A Two-Layer IP Hopping-Based Moving Target Defense Approach to Enhancing the Security of Mobile Ad-Hoc Networks
Abstract
1. Introduction
2. Related Work
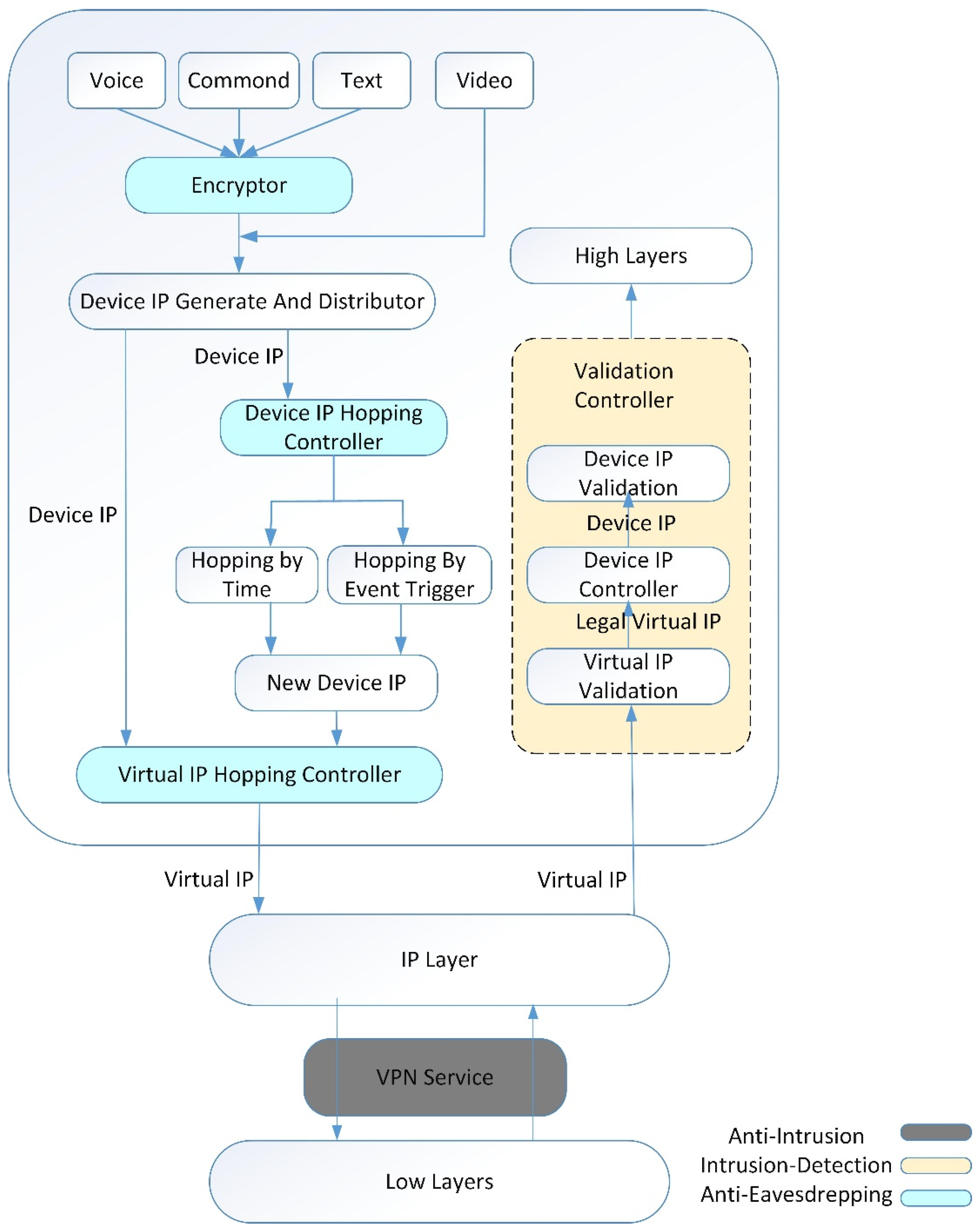
3. Two-Layer IP Hopping Approach
3.1. Encryption Algorithm
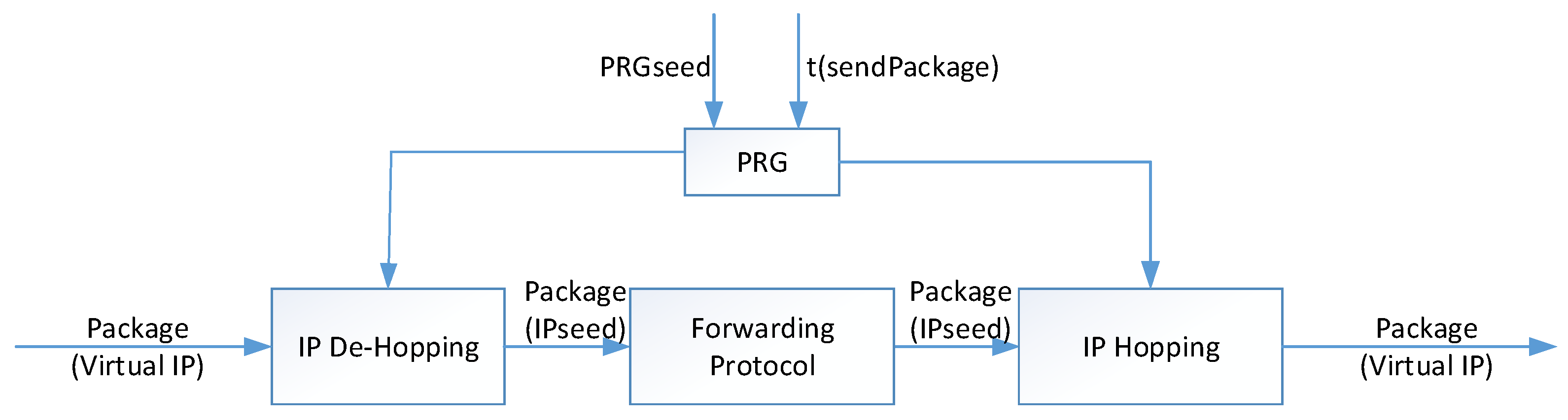
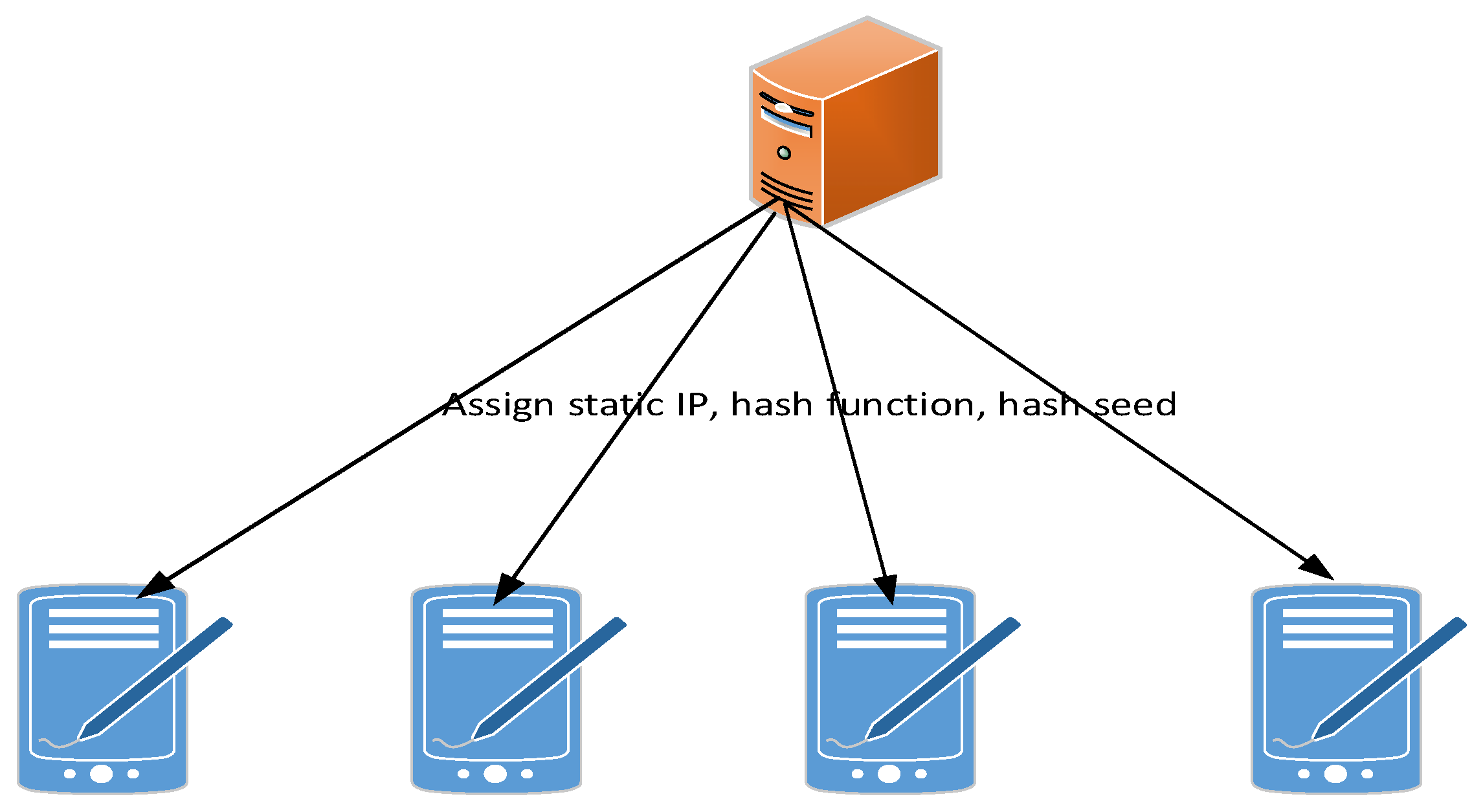
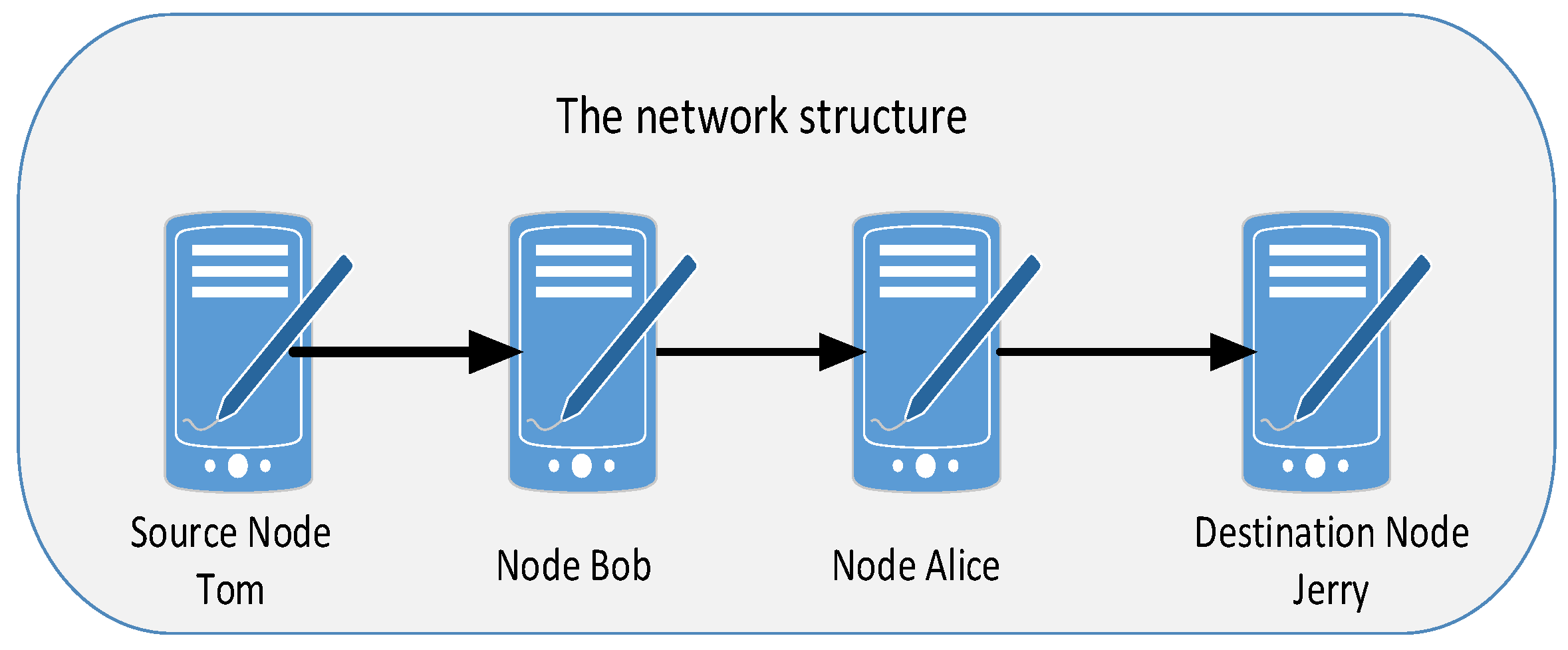
3.2. Access Randomization Scheme: Virtual IP Hopping
3.3. Virtual IP Hopping Randomization Analyses
3.4. Access Randomization Scheme: Device IP Hopping
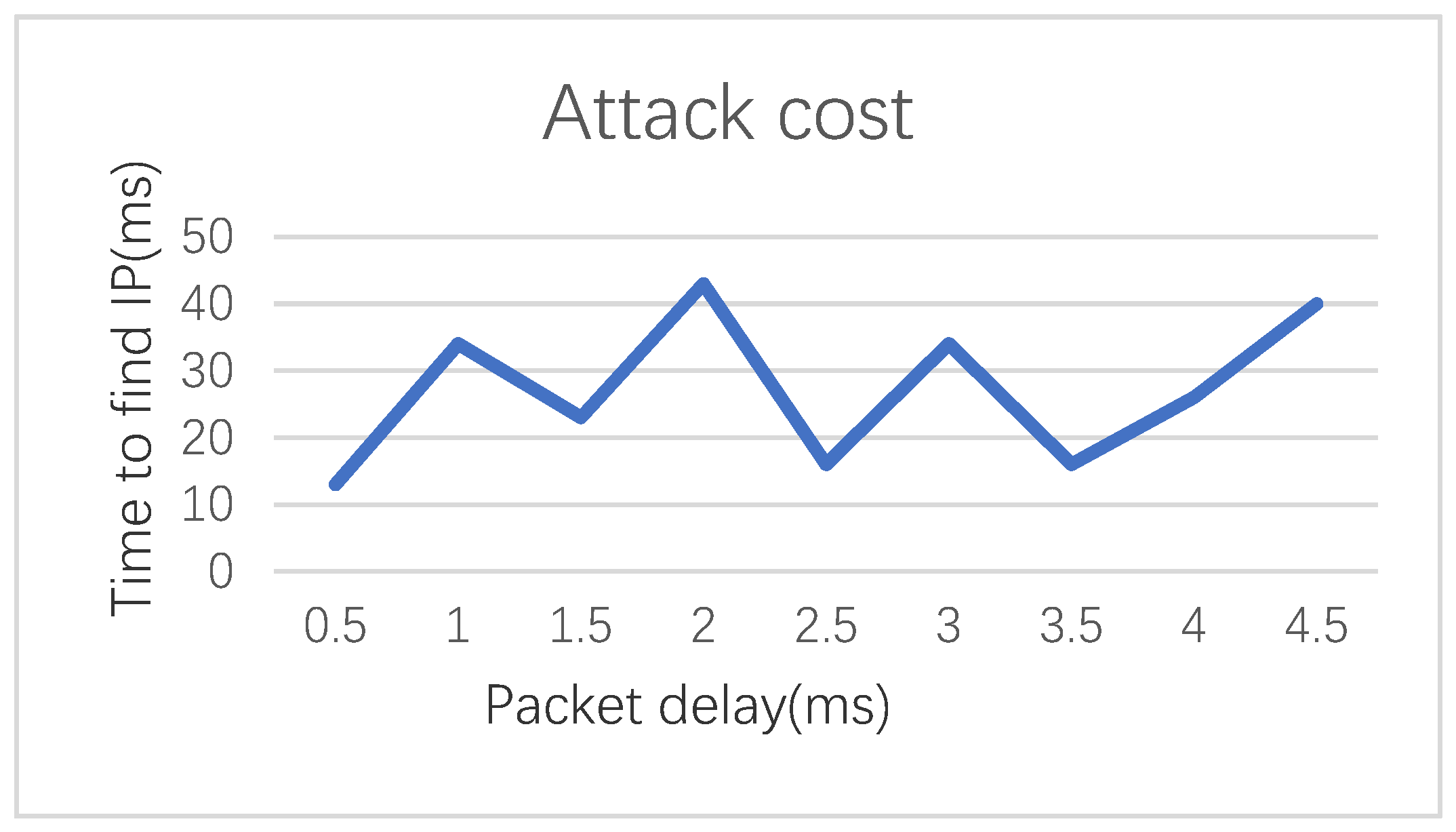
4. Tests and Performance Evaluation
4.1. Prototype Implementation Based on Android
4.2. Random Hopping between Virtual IP and Device IP
4.3. IP Hopping against Eavesdropping
4.4. The Cost of Synchronization after IP Hopping
4.5. A Comparison of Intrusion Prevention Scheme
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kanellopoulos, A.; Vamvoudakis, K.G. A Moving Target Defense Control Framework for Cyber-Physical Systems. IEEE Trans. Autom. Control 2020, 65, 1029–1043. [Google Scholar] [CrossRef]
- Sengupta, S.; Chowdhary, A.; Sabur, A.; Alshamrani, A.; Huang, D.; Kambhampati, S. A Survey of Moving Target Defenses for Network Security. IEEE Commun. Surv. Tutor. 2020, 22, 1909–1941. [Google Scholar] [CrossRef]
- Navas, R.E.; Cuppens, F.; Cuppens, N.B.; Toutain, L.; Papadopoulos, G.Z. MTD, Where Art Thou? A Systematic Review of Moving Target Defense Techniques for IoT. IEEE Internet Things J. 2020, 5, 2327–4662. [Google Scholar]
- Fu, Y.; Ding, Z. Hybrid channel access with CSMA/CA and SOTDMA to improve the performance of MANET. In Proceedings of the IEEE 17th International Conference on Communication Technology (ICCT), Chengdu, China, 27–30 October 2017; pp. 793–799. [Google Scholar]
