A Blockchain-Based Spatial Crowdsourcing System for Spatial Information Collection Using a Reward Distribution
Abstract
:1. Introduction
- We proposed a blockchain-based system that increases transparency and security in the system compared to centralized systems.
- The proposed system uses crowdsourcing to collect spatial information in the form of reports, which reduces the entry of incorrect information into the system. The impact of this reduction on better resource allocation is also examined.
- To our best knowledge, this is the first system to reward all users based on spatial and non-spatial factors. We also provided formulas for calculating this reward.
- Moreover, due to the relevance of spatial information in the system, we performed user privacy and security analysis.
2. Related Works
- To the best of our knowledge, the rewarding mechanism for requesters is overlooked in crowdsourcing systems [29]. Furthermore, the lack of spatial factors to calculate the rewards of various users who participate in spatial crowdsourcing systems poses problems.
- Using users’ history in crowdsourcing systems reveals the users’ sensitive information and endangers their privacy [80].
- The lack of secure and transparent distributed spatial crowdsourcing systems for collecting accurate information is a significant issue and less research has been carried out in this area [81].
3. Problem Statement
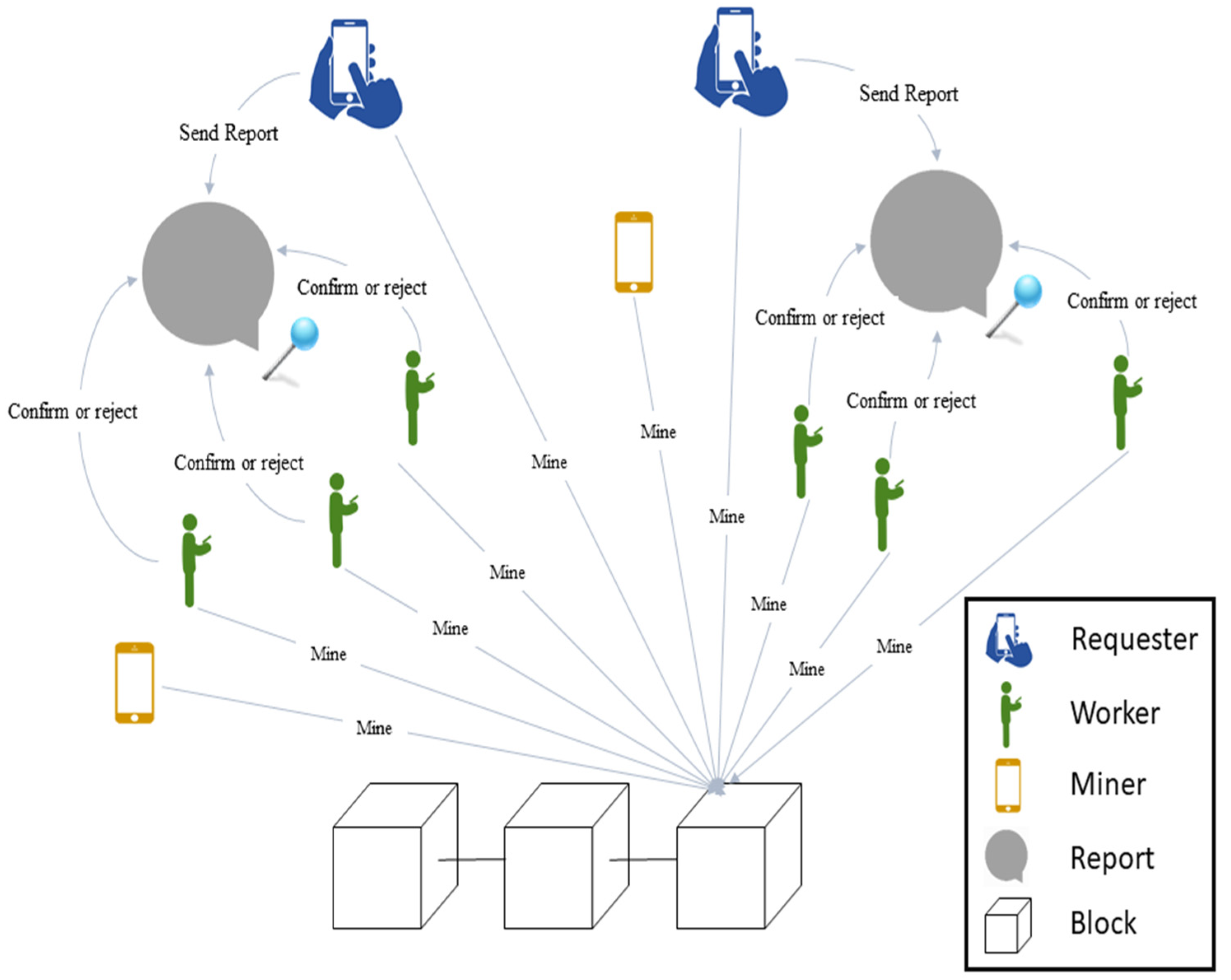
3.1. The Proposed System Architecture
3.2. Notations
- Each Ni can play three main roles in the blockchain-based spatial crowdsourcing system. Wi, Mi, and Ri are the roles that each user i can play in the system. Ri submits REi to the system. The system specifies Uw for validation of REi. Uw votes to confirm or reject TREi that is located at LREi.
- IDw and IDr are the identifiers of each worker and requester. CoREi = (IDr, IDre, TREi, Tre, and LREi) and LREi = (Lati,re, Loni,re), which is compared with each LWi = (Lati,w, Loni,w).
- Ti is placed in Pent. We have many Bi in the designed blockchain, and each Bi has numerous Ti. Ti has unique IDt. CoREi is the content of each report, and CoTk is the content of each transaction in the blockchain-based spatial crowdsourcing system.
