Proof-of-PUF Enabled Blockchain: Concurrent Data and Device Security for Internet-of-Energy
Abstract
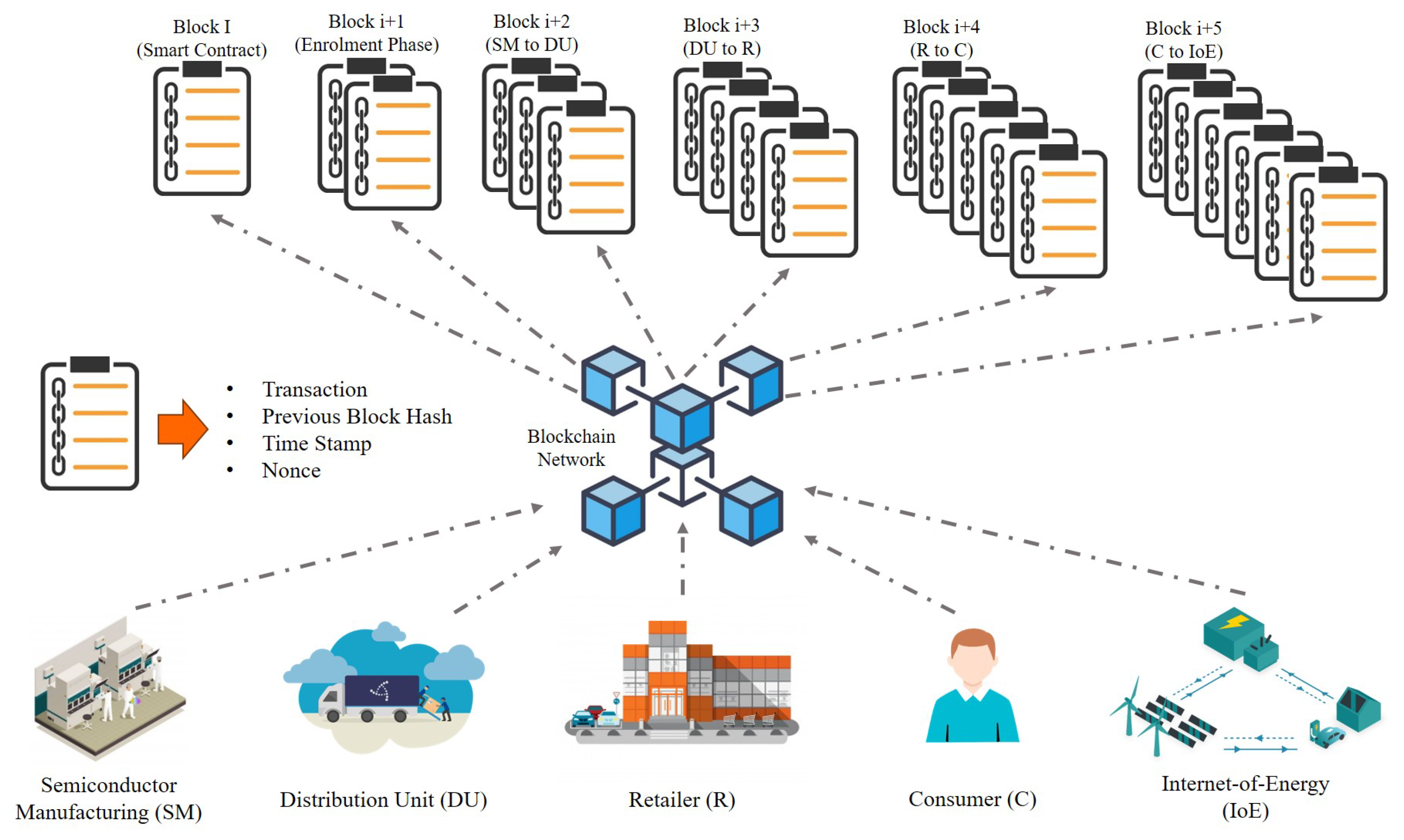
1. Introduction
| TCP/IP Layer | Attack | Attack Vector |
|---|---|---|
| Physical | Jamming [45] | With radio interference |
| Tampering [46] | Making fake nodes | |
| Data Link | Collision [47] | Transmit data at the same time in the same frequency channel |
| Exhaustion [48] | Multiple collisions and continuous re-transmission until the node runs out of resource | |
| Unfairness [49] | Repeatedly ask for the channel to limit others request | |
| Network | Spoofed, or Replayed routing information [49,50] | Routing loops, changing the source of the route, Repelling network from selected nodes |
| Selective forwarding [51] | Send selected information to the legitimate receiver | |
| Sinkhole [52] | Become the target of all nodes in order to gather all information | |
| Sybil [53] | Create lots of pseudonymous identities to undermine the authorised system | |
| Wormholes [54] | Re-transmit information to the IoT nodes | |
| Hello flood [55] | Use Hello messages to flood the network with these tiny messages | |
| Acknowledgement spoofing [56] | Spoof the link layer acknowledgement | |
