A Malware Distribution Simulator for the Verification of Network Threat Prevention Tools
Abstract
:1. Introduction
- Analyze and evaluate the propagation techniques used by the Mirai malware.
- Explain why the Mirai malware is not suitable to verify the functionality of the security solutions and propose a method to propagate malware to IoT devices that are assigned private IP addresses.
- Evaluate new propagation technology in small network environments based on total propagation time.
- Define the real and virtual experimental environments that can verify the functionality and performance of network-based threat prevention solutions.
- Propose the optimal conditions that are to be set for a malware simulation tool, such as a scanning method, the number of master bots, and the number of scan packets, for rapid malware spreading. The value to set for the malware simulation tool can be determined by comparing the number of IoT devices used in the experiment with the number of IoT devices in the infrastructure to which the security solution will be applied.
2. Related Works
2.1. Malware Detection Techniques
2.2. IoT Malwares
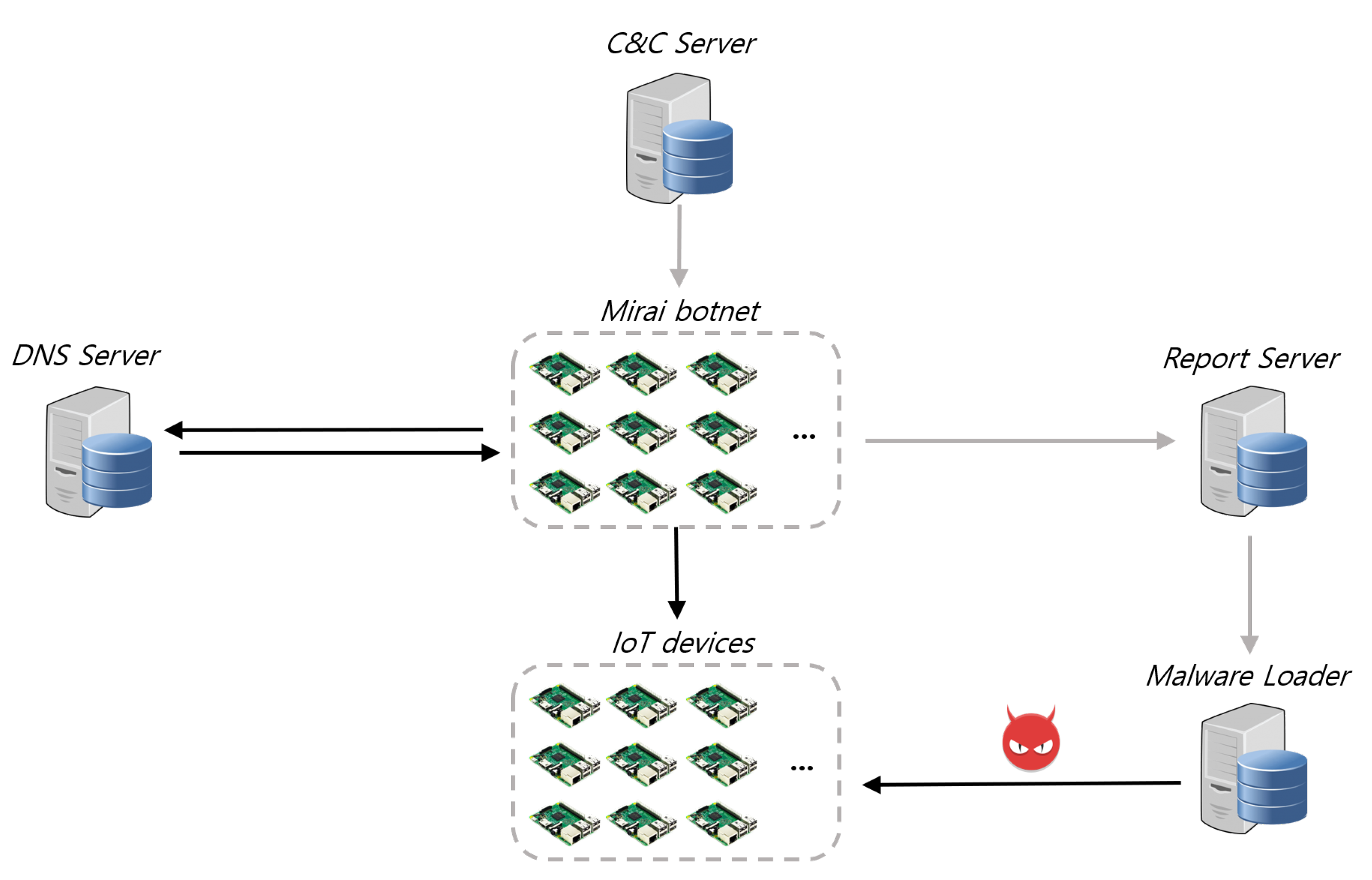
3. The Foundation of the Malware Simulation Tool: Mirai Source Code Released on the Internet
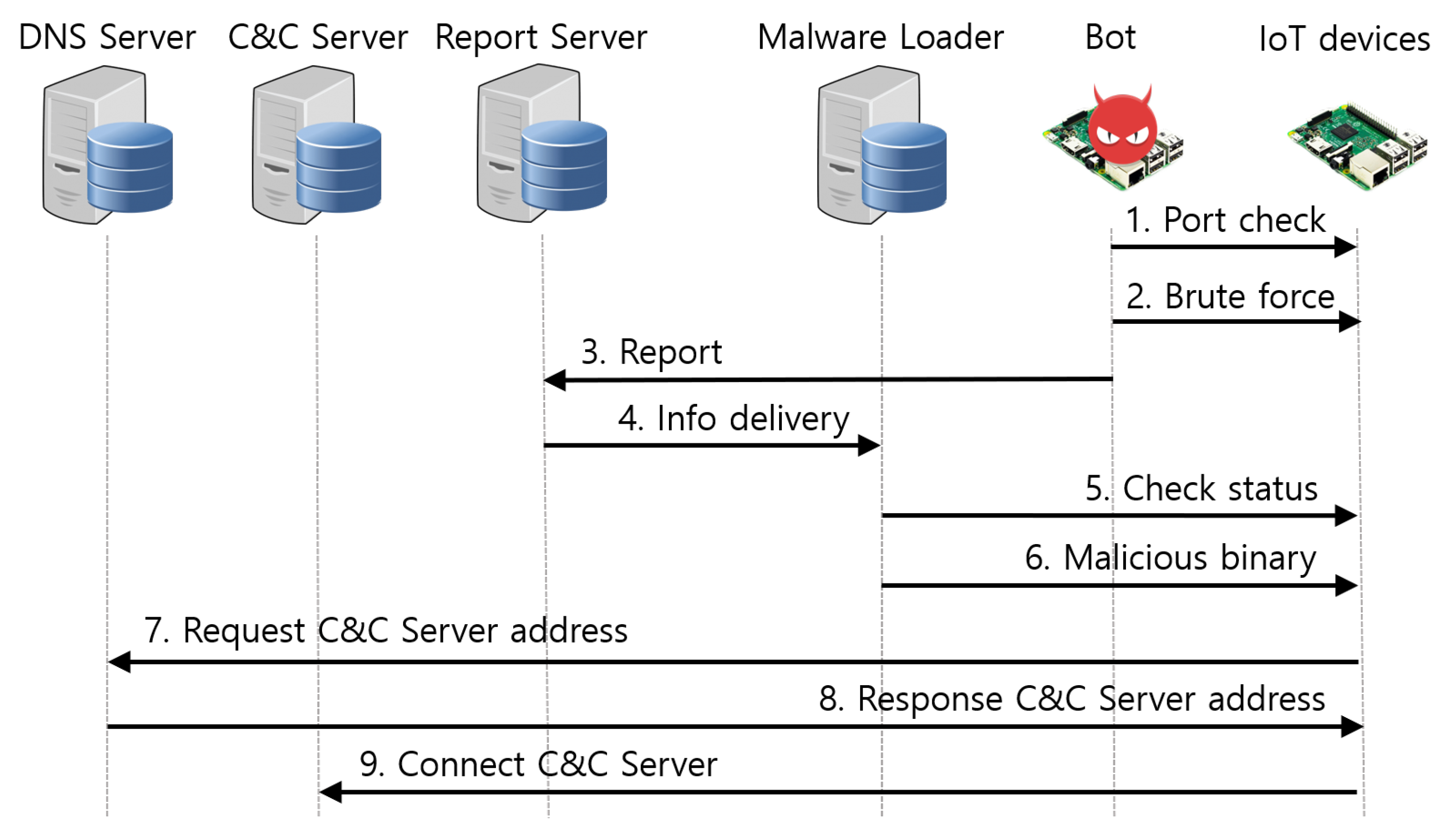
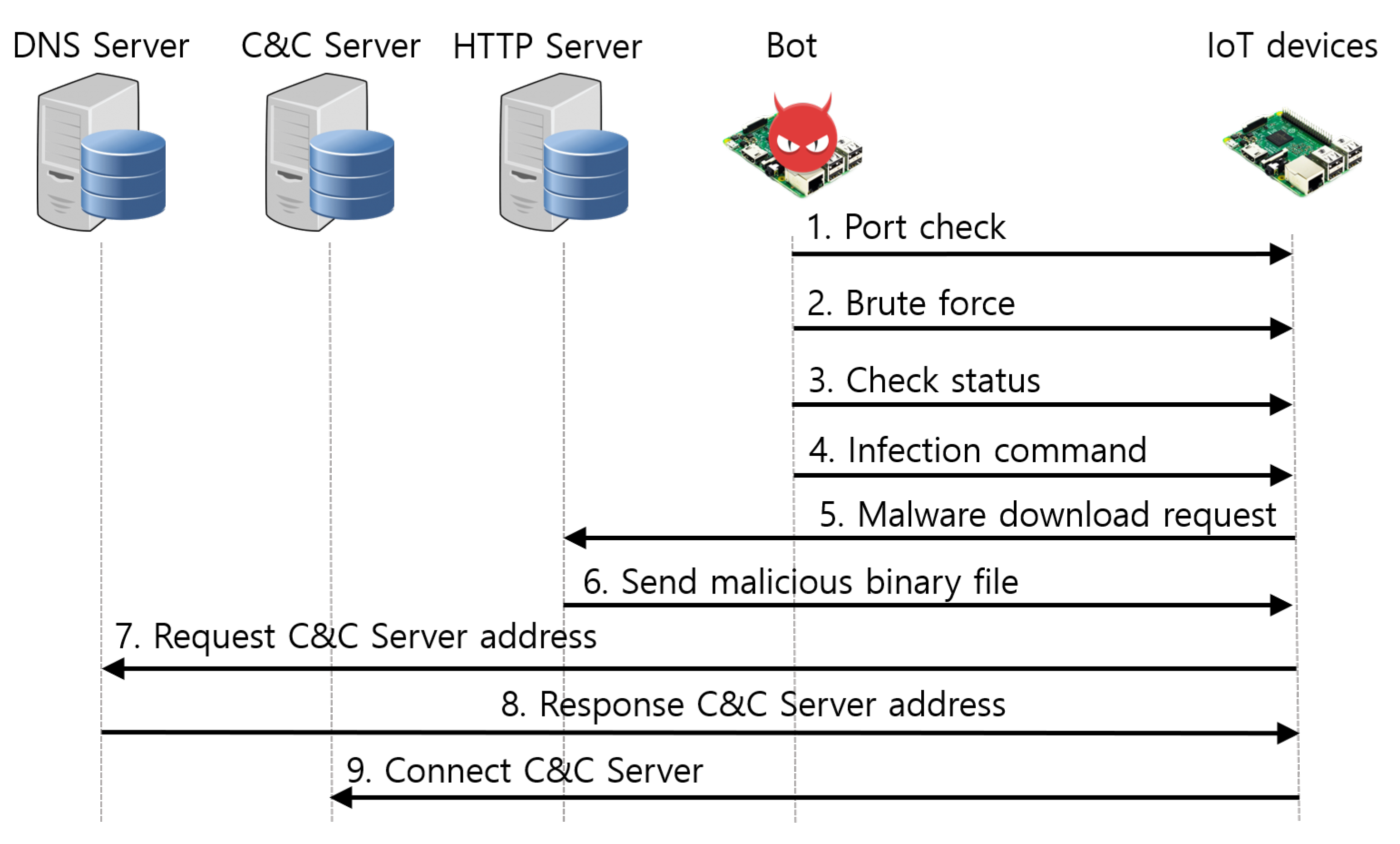
3.1. Propagation Technique of the Mirai Malware
3.1.1. Stateless Random Scanning Method
3.1.2. The Malware Loader’s Malware Infection Method
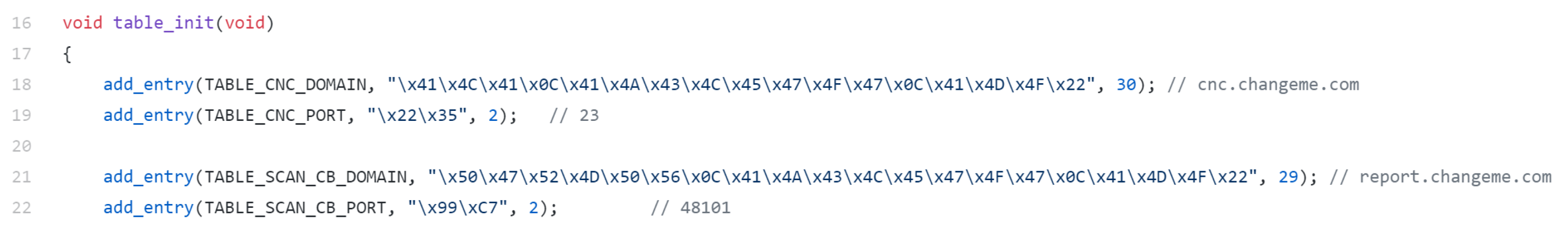
