Abstract
In this study, we consider energy-efficient wireless-powered secure communications, in which N sets of transmitter, receiver, and energy harvesting (EH) nodes exist; each EH node is allowed only to harvest energy from the transmitted signals but is not to permitted to decode information. To maximize the sum secrecy energy efficiency (SEE) of the node sets while ensuring minimum EH requirement for each EH node, we propose a distributed transmit power control algorithm using a dual method, where each transmitter adjusts its transmit power iteratively until convergence without sharing information with the other node sets. Through simulations under various environments, we show that the proposed scheme surpasses conventional schemes in terms of the sum SEE and has significantly reduced computation time compared with the optimal scheme, which suggests the effectiveness and applicability of the proposed distributed method.
1. Introduction
With the rapid growth of mobile traffic and smart devices, next-generation wireless communications are expected to have increased demands for high data rates, wide coverage, and high levels of security [1,2]. At the same time, the energy consumption would inevitably increase as the functions of mobile devices become more diverse. This may cause inconvenience to users as the battery may need to be recharged or replaced more often to extend the lifetime of the network. Accordingly, several methods, such as energy-efficient protocols [3], resource allocation [4,5], and multi-antenna techniques [6,7], have been proposed to improve the energy efficiencies of networks.
In addition to energy-efficient use of resources, energy harvesting (EH) technology has emerged to solve the problem of energy shortages in wireless nodes [8,9,10,11,12]. In particular, the methods to design EH systems were proposed in [8,9], and the potential of EH technology as a promising means to enable self-sustainable operations of wireless nodes was discussed in [10,11,12]. Recent investigations on energy efficiency optimization have been also reported for wireless-powered networks, in which EH-enabled nodes exist [13,14,15,16,17]. In [13], joint optimization of user scheduling and power allocation was studied to maximize energy efficiency considering the characteristics of EH. The authors of [14] investigated a proportional fair energy efficiency method that considers energy efficiency and user fairness simultaneously. In [15,16], resource allocation strategies were proposed to improve the energy efficiency of wireless-powered cognitive radio networks (CRNs). Moreover, the authors of [17] proposed the max–min antenna selection scheme for EH-based two-way relaying and analyzed the diversity gain.
Network diversification also causes increased concerns regarding security issues between different networks because there is increased risk of eavesdropping by unlicensed users when secret keys are shared between legitimate users [1,2]. In this context, a number of studies have been conducted on physical layer security (PLS) to ensure secure communications without relying on secret keys, such as cooperative relaying [18,19] and jamming signal transmission [20]. Regarding PLS and EH simultaneously, optimal policies for EH-enabled relays [21,22] and an optimal resource allocation considering transmit power and EH ratio [23] have been proposed for wireless-powered secure communications (WPSCs). The optimal policy of a friendly jammer capable of EH has also been studied to help secure communication between licensed nodes [24].
Unlike the aforementioned studies that focus only on energy efficiency [3,4,5,6,7,13,14,15,16,17] or PLS [18,19,20,21,22,23,24], secrecy energy efficiency (SEE), which is defined as the ratio of the secrecy rate to dissipated power, was suggested to achieve a balance between energy efficiency and secure communication [25,26,27,28,29,30]. For example, resource allocations including transmit power and beamforming vectors were optimized to maximize the SEE in CRNs [25,27] and multi-antenna systems [26,28], respectively. Furthermore, the problem of SEE optimization was investigated in multi-antenna and multi-user systems with confidentiality and reliability constraints [29], and the optimal control parameters including first- and second-layer power splitting ratios, beamforming vectors, and artificial noise covariance matrix were derived to maximize the SEE in multi-antenna wireless-powered networks [30]. However, only simple scenarios without co-channel interference were considered in [25,26], and high computational complexity and information sharing among the nodes are needed to resolve the problems noted in [27,28,29,30]. Therefore, a distributed algorithm with low complexity that can be operated in real systems is required for energy-efficient WPSCs with co-channel interference. The literature survey is summarized in Table 1.