| Transport | SYN flooding [57] | Resend request multiple times to fill the capacity of the transport layer |
| Desynchronisation [58] | Reinitialise the connection in order to disrupt it | |
| Application | Reliability attacks: Clock skewing, Selective message Forwarding, Data aggregation distortion [59,60] | Impersonate itself as a reliable node in the IoT network and sends corrupted data |
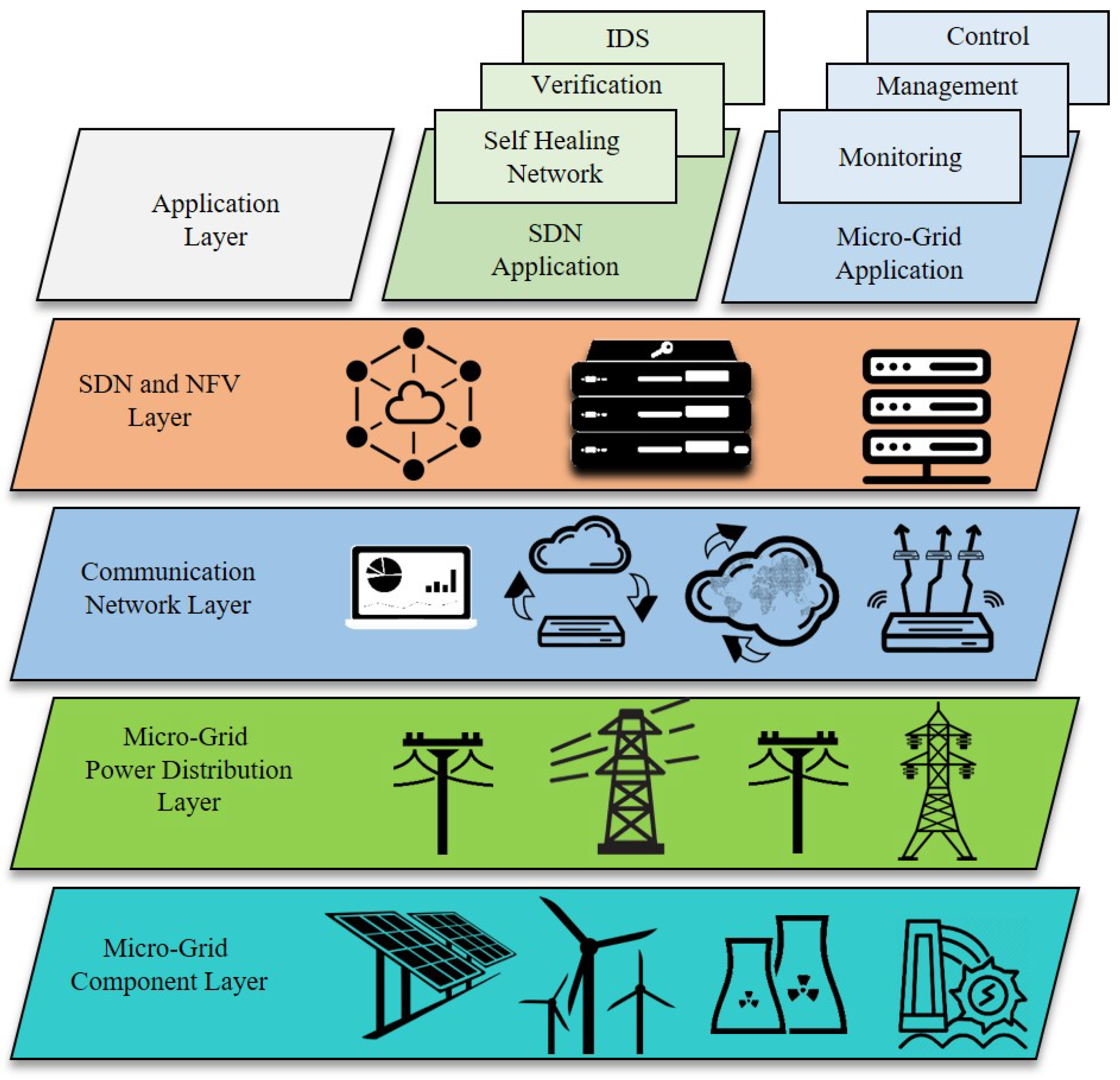
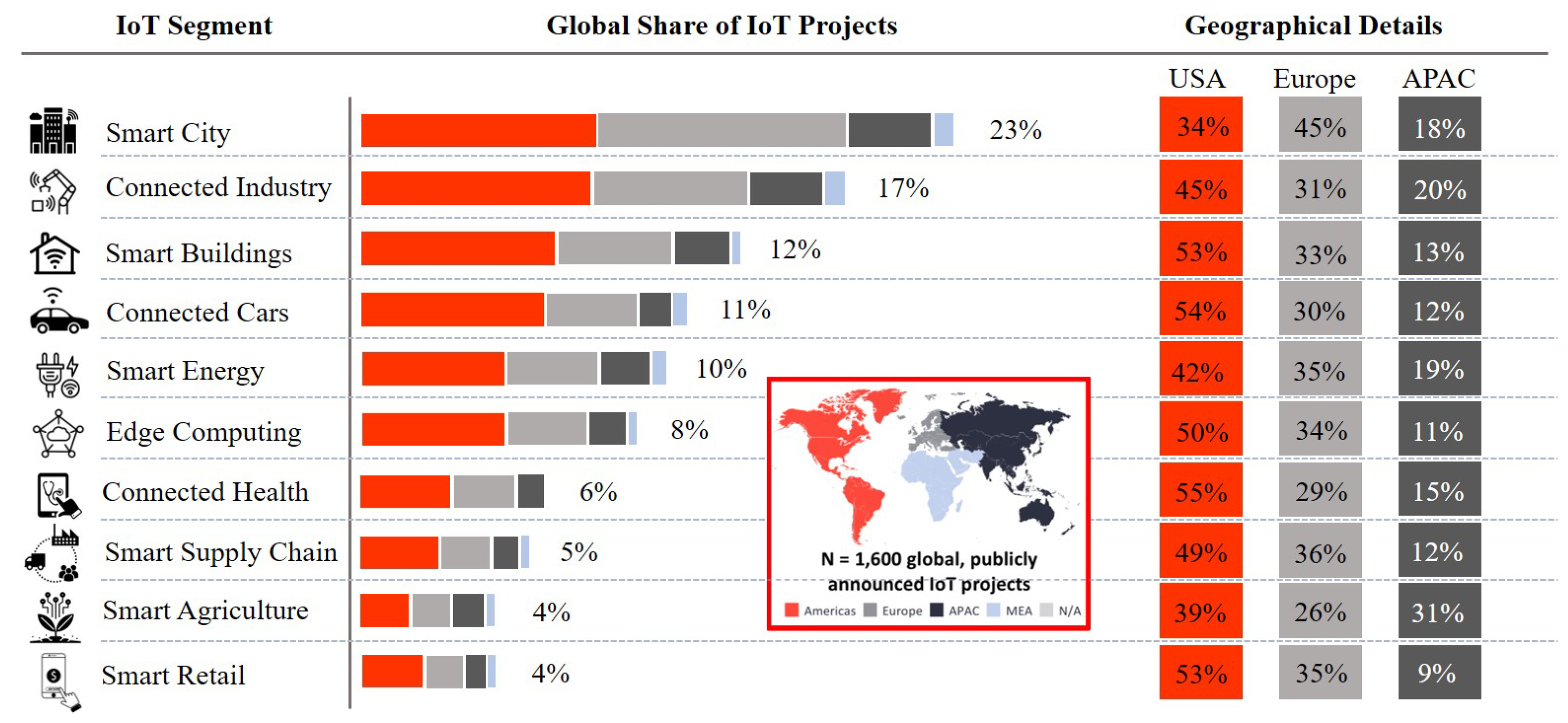
2. Market Survey of IoE
- Improves responsiveness by reducing decision-making latency
- Increases data security and privacy
- Requires less power
- Uses less network bandwidth
- Maximises efficiencies, reliability, and autonomy
- Reduces infrastructure and operational costs
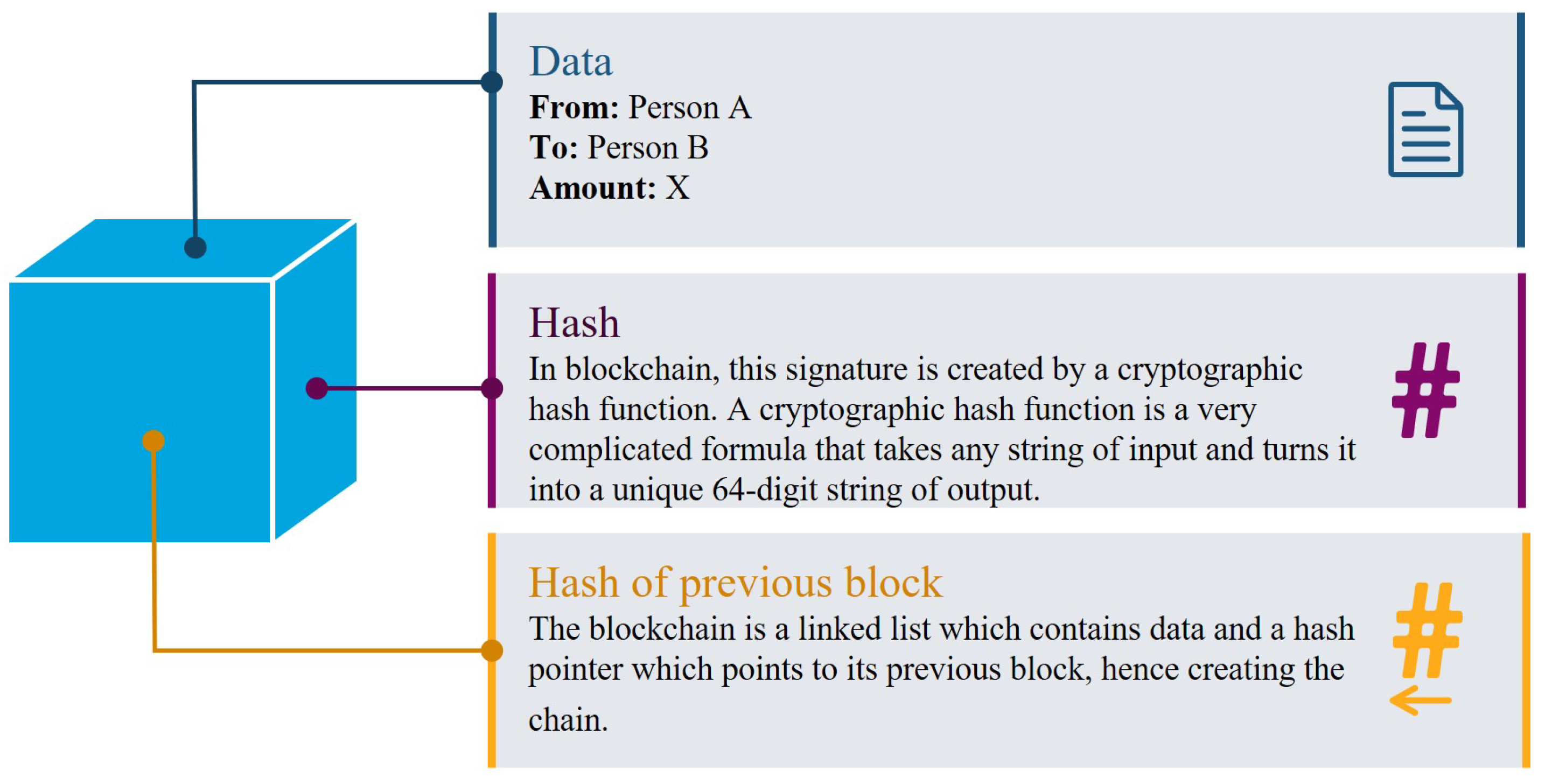
3. Distributed Ledger Technology (DLT) and Blockchain
3.1. Blockchain Networks
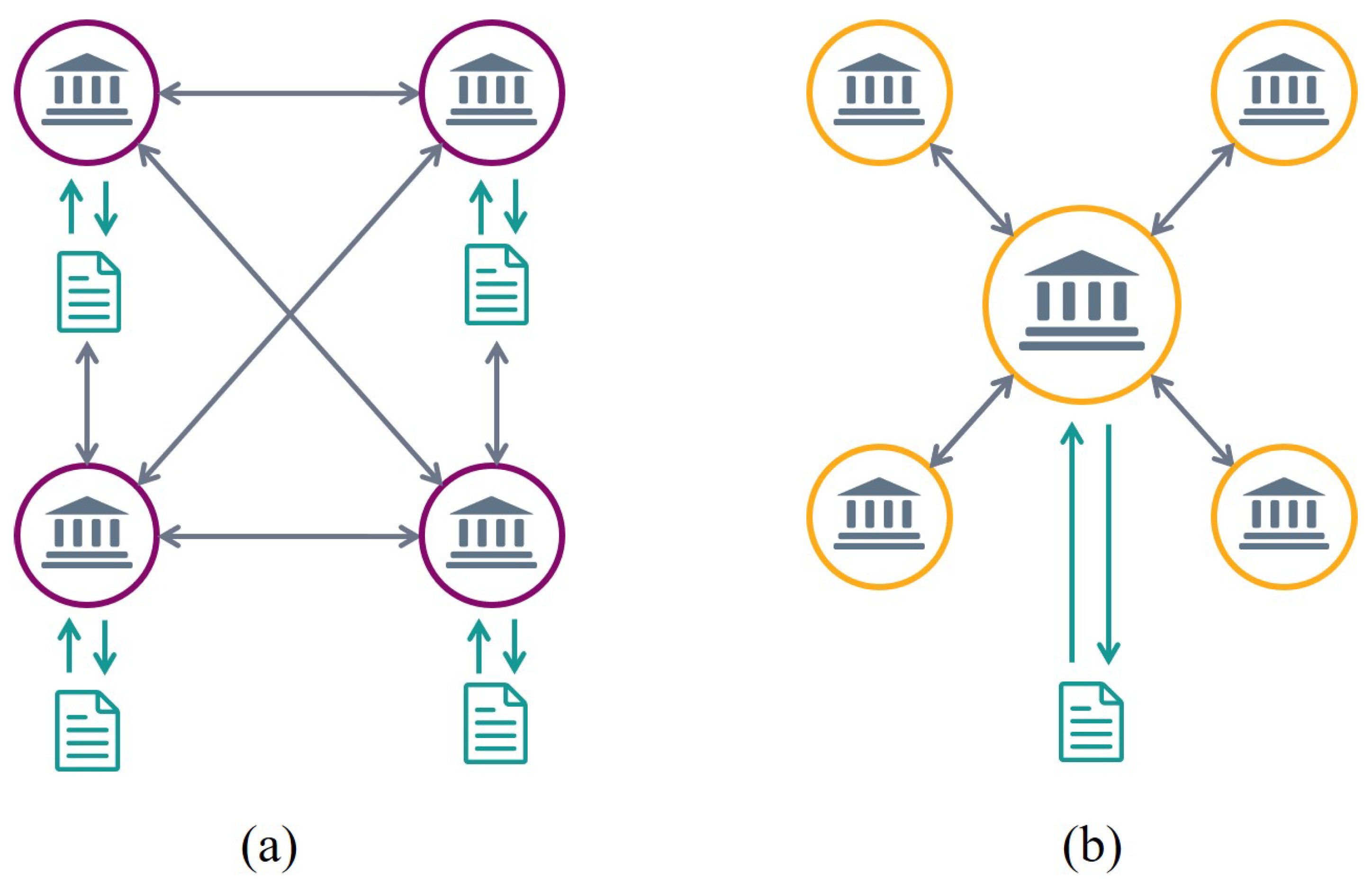
3.1.1. Public Blockchain (Permission-Less Blockchain)
3.1.2. Enterprise Blockchain (Permissioned Blockchain)
3.2. Consensus Algorithms in Blockchain
3.2.1. Proof-of-Work (PoW)
3.2.2. Proof-of-Stake (PoS)
| Property | PoW [96] | PoS [98] | PBFT [102] | DPoS [103] | Ripple [104] | Tendermint [105] |