- Fu, Y.; Ding, Z.; Wang, D. A new type of portable MANET terminal with two modes of CSMA and SOTDMA. In Proceedings of the 3rd IEEE International Conference on Computer and Communications (ICCC), Chengdu, China, 13–16 December 2017; pp. 443–452. [Google Scholar]
- Cho, J.; Sharma, D.P. Toward Proactive, Adaptive Defense: A Survey on Moving Target Defense. IEEE Commun. Surv. Tutor. 2020, 22, 709–745. [Google Scholar] [CrossRef]
- Mohsin, M.; Prakash, R. IP address assignment in a mobile ad hoc network. In Proceedings of the MILCOM 2002, Anaheim, CA, USA, 7–10 October 2002; pp. 856–861. [Google Scholar]
- Tang, H.; Sun, Q.T.; Yang, X.; Long, K. A Network Coding and DES Based Dynamic Encryption Scheme for Moving Target Defense. IEEE Access 2018, 6, 26059–26068. [Google Scholar] [CrossRef]
- Clark, A.; Sun, K.; Poovendran, R. Effectiveness of IP address randomization in decoy-based moving target defense. In Proceedings of the 52nd IEEE Conference on Decision and Control, Firenze, Italy, 10–13 December 2013; pp. 678–685. [Google Scholar]
- Azab, M.; Hassan, R.; Eltoweissy, M. ChameleonSoft: A moving target defense system. In Proceedings of the 7th International Conference on Collaborative Computing: Networking, Applications and Worksharing (CollaborateCom), Orlando, FL, USA, 15–18 October 2011; pp. 241–250. [Google Scholar]
- Larsen, P.; Homescu, A.; Brunthaler, S.; Franz, M. SoK: Automated Software Diversity. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 18–21 May 2014; pp. 276–291. [Google Scholar]