Table 1.
Literature Survey.
In this study, we investigate a distributed transmit power control (TPC) for energy-efficient WPCSs. The main contributions can be summarized as follows.
- We consider WPSCs where the EH nodes harvest energy from the transmitted signals but are not allowed to decode private information shared between the transmitter and receiver (Tx-Rx) pairs. Given this scenario, we formulate an optimization problem to find the optimal transmit powers of the Txs to maximize the sum SEE while guaranteeing that the amount of energy collected from each EH node is greater than a minimum required value.
- To solve this non-convex problem with low complexity, we propose a distributed TPC algorithm using dual decomposition, where each Tx determines its transmit power iteratively until convergence without sharing any information with the other node sets.
- Through performance evaluations under various environments, we show that the proposed scheme achieves a higher sum SEE than conventional schemes and remarkably reduced computation time compared with the optimal scheme.
The remainder of this paper is organized as follows. In Section 2, we provide the problem statement for the considered system model, and the distributed TPC algorithm for energy-efficient WPSCs is proposed in Section 3. In Section 4, the performance evaluations are shown through extensive simulations, and the conclusions are presented in Section 5.
2. System Model and Problem Statement
Figure 1 shows the schematic of the WPSCs, where N number of Tx-Rx pairs use the same frequency band for data transmissions while N number of EH nodes are permitted to only collect energy from the signals sent by the Txs; all nodes are equipped with single antenna. Since the EH nodes are not allowed to interpret the information shared between their corresponding Tx-Rx pairs, they are called untrusted nodes, and each Tx is required to adjust its transmit power to maintain information confidentiality while supplying sufficient energy to guarantee the minimum EH requirement for its EH node. The EH node associated with each Tx-Rx pair is assumed to be predetermined, and the set of these nodes is denoted as , i.e., . The channel gain between Tx i and Rx j is denoted as and that between Tx i and EH node j is denoted as , which are assumed to follow a discrete time block-fading model.
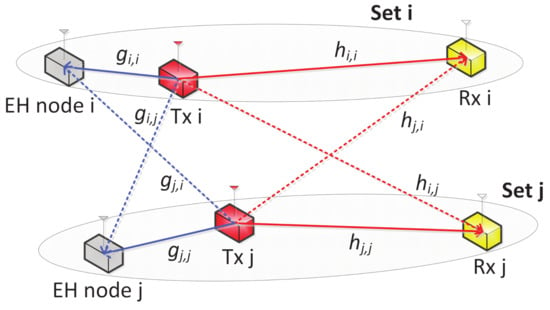
Figure 1.
System model of WPSCs showing only two node sets for brevity.
Then, the signal received at Rx i is represented by
where denotes the normalized data symbol transmitted by Tx i with transmit power , and indicates the noise at Rx i.
From (1), the achievable spectral efficiency (SE) is obtained as
At the same time, the signal received at EH node i is expressed as
where . Considering that each EH node can harvest energy not only from the signal sent by Tx i but also from the signals sent by other Txs, the total harvested energy at EH node i is given by
where is the energy conversion efficiency. On the other hand, if EH node i overhears the signal sent by Tx i instead of harvesting energy, its achievable SE is represented by
From (2) and (5), the secrecy rate of node set i can be defined as the rate difference between the legitimate and eavesdropping links [31] as follows:
where .
Moreover, the total power consumption at node set i can be obtained as
where is the constant energy consumed by the circuits of each node set.
From (6) and (7), the SEE of node set i can be defined as the ratio of secrecy rate to total power consumption (bits/Hz/Joule), which can be formulated as follows:
It should be noted that this metric indicates how efficiently energy can be used to transmit secret information.
Based on these equations, we develop the optimization problem to find the optimal transmit powers of the Txs to maximize the sum SEE while guaranteeing the minimum EH requirement, , for each EH node, as follows.
where and is the maximum transmit power allowed for each Tx. The problem in (9) is non-convex because of the fractional objective function and interference term; hence, the optimal solution of cannot be derived in a closed-form. The optimal solutions can be numerically found by brute-force search, where each is quantized with M equally spaced values and all possible combinations are evaluated to find the optimal value. However, the channel state information (CSI) of all wireless links must be available to implement this method, and a high computational complexity of is incurred, which increases exponentially with the number of node sets.
