Abstract
This paper proposes a new blind, color image watermarking method using fast Walsh–Hadamard transformation (FWHT) and multi-channel fractional Legendre–Fourier moments (MFrLFMs). The input host color image is first split into 4 × 4 non-interfering blocks, and the MFrLFMs are computed for each block, where proper MFrLFMs coefficients are selected and FWHT is applied on the selected coefficients. The scrambled binary watermark has been inserted in the quantized selected MFrLFMs coefficients. The proposed method is a blind extraction, as the original host image is not required to extract the watermark. The proposed method is evaluated over many visual imperceptibility terms such as peak signal-to-noise ratio (PSNR), normalized correlation (NC), and bit error rate. The robustness of the proposed method is tested over several geometrical attacks such as scaling, rotation, cropping, and translation with different parameter values. The most widely recognized image processing attacks are also considered, e.g., compressing and adding noise attacks. A set of combination attacks are also tested to analyze the robustness of the proposed scheme versus several attacks. The proposed model’s experimental and numerical results for invisibility and robustness were superior to the results of similar watermarking methods.
1. Introduction
Copyright protection over the Internet has become a big challenge because it deals with securing the transmitted digital content through the transition medium over the internet. Therefore, the use of digital image watermarking systems has become a hot research area. It is widely used in the copyright protection of images and security from several unwanted modifications of digital content, such as tampering and forgery over these transitions [1]. Digital watermarking can conceal any data type, including images, audio, video, and text in chosen digital media such as color images [2]. Two essential domains are used with the applied watermarking domain: the spatial working domain [3] and the frequency working domain [4]. In the spatial domain method, embedding the watermark can be realized by explicitly modifying the image pixels. It has the benefits of accessible execution at low computing costs. The most prevalent techniques in the spatial domain are LSB, correlation-based methods, histogram shifting, and speed spectral methods.
Furthermore, the most common techniques are primarily used in the frequency domain such as discrete Fourier transformation, discrete cosine transformation, discrete wavelet transformation, and singular value decomposition. Compared with spatial domain methods, the transform domain methods are more robust to several attacks, with high invisibility [5]. The watermark is concealed in the transformed coefficients in the transform domain, resulting in a minor change in image pixel correlation, preserving image quality much more [6].
According to the extraction method, there are three common types of watermarking systems: blind, non-blind, and semi-blind watermarking [5]. In a blind watermarking [7] system, the host cover image is not required in the watermark extraction process; it just needs the watermarked image. In non-blind [8] watermarking, the host and the watermarked images are both required to extract the watermark image. In semi-blind watermarking [9], the watermarked image and security key are required to engage the extraction process fully.
Concerning the desired security purpose of the watermarking models, there are three common characteristics: robustness [10], semi-fragile [11], and fragile [12] watermarking models. The robustness of the watermark system is that it resists a specific set of transformations such as geometric attacks. It is extensively used in copyright protection. The semi-fragile watermark system resists benign transformations only and can be detected after slight changes. It is used to detect and locate malignant transformations. The fragile watermark system cannot be detected after slight modification. It can be destroyed because it is highly sensitive to any slight modification; it is extensively used in tamper detection for proving integrity.
In recent years, many authors have introduced many watermarking methods in using color images; therefore, color images play a significant role in real-life applications such as copyright provisions and image authenticity for medical applications and other similar fields.
Many researchers have presented realistic watermarking approaches in the spatial and frequency working domains. Parekh et al. [13] introduced a blind watermarking method in the spatial domain by modifying the luminosity component, Y, of the transformed YCbCr model. The host color image is split into 8 × 8 blocks, and a binary watermark has been embedded in a sorted correlation of values between corresponding blocks of sub-images. This scheme has been personalized, as it is low in robustness capabilities against various attacks. Su and Chen [14] introduced a watermarking scheme in the spatial domain to solve this problem. A binary logo image is embedded directly in distributed features in the direct current (DC) coefficients. This method proved to be a robust watermarking system against several geometric and standard signal attacks.
Owing to the robustness and indiscernibility of the watermarking systems in the frequency domain, many researchers proposed several watermarking strategies in this domain. Yuan et al. [15] proposed an image watermarking method for copyright protection. The color host image is divided into blocks, which are modified using (2D-DCT). The color logo image is embedded in the chosen intermediate coefficients of these selected blocks. The scheme is robust to most popular image processing attacks. Fares et al. [16] suggested a new image watermarking method based on discrete Fourier transform (DFT) of a fractional quaternion type. The watermark bits are concealed in the intermediate frequency band of the transformed RGB components by adjusting the least significant bits of the quantified magnitudes.
Many authors appealed to utilize the wavelet transformations in many watermarking schemes, in which it is a powerful tool that has been widely used in signal and image processing [17]. However, at the same time, it still has significant disadvantages such as (i) shift sensibility, any transitions in the input signal lead to unexpected changes in wavelet coefficients; (ii) inadequate directionality, since wavelet coefficients disclose only three spatial orientations; (iii) non-stationary signal, in view of the lake of phase information; (iv) computational complexity, especially for wavelet tree and numerous decomposition; and (v) complex accurate compilation of the mother wavelet and sub-bands mainly when applied in complicated fields. Our proposed method tried to overcome these significant problems using a hybrid technique by utilizing FWHT and MFrLFMs benefits to release a new, robust watermarking methodology.
Many researchers have touched upon the concept of perceiving the color image copyrights efficiently by using an advanced hybrid combination of the spatial and frequency domains techniques to achieve fast computation features of the spatial domain and at the same time take advantage of the durability of the frequency domain techniques. Yuan et al. [18] introduced a blind watermarking method based on a combination of spatial and frequency domains techniques. It was achieved by applying quantization steps on the DCT and discrete Hartley transformation (DHT) to embed a color logo image into the standard direct current frequencies blocks of the discrete cosine transform and DHT components. The watermark is extracted in a blind extraction manner by applying an inverse embedding process. The scheme is highly robust to many attacks.
The remnant of this paper is structured as follows. Section 2 handles diverse related works. Section 3 includes the essential preliminaries that have been used in the proposed method. Section 4 illustrates the proposed watermarking methodology in a detailed manner. Section 5 documents the experiment’s numerical results with discussion, followed by the conclusion in Section 6.
2. Related Work
Color medical images are the result of medical imaging of the interior of the human body for clinical analysis and medical intervention to reveal internal structures hidden by the skin and bones for diagnosing and treating disease. Medical images have also been established as a public database for medical purposes.
Due to the rapid increase in different types of attacks on color image watermarking systems, the successful extraction of the embedded watermark has become a common challenge in any current watermarking system because of higher sensitivity for different geometric, signal processing, and combination attacks. Any slight change in image pixel geometry leads to a false extraction process.
For this, many researchers have enhanced their efforts toward realizing many watermarking systems based on different invariant moments to attain the highest robustness and invisibility of watermarking systems. Ma et al. [19] introduced a robust watermarking method according to polar harmonic Fourier moments (PHFMs) and chaotic maps; accurate and robust PHFMs of the original cover image are computed and chosen depending on Gaussian numerical integration (GNI). The watermark was shuffled using a tent map and then concealed in the amplitudes of the selected PHFMs. The watermark extraction was done by applying PHFMs on watermarked images and the inverse of the embedding process in a blind extraction; this scheme is robust to different common geometric attacks. Yamni et al. [20] suggested a digital watermark algorithm based on fractional Charlier moments (FCMs) and singular value decomposition (SVD). In this method, the host cover images are split into 8 × 8 blocks. Then, the FCMs are computed for every block to obtain the FCM matrix, which SVD has decomposed by using adaptive pixel embedding with a quantization step. The method introduced the best superior fineness to reconstruct the watermarked images reasonably.
Wang et al. [21] introduced a watermarking algorithm depending on the TRHFMs’ computation of the input image. The selection of TRHFMs is randomly made using logistic maps to generate a zero-watermarked image by applying XOR between a binary watermark image and a binary feature image. This algorithm is robust to diverse types of attacks compared to similar methods. Ernawan [22] introduced a method using the Tchebichef-moments-based watermarking concept. The binary watermark is first shuffled using Arnold transformation and then concealed in the randomly selected Tchebichef moments matrix. This scheme is resistant to different classes of attacks, especially processing attacks. Singh et al. [23] introduced a watermarking system for medical images using PHFT, where the accurate computation of the chosen moment leads to a robust extraction process. Yamni et al. [24] introduced a blind watermarking method using radial Krawtchouk moments and an MLNCML chaotic system. The scheme was tested over standard signal processing and geometric attacks. Ernawan and Kabir [25] introduced a scheme using Tchebichef moments. The watermark logo is shuffled using an Arnold cat map and then embedded in the modified part of the selected moments over the chosen embedding blocks. Finally, the scheme is assessed for robustness versus widespread attacks.
Many researchers have revealed the use of quaternion-type moments (QTMs) in most current watermarking methods due to the ability and the advantages of dealing with cover images in a holistic manner [26]. It is more invariant to different image amendments such as rotation, translation, and scaling, since it can eliminate the transmutation parameters due to its invariance properties. It is also more efficient for computational analysis. As a result, Darwish et al. [27] introduced a scheme based on QLFMs and logistic maps. Logistic maps were employed on random selections of QLFM coefficients. The extraction process is the inverse operation of the embedding process. This method is successful in decreasing the computational time compared with other similar classical quaternion methods. This method achieves a high robustness level against more common attacks.
Hosny and Darwish [28] proposed a watermarking method of the quaternion type using radial substituted Chebyshev moments (QRSCMs) in a holistic way to deal with color images. This method successfully overcame the limitations of other similar methods, such as low-level accuracy, low-speed computation, and instability changes over the coefficient matrix. Hosny and Darwish [29] introduced an image watermarking method based on fast and accurate QLFMs that first scrambled the binary watermark using Arnold transformation and then embedded this scrambled watermark in the quantized version of selected QLFMs using dither modulation. Li et al. [30] introduced a watermarking method on color images using Hadamard transformation and Zernike moments of a quaternion-type; quaternion Hadamard transform (QHT) is holistically mutated. Then the transformed components were divided into 8 × 8 non-overlapping blocks to apply Schur decomposition, with the watermark embedded on a selected block. The scheme proved its ability to overcome many counterattacks and its robustness against most common geometric attacks. In addition, the scheme lacks evaluation over combined attacks. Liu et al. [31] introduced a scheme on color images using QPHT block magnitudes and Bessel Key form distribution (BKF); the binary watermark was embedded in the amplitudes of the selected precise moment of the cover images blocks. This scheme introduced high imperceptibility compared with similar methods; however, it is still sensitive to most common geometric attacks. Xia et al. [32] introduced a method for copyrights provisions on medical images using QPHFMs. Computing QPHFMs generate the key image to the input CT images to reconstruct the features image, shuffling binary bit pixels using a chaotic system and then applying XOR between the generated feature image and the binary sequence image. Huynh-The et al. [33] proposed a blind color image watermarking scheme depending on optimal selective color channel bits embedding in two middle-frequency bands of quantized coefficients. Xia et al. [34] introduced a robust method on medical images based on QPHFMs using a sped-up robust feature (SURF) to generate multiple zero-watermarking systems. The method is superior in robustness to different complex attacks. Z. Xia et al. [35] introduced a Null-watermarking method on color medical images based on precise quaternion polar harmonic Fourier moments (PQPHFMs) and chaotic maps principles.
