Enhanced Dynamic Spectrum Access in UAV Wireless Networks for Post-Disaster Area Surveillance System: A Multi-Player Multi-Armed Bandit Approach
Abstract
:1. Introduction
- The selection of the transmitted power value for UAVs aiding a post-disaster area surveillance system is formulated as an optimization problem aiming to maximize the achievable data rate while considering the limited available power budget for each UAV. This is done in a decentralized manner as there is no exchange of information among UAVs.
- Integrating the post-disaster surveillance system as a CRN is considered an unconventional solution for the spectrum scarcity problem. Furthermore, it can reduce the overhead cost of renting dedicated frequency channels for post-disaster surveillance operations, while they are rarely used just when a disaster occurs.
- Despite the nature of original MAB algorithms to maximize the long-term reward, i.e., the achieved data rate, MAB algorithms are modified to take into account the limited power budget for transmission. Therefore, the selection of the transmitted power not only aims to maximize the data rate for the current channel but also considers the remaining power budget to maximize the data rate for the next available channel.
2. Related Works
3. System Model
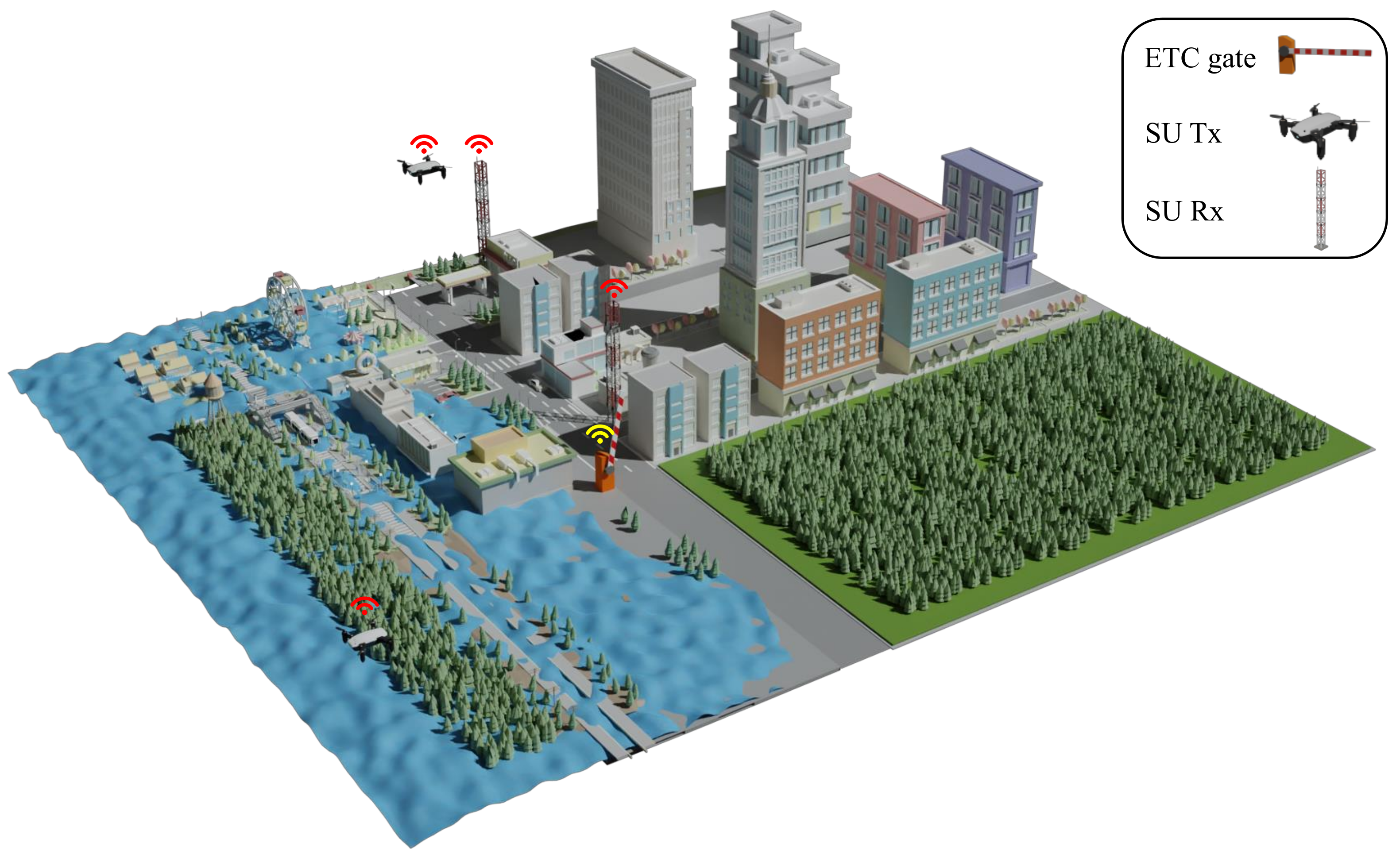
3.1. Post-Disaster Area Surveillance System Architecture
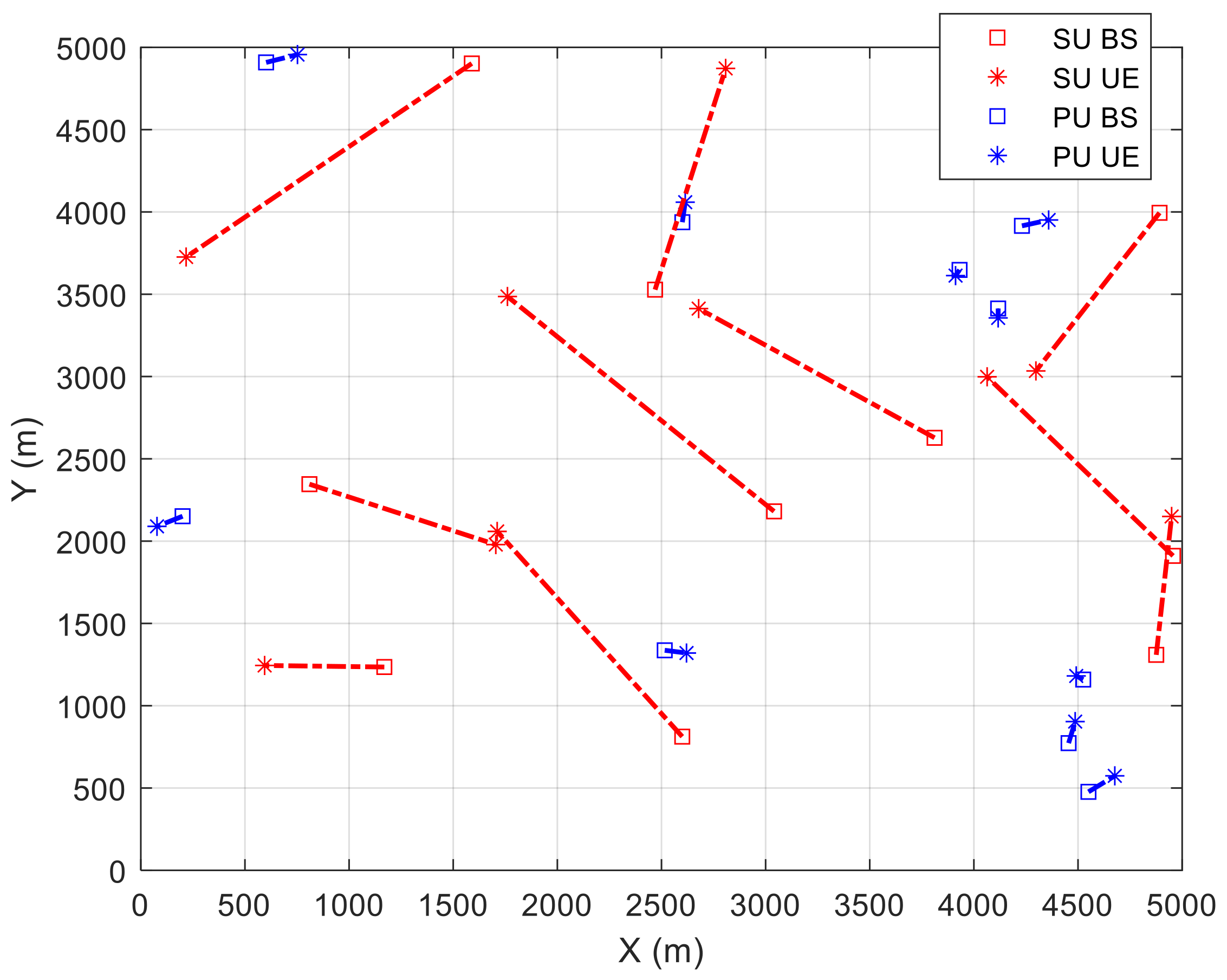
3.2. Problem Formulation
4. Proposed Power Budget Aware MAB Algorithm
4.1. Proposed PBA-UCB Algorithm
| Algorithm 1. PBA-UCB transmission power selection |
|
4.2. Proposed PBA-TS Algorithm
4.3. Complexity Analysis of the Proposed Algorithms
| Algorithm 2. PBA-TS transmission power selection |
|
5. Simulation Results
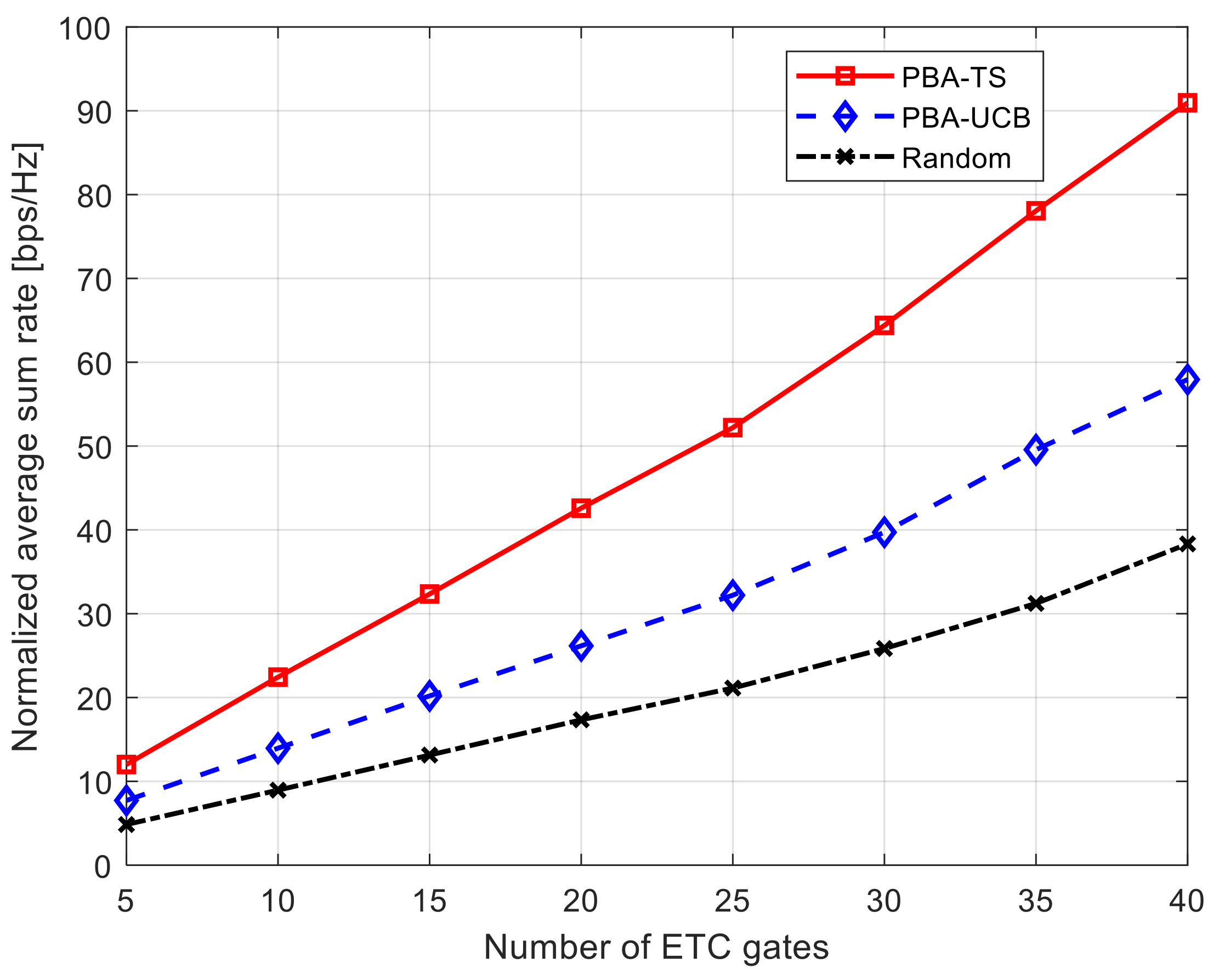
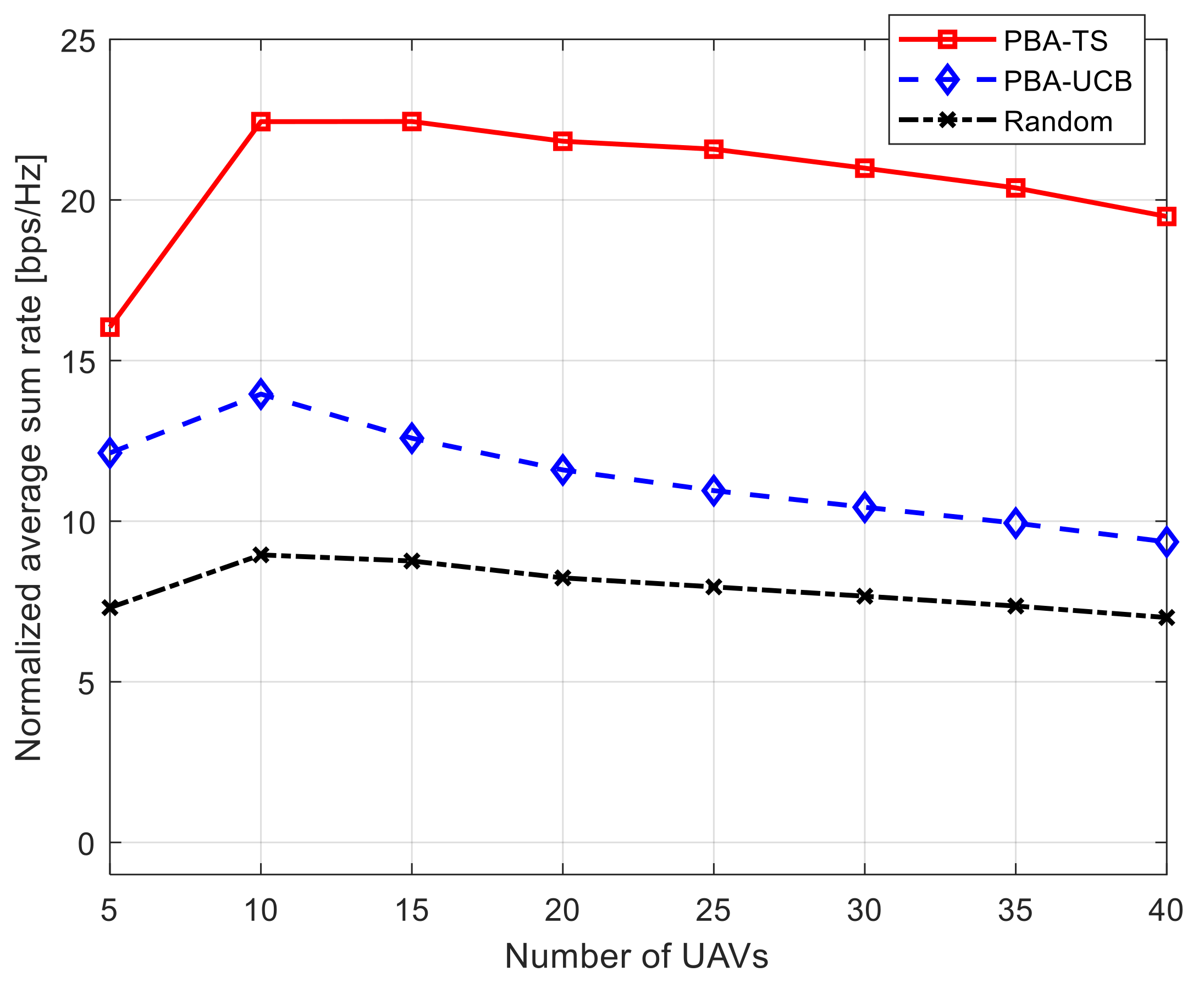
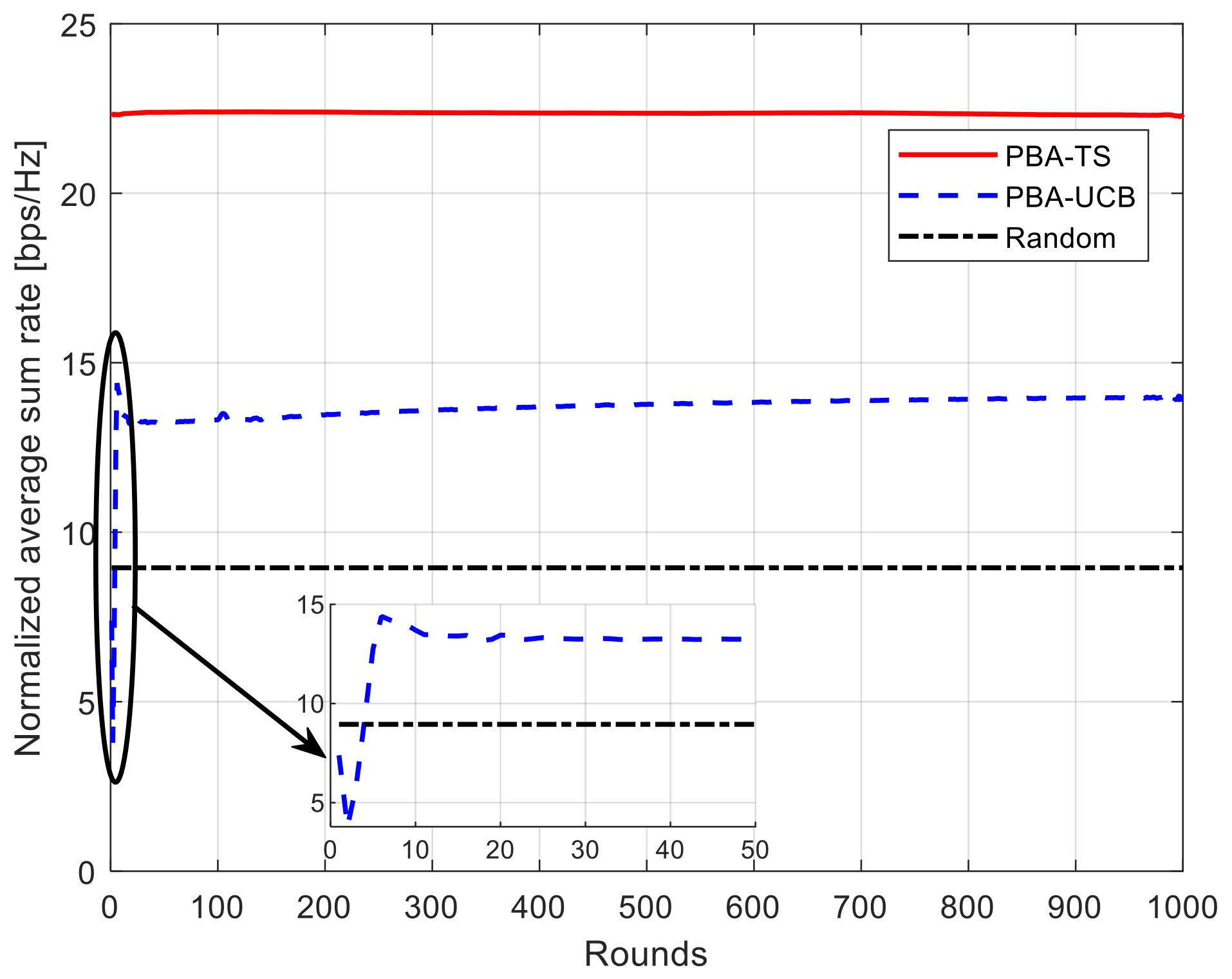
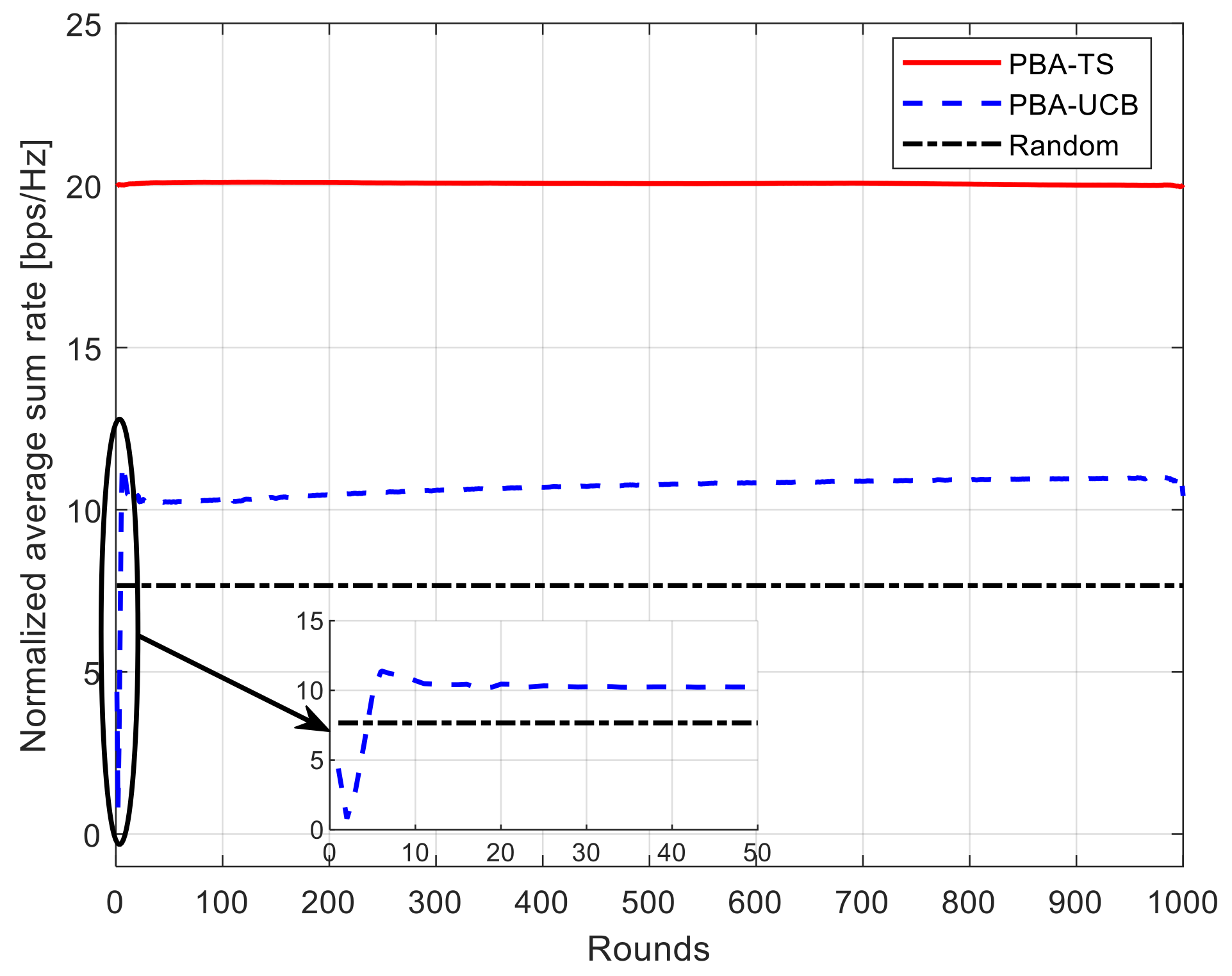
5.1. Average Total System Rate
5.2. Convergence Rate
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| DSA | Dynamic Spectrum Access |
| UAV | Unmanned Aerial Vehicle |
| CRN | Cognitive Radio Network |
| ETC | Electronic Toll Gate |
