User Recommendation for Data Sharing in Social Internet of Things
Abstract
1. Introduction
- It recommends users who can share necessary data by considering both devices and users in SloT environments.
- It identifies a user’s IoT device preference which indicates the interaction degree between users and IoT device through the interaction analysis between users and IoT devices.
- It extracts a user’s interest keywords which appear frequently in social activities through the interaction analysis between users.
- It recommends new top-N users who have a high user similarity based on the IoT device preference and interest keywords.
2. Related Work
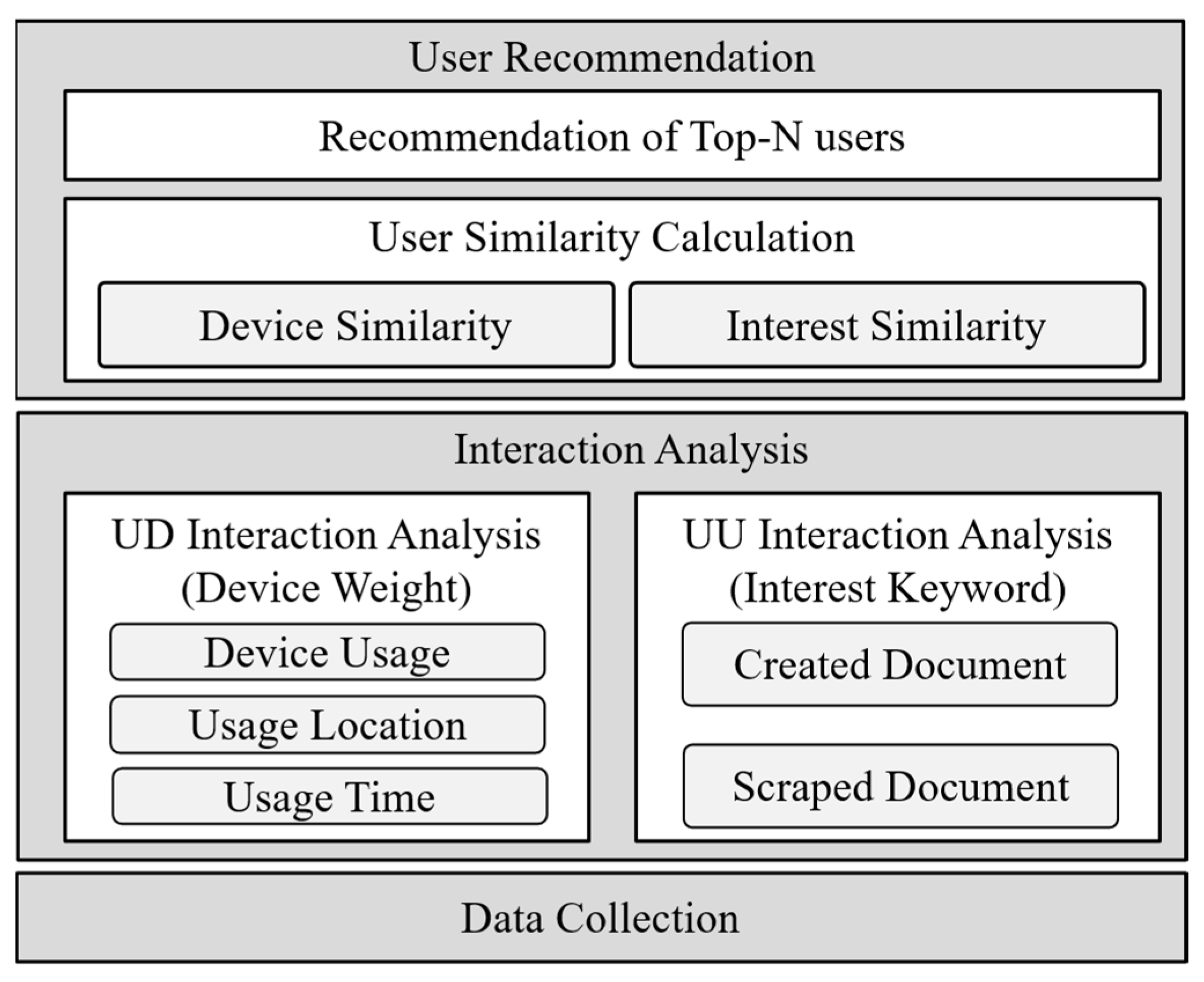
3. User Recommendation Scheme
3.1. Overall Procedure
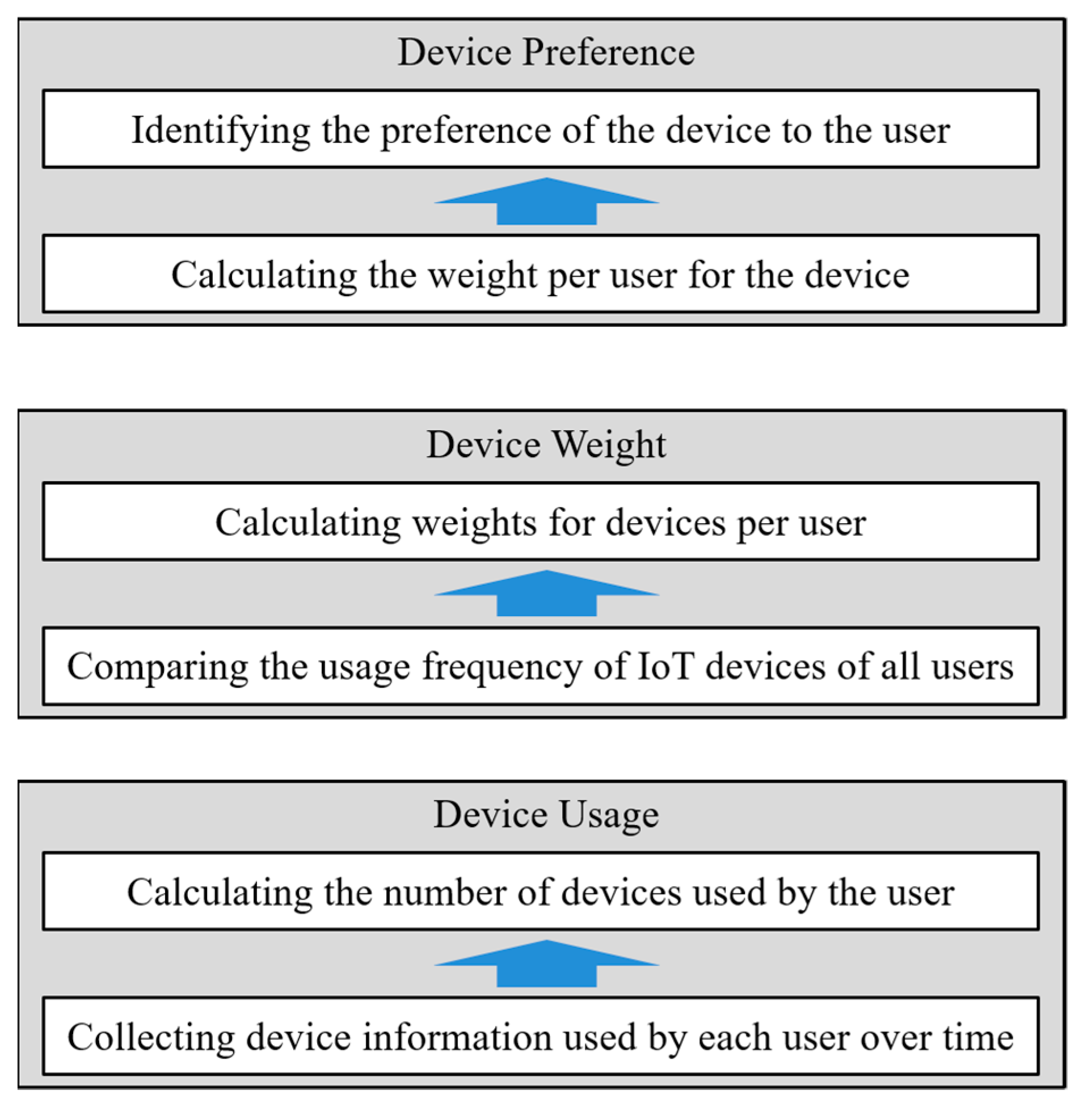
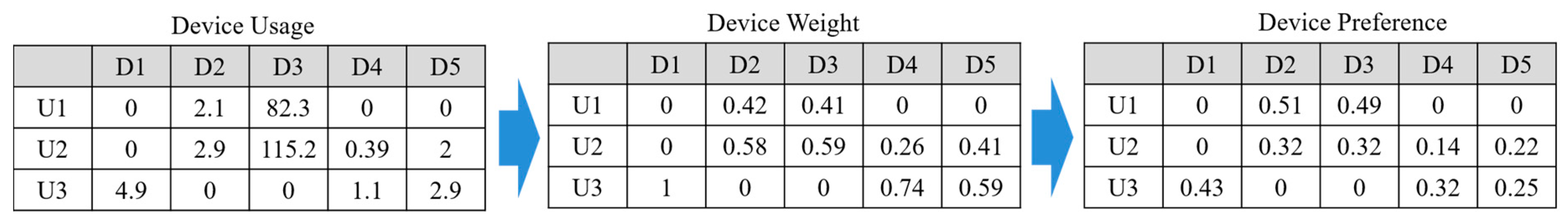
3.2. UD Interaction Analysis
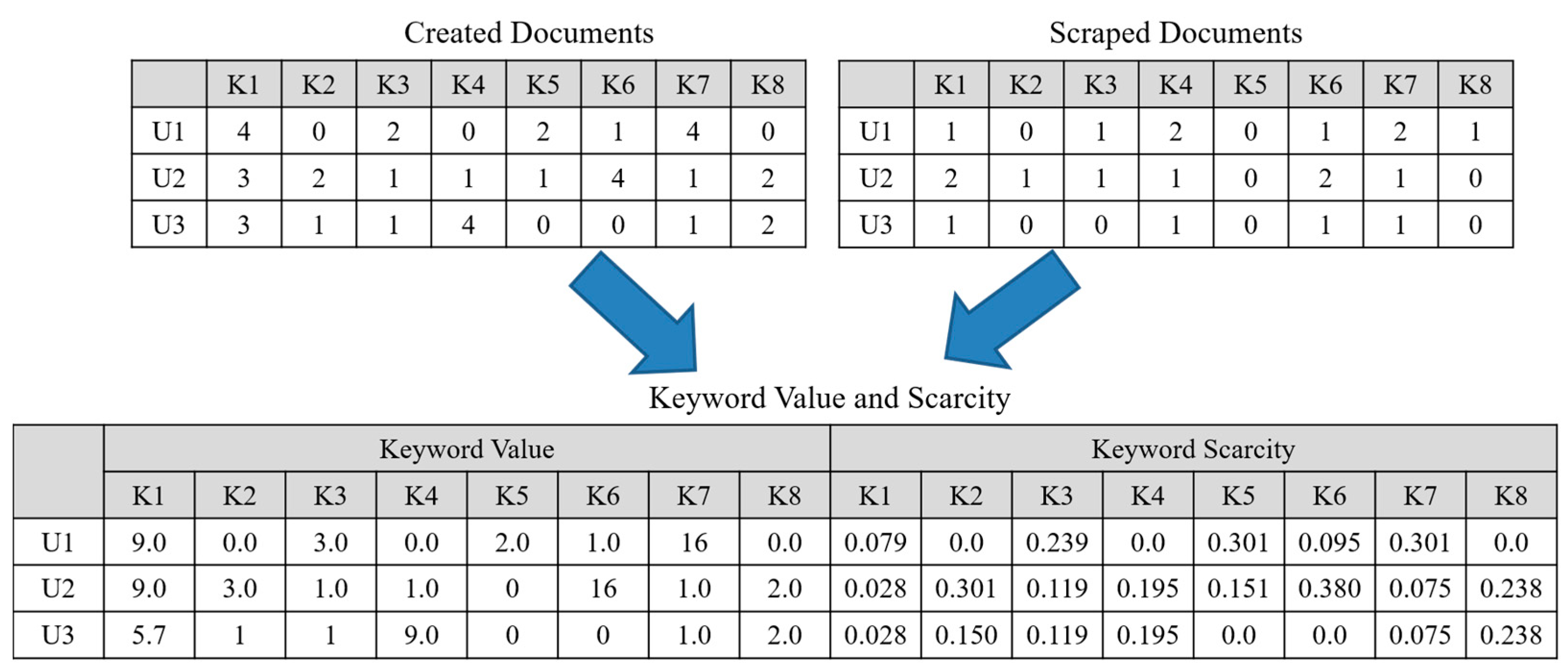
3.3. UU Interaction Analysis
3.4. User Recommendation
| Algorithm 1DataSharingAPI(recUC, target) |
| // recUC is recommended Top-N users // target is a user receiving recommended users for each i included in recUC do i ← readUC(recUC) if hrelationship(i, target) then shDataset ← reqDatasharing(i, targetU) fDataset ← filterData(shDataset, targetU) receive(fDataset, target) end if end for |
