On Improving 5G Internet of Radio Light Security Based on LED Fingerprint Identification Method
Abstract
1. Introduction
- We introduce the LED fingerprint model based on the characteristics of the LED equivalent circuit and design the LED fingerprint extraction and identification mechanisms—by fitting the power spectrum. The parameters which represent the LED’s inherent and stable nature are chosen to constitute the LED feature vector. The feature vector of each LED forms its fingerprint. A multi-SVM (Support Vector Machine) classifier is investigated theoretically to illustrate the process of the fingerprint identification.
- We illustrate the conceptual design of a typical 5G VLC multi-access scenario using the proposed security solution. We present how LED fingerprinting could be used in real-life systems. To detail the process, we choose the IoRL project as an exemplary test system.
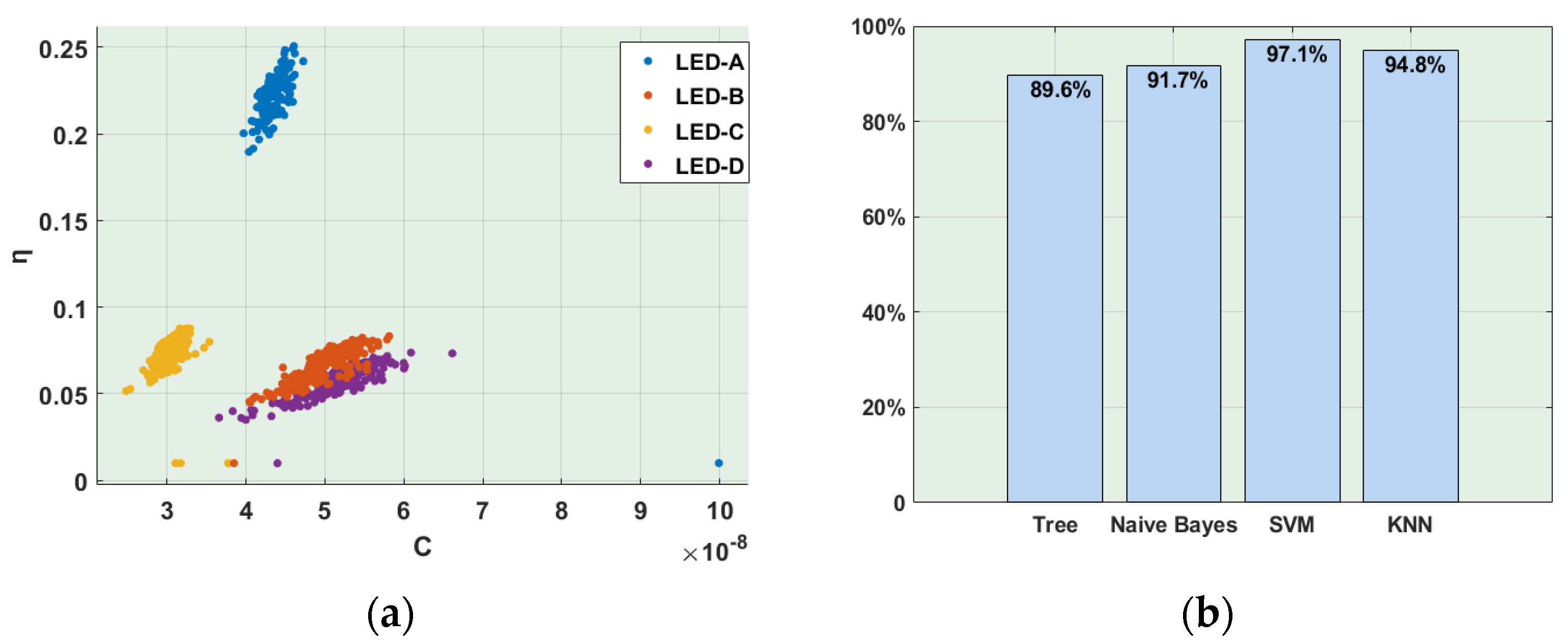
- We demonstrate the feasibility and accuracy of this method in a practical indoor VLC-based 5G network. During experimental evaluation, four identical LEDs were used to extract their fingerprints from the emitted 5G NR signals. Four machine-learning-based classifiers, i.e., decision tree, Naïve Bayes, SVM (Support Vector Machine), and KNN (K-Nearest-Neighbor) were employed to identify the extracted LED fingerprints. It turned out that the best results were achieved for the SVM classifier, which reached the accuracy of 97.1%.
