Hybrid Blockchain for IoT—Energy Analysis and Reward Plan
Abstract
1. Introduction
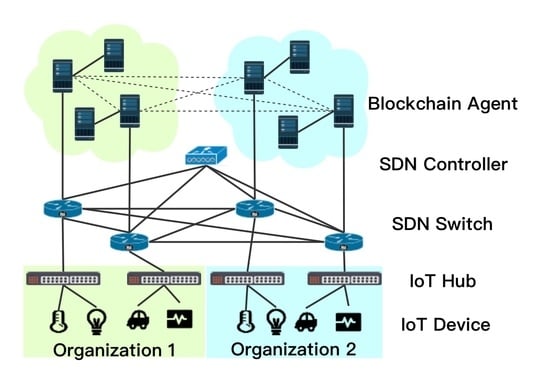
- Scenario 1—Private chain within a single organisation: In this scenario, Organisation 1 has private transactions, such as sensory data generated by local IoT application, to be verified and stored within the organisation. As shows in Figure 1a, sensory data of Organisation 1 can be verified by organisation-owned servers to preserve the privacy.
- Scenario 2—Private chain across organisations: Organisation 1 and 2 form a partnership for an IoT application. The two organisations share IoT devices, and the IoT devices or systems communicate with each other (in Figure 1a). For example, in the aforementioned SerIoT IoT security application [5], after the SDN controller’s path calculation, the flow rules are verified across organisations 1 and 2 by PBFT consensus mechanism.
- Scenario 3—Public chain and private chain cooperation: if, after the flow rule verification by private chain, malicious behaviour is detected, then, the organisations 1 and 2 decide to make this information public to all the organisations as an alert to block a certain system (as in Figure 1b). In such a case, the leading agent in the private blockchain initiates a public chain consensus mechanism, which requires communication between each organisation. This scenario enables a block/allow list to be made public.
- Scenario 4—Public chain only: Organisation 1 for example may notice one of its IoT devices is suffering a denial of service attack from a specific IP address. Instantly, organisation 1 sends this information/transactions directly to the public chain, which informs all the organisations (as in Figure 1b).
- we introduce the architecture of H-chain in this work to provide a customised consensus mechanism, which includes permissioned-PoW and PBFT;
- we analyse the energy consumption of both permissioned-PoW and PBFT consensus mechanism in the proposed network architecture. In particular, we extensively evaluate how the key factors, such as network conditions, computation capability, the number of organisations, and the number of blockchain agents, of the H-chain affect energy consumption.
- we study the design of the proposed reward plan to compensate the energy cost of the verifiers and the miners. The reward aims to encourage the use of more verifiers in the private chain and greater resource contribution by the miners. To provide guideline for H-chain, we consider the proportion of the blocks that stay private as a key factor in the reward plan.
2. Related Works
2.1. Hybrid Blockchain
2.2. Energy Consumption of Blockchain
3. Advantages of H-Chain
- Selective information exposure: The organisations can keep the privacy of their own data and define complex verification contracts within organisations.
- PoW-level of security without PoW work across all transactions: after verification by the private chain, the public chain only needs to verify the hash of a transaction, which leads to more efficient public blockchain, since in pure PoW the whole block and transactions need to be inspected. Moreover, in this work, we propose a permissioned-PoW that enables PoW to run on the permissioned devices verified by the private blockchain.
- Multiple chain security: Some of the transactions have to go through verification of both the private chain and the public chain verification. This process not only provides multiple layers security, but also removes the transaction congestion on the public chain as some transactions are shifted to the private chain.
- Reduce risk of attack on transactions: Some of the organisation-owned information is private, which leads to an unpredictable block generation rate. This fact makes it hard for the attacker to carry out malicious behaviour compared to the public blockchain where block creation is known.
4. Architecture of Hybrid-Blockchain
Entities and Structure of H-Chain
- Blockchain agent (BCA): are software components (i.e., servers) utilising edge computing. BCAs are in charge of the flow verification/validation (and other information) via smart contracts. Furthermore, BCAs also execute basic blockchain functions, such as the consensus process, sending transactions, and maintaining the flow ledger. We assume that for each organisation, it requires at least three BCAs (to fulfill the requirement of PBFT) to form the private blockchain.
- Leading BCA: there is one leading BCA in each organisation that is part of the public blockchain as well as a BCA as explained above. Every leading BCA is able to communicate with other leading BCAs and coordinates not only permissioned-PoW for the public chain, but also PBFT for two or more organisations’ private chain. The leading BCA, namely the miner, can recruit the rest of the BCAs in the organisation to contribute to the public chain.
- Private chain: is owned by an organisation or a group of them in partnership. Private blockchain is in charge of private information verification, which is aided by the PBFT-based consensus mechanism. More than three BCAs are required to operate the private chain;
- Public chain: is operated by the leading BCAs of each organisation. Permissioned-PoW is adopted in public chain for public information verification, validation, storing, and audition. In this work, we propose permissioned-PoW that is similar to traditional PoW, with the difference that it has permissioned miners, that is, leading BCAs. We use PoW as the consensus mechanism of the public chain in the rest of the work.
- Connectivity: intra-organisation connectivity among BCAs is facilitated through an internal network; in our use-case example this is through SDN. Inter-organisation connections are enabled either by dedicated links owned by the connected organisations or provided by a third party—for example, a national or international-network provider.
5. System Model
5.1. Permissioned Proof-of-Work and Energy Modeling
- 1.