- PEYr is the reward of requesters when their reports are confirmed and PEYm is the miners’ reward after mining. PEYw is the reward of the workers in this system.
3.3. Research Assumptions and Threat Model
3.3.1. Research Assumptions
- Nodes cannot record transactions directly in the blockchain and do not have access to unconfirmed reports in the system.
- Submitting reports by the requesters and assigning tasks to the workers is carried out through a secured communication channel.
- Reward payments are transferred securely.
3.3.2. Threat Model
3.4. Design Goals
- Traditional systems perform all the processes of the spatial crowdsourcing system by a centralized authority, which causes risks such as single-point failure. In these systems, the selection of workers and the confirmation or rejection of tasks submitted by the requester are made by the central authority. In addition, in the case of data leakage, sensitive user information, including spatial information, task solutions, and user rewards, is abused. Besides, these systems use the central authority to determine the distribution of rewards and the confirmation of workers’ tasks that blockchain solves these problems.
- The existence of transparent participatory systems for the public and the ability to trace all system activities to improve performance is one of the blockchain-based crowdsourcing system purposes.
- Current data collection systems are inaccurate in data collection, which is more common in location-based systems. Improving the quality of these systems, in terms of accuracy, is another goal of this blockchain-based spatial crowdsourcing system, which is carried out with the confirmation or rejection of reports by workers.
- Despite the benefits of current distributed systems, they have drawbacks. Insufficient requester knowledge in creating provisions of contract can affect the worker’s confirmation or rejection of a task. In these systems, workers can only receive their rewards if they meet the requesters’ requirements. Besides, there is no evaluation for requesters, which results in an unfair evaluation of workers by requesters. In the proposed system, this problem is solved using the votes of the selected workers for each report.
- Better management and allocation of resources in different regions due to reduced incorrect information is another goal of the proposed system.
4. The Proposed Blockchain-Based Spatial Crowdsourcing System
4.1. Overview
4.2. Proposed System Implementation
4.2.1. Task Management
Registration
Task Submission
Task Assignment
| Algorithm 1. Task Assignment Algorithm. |
| Input Report; Users Output Workers 1: Get the report’s location 2: Calculate the region of the report 3: Get users’ location 4: Calculate the distance between users and the report 5: Get the combination of workers in each report 6: if UserDistance < ReportRegionDistance then 7: WorkersInRegion = Users; 8: if WorkersInRegion in WrokerCombinationInEachReport then 9: return False; 10: else 11: Workers = WorkersInRegion; 12: end if 13: return Workers 14: end if |
Task Confirmation
| Algorithm 2. Task Confirmation Algorithm. |