| MAB | Multi-armed Bandit |
| PBA-MAB | Power-Budget-Aware Multi-armed Bandit |
| UCB | Upper Confidence Bound |
| TS | Thompson Sampling |
| PBA-UCB | Power-Budget-Aware Upper Confidence Bound |
| PBA-TS | Power-Budget-Aware Thompson Sampling |
| PU | Primary User |
| SU | Secondary User |
| QoS | Quality of Service |
| ML | Machine Learning |
| RL | Reinforcement Learning |
| SINR | Signal-to-Interference-Plus-Noise Ratio |
| WSN | Wireless Sensor Network |
| CP | Control Plane |
| DP | Data Plane |
| VANET | Vehicle Ad hoc NETwork |
| iid | independent and identical distribution |
| WLAN | Wireless Local Area Network |
| LoS | Line of Sight |
| AWGN | Additive White Gaussian Noise |
| HetNets | Heterogeneous Networks |
| PHY | Physical layer |
| MAC | Medium Access Control layer |
| IoT | Internet of Things |
| VHF | Very High Frequency |
| UHF | Ultra High Frequency |
| mmWave | millimeter-wave |
| D2D | Device to Device |
References
- Mkiramweni, M.E.; Yang, C.; Li, J.; Zhang, W. A Survey of Game Theory in Unmanned Aerial Vehicles Communications. IEEE Commun. Surv. Tutor. 2019, 21, 3386–3416. [Google Scholar] [CrossRef]
- Mozaffari, M.; Saad, W.; Bennis, M.; Nam, Y.H.; Debbah, M. A Tutorial on UAVs for Wireless Networks: Applications, Challenges, and Open Problems. IEEE Commun. Surv. Tutor. 2019, 21, 2334–2360. [Google Scholar] [CrossRef] [Green Version]
- Panda, K.G.; Das, S.; Sen, D.; Arif, W. Design and Deployment of UAV-Aided Post-Disaster Emergency Network. IEEE Access 2019, 7, 102985–102999. [Google Scholar] [CrossRef]
- Hu, F.; Chen, B.; Zhu, K. Full Spectrum Sharing in Cognitive Radio Networks Toward 5G: A Survey. IEEE Access 2018, 6, 15754–15776. [Google Scholar] [CrossRef]
- Zhao, Q.; Swami, A. A Survey of Dynamic Spectrum Access: Signal Processing and Networking Perspectives. In Proceedings of the 2007 IEEE International Conference on Acoustics, Speech and Signal Processing—ICASSP ’07, Honolulu, HI, USA, 15–20 April 2007; Volume 4, pp. IV-1349–IV-1352. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Lee, W.y.; Vuran, M.C.; Mohanty, S. A survey on spectrum management in cognitive radio networks. IEEE Commun. Mag. 2008, 46, 40–48. [Google Scholar] [CrossRef] [Green Version]