3. Distributed Transmit Power Control Algorithm
In this section, we present the distributed TPC algorithm, which can be operated with low complexity without sharing any information with the other node sets.
We decompose the original problem in (9) into N subproblems, which are then solved independently with low computational complexity [32]. In the subproblem, each Tx finds the transmit power to maximize its own SEE while ensuring the minimum EH requirement, which is formulated as follows:
With defining , the objective function in (10) is converted from a fractional form to an equivalent subtractive form, , using nonlinear fractional programming [33]. Accordingly, the subproblem in (10) is reformulated as
To derive the transmit power of each Tx using the dual method, we denote the Lagrangian function of (11) as follows.
where and are the respective Lagrange multipliers of each constraint of (11).
The dual objective is then defined as
Using (13), the dual problem can be formulated as
To find the suboptimal value of , we build the Karush-Kuhn-Tucker (KKT) conditions with the complementary slackness, as follows.
Then, the transmit power that satisfies the KKT conditions in (15)–(18) can be derived as follows.
where and is defined as
In (19), Rx i can easily calculate by subtracting the signal power received from Tx i from the total received signal power. In addition, EH node i can measure readily because the denominator of (20) is the total received signal power at EH node i. Therefore, Tx i can determine its transmit power as shown in (19) by receiving information on from Rx i and information on and from EH node i, respectively. It should be noted that although the EH node is the untrusted node, it should send information on and to Tx i to receive enough energy to meet the EH requirement for operation. Moreover, Tx i does not need to share any information with the other node sets for calculating , thereby allowing the proposed algorithm to operate in a distributed manner.
Moreover, the Lagrange multipliers are updated using a gradient algorithm as follows.
where and are sufficiently small step sizes for the update.
The operations of the proposed algorithm are described in Algorithm 1, where . Specifically, each Tx initializes the transmit power and Lagrange multipliers randomly and calculates the SEE with the initialized transmit power. Next, the Txs determine the transmit powers according to (19) and update the Lagrange multipliers according to (21) iteratively until the transmit powers converge. The Txs also update the SEE and total consumed power with the converged transmit power to assess the convergence of the SEE. This process is repeated until the SEE converges.
| Algorithm 1 Distributed transmit power control algorithm |
| 1: Initialize , , and randomly |
| 2: repeat |
| 3: Set |
| 4: repeat |
| 5: |
| 6: for to N |
| 7: Compute according to (19) |
| 8: Update and according to (21) |
| 9: end for |
| 10: |
| 11: until |
| 12: Update and with |
| 13: until |
Given that iterations are needed to ensure that the norm of the gradient is less than in the worst-case scenario [34], the number of iterations required for convergence of the inner loop is . Moreover, T denotes the number of iterations required for convergence of the outer loop [35], and the computational complexity of the proposed algorithm is , where is the number of computations required to calculate .
4. Simulation Results and Discussion
For the performance evaluations, the following system parameters are used as default unless stated otherwise: N = 3, = = 30 dBm, dBm, dBm, and = 0.5 for . All nodes are distributed randomly over an area of 50 m × 50 m, in which the maximum distance of each signal link and EH link in the same node set is 15 m. Because EH circuits have low power sensitivity, e.g., −10∼−30 dBm for energy harvesters while −60∼−80 dBm for information receivers [12,36], the small size area is appropriate for wireless-powered networks. A simplified path loss model with a path loss exponent of 2.7 is considered for urban areas [21]. Moreover, Rayleigh fading is considered for the signal links to reflect the non-line-of-sight (nLoS) characteristics while Rician fading with a K-factor of 6 is considered for the EH links to reflect the line-of-sight (LoS) characteristics [12]. The following five schemes are considered for performance evaluation in terms of the sum SEE, which can be mathematically written as . Note that a penalty is assigned by setting the sum SEE to zero when the minimum EH constraint is violated; therefore, the effects of EH violation are inherent in the sum SEE calculations.