2. LED Fingerprint Verification Mechanism
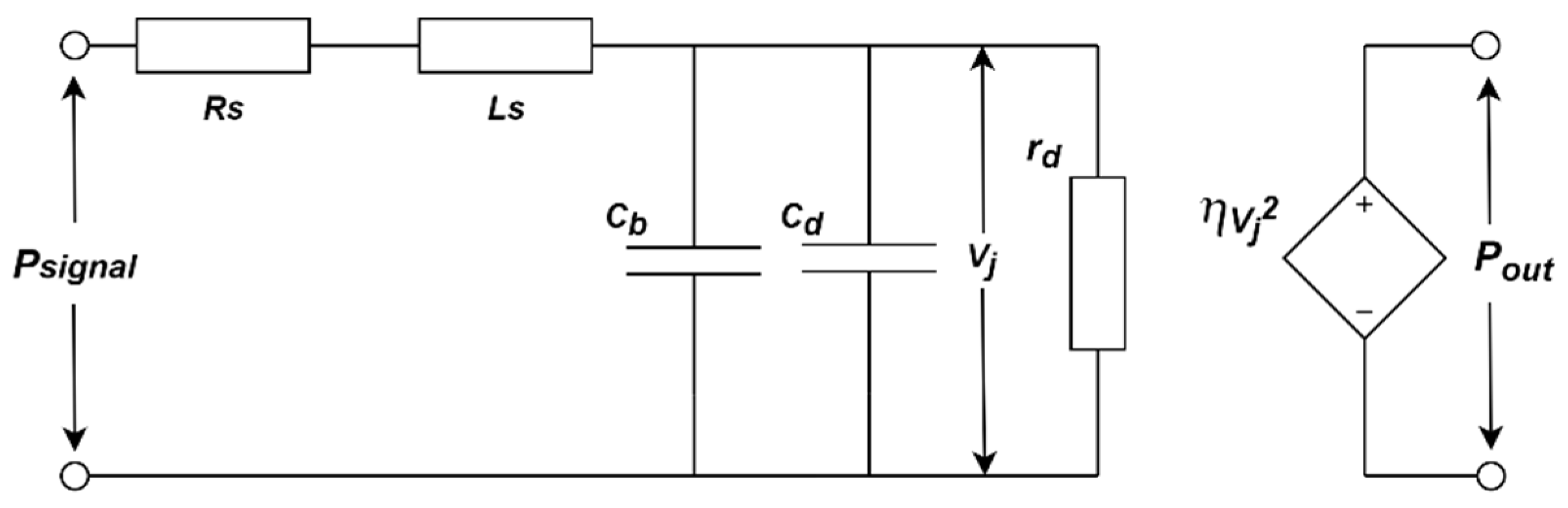
2.1. LED Fingerprint Model
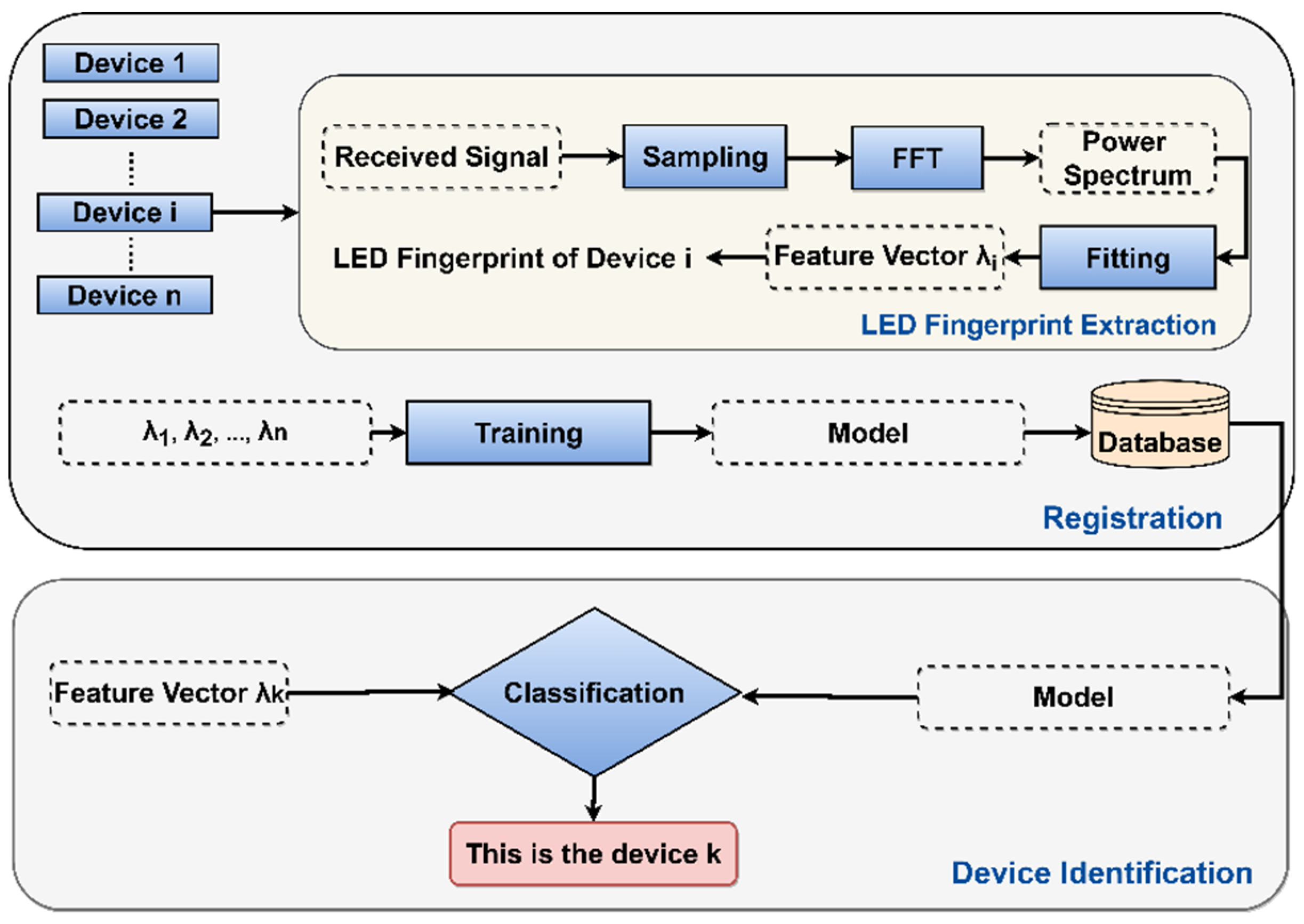
2.2. Extraction and Identification Mechanisms
2.3. Implementation of Features for Extraction and Identification
2.4. Envisioned Applications for the IoRL Security Framework
- Step 0: Register LED fingerprint and their localization database (this information is established and inserted to the database before LED installation)—the database is located at the security system.
- Step 1: A heartbeat-like protocol (UE <-> security subsystem) with which the security subsystem would be able to periodically poll the UE to initiate the LED fingerprint extraction process and securely transmit the determined fingerprint back to the security subsystem.
