BRISK: Dynamic Encryption Based Cipher for Long Term Security
Abstract
1. Introduction
2. Background
2.1. RFID
- Passive Tags: Passive tags absorb the power from radio waves, and they do not have any battery. The absorbed power by tag is used to power the internal circuit and make communication through the antenna.
- Active Tags: In general, active tags are more expensive due to additional expenses on manufactures. Active tags contain the power source onboard. This power source could be a battery that provides power to the antenna and the internal circuit.
- Semi-Active Tags: Semi-active tags contain a battery to give power to the internal circuit, but this power is not used for communication through the antenna. Such tags retain the advantage of both active and passive tags and remove several disadvantages from both. The power can be saved for a long time.
- Healthcare: RFID has several applications in healthcare such as patient tracking, patient monitoring, patient drug compliance, patient monitoring, etc.
- Contact-less Payments: Many companies such as MasterCard, VISA, American Express etc., use RFID technology for contactless payments.
- Passport: Several countries like the United States, Japan, and Norway incorporate RFID tags in passports that store traveller history, photographs and other important information.
- Toll Road Payments: Several highway toll booths use RFID technology where vehicles do not stop on the toll booth but directly passes through an E-Z pass lane, and the toll is automatically deducted.
- Product Tracking: RFID tags are mostly used in tracking the inventory throughout the supply chain. These RFID tags are used as a cost-effective way to track products and used as a substitute for the barcode.
2.2. Cryptology
2.3. Strategy to Design Lightweight Ciphers
- Design new ciphers with a goal of low costs for hardware implementation.
- Slightly modify standard algorithms and make it suitable lightweight applications.
- Optimise the implementation cost of standard and trusted algorithms.
- Area: This requirement is generally measured in m. To analyse the area requirements of a cipher, it is easy to state the area as gate equivalents (GE). A two-input NAND gate requires the area of one GE, and therefore GE area can be derived by dividing the area in m by area of the two-input NAND gate. Some RFID devices like contactless smart cards or RFID tags require low power consumption and small area, but other factors like throughput are not very important.
- Cycle: It represents the number of clock cycles to compute or read the results. A parallel block cipher implementation performs any number of encryption/decryption round operation within one clock cycle. On the other hand, in round-wise implementation, one round function is performed in one cycle.
- Time: Time required for a certain operation can be calculated by taking the ratio of cycles and operating frequency and mathematically can be expressed as . Time can be expressed in milliseconds [ms].
- Power Power consumption is measured in microwatts [W] and estimated on gate level. The following equation represents the power consumption of P in CMOS devices.In the above equation, is the supply voltage, C is circuit capacitance, is short circuit charge, N is switching activity, is leakage current, and f is operating frequency.
- Throughput: Throughput is the rate at which output can be produced with respect to time. Throughput is measured in bits per second [] and can be calculated when output bits are divided by time. Some RFID reader devices require high throughput because at the same time they read out many devices, while power consumption and the area are not that important for them.
- Efficiency: The efficiency is the ratio of throughput and area, and mathematically can be expressed as . This can also be expressed as gate equivalents per bits per second [].
2.4. Lightweight Ciphers
2.5. Contribution
- BRISK is a symmetric block cipher. This implies that the same key is used for encryption as well as decryption.
- BRISK supports two versions of the cipher, and both version use two different types of S-Boxes.
- BRISK is suitable for hardware as well as software. The cipher is word-oriented, which means at a time operations are performed on words of data.
- BRISK follows dynamism in encryption and decryption. For each session of data encryption, it uses either S-Box or S-Box as a non-linear component. The number of rounds also varies in each session, and therefore it provides better security against the attacker.
- BRISK has a key length of 80-bits that can be divided into 5 subkeys used for the first 5 rounds, and after that, it generates other round keys from the main key.
- BRISK has a very simple design and is very easy to implement. The simple structure also allows easy cryptanalysis of the cipher. It has a low memory requirement, and therefore can be easily implemented on resource-constrained devices with small memory.
3. Specifications of BRISK
3.1. Round Function
- bitwise XOR, ⊕;
- Substitution-Box S;
- Permutation-Box P.
3.2. Key Schedule
3.3. Key Exchange Protocol
4. Analysis of the Proposed BRISK Cipher
- To achieve the goal of confusion, BRISK uses non-linear components: S-Box and S-Box.
- The blocks in the cipher are divided into two half words, and both words interchange their sides after each round. Applying this process for several rounds and using permutation boxes P-Box and P-Box provides the property of diffusion.
- Key length plays an important role in the security of any cipher, and therefore, the cipher uses the key size of 80-bit, which is enough to produce tight security.
