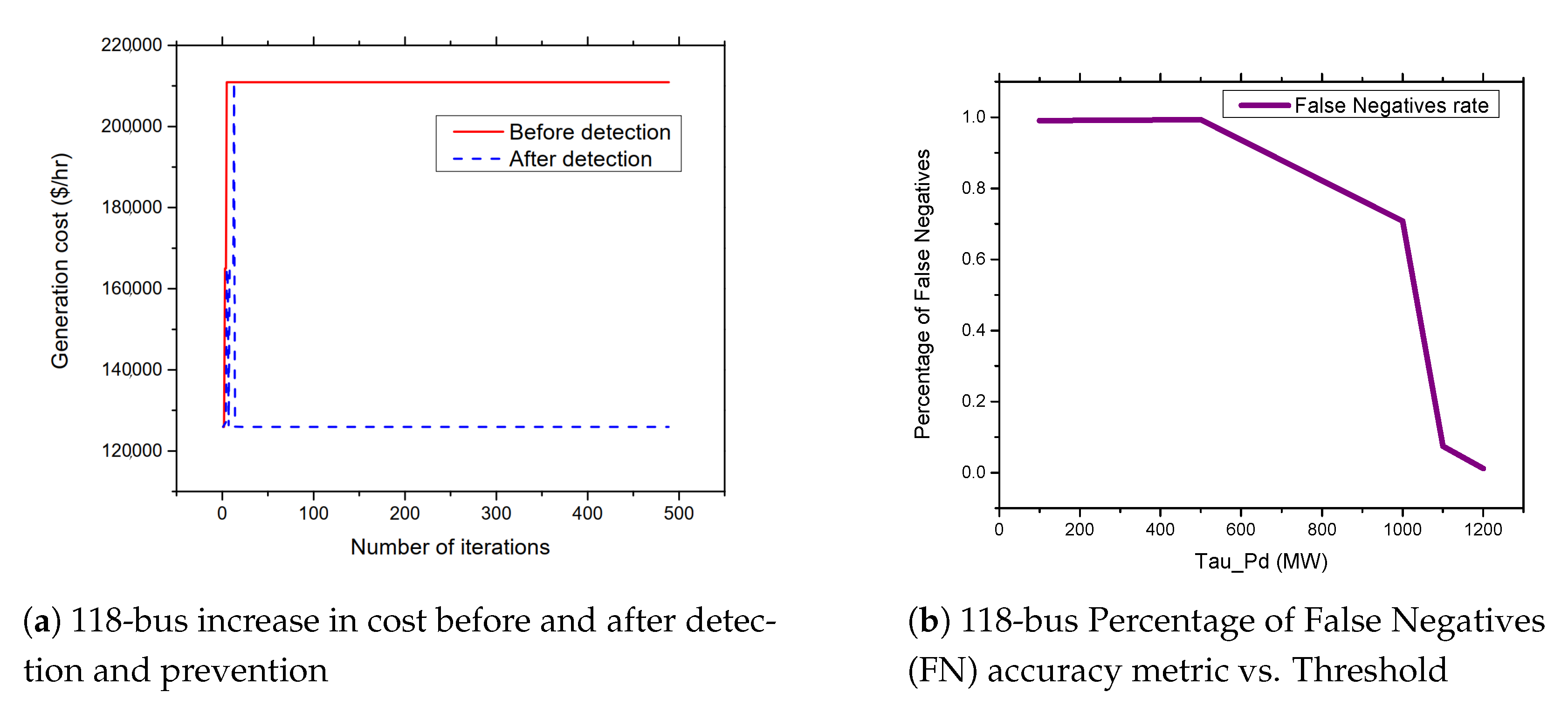
5.5. APT-Based FDIA on IEEE 118-Bus System
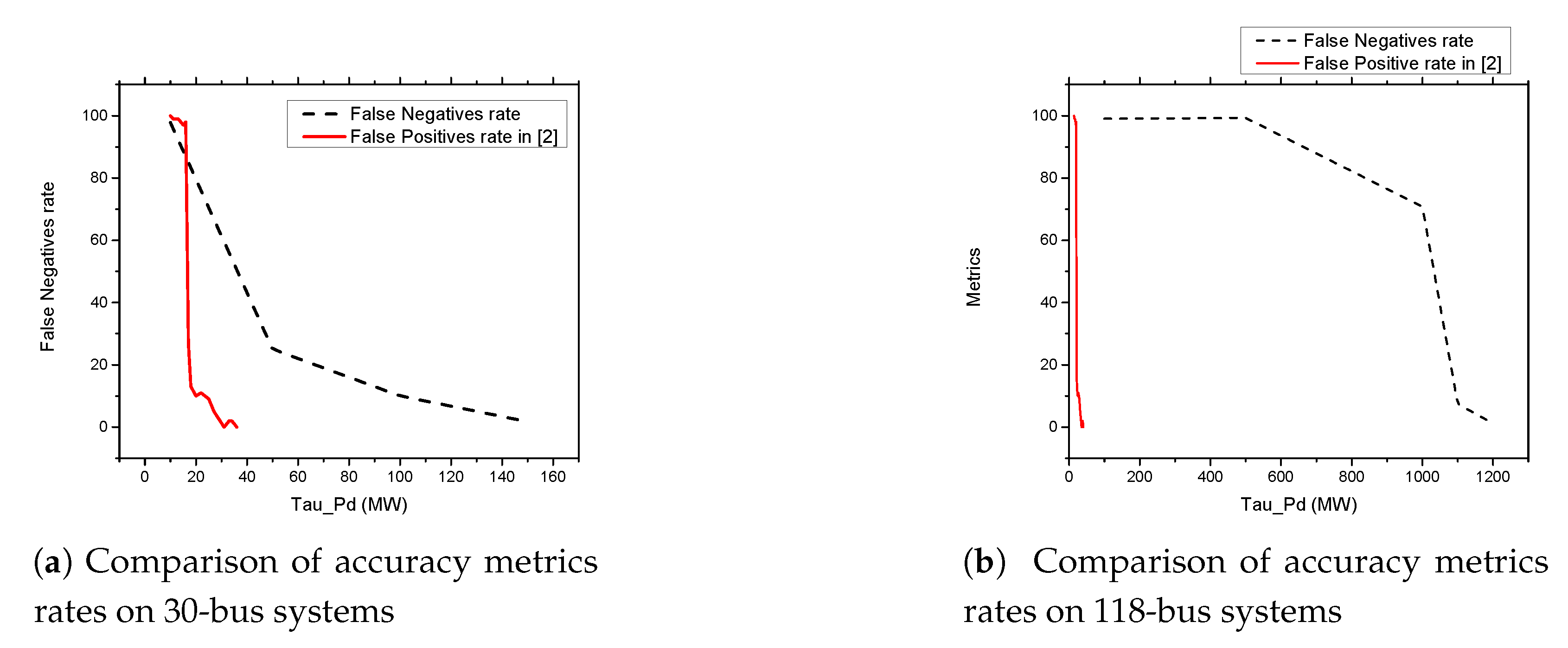
5.6. FDIA Detection Results
6. Conclusions and Future Work
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| FDIA | False Data Injections attacks |
| OPF | Optimal power flow |
| GA | Genetic Algorithm |
| SA | Simulated Annealing |
| TS | Tabu Search |
| PSO | Particle Swarm Optimization |
| PSSE | Power Systems State Estimator |
| AGC | Automatic Generation Control |
| APT | Advanced Persistence Threat |
| KNN | k-nearest neighbor |
| ENN | Extended Nearest Neighbor |
| SVM | support vector machine |
| ANN | Artificial Neural Networks |
| TP | True Positive |
| TN | True Negative |
| FP | False Positive |
| FN | False Negative |
References
- Yang, Q.; Li, D.; Yu, W.; Liu, Y.; An, D.; Yang, X.; Lin, J. Toward data integrity attacks against optimal power flow in smart grid. IEEE Internet Things J. 2017, 4, 1726–1738. [Google Scholar] [CrossRef]
- Salmeron, J.; Wood, K.; Baldick, R. Analysis of electric grid security under terrorist threat. IEEE Trans. Power Syst. 2004, 19, 905–912. [Google Scholar] [CrossRef]
- Yuan, Y.; Li, Z.; Ren, K. Modeling load redistribution attacks in power systems. IEEE Trans. Smart Grid 2011, 2, 382–390. [Google Scholar] [CrossRef]
- Mo, Y.; Kim, T.H.J.; Brancik, K.; Dickinson, D.; Lee, H.; Perrig, A.; Sinopoli, B. Cyber–physical security of a smart grid infrastructure. Proc. IEEE 2011, 100, 195–209. [Google Scholar]
- Liu, J.; Xiao, Y.; Li, S.; Liang, W.; Chen, C.P. Cyber security and privacy issues in smart grids. IEEE Commun. Surv. Tutor. 2012, 14, 981–997. [Google Scholar] [CrossRef]
- Yan, Y.; Qian, Y.; Sharif, H.; Tipper, D. A survey on cyber security for smart grid communications. IEEE Commun. Surv. Tutor. 2012, 14, 998–1010. [Google Scholar] [CrossRef]
- Wang, W.; Lu, Z. Cyber security in the smart grid: Survey and challenges. Comput. Netw. 2013, 57, 1344–1371. [Google Scholar] [CrossRef]
- Liu, L.; Esmalifalak, M.; Ding, Q.; Emesih, V.A.; Han, Z. Detecting false data injection attacks on power grid by sparse optimization. IEEE Trans. Smart Grid 2014, 5, 612–621. [Google Scholar] [CrossRef]
- Ambekar, R.; Mangalvedekar, H. Power system state estimation by linear programming under false data injection attack and contingency. In Proceedings of the 2017 International Conference on Innovative Mechanisms for Industry Applications (ICIMIA), Bengaluru, India, 21–23 February 2017; pp. 698–703. [Google Scholar]