Similarly, Yamni et al. [36] introduced an image watermarking scheme based on FrCMMs and SVD for copyrights provisions. Liu et al. [37] introduced a fractional-order Krawtchouk watermark scheme depending on the decomposition of eigenvalues. This scheme is successful at achieving high robustness compared with other classical integer-order Krawtchouk moments. Yang et al. [38] derived a new fractional order of Jacobi–Fourier moments using mixed low-order moment attributes to increase image descriptor representation and robustness. Xiao et al. [39] derived FrDCMs by using the decomposition eigenvalues of the kernel matrix and applied it to a proposed watermarking scheme. Hosny et al. [40] proposed a new zero-watermarking method for color images based on accurate computation of multi-channel fractional Legendre-Fourier moments (MFrLFMs) and Arnold encryption to generate a robust watermarking system. Hosny et al. [41] proposed a new multi-channel fractional exponent moment order (MFrEM) to construct a robust color image watermarking method. In [42], the authors proposed a semi-blind watermarking method based on combined DWT-CT and Schur SVD decompositions; the method attained a high visual imperceptibility and robustness.
In the field of medical image authentication, many authors suggested many watermarking systems to achieve data privacy and at the same time preserve image quality as possible to manage disease diagnostics. Elbası [43] proposed a watermarking method on medical images based on M-SVD utilizing DWT to embed binary watermarks into medical images. The author succeeds in scoring accurate quality measurements of the watermarked images utilizing the proposed M-SVD technique. Huh and Kim [44] introduced a location-based mobile system that provides a healthcare structure for users to find patients’ location and disease diagnostic easily. Hosny and Darwish [45] proposed multiple zero-watermarking methods based on FrMGMs and scrambled to embed multiple watermarks into color medical images to present a high securing and robust watermarking system. Soualmi et al. [46] introduced multiple blind watermarking schemes based on LWT and QR decomposition for medical images authentication. Sun and Bo [47] proposed a blind watermarking model to embed a binary watermark image into a color medical image utilizing the benefits of wavelet PCA, low-frequency sub-bands, and HSV wavelet coefficients.
Based on this review of major revisions for most related methods, the proposed method’s contributions are as follows:
- Our method contributes to this evidence by using MFrLFMs. It is known for its stability and invariance to many geometric attacks, which keep robust capability over many attacks such as scaling, rotation, translation, etc.
- In addition, MFrLFMs are not restricted to integer-order values, which give them a high ability to represent the finest details in the image rather than their rival’s orthogonal polynomials of integer order.
- The use of Walsh–Hadamard transform comes under generalized Fourier transforms, known as low-computations compilations. Hadamard transform is a perpendicular function, which is composed of (−1 and +1) values only. Therefore, there is no data redundancy, which makes it widely used in many image processing analyses. FWHT is elastic to low-quality compression compared with other transformations such as traditional DCT and DWT, making it robust to most common image processing attacks.
- The proposed method introduced a new combination method of these multi-channel fractional Legendre–Fourier moments (MFrLFMs) and Hadamard transformation in a holistic way to achieve the main target of the proposed method, which represents robustness to both geometric and image processing attacks.
- The evaluation of our proposed method has been assessed for many common types of attacks and visual imperceptibility measurements.
3. Preliminaries
3.1. Fast Walsh–Hadamard Transformation Technique
The Hadamard transform is also known as the Walsh–Hadamard transform, Hadamard–Rademacher–Walsh transform, fast Walsh–Hadamard transform, or Walsh–Fourier transform and it comes under a summed-up class of Fourier transformation. It has the benefits of simple computational complexity among all similar existing transforms [48]. It is orthogonal, symmetric, and has only two values (−1, +1), which results in isomorphism with no data redundancy. The FWHT has been extensively utilized in many image processing algorithms, digital steganography, and compression because it provides fast coefficient computation and fast reconstruction advantages. The fast Walsh–Hadamard transform is represented as follows:
The refers to the FWHT of , while the refers to the Hadamard matrix of squares.
The 4 × 4 Hadamard matrix is represented in the form
The main formula of the FWHT transformation is represented as
where values are based on the values of , where .
The inverse of the fast Walsh–Hadamard transform is represented as
where is the FWHT of the function, .
3.2. MFrLFM Representation for RGB Color Image
Fractional-order polynomials are not restricted to integer-order values compared with other similar orthogonal moments, which give it a high ability to represent the fine details in an image rather than their rivals’ orthogonal polynomials of integer order [49]. These descriptors are also invariant to geometrical transformations (rotation, scaling, and translation). It is defined over a unit circle as follows:
where represents the essential functions of the Legendre–Fourier moments of fractional orders.
The function denotes the RGB color images, the asterisk symbol “*” refers to the complex conjugate; .
The multi-channel fractional-order moments for all RGB color channels of the input image are computed using
Therefore, the original image is reconstructed by the reliance on the orthogonal property [50] of the fractional-order LFMs as follows:
where refer to the reconstructed image elements R, G, B of
3.3. Geometrical Invariances of MFrLFMs
Robust watermarking algorithms are based on their invariance ability to RST geometric transformations. These RST invariants are derived and represented in a mathematical form in the following sub-sections.
3.3.1. Rotational Invariance
Suppose that denotes the original image and denotes the rotated image with a rotational angle where
The MFrLFMs of is computed as follows:
Sparingly, it can be written as
Since, ; then
Equation (10) proves the rotation invariance of MFrLFMs.
3.3.2. Scale Invariance
Let refer to the original image and be the scaled image where
The MFrLFM of the scaled image is computed as follows:
The is the scaled fractional order.
Finally, the MFrLFM of the scaled image is computed as
3.3.3. Translation Invariance
Translation invariance is realized when repositioning the original coordinates to synchronize with the centric points of the color image [51] and are defined as
The central MFrLFMs are represented mathematically as
3.4. Accurate MFrLFM Computation
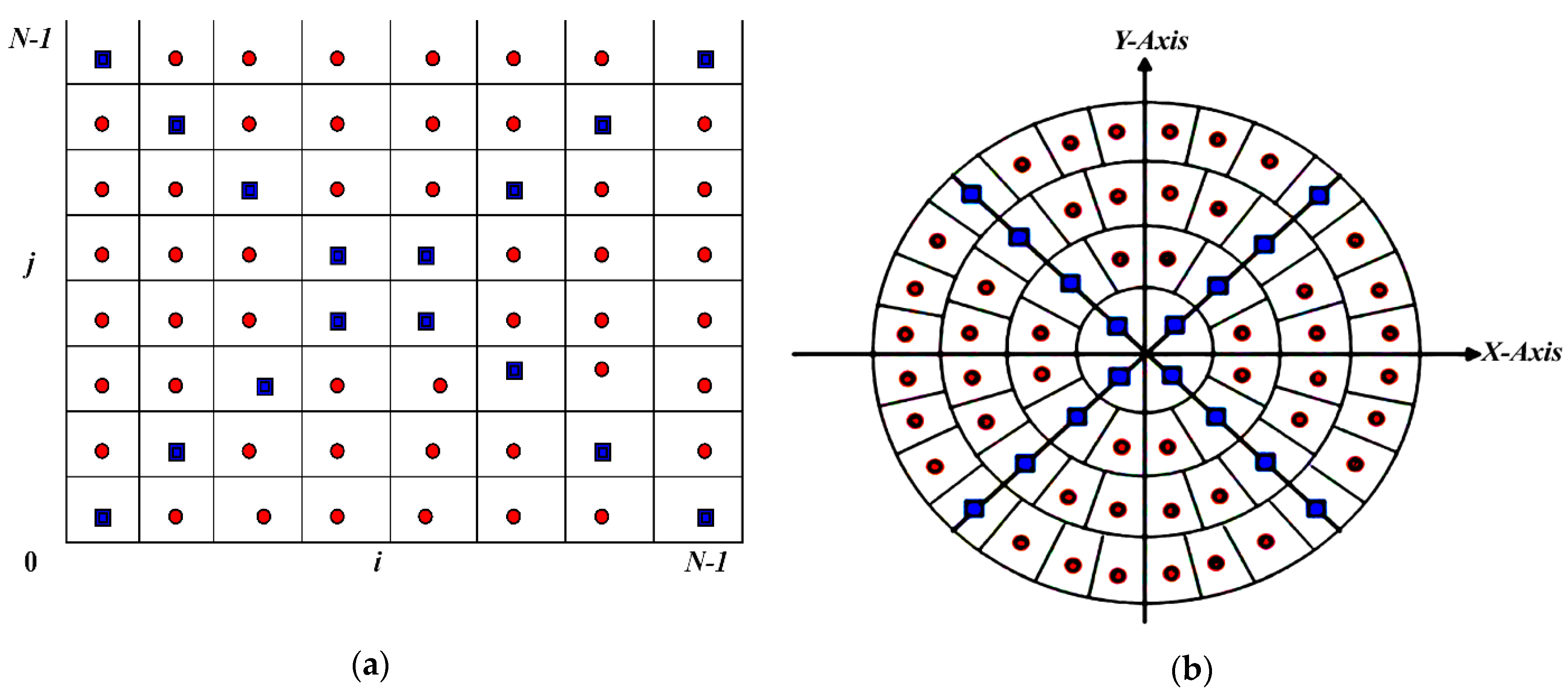
The selection of the accurate computation of MFrLFMs is one of the basic foundation rules of the proposed watermarking method. Any geometric distortion directly affects the robustness of the watermarking system over different geometric attacks, especially in medical images due to its high sensitivity to any distortion, which in turn leads to misdiagnosis. The computing of an accurate, kernel-based approach was introduced in [52]. MFrLFMs can be represented in polar coordinates (see Figure 1a) since they are symbolized in a unit circle. Each red point possesses eight point similarities, whereas each blue point possesses four similarities (see Figure 1b). The coefficient matrix of the MFrLFMs is calculated utilizing the equations:
where
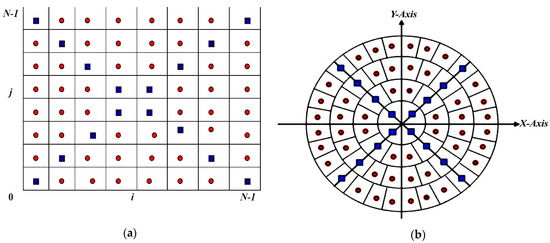
Figure 1.
