Abstract
In this paper, we study the physical layer security for simultaneous wireless information and power transfer (SWIPT)-based half-duplex (HD) decode-and-forward relaying system. We consider a system model including one transmitter that tries to transmit information to one receiver under the help of multiple relay users and in the presence of one eavesdropper that attempts to overhear the confidential information. More specifically, to investigate the secrecy performance, we derive closed-form expressions of outage probability (OP) and secrecy outage probability for dynamic power splitting-based relaying (DPSBR) and static power splitting-based relaying (SPSBR) schemes. Moreover, the lower bound of secrecy outage probability is obtained when the source’s transmit power goes to infinity. The Monte Carlo simulations are given to corroborate the correctness of our mathematical analysis. It is observed from simulation results that the proposed DPSBR scheme outperforms the SPSBR-based schemes in terms of OP and SOP under the impact of different parameters on system performance.
1. Introduction
The Internet of Things (IoT) has become an importation application in 5G and beyond network [1,2,3,4,5,6]. With the evolution of IoT, there will be billions of connected IoT users (IoTUs), which can provide various applications, e.g., smart city, health, and agriculture. However, conventional IoTUs usually have limited operation time due to limited battery capacity. Thanks to the recent development of energy harvesting, IoTUs can help to solve the energy problem. Besides, energy sources from the ambient environment such as wind [7,8], vibration [9,10], and solar [11] can also contribute to solving the energy problem. Nevertheless, these energy sources are unreliable and depend on on external conditions, e.g., weather. Consequently, wireless power transfer (WPT) has emerged as a solution to provide a robust energy supply because the IoTUs can harvest energy from radio frequency (RF) signals, which does not influenced by surrounding environment [12,13,14,15].
Particularly, simultaneous wireless information and power transfer (SWIPT) technology has received significant attention from researchers due to its ability to bring both information and energy at the same time [16,17,18,19,20]. Specifically, the authors of [16,17] investigated SWIPT in IoT networks. Lu et al. [16] proposed two SWIPT-based spectrum sharing methods to enhance the spectrum and energy efficiency in 6G IoT networks. Wang et al. [17] investigated a SWIPT-based massive multiple-input multiple-output (MIMO) two-way relaying system by considering maximum ratio combining and zero-forcing. In [18,19,20,21], the authors investigated the SWIPT in two-way (TW) relaying networks. Nguyen et al. [21] proposed and investigated a new system model for SWIPT-based TW relaying systems. Specifically, they derived the closed-form of three relay schemes, termed decode-and-forward (DF), amplify-and-forward (AF), and hybrid decode-and-forward (HDAF). Garg et al. [18] considered the hordal distance (CD) decomposition-based precoder design to reduce the complexity as compared with semi-definite relaxation (SDR)-based methods, for the SWIPT-assisted AF TW relay system. Tin et al. [19] proposed a new EH-based TW half-duplex (HD) relay sensor network under the presence of a direct link between the transmitter and receiver. Specifically, they derived the closed-form expressions the exact and asymptotic of ergodic capacity and the exact analysis of symbol error rate. Zhang et al. [20] studied the neural network-based relay selection in SWIPT-enabled TW cognitive radio networks (CRNs). Concretely, they proposed two relay selection methods corresponding to fixed and variable number of relays, which outperformed the traditional relay selection and machine learning schemes.
Besides energy harvesting, communication security is crucially important for wireless systems. Recently, physical layer security (PLS) has become an effective method to improve the secrecy of wireless communications without sharing security keys [22,23,24,25]. In [22], the authors proposed a generalized partial relay selection (PRS) protocol to improve the security for CRNs under perfect or imperfect CSI. The PLS in millimeter-wave (mmWave) communications was investigated in [23]. Concretely, they proposed a Sight-based Cooperative Jamming (SCJ) method to enhance the secrecy performance of mmWave communications. Wijewardena studied the PLS for intelligent reflecting surface (IRS) two-way communications. In detail, they aimed to maximize the sum-secrecy rate of an IRS-assisted full-duplex (FD) TW communication system in the presence of an untrusted user. In [25], the authors considered a novel system model for EH-based PLS multi-hop multi-path cooperative wireless networks. Then, they proposed three relay protocols—shortest path, random path, and best path selection schemes—to enhance the PLS performance.
Recently, EH and SWIPT have become hot topics [26,27,28,29,30,31]. An et al. [26] considered a hybrid time-power splitting (HTPS) TW HD cooperative relaying in the presence of an eavesdropper. In this context, they derived the closed-form expression of the outage probability (OP) and intercept probability (IP) using maximal ratio combining (MRC) and selection combining (SC). The authors of [27] investigated the PLS of a power beacon-assisted FD EH relaying system using delay-tolerant (DTT) and delay-limited (DLT) methods. In [28], the PLS was studied in mmWave- and SWIPT-enabled UAV networks by considering considering actual 3-D antenna gain and the effect of beamforming design. In [29], the secrecy performance was investigated in a UAV-assisted NOMA system with SWIPT by using artificial jamming and NOMA information. The PLS of a downlink (DL) multiuser orthogonal frequency division multiplexing (OFDM) IoT system was exploited in [30]. Deng et al. [31] studied the secure beamforming design for a TW CR IoT network with SWIPT by maximizing the secrecy capacity for primary users by designing the beamforming matrix.
In this work, we proposed and investigate the secrecy performance of a SWIPT-assisted HD DF relaying system in the presence of a eavesdropper. The contributions can be summarized as follows.
- We consider a single-input single-output (SISO) system model in which multiple relay nodes harvest energy from a transmitter S and help S to transfer information to the destination in the presence of an eavesdropper. Moreover, partial relay selection protocol is adopted to select the best relay.
- For the SWIPT technique, both dynamic power splitting-based relaying (DPSBR) and static power splitting-based relaying (SPSBR) are considered in our work to give a full picture of the advantages of each method. Specifically, we derive the closed-form expressions in terms of OP and SOP for each scheme. Furthermore, the lower bound of SOP is obtained when the transmit power of S goes to infinity.
- Simulation results are performed to corroborate the exactness of our analysis. Through simulation results, it can be concludes that that DPSBR always obtains a better performance, i.e., OP and SOP, compared to SPSBR.