- Leading BCAs collect the new data, for example, SDN flow rule [28], that is ready for verification, and build a block. We define the computational latency of this step as , where the latency is proportional to the blocksize s. Note that, the leading BCA in each organisation is also the miner of the public chain.
- 2.
- According to the application requirements, that is, types of knowledge, business model, and energy efficiency, the leading BCA decides the proportion of the blocks that goes public during a period of time. In Section 6, we propose the reward plan for miners in respect to the proportion of the blocks.
- 3.
- All the miners begin to solve the PoW puzzle. The winning miner’s PoW computation latency is denoted as , and the rest of the miners’ computational latency is .
- 4.
- The winning miner completes the PoW and broadcasts the new block to all the miners. Here, the resulting transmission latency is defined as , and it is dependent on the number of organisations/miners I. If the first generated block is delayed during transmission, then the miners may mistake the second block as the first one. This phenomenon is termed forking. For simplicity, without loss of generality, we assume there is no forking in this work.
- 5.
- The other miners receive the new block, stop the current PoW, verify the data in the new block and if it passes, then accept and append the new block. The computational latency of new data verification and appending the new block is denoted as . Till here, the miner of each organisation begins to disseminate the new block inside the organisation. The intra-organisation dissemination latency is defined as , which is related to the blocksize.
5.2. Practical Byzantine Fault Tolerance and Energy Modeling
- 1.