- Zhao, J.; Zhang, G.; Dong, Z.Y.; Wong, K.P. Forecasting-aided imperfect false data injection attacks against power system nonlinear state estimation. IEEE Trans. Smart Grid 2015, 7, 6–8. [Google Scholar] [CrossRef]
- Kosut, O.; Jia, L.; Thomas, R.J.; Tong, L. Malicious data attacks on smart grid state estimation: Attack strategies and countermeasures. In Proceedings of the 2010 First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 220–225. [Google Scholar]
- Hu, Z.; Wang, Y.; Tian, X.; Yang, X.; Meng, D.; Fan, R. False data injection attacks identification for smart grids. In Proceedings of the 2015 Third International Conference on Technological Advances in Electrical, Electronics and Computer Engineering (TAEECE), Beirut, Lebanon, 29 April–1 May 2015; pp. 139–143. [Google Scholar]
- Musleh, A.S.; Chen, G.; Dong, Z.Y. A Survey on the Detection Algorithms for False Data Injection Attacks in Smart Grids. IEEE Trans. Smart Grid 2019, 11, 2218–2234. [Google Scholar] [CrossRef]
- Liang, G.; Weller, S.R.; Zhao, J.; Luo, F.; Dong, Z.Y. The 2015 ukraine blackout: Implications for false data injection attacks. IEEE Trans. Power Syst. 2016, 32, 3317–3318. [Google Scholar] [CrossRef]
- Zimmerman, R.D.; Murillo-Sánchez, C.E.; Thomas, R.J. MATPOWER: Steady-state operations, planning, and analysis tools for power systems research and education. IEEE Trans. Power Syst. 2010, 26, 12–19. [Google Scholar] [CrossRef]
- Sun, C.C.; Hahn, A.; Liu, C.C. Cyber security of a power grid: State-of-the-art. Int. J. Electr. Power Energy Syst. 2018, 99, 45–56. [Google Scholar] [CrossRef]
- Lopes, Y.; Fernandes, N.C.; de Castro, T.B.; dos Santos Farias, V.; Noce, J.D.; Marques, J.P.; Muchaluat-Saade, D.C. Vulnerabilities and threats in smart grid communication networks. In Security Solutions and Applied Cryptography in Smart Grid Communications; IGI Global: Hershey, PA, USA, 2017; pp. 1–28. [Google Scholar]
- El Mrabet, Z.; Kaabouch, N.; El Ghazi, H.; El Ghazi, H. Cyber-security in smart grid: Survey and challenges. Comput. Electr. Eng. 2018, 67, 469–482. [Google Scholar] [CrossRef]
- He, H.; Yan, J. Cyber-physical attacks and defences in the smart grid: A survey. IET Cyber-Phys. Syst. Theory Appl. 2016, 1, 13–27. [Google Scholar] [CrossRef]