2. System Model
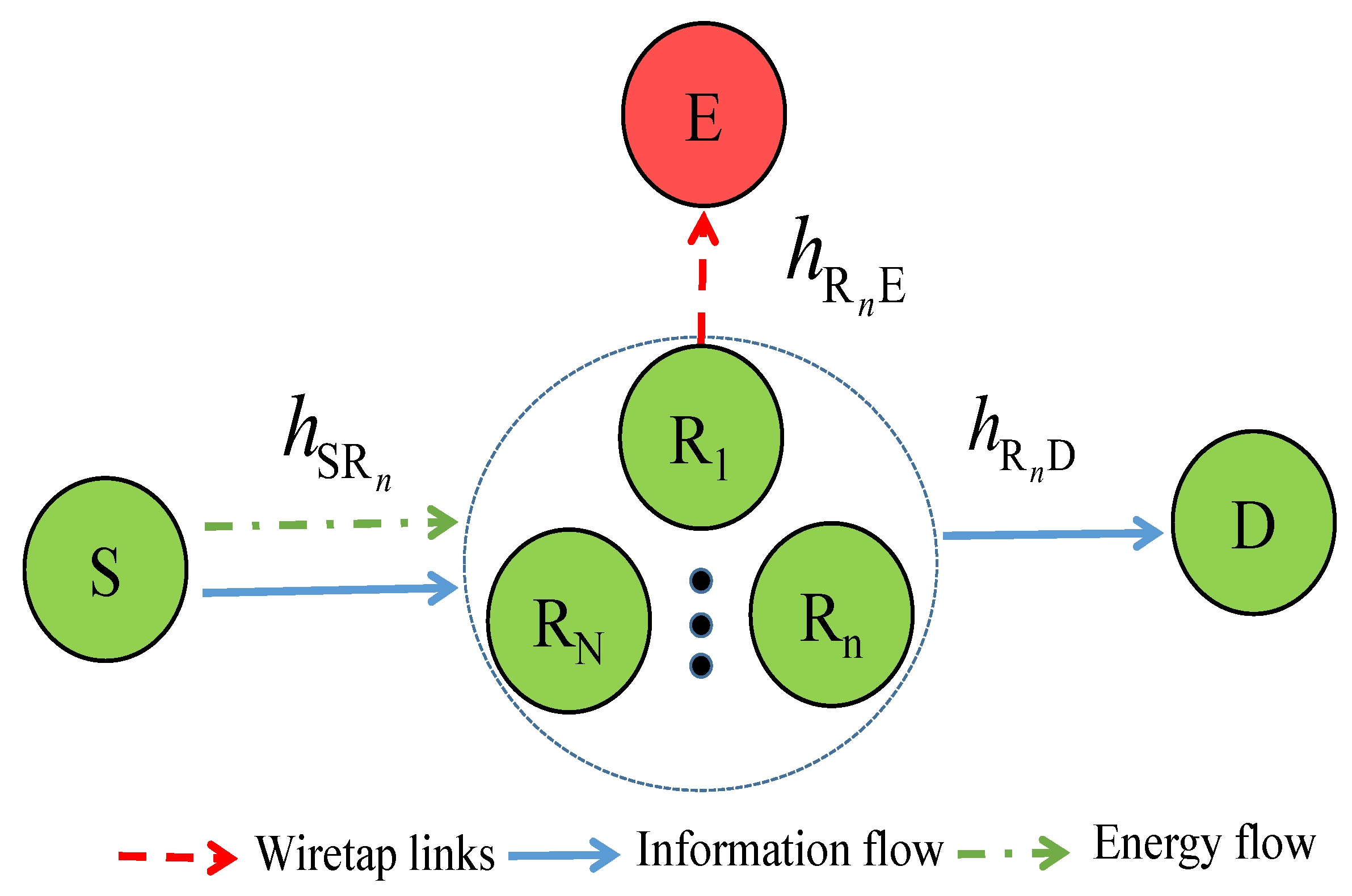
In Figure 1, we describe the proposed system model as follows. The system includes a source S that communicates with a destination D via help of N half-duplex relays denoted by , where . Besides, there exists an eavesdropper that tries to overhear confidential information from relays. Moreover, the source can transmit both data and power to the relay using the SWIPT technique. As relay users are equipped with energy harvesters, they can thus harvest energy from the source’s signals and then use it to transfer information to the destination D.
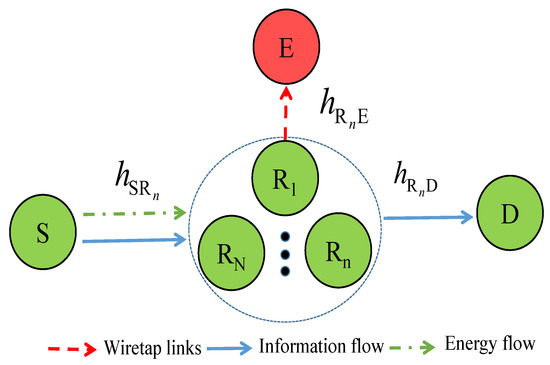
Figure 1.
SWIPT-based cooperative relay networks in the presence of an eavesdropper.
Let us denote , , and as the channel coefficients of the , and links, respectively.
Assume that all of the channels are Rayleigh fading, thus the channel gains , , and are exponential random variables (RVs) whose CDF are given as ([32], Equation (1))
To take path-loss into account, we can model the parameters as follows:
where , , and are link distances of the , , and links, respectively.
The received signal at the relay can be expressed as
where is the energy symbol with , and denotes the expectation operation; is the zero-mean additive white Gaussian noise (AWGN) with variance .
The energy harvesting in relay can be computed as (Equation (3) [33])
where and are the transmit powers of S and , respectively.
The received signal at the destination can be given as
where is the zero mean AWGN with variance .
In this paper, we consider the DF relaying protocols. From (8), the signal to noise ratio (SNR) at the relay node can be derived by
where .
From (9), the SNR at the destination can be obtained as
Finally, the overall SNR and the capacity of system can be claimed by, respectively,
Taking into account the impact of eavesdropper E, E will overhear the information from chosen relay n-th, so the received signal at E can be expressed by
where and is the zero-mean AWGN with variance .
Remark 1.
In this work, we adopt partial relay selection (PRS) protocol. Without loss of generality, we assume that the relay is closer to source S than to destination D, and the relay selection should be performed based on the quality of the second-hop links to improve overall performance. Specifically, the best relay user is selected according to the optimal relay selection method, which is described as follows:
The cumulative density function (CDF) between selected relay to destination D, i.e., , is given as ([34] Equation (14))
Considering the i.i.d. random variables (RVs), i.e., , Equation (13) can be rewritten as
where
Based on (20), the probability density function (PDF) of , i.e., , can be calculated as
3. Performance Analysis
This section provides the mathematical analysis of the outage probability (OP) and secrecy outage probability (SOP) to provide further insight into the two-hop data transmission for SWIPT-based HD DF relay networks in two cases, i.e., dynamic power splitting-based relaying and static power splitting-based relaying.
3.1. Case 1: Static Power Splitting-Based Relaying
3.1.1. Outage Probability (OP) Analysis
In this section, the outage probability of the SWIPT-aided HD DF relaying system over Rayleigh fading channels is derived. Specifically, it can be calculated as (Equation (21) [35])
where , and is the threshold rate at the destination to decode signals successfully.
Theorem 1.
In static power splitting-based relaying, the closed-form expression of the OP can be given as
where M determines the trade-off between complexity and accuracy for the Gaussian–Chebyshev quadrature-based approximation, where and .
3.1.2. Secrecy Outage Probability (SOP) Analysis
- a.
- Exact Analysis
It is noted that . Thus, (28) is reformulated as
- b.
- Asymptotic Analysis
In the high signal-to-noise-ratio (SNR) regime, from (34) SOP can be calculated as follows:
Lemma 1.
In the high signal-to-noise-ratio (SNR) regime, the closed-form expression of SOP according to static power splitting-based relaying is expressed as
3.2. Case 2: Dynamic Power Splitting-Based Relaying
In this section, we would like to find the optimal power splitting factor, i.e., to maximize the system capacity . Because the DF is adopted in our work, can be calculated as follows:
3.2.1. OP Analysis
Theorem 3.
In dynamic power splitting-based relaying, the closed-form expression of the OP is given as
3.2.2. SOP Analysis
- a.
- Exact Analysis
Theorem 4.