| Input Workers; Report Output Confirmed report 1: Request for confirmation to workers 2: Confirm or reject the report 3: if confirm = True then 4: return report confirmation; 5: end if 6: if NumberOfConfirmation > NumberOfWorkers/2 then 7: send report to blockchain; 8: return confirmed report; 9: end if |
4.2.2. Blockchain Structure
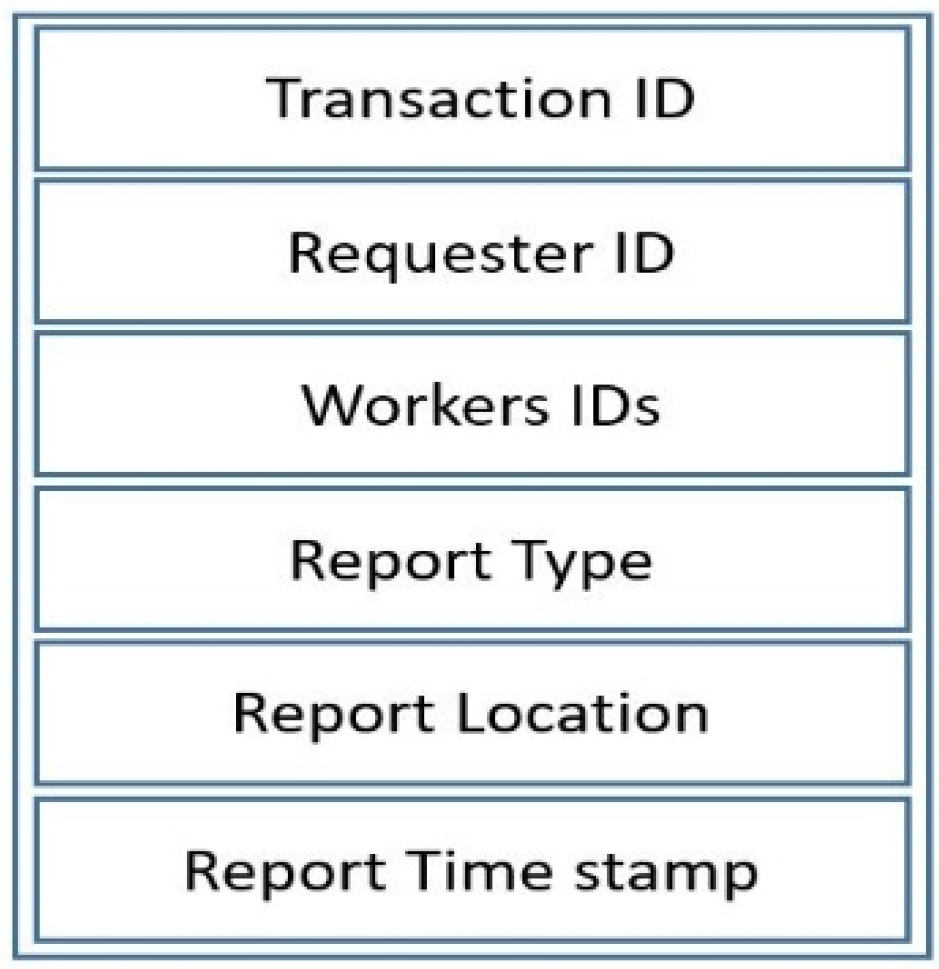
Transaction Structure
Incentive Mechanism
5. Security and Privacy Analysis
5.1. Security Analysis
5.1.1. Byzantine Fault Tolerance
5.1.2. Reputation-Based Attacks
5.1.3. Transaction Malleability
5.1.4. Time Jacking
5.1.5. Race Attack
5.1.6. DDOS Attack
5.1.7. Decentralization
5.1.8. No Single-Point of Failure
5.2. Privacy Analysis
Pseudonymity
6. Performance Evaluation
6.1. System Setting
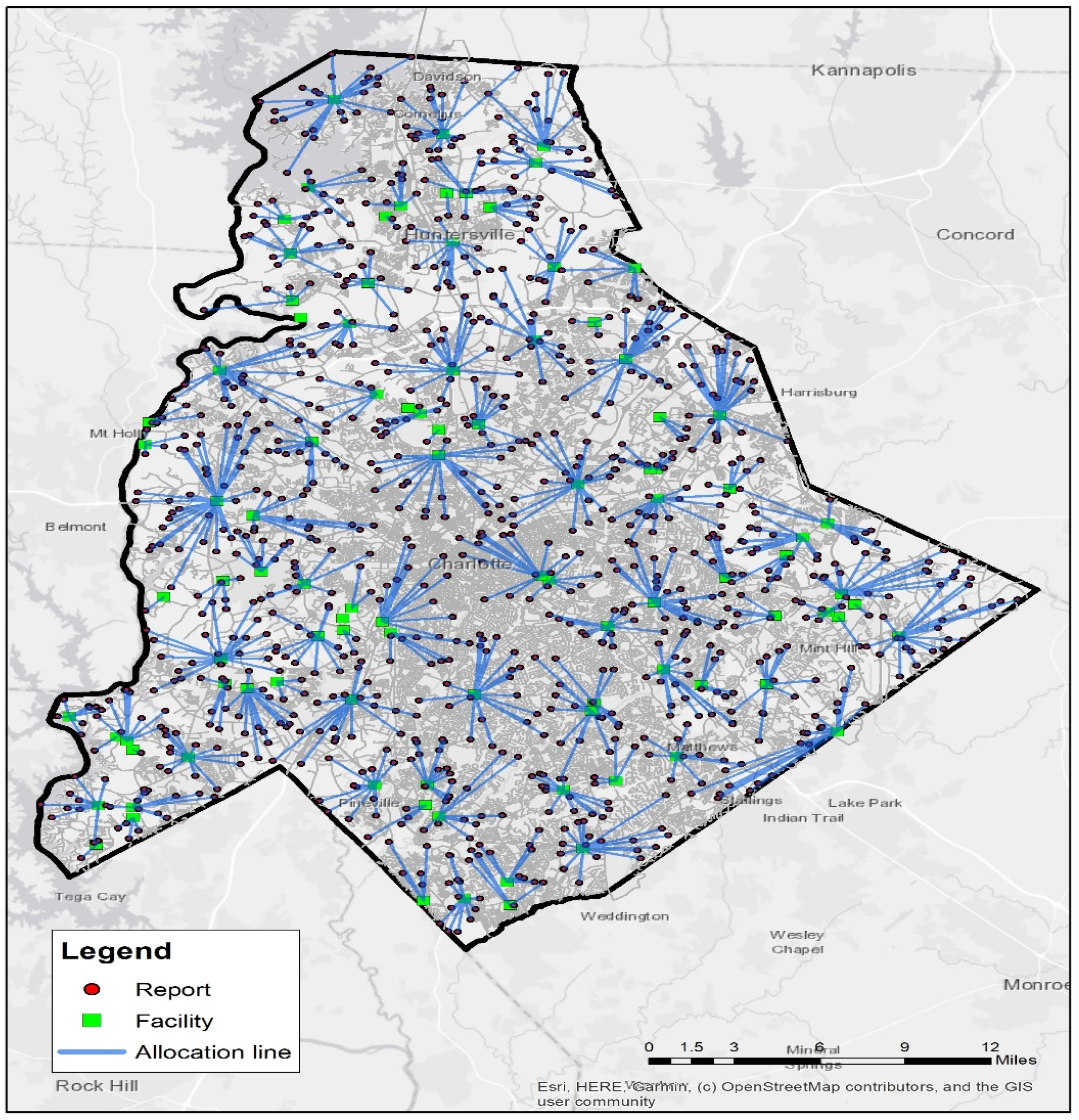
6.2. Resource Allocation
6.3. Comparison
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| Ni | The node i |
| IDr | The ID of requester |
| IDw | The ID of worker |
| IDre | The ID of report |
| IDt | The ID of transaction |
| Ti | The i-th transaction |
| Bi | The i-th block |
| REi | The i-th report |
| Ri | The i-th requester |
| Wi | The i-th worker |
| Mi | The i-th miner |
| Uw | A set of workers |
| Pent | Blockchain pending list |
| Tre | The time stamp of report |
| PEYr | The payment for each requester |
| PEYw | The payment for each worker |
| PEYm | The payment for mining each block |
| CoREi | The content of the i-th report |
| CoTk | The content of the k-th transaction |
| LRi | The location of the i-th requester |
| LREi | The location of the i-th report |
| LWi | The location of the i-th worker |
| Lati,p | The latitude of the i-th node with role p |
| Loni,p | The longitude of i-th node with role p |
| TREi | The type of the i-th report |
| θ | The central angle between two points on a sphere |
References
- Howe, J. The rise of crowdsourcing. Wired Mag. 2006, 14, 1–4. [Google Scholar]
- Kazemi, L.; Shahabi, C. Geocrowd: Enabling query answering with spatial crowdsourcing. In Proceedings of the 20th International Conference on Advances in Geographic Information Systems, Redondo Beach, CA, USA, 6–9 November 2012; pp. 189–198. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System; Decentralized Business Review: Seoul, Korea, 31 October 2008; p. 21260. [Google Scholar]
- Haferkorn, M.; Diaz, J.M.Q. Seasonality and interconnectivity within cryptocurrencies-an analysis on the basis of bitcoin, litecoin and namecoin. In International Workshop on Enterprise Applications and Services in the Finance Industry; Springer: Sydney, Australia, 12 December 2014; pp. 106–120. [Google Scholar]
- Nguyen, Q.K. Blockchain—A financial technology for future sustainable development. In Proceedings of the 2016 3rd International Conference on Green Technology and Sustainable Development (GTSD), Kaohsiung, Taiwan, 25 November 2016; pp. 51–54. [Google Scholar]
- Bhowmik, D.; Feng, T. The multimedia blockchain: A distributed and tamper-proof media transaction framework. In Proceedings of the 2017 22nd International Conference on Digital Signal Processing (DSP), London, UK, 23–25 August 2017; pp. 1–5. [Google Scholar]
- Dupont, Q. Blockchain Identities: Notational Technologies for Control and Management of Abstracted Entities. Metaphilosophy 2017, 48, 634–653. [Google Scholar] [CrossRef]