|---|---|---|---|---|---|---|
| Node Identity Management | Open | Open | Permissioned | Open | Open | Permissioned |
| Energy Savings | No | Partial | Yes | Partial | Yes | Yes |
| Tolerated Power of Adversary | <25% Computing Power | <51% Stake | <33% Faulty Replicas | <51% Validators | <20% Faulty Nodes | <33% Byzantine Voting |
| Transactions (per second) | 7–30 | 30–173 | 100–2500 | 25–2500 | 500–1500 | 10,000 |
| Transactions Fee | High | Low | Very Low | Low | Very Low | High |
| Use-Cases | Bitcoin | Peercoin | Hyperledger Fabric | Bitshares | Ripple | Tendermint |
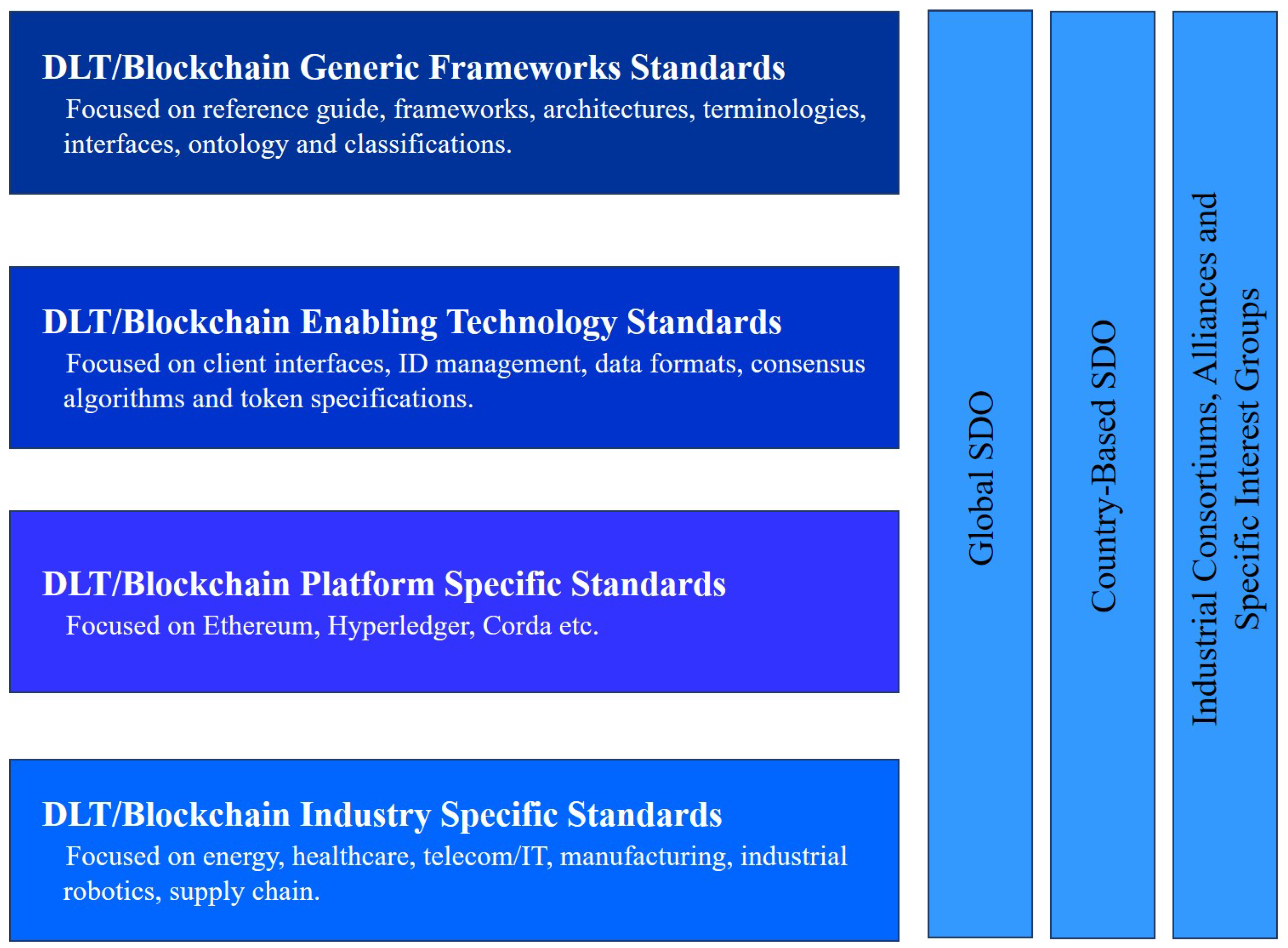
3.3. Interoperable DLT and Blockchain Standards
- IEEE DLT/Blockchain Standards: The IEEE is developing the IEEE P2418 series, focusing on generic frameworks and architectures, interoperability, building blocks for enabling technology, and vertical industry standards [106,107]. In addition, this system tackles the issues of scalability, security, and privacy in implementation and service [108]. It covers different facets and features of Blockchain, including tokens, intelligent contracts, storing of offchain data, as well as Blockchain that is both permissioned and permission-less.