4. Performance Evaluation
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Saleem, T.J.; Chishti, M.A. Data Analytics in the Internet of Things: A Survey. Scalable Comput. Pract. Exp. 2019, 20, 607–630. [Google Scholar] [CrossRef]
- Matos, E.; Tiburski, R.T.; Moratelli, C.R.; Filho, S.J.; Amaral, L.A.; Ramachandran, G.S.; Krishnamachari, B.; Hessel, F. Context information sharing for the Internet of Things: A survey. Comput. Netw. 2020, 166, 1–19. [Google Scholar] [CrossRef]
- Shammar, E.A.; Zahary, A.T. The Internet of Things (IoT): A survey of techniques, operating systems, and trends. Libr. Hi Tech 2020, 38, 5–66. [Google Scholar] [CrossRef]
- Xiang, R.; Neville, J.; Rogati, M. Modeling relationship strength in online social networks. In Proceedings of the International Conference on World Wide Web, Raleigh, NC, USA, 26–30 April 2010. [Google Scholar]
- Bok, K.; Ko, G.; Lim, J.; Yoo, J. Personalized Content Recommendation Scheme Based on Trust in Online Social Networks. Concurr. Comp-Pract. E. 2020, 32, 1–14. [Google Scholar]
- Bok, K.; Lee, C.; Yoo, J. Recommending Similar Users Using Moving Patterns in Mobile Social Networks. Comput. Electr. Eng. 2019, 77, 47–60. [Google Scholar] [CrossRef]
- Li, Z.; Chen, R.; Liu, L.; Min, G. Dynamic resource discovery based on preference and movement pattern similarity for large-scale social Internet of Things. IEEE Internet Things J. 2016, 3, 581–589. [Google Scholar] [CrossRef]
- Hussein, D.; Han, N.; Lee, S.M.; Crespi, G.N.; Bertin, E. Towards a dynamic discovery of smart services in the social internet of things. Comput. Electr. Eng. 2017, 58, 429–443. [Google Scholar] [CrossRef]
- Mardini, W.; Khamayseh, Y.; Khatatbeh, M.H. Genetic algorithm for friendship selection in social IoT. In Proceedings of the International Conference on Engineering & MIS, Monastir, Tunisia, 8–10 May 2017. [Google Scholar]
- Rho, S.; Chen, Y. Social Internet of Things: Applications, architectures and protocols. Future Gener. Comput. Syst. 2019, 92, 959–960. [Google Scholar] [CrossRef]