- Taguinod, M.; Doupé, A.; Zhao, Z.; Ahn, G. Toward a Moving Target Defense for Web Applications. In Proceedings of the IEEE International Conference on Information Reuse and Integration, San Francisco, CA, USA, 13–15 August 2015; pp. 510–517. [Google Scholar]
- Porter, J.; Albassam, E.A. Decentralized Approach to Architecture-Based Self-Protecting Software Systems. In Proceedings of the 10th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 6–8 January 2020; pp. 0169–0175. [Google Scholar]
- Li, Y.; Dai, R.; Zhang, J. Morphing communications of Cyber-Physical Systems towards moving-target defense. In Proceedings of the IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10–14 June 2014; pp. 592–598. [Google Scholar]
- Sun, J.; Sun, K. DESIR: Decoy-enhanced seamless IP randomization. IEEE INFOCOM 2016. In Proceedings of the 35th Annual IEEE International Conference on Computer Communications, San Francisco, CA, USA, 10–14 April 2016; pp. 1–9. [Google Scholar]
- Dunlop, M.; Groat, S.; Urbanski, W.; Marchany, R.; Tront, J. MT6D: A Moving Target IPv6 Defense. In Proceedings of the MILCOM 2011 Military Communications Conference, Baltimore, MD, USA, 7–10 November 2011; pp. 1321–1326. [Google Scholar]
- Antonatos, S.; Akritidis, P.; Markatos, E.P.; Anagnostakis, K.G. Defending against hitlist worms using network address space randomization. Comput. Netw. 2007, 51, 3471–3490. [Google Scholar] [CrossRef]
- Jafarian, J.H.; Al-Shaer, E.; Duan, Q. Adversary-aware IP address randomization for proactive agility against sophisticated attackers. In Proceedings of the IEEE Conference on Computer Communications (INFOCOM), Hong Kong, China, 26 April–1 May 2015; pp. 738–746. [Google Scholar]