- Amin, B.R.; Taghizadeh, S.; Rahman, M.S.; Hossain, M.J.; Varadharajan, V.; Chen, Z. Cyber attacks in smart grid–dynamic impacts, analyses and recommendations. IET Cyber-Phys. Syst. Theory Appl. 2020. [Google Scholar] [CrossRef]
- Aliyu, F.; Sheltami, T.; Shakshuki, E.M. A detection and prevention technique for man in the middle attack in fog computing. Procedia Comput. Sci. 2018, 141, 24–31. [Google Scholar] [CrossRef]
- Foster, J.S., Jr.; Gjelde, E.; Graham, W.R.; Hermann, R.J.; Kluepfel, H.M.; Lawson, R.L.; Soper, G.K.; Wood, L.L.; Woodard, J.B. Report of the Commission to Assess the Threat to the United States from Electromagnetic Pulse (EMP) Attack: Critical National Infrastructures; Technical Report; Electromagnetic Pulse (EMP) Commission: Mclean, VA, USA, 2008. [Google Scholar]
- Peng, L.; Cao, X.; Shi, H.; Sun, C. Optimal jamming attack schedule for remote state estimation with two sensors. J. Frankl. Inst. 2018, 355, 6859–6876. [Google Scholar] [CrossRef]
- Li, B.; Lu, R.; Wang, W.; Choo, K.K.R. Distributed host-based collaborative detection for false data injection attacks in smart grid cyber-physical system. J. Parallel Distrib. Comput. 2017, 103, 32–41. [Google Scholar] [CrossRef]
- Ding, Y.; Liu, J. Real-time false data injection attack detection in energy internet using online robust principal component analysis. In Proceedings of the 2017 IEEE Conference on Energy Internet and Energy System Integration (EI2), Beijing, China, 26–28 November 2017; pp. 1–6. [Google Scholar]
- Beg, O.A.; Nguyen, L.V.; Johnson, T.T.; Davoudi, A. Signal temporal logic-based attack detection in DC microgrids. IEEE Trans. Smart Grid 2018, 10, 3585–3595. [Google Scholar] [CrossRef]
- Adhikari, U.; Morris, T.H.; Pan, S. Applying non-nested generalized exemplars classification for cyber-power event and intrusion detection. IEEE Trans. Smart Grid 2016, 9, 3928–3941. [Google Scholar] [CrossRef]
- Kurt, M.N.; Ogundijo, O.; Li, C.; Wang, X. Online cyber-attack detection in smart grid: A reinforcement learning approach. IEEE Trans. Smart Grid 2018, 10, 5174–5185. [Google Scholar] [CrossRef]
- Li, B.; Lu, R.; Xiao, G. HMM-based fast detection of false data injections in advanced metering infrastructure. In Proceedings of the GLOBECOM 2017-2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar]
- He, Y.; Mendis, G.J.; Wei, J. Real-time detection of false data injection attacks in smart grid: A deep learning-based intelligent mechanism. IEEE Trans. Smart Grid 2017, 8, 2505–2516. [Google Scholar] [CrossRef]