3.1.3. Domain Generation Algorithm (DGA)
4. Malware Simulation Tool
4.1. Problems with the Propagation Technique of the Mirai
4.1.1. Wide Range of IP Addresses to Scan
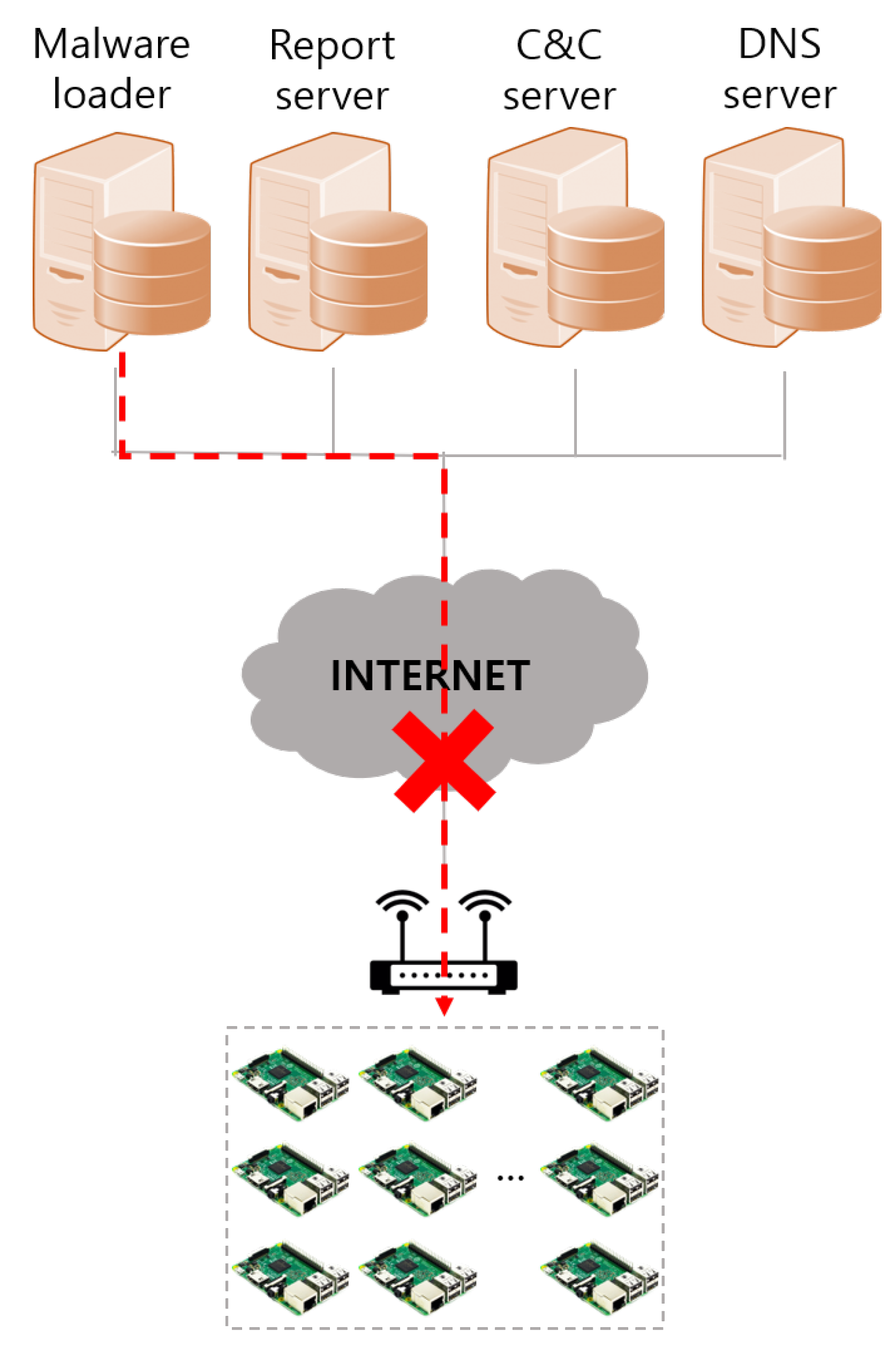
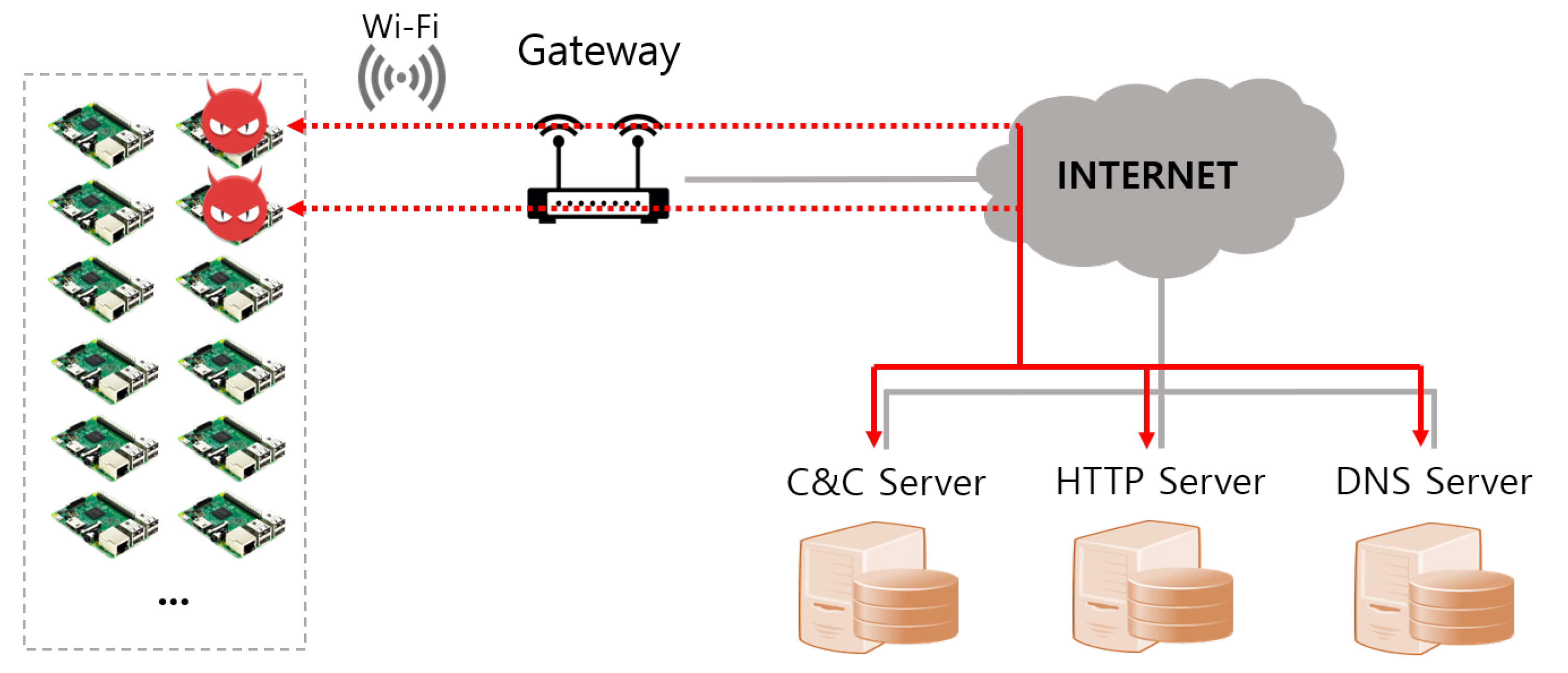
4.1.2. Inaccessible Internal Network
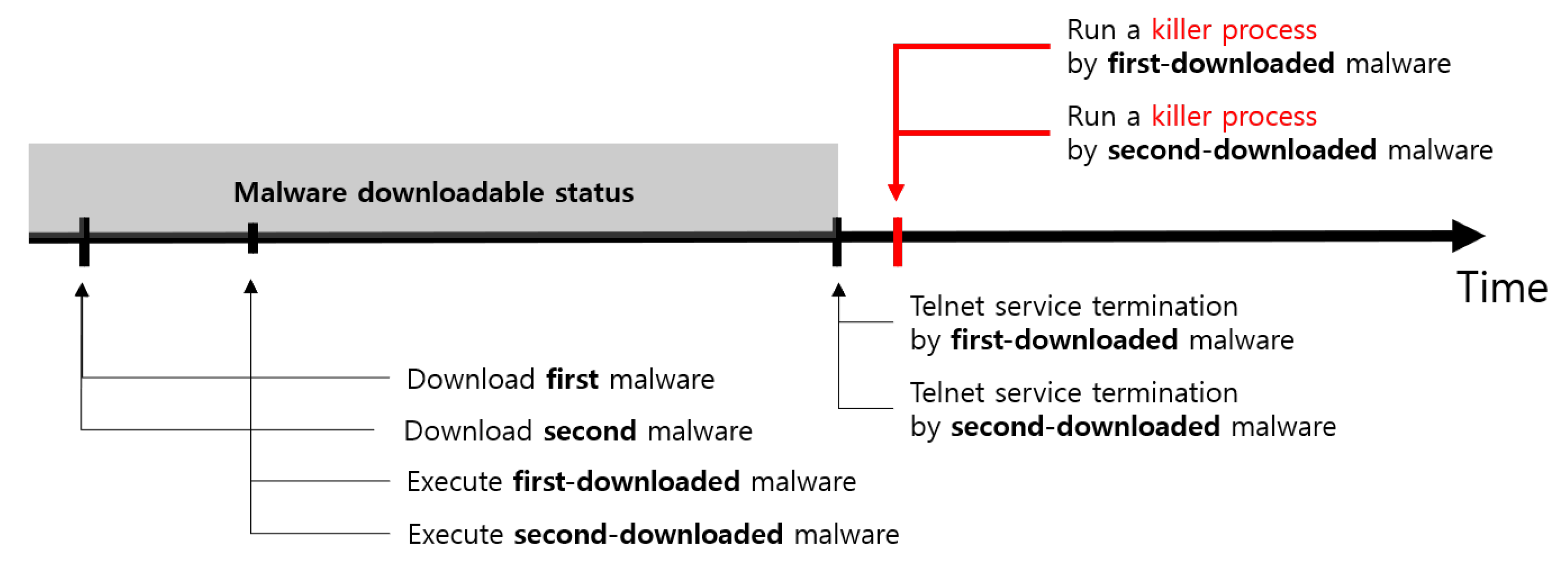
4.1.3. Duplicate Infections
4.1.4. Network Infrastructure Overload
4.1.5. Inefficient Infrastructure Deployment
4.2. Solutions to the Problems of the Mirai Malware’s Propagation Technique
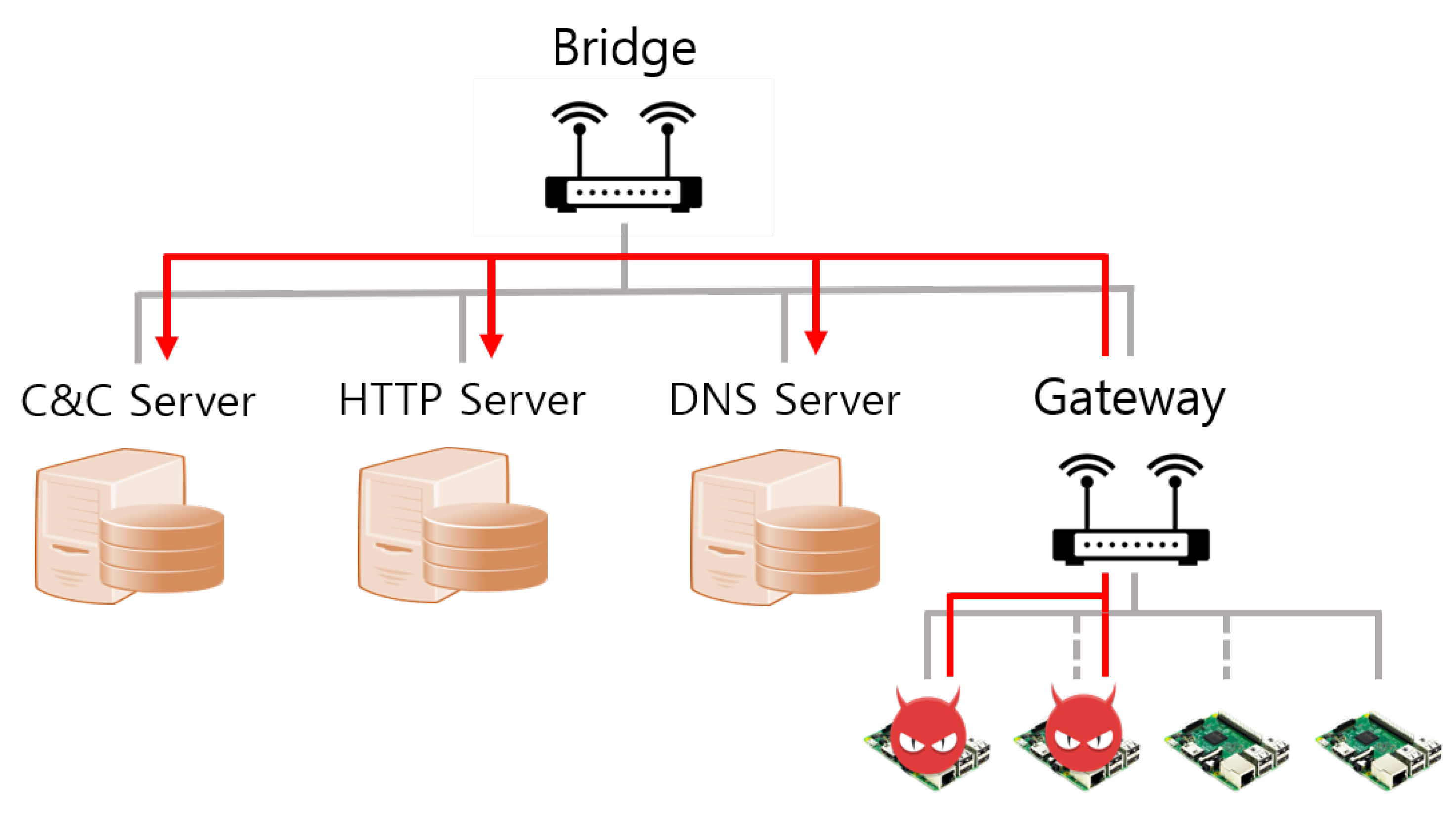
4.2.1. Device-to-Device Command Injection Method
4.2.2. Restricted Range Stateless Scanning Method
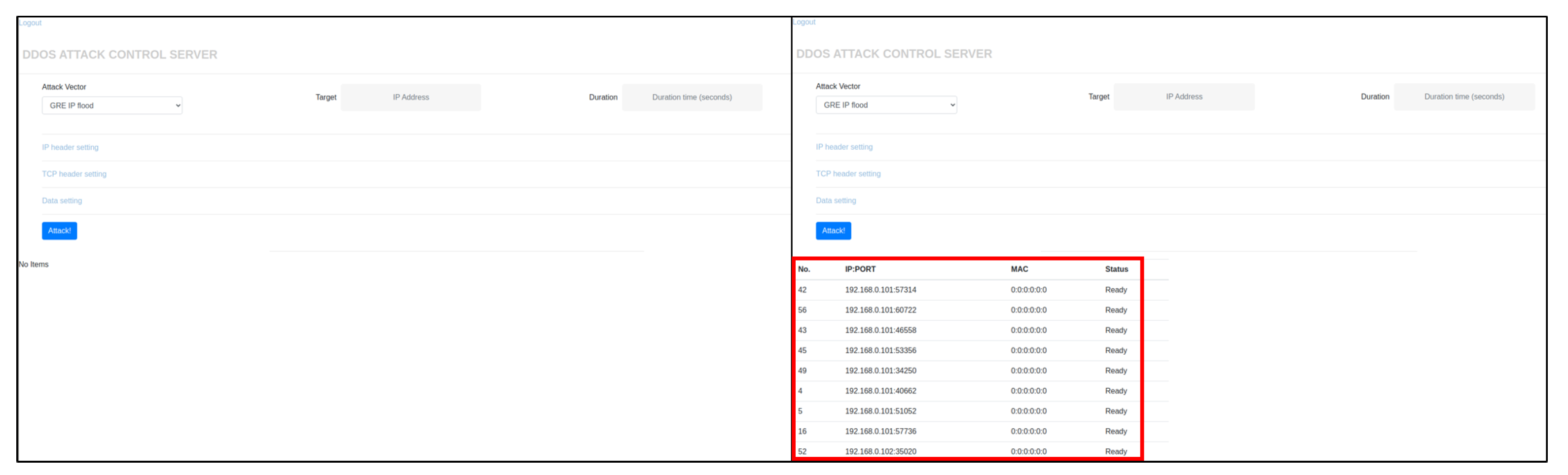
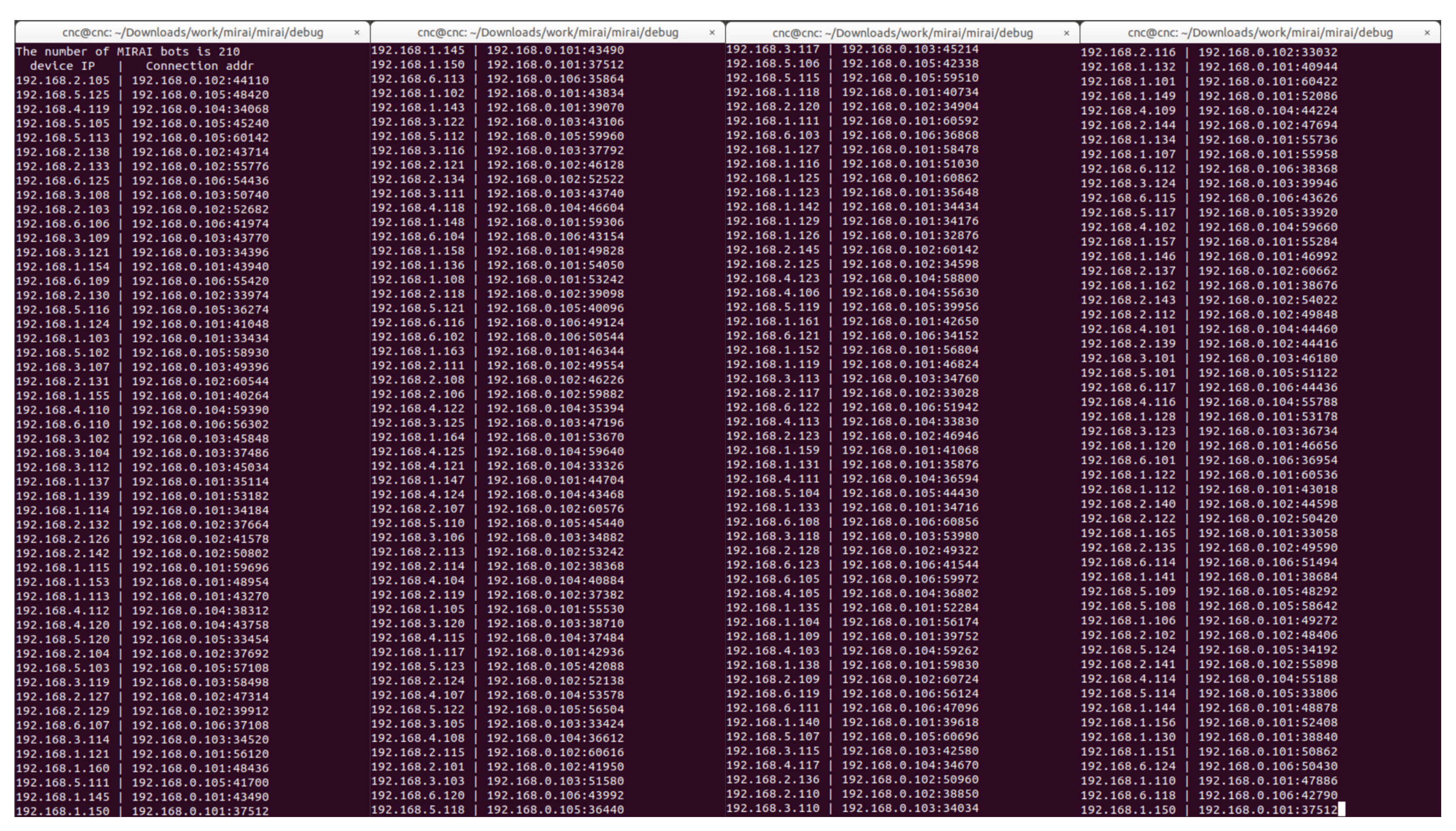
5. Experiments and Evaluations by Changing the Number of Master Bot and Scan Packet