Security Evaluation of Cipher
5. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
| I/O | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | A | B | C | D | E | F |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0 | 8 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 1 | 0 | −2 | 2 | 0 | −2 | 0 | 0 | 2 | −2 | 0 | 0 | 2 | −4 | 2 | −2 | −4 |
| 2 | 0 | 0 | 4 | 0 | 0 | −4 | 0 | 0 | 2 | −2 | 2 | 2 | 2 | 2 | −2 | 2 |
| 3 | 0 | 2 | −2 | −4 | −2 | 0 | 0 | −2 | 0 | 2 | 2 | 0 | −2 | 0 | −4 | 2 |
| 4 | 0 | 0 | −2 | 2 | −2 | −2 | 0 | 4 | −2 | −2 | 0 | −4 | 0 | 0 | −2 | 2 |
| 5 | 0 | 2 | 0 | −2 | 4 | 2 | 0 | 2 | 0 | −2 | 4 | −2 | 0 | 2 | 0 | -2 |
| 6 | 0 | 0 | −2 | −2 | −2 | 2 | −4 | 0 | 0 | −4 | −2 | 2 | 2 | 2 | 0 | 0 |
| 7 | 0 | −2 | 0 | −2 | −4 | 2 | 4 | 2 | 2 | 0 | 2 | 0 | 2 | 0 | 2 | 0 |
| 8 | 0 | 0 | 2 | −2 | 0 | 0 | −2 | 2 | −2 | 2 | 0 | 0 | −2 | 2 | 4 | 4 |
| 9 | 0 | −6 | 0 | −2 | 2 | 0 | −2 | 0 | 0 | 2 | 0 | −2 | 2 | 0 | −2 | 0 |
| A | 0 | 0 | 2 | 2 | 0 | 4 | 2 | −2 | 0 | 0 | −2 | −2 | 0 | 4 | −2 | 2 |
| B | 0 | −2 | 0 | −2 | 2 | 0 | 2 | 0 | 2 | −4 | −2 | 0 | −4 | −2 | 0 | 2 |
| C | 0 | 0 | 0 | 0 | −2 | −2 | −2 | −2 | 4 | 0 | 0 | −4 | −2 | 2 | 2 | −2 |
| D | 0 | −2 | −2 | 4 | 0 | 2 | −2 | 0 | 2 | 0 | 4 | 2 | −2 | 0 | 0 | 2 |
| E | 0 | 0 | 4 | 0 | −2 | 2 | −2 | −2 | −2 | −2 | 2 | −2 | 0 | −4 | 0 | 0 |
| F | 0 | 2 | 2 | 0 | 0 | 2 | −2 | 4 | 4 | 2 | −2 | 0 | 0 | −2 | −2 | 0 |
| I/O | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | A | B | C | D | E | F |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0 | 8 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 1 | 0 | 0 | 2 | 2 | −2 | 2 | −4 | 0 | −4 | 0 | 2 | −2 | −2 | −2 | 0 | 0 |
| 2 | 0 | −2 | 0 | 2 | 0 | 2 | 0 | −2 | 4 | −2 | 4 | 2 | 0 | −2 | 0 | 2 |
| 3 | 0 | 2 | −2 | −4 | −2 | 0 | 0 | −2 | 0 | 2 | 2 | 0 | −2 | 0 | −4 | 2 |
| 4 | 0 | −2 | −2 | 0 | 2 | 0 | 0 | 2 | 0 | −2 | −2 | 0 | −6 | 0 | 0 | 2 |
| 5 | 0 | 2 | 0 | −2 | 4 | 2 | 0 | 2 | 0 | −2 | 4 | −2 | 0 | 2 | 0 | −2 |
| 6 | 0 | 0 | −2 | −2 | −2 | 2 | −4 | 0 | 0 | −4 | −2 | 2 | 2 | 2 | 0 | 0 |
| 7 | 0 | 0 | 4 | −4 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 4 | 4 |
| 8 | 0 | −2 | −2 | 0 | −4 | 2 | 2 | 4 | 0 | 2 | 2 | 0 | 0 | 2 | 2 | 0 |
| 9 | 0 | −6 | 0 | −2 | 2 | 0 | −2 | 0 | 0 | 2 | 0 | −2 | 2 | 0 | −2 | 0 |
| A | 0 | 0 | 2 | 2 | 0 | 4 | 2 | −2 | 0 | 0 | −2 | −2 | 0 | 4 | −2 | 2 |
| B | 0 | 0 | 0 | 0 | −2 | −2 | 2 | 2 | 0 | −4 | 0 | −4 | 2 | −2 | −2 | 2 |
| C | 0 | 0 | 0 | 0 | −2 | −2 | −2 | −2 | 4 | 0 | 0 | −4 | −2 | 2 | 2 | −2 |
| D | 0 | 0 | 2 | 2 | 0 | −4 | −2 | 2 | 0 | 0 | 2 | 2 | 0 | 4 | −2 | 2 |
| E | 0 | −2 | 4 | −2 | −2 | 0 | 2 | 0 | 0 | −2 | 0 | 2 | −2 | 0 | −2 | −4 |
| F | 0 | 2 | 2 | 0 | 0 | 2 | −2 | 4 | 4 | 2 | −2 | 0 | 0 | −2 | −2 | 0 |
| I/O | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | A | B | C | D | E | F |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0 | 16 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 1 | 0 | 0 | 0 | 0 | 0 | 4 | 0 | 4 | 0 | 4 | 0 | 0 | 0 | 4 | 0 | 0 |
| 2 | 0 | 0 | 0 | 4 | 2 | 0 | 2 | 0 | 0 | 0 | 4 | 0 | 2 | 0 | 2 | 0 |
| 3 | 0 | 2 | 0 | 4 | 0 | 0 | 4 | 2 | 0 | 0 | 0 | 2 | 0 | 2 | 0 | 0 |
| 4 | 0 | 0 | 2 | 0 | 0 | 0 | 2 | 0 | 0 | 0 | 2 | 0 | 6 | 2 | 0 | 2 |
| 5 | 0 | 2 | 0 | 0 | 0 | 4 | 0 | 2 | 2 | 0 | 2 | 2 | 0 | 0 | 0 | 2 |
| 6 | 0 | 2 | 2 | 0 | 0 | 0 | 4 | 0 | 2 | 2 | 0 | 0 | 2 | 0 | 2 | 0 |
| 7 | 0 | 2 | 0 | 0 | 2 | 0 | 0 | 0 | 0 | 2 | 0 | 4 | 2 | 0 | 0 | 4 |
| 8 | 0 | 2 | 0 | 2 | 0 | 0 | 0 | 0 | 2 | 2 | 2 | 2 | 0 | 2 | 0 | 2 |
| 9 | 0 | 0 | 2 | 0 | 4 | 0 | 2 | 0 | 2 | 0 | 0 | 0 | 0 | 2 | 2 | 2 |
| A | 0 | 0 | 2 | 2 | 0 | 4 | 0 | 0 | 0 | 2 | 0 | 2 | 0 | 2 | 2 | 0 |
| B | 0 | 0 | 0 | 0 | 2 | 0 | 0 | 2 | 4 | 0 | 2 | 2 | 2 | 0 | 2 | 0 |
| C | 0 | 2 | 0 | 2 | 2 | 4 | 0 | 2 | 0 | 0 | 0 | 0 | 2 | 2 | 0 | 0 |
| D | 0 | 2 | 4 | 0 | 2 | 0 | 0 | 0 | 2 | 2 | 2 | 0 | 0 | 0 | 2 | 0 |
| E | 0 | 2 | 2 | 2 | 0 | 0 | 0 | 2 | 0 | 2 | 0 | 0 | 0 | 0 | 2 | 4 |