- Step 2: The measurement-based protocol (UE <-> LED) that would operate between the selected UE and the LED which would allow to determine the fingerprint of the LED under investigation.
- Step 3: The mechanism at the security subsystem that would compare the fingerprint of the chosen LED and its location with the corresponding data stored in the database.
- Step 4: In the case of a detected security breach, the security system can install rules on the SDN controller to block incoming/outgoing traffic to the LED and notify the administrators.
3. Demonstration and Evaluation
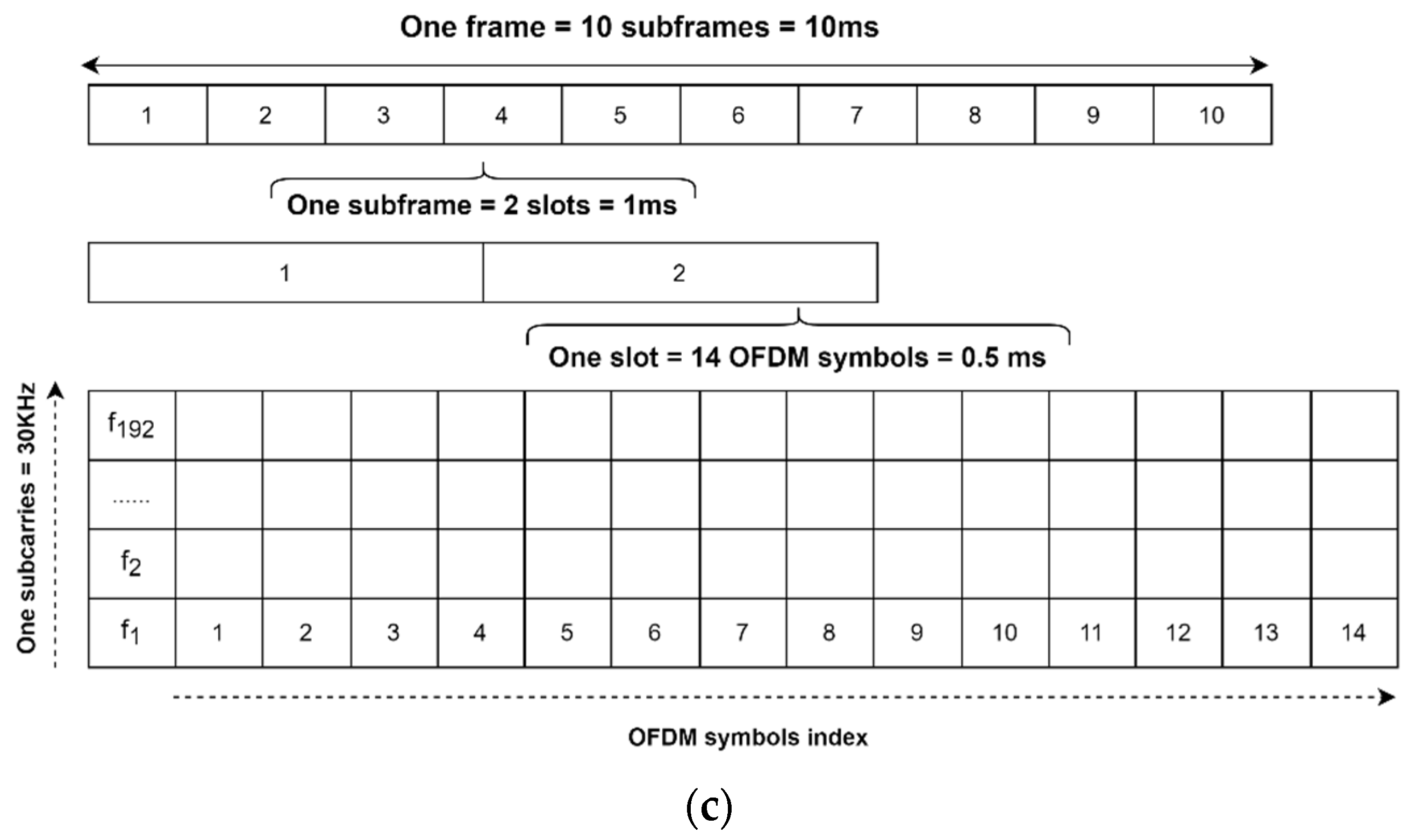
3.1. Demonstration Setup
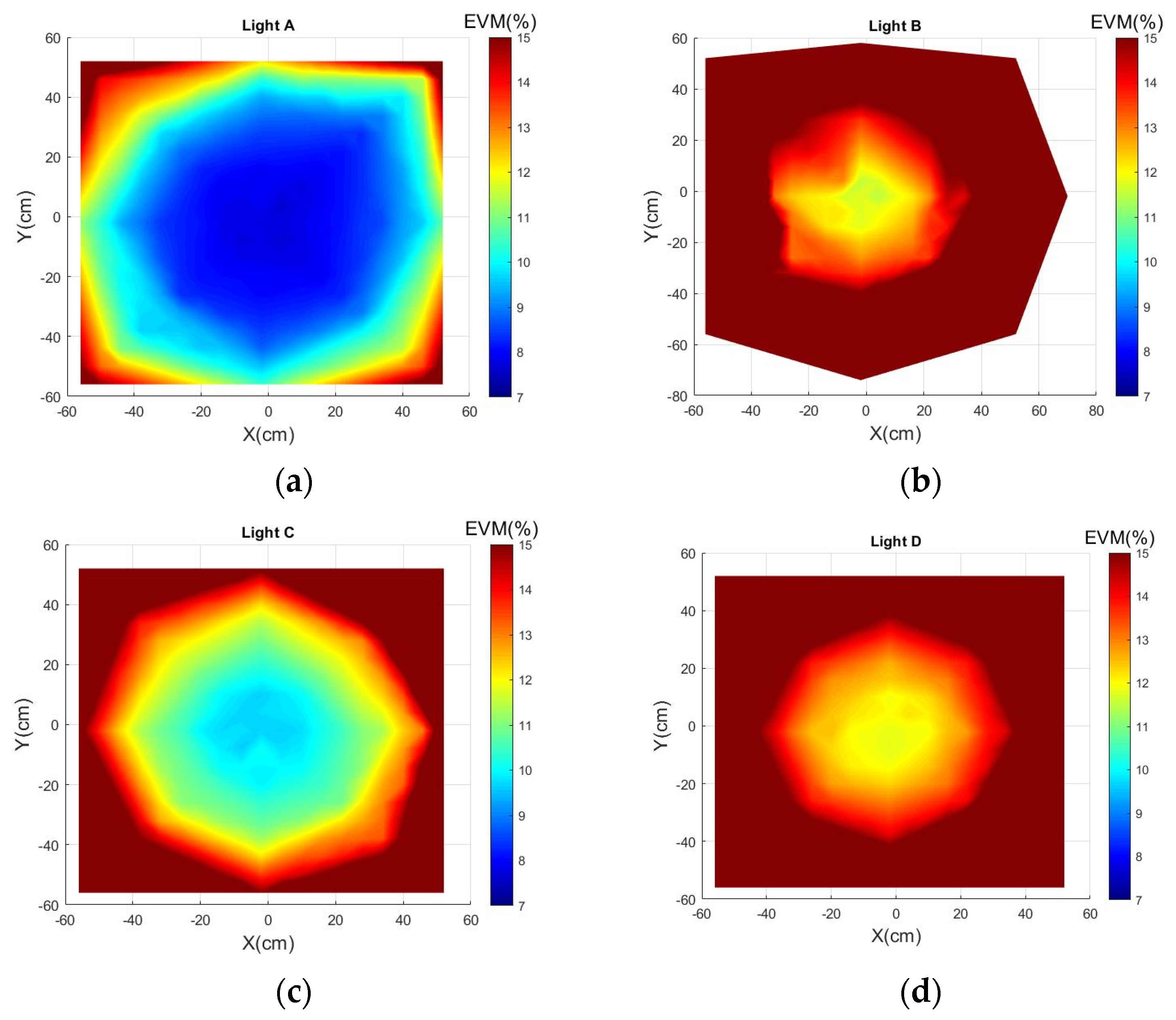
3.2. Results and Analysis
4. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Wang, J.; Spicher, N.; Warnecke, J.M.; Haghi, M.; Schwartze, J.; Deserno, T.M. Unobtrusive health monitoring in private spaces: The smart home. Sensors 2021, 21, 864. [Google Scholar] [CrossRef] [PubMed]
- Honar Pajooh, H.; Rashid, M.; Alam, F.; Demidenko, S. Multi-layer blockchain-based security architecture for internet of things. Sensors 2021, 21, 772. [Google Scholar] [CrossRef] [PubMed]
- Tsonev, D.; Videv, S.; Haas, H. Towards a 100 Gb/s Visible light wireless access network. Opt. Express 2015, 23, 1627–1637. [Google Scholar] [CrossRef] [PubMed]
- Burchardt, H.; Serafimovski, N.; Tsonev, D.; Videv, S.; Haas, H. VLC: Beyond point-to-point communication. IEEE Commun. Mag. 2014, 52, 98–105. [Google Scholar] [CrossRef]
- Tsiatmas, A.; Willems, F.M.; Linnartz, J.-P.M.; Baggen, S.; Bergmans, J.W. Joint Illumination and Visible-Light Communication Systems: Data Rates and Extra Power Consumption. In Proceedings of the 2015 IEEE International Conference on Communication Workshop (ICCW), IEEE, London, UK, 8–12 June 2015; pp. 1380–1386. [Google Scholar]