- Krylov, V.; Kravtsov, K.; Sokolova, E.; Lyakhmanov, D. SDI defense against DDoS attacks based on IP Fast Hopping method. In Proceedings of the International Science and Technology Conference (Modern Networking Technologies) (MoNeTeC), Moscow, Russia, 27–29 October 2014; pp. 1–5. [Google Scholar]
- He, Y.; Zhang, M.; Yang, X.; Sun, Q.T.; Luo, J.; Yu, Y. The Intelligent Offense and Defense Mechanism of Internet of Vehicles Based on the Differential Game-IP Hopping. IEEE Access 2020, 8, 115217–115227. [Google Scholar] [CrossRef]
- Chang, S.; Park, Y.; Babu, B.B.A. Fast IP Hopping Randomization to Secure Hop-by-Hop Access in SDN. IEEE Trans. Netw. Serv. Manag. 2019, 16, 308–320. [Google Scholar] [CrossRef]
- Shaer, E.; Duan, Q.; Jafarian, J.H. Random host mutation for moving target defense. In Security and Privacy in Communication Networks; Springer: Berlin/Heidelberg, Germany, 2012; pp. 310–327. [Google Scholar]
- Albanese, M.; De Benedictis, A.; Jajodia, S. A moving target defense mechanism for MANETs based on identity virtualization. In Proceedings of the IEEE Conference on Communications and Network Security (CNS), National Harbor, MD, USA, 14–16 October 2013; pp. 278–286. [Google Scholar]
- Floissac, N.; L’Hyver, Y. From AES-128 to AES-192 and AES-256, How to Adapt Differential Fault Analysis Attacks on Key Expansion. In Proceedings of the Workshop on Fault Diagnosis and Tolerance in Cryptography, Nara, Japan, 28 September 2011; pp. 43–53. [Google Scholar]
- Shivkumar, S.; Umamaheswari, G. Performance Comparison of Advanced Encryption Standard (AES) and AES Key Dependent S-Box. In Proceedings of the Simulation Using MATLAB, International Conference on Process Automation, Control and Computing, Coimbatore, India, 20–22 July 2011; pp. 1–6. [Google Scholar]