- Haykin, S. Cognitive radio: Brain-empowered wireless communications. IEEE J. Sel. Areas Commun. 2005, 23, 201–220. [Google Scholar] [CrossRef]
- Drozd, A.L.; Mohan, C.K.; Varshney, P.K.; Werner, D.D. Multiobjective joint optimization and frequency diversity for efficient utilization of the RF transmission hyperspace. In Proceedings of the 2004 International Waveform Diversity Design Conference, Edinburgh, UK, 8–10 November 2004; pp. 1–7. [Google Scholar] [CrossRef]
- Sutton, R.S.; Barto, A.G. Reinforcement Learning: An Introduction; MIT Press: Cambridge, MA, USA, 2018. [Google Scholar]
- Kwasinski, A.; Wang, W.; Mohammadi, F.S. Reinforcement learning for resource allocation in cognitive radio networks. Mach. Learn. Future Wirel. Commun. 2020, 2020, 27–44. [Google Scholar] [CrossRef]
- Katehakis, M.N.; Veinott, A.F., Jr. The multi-armed bandit problem: Decomposition and computation. Math. Oper. Res. 1987, 12, 262–268. [Google Scholar] [CrossRef]
- Bubeck, S.; Cesa-Bianchi, N. Regret analysis of stochastic and nonstochastic multi-armed bandit problems. arXiv 2012, arXiv:1204.5721v2. [Google Scholar]
- Auer, P.; Cesa-Bianchi, N.; Fischer, P. Finite-time analysis of the multiarmed bandit problem. Mach. Learn. 2002, 47, 235–256. [Google Scholar] [CrossRef]
- Audibert, J.Y.; Munos, R.; Szepesvári, C. Exploration–exploitation tradeoff using variance estimates in multi-armed bandits. Theor. Comput. Sci. 2009, 410, 1876–1902. [Google Scholar] [CrossRef]
- Francisco-Valencia, I.; Marcial-Romero, J.R.; Valdovinos-Rosas, R.M. A comparison between UCB and UCB-Tuned as selection policies in GGP. J. Intell. Fuzzy Syst. 2019, 36, 5073–5079. [Google Scholar] [CrossRef]
- Olivieri, M.; Barnett, G.; Lackpour, A.; Davis, A.; Ngo, P. A scalable dynamic spectrum allocation system with interference mitigation for teams of spectrally agile software defined radios. In Proceedings of the First IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks (DySPAN 2005), Baltimore, MD, USA, 8–11 November 2005; pp. 170–179. [Google Scholar] [CrossRef]
