Abstract
This study proposes a set of novel random access protocols combining Packet Repetition (PR) schemes, such as Contention Resolution Diversity Slotted Aloha (CRDSA) and Irregular Repetition SA (IRSA), with Non Orthogonal Multiple Access (NOMA). Differently from previous NOMA/CRDSA and NOMA/IRSA proposals, this work analytically derives the energy levels considering two realistic elements: the residual interference due to imperfect Interference Cancellation (IC), and the presence of requirements on the power spent for the transmission. More precisely, the energy-limited scenario is based on the relationship between the average available energy and the selected code modulation pair, thus being of specific interest for the implementation of the Internet of Things (IoT) technology in forthcoming fifth-generation (5G) systems. Moreover, a theoretical model based on the density evolution method is developed and numerically validated by extensive simulations to evaluate the limiting throughput and to explore the actual performance of different NOMA/PR schemes in energy-constrained scenarios.
1. Introduction
The design of an effective technique for handling a large amount of uncoordinated traffic is still an open issue both for Fifth and Sixth Generation (5G/6G) communication systems, whose final aim is the provisioning of a pervasive space/terrestrial scenario implementing the Internet of Things (IoT) paradigm [1,2,3,4]. Existing networks manage the distributed load by adopting the well known Slotted Aloha (SA) protocol [5], for which several extensions have been proposed [6,7,8,9,10,11,12,13]. The SA performance may be in fact significantly improved by introducing energy diversity and Interference Cancellation (IC), whose combination leads to the Non-Orthogonal Multiple Access (NOMA) approach [6,7,8]. In a NOMA scheme, each user randomly selects an energy level by knowing the allowed ones, but not knowing those selected by the other users. In particular, the levels are chosen so that, if at most L users send their packets in a given slot using different levels, all the packets can be decoded.
Beside NOMA, another approach exploits IC, but relying on Packet Repetition (PR), that is, considering the transmission of a certain number M of replicas of a generated packet [9,10,11,12,13]. The M value may be fixed, as in the Contention Resolution Diversity SA (CRDSA) scheme [9], where , or may be a Random Variable (RV), as in the Irregular Repetition SA (IRSA) protocol [10]. The basic mechanism allowing packet diversity to properly operate relies on the possibility, still enabled by IC, that the packets transmitted in an uncollided slot may be successfully detected and then used to remove their replicas present in other slots. Even if the repetition-based solutions have been further extended to include priority [11], load control [12], and coding [13], the recent introduction of the IRSA algorithm in the DVB-RCS2 standard [14] has made this latter strategy a more immediate candidate for managing the random access procedure in 5G/6G networks.
Rather than being alternative, the NOMA and PR approaches are instead complementary. Accordingly, some proposals have explored the joint usage of energy and packet diversity [15], while specific investigations for the NOMA/CRDSA and NOMA/IRSA schemes have been considered [16,17,18]. These latter studies have proved the reciprocal benefits among NOMA and PR, but their joint applicability in a real network requires a further deepening of some practical aspects. The first one concerns the reception criterion, which usually relies on the simplified erasure model and not on the more realistic capture one [19,20,21]. The second aspect involves the assumption of perfect IC, which does not occur in an actual receiver [22,23,24,25,26], and leads to two main consequences, related to the need of increasing the energy separation to allow the decoding of packets using different levels. Firstly, the imperfect IC may reduce the achievable performance, which also depends on the available energy. In a PR scheme, the energy requirements are more severe, the number of packets that have been detected in other slots being unpredictable, but the residual energy of which may prevent the correct detection of packets in the imperfectly cleaned slots. As a second consequence, imperfect IC may prevent the complete successful delivery of the packets, which may be instead assumed in a PR scheme when the total load lies below a given threshold [9,10]. A further aspect that is often neglected in the analysis of NOMA-based protocols concerns the control of the power consumption [27,28,29], representing a relevant issue for 5G/6G networks, which are expected to be developed in agreement with the green communications paradigm.
In agreement with the above discussion, this paper presents the design of energy-constrained NOMA/CRDSA and NOMA/IRSA schemes able to sustain a desired level of imperfect IC. To this aim, a parameterized model is derived to evaluate the energy levels according to the PR scheme, the amount of residual interference, and the available average energy. To check the benefits of the conceived solution, a theoretical method, validated by extensive simulations, is developed to estimate the throughput and determine the conditions at which the limiting performance, obtained with perfect IC, is approached with imperfect IC. Besides, the proposed design is also tested in the presence of a Quadrature Phase-Shift Keying (QPSK) modulation and adopting a discretized set of channel code rates to consider the realistic situation in which a limited set of transmission modes is available. In particular, the key contributions of the presented study are:
- The development and evaluation of an energy design method for joint NOMA/PR schemes able to sustain a desired level of imperfect IC;
- The derivation of a parameterized model to assess the energy thresholds at which the capability of sustaining an imperfect IC improves significantly;
- The testing of the proposed design in the presence of a QPSK modulation by adopting a discretized set of channel code rates with the aim of verifying its usefulness in realistic scenarios.
2. System Model
Consider a distributed wireless network in which H contending users send packets to a common destination. The packet arrival is described by a Poisson process and the time domain is subdivided into Random Access Frames (RAFs) consisting of K slots of identical duration. In such a scenario, the input offered load G that should be managed by the network can be expressed (in packets per slot) as:
where is the activation probability, namely, the probability that a user generates a packet in a frame. The transmission in the RAF of each packet is carried out by adopting an SA-based random access scheme combining energy diversity (i.e., NOMA) with packet diversity (i.e., CRDSA, IRSA, …).
Consider first energy diversity. To this aim, identify by L the total number of available power levels and define as the energy used by the l-th () NOMA level normalized to the noise spectral density . Besides, assume, for generality, that the l-th level may be related to a channel code rate , thus enabling one to define the vector of the code rates associated to all the L levels. When a bi-dimensional modulation is chosen to transmit a packet, the corresponding vector of the selected rates (expressed in information bits/symbol) is given by . When the Shannon bound is assumed, the vector of the Signal-to-Noise Ratio (SNR) thresholds required to sustain the rates can be evaluated by inverting the Shannon bound itself, thus obtaining:
in which the element-wise power function is used to compact the notation. When, instead, a Quadrature Phase-Shift Keying (QPSK) modulation is adopted, the vector of the SNR thresholds can be derived by inverting the expression calculated in [30]. This yields:
where , , and are proper coefficients. Assume , so that, for a given energy level, only one successful packet reception is allowed.
Now, let us introduce, in addition to energy diversity, packet diversity. Accordingly, in each RAF, a generic user can send at most one packet that can be repeated M times. When just energy diversity is adopted, and hence packet diversity is not considered, we necessarily have . Otherwise, if packet diversity is introduced, replicas are employed when the CRDSA scheme is used, while, when the IRSA one is adopted, M becomes a RV having a Probability Density Function (PDF) that can be optimized through the density evolution method. In summary, when a packet must be transmitted, the source can in general select the M value, the relative energy levels, and the M slots of the RAF in which the M replicas have to be inserted.