5.1. Experimental Environment
5.1.1. Real World
5.1.2. Virtual World
5.2. Performance Analysis
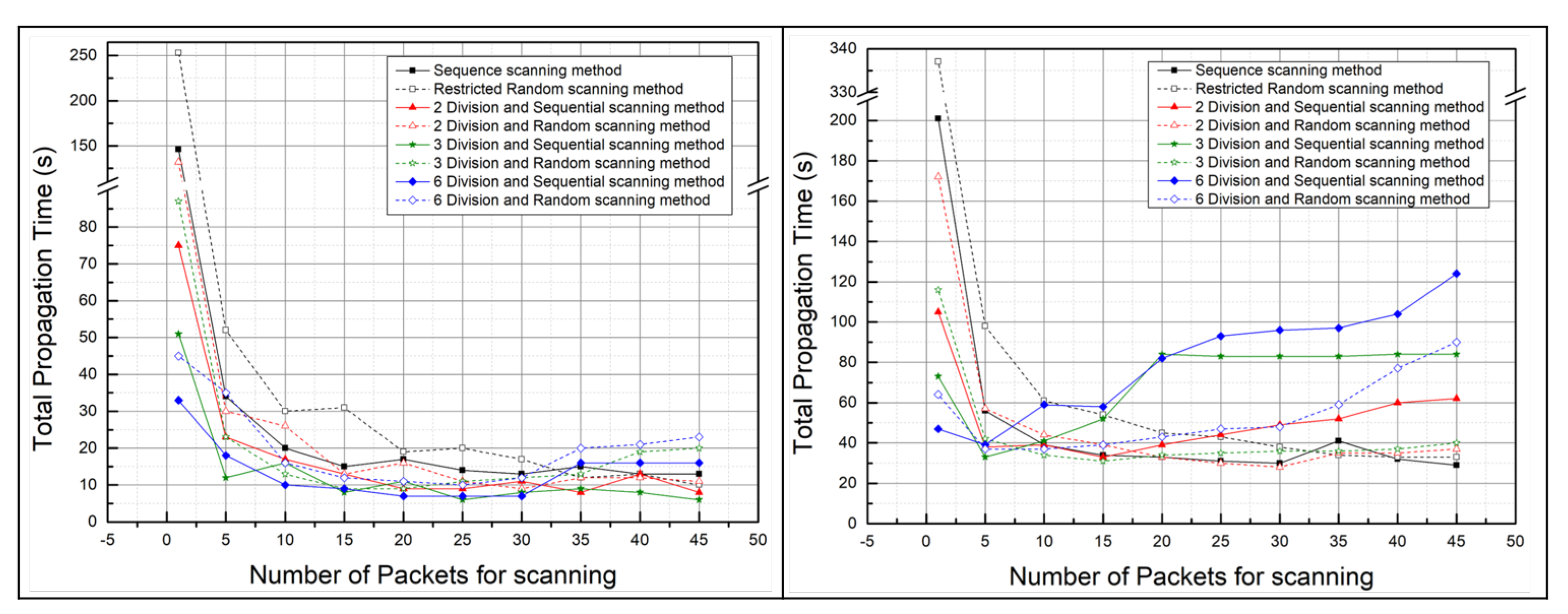
5.2.1. The Total Propagation Time: Malware Propagation Performance According to the Number of Scan Packets
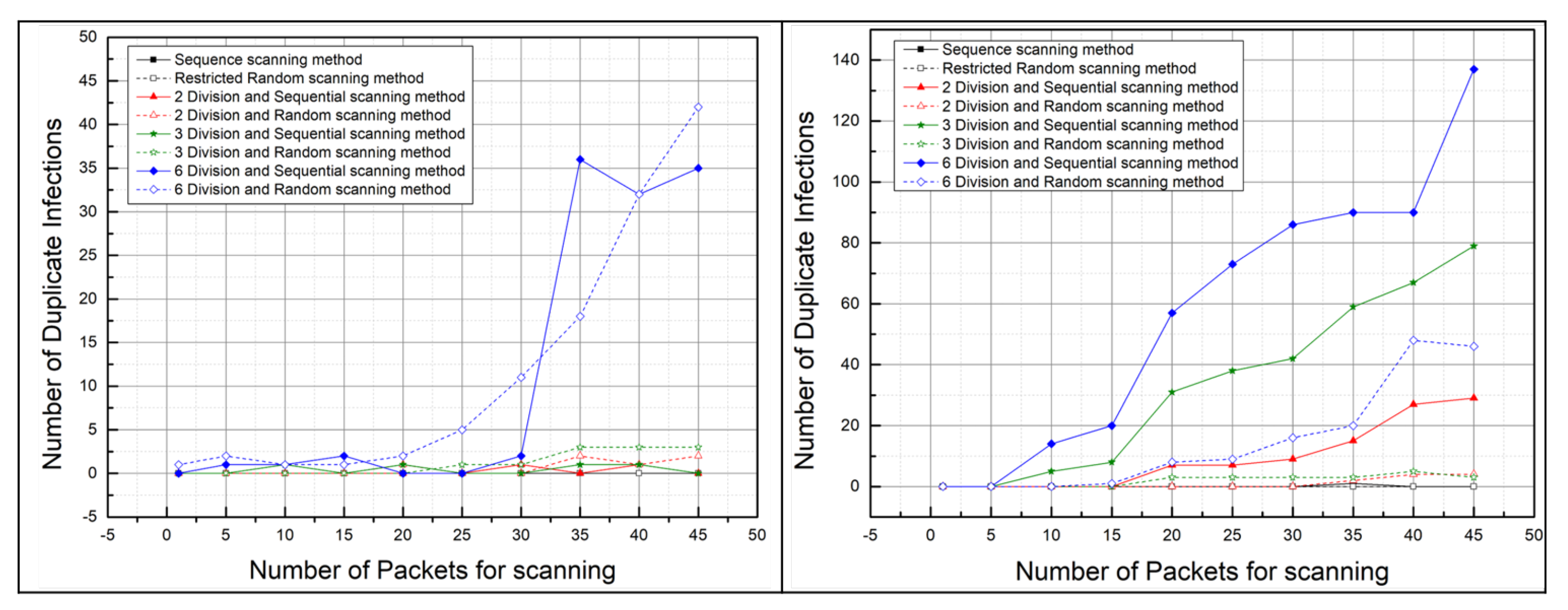
5.2.2. The Number of Duplicate Infections: Malware Propagation Performance According to the Number of Scan Packets
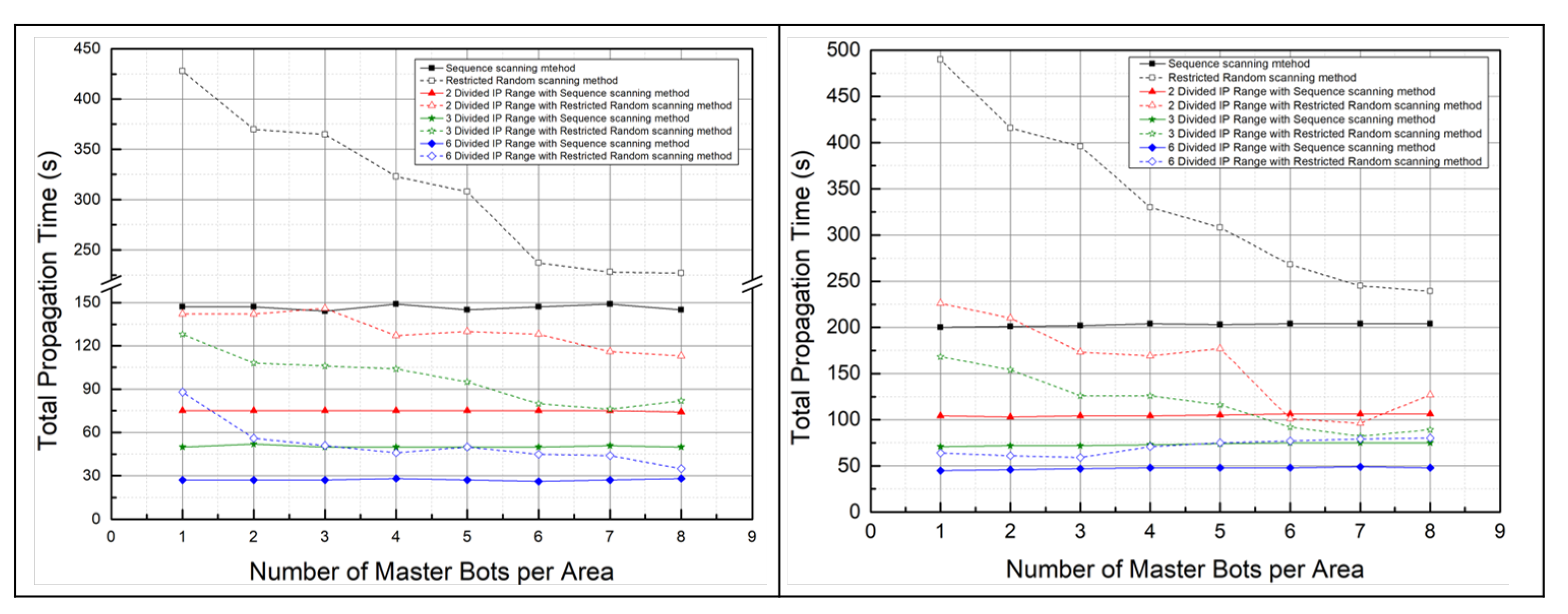
5.2.3. Malware Propagation Performance According to the Number of Master Bots
5.2.4. Comparison of the Total Propagation Time and the Number of Duplicate Infection
6. Conclusions
6.1. Implications
6.2. Future Works