- Yu, L.; Zhang, D.; Wu, L.; Xie, S.; Su, D.; Wang, X. AES Design Improvements Towards Information Security Considering Scan Attack. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science And Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 322–326. [Google Scholar]
- Hajihassani, O.; Monfared, S.K.; Khasteh, S.H.; Gorgin, S. Fast AES Implementation: A High-Throughput Bitsliced Approach. IEEE Trans. Parallel Distrib. Syst. 2019, 30, 2211–2222. [Google Scholar] [CrossRef]
- Tamang, J. Dynamical Properties of Ion-Acoustic Waves in Space Plasma and Its Application to Image Encryption. IEEE Access 2021, 9, 18762–18782. [Google Scholar] [CrossRef]
- García-Guerrero, E.E.; Inzunza-González, E.; López-Bonilla, O.R.; Cárdenas-Valdez, J.R.; Tlelo-Cuautle, E. Randomness improvement of chaotic maps for image encryption in a wireless communication scheme using PIC-microcontroller via Zigbee channels. Chaos Solitons Fractals 2020, 133, 109646. [Google Scholar] [CrossRef]
- Rathor, M.; Sengupta, A. IP Core Steganography Using Switch Based Key-Driven Hash-Chaining and Encoding for Securing DSP Kernels Used in CE Systems. IEEE Trans. Consum. Electron. 2020, 66, 151–157. [Google Scholar] [CrossRef]
- Erdem, E.; Sandıkkaya, M.T. OTPaaS—One Time Password as a Service. IEEE Trans. Inf. Forensics Secur. 2019, 14, 743–756. [Google Scholar] [CrossRef]
- Wu, L.; Cai, H.J.; Li, H. SGX-UAM: A Secure Unified Access Management Scheme with One Time Passwords via Intel SGX. IEEE Access 2021, 9, 38029–38042. [Google Scholar] [CrossRef]