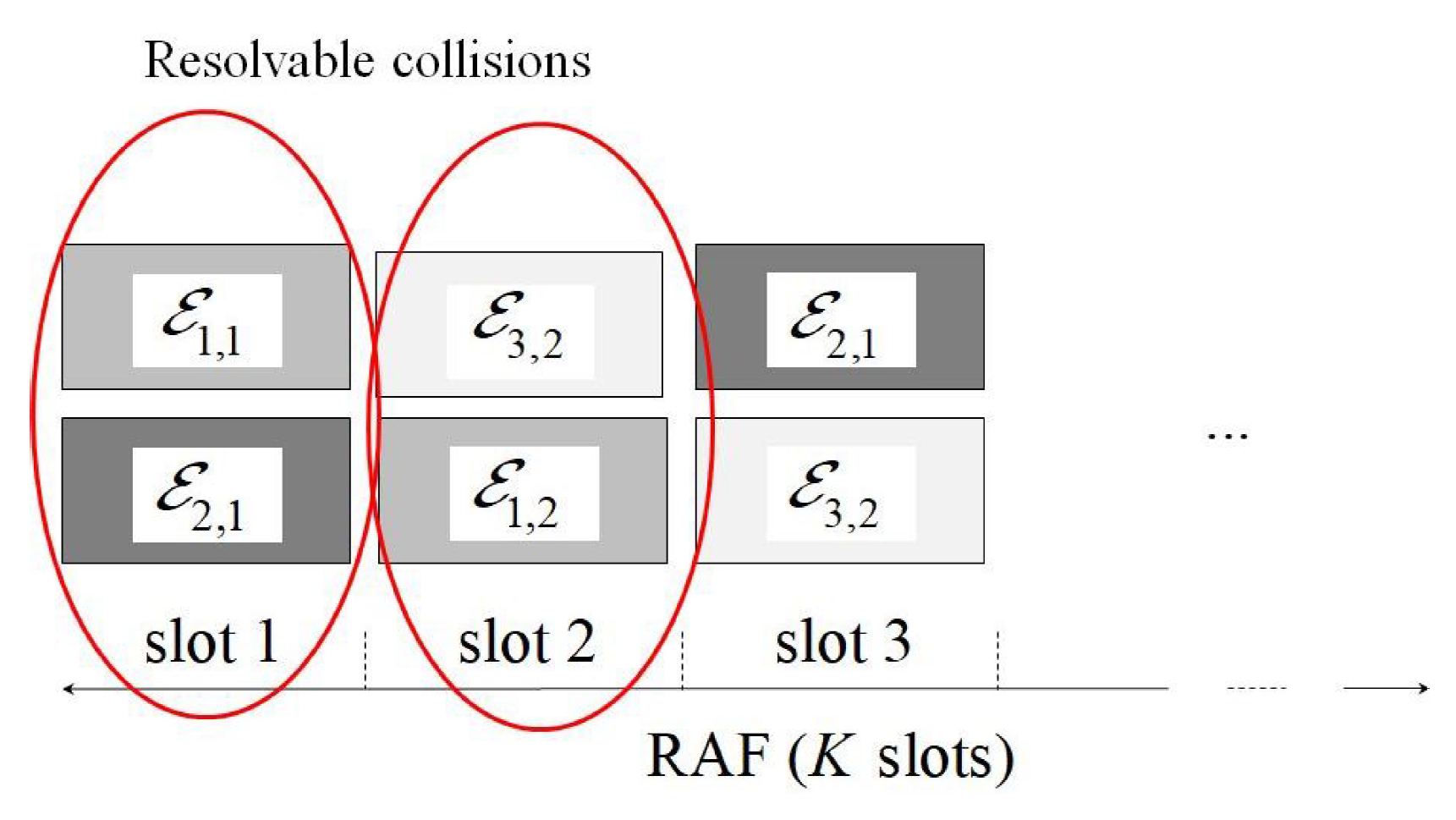
The main protocol operations can be inferred from Figure 1, in which represents the energy selected by the user i for its j-th attempt. More precisely, in the reported situation, user 1 chooses the energy level 1 for its first attempt, and the energy level 2 for the second one. We have a collision in the first and in the second slot, since both users choose the same energy level. In the third slot, instead, the transmitters choose different energy levels, thus, according to the NOMA rules, their packets can be successfully decoded by starting from the higher energy one. In this way, the contribution of users 1 and 3 may be (partly) removed from the other slots, hence allowing the correct detection of packet 2 as well by assuming that the remaining interference is within the design threshold. Observe that the adoption of repetition schemes has the advantage, from the user’s viewpoint, of guaranteeing the complete packet delivery up to a certain load, avoiding the need of further retransmissions. This has a positive impact both on system complexity and delay. The joint adoption of repetitions and power diversity allows one to increment the sustainable load. However, the adoption of power diversity may lead to a significant increase of energy consumption, which makes also more critical the impact of imperfect IC on the performance. Therefore, a suitable energy design is required to achieve the joint benefits of repetitions and power diversity, without negative effects on energy consumption and performance.
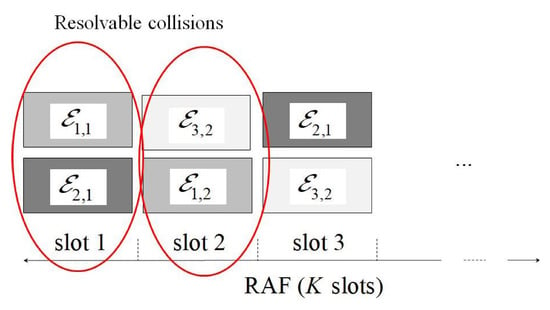
Figure 1.
Protocol operation example.
3. Energy Level Design
When energy and packet diversity are jointly employed, the design of the energy levels should be extended with respect to the typical one adopted for the pure NOMA scheme [6]. Moreover, within this design, two further aspects should be carefully considered. The first one concerns the power consumption, since modern communication systems cannot neglect the importance of energy saving. The addressing of such a problem leads to a different perspective in imposing the mathematical constraints on the energy levels, thus moving from the usual requirement on the maximum peak energy [18] to a more suitable one on the average spent energy. For a proper design of the access algorithm, it is hence useful to rely on the average SNR referred to a packet, which can be expressed as:
where denotes the average number of replicas of a packet and:
represents the average SNR referred to a single replica. The main scope of this paper is to investigate the effects of the available average energy assuming an equally likely energy distribution [8].
The second aspect that should be taken into account in the energy design of a joint NOMA/PR scheme involves the nonidealities of the decoding IC-based process, and in particular the residual interference actually present in a practical receiver due to imperfect cancellation. To ensure the proper algorithm operations in this realistic situation, thus accounting for imperfect IC, limited average energy, and joint power/packet diversity, we propose an energy level design in which the following condition must be met:
where represents the fraction of the interference remaining after IC ( is not considered since it would imply no IC), denotes the number of sustainable cancelled transmissions per energy level derived from packet diversity, and identifies the number of further highest energy sustainable cancelled transmissions. This latter parameter acts as a margin that a designer can introduce to increase the robustness of the decoding process. The condition in (6), which must hold in the slot occupied by a replica to enable its decoding, accounts for the lower (not cancelled) energy levels, and for the residual interference (terms within the round bracket) due to the other (cancelled) replicas deriving from repetition schemes (replicas that are correctly decoded in other slots), and to the higher (cancelled) energy levels in the same slot. By assuming , a large number of further lower energy cancelled transmissions deriving from repetitions may be sustained, if less than highest energy cancelled transmissions are present. Note that (6) can be applied also to basic NOMA with imperfect IC, for which , and, furthermore, to basic NOMA with perfect IC, for which . From condition (6), the limiting normalized energies may be determined as:
and so on for the other lower levels. Under the equally likely energy hypothesis, the above equations may be suitably manipulated to evaluate each normalized level, hence obtaining, after some algebra, the normalized energies in a compact form as:
where:
with:
in which the index is introduced for mathematical purposes. Note that, being , we have for . As a further remark regarding this derivation, it is worth observing that (9) represents a general purpose relationship among energies, in which depends on and only, while and , respectively, depend also on and . Actually, a simplified energy design might be given by:
in which the constant can be determined once the energy probabilities, the transmission scheme, and the average SNR are set. However, the adoption of (9) allows one to relate the energy to the sustainable cancelled patterns, and is, therefore, much more suitable for assessing the performance achievable by a joint NOMA/PR scheme.
In a conventional system, the design parameters are: (the fraction of interference remaining after IC, dependent on the quality of the receiver), (the selected rates), (the number of cancelled interferers per energy level deriving from repetitions that must be sustained), and (the number of further highest energy cancelled interferers deriving from repetitions that must be sustained). Therefore, after the evaluation of by (11), one has to derive , which is necessary to evaluate in (10). This latter operation can be carried out by substituting (9) and (10) in (4)–(5), and then by solving for , thus obtaining:
which allows the calculation of by (10) and the subsequent evaluation of the normalized energies by (9). If all levels are associated to the same modulation and code rate, we have and hence for . By consequence, from (14), we obtain:
which may be usefully inverted as:
The adoption of an identical value simplifies the expressions in (12) and (16), which, by (11) and (18), respectively, become:
and:
Concerning this latter formula, one may observe that, since must be positive and is positive and lower than one, the quantity within the brace must be not negative. This provides the following limiting condition on :
which determines a limit on the maximum IC capability and, in turn, on the throughput.
In some application scenarios characterized by power saving constraints, the average energy, and hence the average SNR, may be considered as a given parameter, in place of the one adopted in conventional systems based on the rate to support. In these energy-constrained random access networks, (20) may be exploited to evaluate the required value, given and the other design parameters , , and . To this aim, (20) can be manipulated to derive a polynomial equation in the unknown as:
where:
In general, this equation must be solved numerically, but, in many common situations, such as for or , closed-form expressions may be derived. This significantly limits the computational complexity of the design process, making simpler the overall implementation of the derived joint NOMA/PR schemes. Once the value is obtained (analytically or numerically), one may calculate the corresponding rate by (18). For example, when , one can easily obtain .
In summary, the main characteristic of the proposed energy design strategy for NOMA/PR schemes consists in enabling the evaluation of the energy levels given the required rates, when power saving is not of concern, or, conversely, the calculation of the rates given the energy levels for power-limited systems.