- Zikratov, I.; Kuzmin, A.; Akimenko, V.; Niculichev, V.; Yalansky, L. Ensuring data integrity using blockchain technology. In Proceedings of the 2017 20th Conference of Open Innovations Association (FRUCT), St-Petersburg, Russia, 3–7 April 2017; pp. 534–539. [Google Scholar]
- Ibba, S.; Pinna, A.; Seu, M.; Pani, F.E. CitySense: Blockchain-oriented smart cities. In Proceedings of the XP2017 Scientific Workshops, Cologne, Germany, 22–26 May 2017; pp. 1–5. [Google Scholar]
- Reijers, W.; O’Brolcháin, F.; Haynes, P. Governance in blockchain technologies & social contract theories. Ledger 2016, 1, 134–151. [Google Scholar]
- Fabiano, N. The Internet of Things ecosystem: The blockchain and privacy issues. The challenge for a global privacy standard. In Proceedings of the 2017 International Conference on Internet of Things for the Global Community (IoTGC), Funchal, Portugal, 10–13 July 2017; pp. 1–7. [Google Scholar]
- Kshetri, N. Can blockchain strengthen the internet of things? IT Prof. 2017, 19, 68–72. [Google Scholar] [CrossRef] [Green Version]
- Liao, C.-F.; Bao, S.-W.; Cheng, C.-J.; Chen, K. On design issues and architectural styles for blockchain-driven IoT services. In Proceedings of the 2017 IEEE International Conference on Consumer Electronics-Taiwan (ICCE-TW), Taipei, Taiwan, 12–14 June 2017; pp. 351–352. [Google Scholar]
- Juneja, A.; Marefat, M. Leveraging blockchain for retraining deep learning architecture in patient-specific arrhythmia classification. In Proceedings of the 2018 IEEE EMBS International Conference on Biomedical & Health Informatics (BHI), Las Vegas, NV, USA, 4–7 March 2018; pp. 393–397. [Google Scholar]
- Lee, S.H.; Yang, C.S. Fingernail analysis management system using microscopy sensor and blockchain technology. Int. J. Distrib. Sens. Netw. 2018, 14. [Google Scholar] [CrossRef] [Green Version]
- Patel, V. A framework for secure and decentralized sharing of medical imaging data via blockchain consensus. Health Inform. J. 2019, 25, 1398–1411. [Google Scholar] [CrossRef]
- Dorri, A.; Steger, M.; Kanhere, S.S.; Jurdak, R. Blockchain: A distributed solution to automotive security and privacy. IEEE Commun. Mag. 2017, 55, 119–125. [Google Scholar] [CrossRef] [Green Version]
- Politou, E.; Alepis, E.; Patsakis, C. Forgetting personal data and revoking consent under the GDPR: Challenges and proposed solutions. J. Cybersecur. 2018, 4, tyy001. [Google Scholar] [CrossRef]
- Bdiwi, R.; de Runz, C.; Faiz, S.; Cherif, A.A. Towards a new ubiquitous learning environment based on Blockchain technology. In Proceedings of the 2017 IEEE 17th International Conference on Advanced Learning Technologies (ICALT), Timisoara, Romania, 3–7 July 2017; pp. 101–102. [Google Scholar]
- Spearpoint, M. A proposed currency system for academic peer review payments using the blockchain technology. Publications 2017, 5, 19. [Google Scholar] [CrossRef]
- Turkanović, M.; Hölbl, M.; Košič, K.; Heričko, M.; Kamišalić, A. EduCTX: A blockchain-based higher education credit platform. IEEE Access 2018, 6, 5112–5127. [Google Scholar] [CrossRef]
- Corda. Available online: https://github.com/corda/corda (accessed on 25 September 2020).
- Ethereum. Available online: https://github.com/ethereum/go-ethereum (accessed on 4 August 2020).
- Fabric, H. Available online: https://github.com/hyperledger/fabric (accessed on 2 June 2021).