- Agrawal, S.; Goyal, N. Further optimal regret bounds for thompson sampling. Artif. Intell. Stat. 2013, 31, 99–107. [Google Scholar]
- Sun, Y.; Peng, M.; Zhou, Y.; Huang, Y.; Mao, S. Application of Machine Learning in Wireless Networks: Key Techniques and Open Issues. IEEE Commun. Surv. Tutor. 2019, 21, 3072–3108. [Google Scholar] [CrossRef] [Green Version]
- Huang, Y.; Xu, C.; Zhang, C.; Hua, M.; Zhang, Z. An Overview of Intelligent Wireless Communications using Deep Reinforcement Learning. J. Commun. Inf. Netw. 2019, 4, 15–29. [Google Scholar] [CrossRef]
- Wilhelmi, F.; Cano, C.; Neu, G.; Bellalta, B.; Jonsson, A.; Barrachina-Muñoz, S. Collaborative spatial reuse in wireless networks via selfish multi-armed bandits. Ad Hoc Netw. 2019, 88, 129–141. [Google Scholar] [CrossRef] [Green Version]
- Zhao, Q.; Sadler, B.M. A Survey of Dynamic Spectrum Access. IEEE Signal Process. Mag. 2007, 24, 79–89. [Google Scholar] [CrossRef]
- Yucek, T.; Arslan, H. A survey of spectrum sensing algorithms for cognitive radio applications. IEEE Commun. Surv. Tutor. 2009, 11, 116–130. [Google Scholar] [CrossRef]
- Wang, J.; Ghosh, M.; Challapali, K. Emerging cognitive radio applications: A survey. IEEE Commun. Mag. 2011, 49, 74–81. [Google Scholar] [CrossRef]
- Liang, Y.C.; Chen, K.C.; Li, G.Y.; Mahonen, P. Cognitive radio networking and communications: An overview. IEEE Trans. Veh. Technol. 2011, 60, 3386–3407. [Google Scholar] [CrossRef]
- Srinivasa, S.; Jafar, S.A. Cognitive Radios for Dynamic Spectrum Access—The Throughput Potential of Cognitive Radio: A Theoretical Perspective. IEEE Commun. Mag. 2007, 45, 73–79. [Google Scholar] [CrossRef]
- Akan, O.B.; Karli, O.B.; Ergul, O. Cognitive radio sensor networks. IEEE Netw. 2009, 23, 34–40. [Google Scholar] [CrossRef]
- Xing, Y.; Chandramouli, R.; Mangold, S.; N, S. Dynamic spectrum access in open spectrum wireless networks. IEEE J. Sel. Areas Commun. 2006, 24, 626–637. [Google Scholar] [CrossRef] [Green Version]
- Theis, N.C.; Thomas, R.W.; DaSilva, L.A. Rendezvous for Cognitive Radios. IEEE Trans. Mob. Comput. 2011, 10, 216–227. [Google Scholar] [CrossRef] [Green Version]