(a) Cartesian coordinates; (b) polar coordinates.
The kernels functions [53] are defined as
where
The upper and lower limits are
Compute in the exact form
Then, calculate the radial kernel using suitable, accurate computation in [54] using the following equation:
Symbols “” and “t” indicate the weights, where and , the value of can be explained in respect of the integrity of and is the order of numeral integration, and the value of w is restricted where .
4. Proposed Blind Watermarking
In this paper, we propose a robust blind color image watermarking model. In the watermark extraction phase, the embedded binary watermark bits can be extracted from the selected MFrLFM coefficient magnitudes in a blind extraction manner. The scrambled watermark bit information is concealed in the accurate RST invariants’ selection of MFrLFM magnitudes of the host color image, transformed by fast Walsh–Hadamard transform to generate a robust watermarking system. The host image is not required; there is only a need for the color watermarked image to carry out the entire extraction procedures, preserving image quality as much as possible.
Blind watermark introduced a crucial function, especially in medical images. It is known for its ability to preserve image quality to guarantee an exact diagnosis of the disease and to protect patient data from unwanted malicious attacks.
The idea behind deploying blind watermarking in our proposed method is to increase security, robustness, and imperceptibility. Furthermore, identity authentication must be provided for medical images, since every pixel in these images plays an essential role and represents essential patient data. Any distortion in these images’ pixels leads to disease misdiagnosis. It also has the advantage of a simple extraction; the watermark image can be extracted without needing the original host cover image, which reduces the time consumed during the extraction process and preserves image quality.
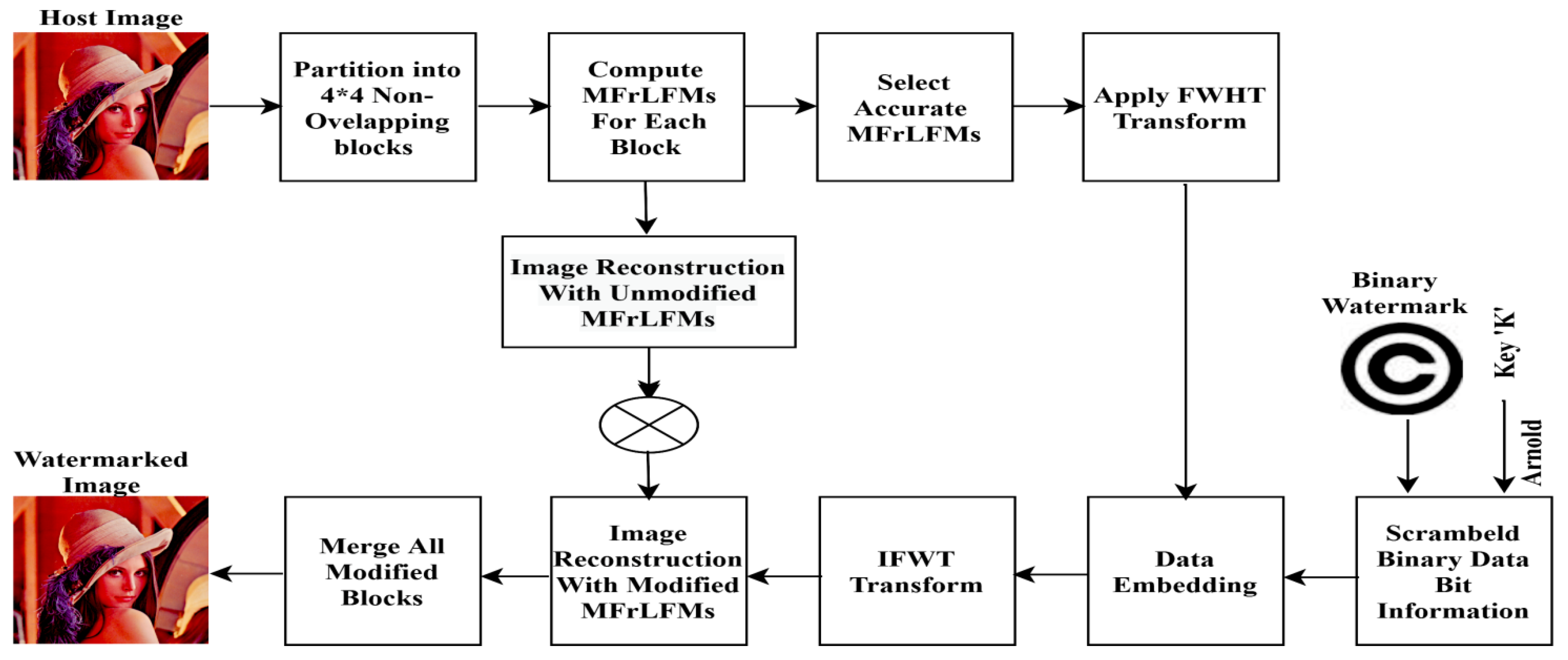
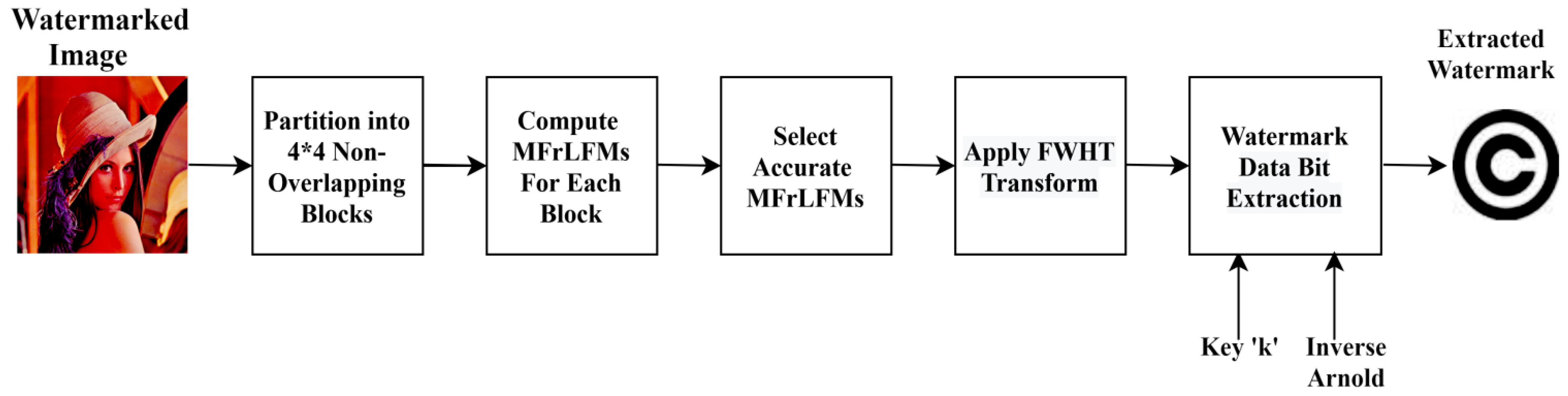
Sequentially, the detailed watermarking method for embedding and extraction processes is listed with illustrative diagrams as shown in Figure 2 and Figure 3, sequentially.
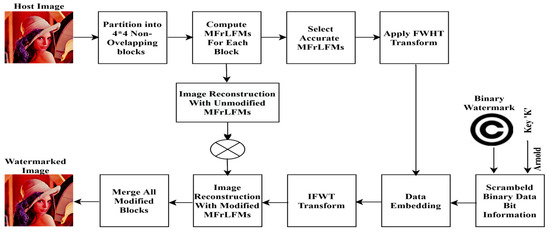
Figure 2.
Proposed watermark embedding.
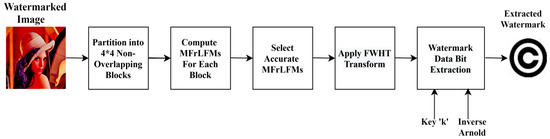
Figure 3.
Proposed watermark extraction.
4.1. Watermarking Embedding Process
Assume that the input color host image is , where
and the input watermark image is W of size P × Q, where
which is to be concealed in the host color image. The embedding steps are discussed as follows:
Step 1: Scramble the binary watermark to banish the correlation between image pixels to add more reliability to the proposed method by using Arnold transformation [55] with arbitrarily chosen key (k), the watermark image is shuffled from W to W1, . Transform it into a one-dimensional bit sequence as follows:
Step 2: Split the input color image, f, into 4 × 4 non-interfering blocks, ,
Step 3: Compute MFrLFMs for each block, using the maximum moment order P × Q as shown in (Section 3) in detail.
Step 4: Select robust and accurate MFrLFMs to carry the watermark; this is done by computing the magnitude values of MFrLFMs to ensure RST invariances. In the proposed method, we selected MFrLFMs with positive reiterations to avoid redundancy as follows:
By utilizing the key coefficients of MFrLFMs, which denote the positions of the selected pixels in the image blocks, are selected randomly from the delicate set depending on the watermark bits to get the feature vector magnitude.
Step 5: Apply fast Walsh–Hadamard transform (FWHT) on selected MFrLFM coefficients using Equation (1).
Step 6: Embed the scrambled binary watermark, bit information in the transformed MFrLFM magnitudes using dither modulation [56] using the following equation:
The denotes the modulated blocks. The mathematical symbols, and refer to the rounding factor, quantization step, and dither modulation.
Step 7: Apply inverse fast Walsh–Hadamard transform (IFWHT) using Equation (4).
Step 8: Reconstruct the color watermarked image as
where is the host color image, is the modified part, and is the unmodified part.
Step 9: Merge all 4 × 4 sub-blocks to get the color watermarked image finally
4.2. Blind Watermarking Extraction
The watermark extraction is done on a fully blind process. There is no need for the cover image; only the watermarked image is needed to generate an entirely successful extraction process by applying inverse operations of the embedding process. The extraction procedures are listed in the following steps in detail:
Step 1: Split the input watermarked image into 4 × 4 non-interfering blocks, ,
Step 2: Compute MFrLFMs for each block by using the method in Section 3.