- Jia, B.; Zhou, T.; Li, W.; Liu, Z.; Zhang, J. A blockchain-based location privacy protection incentive mechanism in crowd sensing networks. Sensors 2018, 18, 3894. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Yang, M.; Zhu, T.; Liang, K.; Zhou, W.; Deng, R.H. A blockchain-based location privacy-preserving crowdsensing system. Future Gener. Comput. Syst. 2019, 94, 408–418. [Google Scholar] [CrossRef]
- Zhu, S.; Cai, Z.; Hu, H.; Li, Y.; Li, W. zkCrowd: A hybrid blockchain-based crowdsourcing platform. IEEE Trans. Ind. Inf. 2019, 16, 4196–4205. [Google Scholar] [CrossRef]
- Li, M.; Weng, J.; Yang, A.; Lu, W.; Zhang, Y.; Hou, L.; Liu, J.-N.; Xiang, Y.; Deng, R.H. Crowdbc: A blockchain-based decentralized framework for crowdsourcing. IEEE Trans. Parallel Distrib. Syst. 2018, 30, 1251–1266. [Google Scholar] [CrossRef]
- Muldoon, C.; O’Grady, M.J.; O’Hare, G.M. A survey of incentive engineering for crowdsourcing. Knowl. Eng. Rev. 2018, 33. [Google Scholar] [CrossRef]
- Gummidi, S.R.B.; Xie, X.; Pedersen, T.B. A survey of spatial crowdsourcing. ACM Trans. Database Syst. (TODS) 2019, 44, 1–46. [Google Scholar] [CrossRef]
- Chon, Y.; Lane, N.D.; Kim, Y.; Zhao, F.; Cha, H. Understanding the coverage and scalability of place-centric crowdsensing. In Proceedings of the 2013 ACM International Joint Conference on Pervasive and Ubiquitous Computing, Zurich, Switzerland, 8–12 September 2013; pp. 3–12. [Google Scholar]
- Kawajiri, R.; Shimosaka, M.; Kashima, H. Steered crowdsensing: Incentive design towards quality-oriented place-centric crowdsensing. In Proceedings of the 2014 ACM International Joint Conference on Pervasive and Ubiquitous Computing, Washington, DC, USA, 13–17 September 2014; pp. 691–701. [Google Scholar]
- Chatzimilioudis, G.; Konstantinidis, A.; Laoudias, C.; Zeinalipour-Yazti, D. Crowdsourcing with smartphones. IEEE Internet Comput. 2012, 16, 36–44. [Google Scholar] [CrossRef]
- Stevens, M.; D’Hondt, E. Crowdsourcing of pollution data using smartphones. In Proceedings of the Workshop on Ubiquitous Crowdsourcing, Beijing, China, 17–21 September 2011; pp. 1–4. [Google Scholar]
- Yan, T.; Marzilli, M.; Holmes, R.; Ganesan, D.; Corner, M. mCrowd: A platform for mobile crowdsourcing. In Proceedings of the 7th ACM Conference on Embedded Networked Sensor Systems, Berkeley, CA, USA, 4–6 November 2009; pp. 347–348. [Google Scholar]
- Alt, F.; Shirazi, A.S.; Schmidt, A.; Kramer, U.; Nawaz, Z. Location-based crowdsourcing: Extending crowdsourcing to the real world. In Proceedings of the 6th Nordic Conference on Human-Computer Interaction: Extending Boundaries, Reykjavik, Iceland, 16–20 October 2010; pp. 13–22. [Google Scholar]
- Benouaret, K.; Valliyur-Ramalingam, R.; Charoy, F. Answering complex location-based queries with crowdsourcing. In Proceedings of the 9th IEEE International Conference on Collaborative Computing: Networking, Applications and Worksharing, Austin, TX, USA, 20–23 October 2013; pp. 438–447. [Google Scholar]
- Ul Hassan, U.; Curry, E. Flag-verify-fix: Adaptive spatial crowdsourcing leveraging location-based social networks. In Proceedings of the 23rd SIGSPATIAL International Conference on Advances in Geographic Information Systems, Seattle, WA, USA, 3–6 November 2015; pp. 1–4. [Google Scholar]
- Väätäjä, H.; Vainio, T.; Sirkkunen, E. Location-based crowdsourcing of hyperlocal news: Dimensions of participation preferences. In Proceedings of the 17th ACM International Conference on Supporting Group Work, Sanibel Island, FL, USA, 27–31 October 2012; pp. 85–94. [Google Scholar]
- Alzantot, M.; Youssef, M. Crowdinside: Automatic construction of indoor floorplans. In Proceedings of the 20th International Conference on Advances in Geographic Information Systems, Redondo Beach, CA, USA, 6–9 November 2012; pp. 99–108. [Google Scholar]
- Cuong, T.T. CrowdRoute: A crowd-sourced routing algorithm in public transit networks. In Proceedings of the Second ACM SIGSPATIAL International Workshop on Crowdsourced and Volunteered Geographic Information, Orlando, FL, USA, 5 November 2013; pp. 9–14. [Google Scholar]
- Eivazy, H.; Malek, M.R. Developing a Multilevel Distribuiting Crowdsourcing System for Aiding and Rescuing to Overcome Widespread Crises. East. Eur. J. Enterp. Technol. 2020, 2, 104. [Google Scholar] [CrossRef]
- Eivazy, H.; Malek, M.R. Flood Management in Aqala through an Agent-Based Solution and Crowdsourcing Services in an Enterprise Geospatial Information System. ISPRS Int. J. Geo Inf. 2019, 8, 420. [Google Scholar] [CrossRef] [Green Version]
- Karam, R.; Melchiori, M. A crowdsourcing-based framework for improving geo-spatial open data. In Proceedings of the 2013 IEEE International Conference on Systems, Man, and Cybernetics, Washington, DC, USA, 13–16 October 2013; pp. 468–473. [Google Scholar]
- Pan, B.; Zheng, Y.; Wilkie, D.; Shahabi, C. Crowd sensing of traffic anomalies based on human mobility and social media. In Proceedings of the 21st ACM SIGSPATIAL International Conference on Advances in Geographic Information Systems, Orlando, FL, USA, 5–8 November 2013; pp. 344–353. [Google Scholar]