- Aljubairy, A.; Zhang, W.E.; Sheng, Q.Z.; Alhazmi, A.A.F. SIoTPredict: A Framework for Predicting Relationships in the Social Internet of Things. In Proceedings of the International Conference on Advanced Information Systems Engineering, Grenoble, France, 8–12 June 2020. [Google Scholar]
- Roopa, M.S.; Pattar, S.; Buyya, R.; Venugopal, K.R.; Iyengar, S.S.; Patnaik, L.M. Social Internet of Things (SIoT): Foundations, thrust areas, systematic review and future directions. Comput. Commun. 2019, 139, 32–57. [Google Scholar]
- Chung, K.C.; Liang, S.W. An Empirical Study of Social Network Activities via Social Internet of Things (SIoT). IEEE Access 2020, 8, 48652–48659. [Google Scholar] [CrossRef]
- Girau, R.; Martis, S.; Atzori, L. Lysis: A Platform for IoT Distributed Applications Over Socially Connected IoT devices. IEEE Internet Things J. 2017, 4, 40–51. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G.; Nitti, M. The Social Internet of Things (SIoT)—When social networks meet the Internet of Things: Concept, architecture and network characterization. Comput. Netw. 2012, 56, 3594–3608. [Google Scholar] [CrossRef]
- Perera, C.; Zaslavsky, A.B.; Christen, P.; Georgakopoulos, D. Context Aware Computing for The Internet of Things: A Survey. IEEE Commun. Surv. Tutor. 2014, 16, 414–454. [Google Scholar] [CrossRef]