In dynamic power splitting-based relaying, SOP can be expressed as
where is the Meijer G-function.
Proof.
By denoting , (43) can be rewritten by
By applying ([38] Equation 3.324.1), can be obtained as
By applying the Taylor series and denoting , SOP can be calculated as
By applying , we have
Finally, by using ([38], Equation 6.592.4), SOP can be obtained as in (41). □
- b.
- Asymptotic Analysis
From (41), SOP can be approximated as
4. Simulation Results
In this section, we present the proposed partial relay selection in terms of the outage probability and secrecy outage probability via analysis and simulation results. All transmission links are Rayleigh fading channels, and the path-loss model is considered, where the path loss exponent equals 2.5. The locations of source S, relay R, destination D, and eavesdropper E are (0,0), (0.5, 0), (2, 0), and (0.5, 2), respectively. To obtain the outage probability and secrecy outage probability for the proposed methods, we execute independent samples, and the channel coefficients are randomly generated as Rayleigh fading in each sample.
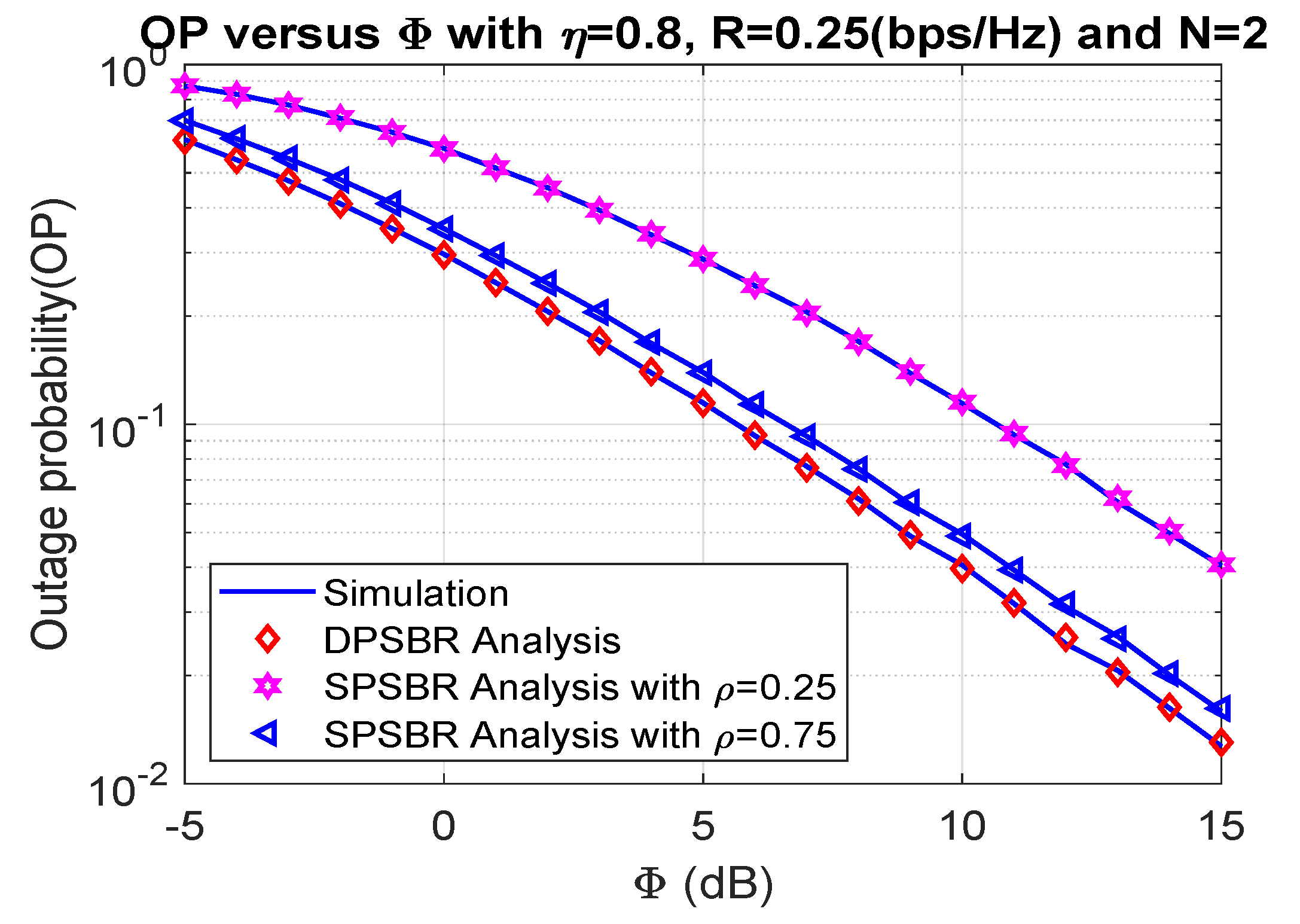