4. Throughput Evaluation
The throughput achievable by a joint power/packet diversity algorithm may be theoretically determined moving from the density evolution method [10]. To this aim, recalling the assumed Poisson arrival process, firstly evaluate the probability of generating i packets as a function of the input offered load G as:
where the term takes into account that, in the presence of a PR scheme, each generated packet produces, on average, replicas. Now, to apply density evolution, consider the relationship between the unsolved contentions and the unknown packets (see [10] for the detailed derivation):
in which q denotes the probability that a replica is still unknown at the certain stage of the IC process, is the PDF of M, and:
represents the probability that a contention in a generic slot is still unresolved. In particular, in (26), identifies the probability of successfully decoding a replica in a slot with i contending ones, t of which have been canceled because they have been correctly decoded in other slots. In ideal conditions, that is, with perfect IC (), we have , whose corresponding approximate expression has been derived in ([27], eq. 18). In such a case, the maximum throughput may be obtained by determining the maximum G value for which the inequality becomes satisfied for . Observe that, in an asymptotic scenario, that is, for , all the packets are successfully delivered if the throughput is lower than . This condition may be reasonably approached when RAFs composed by a sufficiently large number of slots are selected.
In unideal conditions, that is, with imperfect IC (), may be determined as a function of and for a given set of parameters. For example, for , being this limit the guaranteed IC capability. In a more general condition, we have , being the main performance reduction due to the replicas associated to the lower energy levels, which cannot sustain the partially cancelled energy of the replicas associated to the higher energy levels. For the developed energy design, the values may be exhaustively evaluated. However, with partial IC, the density evolution approach cannot be directly used as in [10] to assess the limiting performance. In fact, the full packet delivery is not feasible, given that the density evolution analysis relays on the hypothesis , which cannot be achieved for i values exceeding a threshold dependent on the parameter set. Hence, the condition cannot be guaranteed for very low q values. Actually, the achievable throughput depends on energy, and, as a consequence, on and for a given scenario (access algorithm, value, number of energy levels). A general treatise would require a modification of the density evolution approach. This task is out of the scope of this paper, which focuses on the energy requirements that allow the access algorithm to approach its limiting performance, thus ensuring the almost complete delivery of the packets within the maximum throughput for sufficiently large K values. To deal with this specific problem one may exploit the fact that, by progressively increasing the and values, the limiting throughput may be approached when the condition is guaranteed for with a sufficiently low value, which in this study is selected equal to . Note that this latter achievement is guaranteed for , that is, for all residual fractions of interference lower than the design value . This implies that, if the receiver has IC capabilities better than those assumed during the design, it can sustain a certain fluctuation of the energy level, deriving, for example, from fading.