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Service Provider Opportunities & Strategies in the Internet of Things. Available online: https://docplayer.net/11453801-Machina-research-research-report-sponsored-by-cisco-service-provider-opportunities-strategies-in-the-internet-of-things.html (accessed on 16 April 2021).
- Wireless Communication Service Subscriber Statistics. Available online: https://www.msit.go.kr/SYNAP/skin/doc.html?fn=fdb04f93dec854f8856af3ef7c8b57fb&rs=/SYNAP/sn3hcv/result/ (accessed on 16 April 2021).
- 5G Americas white Paper 5G-the Future of IoT. Available online: https://www.5gamericas.org/wp-content/uploads/2019/07/5G_Americas_White_Paper_on_5G_IOT_FINAL_7.16.pdf (accessed on 16 April 2021).
- Internet of Things-Active Connections Worldwide 2015–2025. Available online: https://www.statista.com/statistics/1101442/iot-number-of-connected-devices-worldwide (accessed on 16 April 2021).
- Hategekimana, F.; Whitaker, T.J.; Pantho, M.J.H.; Bobda, C. IoT Device security through dynamic hardware isolation with cloud-Based update. J. Syst. Archit. 2020, 109, 101827. [Google Scholar] [CrossRef]
- Zarpelão, B.B.; Miani, R.S.; Kawakani, C.T.; de Alvarenga, S.C. A survey of intrusion detection in Internet of Things. J. Netw. Comput. Appl. 2017, 84, 25–37. [Google Scholar] [CrossRef]
- Zikria, Y.B.; Kim, S.W.; Hahm, O.; Afzal, M.K.; Aalsalem, M.Y. Internet of Things (IoT) Operating Systems Management: Opportunities, Challenges, and Solution. Sensors 2019, 19, 1793. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Mid-Year Update: 2020 SonicWall Cyber Threat Report|2020 Global Cyberattack Trends. Available online: https://www.sonicwall.com/resources/2020-cyber-threat-report-mid-year-update-pdf (accessed on 16 April 2021).
- Saeed, A.; Ahmadinia, A.; Javed, A.; Larijani, H. Intelligent intrusion detection in low-power IoTs. ACM Trans. Internet Technol. (TOIT) 2016, 16, 1–25. [Google Scholar] [CrossRef]
- Mirai-Source-Code. Available online: https://github.com/jgamblin/Mirai-Source-Code (accessed on 16 April 2021).
- 2020 Sonicwall Cyber Threat Report: Threat Actors Pivot toward More Targeted Attacks, Evasive Exploits. Available online: https://www.sonicwall.com/news/2020-sonicwall-cyber-threat-report (accessed on 16 April 2021).
- 2020 Unit 42 IoT Threat Report. Available online: https://unit42.paloaltonetworks.com/iot-threat-report-2020 (accessed on 16 April 2021).