- Rahman, A.B.M.M.; Li, T.; Wang, Y. Recent advances in indoor localization via visible lights: A survey. Sensors 2020, 20, 1382. [Google Scholar] [CrossRef] [PubMed]
- Rehman, S.; Ullah, S.; Chong, P.; Yongchareon, S.; Komosny, D. Visible light communication: A system perspective—Overview and challenges. Sensors 2019, 19, 1153. [Google Scholar] [CrossRef] [PubMed]
- IEEE Standard for Local and Metropolitan Area Networks-Part 15.7: Short-Range Optical Wireless Communications; IEEE: New York, NY, USA, 2018.
- Shi, L.; Li, W.; Zhang, X.; Zhang, Y.; Chen, G.; Vladimirescu, A. Experimental 5G New Radio Integration with VLC. In Proceedings of the 2018 25th IEEE International Conference on Electronics, Circuits and Systems (ICECS), Bordeaux, France, 9–12 December 2018; pp. 61–64. [Google Scholar]
- Cabaj, K.; Gregorczyk, M.; Mazurczyk, W.; Nowakowski, P.; Żórawski, P. Network threats mitigation using software-defined networking for the 5G internet of radio light system. Secur. Commun. Netw. 2019, 2019, 1–22. [Google Scholar] [CrossRef]
- Shi, L.; Zhang, X.; Vladimirescu, A.; Wang, Z.; Zhang, Y.; Wang, J.; Garcia, J.; Cosmas, J.; Kapovits, A. Experimental Testbed for VLC-Based Localization Framework in 5G Internet of Radio Light. In Proceedings of the 2019 26th IEEE International Conference on Electronics, Circuits and Systems (ICECS), Genova, Italy, 27–30 November 2019; pp. 430–433. [Google Scholar]
- Abdaoui, R.; Zhang, X.; Xu, F. Potentiality of a Bi-Directional System Based on 60GHz and VLC Technologies for e-Health Applications. In Proceedings of the 2016 IEEE International Conference on Ubiquitous Wireless Broadband (ICUWB), Nanjing, China, 16–19 October 2016; pp. 1–3. [Google Scholar]
- Zhang, X.; Cosmas, J.; Meunier, B.; Ali, K.; Jawad, N.; Salih, M.; Meng, H.-Y.; Song, J.; Wang, J.; Tong, M.; et al. 5G Internet of Radio Light Services for Supermarkets. In Proceedings of the 2017 14th China International Forum on Solid State Lighting: International Forum on Wide Bandgap Semiconductors China (SSLChina: IFWS), Beijing, China, 1–3 November 2017. [Google Scholar]