The conceived throughput estimation is applied to the NOMA/CRDSA and NOMA/IRSA algorithms, which are of main interest because of the implementation of the CRDSA and IRSA schemes in last generation satellite systems [14]. In particular, for the NOMA/CRDSA algorithm, we simply have and for [9], since M is deterministic. In the NOMA/IRSA case, instead, M is a RV, whose PDF have been determined in [18] assuming . For this protocol, named NOMA/IRSA-8 from now on, the energy requirements are very severe and the limiting performance may be approached just using a very large number of slots. Hence, in this paper, we also adopt a simpler version characterized by , named NOMA/IRSA-3, which allows a more quick identification of the energy required to approach . Table 1 summarizes the parameters adopted for these two schemes.

Table 1.
PDF of the number M of replicas as a function of the number L of energy levels for the considered NOMA/IRSA schemes.
5. Results
As a first set of results, Table 2 reports the achievable limiting throughput and the required average SNR in the presence of perfect IC () for the three algorithms under investigation (NOMA/CRDSA, NOMA/IRSA-3, NOMA/IRSA-8). The values are obtained assuming information bits per symbol, using the Shannon model (for which also ), and selecting the parameters in Table 1. In particular, Table 2 shows that, for a given scheme, the increase of the number of levels provides, as expected, a higher throughput, but at the cost of an increased average energy (higher power consumption). Throughput improvements may be also obtained, for a given L value, by increasing the level of packet diversity, still spending a higher energy.

Table 2.
Limiting throughput and required SNR as a function of the number L of energy levels in ideal conditions for information bits/symbol and assuming the Shannon bound.
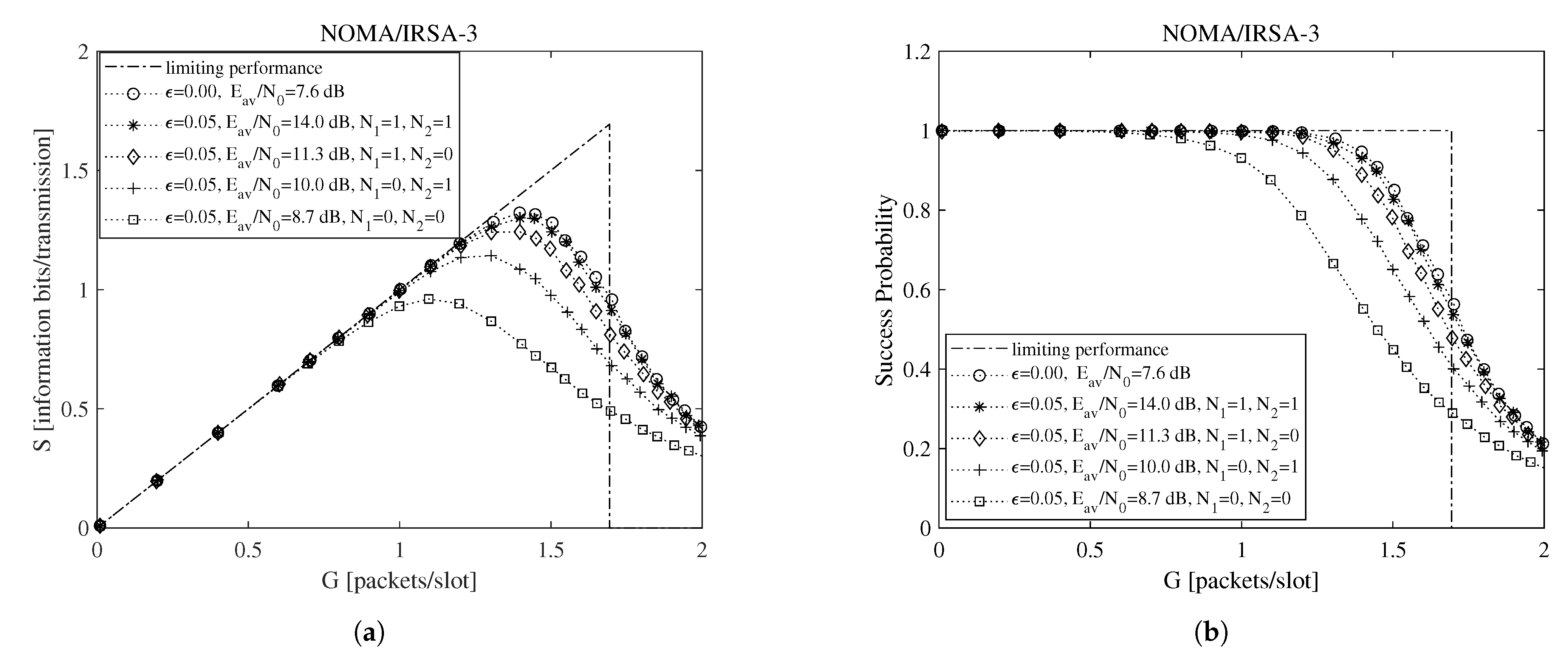
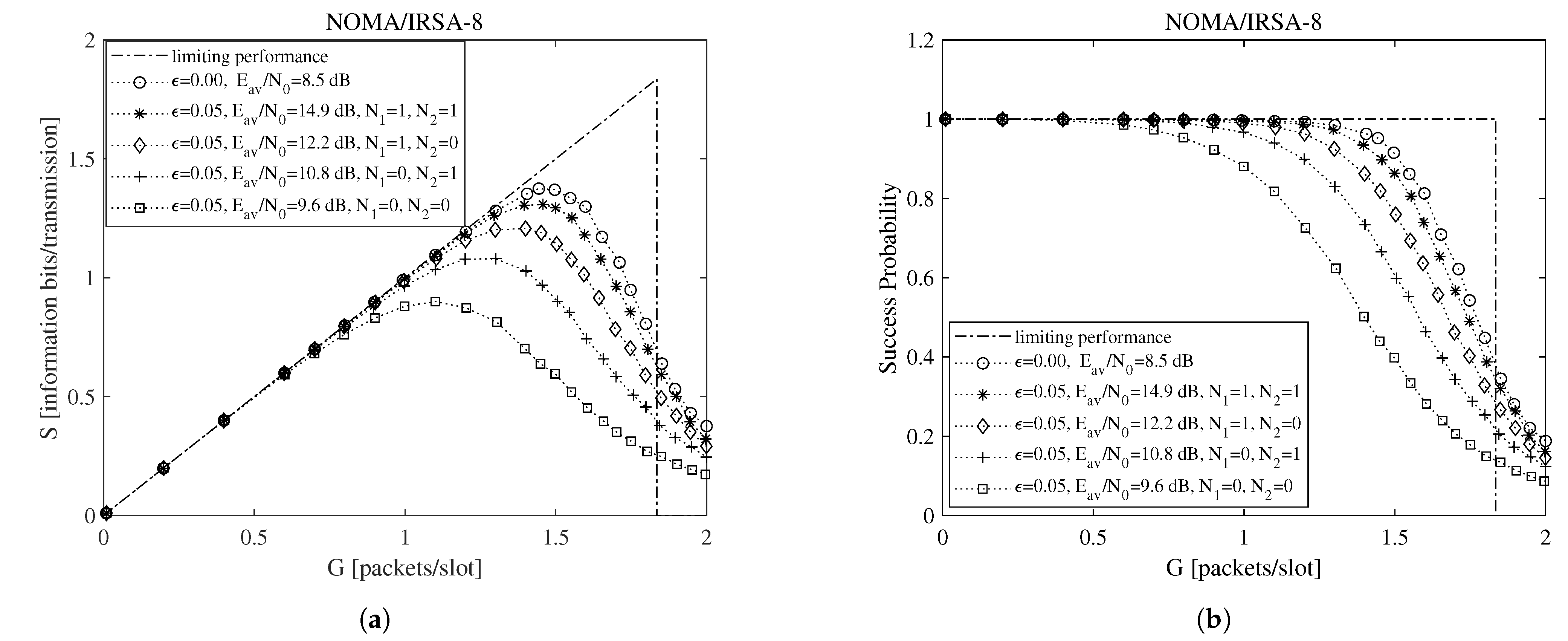
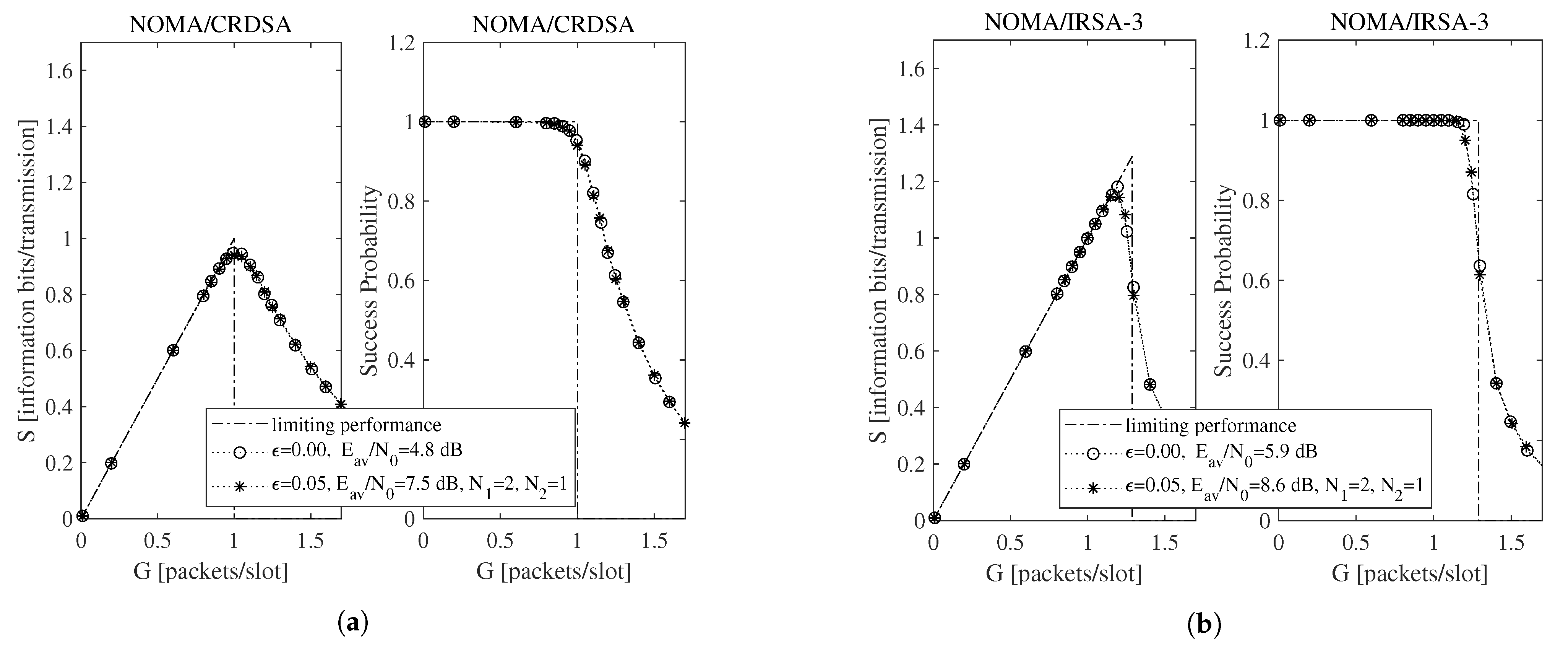
To begin the exploration of the performance under imperfect IC when the Shannon bound is adopted, consider Figure 2 and Figure 3, which report, for , , , and information bits per symbol, the throughput for the NOMA/IRSA-3 (Figure 2a) and the NOMA/IRSA-8 (Figure 3a) schemes, together with the corresponding success probabilities (Figure 2b and Figure 3b).
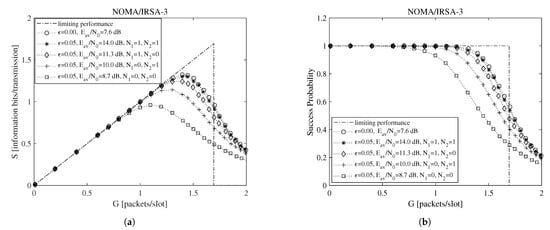
Figure 2.
Performance as a function of the channel load for NOMA/IRSA-3 with , , and information bits per symbol: (a) throughput, (b) success probability.
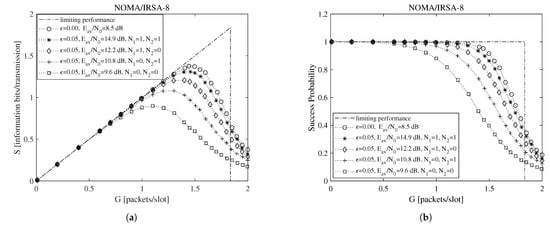
Figure 3.
Performance as a function of the channel load for NOMA/IRSA-8 with , , and information bits per symbol: (a) throughput, (b) success probability.