| F | 0 | 0 | 2 | 0 | 2 | 0 | 2 | 2 | 2 | 0 | 2 | 2 | 0 | 0 | 2 | 0 |
| I/O | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | A | B | C | D | E | F |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0 | 16 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 1 | 0 | 2 | 2 | 2 | 0 | 2 | 0 | 0 | 0 | 2 | 0 | 0 | 0 | 2 | 2 | 2 |
| 2 | 0 | 2 | 4 | 2 | 0 | 0 | 0 | 0 | 2 | 0 | 2 | 0 | 0 | 0 | 4 | 0 |
| 3 | 0 | 2 | 0 | 4 | 0 | 0 | 2 | 0 | 0 | 0 | 0 | 2 | 2 | 4 | 0 | 0 |
| 4 | 0 | 0 | 2 | 0 | 2 | 0 | 2 | 2 | 2 | 0 | 2 | 2 | 0 | 0 | 2 | 0 |
| 5 | 0 | 0 | 0 | 0 | 0 | 6 | 0 | 2 | 2 | 0 | 2 | 4 | 0 | 0 | 0 | 0 |
| 6 | 0 | 2 | 0 | 0 | 2 | 0 | 4 | 0 | 4 | 2 | 0 | 0 | 2 | 0 | 0 | 0 |
| 7 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 2 | 4 | 2 | 4 | 0 | 2 | 0 | 2 |
| 8 | 0 | 4 | 0 | 2 | 2 | 0 | 0 | 0 | 0 | 0 | 0 | 2 | 2 | 0 | 0 | 4 |
| 9 | 0 | 0 | 4 | 0 | 2 | 0 | 2 | 0 | 0 | 0 | 0 | 0 | 0 | 2 | 4 | 2 |
| A | 0 | 2 | 2 | 2 | 0 | 2 | 0 | 0 | 0 | 2 | 0 | 0 | 0 | 2 | 2 | 2 |
| B | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 2 | 0 | 2 | 0 | 8 | 2 | 0 | 2 |
| C | 0 | 2 | 0 | 2 | 2 | 4 | 2 | 4 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| D | 0 | 0 | 0 | 2 | 4 | 0 | 2 | 0 | 0 | 2 | 4 | 0 | 2 | 0 | 0 | 0 |
| E | 0 | 0 | 0 | 0 | 0 | 2 | 0 | 6 | 0 | 4 | 0 | 0 | 0 | 2 | 0 | 2 |
| F | 0 | 0 | 2 | 0 | 2 | 0 | 2 | 2 | 2 | 0 | 2 | 2 | 0 | 0 | 2 | 0 |
| Round | Block1 | Block2 | Bias | Active S-Box |
|---|---|---|---|---|
| 1 | 0xa43b | 0x26c6 | 8 | 4 |
| 2 | 0x6313 | 0x0be7 | 6 | 3 |
| 3 | 0xf385 | 0xe200 | 3 | 2 |
| 4 | 0x0071 | 0x00c0 | 2 | 1 |
| 5 | 0x6000 | 0x0200 | 1 | 1 |
| 6 | 0x0001 | 0x0080 | 2 | 1 |
| 7 | 0x4000 | 0x0010 | 2 | 1 |
| 8 | 0x0800 | 0x4000 | 2 | 1 |
| 9 | 0x0020 | 0x0040 | 2 | 1 |
| 10 | 0x2000 | 0x0200 | 1 | 1 |
| 11 | 0x0001 | 0x0080 | 1 | 1 |
| Total Probability: | 31 | 17 |
| Round | Block1 | Block2 | Active S-Box | |
|---|---|---|---|---|
| 1 | 0x8000 | 0x0000 | 0 | 0 |
| 2 | 0x0000 | 0x8000 | 3 | 1 |
| 3 | 0x8000 | 0x1000 | 2 | 1 |
| 4 | 0x1000 | 0x9800 | 6 | 2 |
| 5 | 0x9800 | 0x1006 | 5 | 2 |
| 6 | 0x1006 | 0x0040 | 3 | 1 |
| 7 | 0x0040 | 0x5006 | 5 | 2 |
| 8 | 0x5006 | 0x9000 | 3 | 1 |
| 9 | 0x9000 | 0x5004 | 3.41 | 2 |
| Total Probability: | 30.41 | 12 |
| Round | Block1 | Block2 | Bias | Active S-Box |
|---|---|---|---|---|
| 1 | 0xc189 | 0xb110 | 5 | 3 |
| 2 | 0x8858 | 0x0918 | 5 | 3 |
| 3 | 0x8c04 | 0xe400 | 4 | 2 |
| 4 | 0x0072 | 0x000e | 1 | 1 |
| 5 | 0x0700 | 0x0020 | 2 | 1 |
| 6 | 0x1000 | 0x0040 | 2 | 1 |
| 7 | 0x2000 | 0x0010 | 2 | 1 |
| 8 | 0x0800 | 0x0010 | 2 | 1 |
| 9 | 0x0800 | 0x0050 | 2 | 1 |
| 10 | 0x2800 | 0x0050 | 2 | 1 |
| 11 | 0x2800 | 0x0240 | 2.41 | 2 |
| Total Probability: | 30.41 | 17 |
| Round | Block1 | Block2 | Active S-Box | |
|---|---|---|---|---|
| 1 | 0x0000 | 0x8000 | 2 | 1 |
| 2 | 0x0040 | 0x0001 | 3 | 1 |
| 3 | 0x0080 | 0x1040 | 6 | 2 |
| 4 | 0x2008 | 0x0020 | 2 | 1 |
| 5 | 0x1000 | 0x0008 | 2 | 1 |
| 6 | 0x0400 | 0x0000 | 0 | 0 |
| 7 | 0x0000 | 0x0400 | 3 | 1 |
| 8 | 0x0002 | 0x0008 | 3 | 1 |
| 9 | 0x0400 | 0x1000 | 3 | 1 |
| 10 | 0x0008 | 0x0001 | 3 | 1 |
| 11 | 0x0080 | 0x000a | 3 | 1 |
| Total Probability: | 30 | 11 |
References
- Aboushosha, B.; Ramadan, R.A.; Dwivedi, A.D.; El-Sayed, A.; Dessouky, M.M. SLIM: A Lightweight Block Cipher for Internet of Health Things. IEEE Access 2020, 8, 203747–203757. [Google Scholar] [CrossRef]
- Daemen, J.; Rijmen, V. The Design of Rijndael: AES—The Advanced Encryption Standard; Information Security and Cryptography; Springer: Berlin/Heidelberg, Germany, 2002. [Google Scholar] [CrossRef]
- Dwivedi, A.D.; Morawiecki, P.; Wójtowicz, S. Differential-linear and Impossible Differential Cryptanalysis of Round-reduced Scream. In Proceedings of the 14th International Joint Conference on e-Business and Telecommunications (ICETE 2017)—Volume 4: SECRYPT, Madrid, Spain, 24–26 July 2017; Samarati, P., Obaidat, M.S., Cabello, E., Eds.; SciTePress: Setubal, Portugal, 2017; pp. 501–506. [Google Scholar] [CrossRef]