- Mostafa, A.; Lampe, L. Physical-Layer Security for Indoor Visible Light Communications. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, Australia, 10–14 June 2014; pp. 3342–3347. [Google Scholar]
- Xu, Q.; Zheng, R.; Saad, W.; Han, Z. Device fingerprinting in wireless networks: Challenges and opportunities. IEEE Commun. Surv. Tutor. 2015, 18, 94–104. [Google Scholar] [CrossRef]
- Sun, H.; Zhu, X.; Liu, Y.; Liu, W. Construction of hybrid dual radio frequency RSSI (HDRF-RSSI) fingerprint database and indoor location method. Sensors 2020, 20, 2981. [Google Scholar] [CrossRef] [PubMed]
- Yu, J.; Hu, A.; Zhu, C.; Peng, L.; Jiang, Y. Rf Fingerprinting extraction and identification of wireless communication devices. J. Cryptol. Res 2016, 3, 433–446. [Google Scholar]
- Merchant, K.; Revay, S.; Stantchev, G.; Nousain, B. Deep learning for RF device fingerprinting in cognitive communication networks. IEEE J. Sel. Top. Signal Process. 2018, 12, 160–167. [Google Scholar] [CrossRef]
- Dissanayake, S.D.; Armstrong, J. Comparison of Aco-Ofdm, Dco-Ofdm and Ado-Ofdm in Im/Dd systems. J. Lightwave Technol. 2013, 31, 1063–1072. [Google Scholar] [CrossRef]
- Yin, Y.; Qiu, J.; Li, Z.; Cao, M. Research on secure debugging interaction of sensor nodes based on visible light communication. Sensors 2021, 21, 953. [Google Scholar] [CrossRef] [PubMed]
- Hall, J.; Barbeau, M.; Kranakis, E. Detection of transient in radio frequency fingerprinting using signal phase. Wirel. Opt. Commun. 2003, 7, 13–18. [Google Scholar]
- Kennedy, I.O.; Scanlon, P.; Mullany, F.J.; Buddhikot, M.M.; Nolan, K.E.; Rondeau, T.W. Radio Transmitter Fingerprinting: A Steady State Frequency Domain Approach. In Proceedings of the 2008 IEEE 68th Vehicular Technology Conference, Calgary, AB, Canada, 21–24 September 2008; pp. 1–5. [Google Scholar]