- Homssi, B.A.; Al-Hourani, A.; Krusevac, Z.; Rowe, W.S.T. Machine Learning Framework for Sensing and Modeling Interference in IoT Frequency Bands. IEEE Internet Things J. 2021, 8, 4461–4471. [Google Scholar] [CrossRef]
- Xiao, Z.; Li, F.; Jiang, H.; Bai, J.; Xu, J.; Zeng, F.; Liu, M. A Joint Information and Energy Cooperation Framework for CR-Enabled Macro–Femto Heterogeneous Networks. IEEE Internet Things J. 2020, 7, 2828–2839. [Google Scholar] [CrossRef]
- Farag, H.M.; Mohamed, E.M. Soft decision cooperative spectrum sensing with noise uncertainty reduction. Pervasive Mob. Comput. 2017, 35, 146–164. [Google Scholar] [CrossRef]
- Erdelj, M.; Natalizio, E. UAV-assisted disaster management: Applications and open issues. In Proceedings of the 2016 International Conference on Computing, Networking and Communications (ICNC), Kauai, HI, USA, 15–18 February 2016; pp. 1–5. [Google Scholar] [CrossRef] [Green Version]
- Merwaday, A.; Tuncer, A.; Kumbhar, A.; Guvenc, I. Improved Throughput Coverage in Natural Disasters: Unmanned Aerial Base Stations for Public-Safety Communications. IEEE Veh. Technol. Mag. 2016, 11, 53–60. [Google Scholar] [CrossRef]
- Lee, S.; Har, D.; Kum, D. Drone-Assisted Disaster Management: Finding Victims via Infrared Camera and Lidar Sensor Fusion. In Proceedings of the 2016 3rd Asia-Pacific World Congress on Computer Science and Engineering (APWC on CSE), Nadi, Fiji, 4–6 December 2016; pp. 84–89. [Google Scholar] [CrossRef]
- Rivera, A.; Villalobos, A.; Monje, J.; Mariñas, J.; Oppus, C. Post-disaster rescue facility: Human detection and geolocation using aerial drones. In Proceedings of the 2016 IEEE Region 10 Conference (TENCON), Singapore, 22–26 November 2016; pp. 384–386. [Google Scholar] [CrossRef]
- Kobayashi, T.; Matsuoka, H.; Betsumiya, S. Flying Communication Server in case of a Largescale Disaster. In Proceedings of the 2016 IEEE 40th Annual Computer Software and Applications Conference (COMPSAC), Atlanta, GA, USA, 10–14 June 2016; Volume 2, pp. 571–576. [Google Scholar] [CrossRef]