- Sedghi, H.; Jonckheere, E. Statistical structure learning of smart grid for detection of false data injection. In Proceedings of the 2013 IEEE Power & Energy Society General Meeting, Vancouver, BC, Canada, 21–25 July 2013; pp. 1–5. [Google Scholar]
- Esmalifalak, M.; Liu, L.; Nguyen, N.; Zheng, R.; Han, Z. Detecting stealthy false data injection using machine learning in smart grid. IEEE Syst. J. 2014, 11, 1644–1652. [Google Scholar] [CrossRef]
- Yan, J.; Tang, B.; He, H. Detection of false data attacks in smart grid with supervised learning. In Proceedings of the 2016 International Joint Conference on Neural Networks (IJCNN), Vancouver, BC, Canada, 24–29 July 2016; pp. 1395–1402. [Google Scholar]
- Ferragut, E.M.; Laska, J.; Olama, M.M.; Ozmen, O. Real-Time Cyber-Physical False Data Attack Detection in Smart Grids Using Neural Networks. In Proceedings of the 2017 International Conference on Computational Science and Computational Intelligence (CSCI), Las Vegas, NV, USA, 14–16 December 2017; pp. 1–6. [Google Scholar]
- Ahmed, S.; Lee, Y.; Hyun, S.H.; Koo, I. Unsupervised machine learning-based detection of covert data integrity assault in smart grid networks utilizing isolation forest. IEEE Trans. Inf. Forensics Secur. 2019, 14, 2765–2777. [Google Scholar] [CrossRef]
- Duan, J.; Zeng, W.; Chow, M.Y. Resilient distributed DC optimal power flow against data integrity attack. IEEE Trans. Smart Grid 2016, 9, 3543–3552. [Google Scholar] [CrossRef]
- Rahman, M.A.; Al-Shaer, E.; Kavasseri, R.G. A formal model for verifying the impact of stealthy attacks on optimal power flow in power grids. In Proceedings of the 2014 ACM/IEEE International Conference on Cyber-Physical Systems (ICCPS), Berlin, Germany, 14–17 April 2014; pp. 175–186. [Google Scholar]
- Khanna, K.; Panigrahi, B.K.; Joshi, A. Bi-level modelling of false data injection attacks on security constrained optimal power flow. IET Gener. Transm. Distrib. 2017, 11, 3586–3593. [Google Scholar] [CrossRef]
- Abdallah, A.; Shen, X.S. Efficient prevention technique for false data injection attack in smart grid. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–6. [Google Scholar]
- Manandhar, K.; Cao, X.; Hu, F.; Liu, Y. Combating false data injection attacks in smart grid using kalman filter. In Proceedings of the 2014 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 3–6 February 2014; pp. 16–20. [Google Scholar]