- Optimal scheme: With the knowledge of the CSI of all wireless links, the near-optimal performance can be found using a brute-force search with ; however, the performance for is found using a divide and conquer algorithm because of the extremely high computational complexity of the brute-force search.
- Proposed scheme: The transmit powers of the Txs are determined using the proposed algorithm given in Algorithm 1.
- max. scheme: The transmit powers of the Txs are determined to maximize the sum secrecy rate, , which is found from the divide and conquer algorithm.
- Equally reduced power (ERP) scheme [37]: All Txs use the same transmit power that maximizes the sum SEE while meeting the minimum EH constraint, and the optimal value of the transmit power is found by one-dimensional exhaustive search.
- EH max. scheme: The Txs use their maximum transmit powers to maximize the total harvested energies of the EH nodes, .
- Rand scheme: The transmit powers of the Txs are determined randomly.
Figure 2 depicts the transmit power of each Tx and the sum SEE against the number of iterations, which shows the convergence of the proposed scheme. Each Tx adjusts the transmit power to maximize its own SEE, which affects the SEEs of the other node sets. Although the transmit power update at each Tx influences the other Txs, the transmit powers of all Txs converge to stationary points with iteration progression; finally, the sum SEE also converges to a value of 8.85 within 70 iterations.
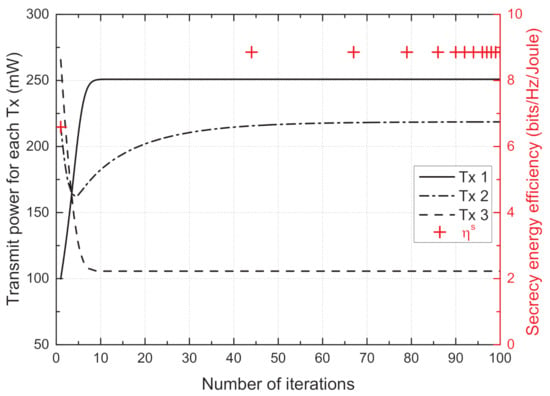
Figure 2.
Convergence of the proposed scheme.
Figure 3 depicts the sum SEE versus maximum transmit power (). In the optimal, proposed, and ERP schemes, the sum SEE increases with when dBm but converges to a stationary point when dBm. This indicates that there is an optimal transmit power at which the maximum SEE is achieved, i.e., the use of extra transmit power beyond this value reduces the sum SEE. Therefore, these schemes do not use transmit powers of more than 27 dBm even though increases over 27 dBm. On the other hand, the max. and EH max. schemes use more transmit power to maximize the sum secrecy rate and total harvested energy, respectively, as increases. However, the excessive use of transmit power exceeding 27 dBm causes inefficient energy consumption rather than improvement of the secrecy rate, so the sum SEE degrades seriously when is greater than 27 dBm. The sum SEE of the rand scheme also decreases as increases because it uses more transmit power without the adaptive TPC strategy.
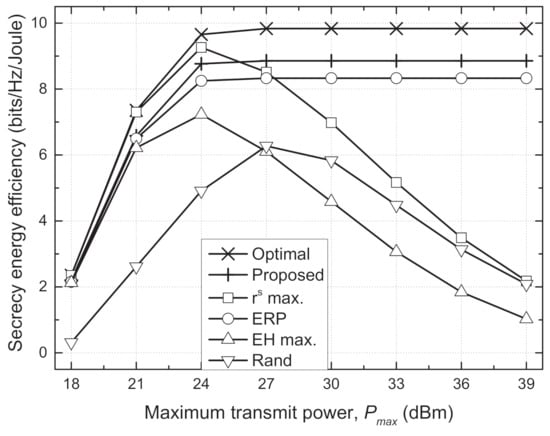
Figure 3.