- Lu, Y.; Zhao, Z.; Zhang, B.; Gao, Q. An advertisement dissemination strategy with maximal influence for Internet-of-Vehicles. Int. J. Distrib. Sens. N. 2019, 15, 1–12. [Google Scholar] [CrossRef]
- Butt, T.A.; Iqbal, R.; Shah, S.C.; Umar, T. Social Internet of Vehicles: Architecture and enabling technologies. Comput. Electr. Eng. 2018, 69, 68–84. [Google Scholar] [CrossRef]
- Kang, D.H.; Choi, H.S.; Rhee, W.S. SRS: Social Correlation Group based Recommender System for Social IoT Environment. Int. J. Contents 2017, 13, 53–61. [Google Scholar]
- Chen, Z.; Ling, R.; Huang, C.M.; Zhu, X. A scheme of access service recommendation for the Social Internet of Things. Int. J. Commun. Syst. 2016, 29, 694–706. [Google Scholar] [CrossRef]
- Wang, W.; Tan, J.; Ding, W.; Zhang, Y.; Yang, F.; Song, J.; Han, Z. Intercommunity detection scheme for social Internet of things. IEEE Internet Things J. 2018, 5, 4550–4557. [Google Scholar] [CrossRef]
- Chen, Y.; Zhou, M.; Zheng, Z.; Chen, D. Time-Aware Smart IoT device Recommendation in Social Internet of Things. IEEE Internet Things J. 2020, 7, 2014–2027. [Google Scholar] [CrossRef]