- Peng, L.; Hu, A. A Design of Deep Learning Based Optical Fiber Ethernet Device Fingerprint Identification System. In Proceedings of the ICC 2019 IEEE International Conference on Communications (ICC), Shanghai, China, 21–23 May 2019; pp. 1–6. [Google Scholar]
- Peng, L.; Hu, A.; Jiang, Y.; Yan, Y.; Zhu, C. A Differential Constellation Trace Figure Based Device Identification Method for ZigBee Nodes. In Proceedings of the 2016 8th International Conference on Wireless Communications & Signal Processing (WCSP), Yanghzhou, China, 13–15 October 2016; pp. 1–6. [Google Scholar]
- Peng, L.; Hu, A.; Zhang, J.; Jiang, Y.; Yu, J.; Yan, Y. Design of a Hybrid RF Fingerprint Extraction and Device Classification Scheme. IEEE Internet Things J. 2018, 6, 349–360. [Google Scholar] [CrossRef]
- Xing, Y.; Hu, A.; Yu, J.; Li, G.; Peng, L.; Zhou, F. A Robust Radio Frequency Fingerprint Identification Scheme for LFM Pulse Radars. In Proceedings of the 2019 International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Barcelona, Spain, 21–23 October 2019; pp. 1–6. [Google Scholar]
- Yang, H.; Zhong, W.-D.; Chen, C.; Alphones, A.; Du, P.; Zhang, S.; Xie, X. Coordinated resource allocation-based integrated visible light communication and positioning systems for indoor IoT. IEEE Trans. Wirel. Commun. 2020, 19, 4671–4684. [Google Scholar] [CrossRef]
- Yang, H.; Zhong, W.-D.; Chen, C.; Alphones, A. Integration of visible light communication and positioning within 5G networks for internet of things. IEEE Netw. 2020, 34, 134–140. [Google Scholar] [CrossRef]
- Shi, D.; Li, J.; Liu, Y.; Shi, L.; Huang, Y.; Wang, Z.; Zhang, X.; Vladimirescu, A. Effect of Illumination Intensity on LED Based Visible Light Communication System. In Proceedings of the 15th Symposium on Broadband Multimedia Systems and Broadcasting, Paris, France, 27–29 October 2020. [Google Scholar]