- Maidhili, R.; Karthik, G. Energy Efficient and Secure Multi-User Broadcast Authentication Scheme in Wireless Sensor Networks. In Proceedings of the International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 4–6 January 2018; pp. 1–6. [Google Scholar]
- Kwon, T.; Hong, J. Secure and Efficient Broadcast Authentication in Wireless Sensor Networks. IEEE Trans. Comput. 2010, 8, 1120–1133. [Google Scholar] [CrossRef]
- Najib, A.F.; Rachmawanto, E.H.; Sari, C.A.; Sarker, K.; Rijati, N. A Comparative Study MD5 and SHA1 Algorithms to Encrypt REST API Authentication on Mobile-based Application. In Proceedings of the International Conference on Information and Communications Technology (ICOIACT), Yogyakarta, Indonesia, 24–25 July 2019; pp. 206–211. [Google Scholar]




| References | [15] | [16] | [17] | [18] | [19] | [20] | [21] | [22] | [23] | Ours | |
|---|---|---|---|---|---|---|---|---|---|---|---|
| Topology | Needs central node | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | No | No |
| Needs central authentication | Yes | No | Yes | Yes | Yes | No | No | No | No | No | |
| Needs DHCP server | Yes | No | Yes | Yes | Yes | No | No | No | No | No | |
| IP | Device IP hopping | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | No | Yes |
| Transmitted IP over air * | DIP | DIP | DIP | DIP | DIP | DIP | DIP | DIP | VIP | VIP | |
| Virtual IP hopping | No | No | No | No | No | No | No | No | Yes | Yes | |
| IP synchronization | No | No | No | No | No | Yes | Yes | Yes | No | No | |
| Hopping by time | No | Yes | No | No | No | Yes | Yes | Yes | Yes | Yes | |
| Hopping by event | No | No | Yes | Yes | Yes | No | No | No | No | Yes | |