- Lim, J.; Sohn, S.; Kim, J. Proposal of Smart Segmentation Framework for preventing threats from spreading in IoT. In Proceedings of the 2020 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Korea, 21–23 October 2020; pp. 1745–1747. [Google Scholar]
- Kumar, A.; Lim, T.J. Early detection of Mirai-like IoT bots in large-scale networks through sub-sampled packet traffic analysis. In Future of Information and Communication Conference; Springer: Cham, Switzerland, 2019; pp. 847–867. [Google Scholar]
- Liu, Z.; Zhang, L.; Ni, Q.; Chen, J.; Wang, R.; Li, Y.; He, Y. An integrated architecture for IoT malware analysis and detection. In International Conference on Internet of Things as a Service; Springer: Cham, Switzerland, 2018; pp. 127–137. [Google Scholar]
- Meidan, Y.; Bohadana, M.; Mathov, Y.; Mirsky, Y.; Shabtai, A.; Breitenbacher, D.; Elovici, Y. N-baiot—Network-based detection of iot botnet attacks using deep autoencoders. IEEE Pervasive Comput. 2018, 17, 12–22. [Google Scholar] [CrossRef] [Green Version]
- Vignau, B.; Khoury, R.; Hallé, S. 10 years of IoT malware: A feature-based taxonomy. In Proceedings of the 2019 IEEE 19th International Conference on Software Quality, Reliability and Security Companion (QRS-C), Sofia, Bulgaria, 22–26 July 2019; pp. 458–465. [Google Scholar]
- Vignau, B.; Khoury, R.; Hallé, S.; Hamou-Lhadj, A. The evolution of IoT Malwares, from 2008 to 2019: Survey, taxonomy, process simulator and perspectives. J. Syst. Archit. 2021, 116, 102143. [Google Scholar] [CrossRef]
- Alrawi, O.; Lever, C.; Valakuzhy, K.; Snow, K.; Monrose, F.; Antonakakis, M. The Circle Of Life: A Large-Scale Study of The IoT Malware Lifecycle. In Proceedings of the 30th USENIX Security Symposium (USENIX Security 21), Virtual, CA, USA, 11–13 August 2021. [Google Scholar]
- Github Repo of Open Source IoT Malware. Available online: https://github.com/ifding/iot-malware/tree/master/BASHLITE (accessed on 10 August 2021).
- Mirai Botnet Sees Big 2019 Growth, Shifts Focus to Enterprises. Available online: https://threatpost.com/mirai-botnet-sees-big-2019-growth-shifts-focus-to-enterprises/146547/ (accessed on 10 August 2021).
- Antonakakis, M.; April, T.; Bailey, M.; Bernhard, M.; Bursztein, E.; Cochran, J.; Zhou, Y. Understanding the mirai botnet. In Proceedings of the 26th USENIX Security Symposium (USENIX Security 17), Vancouver, BC, Canada, 16–18 August 2017; pp. 1093–1110. [Google Scholar]
- Netlab Now Mirai Has DGA Feature Built in. Available online: https://blog.netlab.360.com/new-mirai-variant-with-dga/ (accessed on 10 August 2021).
- Overall IPv4 Address Allocation Status. Available online: https://xn--3e0bx5euxnjje69i70af08bea817g.xn--3e0b707e/jsp/statboard/IPAS/ovrse/total/currentV4Addr.jsp (accessed on 16 April 2021).
- State of the IoT 2020: 12 Billion IoT Connections, Surpassing Non-IoT for the First Time. Available online: https://iot-analytics.com/state-of-the-iot-2020-12-billion-iot-connections-surpassing-non-iot-for-the-first-time (accessed on 16 April 2021).

| Categories | BASHLITE (2014) | Hajime (2016) | Mirai (2016) |
|---|---|---|---|
| Target Arch. | MIPS, ARM | MIPS, ARM, x86/64 | MIPS, ARM, x86/64 |
| Capability | DDoS | not known | DDoS |
| Scan | Random | Random | Stateless, Random |
| Infection | Dictionary | Dictionary | Balanced |
| password | password | dictionary password | |
| Architecture | Centralized C&C | P2P | Centralized C&C |
| (dedicated | (Decentralized) | (dedicated | |
| protocol) | protocol) | ||
| Persist | None | Anti reboot | Anti reboot |
| DGA | None | None | Use |
| Source code | [20] | not available | [10] |
| Categories | BrickerBot (2017) | IoT Reaper (2017) | VPNFilter (2018) |
|---|---|---|---|
| Target Arch. | BASH Script | Targeted | MIPS, ARM, x86/64, |
| manufacturer | BASH Script | ||
| Capability | Destruction | DDoS | Destruction, |
| Info. Theft, | |||
| Man in the Middle, | |||
| Resource abuse | |||
| Scan | Stateless, Random | Random | Stateless, Random |
| Infection | Balanced | Multiple CVE | Multiple CVE |
| dictionary password | |||
| Architecture | Centralized C&C | Centralized C&C | Centralized C&C |
| (dedicated | (dedicated | (dedicated | |
| protocol) | protocol) | protocol) | |
| Persist | None | Anti reboot | Anti reboot, |
| Alter firmware | |||
| DGA | None | None | Use |
| Source code | not available | not available | not available |
| Reason | IP Range |
|---|---|
| Loopback | 127.0.0.0/8 |
| Invalid address space | 0.0.0.0/8 |
| General Electric Company | 3.0.0.0/8 |
| Hewlett-Packard Company | 15.0.0.0/7 |
| US Postal Service | 56.0.0.0/8 |
| Internal network | 10.0.0.0/8 |
| 192.168.0.0/16 | |
| 172.16.0.0/14 | |
| IANA NAT reserved | 169.254.0.0/16 |
| 100.64.0.0/10 | |
| IANA Special use | 198.18.0.0/15 |
| Multicast | 224.0.0.0-239.255.255.255 |
| CPU | Intel(R) Core(TM) i7 CPU 960 @ 3.20 GHz | |
| Server | RAM | 12 G |
| OS | Ubuntu bionic Ubuntu 18.04.5 LTS) | |
| CPU | ARMv7 Processor 5(v7l) | |
| Gateway | RAM | 497 MB |
| OS | OpenWrt SNAPSHOT r13968-c5360894dc | |
| CPU | ARMv7 Processor 4 (v7l) | |
| IoT device | RAM | 1 GB |
| OS | Raspbian GNU/Linux 9 stretch |
| Host PC | CPU | Intel(R) Core(TM) i9-10900 CPU |
| @ 2.80 GHz, 20 Core | ||
| RAM | 128 GB | |
| OS | Ubuntu bionic Ubuntu 18.04.5 LTS) | |
| Emulated | CPU | Intel(R) Core(TM) i9-10900 CPU |
| Server | @ 2.80 GHz, 4 Core | |
| RAM | 8 GB | |
| OS | Ubuntu bionic Ubuntu 18.04.5 LTS) | |
| Emulated | CPU | ARM1176 |
| IoT device | (ARMv6-compatible processor rev 7 (v6l)) | |
| RAM | 253 MB | |
| OS | Raspbian GNU/Linux 9 stretch |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hwang, S.-Y.; Kim, J.-N. A Malware Distribution Simulator for the Verification of Network Threat Prevention Tools. Sensors 2021, 21, 6983. https://doi.org/10.3390/s21216983
Hwang S-Y, Kim J-N. A Malware Distribution Simulator for the Verification of Network Threat Prevention Tools. Sensors. 2021; 21(21):6983. https://doi.org/10.3390/s21216983
Chicago/Turabian StyleHwang, Song-Yi, and Jeong-Nyeo Kim. 2021. "A Malware Distribution Simulator for the Verification of Network Threat Prevention Tools" Sensors 21, no. 21: 6983. https://doi.org/10.3390/s21216983
APA StyleHwang, S.-Y., & Kim, J.-N. (2021). A Malware Distribution Simulator for the Verification of Network Threat Prevention Tools. Sensors, 21(21), 6983. https://doi.org/10.3390/s21216983