Sum secrecy energy efficiency vs. maximum transmit power () for different schemes.
Figure 4 and Figure 5 depict the sum SEE versus required harvested energy () and energy conversion efficiency (), respectively. In an environment where it is difficult to satisfy the EH requirements, i.e., larger and smaller , the Txs should use the additional transmit power inefficiently to satisfy the EH requirements. For some channel realizations, e.g., deep fading, the EH requirements cannot be inherently guaranteed at extremely large or small . Then, this causes serious degradation in the sum SEE because it is set to zero when the minimum EH constraint is violated. Hence, the sum SEEs of all schemes decrease as increases or decreases, especially when dBm and . However, we can see that the proposed scheme shows a trend similar to the optimal scheme and outperforms the conventional schemes. In particular, the performance gain of the proposed scheme compared to the conventional schemes is greater in an environment that favorably satisfies the EH requirements, where the adaptive TPC strategy can operate more effectively.
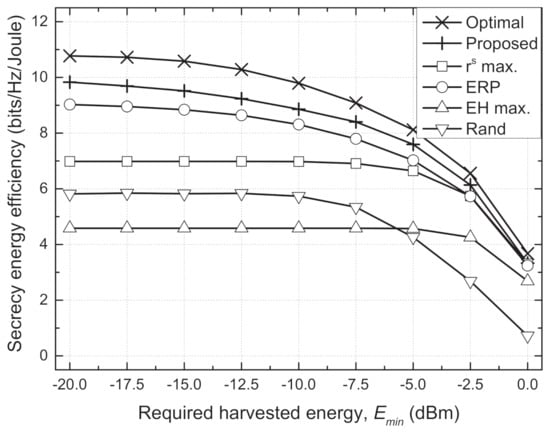
Figure 4.
Sum secrecy energy efficiency vs. required harvested energy () for different schemes.
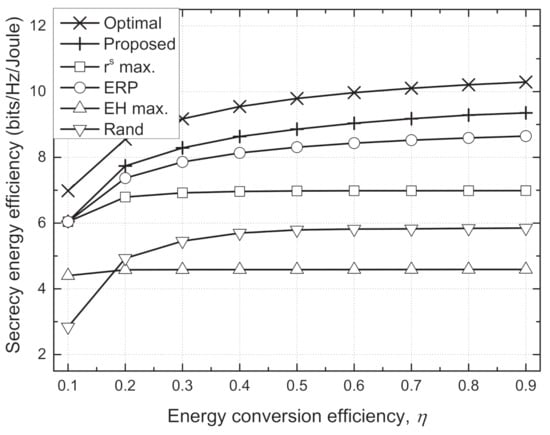
Figure 5.
Sum secrecy energy efficiency vs. energy conversion efficiency () for different schemes.
Figure 6 depicts the cumulative distribution function (CDF) versus sum SEE. It is observed that the CDF of the proposed scheme is closest to that of the optimal scheme, thus confirming the effectiveness of the proposed TPC strategy. Given that high values of SEE are more distributed in the CDFs of the optimal and proposed schemes, rather than those of the conventional schemes, we note that the effective TPC is important for improving the SEE.
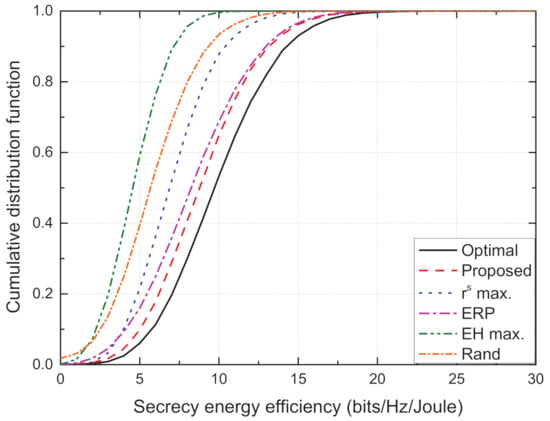
Figure 6.