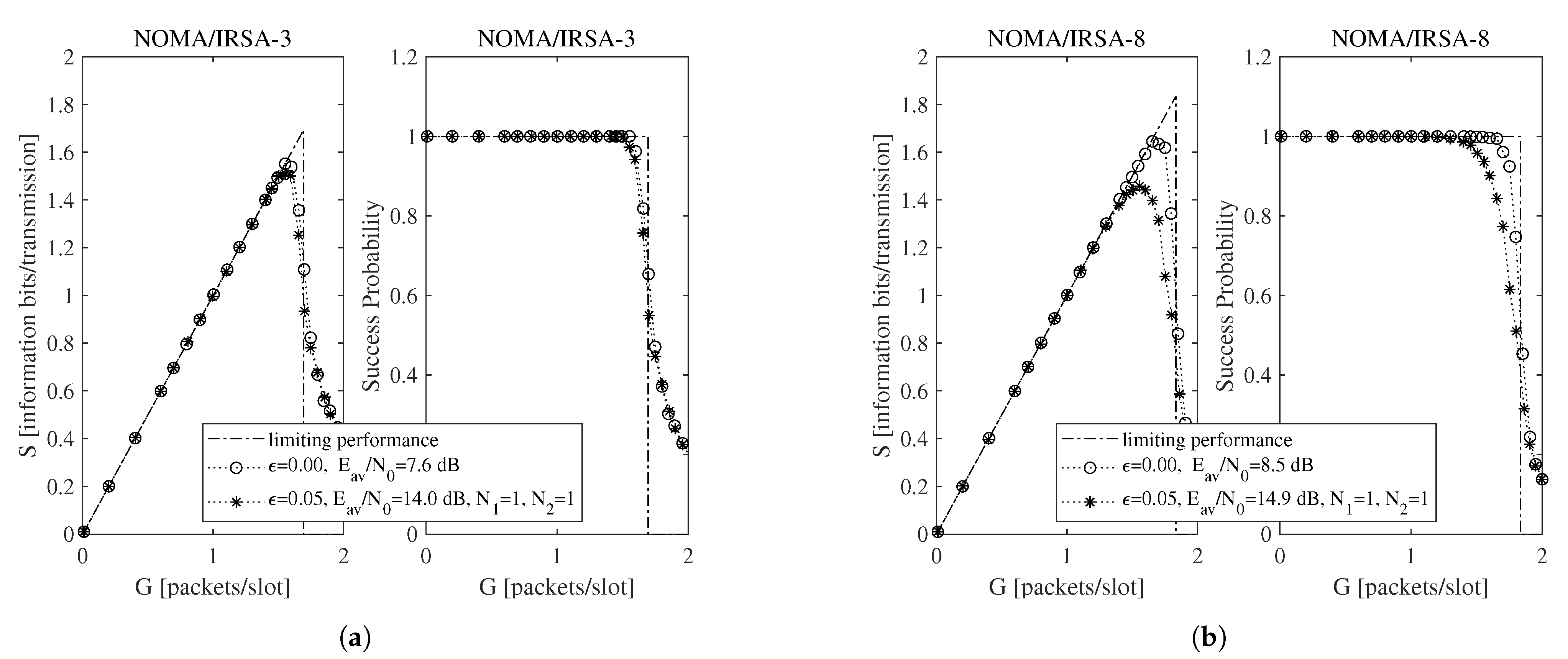
Beside the analytical plot representing the limiting performance (dash-dotted line) and the perfect IC case (dotted line with circle marker), each figure shows a set of simulated curves derived by selecting different and values. Both analysis and simulations are implemented in Matlab. In particular, the simulations are carried out by generating the Poisson traffic for a given load G, assigning to each packet the proper M and energy values, and then randomly locating the replicas in the RAF. Each simulated point is calculated by averaging the results obtained from = 10,000 RAF realizations. From these figures one may observe that, for NOMA/IRSA-3, the limiting performance is approached using and , while, for NOMA/IRSA-8, higher values would be required. Besides, for a given pair, the performance of NOMA/IRSA-8 is comparable to that of NOMA/IRSA-3, despite the higher energy level and the higher limiting performance of the first scheme. Similar arguments hold also for , that is, when longer RAFs are considered, as it may be noticed from Figure 4 and Figure 5.
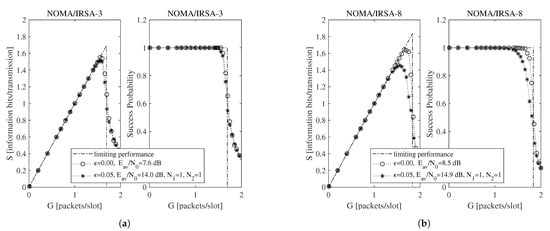
Figure 4.
Throughput and success probability as a function of the channel load for , , and information bits per symbol: (a) NOMA/IRSA-3, (b) NOMA/IRSA-8.
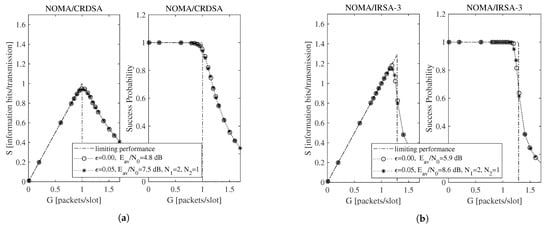
Figure 5.
Throughput and success probability as a function of the channel load for , , and information bits per symbol: (a) NOMA/CRDSA, (b) NOMA/IRSA-3.
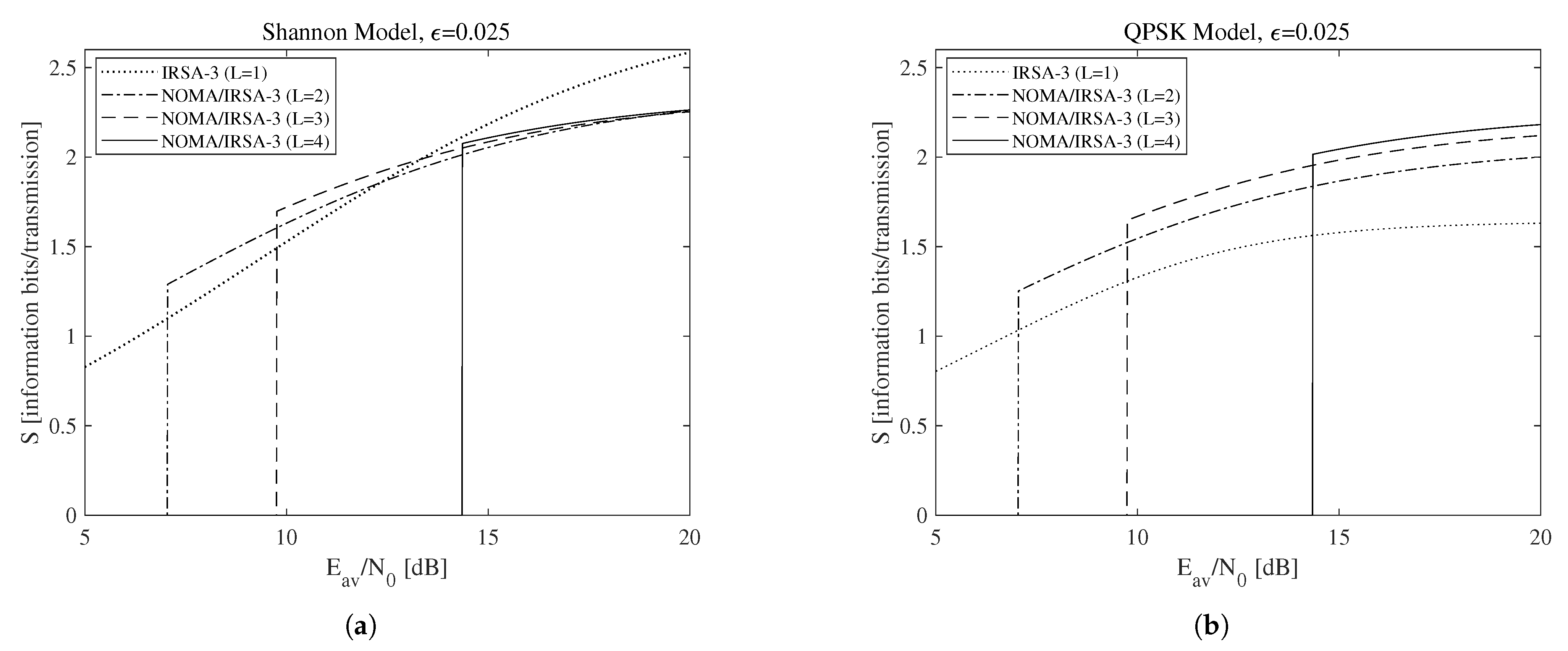
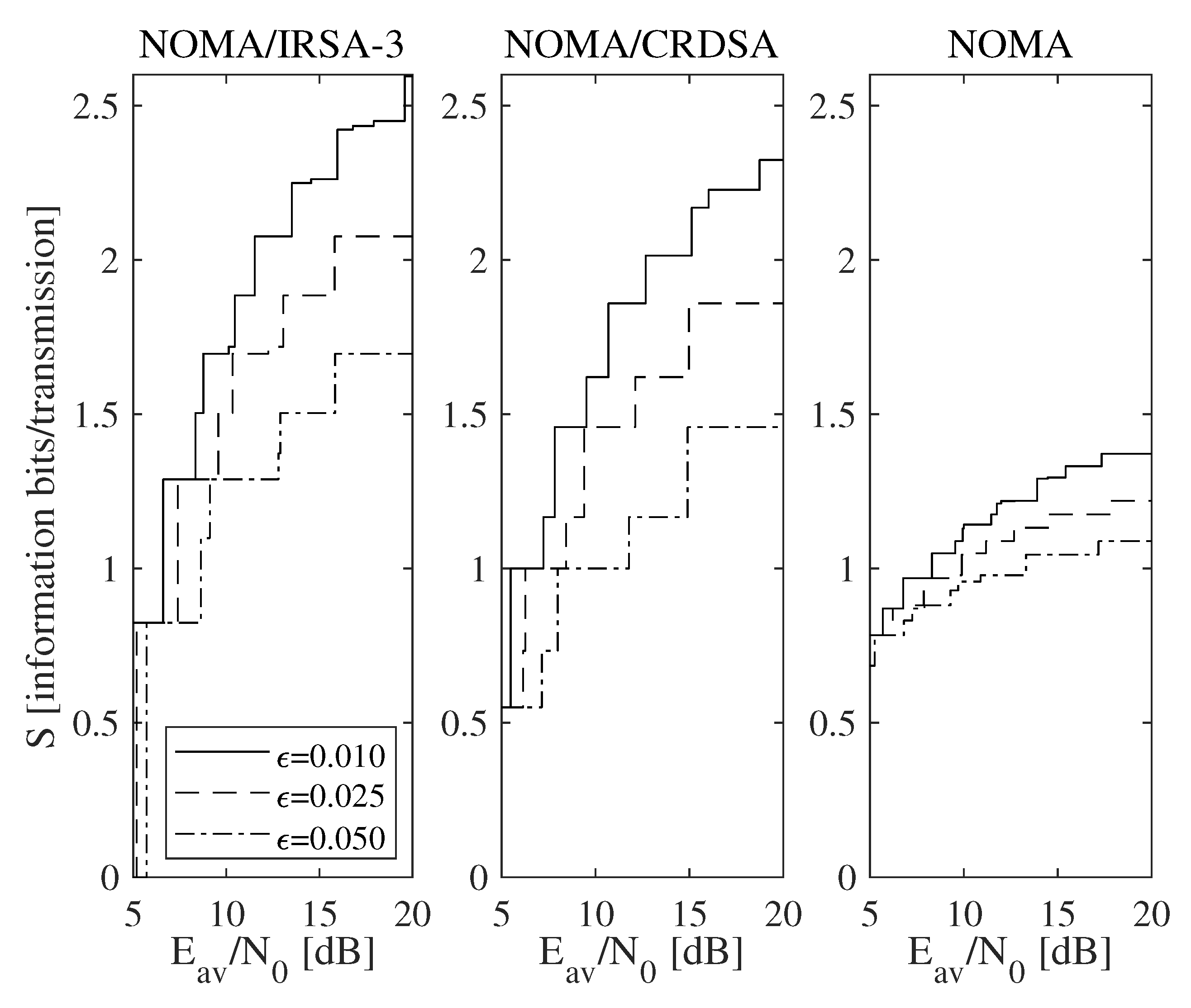
According to the above discussion, let us now focus on the relationship between the sustainable rate and the available energy. More precisely, consider the minimum threshold , achievable by selecting the minimum average SNR , and the maximum sustainable threshold , obtainable from (22) and (18) when and hence . These parameters, together with the maximum sustainable rate , derived by (2) for the Shannon bound and by (3) for the QPSK modulation, are reported in Table 3 for each of the analyzed scenarios, that is, when the access algorithm and the parameters L, , , and are identified. In this table, the pairs are properly selected according to the method explained in the previous section, which allows the analyzed algorithms to approach for a sufficiently large K value. It is worth to observe, firstly, that and do not depend from the chosen modulation bound, and, secondly, that all the values in the table have been calculated in closed-form, since all the involved scenarios are characterized by and/or , thus enabling to analytically solve (22). Among the values in the table, let us start by considering those corresponding to for NOMA/IRSA-3 and without constraints on the code rate and on the modulation complexity, hence allowing the usage of all the rates complying with . The throughput achievable in these scenarios for different values of L is reported in Figure 6a for the Shannon bound and in Figure 6b for the QPSK modulation. More precisely, Figure 6a interestingly reveals that the simple IRSA-3 algorithm (), in which NOMA is not adopted, may anyway achieve a satisfactory performance, close or, in some cases, even better than that provided by the combined schemes. This is due to its low energy requirements and to the possibility of using complex modulations, which are implicitly available when the Shannon bound is assumed. A realistic setting involving the QPSK modulation () modifies the previous conclusion, putting into evidence that the increase of the number of energy levels enables the NOMA/IRSA-3 scheme to better exploit its higher sustainable load.

Table 3.
Relationship between energy requirement and sustainable rate for different scenarios.
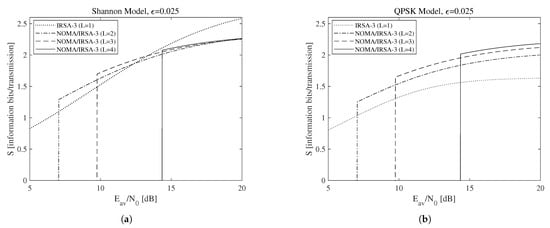
Figure 6.
Throughput as a function of the available average SNR for : (a) Shannon bound, (b) QPSK modulation.
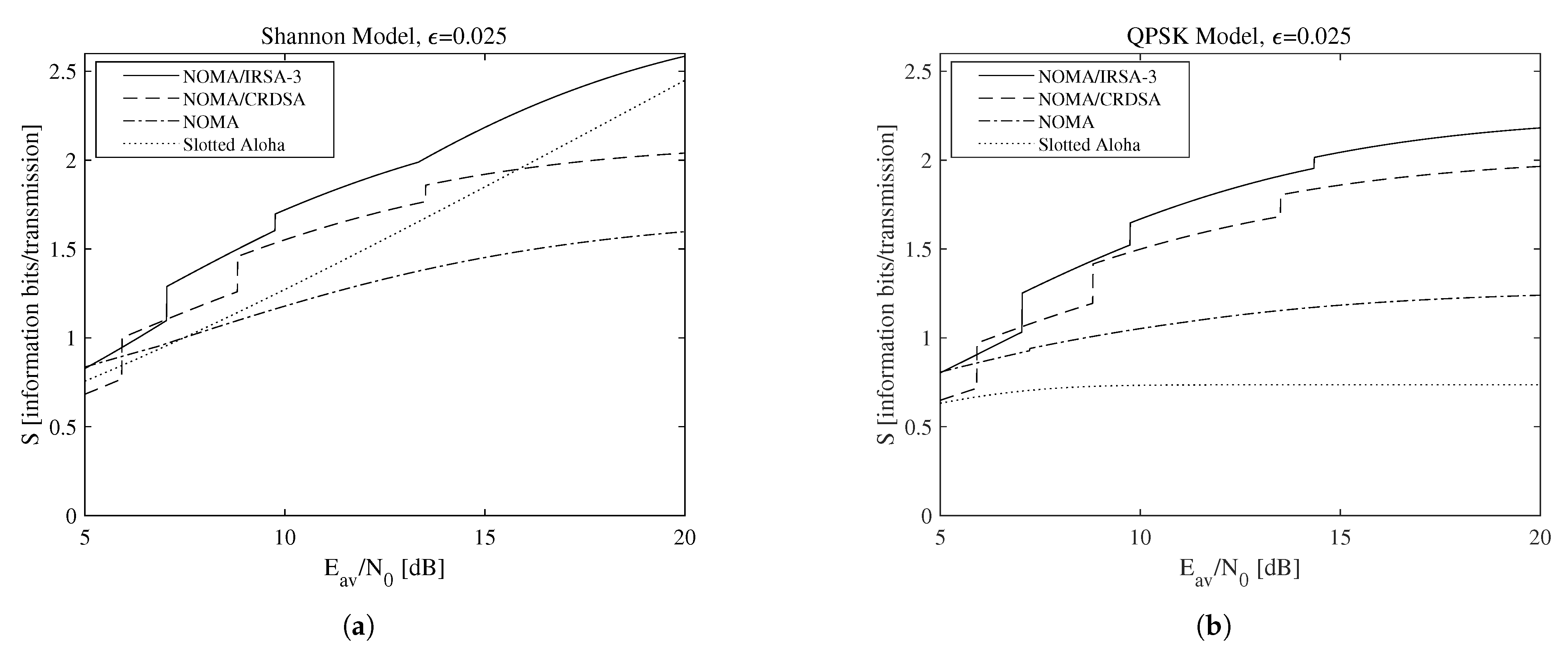
A more general set of results is reported in Figure 7, which shows the achievable throughput, that is, the maximum throughput calculated over all the available L values for NOMA/IRSA-3, NOMA/CRDSA, pure NOMA, and SA when the Shannon bound (Figure 7a) and the QPSK modulation (Figure 7b) are adopted. The performance of the pure NOMA algorithm ( and ) is shown separately from that of the SA one (), since the latter does not use IC and, by consequence, does not depend on . When the Shannon bound is adopted (i.e., ), thus no limitations on the code rate and on the modulation complexity are present, the simple SA, despite its low sustainable rate, is able to achieve an interesting performance by exploiting its very low energy requirements. When QPSK modulation is instead assumed, the repetition schemes perform significantly better and are definitely preferable. However, despite the specific modulation model, the algorithms adopting repetition schemes, that is, NOMA/IRSA and NOMA/CRDSA (even in their base version with ), allow the transmitters to deliver all their packets in a sufficiently long RAF, while pure NOMA (including SA) necessarily requires retransmissions in successive RAFs to recover the failed attempts.