- ISO/TC 307 Blockchain and DLT: TC 307, driven by the Australian Standards Body and the International Organization for Standardization ( ISO), is an important global initiative. The TC 307 for ISO 307 is in its early stages. Architecture and taxonomy, usage cases, protection and privacy, identification, smart contracts, governance, and interoperability between Blockchain apps are some focal areas here. The first reference design, privacy description, and security of publicly identifiable information will be available by 2021 [109].
- Enterprise Ethereum Alliance (EEA): This partnership is a member-driven association of standards whose charter is to create transparent Blockchain specifications that facilitate harmonisation and interoperability for global companies and customers [110]. With more than 500 participants working on transparency, standards-based architectures and requirements to speed up the acceptance of Enterprise Ethereum, the EEA is one of the most involved industry partnerships, focused on the creation of software specifications and Ethereum enterprise certification.
- ITU-T Blockchain: In order to examine the standardisation criteria of DLT-based applications and services, the ITU has developed an open participation ITU-T focus group DLT. The key emphasis of the focus group is the recognition and review of DLT-based applications and services, along with the development of best practises and recommendations to facilitate the global deployment of such applications and services [111].
- W3C: The W3C has a Blockchain Community Group working on a Network Ledger Protocol (WLP) to produce ISO 20022-based Blockchain message format standards and create storage usage guidelines, including torrent, public Blockchain, private Blockchain, and side-chain storage [112]. This group will review and analyse emerging Blockchain-related technologies and use cases such as interbank communications, crypto-currencies, etc.
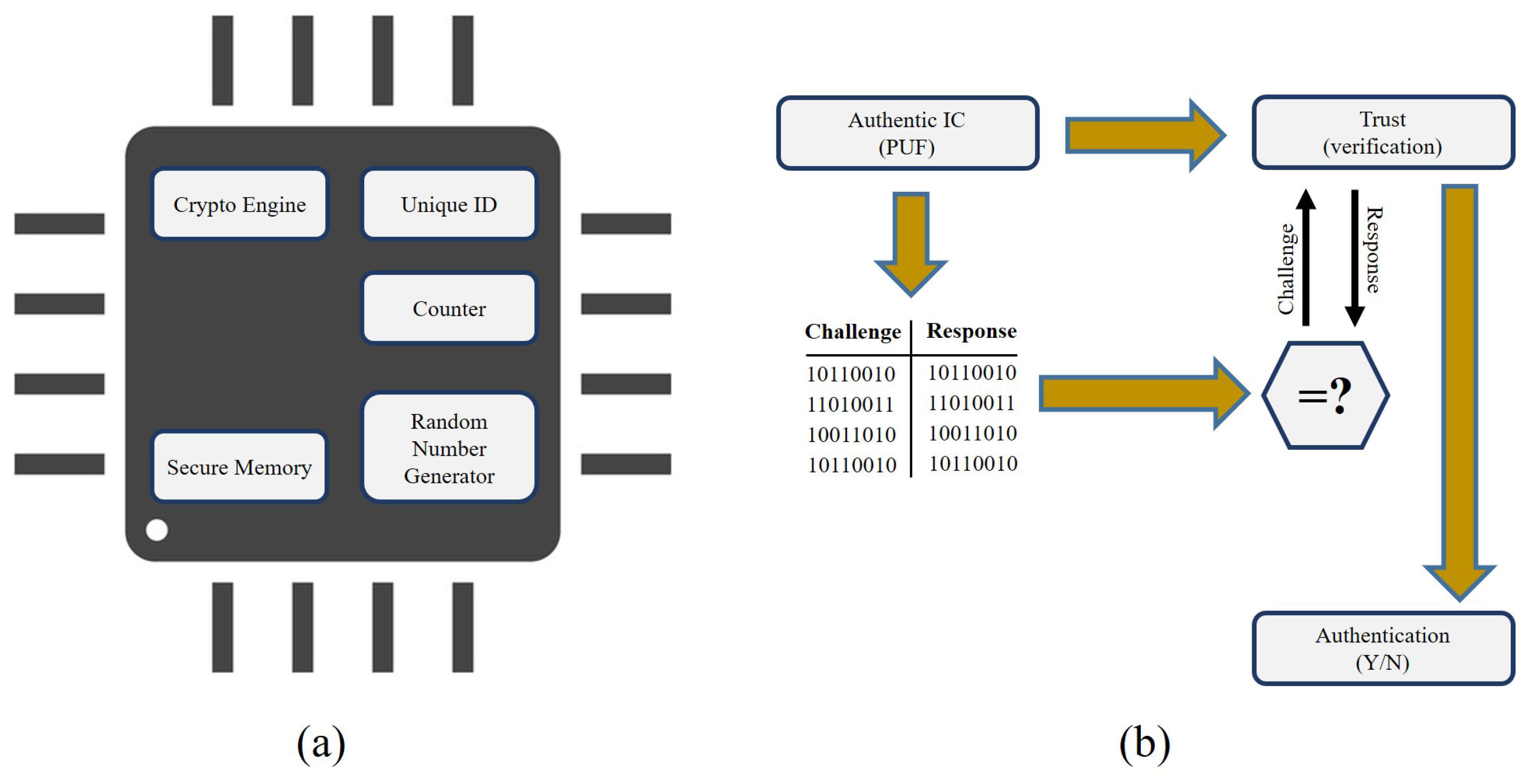
4. Physical Unclonable Functions (PUF)
4.1. Basics of PUFs
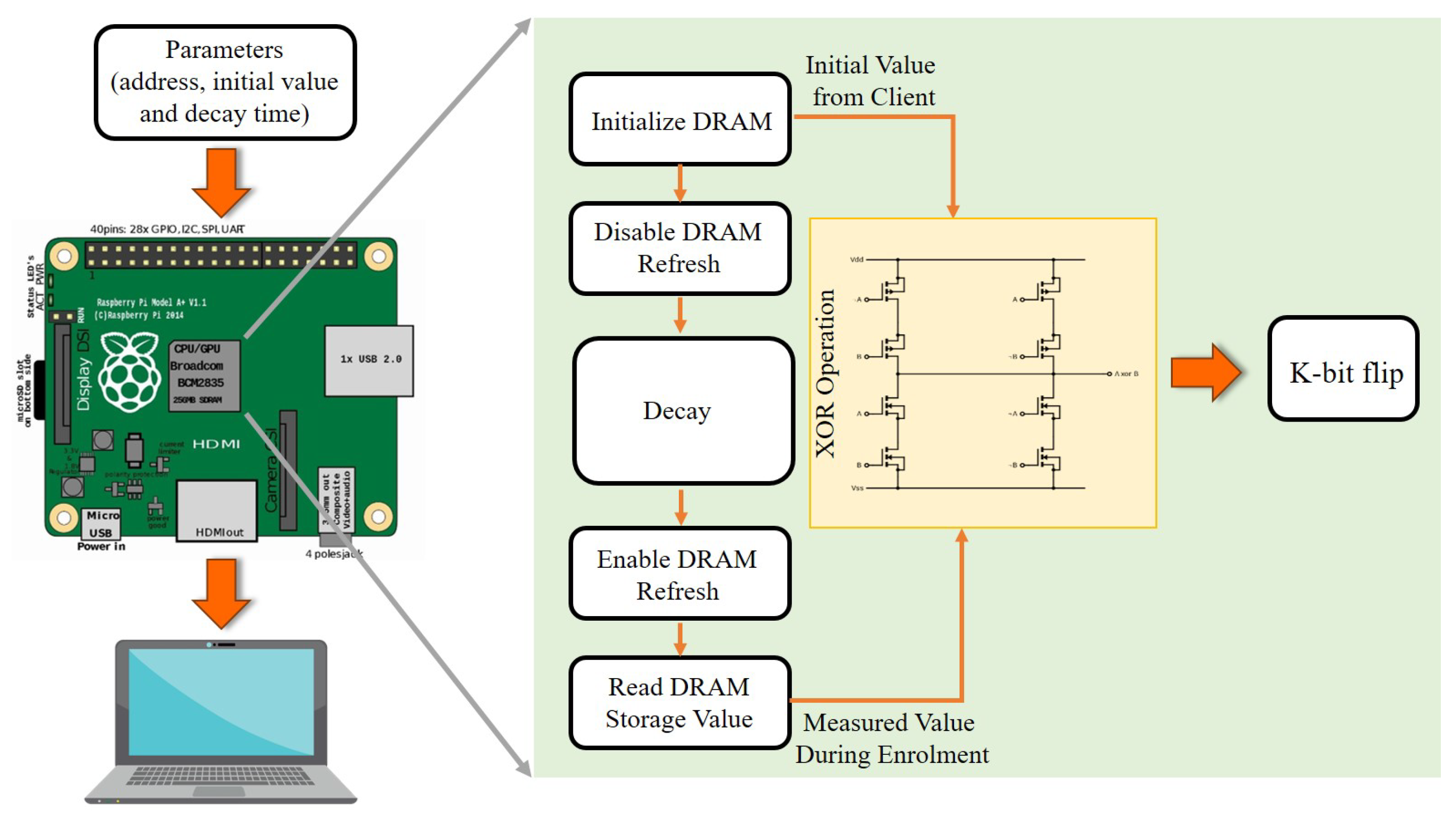
4.1.1. Implementation of PUFs
| PUFs Taxonomy | |||
|---|---|---|---|
| Intrinsic | Extrinsic | ||
| Memory-Based | Delay-Based | Miscellaneous | Generic |
| DRAM PUF [139] | Arbiter PUF [140] | Metal Based PUF [141] | Optical PUF [142] |
| SRAM PUF [138,143] | XOR Arbiter PUF [144] | Photonic PUF [145] | Coating PUF [146] |
| MRAM PUF [147] | Butterfly PUF [148] | Glitch PUF [149] | |
| Flash Memory PUF [150] | Bistable Ring PUF [151] | Quantum Confinement PUF [152] | |
| Ring Oscillator PUF [153] | |||