- Arjunasamy, A.; Rathi, S. Relationship Based Heuristic for Selecting Friends in Social Internet of Things. Wirel. Pers. Commun. 2019, 107, 1537–1547. [Google Scholar] [CrossRef]
- Ramasamy, T.; Arjunasamy, A. Advanced Heuristics for Selecting Friends in Social Internet of Things. Wirel. Pers. Commun. 2017, 97, 4951–4965. [Google Scholar] [CrossRef]
- Kasnesis, P.; Patrikakis, C.Z.; Kogias, D.; Toumanidis, L.; Venieris, I.S. Cognitive friendship and goal management for the social IoT. Comput. Electr. Eng. 2017, 58, 412–428. [Google Scholar] [CrossRef]
- Lee, H.; Kim, K.; Kwon, J. A pervasive interconnection technique for efficient information sharing in social IoT environment. Int. J. Smart Home 2016, 10, 9–22. [Google Scholar] [CrossRef]
- Jung, J.; Chun, S.; Jin, X.; Lee, K. Quantitative Computation of Social Strength in Social Internet of Things. IEEE Internet Things J. 2018, 5, 4066–4075. [Google Scholar] [CrossRef]
- Kang, D.H.; Choi, H.S.; Rhee, W.S. Social correlation group generation mechanism in social IoT environment. In Proceedings of the Ubiquitous and Future Networks, Vienna, Austria, 5–8 July 2016. [Google Scholar]