- Sánchez-García, J.; García-Campos, J.; Toral, S.L.; Reina, D.G.; Barrero, F. A Self Organising Aerial Ad Hoc Network Mobility Model for Disaster Scenarios. In Proceedings of the 2015 International Conference on Developments of E-Systems Engineering (DeSE), Dubai, United Arab Emirates, 13–14 December 2015; pp. 35–40. [Google Scholar] [CrossRef]
- Ejaz, W.; Ahmed, A.; Mushtaq, A.; Ibnkahla, M. Energy-efficient task scheduling and physiological assessment in disaster management using UAV-assisted networks. Comput. Commun. 2020, 155, 150–157. [Google Scholar] [CrossRef]
- Zhan, P.; Yu, K.; Swindlehurst, A.L. Wireless Relay Communications with Unmanned Aerial Vehicles: Performance and Optimization. IEEE Trans. Aerosp. Electron. Syst. 2011, 47, 2068–2085. [Google Scholar] [CrossRef]
- Zhang, S.; Shi, S.; Gu, S.; Gu, X. Power Control and Trajectory Planning Based Interference Management for UAV-Assisted Wireless Sensor Networks. IEEE Access 2020, 8, 3453–3464. [Google Scholar] [CrossRef]
- Baek, J.; Han, S.I.; Han, Y. Energy-Efficient UAV Routing for Wireless Sensor Networks. IEEE Trans. Veh. Technol. 2020, 69, 1741–1750. [Google Scholar] [CrossRef]
- Seliem, H.; Shahidi, R.; Ahmed, M.H.; Shehata, M.S. Drone-Based Highway-VANET and DAS Service. IEEE Access 2018, 6, 20125–20137. [Google Scholar] [CrossRef]
- Lai, T.L.; Robbins, H. Asymptotically efficient adaptive allocation rules. Adv. Appl. Math. 1985, 6, 4–22. [Google Scholar] [CrossRef] [Green Version]
- Thompson, W.R. On the likelihood that one unknown probability exceeds another in view of the evidence of two samples. Biometrika 1933, 25, 285–294. [Google Scholar] [CrossRef]
- Toldov, V.; Clavier, L.; Loscrí, V.; Mitton, N. A Thompson sampling approach to channel exploration-exploitation problem in multihop cognitive radio networks. In Proceedings of the 2016 IEEE 27th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Valencia, Spain, 4–7 September 2016; pp. 1–6. [Google Scholar] [CrossRef] [Green Version]
- Bonnefoi, R.; Moy, C.; Palicot, J. Advanced metering infrastructure backhaul reliability improvement with cognitive radio. In Proceedings of the 2016 IEEE International Conference on Smart Grid Communications (SmartGridComm), Sydney, Australia, 6–9 November 2016; pp. 230–236. [Google Scholar] [CrossRef] [Green Version]