Cumulative distribution function vs. sum secrecy energy efficiency for different schemes.
Figure 7 depicts the average SEE for each node set () and the computation time against number of node sets (N). It should be noted that the computation time of the EH max. and random schemes are omitted in subfigure (b) because they do not perform any computations to determine the transmit powers. As N increases, the Txs experience severe interference with each other. As a result, the improvement in the secrecy rate is insignificant compared to the transmit power used, which in turn deteriorates the average SEE with increasing N. However, the proposed scheme achieves a higher SEE than the conventional schemes by coping with the interference and reduces the computation time significantly compared with the optimal and max. schemes. Although the ERP scheme can achieve the lowest computation time for a large number of N because the optimal transmit power can be found by one-dimensional search even as N increases, the proposed scheme achieves higher sum SEE than the ERP scheme, which verifies the effectiveness of the proposed distributed method in term of energy efficiency and secure communication.
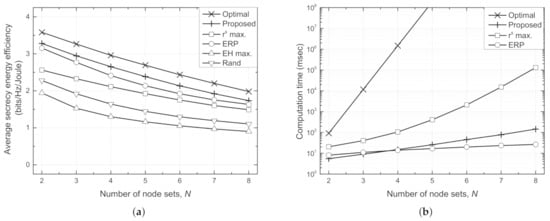
Figure 7.
Performance comparison against number of node sets (N) for different schemes. (a) Average secrecy energy efficiency per each node set vs. N. (b) Computation time vs. N.
Thus, the simulation results show that the proposed scheme has a slight difference in performance from the optimal scheme of about 10% because of its distributed nature; however, it is confirmed that the proposed scheme improves the sum SEE using the effective TPC strategy compared with the conventional schemes while significantly reducing computation time.
5. Conclusions
This study involves investigation of a distributed TPC algorithm for energy-efficient WPSCs, in which the transmit powers of the Txs are optimized to maximize their own SEEs while guaranteeing the minimum EH requirements for the corresponding EH nodes. Specifically, we analytically derived the closed-form equation for the transmit power, and proposed an iterative algorithm using a dual method, that can be operated in a distributed manner without sharing information with the other node sets. The simulation results confirm that the proposed scheme can achieve a higher sum SEE than existing schemes by adjusting the transmit power with respect to secrecy rate and energy efficiency; moreover, the computation time is significantly reduced compared with the optimal scheme. It is expected that our solution will be used to solve the complex TPC problems of WPSCs in a simple distributed manner. Interesting topics for future work include a deep learning-based distributed TPC algorithm for improving the performance of WPSCs.
Funding
This work was supported by the National Research Foundation of Korea (NRF) grant funded by the Korea government (MSIT) (No. 2021R1A2C4002024).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Frustaci, M.; Pace, P.; Aloi, G.; Fortino, G. Evaluating critical security issues of the IoT world: Present and future challenges. IEEE Internet Things J. 2018, 5, 2483–2495. [Google Scholar] [CrossRef]
- Gui, G.; Liu, M.; Tang, F.; Kato, N.; Adachi, F. 6G: Opening new horizons for integration of comfort, security and intelligence. IEEE Wirel. Commun. 2020, 27, 126–132. [Google Scholar] [CrossRef]