- Dwivedi, A.D.; Dhar, S.; Srivastava, G.; Singh, R. Cryptanalysis of Round-Reduced Fantomas, Robin and iSCREAM. Cryptography 2019, 3, 4. [Google Scholar] [CrossRef]
- Knudsen, L.R. Dynamic Encryption. J. Cyber Secur. Mobil. 2014, 3, 357–370. [Google Scholar] [CrossRef][Green Version]
- Beaulieu, R.; Shors, D.; Smith, J.; Treatman-Clark, S.; Weeks, B.; Wingers, L. The SIMON and SPECK Families of Lightweight Block Ciphers. IACR Cryptol. EPrint Arch. 2013, 2013, 404. [Google Scholar]
- Yang, G.; Zhu, B.; Suder, V.; Aagaard, M.D.; Gong, G. The Simeck Family of Lightweight Block Ciphers. In Cryptographic Hardware and Embedded Systems—CHES 2015–2017th International Workshop, Saint-Malo, France, 13–16 September 2015; Güneysu, T., Handschuh, H., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; Lecture Notes in Computer Science; Volume 9293, pp. 307–329. [Google Scholar] [CrossRef]
- Hong, D.; Lee, J.; Kim, D.; Kwon, D.; Ryu, K.H.; Lee, D. LEA: A 128-Bit Block Cipher for Fast Encryption on Common Processors. In Information Security Applications—14th International Workshop, WISA 2013, Jeju Island, Korea, 19–21 August 2013; Kim, Y., Lee, H., Perrig, A., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2013; Volume 8267, pp. 3–27. [Google Scholar] [CrossRef]
- Knudsen, L.R.; Leander, G. PRESENT—Block Cipher. In Encyclopedia of Cryptography and Security, 2nd ed.; van Tilborg, H.C.A., Jajodia, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 953–955. [Google Scholar] [CrossRef]
- Wheeler, D.J.; Needham, R.M. TEA, a Tiny Encryption Algorithm. In Fast Software Encryption: Second International Workshop, Leuven, Belgium, 14–16 December 1994; Preneel, B., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1994; Volume 1008, pp. 363–366. [Google Scholar] [CrossRef]
- Cannière, C.D.; Dunkelman, O.; Knezevic, M. KATAN and KTANTAN–A Family of Small and Efficient Hardware-Oriented Block Ciphers. In Cryptographic Hardware and Embedded Systems—CHES 2009, 11th International Workshop, Lausanne, Switzerland, 6–9 September 2009; Clavier, C., Gaj, K., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5747, pp. 272–288. [Google Scholar] [CrossRef]
- Data Encryption Standard. In FIPS PUB 46, Federal Information Processing Standards Publication; NIST Computer Security Resource Center: Gaithersburg, MD, USA, 1977.
- IBM. Triple DES. 1995. Available online: https://en.wikipedia.org/wiki/Triple_DES (accessed on 30 August 2020).
- Knudsen, L.R.; Rijmen, V.; Rivest, R.L.; Robshaw, M.J.B. On the Design and Security of RC2. In Fast Software Encryption, 5th International Workshop, FSE ’98, Paris, France, 23–25 March 1998; Vaudenay, S., Ed.; Springer: Berlin/Heidelberg, Germany, 1998; Lecture Notes in Computer Science; Volume 1372, pp. 206–221. [Google Scholar] [CrossRef]
- Rivest, R.L. The RC5 Encryption Algorithm. In Fast Software Encryption: Second International Workshop, Leuven, Belgium, 14–16 December 1994; Preneel, B., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1994; Volume 1008, pp. 86–96. [Google Scholar] [CrossRef]
- Rivest, R.L.; Robshaw, M.; Sidney, R.; Yin, Y. The RC6 Block Cipher. 1998. Available online: http://people.csail.mit.edu/rivest/pubs/RRSY98.pdf (accessed on 30 August 2020).
- Bogdanov, A.; Knudsen, L.R.; Leander, G.; Paar, C.; Poschmann, A.; Robshaw, M.J.B.; Seurin, Y.; Vikkelsoe, C. PRESENT: An Ultra-Lightweight Block Cipher. In Cryptographic Hardware and Embedded Systems—CHES 2007, 9th International Workshop, Vienna, Austria, 10–13 September 2007; Paillier, P., Verbauwhede, I., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2007; Volume 4727, pp. 450–466. [Google Scholar] [CrossRef]
- Needham, R.M.; Wheeler, D.J. Tea Extensions. 1997. Available online: http://www.cix.co.uk/~klockstone/xtea.pdf (accessed on 30 August 2020).