Step 3: Select the MFrLFM coefficients’ feature vector,
As shown in the embedding process.
Step 4: Apply the fast Walsh–Hadamard transform (FWHT) on the selected MFrLFM magnitudes using Equation (1).
Step 5: Extract the watermark binary data bit information from the MFrLFM magnitudes by applying the inverse operation of Arnold transformation using the secret key, K, where the 1D binary bit series is extracted.
Step 6: Reconstruct the binary watermark image from the extracted one-dimensional binary bit sequence, by rearranging it into a two-dimensional binary image as
Step 7: Finally, obtain the binary extracted watermark image, .
5. Experimental Results
In this part, various numeral simulations are enacted to assess the effectiveness of the proposed method according to the visual quality perception. PSNR and robustness evaluation has assessed these to several typical geometric, image filtering, and combination attacks conducted using NC and BER to measure the degree changes among pixels in the extracted binary watermark. The proposed method is tested over color host images of size 256 × 256 (shown in Figure 4) and color medical images selected from datasets [57,58,59] (shown in Figure 5). Binary watermark images are shown in Figure 6.

Figure 4.
The host standard color images (a) Lena; (b) Peppers; (c) Baboon; (d) F16; (e) San Diego miramar; (f) San Diego north island; (g) Man; (h) Elephant; (i) Monarch; (j) Museum.

Figure 5.
Selected host color medical images from datasets [57,58,59].
Figure 6.
Selected binary watermark images (a–j).
The attained numerical results are compared with other similar moment-based watermarking methods [28,29,41,60,61].
Additional comparisons with statistical watermarking methods [6,9,16,18,33] are also conducted to ensure the robustness and visual invisibility of the proposed methodology.
We document our experimental results according to the best and correct choice of where and.
Correspondingly, we tested different parameters values at and ; from different experimental results, we noticed that the value of at is the optimum choice, where there are no readjustments while using the optimum value .
Experimental results documented using different image sizes (128 × 128 and 256 × 256) are depicted in the following sub-sections. The watermark logo images are of sizes 32 × 32 and 10 × 10.
5.1. Visual Imperceptibility
We utilized peak signal-to-noise ratio to measure and evaluate the proposed watermarking’s imperceptibility. Increasing the PSNR values leads to the high invisibility of the watermarking model. The PSNR is defined as
where is the host color image and is the color watermarked image; is the mean square error, and it is represented as
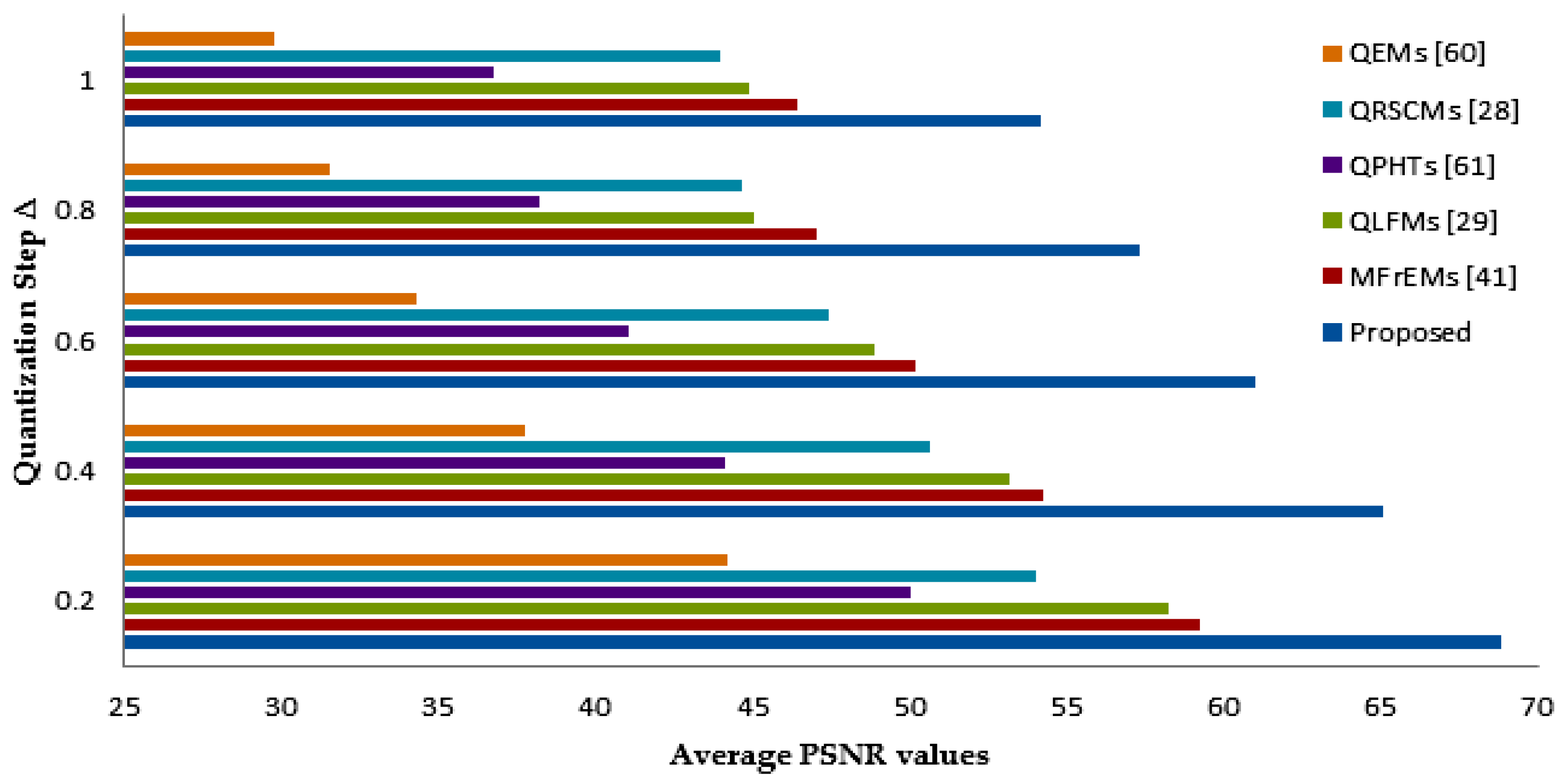
The invisibility of the proposed methodology was evaluated at the value of and values ranged from 0.2 to 1.0 in comparison with other existing moment-based methods [28,29,41,60,61], which in turn embedded binary watermarks of size 32 × 32 into the standard color images. The average PSNR values are indicated in Figure 7. As we notice, there is a reverse operation between the PSNR values, and PSNR values increased as values decreased. The average PSNR values of the proposed watermarking method and other similar methods are shown in Table 1. From these values, we note the proposed method’s success in attaining high PSNR values up to ~68 dB compared with other similar methods, which ensures the high imperceptibility of our method compared to other similar methods.
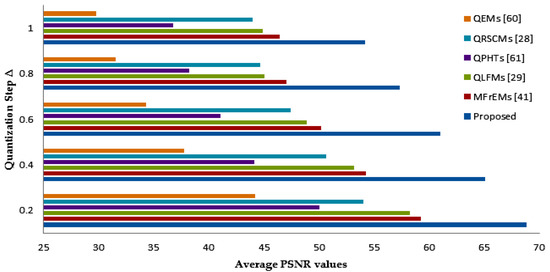
Figure 7.
Average PSNR values using varying values of ∆.

Table 1.
PSNR values using varying values of ∆.
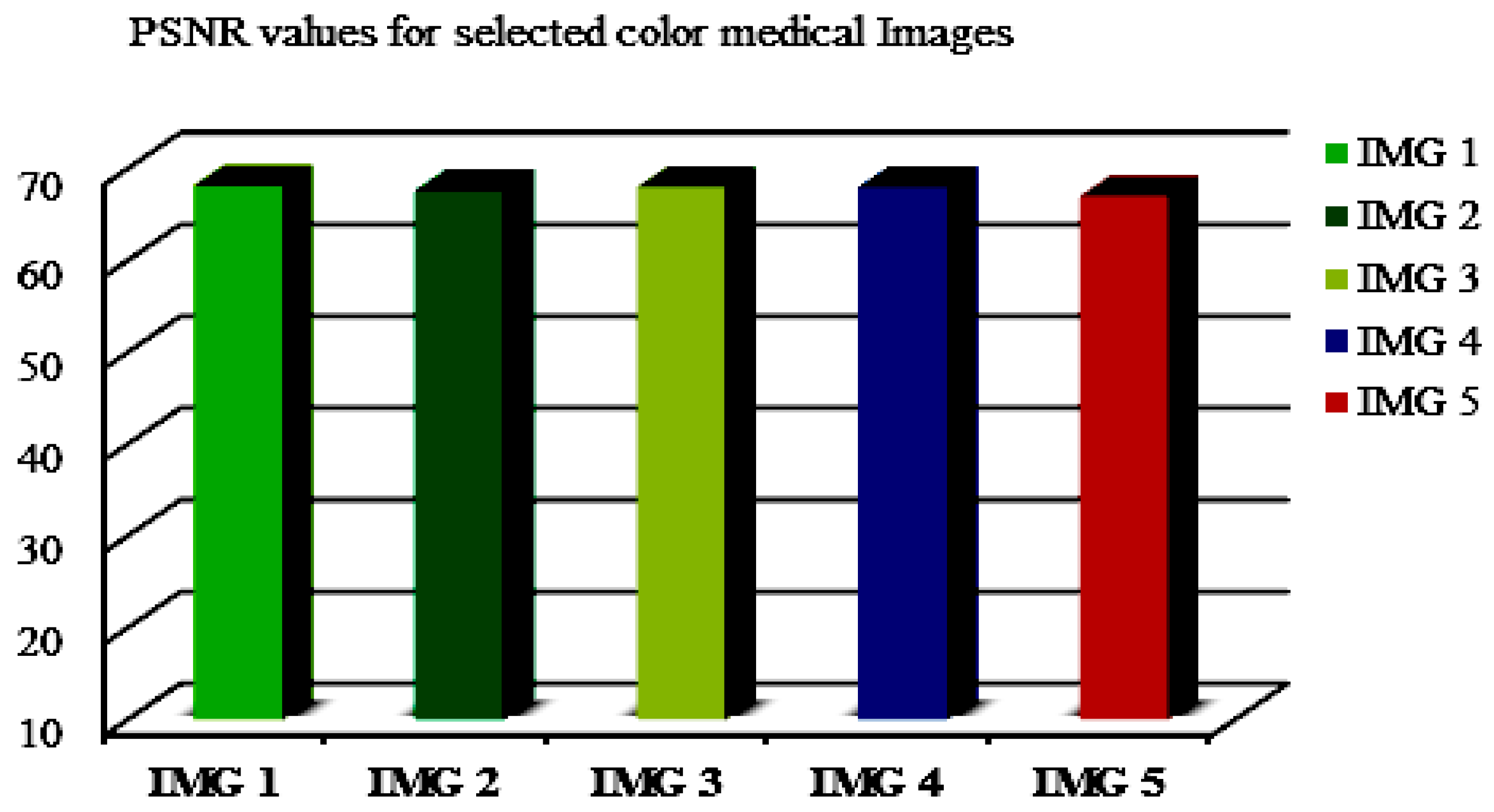
The PSNR values for a chosen color medical image (named IMG 1–5) are also indicated in an illustrative example (Figure 8) with high PSNR values, ensuring that our proposed method is suitable for application on medical images in a reasonable manner.