- Wei, L.; Gao, D.; Luo, C. False data injection attacks detection with deep belief networks in smart grid. In Proceedings of the 2018 Chinese Automation Congress (CAC), Xi’an, China, 30 November–2 December 2018; pp. 2621–2625. [Google Scholar]
- Zhang, T.Y.; Ye, D. False data injection attacks with complete stealthiness in cyber–physical systems: A self-generated approach. Automatica 2020, 120, 109117. [Google Scholar] [CrossRef]
- Lu, A.Y.; Yang, G.H. False data injection attacks against state estimation in the presence of sensor failures. Inf. Sci. 2020, 508, 92–104. [Google Scholar] [CrossRef]
- Sayghe, A.; Hu, Y.; Zografopoulos, I.; Liu, X.; Dutta, R.G.; Jin, Y.; Konstantinou, C. Survey of machine learning methods for detecting false data injection attacks in power systems. IET Smart Grid 2020. [Google Scholar] [CrossRef]
- Ashrafuzzaman, M.; Das, S.; Chakhchoukh, Y.; Shiva, S.; Sheldon, F.T. Detecting stealthy false data injection attacks in the smart grid using ensemble-based machine learning. Comput. Secur. 2020, 97, 101994. [Google Scholar] [CrossRef]
- Saadat, H. Power System Analysis; McGraw-Hill Series in Electrical and Computer Engineering; WCB/McGraw-Hill: New York, NY, USA, 1999. [Google Scholar]
- Kundur, D.; Feng, X.; Liu, S.; Zourntos, T.; Butler-Purry, K.L. Towards a framework for cyber attack impact analysis of the electric smart grid. In Proceedings of the 2010 First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 244–249. [Google Scholar]
- Sivasubramani, S.; Swarup, K. Multi-objective harmony search algorithm for optimal power flow problem. Int. J. Electr. Power Energy Syst. 2011, 33, 745–752. [Google Scholar] [CrossRef]
- Selim, S.Z.; Alsultan, K. A simulated annealing algorithm for the clustering problem. Pattern Recognit. 1991, 24, 1003–1008. [Google Scholar] [CrossRef]
- Kirkpatrick, S.; Gelatt, C.D., Jr.; Vecchi, M.P. Optimization by simulated annealing. Optim. Simmul. Annealing. Sci. 1983, 220, 671–680. [Google Scholar]
- Dowsland, K.A.; Thompson, J. Simulated annealing. In Handbook of Natural Computing; Springer: Berlin/Heidelberg, Gemany, 2012; pp. 1623–1655. [Google Scholar]
- Kramer, O. Genetic Algorithm Essentials; Springer: Berlin/Heidelberg, Germany, 2017; Volume 679. [Google Scholar]
- Elbes, M.; Alzubi, S.; Kanan, T.; Al-Fuqaha, A.; Hawashin, B. A survey on particle swarm optimization with emphasis on engineering and network applications. Evol. Intell. 2019, 1–17. [Google Scholar] [CrossRef]