- Vladimirescu, A. The SPICE Book; Wiley: New York, NY, USA, 1994. [Google Scholar]
- Liu, Y.; Zheng, Y.F. One-against-All Multi-Class SVM Classification Using Reliability Measures. In Proceedings of the 2005 IEEE International Joint Conference on Neural Networks, Montreal, QC, Canada, 31 July–4 August 2005; Volume 2, pp. 849–854. [Google Scholar]
- Cosmas, J.; Meunier, B.; Ali, K.; Jawad, N.; Salih, M.; Zhang, Y.; Hadad, Z.; Globen, B.; Gokmen, H.; Malkos, S. A 5G Radio-Light SDN Architecture for Wireless and Mobile Network Access in Buildings. In Proceedings of the 2018 IEEE 5G World Forum (5GWF), Silicon Valley, CA, USA, 9–11 July 2018; pp. 135–140. [Google Scholar]



Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shi, D.; Zhang, X.; Shi, L.; Vladimirescu, A.; Mazurczyk, W.; Cabaj, K.; Meunier, B.; Ali, K.; Cosmas, J.; Zhang, Y. On Improving 5G Internet of Radio Light Security Based on LED Fingerprint Identification Method. Sensors 2021, 21, 1515. https://doi.org/10.3390/s21041515
Shi D, Zhang X, Shi L, Vladimirescu A, Mazurczyk W, Cabaj K, Meunier B, Ali K, Cosmas J, Zhang Y. On Improving 5G Internet of Radio Light Security Based on LED Fingerprint Identification Method. Sensors. 2021; 21(4):1515. https://doi.org/10.3390/s21041515
Chicago/Turabian StyleShi, Dayu, Xun Zhang, Lina Shi, Andrei Vladimirescu, Wojciech Mazurczyk, Krzysztof Cabaj, Benjamin Meunier, Kareem Ali, John Cosmas, and Yue Zhang. 2021. "On Improving 5G Internet of Radio Light Security Based on LED Fingerprint Identification Method" Sensors 21, no. 4: 1515. https://doi.org/10.3390/s21041515
APA StyleShi, D., Zhang, X., Shi, L., Vladimirescu, A., Mazurczyk, W., Cabaj, K., Meunier, B., Ali, K., Cosmas, J., & Zhang, Y. (2021). On Improving 5G Internet of Radio Light Security Based on LED Fingerprint Identification Method. Sensors, 21(4), 1515. https://doi.org/10.3390/s21041515