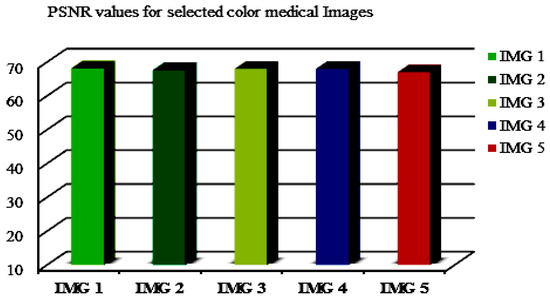
Figure 8.
The PSNR values for selected color medical images at ∆ = 0.2.
5.2. Robustness Evaluation
The robustness of our method was evaluated over the bit error rate (BER) and normalized correlation (NC), which are formulated as
The robustness was evaluated over several categories of attacks, the first category comprised geometrics attacks such as rotation, scaling, cropping, magnification, and shearing attacks, with different parameter factors.
The second category included signal processing attacks such as jpeg, jpeg 2000, noising, salt and peppers, Gaussian, Gaussian low-pass, speckle noise attack, median filter attack, average filter attack, sharpen attack, histogram equalization, and motion blur attack. The third category included many common combination attacks.
The watermark logo was first resized to 10 × 10 and then embedded in the host color image by using and applying various geometric attacks on the watermarked image. Results for geometric attacks are shown in Table 2; several image processing attacks are also shown in Table 3, respectively.

Table 2.
Robustness results of the extracted watermark from the attacked image “Lena” using geometrics attacks, ∆ = 0.2.

Table 3.
Robustness results of the extracted watermark from the attacked image “Lena” using processing attacks ∆ = 0.2.
The proposed method attained the highest robustness level against various geometrical and signal processing attacks.
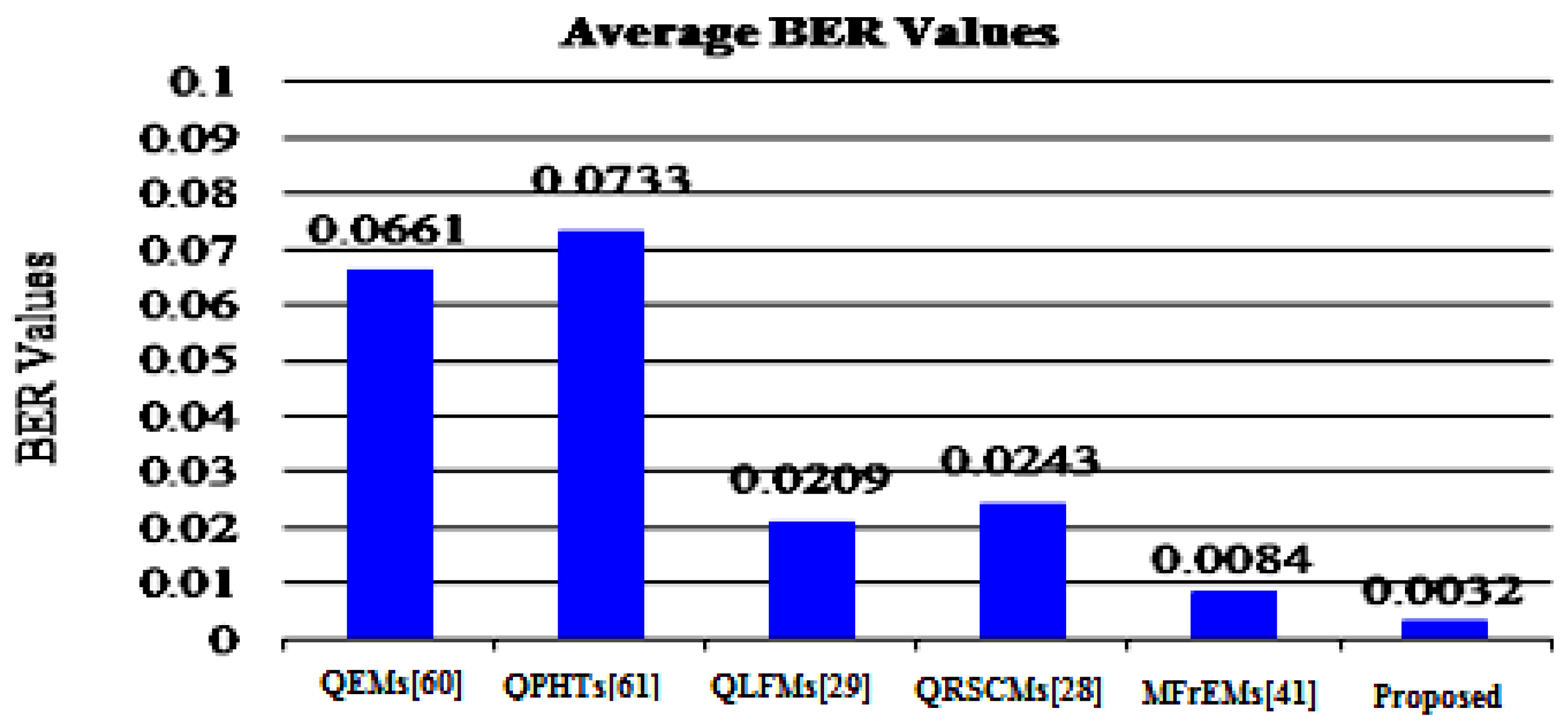
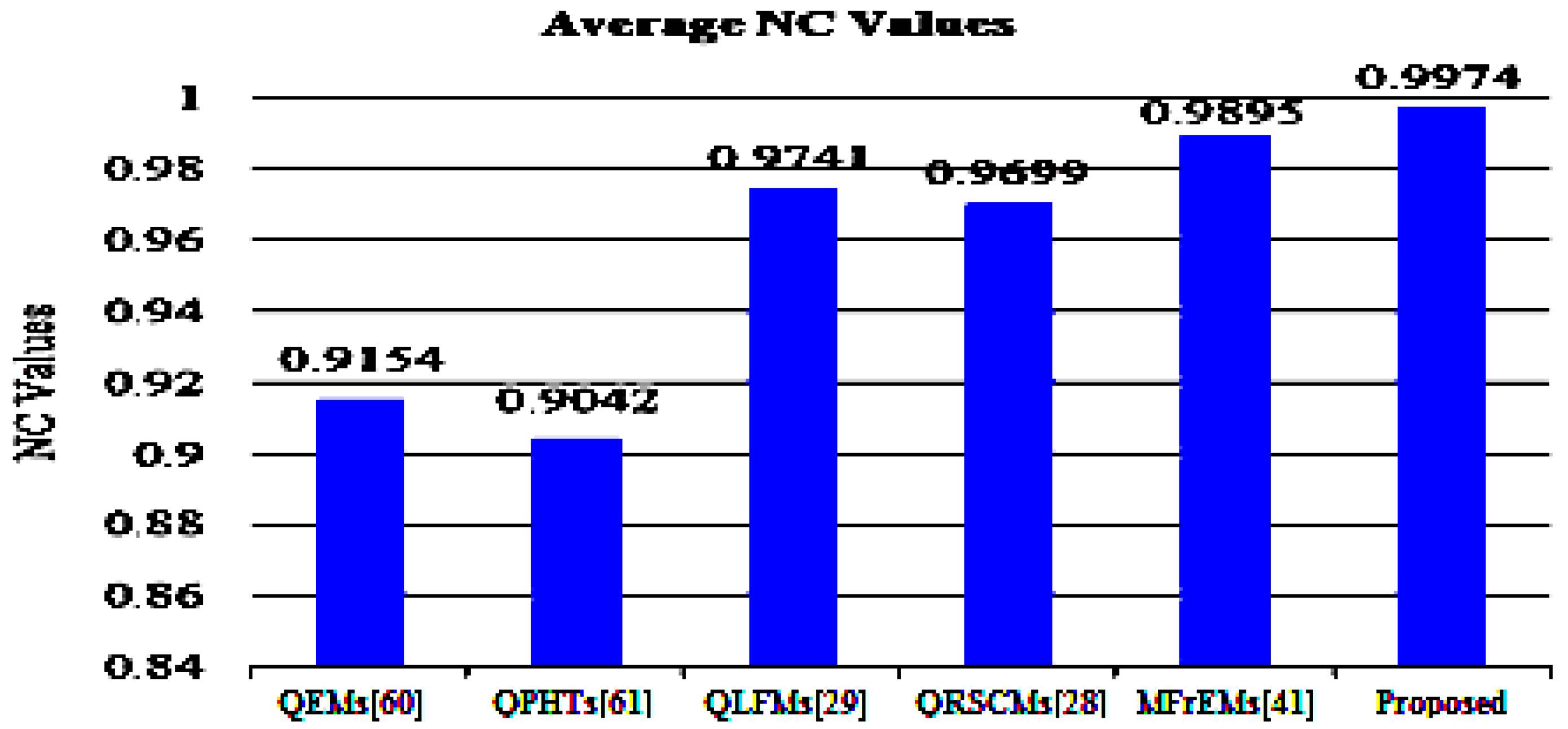
To assess the robustness of the proposed method and other mentioned methods, the average BER and NC values are represented in Figure 9 and Figure 10 for easy comparison. From these simulation results, (in the referred Figure 9 and Figure 10), we note that our method successfully scored the minimum average value (BER = 0.0032) among the compared methods. Moreover, our method scored the maximum average value of NC = 0.9974. From these compared values, we deduce that our method surpassed other existing methods.