- Gallego, R.A.; Romero, R.; Monticelli, A.J. Tabu search algorithm for network synthesis. IEEE Trans. Power Syst. 2000, 15, 490–495. [Google Scholar] [CrossRef]
- Ghafir, I.; Prenosil, V. Advanced persistent threat attack detection: An overview. Int. J. Adv. Comput. Netw. Secur. 2014, 4, 5054. [Google Scholar]
- Chen, P.Y.; Yang, S.; McCann, J.A.; Lin, J.; Yang, X. Detection of false data injection attacks in smart-grid systems. IEEE Commun. Mag. 2015, 53, 206–213. [Google Scholar] [CrossRef]






| Attacks | Year | Region | Consequences |
|---|---|---|---|
| False Data Injection Attacks | 2015 | Kyiv, Ukraine | Several hours of power outage (blackout). Affecting about 225,000 customers. |
| 2008 | Turkey | Explosion of oil pipeline in which 30,000 barrels of oil is spilled in water. | |
| 2007 | Idoha National Lab, USA | Generator exploded. | |
| Code Manipulation | 1999 | Bellingham, USA | Three people were killed by a huge fireball and many others were injured. |
| 1982 | Russia | Explosion of 3 kilotons of Trinitrotoluene (TNT) | |
| Malware Injection | 2012 | Saudi Arabia, and Qatar | Energy distribution, and energy generation are affected. |
| 2003 | Ohio, USA | System shutdown for 5 h. |
| Notation | Notation Definition |
|---|---|
| R | Set of all From nodes |
| L | Set of all To nodes |
| Set of all nodes (buses) in the network | |
| Set of all nodes (buses) in which a demand/load is connected | |
| Set of all nodes (buses) in which a generator is connected | |
| Set of all lines connected to the ith node (bus) | |
| Generator output of ith generator | |
| Lower bound of the generator output | |
| upper bound of the generator output | |
| Load/demand at node (bus) i | |
| Voltage phase angle of node (bus) i | |
| Power flow between bus i and j | |
| Upper bound of the Power flow between node (bus) i and j | |
| Line admittance between node (bus) i and j | |
| Cost function of the generator at ith node (bus) | |
| Target transmission lines | |
| False load demand value | |
| Control parameter |
| Bus-Systems | Normal Systems State | Minimum Effort Attack |
|---|---|---|
| 6-bus systems | 3046.413 | 3059.031 |
| (0.41%) | ||
| 9-bus systems | 5216.026 | 5216.477 |
| (0.008%) | ||
| 30-bus systems | 951.62 | 951.62 |
| (0%) | ||
| 118-bus systems | 125,947.88 | 125,948.37 |
| (0.0004%) |
| Notation | Value | Notation Definition |
|---|---|---|