- Kalathil, D.; Nayyar, N.; Jain, R. Decentralized Learning for Multiplayer Multiarmed Bandits. IEEE Trans. Inf. Theory 2014, 60, 2331–2345. [Google Scholar] [CrossRef] [Green Version]
- Liu, K.; Zhao, Q.; Krishnamachari, B. Decentralized multi-armed bandit with imperfect observations. In Proceedings of the 2010 48th Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, IL, USA, 29 September–1 October 2010; pp. 1669–1674. [Google Scholar] [CrossRef]
- Anandkumar, A.; Michael, N.; Tang, A.K.; Swami, A. Distributed Algorithms for Learning and Cognitive Medium Access with Logarithmic Regret. IEEE J. Sel. Areas Commun. 2011, 29, 731–745. [Google Scholar] [CrossRef] [Green Version]
- Mohamed, E.M.; Hashima, S.; Aldosary, A.; Hatano, K.; Abdelghany, M.A. Gateway Selection in Millimeter Wave UAV Wireless Networks Using Multi-Player Multi-Armed Bandit. Sensors 2020, 20, 3947. [Google Scholar] [CrossRef]
- Takeuchi, S.; Hasegawa, M.; Kanno, K.; Uchida, A.; Chauvet, N.; Naruse, M. Dynamic channel selection in wireless communications via a multi-armed bandit algorithm using laser chaos time series. Sci. Rep. 2020, 10, 1574. [Google Scholar] [CrossRef]
- Oshima, K.; Onishi, T.; Kim, S.J.; Ma, J.; Hasegawa, M. Efficient wireless network selection by using multi-armed bandit algorithm for mobile terminals. Nonlinear Theory Its Appl. IEICE 2020, 11, 68–77. [Google Scholar] [CrossRef]
- Mohamed, E.M.; Hashima, S.; Hatano, K.; Fouda, M.M.; Fadlullah, Z.M. Sleeping Contextual/Non-Contextual Thompson Sampling MAB for mmWave D2D Two-Hop Relay Probing. IEEE Trans. Veh. Technol. 2021, 70, 12101–12112. [Google Scholar] [CrossRef]
- Hashima, S.; Hatano, K.; Takimoto, E.; Mahmoud Mohamed, E. Neighbor Discovery and Selection in Millimeter Wave D2D Networks Using Stochastic MAB. IEEE Commun. Lett. 2020, 24, 1840–1844. [Google Scholar] [CrossRef]
- Bhardwaj, P.; Panwar, A.; Ozdemir, O.; Masazade, E.; Kasperovich, I.; Drozd, A.L.; Mohan, C.K.; Varshney, P.K. Enhanced Dynamic Spectrum Access in Multiband Cognitive Radio Networks via Optimized Resource Allocation. IEEE Trans. Wirel. Commun. 2016, 15, 8093–8106. [Google Scholar] [CrossRef]