- Karam, R.; Melchiori, M. Improving geo-spatial linked data with the wisdom of the crowds. In Proceedings of the Joint EDBT/ICDT 2013 Workshops, Genoa, Italy, 18–22 March 2013; pp. 68–74. [Google Scholar]
- Besaleva, L.I.; Weaver, A.C. CrowdHelp: A crowdsourcing application for improving disaster management. In Proceedings of the 2013 IEEE Global Humanitarian Technology Conference (GHTC), Silicon Valley, CA, USA, 20–23 October 2013; pp. 185–190. [Google Scholar]
- Chen, X.; Wu, X.; Li, X.-Y.; Ji, X.; He, Y.; Liu, Y. Privacy-aware high-quality map generation with participatory sensing. IEEE Trans. Mob. Comput. 2015, 15, 719–732. [Google Scholar] [CrossRef]
- Cheng, Z.; Caverlee, J.; Barthwal, H.; Bachani, V. Who is the barbecue king of texas? A geo-spatial approach to finding local experts on twitter. In Proceedings of the 37th International ACM SIGIR Conference on Research & Development in Information Retrieval, Gold Coast, Australia, 6–11 July 2014; pp. 335–344. [Google Scholar]
- He, S.; Shin, D.-H.; Zhang, J.; Chen, J. Toward optimal allocation of location dependent tasks in crowdsensing. In Proceedings of the IEEE INFOCOM 2014-IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; pp. 745–753. [Google Scholar]
- Lenkei, Z. Crowdsourced Traffic Information in Traffic Management: Evaluation of Traffic Information from Waze. Master’s Thesis, KTH Stockholm, Stockholm, Sweden, 2018. [Google Scholar]
- Daniel, F.; Kucherbaev, P.; Cappiello, C.; Benatallah, B.; Allahbakhsh, M. Quality control in crowdsourcing: A survey of quality attributes, assessment techniques, and assurance actions. ACM Comput. Surv. (CSUR) 2018, 51, 1–40. [Google Scholar] [CrossRef] [Green Version]
- Mohammadi, N.; Malek, M. VGI and reference data correspondence based on location-orientation rotary descriptor and segment matching. Trans. GIS 2015, 19, 619–639. [Google Scholar] [CrossRef]
- Mohammadi, N.; Malek, M. Artificial intelligence-based solution to estimate the spatial accuracy of volunteered geographic data. J. Spat. Sci. 2015, 60, 119–135. [Google Scholar] [CrossRef]
- Liu, A.; Wang, W.; Shang, S.; Li, Q.; Zhang, X. Efficient task assignment in spatial crowdsourcing with worker and task privacy protection. GeoInformatica 2018, 22, 335–362. [Google Scholar] [CrossRef] [Green Version]
- To, H.; Ghinita, G.; Shahabi, C. PrivGeoCrowd: A toolbox for studying private spatial crowdsourcing. In Proceedings of the 2015 IEEE 31st International Conference on Data Engineering, Seoul, Korea, 13–17 April 2015; pp. 1404–1407. [Google Scholar]
- Chen, Z.; Fu, R.; Zhao, Z.; Liu, Z.; Xia, L.; Chen, L.; Cheng, P.; Cao, C.C.; Tong, Y.; Zhang, C.J. Gmission: A general spatial crowdsourcing platform. Proc. VLDB Endow. 2014, 7, 1629–1632. [Google Scholar] [CrossRef]
- Difallah, D.E.; Catasta, M.; Demartini, G.; Ipeirotis, P.G.; Cudré-Mauroux, P. The dynamics of micro-task crowdsourcing: The case of amazon mturk. In Proceedings of the 24th International Conference on World Wide Web, Florence, Italy, 18–22 May 2015; pp. 238–247. [Google Scholar]
- Li, Y.; Yiu, M.L.; Xu, W. Oriented online route recommendation for spatial crowdsourcing task workers. In Proceedings of the International Symposium on Spatial and Temporal Databases, HKUST, Hong Kong, China, 26–28 August 2015; pp. 137–156. [Google Scholar]
- To, H.; Shahabi, C.; Kazemi, L. A server-assigned spatial crowdsourcing framework. ACM Trans. Spat. Algorithms Syst. (TSAS) 2015, 1, 1–28. [Google Scholar] [CrossRef]
- Tran, L.; To, H.; Fan, L.; Shahabi, C. A real-time framework for task assignment in hyperlocal spatial crowdsourcing. ACM Trans. Intell. Syst. Technol. (TIST) 2018, 9, 1–26. [Google Scholar] [CrossRef] [Green Version]
- Zhang, S.; Wu, J.; Lu, S. Minimum makespan workload dissemination in DTNs: Making full utilization of computational surplus around. In Proceedings of the Fourteenth ACM International Symposium on Mobile Ad Hoc Networking and Computing, Bangalore, India, 29 July–1 August 2013; pp. 293–296. [Google Scholar]
- Huang, Q.; Cervone, G.; Jing, D.; Chang, C. DisasterMapper: A CyberGIS framework for disaster management using social media data. In Proceedings of the 4th International ACM SIGSPATIAL Workshop on Analytics for Big Geospatial Data, Bellevue WA, USA, 3–6 November 2015; pp. 1–6. [Google Scholar]
- Cheung, M.H.; Southwell, R.; Hou, F.; Huang, J. Distributed time-sensitive task selection in mobile crowdsensing. In Proceedings of the 16th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Hangzhou, China, 22–25 June 2015; pp. 157–166. [Google Scholar]
- Ast, F.; Sewrjugin, A. The Crowdjury, a Crowdsourced Justice System for the Collaboration Era. 2015. Available online: https://www.weusecoins.com/assets/pdf/library/The%20CrowdJury%20a%20Crowdsourced%20Justice%20System%20for%20the%20Collaboration%20Era.pdf (accessed on 11 November 2020).