- The initiating BCA collects the new data, for example, SDN flow rules, as transactions and builds a block. Similar to PoW case we define the computational latency for this stage as .
- 2.
- According to an organisation’s requirement, the initiating BCA defines the number of following BCAs and the number of organisations I, and the proportion of the private blocks (details in Section 6). Then, the initiating BCA sends the new block to the other BCAs.
- 2.1.
- if the consensus is within one organisation, the new block is broadcast to all the following BCAs within the organisation. This leads to the broadcast transmission latency .
- 2.2.
- if the PBFT is across organisations, there is an extra inter-organisation transmission latency accounting the latency introduced because of leading BCAs communication within each organisation. This is denoted as .
- 3.
- The following BCAs first send all-to-all acknowledgement (ACK) messages to confirm the acceptance of the new block, which results in intra-organisation transmission latency and inter-organisation transmission latency . Then, all the BCAs begin with the verification that incurs a verification latency . For example, in our SDN/IoT scenario, BCAs conduct verification of the new SDN-flow as new data according to pre-defined flow conformance policy [28].
- 4.
- Another all-to-all ACK messages exchanging happens to confirm the verification result, which is similar to Step 3 ( and ).
- 5.
- The initiating BCA waits for all the ACK messages from the following BCAs. If the votes reach the requirement, the BCAs append the new block to the ledger. In case the votes are inadequate for the consensus requirement, the initiator BCA is informed.
5.3. Hybrid Blockchain and Energy Consumption
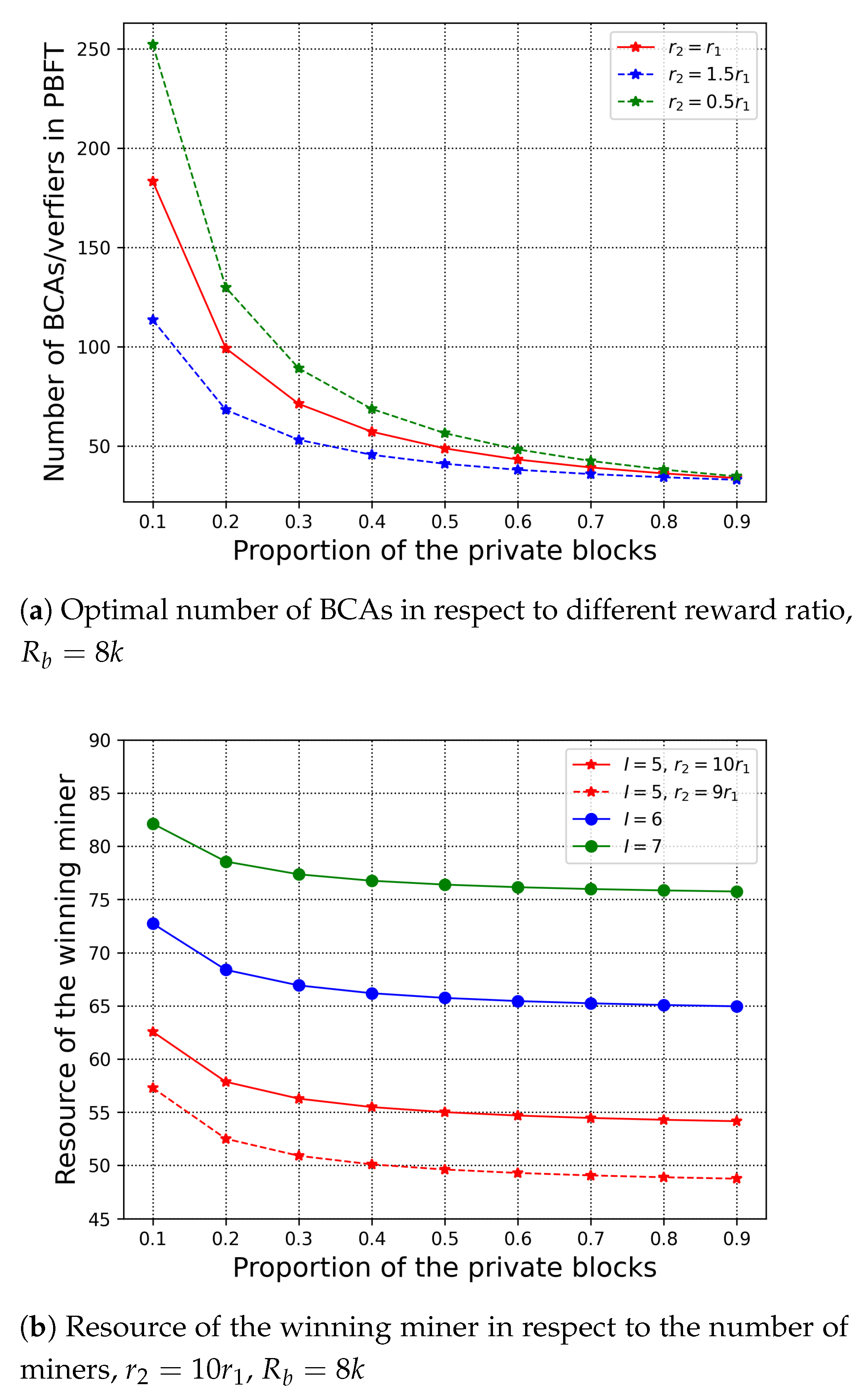