- Li, S.; Kim, J.G.; Han, D.H.; Lee, K.S. A survey of energy-efficient communication protocols with QoS guarantees in wireless multimedia sensor networks. Sensors 2019, 19, 199. [Google Scholar] [CrossRef] [Green Version]
- Hoang, T.D.; Le, L.B.; Le-Ngoc, T. Energy-efficient resource allocation for D2D communications in cellular networks. IEEE Trans. Veh. Technol. 2016, 65, 6972–6986. [Google Scholar] [CrossRef]
- Shi, J.; Yu, W.; Ni, Q.; Liang, W.; Li, Z.; Xiao, P. Energy efficient resource allocation in hybrid non-orthogonal multiple access systems. IEEE Trans. Commun. 2019, 67, 3496–3511. [Google Scholar] [CrossRef] [Green Version]
- He, S.; Huang, Y.; Wang, J.; Yang, L.; Hong, W. Joint antenna selection and energy-efficient beamforming design. IEEE Signal Process. Lett. 2016, 23, 1165–1169. [Google Scholar] [CrossRef]
- Lee, K. Distributed joint optimization of beamforming and power allocation for maximizing the energy efficiency of cognitive heterogeneous networks. Sensors 2021, 21, 3186. [Google Scholar] [CrossRef] [PubMed]
- Raghunathan, V.; Chou, P.H. Design and power management of energy harvesting embedded systems. In Proceedings of the 2006 International Symposium on Low Power Electronics and Design (ISLPED), Tegernsee, Germany, 4–6 October 2006; pp. 369–374. [Google Scholar]
- Lu, C.; Raghunathan, V.; Roy, K. Efficient design of micro-scale energy harvesting systems. IEEE J. Emerg. Sel. Top. Circuits Syst. 2011, 1, 254–266. [Google Scholar] [CrossRef]
- Prauzek, M.; Konecny, J.; Borova, M.; Janosova, K.; Hlavica, J.; Musilek, P. Energy harvesting sources, storage devices and system topologies for environmental wireless sensor networks: A review. Sensors 2018, 18, 2446. [Google Scholar] [CrossRef] [Green Version]
- Pinuela, M.; Mitcheson, P.; Lucyszyn, S. Ambient RF energy harvesting in urban and semi-urban environments. IEEE Trans. Microw. Theory Techn. 2013, 61, 2715–2726. [Google Scholar] [CrossRef]
- Lu, X.; Wang, P.; Niyato, D.; Kim, D.I.; Han, Z. Wireless networks with RF energy harvesting: A contemporary survey. IEEE Commun. Surv. Tut. 2015, 17, 757–789. [Google Scholar] [CrossRef] [Green Version]
- Lee, K.; Hong, J. Energy-efficient resource allocation for simultaneous information and energy transfer with imperfect channel estimation. IEEE Trans. Veh. Technol. 2016, 65, 2775–2780. [Google Scholar] [CrossRef]
- Chung, B.C.; Lee, K.; Cho, D. Proportional fair energy-efficient resource allocation in energy-harvesting-based wireless networks. IEEE Syst. J. 2018, 12, 2106–2116. [Google Scholar] [CrossRef]
- Lee, K.; Yoon, C.; Jo, O.; Lee, W. Joint optimization of spectrum sensing and transmit power in energy harvesting-based cognitive radio networks. IEEE Access 2018, 6, 30653–30662. [Google Scholar] [CrossRef]
- Shahini, A.; Kiani, A.; Ansari, N. Energy efficient resource allocation in EH-enabled CR networks for IoT. IEEE Internet Things J. 2019, 6, 3186–3193. [Google Scholar] [CrossRef] [Green Version]
- Noor-A-Rahim, M.; Khyam, M.O.; Guan, Y.L. Energy harvesting two-way relaying with antenna selection scheme. IET Commun. 2019, 13, 198–204. [Google Scholar] [CrossRef]
- Chu, S. Secrecy analysis of modify-and-forward relaying with relay selection. IEEE Trans. Veh. Technol. 2019, 68, 1796–1809. [Google Scholar] [CrossRef]
- Atapattu, S.; Ross, N.; Jing, Y.; He, Y.; Evans, J.S. Physical-layer security in full-duplex multi-hop multi-user wireless network with relay selection. IEEE Trans. Wirel. Commun. 2019, 18, 1216–1232. [Google Scholar] [CrossRef]