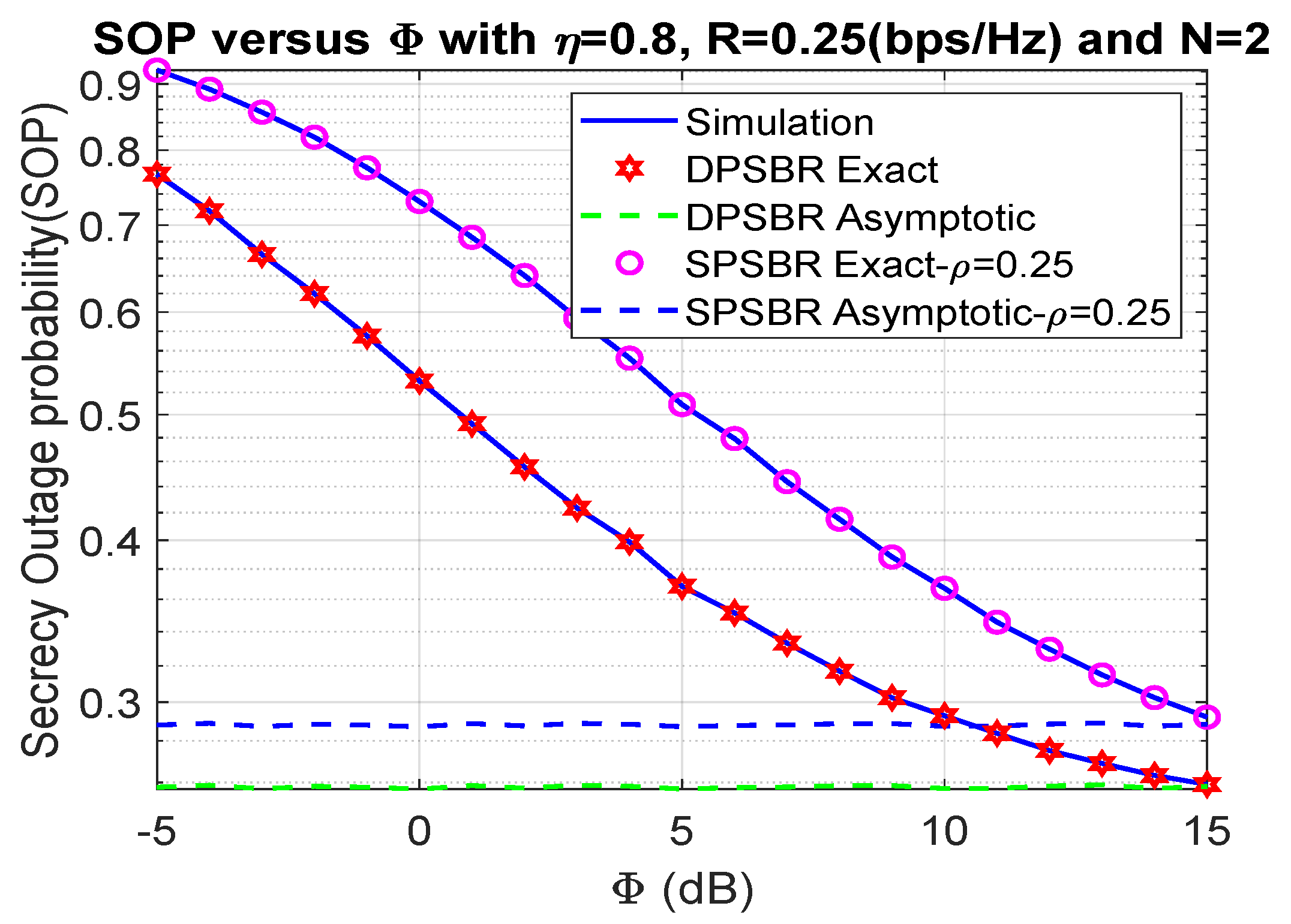
In Figure 2 and Figure 3, we show the impact of on the OP and SOP, where 0.8, 0.25 bps/Hz, and N = 2. In Figure 2 and Figure 3, we compared the dynamic power splitting-based relaying (DPSBR) with the static power splitting-based relaying (SPSBR), whereas the SPSBR is considered in two-mode equals 0.25 and 0.75, respectively. First, it is easy to see that the DPSBR obtains better OP and SOP results compared to SPSBR methods. Specifically, when = 15 dB, the OP of DPSBR is 0.013, while the SPSBR with and impose 0.0407 and 0.0159, respectively. This is because the DPSBR scheme aims to maximize the system capacity, thus it can improve the outage performance while the SPSBR scheme always select a fixed value of power splitting factor . Second, the higher the value is, the better OP and SOP can be obtained. It can be explained by the fact that the higher value means the more transmit power of source S is assigned, which is defined in Equation (11).
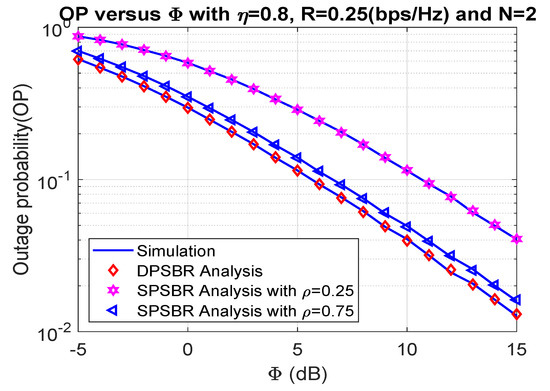
Figure 2.
Outage probability versus (dB).