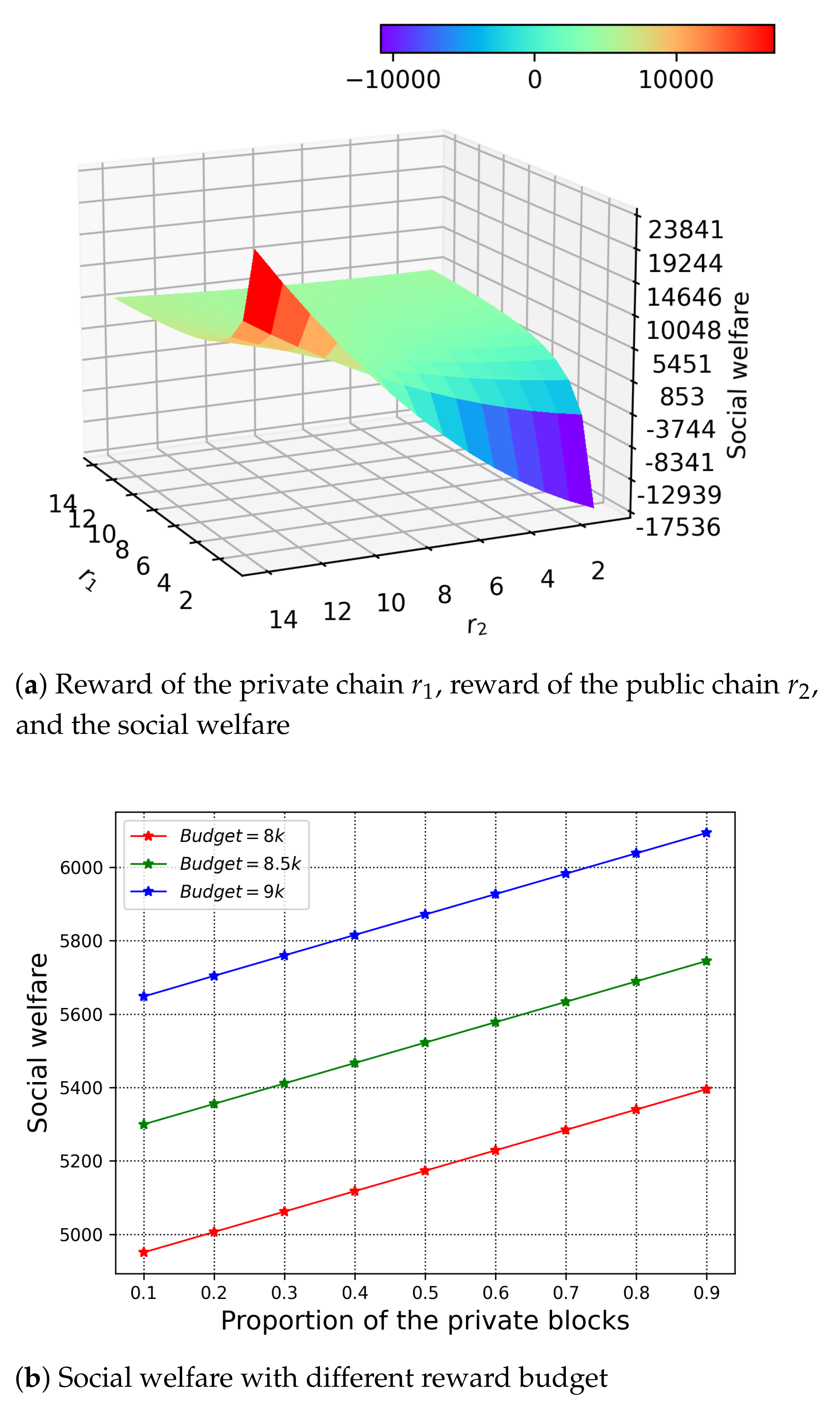
6. Reward Scheme of H-Chain
6.1. Satisfaction Function of the Private Chain
6.2. Satisfaction Function of the Public Chain Bcas
6.3. Social Welfare Maximisation
7. Simulation and Results
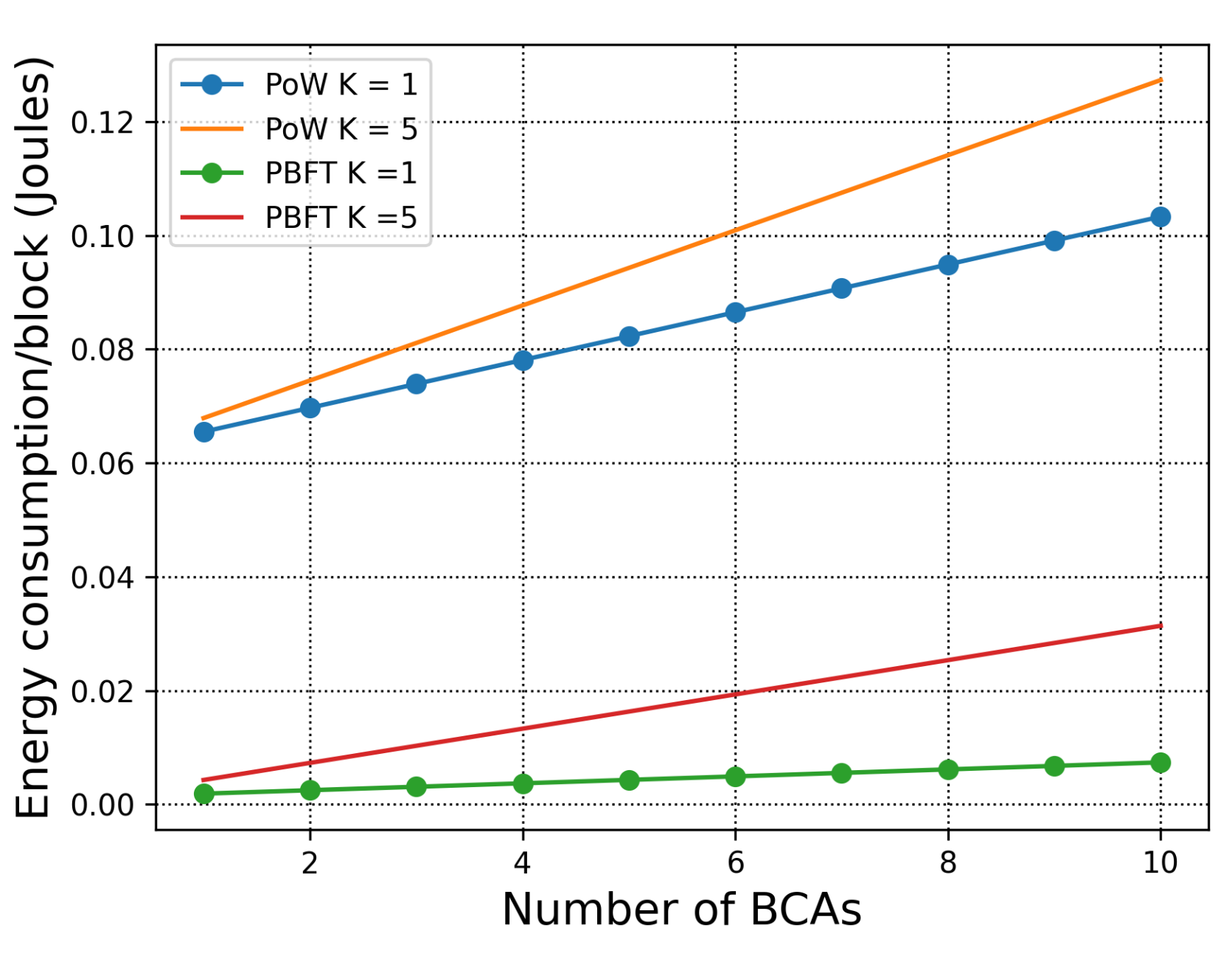
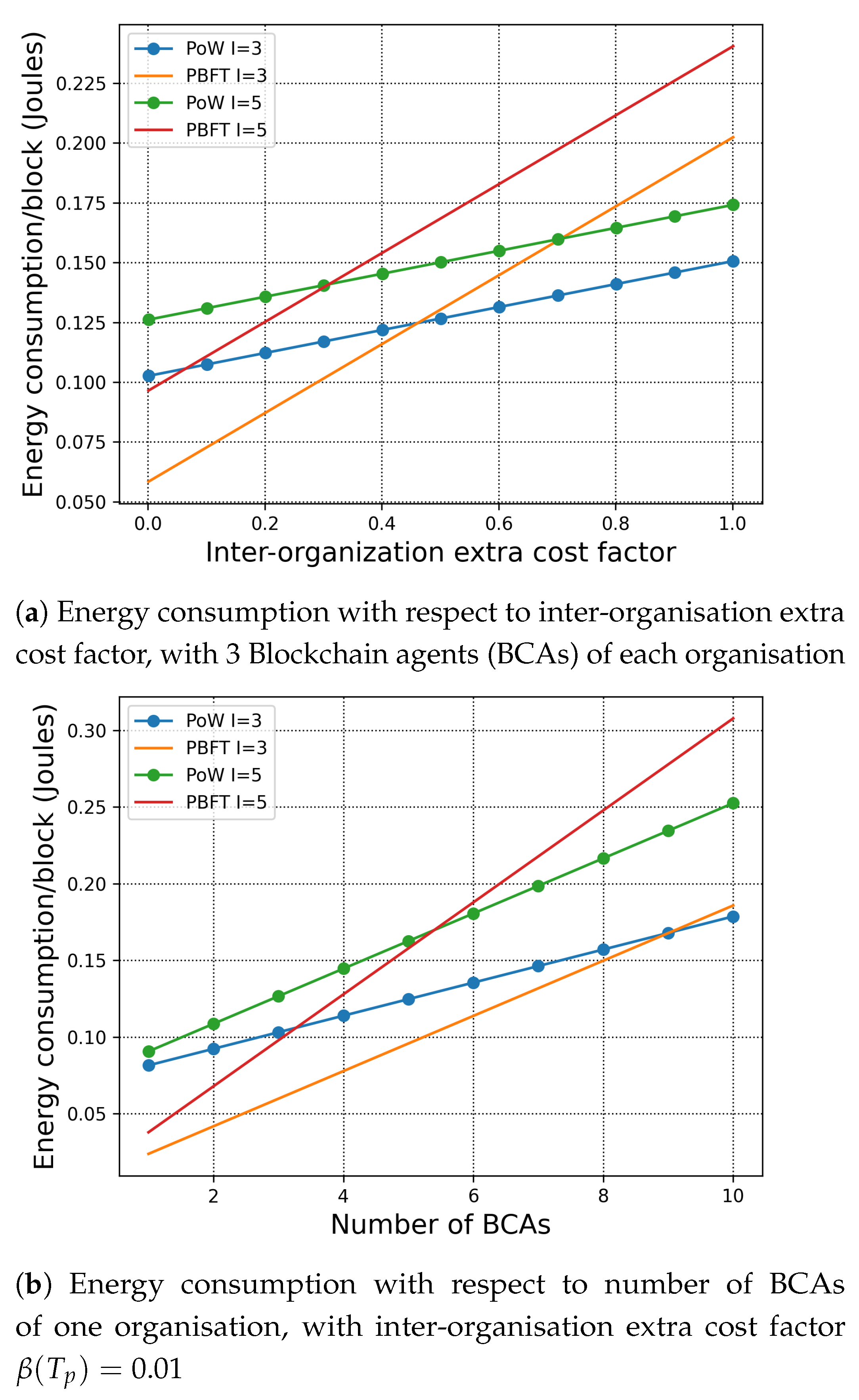
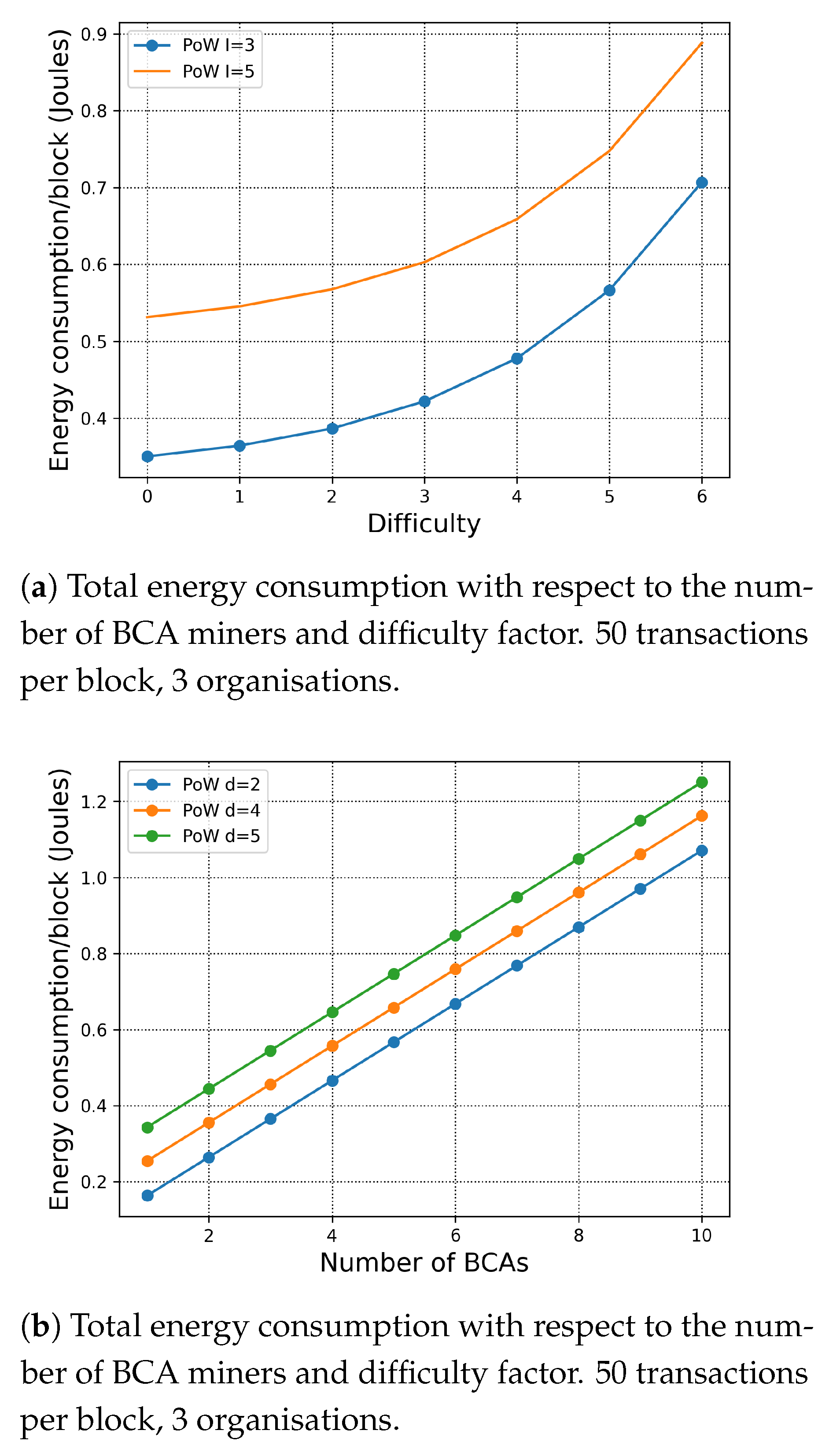
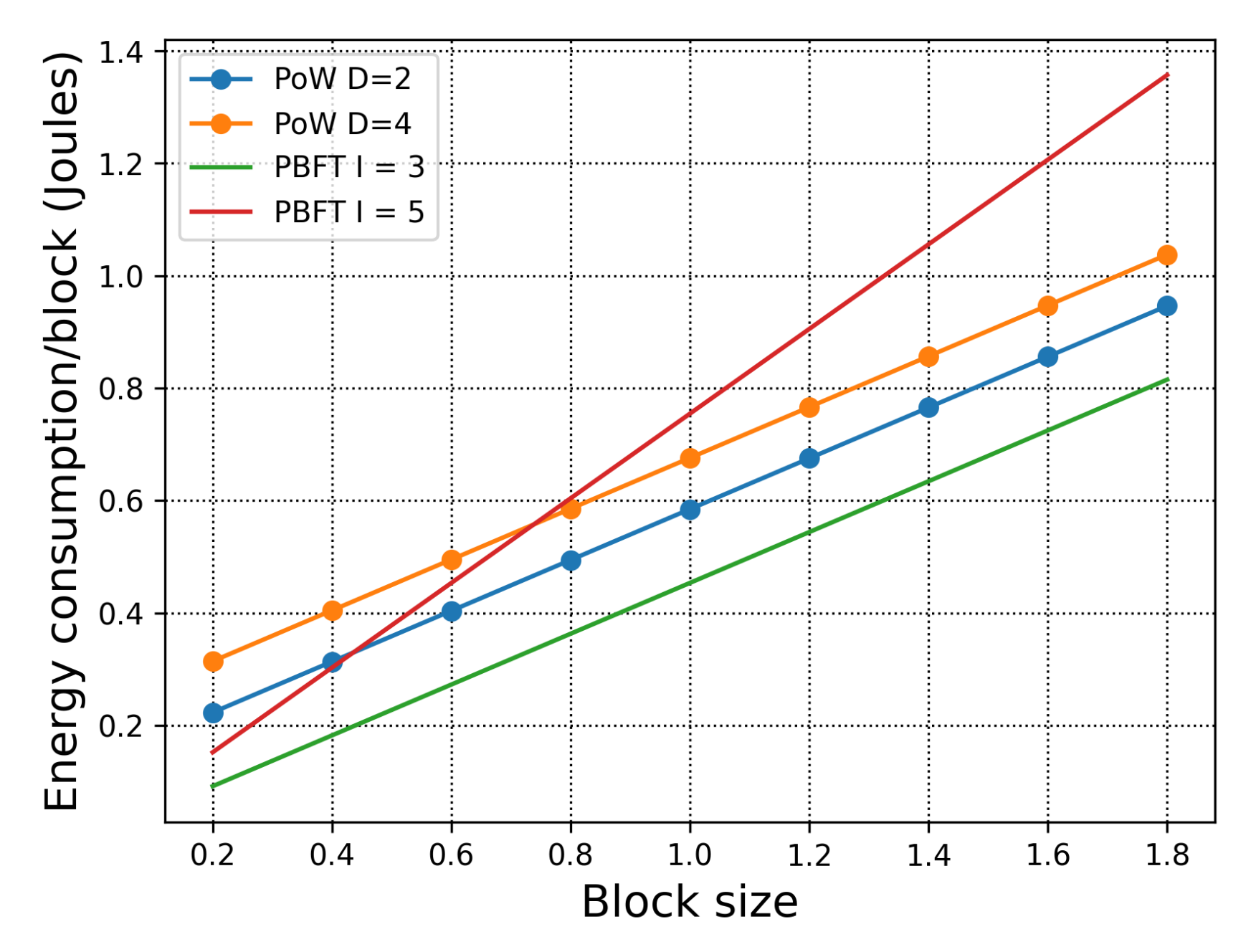
7.1. Energy Consumption of H-Chain
7.1.1. Consensus within One Organisation
7.1.2. Consensus across Organisations
7.1.3. Exploration of the Difficulty of the Puzzle
7.2. Evaluation of the Reward Plan
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Cisco Annual Internet Report (2018–2023). White Paper. 2020. Available online: https://www.cisco.com/c/en/us/solutions/collateral/executive-perspectives/annual-internet-report/white-paper-c11-741490.pdf (accessed on 1 October 2020).