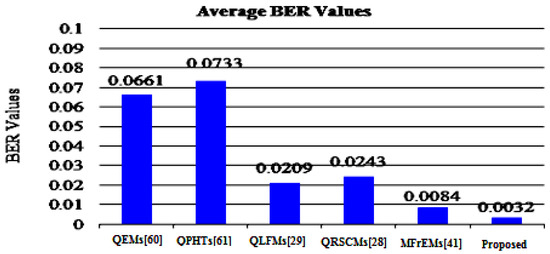
Figure 9.
Average BER values of the proposed and compared methods for common attacks.
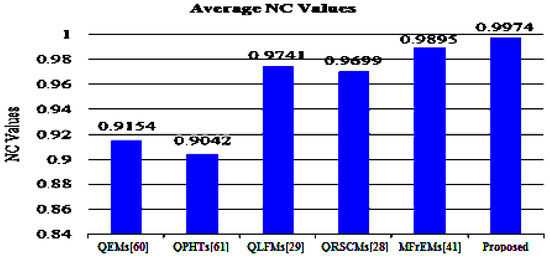
Figure 10.
Average NC values of the proposed and compared methods for common attacks.
The additional numerical experimental test was performed on a chosen binary watermark image called “cup” of size 32 × 32, which was embedded in the standard host image “Lena” and attacked using different common types of attacks, resulting in a fair comparison between the proposed method and moment-based methods [28,29,41,60,61]. The extracted watermark within the corresponding values of BER and NC is notated in Table 4.

Table 4.
Robustness evaluation for the proposed method and other exiting moment-based methods under common attacks.
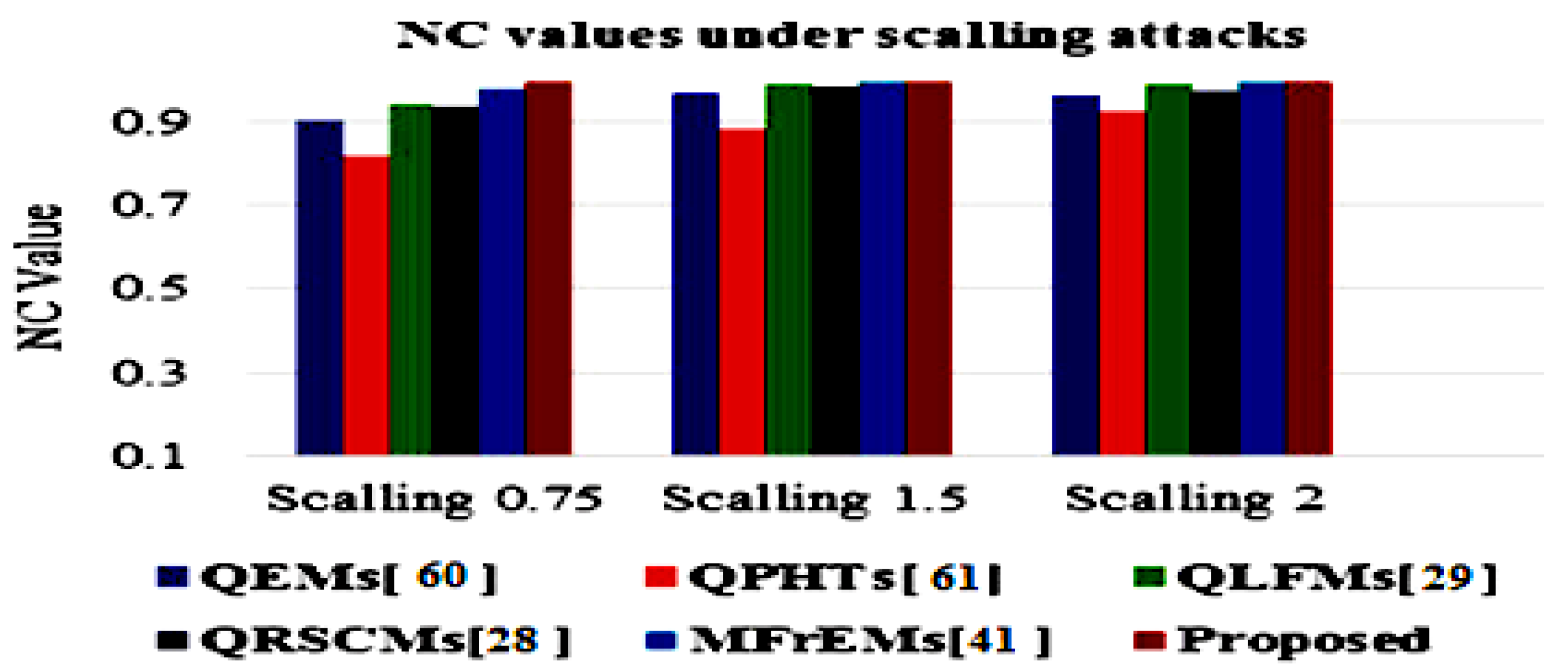
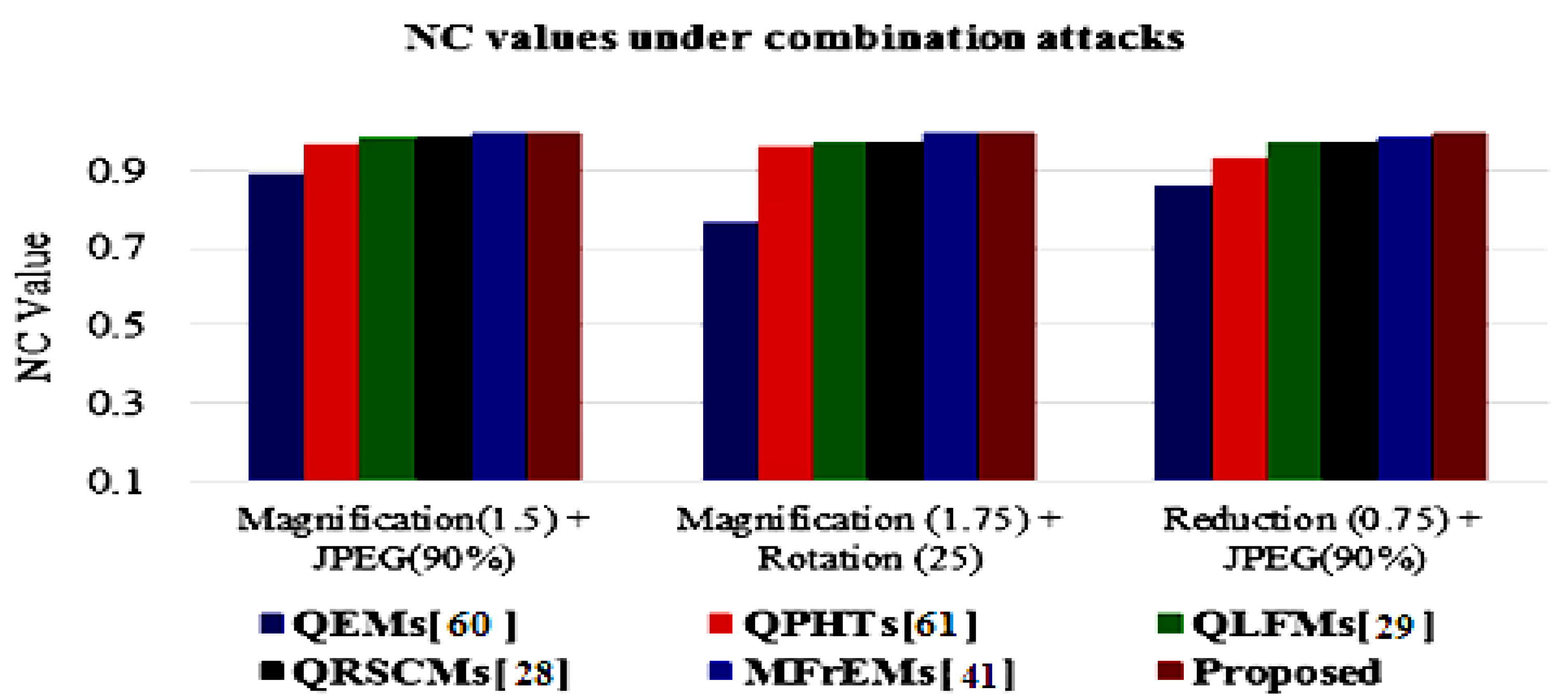
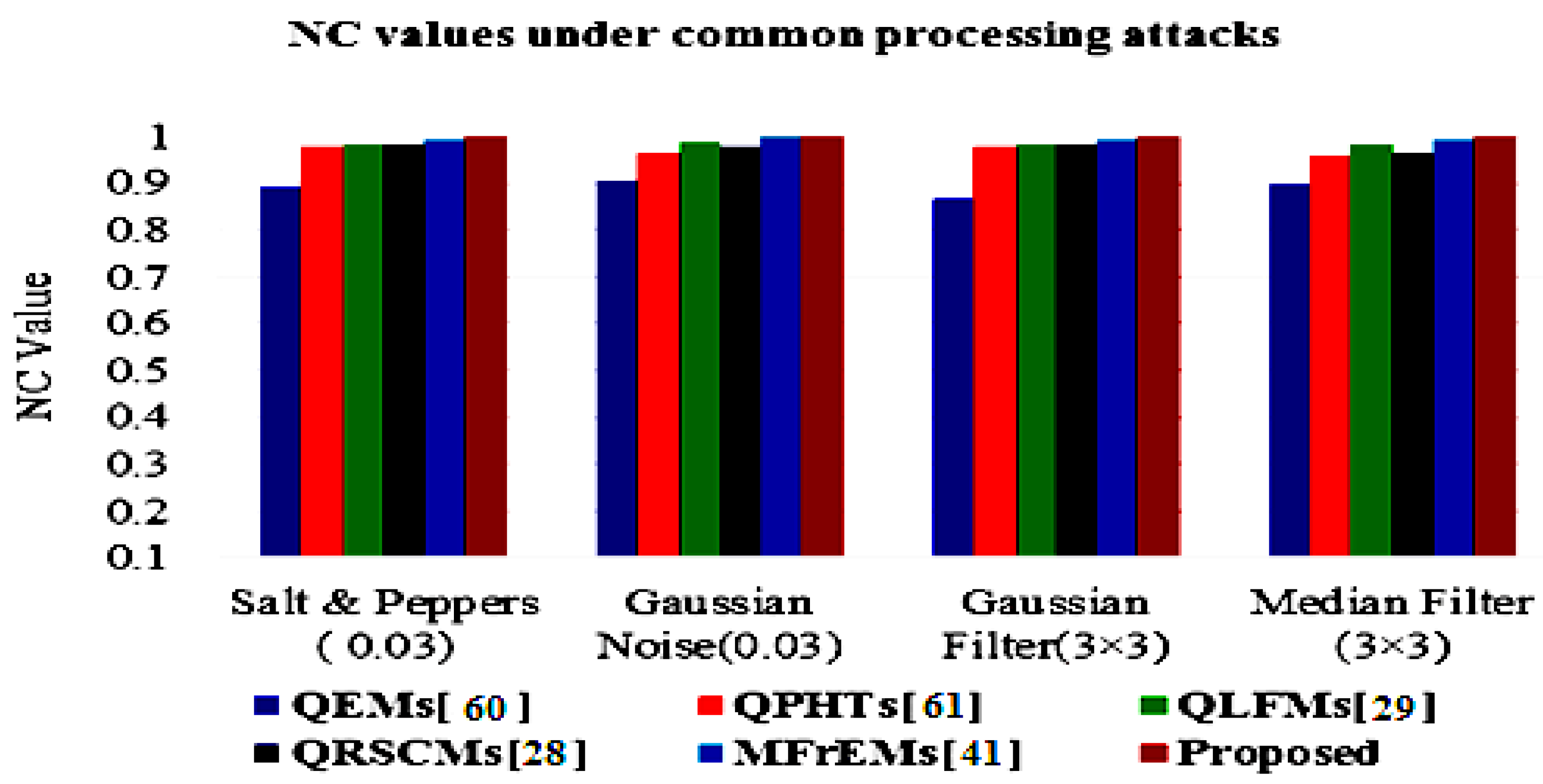
The simulation results of the proposed method and compared methods [28,29,41,60,61] of different NC values under various common attacks are also presented in a graphical simulation in Figure 11, Figure 12 and Figure 13. These results denote that the proposed method exceeded other existing methods and was robust to the various tested attacks.