- Park, K.; Wang, T.; Alouini, M. On the jamming power allocation for secure amplify-and-forward relaying via cooperative jamming. IEEE J. Sel. Areas Commun. 2013, 31, 1741–1750. [Google Scholar] [CrossRef]
- Kalamkar, S.S.; Banerjee, A. Secure communication via a wireless energy harvesting untrusted relay. IEEE Trans. Veh. Technol. 2017, 66, 2199–2213. [Google Scholar] [CrossRef] [Green Version]
- Lee, K.; Bang, J.; Choi, H. Secrecy outage minimization for wireless-powered relay networks with destination-assisted cooperative jamming. IEEE Internet Things J. 2021, 8, 1467–1476. [Google Scholar] [CrossRef]
- Xu, D.; Zhu, H. Secure transmission for SWIPT IoT systems with full-duplex IoT devices. IEEE Internet Things J. 2019, 6, 10915–10933. [Google Scholar] [CrossRef]
- Liu, W.; Zhou, X.; Durrani, S.; Popovski, P. Secure communication with a wireless-powered friendly jammer. IEEE Trans. Wirel. Commun. 2016, 15, 401–415. [Google Scholar] [CrossRef] [Green Version]
- Ouyang, J.; Lin, M.; Zou, Y.; Zhu, W.; Massicotte, D. Secrecy energy efficiency maximization in cognitive radio networks. IEEE Access 2017, 5, 2641–2650. [Google Scholar] [CrossRef]
- Wang, G.; Meng, C.; Heng, W.; Chen, X. Secrecy energy efficiency optimization in AN-aided distributed antenna systems with energy harvesting. IEEE Access 2018, 6, 32830–32838. [Google Scholar] [CrossRef]
- Jiang, Y.; Zou, Y.; Ouyang, J.; Zhu, J. Secrecy energy efficiency optimization for artificial noise aided physical-layer security in OFDM-based cognitive radio networks. IEEE Trans. Veh. Technol. 2018, 67, 11858–11872. [Google Scholar] [CrossRef] [Green Version]
- Jiang, Y.; Zou, Y.; Ouyang, J.; Zhu, J. Beamforming aided secrecy energy efficiency maximization in heterogeneous cellular networks. IEEE Trans. Veh. Technol. 2021, 70, 2576–2589. [Google Scholar] [CrossRef]
- Zappone, A.; Lin, P.; Jorswieck, E.A. Secrecy energy efficiency for MIMO single- and multi-cell downlink transmission with confidential messages. IEEE Trans. Inf. Forensics Secur. 2019, 14, 2059–2073. [Google Scholar] [CrossRef]
- Lu, Y.; Xiong, K.; Fan, P.; Ding, Z.; Zhong, Z.; Letaief, K.B. Secrecy energy efficiency in multi-antenna SWIPT networks with dual-layer PS receivers. IEEE Trans. Wirel. Commun. 2020, 19, 4290–4306. [Google Scholar] [CrossRef]
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Yu, W.; Lui, R. Dual methods for nonconvex spectrum optimization of multicarrier systems. IEEE Trans. Commun. 2006, 54, 1310–1321. [Google Scholar] [CrossRef] [Green Version]
- Dinkelbach, W. On nonlinear fractional programming. Manag. Sci. 1967, 13, 492–498. [Google Scholar] [CrossRef]
- Fliege, J.; Vaz, A.I.F.; Vicente, L.N. Complexity of gradient descent for multiobjective optimization. Optim. Methods Softw. 2018, 34, 949–959. [Google Scholar] [CrossRef] [Green Version]
- Venturino, L.; Prasad, N.; Wang, X. Coordinated scheduling and power allocation in downlink multicell OFDMA networks. IEEE Trans. Veh. Technol. 2009, 58, 2835–2848. [Google Scholar] [CrossRef]
- Stoopman, M.; Keyrouz, S.; Visser, H.J.; Philips, K.; Serdijn, W.A. Co-design of a CMOS rectifier and small loop antenna for highly sensitive RF energy harvesters. IEEE J. Solid-State Circuits 2014, 49, 622–634. [Google Scholar] [CrossRef]
- Lee, W.; Ban, T.; Jung, B.C. Distributed transmit power optimization for device-to-device communications underlying cellular networks. IEEE Access 2019, 7, 87617–87633. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).