- Hernández-Ramos, J.L.; Baldini, G.; Neisse, R.; Al-Naday, M.; Reed, M.J. A Policy-based Framework in Fog enabled Internet of Things for Cooperative ITS. In Proceedings of the 2019 Global IoT Summit (GIoTS), Aarhus, Denmark, 17–21 June 2019; pp. 1–6. [Google Scholar]
- Hu, J.; Yang, K.; Wang, K.; Zhang, K. A Blockchain-Based Reward Mechanism for Mobile Crowdsensing. IEEE Trans. Comput. Soc. Syst. 2020, 7, 178–191. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Gelenbe, E.; Domanska, J.; Czàchorski, T.; Drosou, A.; Tzovaras, D. Security for internet of things: The seriot project. In Proceedings of the 2018 International Symposium on Networks, Computers and Communications (ISNCC), Rome, Italy, 19–21 June 2018; pp. 1–5. [Google Scholar]
- Daghmehchi Firoozjaei, M.; Ghorbani, A.; Kim, H.; Song, J. Hy-Bridge: A hybrid blockchain for privacy-preserving and trustful energy transactions in Internet-of-Things platforms. Sensors 2020, 20, 928. [Google Scholar] [CrossRef] [PubMed]
- Guo, H.; Li, W.; Nejad, M.; Shen, C. Access Control for Electronic Health Records with Hybrid Blockchain-Edge Architecture. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 44–51. [Google Scholar]
- Zhu, S.; Cai, Z.; Hu, H.; Li, Y.; Li, W. zkCrowd: A hybrid blockchain-based crowdsourcing platform. IEEE Trans. Ind. Inform. 2019, 16, 4196–4205. [Google Scholar] [CrossRef]
- Guan, Z.; Lu, X.; Wang, N.; Wu, J.; Du, X.; Guizani, M. Towards secure and efficient energy trading in IIoT-enabled energy internet: A blockchain approach. Future Gener. Comput. Syst. 2020, 110, 686–695. [Google Scholar] [CrossRef]
- Cachin, C. Architecture of the hyperledger blockchain fabric. In Workshop on Distributed Cryptocurrencies and Consensus Ledgers; ACM: Chicago, IL, USA, 2016; Volume 310. [Google Scholar]
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Bitcoin Energy Consumption Index. Available online: https://digiconomist.net/bitcoin-energy-consumption (accessed on 1 October 2020).
- Change, U.C. The Paris Agreement Report of the Conference of the Parties to the United Nations Framework Convention on Climate Change. HeinOnline. 2018. Available online: https://unfccc.int (accessed on 1 October 2020).
- Hu, J.; Reed, M.; Al-Naday, M.; Thomos, N. Blockchain-aided flow insertion and verification in software defined networks. In Proceedings of the 2020 Global Internet of Things Summit (GIoTS), Dublin, Ireland, 18 January 2020; pp. 1–6. [Google Scholar]
- Desai, H.; Kantarcioglu, M.; Kagal, L. A Hybrid Blockchain Architecture for Privacy-Enabled and Accountable Auctions. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Seoul, Korea, 14–17 May 2019; pp. 34–43. [Google Scholar]
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Zhang, Q.; Choo, K.K.R. An energy-efficient SDN controller architecture for IoT networks with blockchain-based security. IEEE Trans. Serv. Comput. 2020. [Google Scholar] [CrossRef]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. Blockchain for IoT security and privacy: The case study of a smart home. In Proceedings of the 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom workshops), Kona, HI, USA, 13–17 March 2017; pp. 618–623. [Google Scholar]
- Dorri, A.; Kanhere, S.S.; Jurdak, R. Towards an optimized blockchain for IoT. In Proceedings of the 2017 IEEE/ACM Second International Conference on Internet-of-Things Design and Implementation (IoTDI), Pittsburgh, PA, USA, 18–21 April 2017; pp. 173–178. [Google Scholar]
- Kim, H.M.; Turesson, H.; Laskowski, M.; Bahreini, A.F. Permissionless and Permissioned, Technology-Focused and Business Needs-Driven: Understanding the Hybrid Opportunity in Blockchain Through a Case Study of Insolar. IEEE Trans. Eng. Manag. 2020, 1–16. [Google Scholar] [CrossRef]
- Sagirlar, G.; Carminati, B.; Ferrari, E.; Sheehan, J.D.; Ragnoli, E. Hybrid-iot: Hybrid blockchain architecture for internet of things-pow sub-blockchains. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1007–1016. [Google Scholar]
- Li, Z.; Kang, J.; Yu, R.; Ye, D.; Deng, Q.; Zhang, Y. Consortium blockchain for secure energy trading in industrial internet of things. IEEE Trans. Ind. Inform. 2017, 14, 3690–3700. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System; Technical Report; 2019. Available online: http://nakamotoinstitute.org/bitcoin/ (accessed on 1 October 2020).