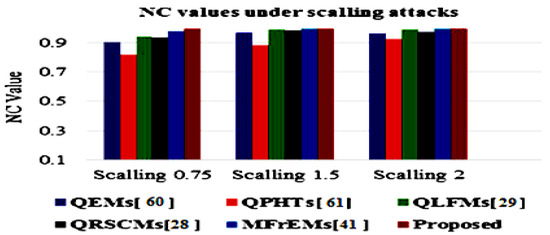
Figure 11.
Graphical comparative of NC values under a scaling attack with different parameters.
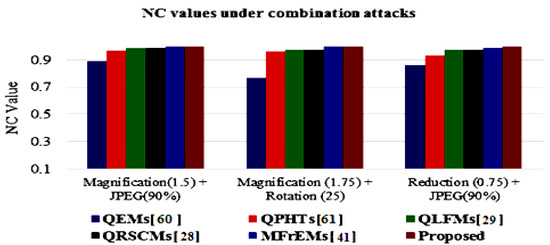
Figure 12.
Graphical comparison of NC values using combination attacks with different parameters.
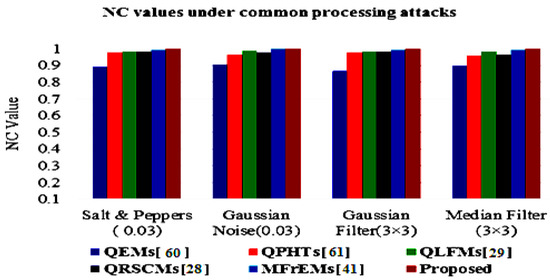
Figure 13.
Graphical comparison of NC values under common noise and filtering attacks.
From these results, we conclude that our method outperformed other existing methods. The watermark could be realized under various attacks suitably, and it seemed close to its original. In addition, the numerical values of BER and NC proved that the robustness of the proposed model surpassed other similar models.
We compared our method with more exiting statistical watermarking methods [6,9,16,18,33] in a comparison of maximum PSNR values of the watermarked images and the robustness of the extracted watermark over NC values under common attacks as shown in Table 5, from these values we can note that our proposed method succeeded in achieving a high robustness level and visual imperceptibility compared with others methods.

Table 5.
Robustness evaluation of the proposed method and other exiting watermarking methods under common attacks.
5.3. Capacity Evaluation
As there is a reverse operation between the payload capacity and visual image quality, increasing capacity degrades image quality (PSNR), so we considered this in our proposed method. The payload capacity of the proposed method was analyzed by the number of embedded bits per pixel (bpp). The maximum payload capacity for a chosen color host image of size 256 × 256 and watermark image of size 32 × 32 computed as (32 × 32)/(256 × 256 × 3) = 0.00520833 (bpp). It was obvious that our method scored satisfying results among the compared method as shown in Table 6, and at the same time preserved image quality as much as possible.

Table 6.
Capacity analysis for different methods.
6. Conclusions
In this paper, a robust and efficient blind watermark method was proposed by utilizing FWHT and MFrLFMs on color images. The input binary watermark was scrambled using Arnold transformation to add more security and reliability to the proposed method. The accurate magnitude of MFrLFMs was selected to attain the goal of the watermarking system, which resulted in improved robustness and visual imperceptibility. The watermark bits were embedded in the modified magnitudes of the MFrLFMs based on the quantization step with optimum selected values. The proposed method successfully countered common geometric attacks, processing attacks, and combination complex attacks. The numerical results clearly show that our method surpassed existing similar methods with higher watermark invisibility, efficiency, and security, and it was suitable for medical images applications. In future work, we are looking to extend improvement to apply this method in a complete color image watermarking system to conceal color watermark logo images into color host cover images in a holistic way.
Author Contributions
Conceptualization, K.M.H. and M.M.A.-A.; methodology, K.M.H. and M.M.A.-A.; software, K.M.H. and M.M.A.-A.; validation, M.M.A.-A., K.M.H., N.A.L. and M.M.F.; formal analysis, K.M.H. and N.A.L.; investigation, K.M.H. and M.M.A.-A.; resources, K.M.H. and M.M.A.-A.; data curation, M.M.A.-A.; writing—original draft preparation, M.M.A.-A. and M.M.F.; writing—review and editing, K.M.H., N.A.L., M.M.A.-A. and M.M.F.; visualization, M.M.A.-A. and K.M.H.; supervision, K.M.H. and N.A.L.; project administration, K.M.H.; funding acquisition, M.M.F. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Qi, X.; Qi, J. A robust content-based digital image watermarking scheme. Signal Process. 2007, 87, 1264–1280. [Google Scholar] [CrossRef]
- Roy, S.S.; Basu, A.; Chattopadhyay, A. On the implementation of a copyright protection scheme using digital image watermarking. Multimed. Tools Appl. 2020, 79, 13125–13138. [Google Scholar] [CrossRef]
- Al-khafaji, A.; Nur, N.; Sjarif, N.N.A.; Mahdi, M.; Shafry, M.; Rahim, M. A review and open issues of diverse text watermarking techniques in spatial domain. J. Theor. Appl. Inf. Technol. 2018, 96, 5819–5840. [Google Scholar]
- Jibrin, B.; Tekanyi, A.; Sani, S. Image Watermarking Algorithm in Frequency Domain: A Review of Technical Literature. ATBU J. Sci. Technol. Educ. 2019, 7, 257–263. [Google Scholar]
- Agarwal, N.; Singh, A.K.; Singh, P.K. Survey of robust and imperceptible watermarking. Multimed. Tools Appl. 2019, 78, 8603–8633. [Google Scholar] [CrossRef]
- Prabha, K.; Sam, I.S. An effective robust and imperceptible blind color image watermarking using WHT. J. King Saud Univ. Comput. Inf. Sci. 2020, in press. [Google Scholar] [CrossRef]
- Naidu, S.; Upadhyay, G. A Review on Blind Watermarking Technique for Copyright Protection of Image-based on DCT, DWT, and SVD Domain. Int. Res. J. Eng. Technol. 2020, 7, 364–366. [Google Scholar]
- Anbarjafari, G.; Ozcinar, C. Imperceptible non-blind watermarking and robustness against tone mapping operation attacks for high dynamic range images. Multimed. Tools Appl. 2018, 77, 24521–24535. [Google Scholar] [CrossRef]
- Izhar, M.N. A Semi Blind Watermarking Technique for Copyright Protection of Image-Based on DCT and SVD Domain. Glob. J. Res. Eng. 2017, 16, 364–366. [Google Scholar]
- Valandar, M.Y.; Barani, M.J.; Ayubi, P. A blind and robust color images watermarking method based on block transform and secured by modified 3-dimensional Hénon map. Soft Comput. 2020, 24, 771–794. [Google Scholar] [CrossRef]
- Feng, B.; Li, X.; Jie, Y.; Guo, C.; Fu, H. A Novel Semi-fragile Digital Watermarking Scheme for Scrambled Image Authentication and Restoration. Mob. Netw. Appl. 2020, 25, 82–94. [Google Scholar] [CrossRef]
- Molina-Garcia, J.; Garcia-Salgado, B.P.; Ponomaryov, V.; Reyes-Reyes, R.; Sadovnychiy, S.; Cruz-Ramos, C. An effective fragile watermarking scheme for color image tampering detection and self-recovery. Signal Process. Image Commun. 2020, 81, 115725. [Google Scholar] [CrossRef]
- Varma, P.R.K.; Kumari, V.V.; Kumar, S.S. Spatial Domain Blind Watermarking for Digital Images. In Progress in Computing, Analytics and Networking; Springer: Singapore, 2018; Volume 710. [Google Scholar] [CrossRef]
- Su, Q.; Chen, B. Robust color image watermarking technique in the spatial domain. Soft Comput. 2018, 22, 91–106. [Google Scholar] [CrossRef]
- Yuan, Z.; Liu, D.; Zhang, X.; Su, Q. New image blind watermarking method based on two-dimensional discrete cosine transform. Optik 2020, 204, 164152. [Google Scholar] [CrossRef]
- Fares, K.; Amine, K.; Salah, E. A robust blind color image watermarking based on Fourier transform domain. Optik 2020, 208, 164562. [Google Scholar] [CrossRef]
- Shukla, M. A Comparative Study of Wavelet and Curvelet Transform for Image Denoising. IOSR J. Electron. Commun. Eng. 2013, 7, 63–68. [Google Scholar] [CrossRef]
- Yuan, Z.; Su, Q.; Liu, D.; Zhang, X. A blind image watermarking scheme combining spatial domain and frequency domain. Vis. Comput. 2020, 37, 1867–1881. [Google Scholar] [CrossRef]
- Ma, B.; Chang, L.; Wang, C.; Li, J.; Wang, X.; Shi, Y.Q. Robust image watermarking using invariant accurate polar harmonic Fourier moments and chaotic mapping. Signal Process. 2020, 172, 107544. [Google Scholar] [CrossRef]
- Yamni, M.; Daoui, A.; El Ogri, O.; Karmouni, H.; Sayyouri, M.; Qjidaa, H.; Flusser, J. Fractional Charlier moments for image reconstruction and image watermarking. Signal Process. 2020, 171, 107509. [Google Scholar] [CrossRef]
- Wang, C.; Wang, X.; Xia, Z.; Zhang, C. Ternary radial harmonic Fourier moments based robust stereo image zero-watermarking algorithm. Inf. Sci. 2019, 470, 109–120. [Google Scholar] [CrossRef]
- Ernawan, F. Tchebichef image watermarking along the edge using YCoCg-R color space for copyright protection. Int. J. Electr. Comput. Eng. 2019, 9, 1850–1860. [Google Scholar] [CrossRef]