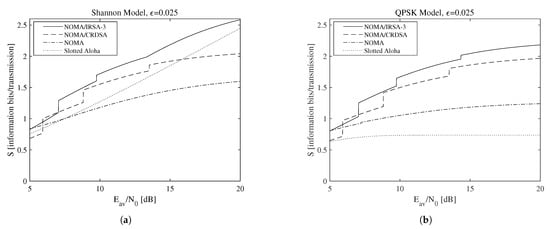
Figure 7.
Maximum throughput as a function of the available average SNR for : (a) Shannon bound, (b) QPSK modulation.
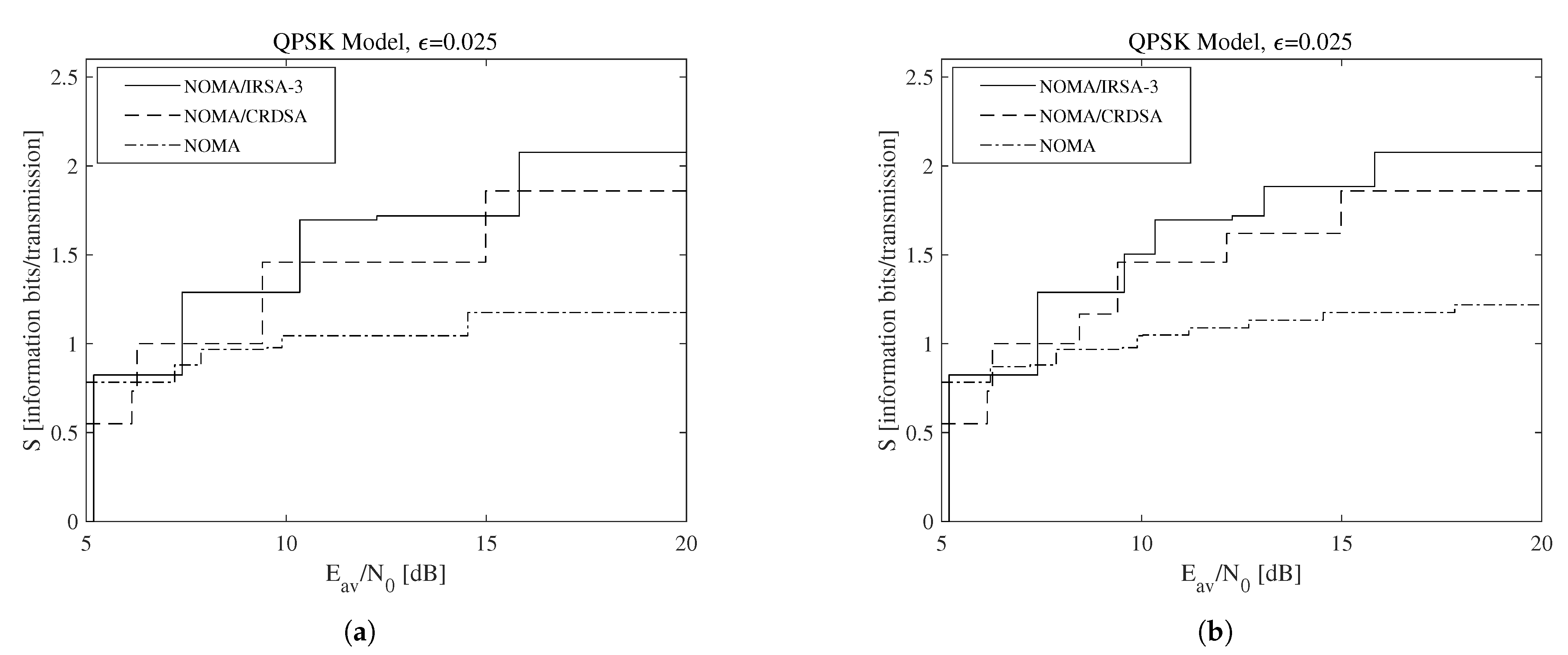
To make the presented discussion more adherent to a practical context, consider now that the code rate for the l-th energy level can be selected in a finite set , whose corresponding average SNRs referred to a single replica may be determined by (16). The resulting achievable throughput is reported in Figure 8, which is obtained for when the QPSK modulation is used. In particular, Figure 8a refers to the scenario in which a single code rate is adopted by all the energy levels (i.e., for ), while Figure 8b refers to the scenario in which a double code rate is allowed, since a higher code rate may be used by the lowest energy level for compensation (i.e., for and ). Both subfigures reveal that, in a discrete-rate situation, the algorithms that offer the best performance are influenced by the available energy. Besides, observe that all the results in Figure 8 are bounded by those in Figure 7b. A more specific view, referred to the NOMA/IRSA-3 scheme, is available in Table 4, which lists a suitable combination of rates and the corresponding limiting performance. Finally, a complete evaluation, considering the multi-rate design for different values is shown in Figure 9. From this figure, we may infer that just the multi-rate design allows one to approach the continuous throughput curve, and that the distinction about the performance of the different algorithms becomes clearer. In particular, the throughput improvement deriving from the repetition schemes strongly depends on the residual amount of interference remaining after the IC process.
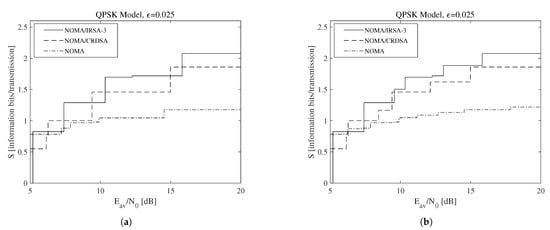
Figure 8.
Throughput as a function of the available average SNR for and a discrete set of code rates adopting the QPSK modulation: (a) single code rate, (b) double code rate.

Table 4.
Discrete code rate/energy level designs for the NOMA/IRSA-3 scheme with .
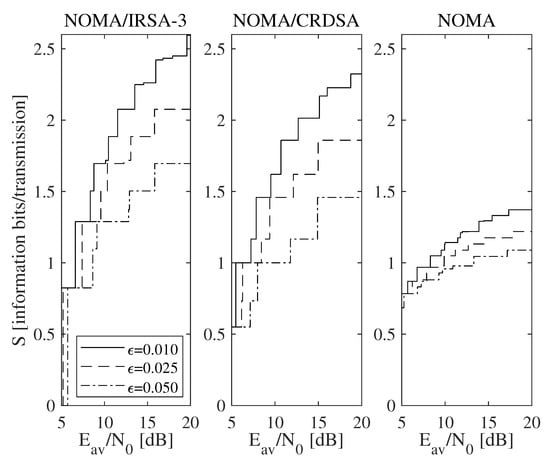
Figure 9.
Throughput as a function of the available average SNR for different values assuming the QPSK modulation and a discrete set of code rates.
6. Conclusions
The joint adoption of NOMA and packet diversity in the presence of imperfect IC and constraints on the average available energy has been investigated. A suitable energy design allows one to achieve the benefits of repetitions and power diversity, without negative effects on energy consumption, which may affect the user’s experience. The relationship between the energy levels and the rates sustainable by the system has been theoretically derived to enable the design of both rate-based and energy-constrained random access networks. Besides, a throughput analysis moving from the density evolution approach has been developed to identify the limiting performance of NOMA/CRDSA and NOMA/IRSA schemes.
The obtained results have shown that the NOMA/PR strategy allows significant throughput improvements with respect to the pure NOMA and PR algorithms, but have confirmed also that the residual interference may severely affect the performance of solutions previously conceived assuming perfect IC. A comparison carried out considering an ideal Shannon model and a more realistic QPSK modulation in a practical scenario characterized by discretized code rates has revealed that, in the first case, the basic SA scheme is competitive with the more sophisticated NOMA/PR ones, while, in the second case, the joint usage of energy and packet diversity is highly preferable. To exploit this capability, some possible code rate combinations have been explored by taking into account different levels of cancelled interference. This has more clearly put into evidence the applicability of the developed energy design, which may hence represent a useful tool for introducing energy saving in next-generation satellite and terrestrial systems, while maintaining a satisfactory performance for the corresponding random access channels.
Current research efforts are devoted to deepen the behavior of the NOMA/PR schemes in the low SNR regime, in which the correct detection of more than one packet in a single attempt is possibile. The modifications of the energy design in these situations is one of the activities carried out in the present research activity.