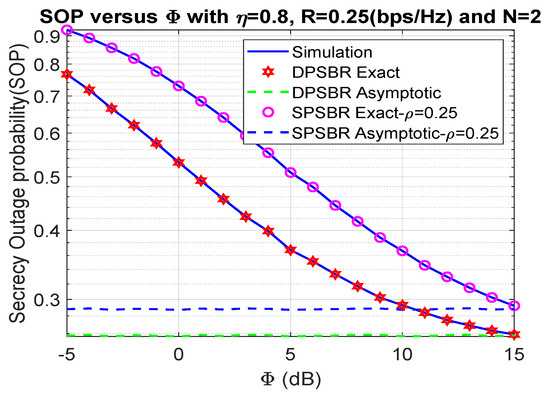
Figure 3.
Outage probability versus (dB).
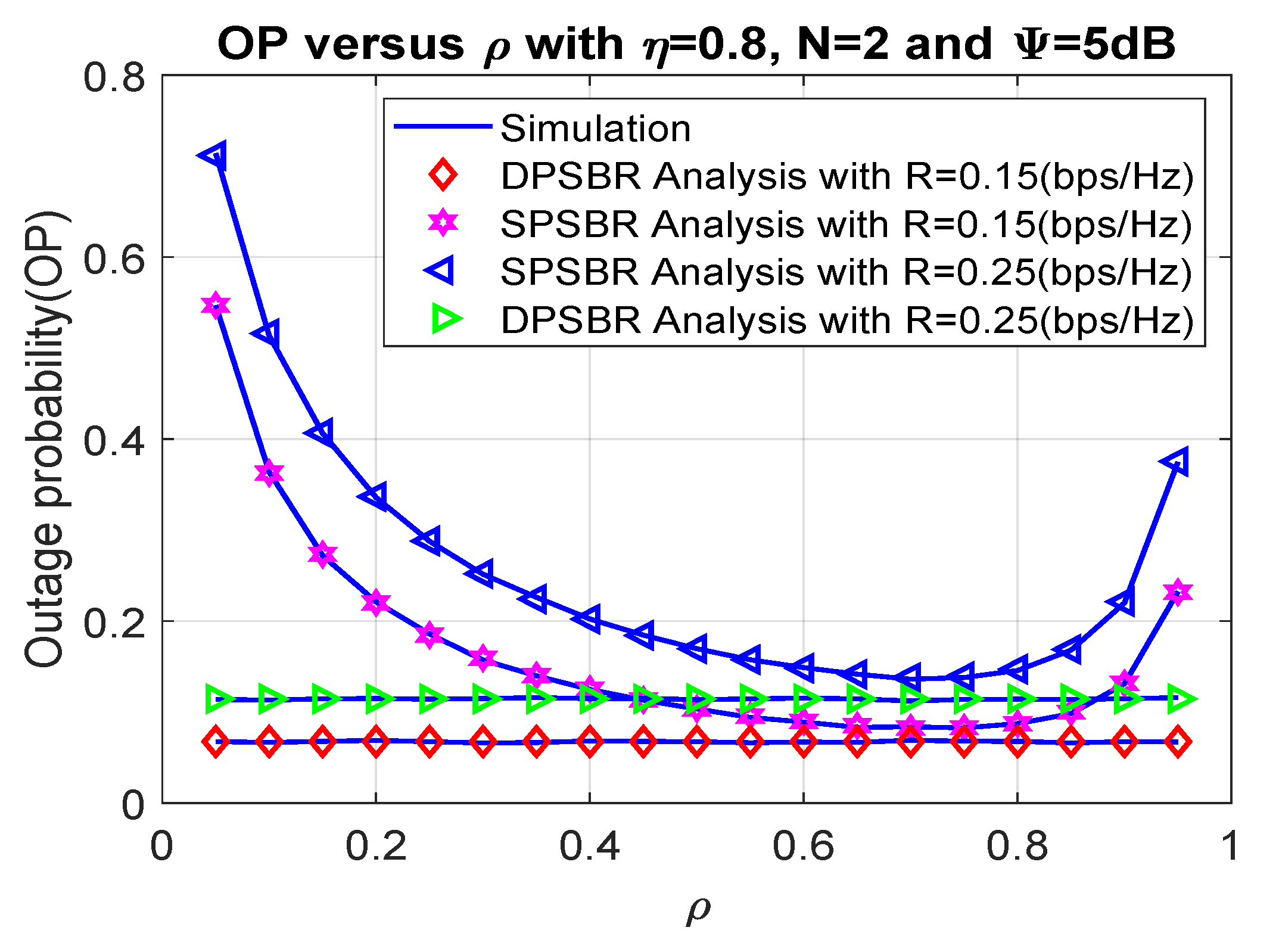
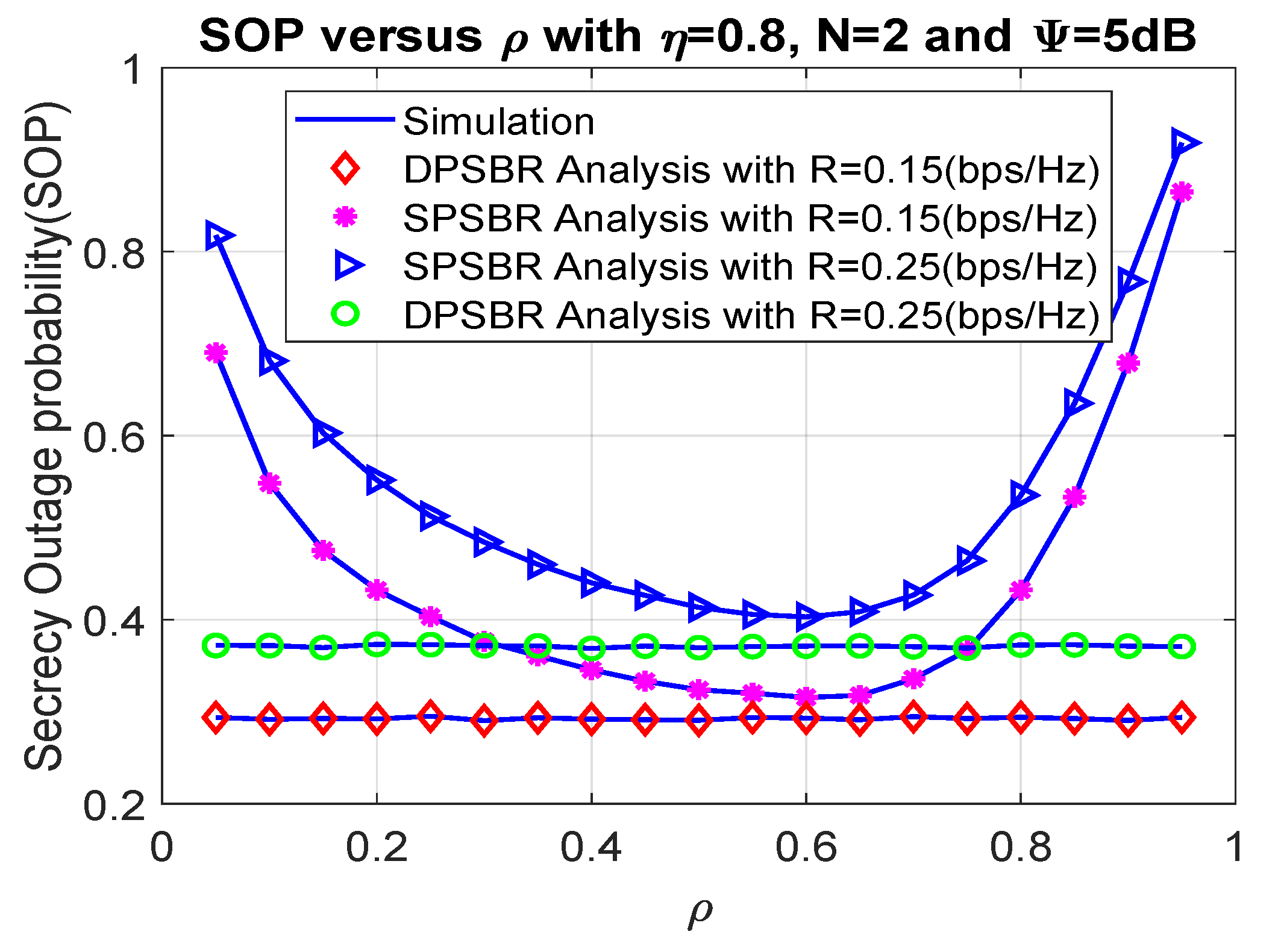
Next, we investigate the OP and SOP subject to different power splitting factor in Figure 4 and Figure 5, where 0.8, number of relays N = 2, and = 5 dB. The power splitting factor plays an important role as it affects the fraction of power used for energy harvesting and data transmission. Therefore, there exists an optimal value of power splitting factor to maximize the outage probability and secrecy outage probability. Specifically, the SPSBR with R = 0.15 bps/Hz and R = 0.25 bps/Hz can obtain the best outage value at = 0.7, and their OP/SOP values result in a parabolic shape. Notably, it is shown from Figure 4 and Figure 5 that the OP and SOP of the DPSBR do not depend on value. This is because the DPSBR is designed to be used at the best value and it is fixed when we operate the system.
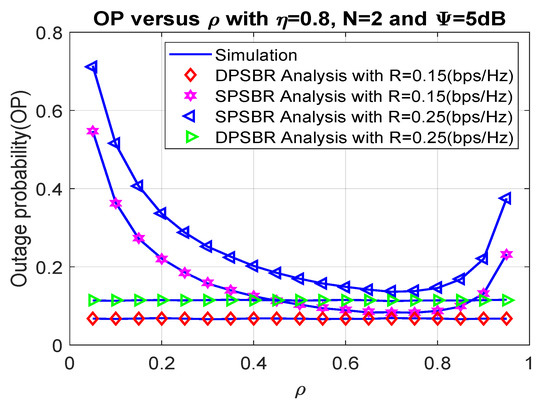
Figure 4.
Outage probability versus .
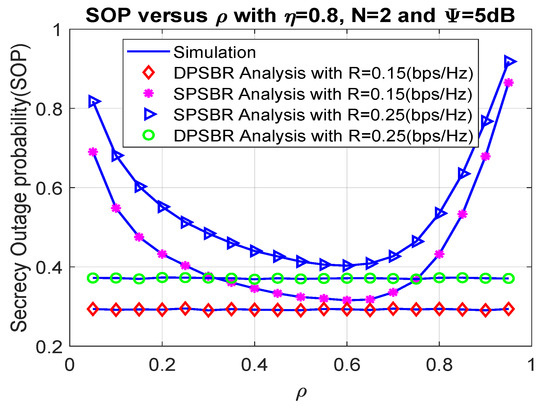
Figure 5.
Secrecy outage probability versus .