4.1.2. Working of PUFs
- Temperature: −55 °C to +150 °C (−67 °F to +300 °F)
- Voltage Variation: ± 20%
- Humidity: 80%
- EMC Test: 3 V/m (EN55020 0.15–150 MHz and IEC 61000-4-3 80–1000 MHz)
4.2. PUFs Standardisation
- Steadiness: It is an indicator of the stability of the response time of the PUF. This initiative can be used as a protection necessity. However, PUFs with unsteady responses may be prone to cyber attacks (if the response is very biased) or related key attacks.
- Randomness: It assesses the unpredictability of PUF responses when considering the set of stimulus inputs. Ideally, the fingerprints collected could be unpredictable. This protection criterion certifies the unclonability of the PUF.
- Uniqueness: It calculates how different the two pairs of different PUFs are. This inter-PUF metric is necessary to measure the degree to which the semiconductor manufacturing process is not capable of producing PUF clones.
- Unpredictability: It calculates the difficulty of predicting the response of a (n+1)th PUF that knows all previous “n” instances. This calculation refers to randomness but is more realistic when it includes machine learning or ad hoc research.
- Unclonability: This metric means that no easy-to-use bias or parameter occurs by nature in the PUF architecture. The purpose of this protection criterion is to verify the absence of loop holes in PUF systems.
- Reliability: Bit error rate of 10 (or less)
- Unpredictability: Entropy of 128 bit (or more)
- Diffuseness: Pearson correlation coefficient between challenges and responses of 10 (or less)
4.3. Cyber Resilience of PUFs
- Overbuilding: These types of cyber attacks originate because of the lack of intellectual property (IP) on the chip information or devices. The extra devices can be then sold in open market. The design could also be sold to third parties and PUF devices can be replicated easily.
- Theft-of-Service: In the era of digitisation, the edge devices are virtualised with different services and processing algorithms from the cloud. In case of any adversary on the IoE nodes, the services not authorised to some of the nodes can be accessed by creating a perfect clone or CRPs.
- Denial-of-Service: The regular upgradation of the edge devices in IoE should be audited and encrypted. For any malicious node, if it can get the respective upgraded firmware code it can launch the cyber attacks. This results in the malfunctioning of the operations and denial-of-service attack. The PUF developer should design firmware update procedures very securely to make sure they cannot be used without proper authentication.