Author Contributions
F.B.: conceptualization, software and original draft preparation, G.B.: review and editing, F.V.: review and editing, M.C.: conceptualization, writing and validation. All authors have read and agreed to the published version of the manuscript.
Funding
This research was partly funded by the Italian Ministry of University and Research (MIUR) within the project FRA 2021 (University of Trieste, Italy), entitled “Interference modeling in ultra-dense 5G/6G networks.”
Conflicts of Interest
The authors declare no conflict of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript, or in the decision to publish the results.
Abbreviations
The following abbreviations are used in this manuscript:
| CRDSA | Contention Resolution Diversity SA |
| IC | Interference Cancellation |
| IoT | Internet of Things |
| IRSA | Irregular Repetition SA |
| NOMA | Non-Orthogonal Multiple Access |
| QPSK | Quadrature Phase-Shift Keying |
| Probability Density Function | |
| PR | Packet Repetition |
| RAF | Random Access Frame |
| RV | Random Variable |
| SA | Slotted Aloha |
| SNR | Signal to Noise Ratio |
References
- Andrews, J.G.; Buzzi, S.; Choi, W.; Hanly, S.V.; Lozano, A.; Soong, A.C.K.; Zhang, J.C. What will 5G be? IEEE J. Sel. Areas Commun. 2014, 32, 1065–1082. [Google Scholar] [CrossRef]
- Sanchez-Aguero, V.; Vidal, I.; Valera, F.; Nogales, B.; Mendes, L.L.; Damascena Dias, W.; Carvalho Ferreira, A. Deploying an NFV-based experimentation scenario for 5G solutions in underserved areas. Sensors 2021, 21, 1897. [Google Scholar] [CrossRef]
- Babich, F.; Comisso, M. Impact of segmentation and capture on slotted Aloha systems exploiting interference cancellation. IEEE Trans. Veh. Technol. 2019, 68, 2878–2892. [Google Scholar] [CrossRef]
- Giordani, M.; Zorzi, M. Non-terrestrial networks in the 6G era: Challenges and opportunities. IEEE Netw. 2021, 35, 244–251. [Google Scholar] [CrossRef]
- Roberts, L.G. ALOHA packet systems with and without slots and capture. ACM SIGCOMM Comput. Commun. Rev. 1975, 5, 28–42. [Google Scholar] [CrossRef]
- Xu, C.; Ping, L.; Wang, P.; Chan, S.; Lin, X. Decentralized power control for random access with successive interference cancellation. IEEE J. Sel. Areas Commun. 2013, 31, 2387–2395. [Google Scholar] [CrossRef]
- Marques da Silva, M.; Dinis, R. Power-ordered NOMA with massive MIMO for 5G systems. Appl. Sci. 2021, 11, 3541. [Google Scholar] [CrossRef]
- Shin, W.; Vaezi, M.; Lee, B.; Love, D.J.; Lee, J.; Poor, H.V. Non-orthogonal multiple access in multi-cell networks: Theory, performance, and practical challenges. IEEE Commun. Mag. 2017, 55, 176–183. [Google Scholar] [CrossRef]
- Casini, E.; De Gaudenzi, R.; del Rio Herrero, O. Contention resolution diversity slotted ALOHA (CRDSA): An enhanced random access scheme for satellite access packet networks. IEEE Trans. Wirel. Commun. 2007, 6, 1408–1419. [Google Scholar] [CrossRef]
- Liva, G. Graph-based analysis and optimization of contention resolution diversity slotted ALOHA. IEEE Trans. Commun. 2011, 59, 477–487. [Google Scholar] [CrossRef]
- Toni, L.; Frossard, P. Prioritized random MAC optimization via graph-based analysis. IEEE Trans. Commun. 2015, 63, 5002–5013. [Google Scholar] [CrossRef]
- Fei, C.; Jiang, B.; Xu, K.; Wang, L.; Zhao, B. An intelligent load control-based random access scheme for space-based Internet of Things. Sensors 2021, 21, 1040. [Google Scholar] [CrossRef] [PubMed]
- Paolini, E.; Liva, G.; Chiani, M. Coded slotted ALOHA: A graph-based method for uncoordinated multiple access. IEEE Trans. Inf. Theory 2015, 61, 6815–6832. [Google Scholar] [CrossRef]
- Sec. Gener. DVB Interact. Satellite Syst. (DVB-RCS2): Lower Layers for Satellite Std, ETSI EN 301 545-2 V1.2.1. 2014. Available online: https://www.etsi.org/deliver/etsi_en/301500_301r599/30154502/01.02.01_60/en_30154502v010201p.pdf (accessed on 17 June 2021).
- Choi, J. NOMA-based random access with multichannel ALOHA. IEEE J. Sel. Areas Commun. 2017, 35, 2736–2743. [Google Scholar] [CrossRef]
- Clazzer, F.; Munari, A.; Liva, G.; Lazaro, F.; Stefanovic, C.; Popovski, P. From 5G to 6G: Has the time for modern random access come? arXiv 2019, arXiv:1903.03063. [Google Scholar]
- Alvi, S.; Durrani, S.; Zhou, X. Enhancing CRDSA with transmit power diversity for machine-type communication. IEEE Trans. Veh. Technol. 2018, 8, 7790–7794. [Google Scholar] [CrossRef]
- Shao, X.; Sun, Z.; Yang, M.; Gu, S.; Guo, Q. NOMA-based irregular repetition slotted ALOHA for satellite networks. IEEE Commun. Lett. 2019, 23, 624–627. [Google Scholar] [CrossRef]
- Corrado, R.; Comisso, M.; Babich, F. On the impact of the video quality assessment in 802.11e ad-hoc networks using adaptive retransmissions. In Proceedings of the 2014 13th Annual Mediterranean Ad Hoc Networking Workshop (MED-HOC-NET), Piran, Slovenia, 2–4 June 2014; pp. 47–54. [Google Scholar] [CrossRef]
- Amezcua Valdovinos, I.; Figueroa Milla´n, P.E.; Pe´rez-Di´az, J.A.; Vargas-Rosales, C. Distributed channel ranking scheduling function for dense industrial 6TiSCH networks. Sensors 2021, 21, 1593. [Google Scholar] [CrossRef] [PubMed]
- Babich, F.; Comisso, M. Multi-packet communication in heterogeneous wireless networks adopting spatial reuse: Capture analysis. IEEE Trans. Wirel. Commun. 2013, 12, 5346–5359. [Google Scholar] [CrossRef]
- Zanella, A.; Zorzi, M. Theoretical analysis of the capture probability in wireless systems with multiple packet reception capabilities. IEEE Trans. Commun. 2012, 60, 1058–1071. [Google Scholar] [CrossRef]
- Buttazzoni, G.; Babich, F.; Vatta, F.; Comisso, M. Geometrical synthesis of sparse antenna arrays using compressive sensing for 5G IoT applications. Sensors 2020, 20, 350. [Google Scholar] [CrossRef] [PubMed]
- Amer, A.; Ahmad, A.-M.; Hoteit, S. Resource allocation for downlink full-duplex cooperative NOMA-based cellular system with imperfect SI cancellation and underlaying D2D communications. Sensors 2021, 21, 2768. [Google Scholar] [CrossRef]
- Comisso, M.; Palese, G.; Babich, F.; Vatta, F.; Buttazzoni, G. 3D multi-beam and null synthesis by phase-only control for 5G antenna arrays. Electronics 2019, 8, 656. [Google Scholar] [CrossRef]
- Islam, S.M.R.; Avazov, N.; Dobre, O.A.; Kwak, K. Power-domain non-orthogonal multiple access (NOMA) in 5G systems: Potentials and challenges. IEEE Commun. Surv. Tut. 2017, 19, 721–742. [Google Scholar] [CrossRef]
- Babich, F.; Buttazzoni, G.; Vatta, F.; Comisso, M. Energy-constrained uncoordinated multiple access for next-generation networks. IEEE Open J. Commun. Soc. 2020, 1, 1808–1819. [Google Scholar] [CrossRef]
- Fanti, A.; Schirru, L.; Casu, S.; Lodi, M.B.; Riccio, G.; Mazzarella, G. Improvement and testing of models for field level evaluation in urban environment. IEEE Trans. Antennas Propag. 2020, 68, 4038–4047. [Google Scholar] [CrossRef]
- El-Saleh, A.A.; Shami, T.M.; Nordin, R.; Alias, M.Y.; Shayea, I. Multi-objective optimization of joint power and admission control in cognitive radio networks using enhanced swarm intelligence. Electronics 2021, 10, 189. [Google Scholar] [CrossRef]
- Babich, F.; Soranzo, A.; Vatta, F. Useful mathematical tools for capacity approaching codes design. IEEE Commun. Lett. 2017, 21, 1949–1952. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).