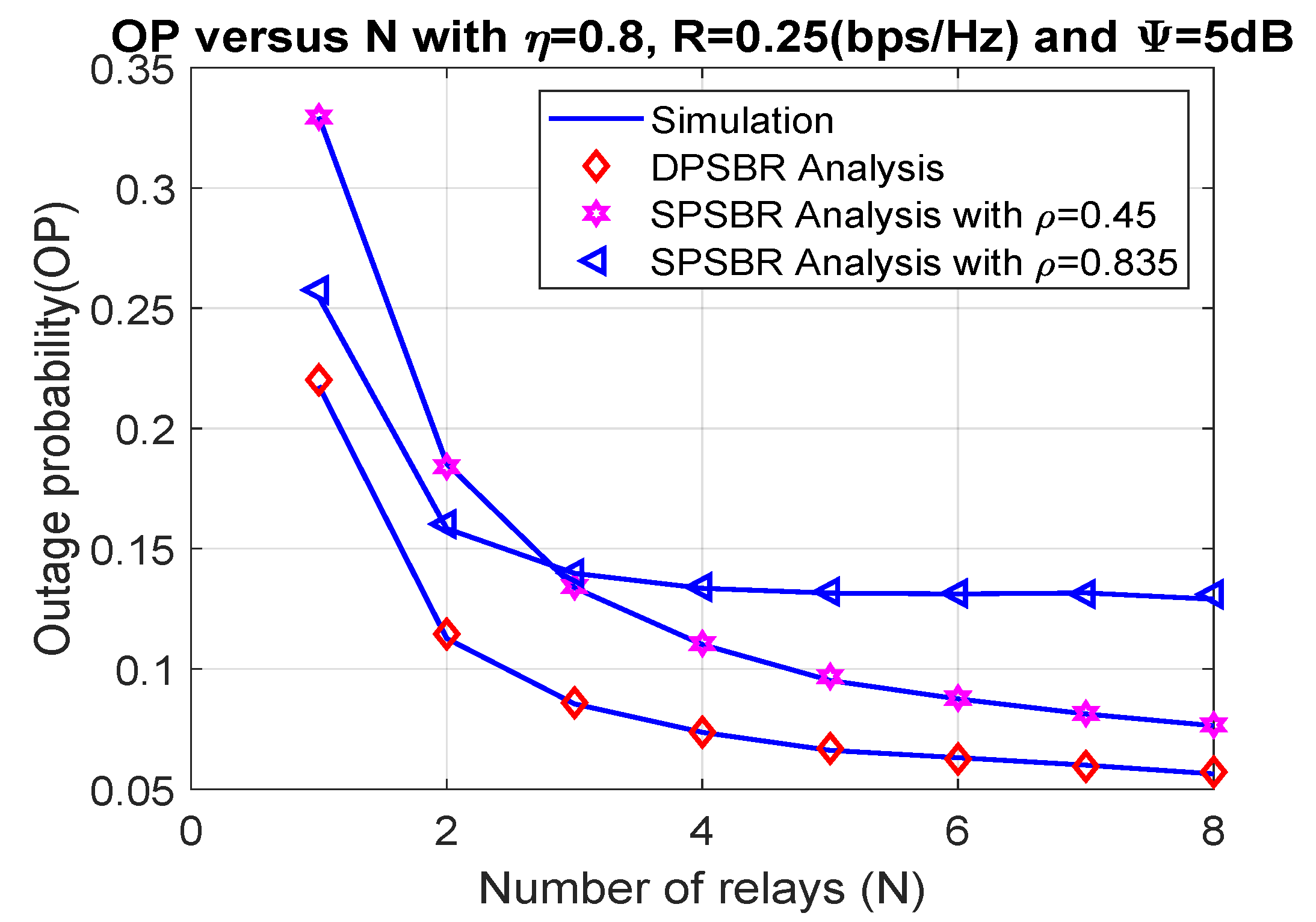
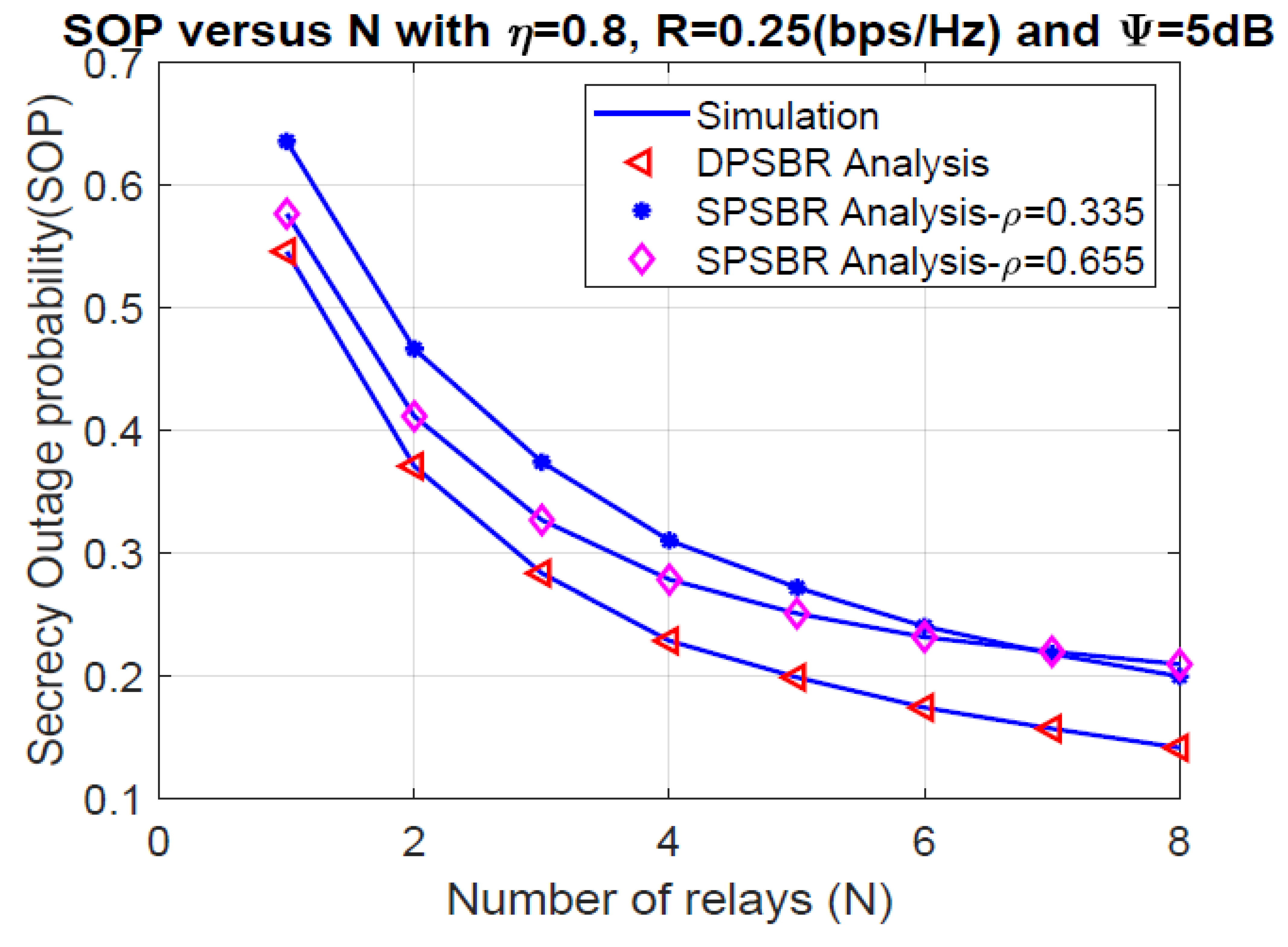
Last, Figure 6 and Figure 7 plot the OP and SOP as functions of number of relays (N), where = 0.8, R = 0.25 bps/Hz, and 5 dB. It is observed that the proposed DPSBR method outperforms other benchmark ones, i.e., SPSBR with = 0.45 and SPSBR with = 0.835. More specifically, when N = 8, the OP of DPSBR scheme is 0.0571, while the SPSBR with = 0.45 and SPSBR with = 0.835 impose 0.0767 and 0.129, respectively. Particularly, the SPSBR with = 0.835 can obtain a better outage performance compared to SPSBR with = 0.45 with a low number of relays, i.e., N < 3. However, when the number of relays is large enough, i.e., N > 3, SPSBR with = 0.835 deteriorates than SPSBR with = 0.45. In Figure 7, we study the effect of number of relays on SOP. It is revealed that increasing the number of relays significantly improves the secrecy performance. This is because the higher the number of relays is, the better the channel selection from relay to destination is, which enhances the secrecy performance.