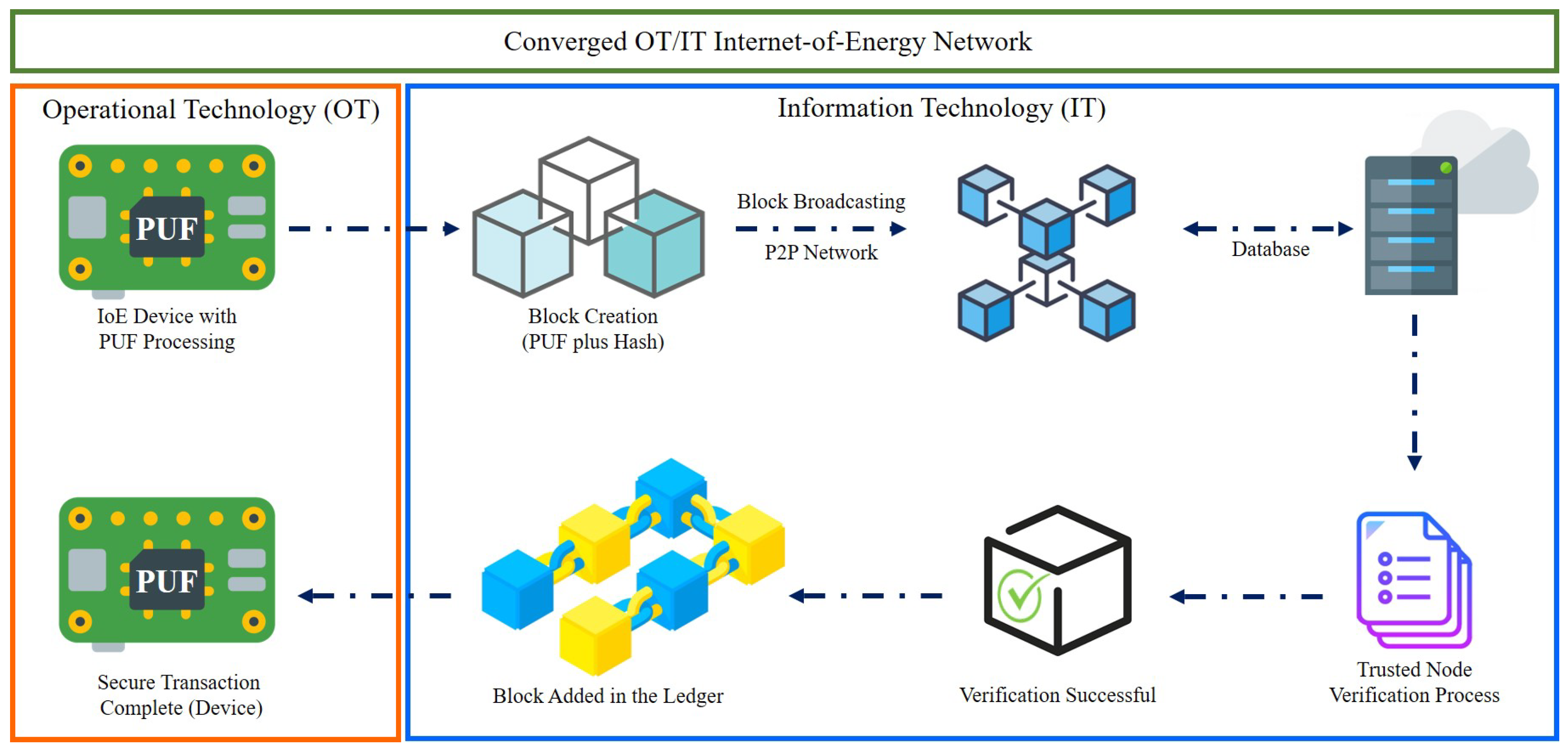
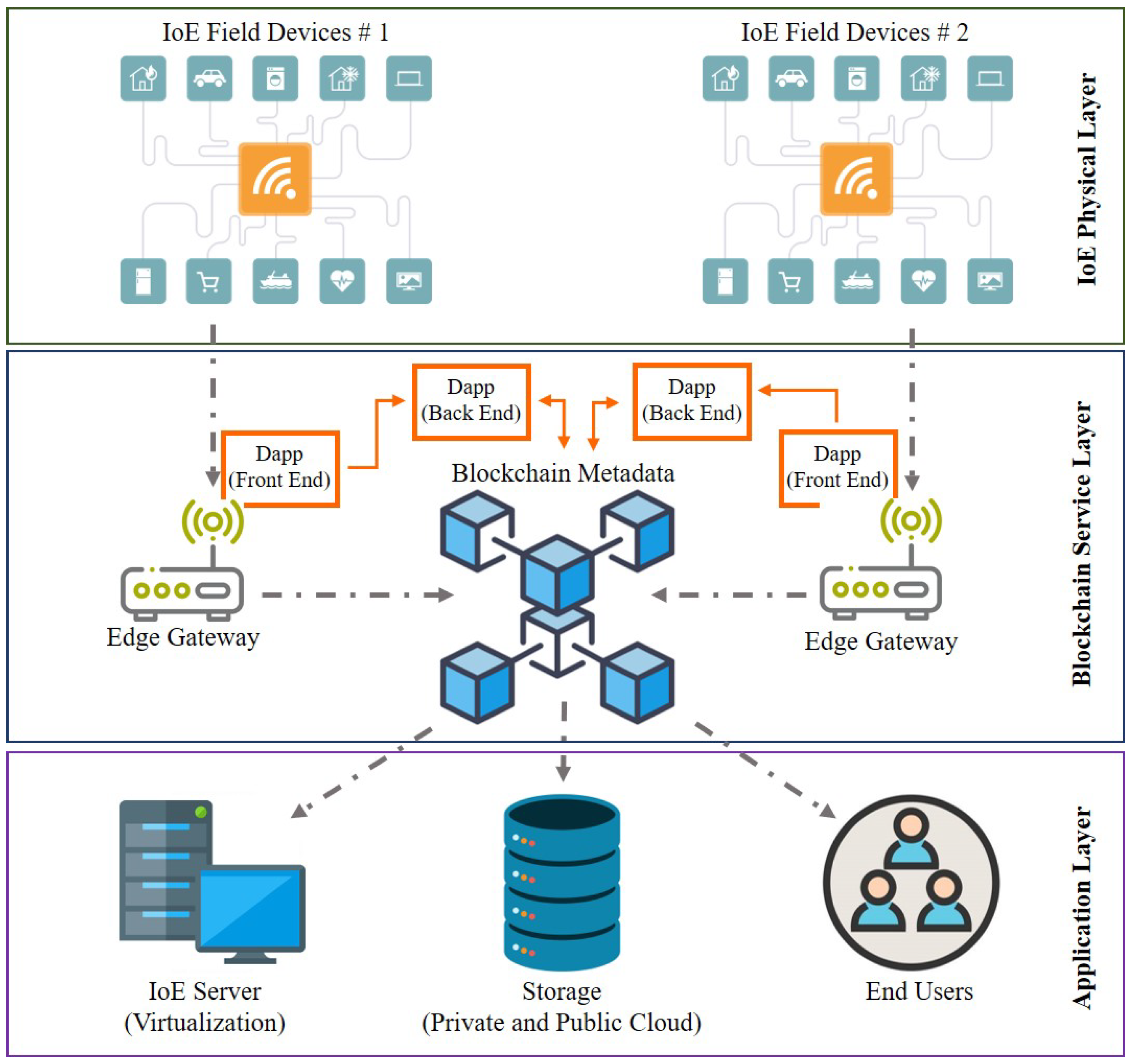
5. Proof-of-PUF Authentication in IoE
- Key storage and key vault in high-security and mass-volume edge devices
- Secure cloud integration (OT/IT Convergence)
- Preventing reverse engineering of IP and software
- Combating counterfeiting and cloned devices
- Securing FPGAs and ASICs
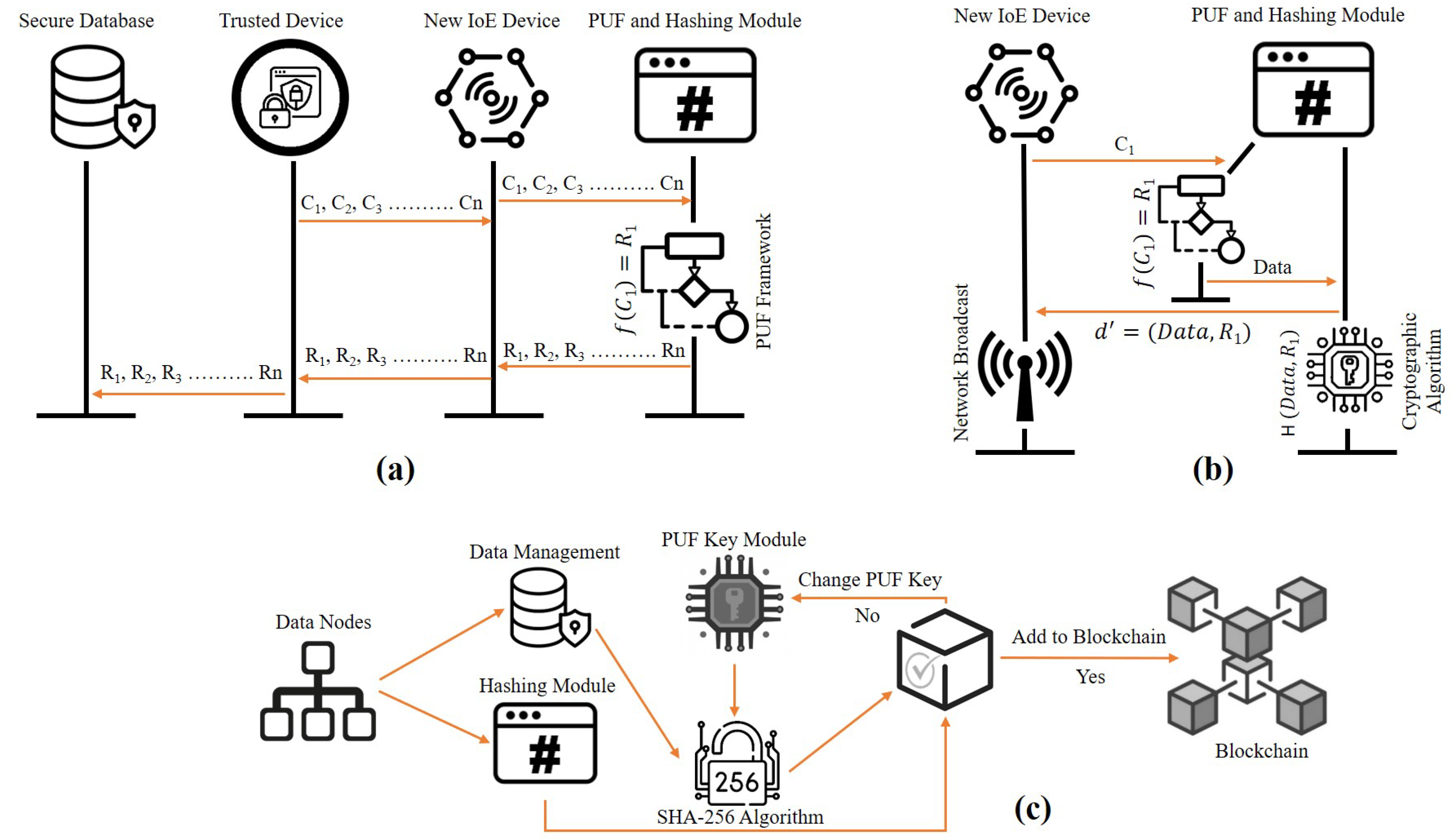
5.1. Hardware Assisted Proof-of-PUF Authentication
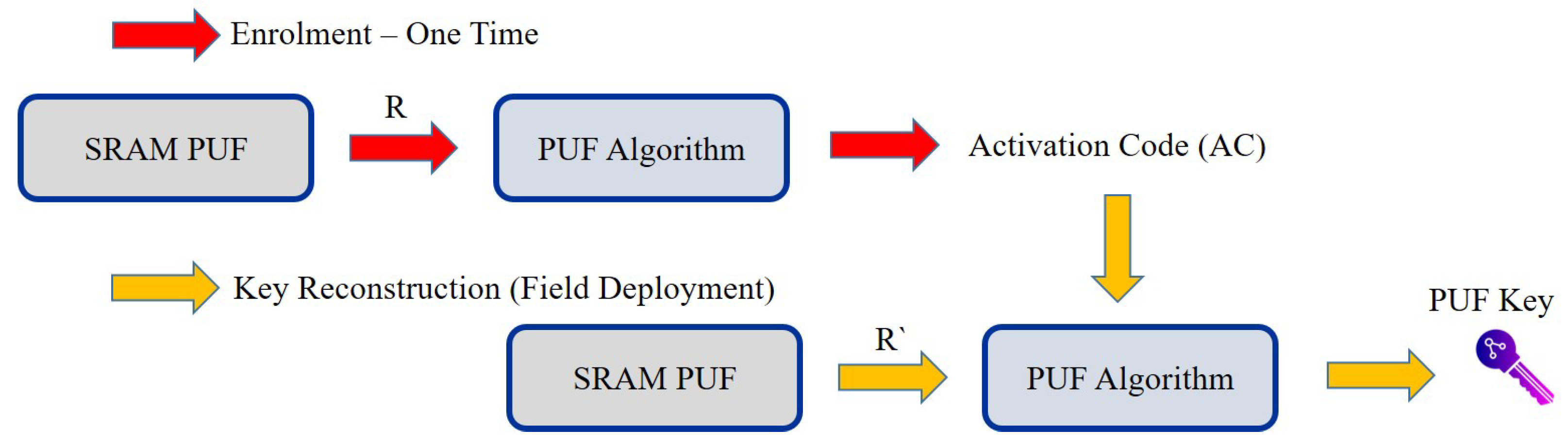
5.2. Enrolment and Authentication Steps in Proof-of-PUF Authentication
5.3. Hardware Implementation of PUFChain
6. Applications and Use-Cases
- Authentication: PUFs on devices can be used for authentication and binding hardware to software platforms, secure key storage, key-less secure communication in the OT/IT convergence. Two different schemes of authentication exist, namely client authentication and server authentication, both being based on the CRPs.
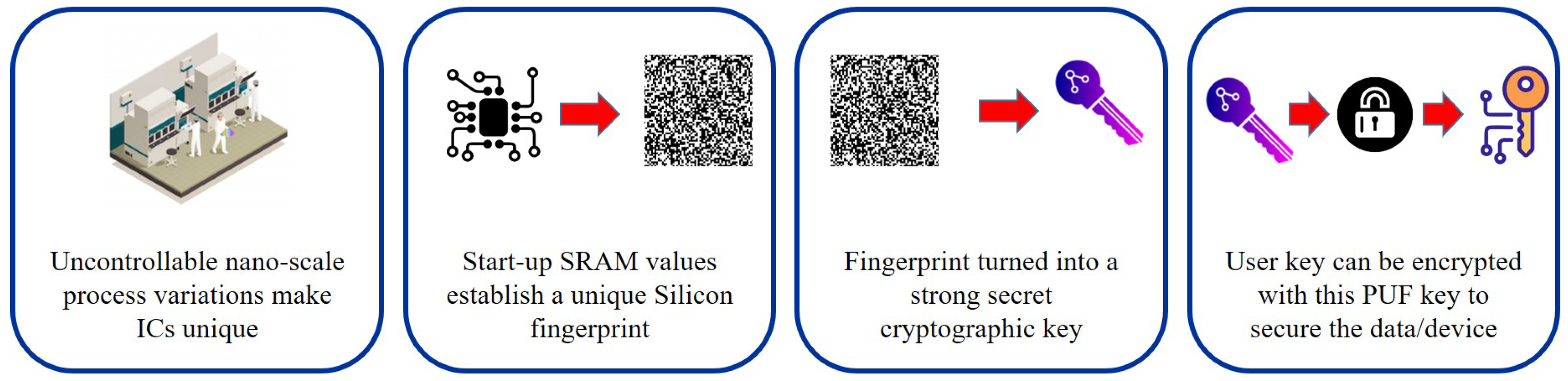
- Device Identification: The use of PUFs for device identification purposes effectively turns the device into the authentication token. It reduces the necessity to store cryptographic keys and look-up tables inside the device, which can be a cyber threat and adversary can extract cryptographic material from nonvolatile memory. Instead, the PUF device generates an transient key “on-the-fly” on the basis of it‘s unique fingerprint, minimising the attack surface to extract the key.