- Lim, C.H.; Korkishko, T. mCrypton—A Lightweight Block Cipher for Security of Low-Cost RFID Tags and Sensors. In Information Security Applications, 6th International Workshop, WISA 2005, Jeju Island, Korea, 22–24 August 2005, Revised Selected Papers; Song, J., Kwon, T., Yung, M., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3786, pp. 243–258. [Google Scholar] [CrossRef]
- Schneier, B.; Kelsey, J.; Whiting, D.; Wagner, D.; Hall, C.; Ferguson, N. Twofish: A 128-Bit Block Cipher. In Proceedings of the First Advanced Encryption Standard (AES) Conference, Ventura, CA, USA, 20–22 August 1998. [Google Scholar]
- Lai, X.; Massey, J.L. A Proposal for a New Block Encryption Standard. In Advances in Cryptology—EUROCRYPT ’90, Workshop on the Theory and Application of of Cryptographic Techniques, Aarhus, Denmark, 21–24 May 1990; Damgård, I., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1990; Volume 473, pp. 389–404. [Google Scholar] [CrossRef]
- GOST. 1994. Available online: https://web.archive.org/web/20150924113434/http://tc26.ru/standard/gost/GOST_R_3412-2015.pdf (accessed on 30 August 2020).
- Knudsen, L.R.; Leander, G.; Poschmann, A.; Robshaw, M.J.B. PRINTcipher: A Block Cipher for IC-Printing. In Cryptographic Hardware and Embedded Systems, CHES 2010, 12th International Workshop, Santa Barbara, CA, USA, 17–20 August 2010; Mangard, S., Standaert, F., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2010; Volume 6225, pp. 16–32. [Google Scholar] [CrossRef]
- Cannière, C.D. Blowfish. In Encyclopedia of Cryptography and Security; van Tilborg, H.C.A., Ed.; Springer: Berlin/Heidelberg, Germany, 2005. [Google Scholar] [CrossRef]
- Kolay, S.; Mukhopadhyay, D. Khudra: A New Lightweight Block Cipher for FPGAs. In Security, Privacy, and Applied Cryptography Engineering—4th International Conference, SPACE 2014, Pune, India, 18–22 October 2014; Chakraborty, R.S., Matyas, V., Schaumont, P., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8804, pp. 126–145. [Google Scholar] [CrossRef]
- Skipjack. 1998. Available online: https://web.archive.org/web/20010603000755/http://csrc.nist.gov/encryption/skipjack/skipjack.pdf (accessed on 30 August 2020).
- Matsui, M. New Block Encryption Algorithm MISTY. In Fast Software Encryption, 4th International Workshop, FSE ’97, Haifa, Israel, 20–22 January 1997; Biham, E., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1997; Volume 1267, pp. 54–68. [Google Scholar] [CrossRef]
- Borghoff, J.; Canteaut, A.; Güneysu, T.; Kavun, E.B.; Knezevic, M.; Knudsen, L.R.; Leander, G.; Nikov, V.; Paar, C.; Rechberger, C.; et al. PRINCE—A Low-Latency Block Cipher for Pervasive Computing Applications—Extended Abstract. In Advances in Cryptology—ASIACRYPT 2012—18th International Conference on the Theory and Application of Cryptology and Information Security, Beijing, China, 2–6 December 2012; Wang, X., Sako, K., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7658, pp. 208–225. [Google Scholar] [CrossRef]