- Nitti, M.; Atzori, L.; Cvijikj, I.P. Friendship selection in the social internet of things: Challenges and possible strategies. IEEE Internet Things J. 2015, 2, 240–247. [Google Scholar] [CrossRef]
- Xing, W.; Ghorbani, A. Weighted pagerank algorithm. In Proceedings of the Annual Conference on Communication Networks and Services Research, Fredericton, NB, Canada, 19–21 May 2004. [Google Scholar]
- Pham, H.; Shahabi, C.; Liu, Y. EBM: An entropy-based model to infer social strength from spatiotemporal data. In Proceedings of the ACM SIGMOD International Conference on Management of Data, New York, NY, USA, 22–27 June 2013. [Google Scholar]
- Medina, C.P.; Ramon, M.R.R. Using TF-IDF to Determine Word Relevance in Document Queries Juan. New Educ. Rev. 2015, 42, 40–51. [Google Scholar] [CrossRef]
- IoT Network Dataset. Available online: http://www.social-iot.org/index.php?p=downloads (accessed on 18 August 2020).
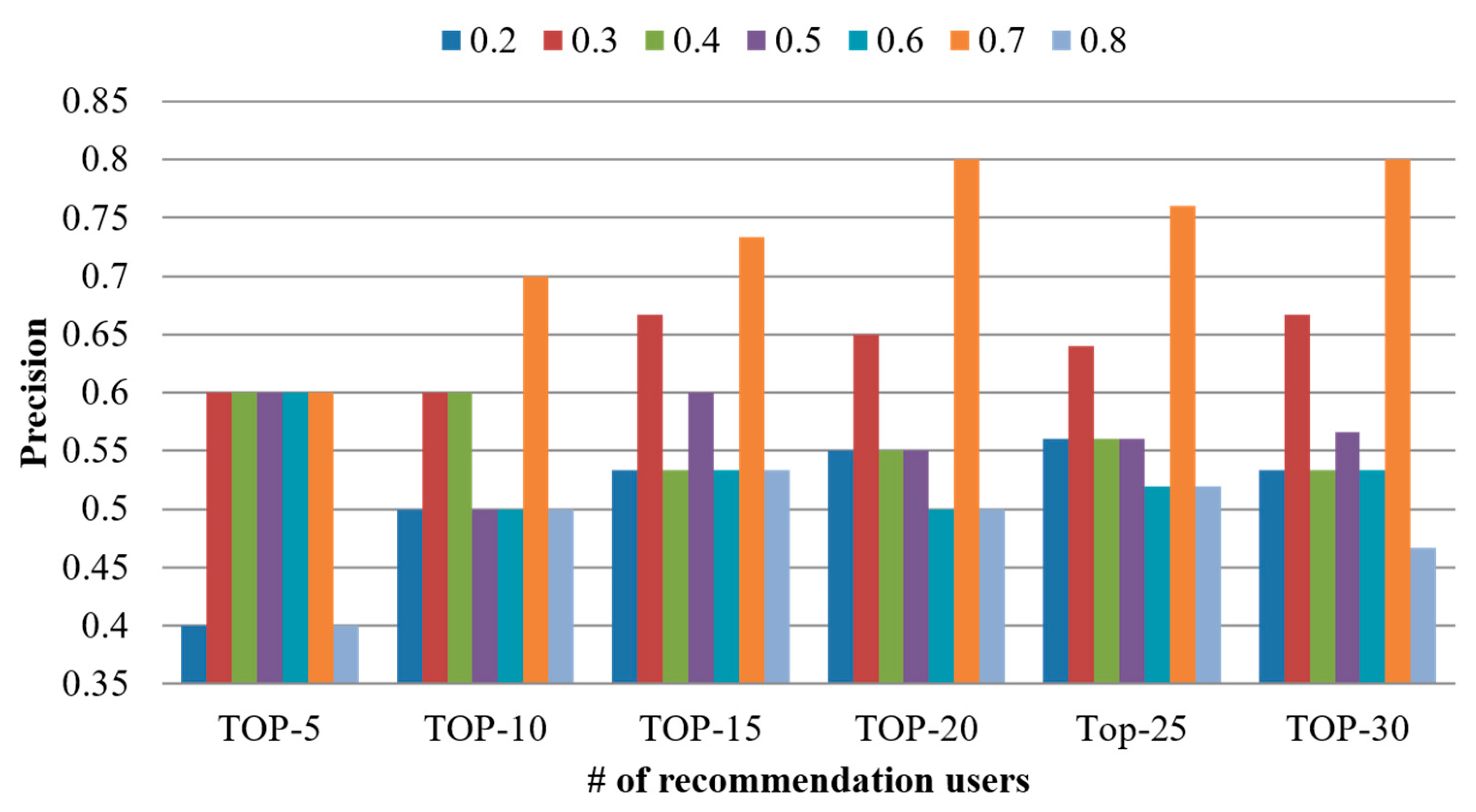
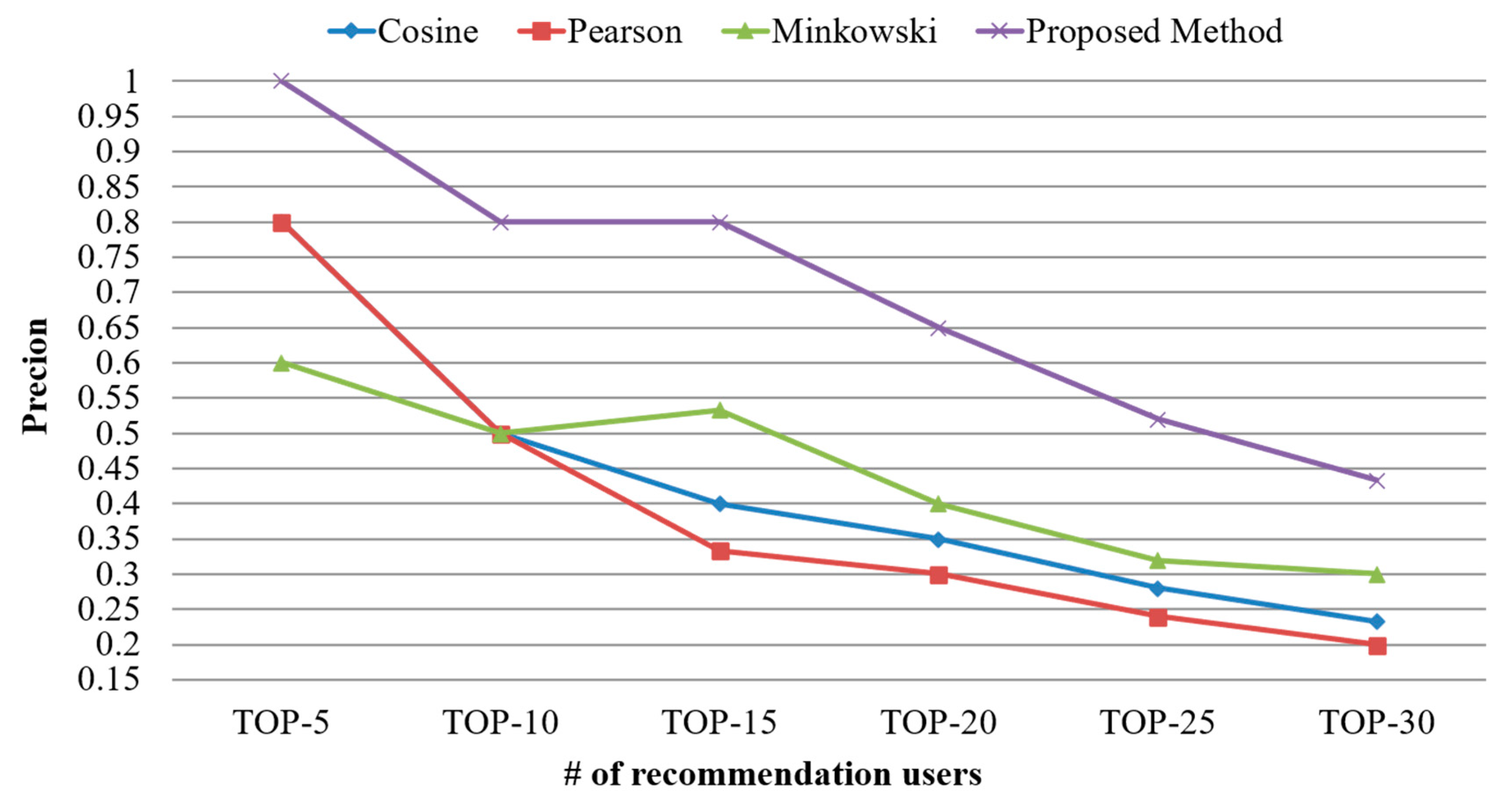
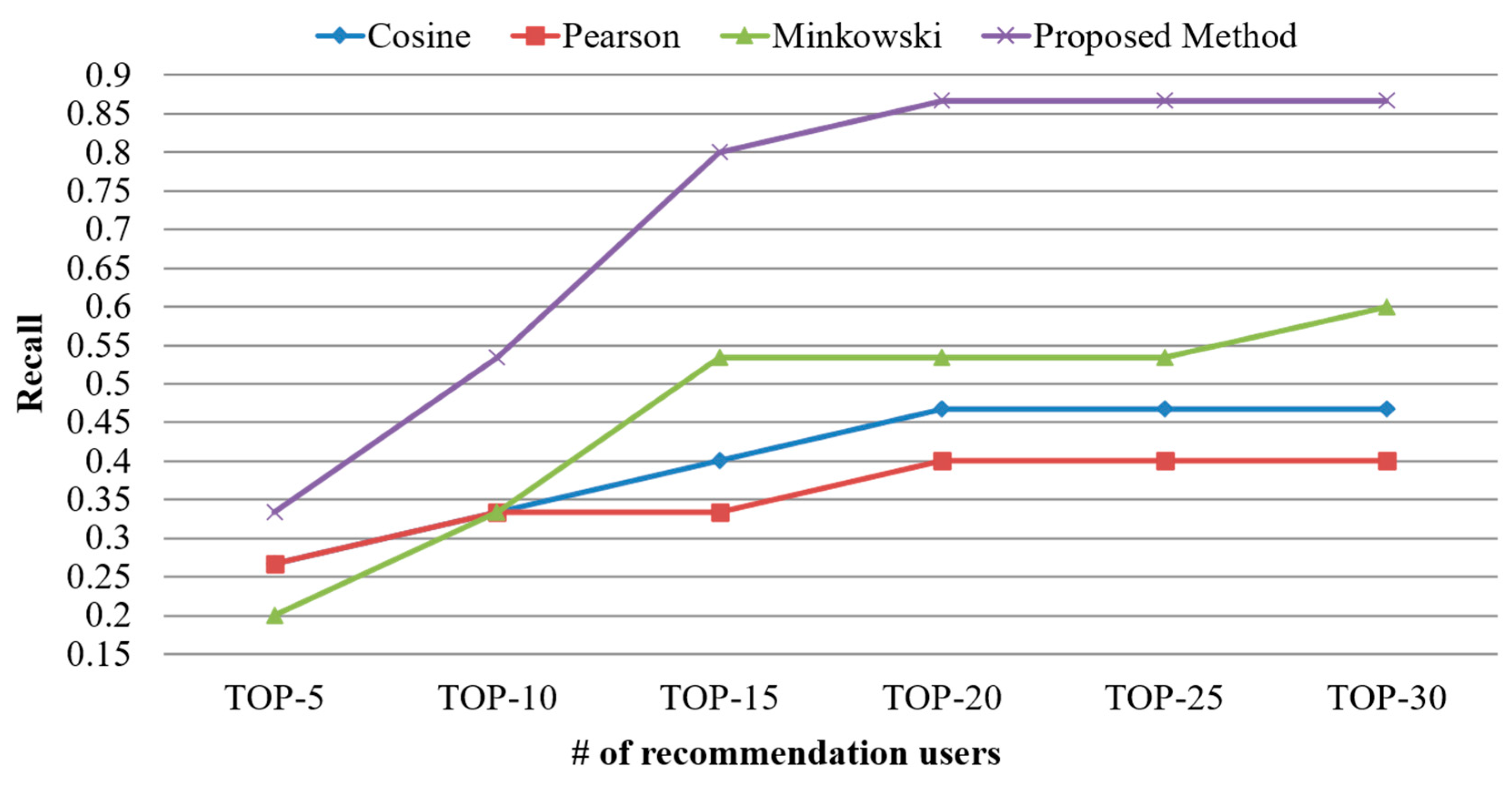
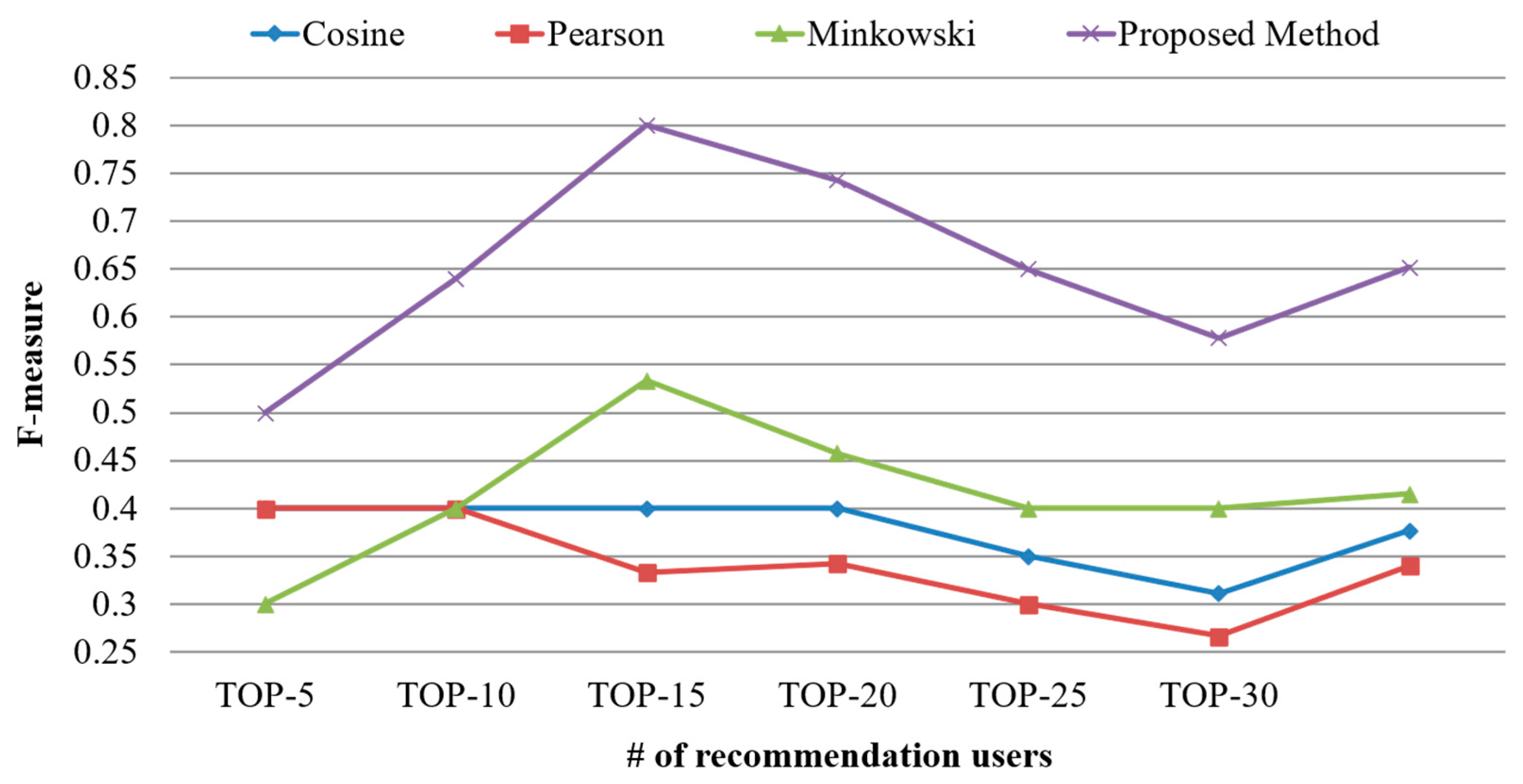