- Truby, J. Decarbonizing Bitcoin: Law and policy choices for reducing the energy consumption of Blockchain technologies and digital currencies. Energy Res. Soc. Sci. 2018, 44, 399–410. [Google Scholar] [CrossRef]
- Sedlmeir, J.; Buhl, H.U.; Fridgen, G.; Keller, R. The energy consumption of blockchain technology: Beyond myth. Bus. Inf. Syst. Eng. 2020, 62, 599–608. [Google Scholar] [CrossRef]
- Bach, L.M.; Mihaljevic, B.; Zagar, M. Comparative analysis of blockchain consensus algorithms. In Proceedings of the 2018 41st International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 21–25 May 2018; pp. 1545–1550. [Google Scholar]
- Sharma, V. An Energy-Efficient Transaction Model for the Blockchain-Enabled Internet of Vehicles (IoV). IEEE Commun. Lett. 2019, 23, 246–249. [Google Scholar] [CrossRef]
- Lasla, N.; Alsahan, L.; Abdallah, M.; Younis, M. Green-PoW: An Energy-Efficient Blockchain Proof-of-Work Consensus Algorithm. arXiv 2020, arXiv:2007.04086. [Google Scholar]
- Hu, J.; Reed, M.; Thomos, N.; AI-Naday, M.F.; Yang, K. Securing SDN controlled IoT Networks Through Edge-Blockchain. IEEE Internet Things J. 2020, 1. [Google Scholar] [CrossRef]
- Wiatr, P.; Monti, P.; Wosinska, L. Power savings versus network performance in dynamically provisioned WDM networks. IEEE Commun. Mag. 2012, 50, 48–55. [Google Scholar] [CrossRef]
- Jiao, Y.; Wang, P.; Niyato, D.; Xiong, Z. Social welfare maximization auction in edge computing resource allocation for mobile blockchain. In Proceedings of the 2018 IEEE International Conference On Communications (ICC), Chengdu, China, 19–21 December 2018; pp. 1–6. [Google Scholar]
- Arrow, K.J. Social Choice and Individual Values; Yale University Press: New Haven, CT, USA, 2012; Volume 12. [Google Scholar]
- Chvatal, V.; Chvatal, V. Linear Programming; Macmillan: London, UK, 1983. [Google Scholar]
- Gale, D.; Kuhn, H.W.; Tucker, A.W. Linear programming and the theory of games. Act. Anal. Prod. Alloc. 1951, 13, 317–335. [Google Scholar]
- Thakkar, P.; Nathan, S.; Viswanathan, B. Performance Benchmarking and Optimizing Hyperledger Fabric Blockchain Platform. In Proceedings of the 2018 IEEE 26th International Symposium on Modeling, Analysis, and Simulation of Computer and Telecommunication Systems (MASCOTS), Milwaukee, WI, USA, 25–28 September 2018; pp. 264–276. [Google Scholar]
- Yildiz, H.U.; Gungor, V.C.; Tavli, B. Packet Size Optimization for Lifetime Maximization in Underwater Acoustic Sensor Networks. IEEE Trans. Ind. Inform. 2019, 15, 719–729. [Google Scholar] [CrossRef]
- Dayarathna, M.; Wen, Y.; Fan, R. Data center energy consumption modeling: A survey. IEEE Commun. Surv. Tutor. 2015, 18, 732–794. [Google Scholar] [CrossRef]
- Wei, M.; Zhou, J.; Gao, Y. Energy efficient routing algorithm of software defined data center network. In Proceedings of the 2017 IEEE 9th International Conference on Communication Software and Networks (ICCSN), Guangzhou, China, 6–8 May 2017; pp. 171–176. [Google Scholar] [CrossRef]
- Li, Y.; Wang, Y.; Yin, B.; Guan, L. An Online Power Metering Model for Cloud Environment. In Proceedings of the 2012 IEEE 11th International Symposium on Network Computing and Applications, Cambridge, MA, USA, 23–25 August 2012; pp. 175–180. [Google Scholar]

| Notation | Description | Notation | Description |
|---|---|---|---|
| Transmission power | Number of BCAs of Organisation i | ||
| Computation power | Computation latency of a new block | ||
| R | Intra-organisation effective throughput | Computation latency of winning miner | |
| Inter-organisation effective throughput | Computation latency of new block verification | ||
| Intra-organisation dissemination latency | Size of verification task | ||
| New block transmission latency | Difficulty coefficient | ||
| Extra transmission cost factor | B | Basic puzzle size | |
| f | CPU capability | D | Difficulty factor |
| s | Block size | Reward difference of the miners | |
| K | Number of transactions in one block | Proportion of the private blocks | |
| Size of ACK message | Block rate | ||
| Size of winning miner’s puzzle | l | Period | |
| Size of non-winning miner’s puzzle | Probability of being a winning miner | ||
| Energy price per unit | Reward to the BCA verifiers | ||
| I | Number of organisations/miners | Reward to the winning miner | |
| N | Number of BCAs | Reward budget |
| Parameters | Value | Parameters | Value |
|---|---|---|---|
| 48 W | 1 KB | ||
| 150 W | 0.1 | ||
| R | 10 Gbps | B | 100 KB |
| 1 Gbps | 2 | ||
| f | 2 GHz | ||
| s | 0.2 KB–2 KB | 5 | |
| 20 Bytes | l | 10 ms | |
| 100 KB | 8000 | ||
| 1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hu, J.; Reed, M.J.; Al-Naday, M.; Thomos, N. Hybrid Blockchain for IoT—Energy Analysis and Reward Plan. Sensors 2021, 21, 305. https://doi.org/10.3390/s21010305
Hu J, Reed MJ, Al-Naday M, Thomos N. Hybrid Blockchain for IoT—Energy Analysis and Reward Plan. Sensors. 2021; 21(1):305. https://doi.org/10.3390/s21010305
Chicago/Turabian StyleHu, Jiejun, Martin J. Reed, Mays Al-Naday, and Nikolaos Thomos. 2021. "Hybrid Blockchain for IoT—Energy Analysis and Reward Plan" Sensors 21, no. 1: 305. https://doi.org/10.3390/s21010305
APA StyleHu, J., Reed, M. J., Al-Naday, M., & Thomos, N. (2021). Hybrid Blockchain for IoT—Energy Analysis and Reward Plan. Sensors, 21(1), 305. https://doi.org/10.3390/s21010305