- Miao, G.; Himayat, N.; Li, G.Y.; Talwar, S. Low-Complexity Energy-Efficient Scheduling for Uplink OFDMA. IEEE Trans. Commun. 2012, 60, 112–120. [Google Scholar] [CrossRef] [Green Version]
- Gupta, P.; Kumar, P. The capacity of wireless networks. IEEE Trans. Inf. Theory 2000, 46, 388–404. [Google Scholar] [CrossRef] [Green Version]
- Arnold, P.; Bayer, N.; Belschner, J.; Zimmermann, G. 5G radio access network architecture based on flexible functional control/user plane splits. In Proceedings of the 2017 European Conference on Networks and Communications (EuCNC), Oulu, Finland, 12–15 June 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Chapelle, O.; Li, L. An empirical evaluation of thompson sampling. Adv. Neural Inf. Process. Syst. 2011, 24, 2249–2257. [Google Scholar]
| Notation | Value |
|---|---|
| No. of armed bandits | 10 |
| Simulation area | 5 km × 5 km |
| PU Tx power | 24 dBm |
| 30 dBm | |
| W | 10 MHz |
| 5.8 GHz | |
| c | m/s |
| 3 | |
| 30 dB | |
| 5 dB | |
| −100 dBm | |
| 0.5 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Amrallah, A.; Mohamed, E.M.; Tran, G.K.; Sakaguchi, K. Enhanced Dynamic Spectrum Access in UAV Wireless Networks for Post-Disaster Area Surveillance System: A Multi-Player Multi-Armed Bandit Approach. Sensors 2021, 21, 7855. https://doi.org/10.3390/s21237855
Amrallah A, Mohamed EM, Tran GK, Sakaguchi K. Enhanced Dynamic Spectrum Access in UAV Wireless Networks for Post-Disaster Area Surveillance System: A Multi-Player Multi-Armed Bandit Approach. Sensors. 2021; 21(23):7855. https://doi.org/10.3390/s21237855
Chicago/Turabian StyleAmrallah, Amr, Ehab Mahmoud Mohamed, Gia Khanh Tran, and Kei Sakaguchi. 2021. "Enhanced Dynamic Spectrum Access in UAV Wireless Networks for Post-Disaster Area Surveillance System: A Multi-Player Multi-Armed Bandit Approach" Sensors 21, no. 23: 7855. https://doi.org/10.3390/s21237855
APA StyleAmrallah, A., Mohamed, E. M., Tran, G. K., & Sakaguchi, K. (2021). Enhanced Dynamic Spectrum Access in UAV Wireless Networks for Post-Disaster Area Surveillance System: A Multi-Player Multi-Armed Bandit Approach. Sensors, 21(23), 7855. https://doi.org/10.3390/s21237855