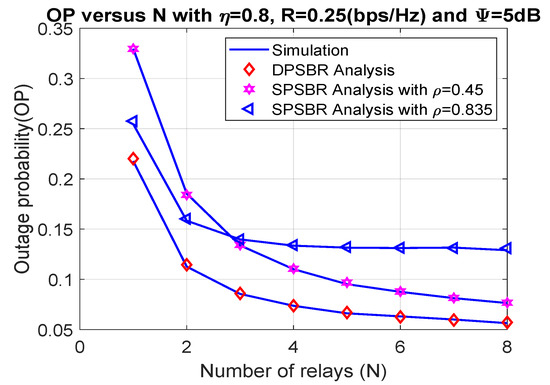
Figure 6.
Outage probability versus number of relays (N).
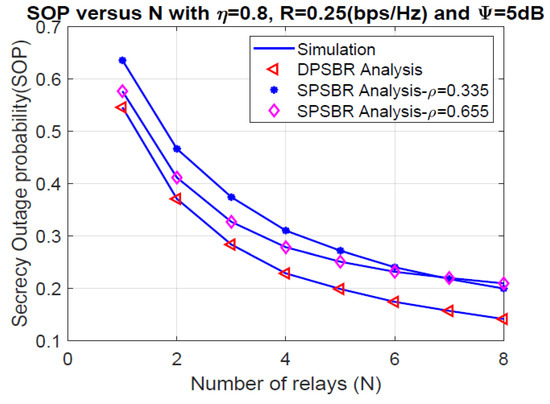
Figure 7.
Secrecy outage probability versus number of relays (N).
5. Conclusions
This paper proposed a partial relay selection scheme for SWIPT-based HD DF relaying under the presence of an eavesdropper. Specifically, we investigated the OP and SOP for dynamic power splitting-based relaying and statistic power splitting-based relaying. Most importantly, the closed-form expressions of OP and SOP (i.e., for exact and asymptotic analysis) are derived. Mote Carlo simulations were given to demonstrate the correctness of our theoretical analysis. In general, the proposed DPSBR scheme showed its superiority compared to SPSBR in terms of OP and SOP. More specifically, extensive simulation results showed that the OP and SOP performance of the DPSBR can improve up 94.5% and 33.4% than SPSBR schemes, respectively. In particular, when the power splitting factor equals 0.5, the OP and SOP values of the SPSBR scheme with = 0.15 bps/Hz obtained a performance almost DPSBR. Therefore, the system should operate in the SPSBR scheme in this scenario for a simple implementation.
In future work, it will be interesting to extend this work to the following research directions: (1) The relay users can be UAVs or intelligent reflecting surfaces; (2) Using a friendly jammer or artificial noise to improve the system security; (3) A more general system model such as an independent but not identically distributed Rayleigh fading or Nakagami-m fading channel.
Author Contributions
The main contribution of V.-D.P. and T.N.N. were to execute performance evaluations by theoretical analysis and simulations, while A.V.L. and M.V. worked as the advisors of V.-D.P. and T.N.N. in discussing, creating, and advising on performance evaluations together. All authors have read and agreed to the published version of the manuscript.
Funding
The research was supported by the Ministry of Education, Youth and Sport of the Czech Republic within the grant SP2021/25 conducted at the VSB-Technical University of Ostrava.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Jasiński, M.; Majtczak, P.; Malinowski, A. Fuzzy logic in decision support system as a simple Human/Internet of Things interface for shunt active power filter. Bull. Pol. Acad. Sci. Tech. Sci. 2016, 64, 877–886. [Google Scholar] [CrossRef][Green Version]
- Kiciński, J. Green energy transformation in Poland. Bull. Pol. Acad. Sci. Tech. Sci. 2021, 69. [Google Scholar] [CrossRef]
- Nguyen, P.X.; Tran, D.H.; Onireti, O.; Tin, P.T.; Nguyen, S.Q.; Chatzinotas, S.; Vincent Poor, H. Backscatter-Assisted Data Offloading in OFDMA-Based Wireless-Powered Mobile Edge Computing for IoT Networks. IEEE Internet Things J. 2021, 8, 9233–9243. [Google Scholar] [CrossRef]
- Cong, R.; Zhao, Z.; Min, G.; Feng, C.; Jiang, Y. EdgeGO: A Mobile Resource-sharing Framework for 6G Edge Computing in Massive IoT Systems. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Fang, X.; Feng, W.; Wei, T.; Chen, Y.; Ge, N.; Wang, C.X. 5G Embraces Satellites for 6G Ubiquitous IoT: Basic Models for Integrated Satellite Terrestrial Networks. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Tran, D.H.; Nguyen, V.D.; Symeon, C.; Vu, X.T.; Bjorn, O. UAV Relay-Assisted Emergency Communications in IoT Networks: Resource Allocation and Trajectory Optimization. arXiv 2020, arXiv:2008.00218. [Google Scholar]
- Jung, H.J.; Park, J.; Kim, I.H. Investigation of Applicability of Electromagnetic Energy Harvesting System to Inclined Stay Cable Under Wind Load. IEEE Trans. Magn. 2012, 48, 3478–3481. [Google Scholar] [CrossRef]
- Tan, Y.K.; Panda, S.K. Self-Autonomous Wireless Sensor Nodes with Wind Energy Harvesting for Remote Sensing of Wind-Driven Wildfire Spread. IEEE Trans. Instrum. Meas. 2011, 60, 1367–1377. [Google Scholar] [CrossRef]
- Sang, Y.; Huang, X.; Liu, H.; Jin, P. A Vibration-Based Hybrid Energy Harvester for Wireless Sensor Systems. IEEE Trans. Magn. 2012, 48, 4495–4498. [Google Scholar] [CrossRef]
- Qiu, J.; Liu, X.; Chen, H.; Xu, X.; Wen, Y.; Li, P. A Low-Frequency Resonant Electromagnetic Vibration Energy Harvester Employing the Halbach Arrays for Intelligent Wireless Sensor Networks. IEEE Trans. Magn. 2015, 51, 1–4. [Google Scholar] [CrossRef]
- Hieu, T.D.; Dung, L.T.; Kim, B.S. Stability-aware geographic routing in energy harvesting wireless sensor networks. Sensors 2016, 16, 696. [Google Scholar] [CrossRef]
- Tavana, M.; Ozger, M.; Baltaci, A.; Schleicher, B.; Schupke, D.; Cavdar, C. Wireless Power Transfer for Aircraft IoT Applications: System Design and Measurements. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Nguyen, B.C.; Hoang, T.M.; Tran, P.T.; Nguyen, T.N. Outage probability of NOMA system with wireless power transfer at source and full-duplex relay. AEU-Int. J. Electron. Commun. 2020, 116, 152957. [Google Scholar] [CrossRef]
- Hieu, T.D.; Duy, T.T.; Choi, S.G. Performance evaluation of relay selection schemes in beacon-assisted dual-hop cognitive radio wireless sensor networks under impact of hardware noises. Sensors 2018, 18, 1843. [Google Scholar] [CrossRef] [PubMed]