- Singh, M.K.; Kumar, S.; Ali, M.; Saini, D. Application of a novel image moment computation in X-ray and M.R.I. image watermarking. IET Image Process. 2021, 15, 666–682. [Google Scholar] [CrossRef]
- Yamni, M.; Karmouni, H.; Daoui, A.; el ogri, O.; Sayyouri, M.; Qjidaa, H. Blind Image Zero-Watermarking Algorithm Based on Radial Krawtchouk Moments and Chaotic System. In Proceedings of the 2020 International Conference on Intelligent Systems and Computer Vision (ISCV), Fez, Morocco, 9–11 June 2020; pp. 1–7. [Google Scholar] [CrossRef]
- Ernawan, F.; Kabir, M.N. An Improved Watermarking Technique for Copyright Protection Based on Tchebichef Moments. IEEE Access 2019, 7, 151985–152003. [Google Scholar] [CrossRef]
- Chen, B.; Shu, H.; Coatrieux, G.; Chen, G.; Sun, X.; Coatrieux, J. Color Image Analysis by Quaternion-Type Moments. J. Math. Imaging Vis. 2014, 51, 124–144. [Google Scholar] [CrossRef]
- Darwish, M.; Hosny, K.; Kamal, S. Improved Color Image Watermarking Using Logistic Maps and Quaternion Legendre-Fourier Moments. In Multimedia Security Using Chaotic Maps: Principles and Methodologies; Springer: Berlin/Heidelberg, Germany, 2020. [Google Scholar] [CrossRef]
- Hosny, K.; Darwish, M. Resilient Color Image Watermarking Using Accurate Quaternion Radial Substituted Chebyshev Moments. ACM Trans. Multimed. Comput. Commun. Appl. 2019, 15, 46. [Google Scholar] [CrossRef]
- Hosny, K.M.; Darwish, M.M. Robust color image watermarking using invariant quaternion Legendre-Fourier moments. Multimed. Tools Appl. 2018, 77, 24727–24750. [Google Scholar] [CrossRef]
- Li, J.; Yu, C.; Gupta, B.B.; Ren, X. Color image watermarking scheme based on quaternion Hadamard transform and Schur decomposition. Multimed. Tools Appl. 2018, 77, 4545–4561. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, S.; Yang, J. Color image watermark decoder by modeling quaternion polar harmonic transform with B.K.F. distribution. Signal Process. Image Commun. 2020, 88, 115946. [Google Scholar] [CrossRef]
- Xia, Z.; Wang, X.; Li, X.; Wang, C.; Unar, S.; Wang, M.; Zhao, T. Efficient copyright protection for three C.T. images based on quaternion polar harmonic Fourier moments. Signal Process. 2019, 164, 368–379. [Google Scholar] [CrossRef]
- Huynh-The, T.; Hua, C.H.; Tu, N.A.; Hur, T.; Bang, J.; Kim, D.; Amin, M.B.; Kang, B.H.; Seung, H.; Lee, S. Selective bit embedding scheme for robust blind color image watermarking. Inf. Sci. 2018, 426, 1–18. [Google Scholar] [CrossRef]
- Xia, Z.; Wang, X.; Wang, C.; Ma, B.; Wang, M.; Shi, Y. Local quaternion polar harmonic Fourier moments-based multiple zero-watermarking scheme for color medical images. Knowl.-Based Syst. 2021, 216, 106568. [Google Scholar] [CrossRef]
- Xia, Z.; Wang, X.; Wang, M.; Unar, S.; Wang, C.; Liu, Y.; Li, X. Geometrically Invariant Color Medical Image Null-Watermarking Based on Precise Quaternion Polar Harmonic Fourier Moments. IEEE Access 2019, 7, 122544–122560. [Google Scholar] [CrossRef]
- Yamni, M.; Karmouni, H.; Sayyouri, M.; Qjidaa, H. Image watermarking using separable fractional moments of Charlier–Meixner. J. Frankl. Inst. 2021, 358, 2535–2560. [Google Scholar] [CrossRef]
- Liu, X.; Han, G.; Wu, J.; Shao, Z.; Coatrieux, G.; Shu, H. Fractional Krawtchouk Transform with an Application to Image Watermarking. IEEE Trans. Signal Process. 2017, 65, 1894–1908. [Google Scholar] [CrossRef]
- Yang, H.; Qi, S.; Tian, J.; Niu, P.; Wang, X. Robust and discriminative image representation: Fractional-order Jacobi-Fourier moments. Pattern Recognit. 2021, 115, 107898. [Google Scholar] [CrossRef]
- Xiao, B.; Luo, J.; Bi, X.; Li, W.; Chen, B. Fractional discrete Tchebyshev moments and their applications in image encryption and watermarking. Inf. Sci. 2020, 516, 545–559. [Google Scholar] [CrossRef]
- Hosny, K.M.; Darwish, M.M.; Fouda, M.M. New Color Image Zero-Watermarking Using Orthogonal Multi-Channel Fractional-Order Legendre-Fourier Moments. IEEE Access 2021, 9, 91209–91219. [Google Scholar] [CrossRef]
- Hosny, K.M.; Darwish, M.M.; Fouda, M.M. Robust Color Images Watermarking Using New Fractional-Order Exponent Moments. IEEE Access 2021, 9, 47425–47435. [Google Scholar] [CrossRef]
- Vaidya, P.; Pvssr, C.M. A robust semi-blind watermarking for color images based on multiple decompositions. Multimed. Tools Appl. 2017, 76, 25623–25656. [Google Scholar] [CrossRef]
- Elbaşı, E. M-SVD based Quality Measurement in Hybrid non-blind Watermarked Medical Images. In Proceedings of the 2020 43rd International Conference on Telecommunications and Signal Processing (TSP), Milan, Italy, 7–9 July 2020. [Google Scholar] [CrossRef]
- Huh, J.-H.; Kim, T.-J. A location-based mobile health care facility search system for senior citizens. J. Supercomput. 2019, 75, 1831–1848. [Google Scholar] [CrossRef]
- Hosny, K.M.; Darwish, M.M. New geometrically invariant multiple zero-watermarking algorithm for color medical images. Biomed. Signal Process. Control. 2021, 70, 103007. [Google Scholar] [CrossRef]
- Soualmi, A.; Alti, A.; Laouamer, L. Multiple Blind Watermarking Framework for Security and Integrity of Medical Images in E-Health Applications. Int. J. Comput. Vis. Image Process. 2021, 11, 1–16. [Google Scholar] [CrossRef]
- Sun, X.; Bo, S. A blind digital watermarking for color medical images based on P.C.A. In Proceedings of the 2010 IEEE International Conference on Wireless Communications, Networking and Information Security, Beijing, China, 25–27 June 2010; pp. 421–427. [Google Scholar] [CrossRef]
- Meenakshi, K.; Rao, C.S.; Prasad, K.S. A Robust Watermarking Scheme Based Walsh-Hadamard Transform and S.V.D. Using ZIG ZAG Scanning. In Proceedings of the 2014 International Conference on Information Technology, Bhubaneswar, India, 22–24 December 2014; pp. 167–172. [Google Scholar] [CrossRef]
- Erfani, S.; Babolian, E.; Javadi, S.; Shamsi, M. Stable evaluations of fractional derivative of the Müntz–Legendre polynomials and application to fractional differential equations. J. Comput. Appl. Math. 2019, 348, 70–88. [Google Scholar] [CrossRef]
- Hosny, K.M.; Darwish, M.M.; Aboelenen, T. New fractional-order Legendre-Fourier moments for pattern recognition applications. Pattern Recognit. 2020, 103, 107324. [Google Scholar] [CrossRef]
- Suk, T.; Flusser, J. Affine Moment Invariants of Color Images. In Computer Analysis of Images and Patterns; Jiang, X., Petkov, N., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5702. [Google Scholar] [CrossRef]
- Hosny, K.M.; Darwish, M.M. A kernel-based method for fast and accurate computation of PHT in polar coordinates. J. Real-Time Image Process. 2019, 16, 1235–1247. [Google Scholar] [CrossRef]
- Hosny, K.M.; Darwish, M.M. Highly accurate and numerically stable higher order QPCET moments for color image representation. Pattern Recognit. Lett. 2017, 97, 29–36. [Google Scholar] [CrossRef]
- Upneja, R.; Pawlak, M.; Sahan, A.M. An accurate approach for the computation of polar harmonic transforms. Optik 2018, 158, 623–633. [Google Scholar] [CrossRef]
- Yang, H.-Y.; Wang, X.-Y.; Wang, P.; Niu, P.-P. Geometrically resilient digital watermarking scheme based on radial harmonic Fourier moments magnitude. AEU Int. J. Electron. Commun. 2015, 69, 389–399. [Google Scholar] [CrossRef]
- Xin, Y.; Liao, S.; Pawlak, M. Circularly orthogonal moments for geometrically robust image watermarking. Pattern Recognit. 2007, 40, 3740–3752. [Google Scholar] [CrossRef]
- Color Melanoma Images. Available online: https://www.isic-archive.com (accessed on 1 May 2021).
- Color Retinal Images. Available online: https://www5.cs.fau.de (accessed on 1 May 2021).
- Color Anatomical Images. Available online: https://www.nlm.nih.gov (accessed on 1 May 2021).
- Wang, X.Y.; Yang, H.Y.; Niu, P.P.; Wang, C.P. Quaternion exponent moments based robust color image watermarking. J. Comput. Res. Dev. 2016, 53, 651–665. [Google Scholar]
- Xu, H.; Kang, X.; Chen, Y.; Wang, Y. Rotation and scale invariant image watermarking based on polar harmonic transforms. Optik 2019, 183, 401–414. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).