| 1000 | Maximum temperature | |
| 0 | Minimum temperature | |
| C | 0.99 | Cooling rate |
| P | 50 | Population size |
| N/A | Dynamic false load demand | |
| N/A | Dynamic tabu list | |
| 3046.03 | 6-bus systems initial cost | |
| 5216.03 | 9-bus systems initial cost | |
| 951.62 | 30-bus systems initial cost | |
| 125,947.9 | 118-bus systems initial cost | |
| N/A | Dynamic cost increase threshold |
| Bus Systems | Metaheuristics | Min. Cost ($/hr) | Avg. Cost ($/hr) | Max. Cost ($/hr) |
|---|---|---|---|---|
| 6-Bus System | SA | 3484.9 | 3490.03 | 3491.73 |
| GA | 3491.72 | 3491.73 | 3491.74 | |
| PSO | 3492.21 | 3501.80 | 3521.65 | |
| TA | 3455.64 | 3462.456 | 3467 | |
| 9-Bus System | SA | 7527.79 | 7555.77 | 7564.83 |
| GA | 7564.81 | 7564.82 | 7564.83 | |
| PSO | 7478.89 | 7541.73 | 7568.70 | |
| TA | 7478.89 | 7496.945 | 7515 | |
| 30-Bus System | SA | 1481.58 | 1499.982 | 1517.57 |
| GA | 1494.56 | 1509.62 | 1517.57 | |
| PSO | 1492.11 | 1505.99 | 1523.75 | |
| TA | 1469 | 1469 | 1470 | |
| 118-Bus System | SA | 212,166.41 | 216,312.38 | 219,180.72 |
| GA | 212,108.16 | 213,703.66 | 214,387.45 | |
| PSO | 211,535.02 | 215,681.64 | 218,954.18 | |
| TA | 211,000 | 211,900 | 212,500 |
| Bus Systems | Normal | Min. Effort [1] | APT-Based |
|---|---|---|---|
| 6-bus systems | 3046.41 | 3256.37 | 3521.65 |
| (6.89%) | (15.6%) | ||
| 9-bus systems | 5216.03 | 6652.88 | 7568.70 |
| (27.55%) | (45.1%) | ||
| 30-Bus systems | 951.62 | 1034.49 | 1523.75 |
| (8.7%) | (60.12%) | ||
| 118-bus systems | 125,947.88 | 132,697.88 | 219,180.72 |
| (5.36%) | (74.02%) |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Umar, S.; Felemban, M. Rule-Based Detection of False Data Injections Attacks against Optimal Power Flow in Power Systems. Sensors 2021, 21, 2478. https://doi.org/10.3390/s21072478
Umar S, Felemban M. Rule-Based Detection of False Data Injections Attacks against Optimal Power Flow in Power Systems. Sensors. 2021; 21(7):2478. https://doi.org/10.3390/s21072478
Chicago/Turabian StyleUmar, Sani, and Muhamad Felemban. 2021. "Rule-Based Detection of False Data Injections Attacks against Optimal Power Flow in Power Systems" Sensors 21, no. 7: 2478. https://doi.org/10.3390/s21072478
APA StyleUmar, S., & Felemban, M. (2021). Rule-Based Detection of False Data Injections Attacks against Optimal Power Flow in Power Systems. Sensors, 21(7), 2478. https://doi.org/10.3390/s21072478