- Random Number Generation: An important building block for many cryptographic systems is the random number generator. Random numbers with high entropy are required in these frameworks, because they are unclonable for potential attackers. Since an interesting source of randomness is readily available in PUFs due to semiconductor manufacturing process. This property can be exploited to use PUF as a truly random number generator.
- Secure Environment: The idea of this application is to provide hybrid software-hardware security and generate a cryptographic key. Subsequently, the key is used to decrypt software, which is installed on the chip. The basic function is to decrypt the boot-loader, which is executed first during PUF start-up or embedded devices. After the boot-loader has been decrypted using the key, derived from the PUF response, it subsequently unlocks the kernel, which in turn decrypts user space applications.
- IP Protection: The integrated circuit (IC) design flow is globalised due to increase in design, fabrication, testing, and verification costs. While globalisation has provided cost benefits and reduced the time-to-market, it has introduced several attacks such as piracy, malicious modifications, and counterfeiting. IP of the devices can make use of unique PUFs fingerprint to protect the devices.
IC Traceability via PUF and Blockchain (Use-Case)
7. Current Challenges and Future Research
- Blockchain Design Types: Decision from the energy utilities of whether your Blockchain design will be a public Blockchain (generally open to participation by anyone and not permissioned), private Blockchain (involving limited participation and having permission structures), or a hybrid (Blockchain systems with both public and private designs). Specially, privacy laws and data jurisdiction/sovereignty should be considered for all of the digital data on the system.