- Standaert, F.; Piret, G.; Gershenfeld, N.; Quisquater, J. SEA: A Scalable Encryption Algorithm for Small Embedded Applications. In Smart Card Research and Advanced Applications, 7th IFIP WG 8.8/11.2 International Conference, CARDIS 2006, Tarragona, Spain, 19–21 April 2006; Domingo-Ferrer, J., Posegga, J., Schreckling, D., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2006; Volume 3928, pp. 222–236. [Google Scholar] [CrossRef]
- Akishita, T.; Hiwatari, H. Very Compact Hardware Implementations of the Blockcipher CLEFIA. In Selected Areas in Cryptography—18th International Workshop, SAC 2011, Toronto, ON, Canada, 11–12 August 2011, Revised Selected Papers; Miri, A., Vaudenay, S., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2011; Volume 7118, pp. 278–292. [Google Scholar] [CrossRef]
- Guo, J.; Peyrin, T.; Poschmann, A.; Robshaw, M.J.B. The LED Block Cipher. In Cryptographic Hardware and Embedded Systems—CHES 2011–2013th International Workshop, Nara, Japan, 28 September–1 October 2011; Preneel, B., Takagi, T., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2011; Volume 6917, pp. 326–341. [Google Scholar] [CrossRef]
- Gong, Z.; Nikova, S.; Law, Y.W. KLEIN: A New Family of Lightweight Block Ciphers. In RFID. Security and Privacy—7th International Workshop, RFIDSec 2011, Amherst, USA, 26–28 June 2011; Juels, A., Paar, C., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2011; Volume 7055, pp. 1–18. [Google Scholar] [CrossRef]
- Plos, T.; Dobraunig, C.; Hofinger, M.; Oprisnik, A.; Wiesmeier, C.; Wiesmeier, J. Compact Hardware Implementations of the Block Ciphers mCrypton, NOEKEON, and SEA. In Progress in Cryptology—INDOCRYPT 2012, 13th International Conference on Cryptology in India, Kolkata, India, 9–12 December 2012; Galbraith, S.D., Nandi, M., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7668, pp. 358–377. [Google Scholar] [CrossRef]
- Borghoff, J.; Canteaut, A.; Güneysu, T.; Kavun, E.B.; Knezevic, M.; Knudsen, L.R.; Leander, G.; Nikov, V.; Paar, C.; Rechberger, C.; et al. PRINCE—A Low-latency Block Cipher for Pervasive Computing Applications (Full version). IACR Cryptol. EPrint Arch. 2012, 2012, 529. [Google Scholar]
- Hämäläinen, P.; Alho, T.; Hännikäinen, M.; Hämäläinen, T.D. Design and Implementation of Low-Area and Low-Power AES Encryption Hardware Core. In Proceedings of the Ninth Euromicro Conference on Digital System Design: Architectures, Methods and Tools (DSD 2006), Dubrovnik, Croatia, 30 August–1 September 2006; IEEE Computer Society: Washington, DC, USA, 2006; pp. 577–583. [Google Scholar] [CrossRef]
- Zhang, W.; Bao, Z.; Lin, D.; Rijmen, V.; Yang, B.; Verbauwhede, I. RECTANGLE: A Bit-slice Ultra-Lightweight Block Cipher Suitable for Multiple Platforms. IACR Cryptol. EPrint Arch. 2014, 2014, 84. [Google Scholar] [CrossRef]
- Shibutani, K.; Isobe, T.; Hiwatari, H.; Mitsuda, A.; Akishita, T.; Shirai, T. Piccolo: An Ultra-Lightweight Blockcipher. In Cryptographic Hardware and Embedded Systems—CHES 2011–2013th International Workshop, Nara, Japan, 28 September–1 October 2011; Preneel, B., Takagi, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; Lecture Notes in Computer Science; Volume 6917, pp. 342–357. [Google Scholar] [CrossRef]
- Beaulieu, R.; Shors, D.; Smith, J.; Treatman-Clark, S.; Weeks, B.; Wingers, L. The SIMON and SPECK Lightweight Block Ciphers. DAC; ACM: New York, NY, USA, 2015; pp. 175:1–175:6. [Google Scholar]