- Wang, X.; Liu, J.; Zhai, C. Wireless Power Transfer-Based Multi-Pair Two-Way Relaying With Massive Antennas. IEEE Trans. Wirel. Commun. 2017, 16, 7672–7684. [Google Scholar] [CrossRef]
- Lu, W.; Si, P.; Huang, G.; Han, H.; Qian, L.; Zhao, N.; Gong, Y. SWIPT Cooperative Spectrum Sharing for 6G-Enabled Cognitive IoT Network. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Wang, J.; Wang, G.; Li, B.; Yang, H.; Hu, Y.; Schmeink, A. Massive MIMO Two-Way Relaying Systems with SWIPT in IoT Networks. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Garg, N.; Zhang, J.; Ratnarajah, T. Rate-Energy Balanced Precoding Design for SWIPT based Two-Way Relay Systems. IEEE J. Sel. Top. Signal Process. 2021. [Google Scholar] [CrossRef]
- Tin, P.T.; Nguyen, T.N.; Tran, M.; Trang, T.T.; Sevcik, L. Exploiting direct link in two-way half-duplex sensor network over block rayleigh fading channel: Upper bound ergodic capacity and exact SER analysis. Sensors 2020, 20, 1165. [Google Scholar] [CrossRef]
- Zhang, Z.; Lu, Y.; Huang, Y.; Zhang, P. Neural Network-Based Relay Selection in Two-Way SWIPT-Enabled Cognitive Radio Networks. IEEE Trans. Veh. Technol. 2020, 69, 6264–6274. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Tran, P.T.; Voznak, M. Wireless energy harvesting meets receiver diversity: A successful approach for two-way half-duplex relay networks over block Rayleigh fading channel. Comput. Netw. 2020, 172, 107176. [Google Scholar] [CrossRef]
- Dinh Tran, H.; Trung Tran, D.; Choi, S.G. Secrecy performance of a generalized partial relay selection protocol in underlay cognitive networks. Int. J. Commun. Syst. 2018, 31, e3806. [Google Scholar] [CrossRef]
- Zhang, Y.; Shen, Y.; Jiang, X.; Kasahara, S. Secure Millimeter-Wave Ad Hoc Communications Using Physical Layer Security. IEEE Trans. Inf. Forensics Secur. 2021. [Google Scholar] [CrossRef]
- Wijewardena, M.; Samarasinghe, T.; Hemachandra, K.T.; Atapattu, S.; Evans, J.S. Physical Layer Security for Intelligent Reflecting Surface Assisted Two–Way Communications. IEEE Commun. Lett. 2021. [Google Scholar] [CrossRef]
- Hieu, T.D.; Duy, T.T.; Kim, B.S. Performance Enhancement for Multihop Harvest-to-Transmit WSNs With Path-Selection Methods in Presence of Eavesdroppers and Hardware Noises. IEEE Sens. J. 2018, 18, 5173–5186. [Google Scholar] [CrossRef]
- Hoang An, N.; Tran, M.; Nguyen, T.N.; Ha, D.H. Physical layer security in a hybrid TPSR two-way half-duplex relaying network over a Rayleigh fading channel: Outage and intercept probability analysis. Electronics 2020, 9, 428. [Google Scholar] [CrossRef]
- Tin, P.T.; Dinh, B.H.; Nguyen, T.N.; Ha, D.H.; Trang, T.T. Power Beacon-Assisted Energy Harvesting Wireless Physical Layer Cooperative Relaying Networks: Performance Analysis. Symmetry 2020, 12, 106. [Google Scholar] [CrossRef]
- Sun, X.; Yang, W.; Cai, Y.; Wang, M. Secure mmWave UAV-Enabled SWIPT Networks Based on Random Frequency Diverse Arrays. IEEE Internet Things J. 2021, 8, 528–540. [Google Scholar] [CrossRef]
- Wang, W.; Tang, J.; Zhao, N.; Liu, X.; Zhang, X.Y.; Chen, Y.; Qian, Y. Joint Precoding Optimization for Secure SWIPT in UAV-Aided NOMA Networks. IEEE Trans. Commun. 2020, 68, 5028–5040. [Google Scholar] [CrossRef]
- Xu, D.; Zhu, H. Secure Transmission for SWIPT IoT Systems With Full-Duplex IoT Devices. IEEE Internet Things J. 2019, 6, 10915–10933. [Google Scholar] [CrossRef]
- Deng, Z.; Li, Q.; Zhang, Q.; Yang, L.; Qin, J. Beamforming Design for Physical Layer Security in a Two-Way Cognitive Radio IoT Network With SWIPT. IEEE Internet Things J. 2019, 6, 10786–10798. [Google Scholar] [CrossRef]
- Ha, D.H.; Nguyen, T.N.; Tran, M.H.Q.; Li, X.; Tran, P.T.; Voznak, M. Security and Reliability Analysis of a Two-Way Half-Duplex Wireless Relaying Network Using Partial Relay Selection and Hybrid TPSR Energy Harvesting at Relay Nodes. IEEE Access 2020, 8, 187165–187181. [Google Scholar] [CrossRef]
- Tin, P.T.; Nguyen, T.N.; Tran, D.H.; Voznak, M.; Phan, V.D.; Chatzinotas, S. Performance Enhancement for Full-Duplex Relaying with Time-Switching-Based SWIPT in Wireless Sensors Networks. Sensors 2021, 21, 3847. [Google Scholar] [CrossRef] [PubMed]
- Nguyen, T.N.; Tran, M.; Nguyen, T.L.; Ha, D.H.; Voznak, M. Performance analysis of a user selection protocol in cooperative networks with power splitting protocol-based energy harvesting over Nakagami-m/Rayleigh channels. Electronics 2019, 8, 448. [Google Scholar] [CrossRef]
- Wu, H.; Zou, Y.; Cao, W.; Chen, Z.; Tsiftsis, T.A.; Bhatnagar, M.R.; De Lamare, R.C. Impact of Hardware Impairments on Outage Performance of Hybrid Satellite-Terrestrial Relay Systems. IEEE Access 2019, 7, 35103–35112. [Google Scholar] [CrossRef]
- Phu, T.T.; Phan, D.; Ha, D.H.; Nguyen, T.N.; Tran, M.; Voznak, M. Nonlinear energy harvesting based power splitting relaying in full-duplex AF and DF relaying networks: System performance analysis. Proc. Est. Acad. Sci. 2020, 69, 368–381. [Google Scholar]
- Bankey, V.; Upadhyay, P.K. Physical Layer Security of Multiuser Multirelay Hybrid Satellite-Terrestrial Relay Networks. IEEE Trans. Veh. Technol. 2019, 68, 2488–2501. [Google Scholar] [CrossRef]
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series, and Products; Academic Press: Cambridge, MA, USA, 2014. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).