| User | # of Created Documents | # of Scraped Documents |
|---|---|---|
| U1 | 4 | 2 |
| U1 | 4 | 2 |
| U3 | 4 | 2 |
| Parameters | Values |
|---|---|
| Number of users | 4000 |
| Number of IoT devices | 18 |
| Measurement period | 30 |
| Number of user created documents | 0~30 |
| Number of scraped documents | 0~10 |
| Weight (α) | 0~1 |
| Number of recommendations | 5~30 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bok, K.; Kim, Y.; Choi, D.; Yoo, J. User Recommendation for Data Sharing in Social Internet of Things. Sensors 2021, 21, 462. https://doi.org/10.3390/s21020462
Bok K, Kim Y, Choi D, Yoo J. User Recommendation for Data Sharing in Social Internet of Things. Sensors. 2021; 21(2):462. https://doi.org/10.3390/s21020462
Chicago/Turabian StyleBok, Kyoungsoo, Yeondong Kim, Dojin Choi, and Jaesoo Yoo. 2021. "User Recommendation for Data Sharing in Social Internet of Things" Sensors 21, no. 2: 462. https://doi.org/10.3390/s21020462
APA StyleBok, K., Kim, Y., Choi, D., & Yoo, J. (2021). User Recommendation for Data Sharing in Social Internet of Things. Sensors, 21(2), 462. https://doi.org/10.3390/s21020462