| Hopping range | Low | High | Low | Low | Low | High | Low | High | Low | High |
| Time Spent (μs) | |
|---|---|
| Hash AND Update IP | 10.5 |
| Generate a new hash parameter | 0.1 |
| Method | Infrastructure Support | Wiretapping Capability | Scanning Attack | MIMT Attack | Additional Packets | Hopping on Time | Hopping on Event | Hopping Range |
|---|---|---|---|---|---|---|---|---|
| Our Method | x | √ | √ | √ | x | √ | √ | High |
| Kravtsov [19] | √ | √ | √ | √ | x | x | x | Low |
| Chang [29] | √ | √ | √ | √ | x | x | x | Low |
| Zhao [12] | √ | x | √ | x | x | x | x | Low |
| Albanese [23] | √ | √ | √ | √ | x | √ | x | Low |
| Yun He [20] | √ | √ | √ | √ | x | x | √ | Low |
| Park [21] | √ | x | x | x | x | √ | x | High |
| Sun [15] | √ | √ | √ | √ | √ | x | √ | Low |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, P.; Zhou, M.; Ding, Z. A Two-Layer IP Hopping-Based Moving Target Defense Approach to Enhancing the Security of Mobile Ad-Hoc Networks. Sensors 2021, 21, 2355. https://doi.org/10.3390/s21072355
Wang P, Zhou M, Ding Z. A Two-Layer IP Hopping-Based Moving Target Defense Approach to Enhancing the Security of Mobile Ad-Hoc Networks. Sensors. 2021; 21(7):2355. https://doi.org/10.3390/s21072355
Chicago/Turabian StyleWang, Pengkun, Momiao Zhou, and Zhizhong Ding. 2021. "A Two-Layer IP Hopping-Based Moving Target Defense Approach to Enhancing the Security of Mobile Ad-Hoc Networks" Sensors 21, no. 7: 2355. https://doi.org/10.3390/s21072355
APA StyleWang, P., Zhou, M., & Ding, Z. (2021). A Two-Layer IP Hopping-Based Moving Target Defense Approach to Enhancing the Security of Mobile Ad-Hoc Networks. Sensors, 21(7), 2355. https://doi.org/10.3390/s21072355