- Biham, E.; Shamir, A. Differential Cryptanalysis of DES-like Cryptosystems. J. Cryptol. 1991, 4, 3–72. [Google Scholar] [CrossRef]
- Biham, E.; Shamir, A. Differential Cryptanalysis of the Full 16-Round DES. In Advances in Cryptology—CRYPTO ’92, 12th Annual International Cryptology Conference, Santa Barbara, California, USA, 16–20 August 1992; Brickell, E.F., Ed.; Springer: Berlin/Heidelberg, Germany, 1992; Lecture Notes in Computer Science; Volume 740, pp. 487–496. [Google Scholar] [CrossRef]
- Dwivedi, A.D.; Srivastava, G. Differential Cryptanalysis of Round-Reduced LEA. IEEE Access 2018, 6, 79105–79113. [Google Scholar] [CrossRef]
- Dwivedi, A.D. Security Analysis of Lightweight IoT Cipher: Chaskey. Cryptography 2020, 4, 22. [Google Scholar] [CrossRef]
- Matsui, M. Linear Cryptanalysis Method for DES Cipher. In Proceedings of the Workshop on the Theory and Application of of Cryptographic Techniques, Lofthus, Norway, 23–27 May 1993; pp. 386–397. [Google Scholar] [CrossRef]
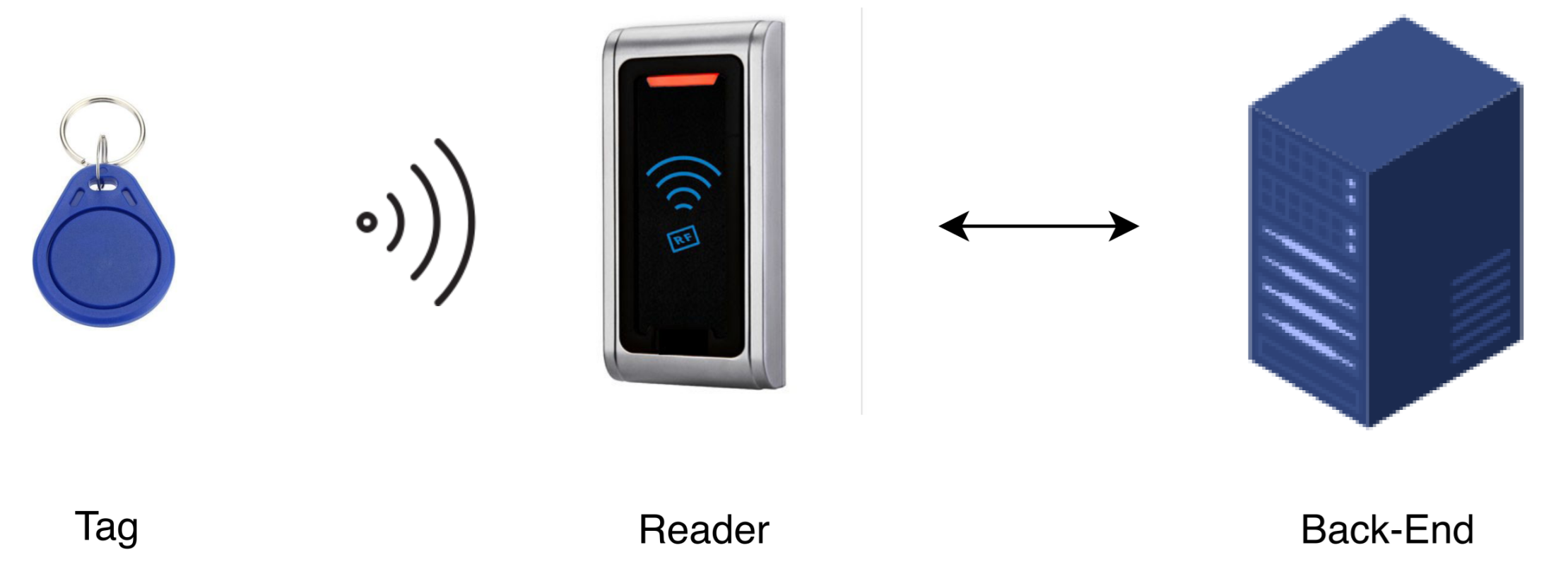
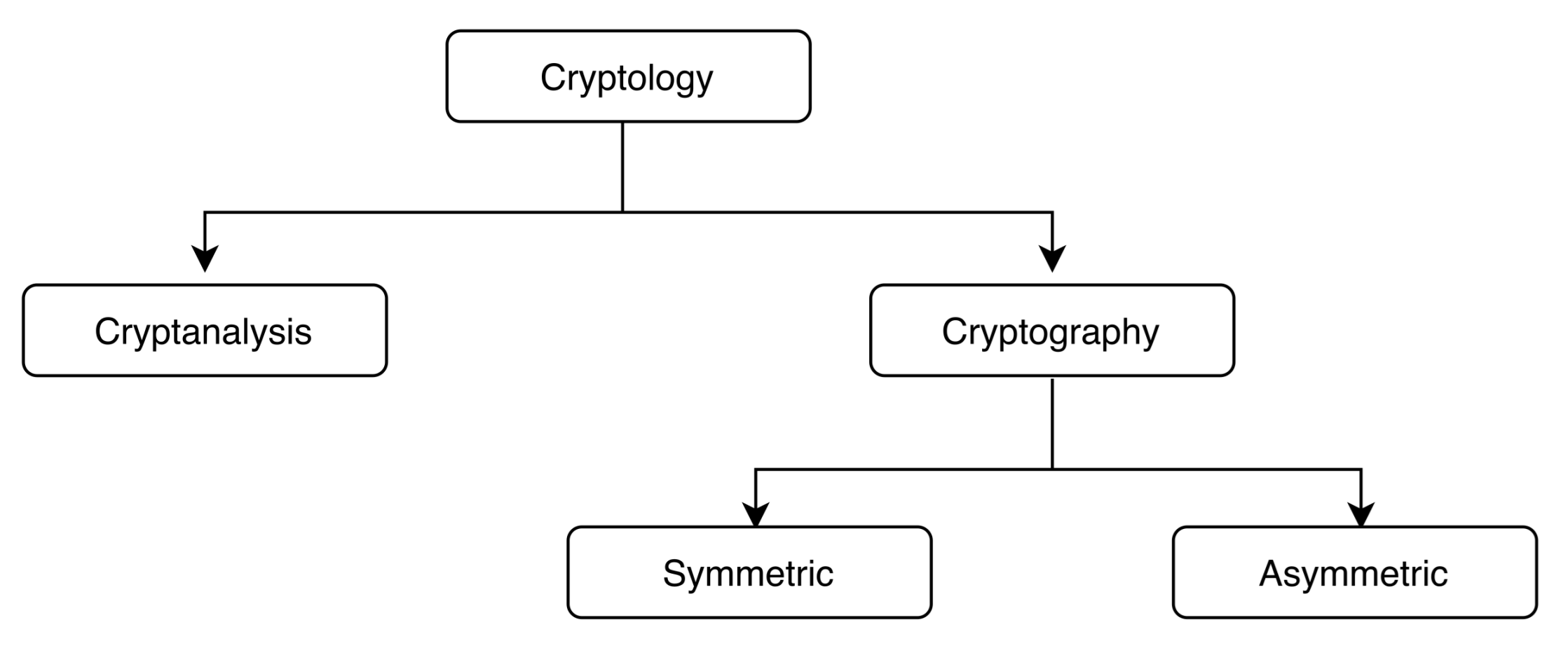
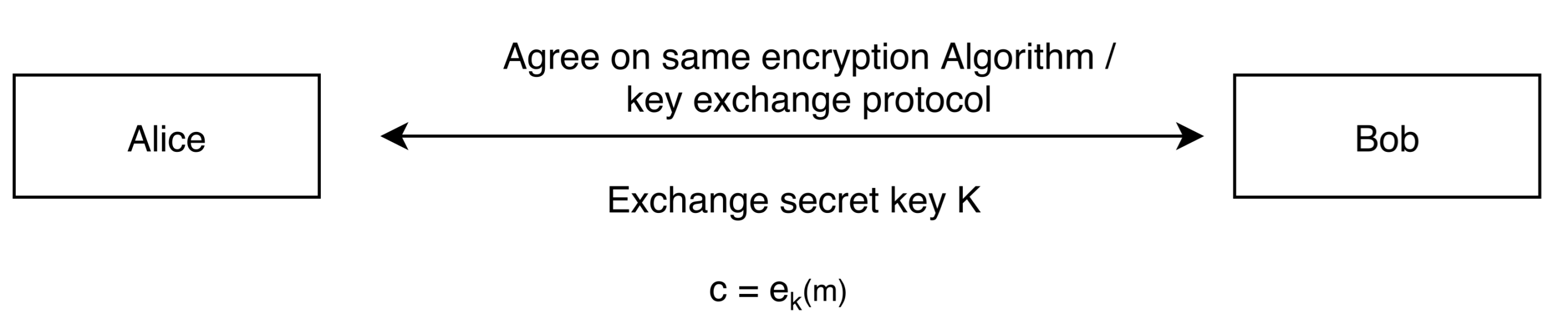





| Specifications | Active Tag | Passive Tags |
|---|---|---|
| Price | 2–5 Euro | 0.1 Euro |
| Storage | 32–70 KB | 32-1K bits |
| Reading Distance | up to 10 cm | up to 3 cm |
| Security Capabilities | RSA, SHA, 3DES | 250-4K gates |
| Standard Cell | GE | Area (m) | Process |
|---|---|---|---|
| XOR | 2.67 | 25.805 | 0.18 m |
| OR | 1.33 | 12.902 | 0.18 m |
| NOR | 1.00 | 9.677 | 0.18 m |
| AND | 1.33 | 12.902 | 0.18 m |
| NAND | 1.00 | 9.677 | 0.18 m |
| NOT | 0.67 | 6.451 | 0.18 m |
| Algorithm | Structure | Block Size | Key Size | No. of Rounds |
|---|---|---|---|---|
| AES [2] | SPN | 128 | 128/192/256 | 10/12/14 |
| DES [12] | Feistel | 64 | 54 | 16 |
| 3DES [13] | Feistel | 64 | 56/112/168 | 48 |
| LEA [8] | Feistel | 128 | 128,192,256 | 24/28/32 |
| RC2 [14] | Feistel | 64 | 8–1024 | 18 |
| RC5 [15] | Feistel | 32/64/128 | 0–2040 | 1–255 |
| RC6 [16] | Feistel | 128 | 128/192/256 | 20 |
| Present [17] | SPN | 64 | 80/128 | 31 |
| XTEA [18] | Feistel | 128 | 128 | 64 |
| TEA [10] | Feistel | 64 | 128 | 64 |
| mCrypton [19] | SPN | 64 | 64/96/128 | 12 |
| Twofish [20] | Feistel | 128 | 128/192/256 | 16 |
| Idea [21] | Lai–Massey | 64 | 128 | 8.5 |
| GOST [22] | Feistel | 64 | 256 | 32 |
| Katan [11] | Stream | 32/48/64 | 80 | 254 |
| PRINTcipher [23] | SPN | 48/46 | 48/96 | 48/96 |
| Blowfish [24] | Feistel | 64 | 32–448 | 16 |
| Khundra [25] | Feistel | 64 | 80 | 18 |
| Skipjack [26] | Feistel | 64 | 80 | 32 |
| Misty1 [27] | Feistel | 64 | 128 | 8 |
| Prince [28] | SPN | 64 | 128 | 12 |
| Sea [29] | Feistel | 48/96/144 | 48,96,144 | Variable |
| Notation | Description |
|---|---|
| n | half of the block size |
| Key and Subkeys | |
| Secret Key | |
| S-Box (S) | Substitution Box |
| P-Box (P) | Permutation Box |
| left circular shift of p by r position | |
| right circular shift of q by r position | |
| left n-bit input words to the i-th round | |
| right n-bit input words to the i-th round |
| x | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | A | B | C | D | E | F |