- Jacynycz, V.; Calvo, A.; Hassan, S.; Sánchez-Ruiz, A.A. Betfunding: A distributed bounty-based crowdfunding platform over ethereum. In Proceedings of the 13th International Conference on Distributed Computing and Artificial Intelligence, Sevilla, Spain, 1–3 June 2016; pp. 403–411. [Google Scholar]
- Ropsten. Available online: https://github.com/ethereum/ropsten (accessed on 8 December 2020).
- Lu, Y.; Tang, Q.; Wang, G. Zebralancer: Private and anonymous crowdsourcing system atop open blockchain. In Proceedings of the 2018 IEEE 38th International Conference on Distributed Computing Systems (ICDCS), Vienna, Austria, 2–5 July 2018; pp. 853–865. [Google Scholar]
- Yuan, Y.; Wang, F.-Y. Towards blockchain-based intelligent transportation systems. In Proceedings of the 2016 IEEE 19th International Conference on Intelligent Transportation Systems (ITSC), Rio de Janeiro, Brazil, 1–4 November 2016; pp. 2663–2668. [Google Scholar]
- Mottur, P.A.; Whittaker, N.R. Vizsafe: The decentralized crowdsourcing safety network. In Proceedings of the 2018 IEEE International Smart Cities Conference (ISC2), Kansas City, MO, USA, 16–19 September 2018; pp. 1–6. [Google Scholar]
- Farnaghi, M. Blockchain, an enabling technology for transparent and accountable decentralized public participatory GIS. Cities 2020, 105, 102850. [Google Scholar] [CrossRef]
- Web3.js. Available online: https://github.com/ethereum/web3.js/ (accessed on 20 May 2021).
- Asmoredjo, K.; Hovanesyan, A.; To, S.; Wong Loi Sing, C. Decentralized Mortgage Market: An Open Market for Real-Estate Crowdsourcing. 2017. Available online: http://resolver.tudelft.nl/uuid:a20fc94f-a959-44ec-9c29-0cae8ad831ce (accessed on 11 August 2020).
- Wang, S.; Taha, A.F.; Wang, J. Blockchain-assisted crowdsourced energy systems. In Proceedings of the 2018 IEEE Power & Energy Society General Meeting (PESGM), Portland, OR, USA, 5–9 August 2018; pp. 1–5. [Google Scholar]
- Pinto, G.V.; Dias, J.P.; Ferreira, H.S. Blockchain-based PKI for crowdsourced IoT sensor information. In Proceedings of the International Conference on Soft Computing and Pattern Recognition, Online, 15–18 December 2020; pp. 248–257. [Google Scholar]
- Hu, S.; Hou, L.; Chen, G.; Weng, J.; Li, J. Reputation-based distributed knowledge sharing system in blockchain. In Proceedings of the 15th EAI International Conference on Mobile and Ubiquitous Systems: Computing, Networking and Services, New York, NY, USA, 5–7 November 2018; pp. 476–481. [Google Scholar]
- Sheng, D.; Xiao, M.; Liu, A.; Zou, X.; An, B.; Zhang, S. CPchain: A Copyright-Preserving Crowdsourcing Data Trading Framework Based on Blockchain. In Proceedings of the 2020 29th International Conference on Computer Communications and Networks (ICCCN), Honolulu, HI, USA, 3–6 August 2020; pp. 1–9. [Google Scholar]
- Ma, H.; Huang, E.X.; Lam, K.-Y. Blockchain-based mechanism for fine-grained authorization in data crowdsourcing. Future Gener. Comput. Syst. 2020, 106, 121–134. [Google Scholar] [CrossRef]
- Gao, L.; Cheng, T.; Gao, L. TSWCrowd: A Decentralized Task-Select-Worker Framework on Blockchain for Spatial Crowdsourcing. IEEE Access 2020, 8, 220682–220691. [Google Scholar] [CrossRef]
- Xia, H.; McKernan, B. Privacy in Crowdsourcing: A Review of the Threats and Challenges. Comput. Supported Coop. Work (CSCW) 2020, 29, 263–301. [Google Scholar] [CrossRef]
- Feng, W.; Yan, Z. MCS-Chain: Decentralized and trustworthy mobile crowdsourcing based on blockchain. Future Gener. Comput. Syst. 2019, 95, 649–666. [Google Scholar] [CrossRef]
- Shevchenko, N.; Chick, T.A.; O’Riordan, P.; Scanlon, T.P.; Woody, C. Threat Modeling: A Summary of Available Methods; Carnegie Mellon University: Pittsburgh, PA, USA, 2018. [Google Scholar]
- Robusto, C.C. The cosine-haversine formula. Am. Math. Mon. 1957, 64, 38–40. [Google Scholar] [CrossRef]
- CrowdFlower. Available online: https://appen.com/ (accessed on 15 April 2021).
- Ahmad, S.; Battle, A.; Malkani, Z.; Kamvar, S. The jabberwocky programming environment for structured social computing. In Proceedings of the 24th Annual ACM Symposium on User Interface Software and Technology, Santa Barbara, CA, USA, 16–19 October 2011; pp. 53–64. [Google Scholar]
- Upwork. Available online: https://www.upwork.com/ (accessed on 20 March 2021).