| S(x) | 5 | C | B | 6 | 9 | 0 | D | A | E | 3 | 8 | F | 4 | 1 | 7 | 2 |
| x | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | A | B | C | D | E | F |
| S(x) | C | 5 | 6 | B | 9 | 0 | A | D | 3 | E | F | 8 | 4 | 7 | 1 | 2 |
| x | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | A | B | C | D | E | F |
| P(x) | 15 | 10 | 5 | 0 | 3 | 14 | 9 | 4 | 2 | 7 | 13 | 8 | 12 | 1 | 6 | 11 |
| x | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | A | B | C | D | E | F |
| P(x) | 15 | 5 | 10 | 0 | 6 | 4 | 9 | 14 | 2 | 7 | 13 | 8 | 12 | 1 | 3 | 11 |
| Cryptosystem | Algorithm Family | Security Level | |||
|---|---|---|---|---|---|
| 80 | 128 | 192 | 256 | ||
| Elliptic Curve Digital Signature Algorithm (ECDSA), Elliptic-curve Diffie–Hellman (ECDH) | Elliptical Curve | 160 bit | 256 bit | 384 bit | 512 bit |
| Digital Signature Algorithm (DSA), Elgamal, Diffie–Hellman (DH) | Discrete logarithm | 1024 bit | 3072 bit | 7680 bit | 15,360 bit |
| Rivest-Shamir-Adleman (RSA) | Integer factorization | 1024 bit | 3072 bit | 7680 bit | 15,360 bit |
| Algorithm | Key Size | Block Size | Technology (m) | Area (GE) |
|---|---|---|---|---|
| CLEFIA [30] | 128 | 128 | 0.13 | 2488 |
| LED [31] | 128 | 64 | 0.13 | 3194 |
| XTEA [18] | 128 | 64 | 0.13 | 2521 |
| KLEIN [32] | 64 | 64 | 0.13 | 1432 |
| SEA [33] | 96 | 96 | 0.13 | 2562 |
| PRINCE [34] | 128 | 64 | 0.13 | 2953 |
| AES-128 [35] | 128 | 128 | 0.13 | 3100 |
| NOEKEON [33] | 128 | 128 | 0.13 | 2880 |
| PRESENT-80 [17] | 80 | 64 | 0.13 | 2195 |
| RECTANGLE [36] | 80 | 64 | 0.13 | 1111 |
| Piccolo-80 [37] | 80 | 64 | 0.13 | 683 |
| Piccolo-128 [37] | 128 | 64 | 0.13 | 758 |
| mCrypton-64 [19] | 64 | 128 | 0.13 | 2420 |
| mCrypton-96 [19] | 96 | 128 | 0.13 | 2681 |
| mCrypton-128 [19] | 128 | 128 | 0.13 | 2949 |
| SIMON [38] | 64 | 32 | 0.13 | 562 |
| SIMON [38] | 96 | 48 | 0.13 | 796 |
| SIMON [38] | 128 | 64 | 0.13 | 1026 |
| SPECK [38] | 64 | 32 | 0.13 | 549 |
| SPECK [38] | 96 | 48 | 0.13 | 778 |
| SPECK [38] | 128 | 64 | 0.13 | 1005 |
| BRISK | 80 | 32 | 0.13 | <580 |
| Cipher Version | Plaintext | Ciphertext | Bias | Active S-Boxes |
|---|---|---|---|---|
| S-Box and P-Box | 0x8000 0x0000 | 0x9000 0x5004 | 30.41 | 12 |
| S-Box and P-Box | 0x0000 0x8000 | 0x0080 0x000a | 30 | 11 |
| Cipher Version | Plaintext | Ciphertext | Bias | Active S-Boxes |
|---|---|---|---|---|
| S-Box and P-Box | 0xa43b 0x26c6 | 0x0001 0x0080 | 31 | 17 |
| S-Box and P-Box | 0xc189 0xb110 | 0x2800 0x0240 | 30.41 | 17 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dwivedi, A.D. BRISK: Dynamic Encryption Based Cipher for Long Term Security. Sensors 2021, 21, 5744. https://doi.org/10.3390/s21175744
Dwivedi AD. BRISK: Dynamic Encryption Based Cipher for Long Term Security. Sensors. 2021; 21(17):5744. https://doi.org/10.3390/s21175744
Chicago/Turabian StyleDwivedi, Ashutosh Dhar. 2021. "BRISK: Dynamic Encryption Based Cipher for Long Term Security" Sensors 21, no. 17: 5744. https://doi.org/10.3390/s21175744
APA StyleDwivedi, A. D. (2021). BRISK: Dynamic Encryption Based Cipher for Long Term Security. Sensors, 21(17), 5744. https://doi.org/10.3390/s21175744