- Marquis, M.J.A.N.C. Essai sur L’application de L’analyse à la Probabilité des Décisions Rendues à la Pluralité des Voix; Cambridge University Press: Chelsea, UK, 1785. [Google Scholar]
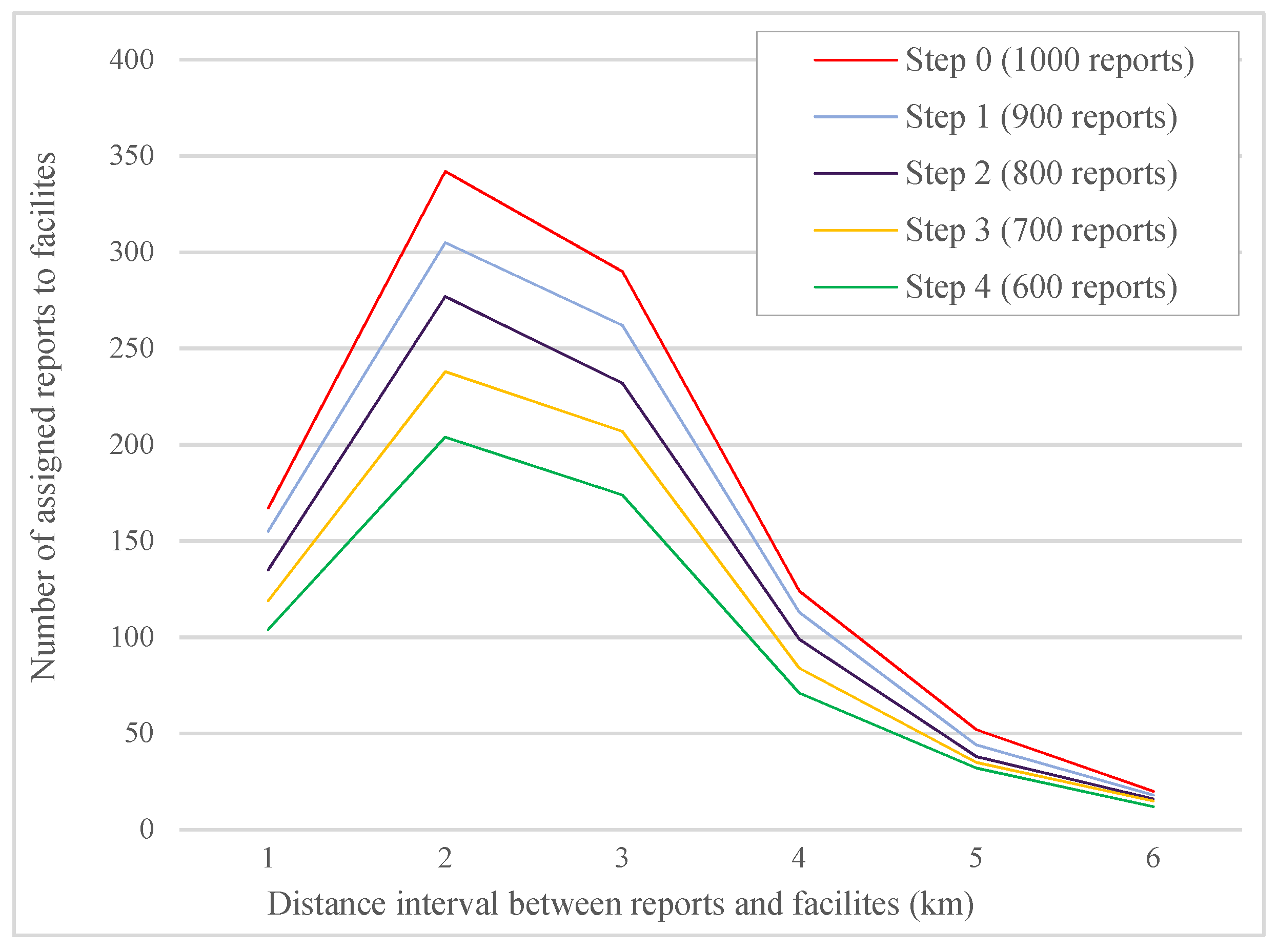

| 1000 Reports | 900 Reports | 800 Reports | 700 Reports | 600 Reports | |
|---|---|---|---|---|---|
| Total optimal time (min) | 1651.99 | 1573.74 | 1329.33 | 1238.65 | 1146.84 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kamali, M.; Malek, M.R.; Saeedi, S.; Liang, S. A Blockchain-Based Spatial Crowdsourcing System for Spatial Information Collection Using a Reward Distribution. Sensors 2021, 21, 5146. https://doi.org/10.3390/s21155146
Kamali M, Malek MR, Saeedi S, Liang S. A Blockchain-Based Spatial Crowdsourcing System for Spatial Information Collection Using a Reward Distribution. Sensors. 2021; 21(15):5146. https://doi.org/10.3390/s21155146
Chicago/Turabian StyleKamali, Masoud, Mohammad Reza Malek, Sara Saeedi, and Steve Liang. 2021. "A Blockchain-Based Spatial Crowdsourcing System for Spatial Information Collection Using a Reward Distribution" Sensors 21, no. 15: 5146. https://doi.org/10.3390/s21155146
APA StyleKamali, M., Malek, M. R., Saeedi, S., & Liang, S. (2021). A Blockchain-Based Spatial Crowdsourcing System for Spatial Information Collection Using a Reward Distribution. Sensors, 21(15), 5146. https://doi.org/10.3390/s21155146