- Scalability: One major technology challenge of Blockchain and PUF is related to the technical scalability and integration of the network which can put a strain on the adoption process, especially for public Blockchains. As more and more edge devices are integrated into the legacy energy networks, they need to be verified, authenticated, and orchestrated with existing Blockchain network.
- Standardisation and Interoperability: Another vital challenge is the lack of interoperability between the large number of Blockchain networks that coexist in the same smart grid domain. The lack of such uniformity across Blockchain frameworks also takes away consistency from basic processes like security, making network wide adoption an almost impracticable task.
- Seamless Integration with IoE: This is the biggest challenge for energy utilities and IoE systems to integrate the advancements with legacy systems. In most cases, if they decide to use Blockchain and PUF, the organisations are required to completely restructure their classical system or design a way to successfully integrate the two technologies.
- Data Sharing and Access: Sharing and access to critical monitoring data is subject to various privacy, legal, and regulatory laws. Decisions need to be made about what type of data will be shared with the Blockchain participants. Thoughtful network architecture is required to see if data will be stored on-chain, offchain or on a side-chain, and the type of permission structures that will be utilised.
- Productivity Paradox: The effectiveness with which PUF and Blockchain networks can execute peer-to-peer data transfer comes at a high aggregate cost/bandwidth, which is greater for a dense edge system. This inefficiency come into play because each node performs the same tasks as every other node on it’s own copy of the data in an attempt to be the first to find a solution.
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| 5G | Fifth Generation Cellular Network |
| AES | Advanced Encryption Standard |
| ASICS | Application-Specific Integrated Circuits |
| AI | Artificial Intelligence |
| BaaS | Blockchain-as-a-Service |
| CAGR | Compound Annual Growth Rate |
| CAPEX | Capital Expenses |
| CPS | Cyber Physical System |
| CRPS | Challenge-Response Pairs |
| CS | Cybersecurity |
| DAppss | Dated, Achievable, Personal, Positive and Specific |
| DLT | Distributed Ledger Technology |
| DNOs | Distribution Network Operators |
| DPoS | Delegated Proof-of-Stake |
| DTs | Digital Twins |
| DUT | Device Under Test |
| E2E | End-to-End |
| EEA | Enterprise Ethereum Alliance |
| EMC | Electromagnetic Compatibility |
| FIB | Focused Ion Beam |
| FPGAs | Field Programmable Gate Arrays |
| ICs | Integrated Circuits |
| ICT | Information and Communication Technology |
| IoE | Internet-of-Energy |
| IIoT | Industrial Internet-of-Things |
| IoT | Internet-of-Things |
| IP | Intellectual Property |
| ISO | International Organization for Standardization |
| IT | Informational Technology |
| ITU-T | International Telecommunication Union |
| LTE | Long Term Evaluation |
| LPWAN | Low-Power Wide-Area Network |
| MAC | Message Authentication Code |
| MITM | Man-in-the-Middle |
| NVM | Non-Volatile Memories |
| OPEX | Operational Expenses |
| OT | Operational Technology |
| PBFT | Practical Byzantine Fault Tolerance |
| PKI | Public Key Infrastructure |
| PoP | Proof-of-Physical Unclonable Function |
| PoS | Proof-of-Stake |
| PoW | Proof-of-Work |
| PUF | Physical Unclonable Function |
| PUFChain | Physical Unclonable Function assisted Blockchain |
| REST | Representational State Transfer |
| ROM | Read-Only-Memory |
| SCADA | Supervisory Control and Data Acquisition |
| SDOs | Standards Developing Organization |
| SRAM | Static Random-Access Memory |
| TRNGs | True Random Number Generators |
| WLP | Web Ledger Protocol |
References
- Bui, N.; Castellani, A.P.; Casari, P.; Zorzi, M. The internet of energy: A web-enabled smart grid system. IEEE Netw. 2012, 26, 39–45. [Google Scholar] [CrossRef]
- Moness, M.; Moustafa, A.M. A Survey of Cyber-Physical Advances and Challenges of Wind Energy Conversion Systems: Prospects for Internet of Energy. IEEE Internet Things J. 2016, 3, 134–145. [Google Scholar] [CrossRef]
- Shit, R.C.; Sharma, S.; Puthal, D.; Zomaya, A.Y. Location of Things (LoT): A Review and Taxonomy of Sensors Localization in IoT Infrastructure. IEEE Commun. Surv. Tutor. 2018, 20, 2028–2061. [Google Scholar] [CrossRef]
- Bedi, G.; Venayagamoorthy, G.K.; Singh, R.; Brooks, R.R.; Wang, K. Review of Internet of Things (IoT) in Electric Power and Energy Systems. IEEE Internet Things J. 2018, 5, 847–870. [Google Scholar] [CrossRef]
- Ma, M.; Wang, P.; Chu, C. Data Management for Internet of Things: Challenges, Approaches and Opportunities. In Proceedings of the 2013 IEEE International Conference on Green Computing and Communications and IEEE Internet of Things and IEEE Cyber, Physical and Social Computing, Beijing, China, 20–23 August 2013; pp. 1144–1151. [Google Scholar]
- Ma, Z.; Xie, J.; Li, H.; Sun, Q.; Si, Z.; Zhang, J.; Guo, J. The Role of Data Analysis in the Development of Intelligent Energy Networks. IEEE Netw. 2017, 31, 88–95. [Google Scholar] [CrossRef]
- Vermesan, O.; Blystad, L.C.; Zafalon, R.; Moscatelli, A.; Kriegel, K.; Mock, R.; John, R.; Ottella, M.; Perlo, P. Internet of Energy—Connecting Energy Anywhere Anytime. In Advanced Microsystems for Automotive Applications 2011; Meyer, G., Valldorf, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 33–48. [Google Scholar]
- Fang, X.; Misra, S.; Xue, G.; Yang, D. Smart Grid—The New and Improved Power Grid: A Survey. IEEE Commun. Surv. Tutor. 2012, 14, 944–980. [Google Scholar] [CrossRef]
- Farhangi, H. The path of the smart grid. IEEE Power Energy Mag. 2010, 8, 18–28. [Google Scholar] [CrossRef]
- Gungor, V.C.; Sahin, D.; Kocak, T.; Ergut, S.; Buccella, C.; Cecati, C.; Hancke, G.P. Smart Grid Technologies: Communication Technologies and Standards. IEEE Trans. Ind. Inform. 2011, 7, 529–539. [Google Scholar] [CrossRef]
- Wang, K.; Wang, Y.; Hu, X.; Sun, Y.; Deng, D.; Vinel, A.; Zhang, Y. Wireless Big Data Computing in Smart Grid. IEEE Wirel. Commun. 2017, 24, 58–64. [Google Scholar] [CrossRef]
- Combe, T.; Martin, A.; Di Pietro, R. To Docker or Not to Docker: A Security Perspective. IEEE Cloud Comput. 2016, 3, 54–62. [Google Scholar] [CrossRef]
- Blenk, A.; Basta, A.; Reisslein, M.; Kellerer, W. Survey on Network Virtualization Hypervisors for Software Defined Networking. IEEE Commun. Surv. Tutor. 2016, 18, 655–685. [Google Scholar] [CrossRef]
- Ruland, K.C.; Sassmannshausen, J.; Waedt, K.; Zivic, N. Smart grid security-an overview of standards and guidelines. Elektrotechnik Informationstechnik 2017, 134, 19–25. [Google Scholar] [CrossRef]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. Blockchain for IoT security and privacy: The case study of a smart home. In Proceedings of the 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kona, HI, USA, 13–17 March 2017; pp. 618–623. [Google Scholar]
- Hellaoui, H.; Koudil, M.; Bouabdallah, A. Energy-efficient mechanisms in security of the internet of things: A survey. Comput. Netw. 2017, 127, 173–189. [Google Scholar] [CrossRef]
- Zhabelova, G.; Vyatkin, V. Multiagent Smart Grid Automation Architecture Based on IEC 61850/61499 Intelligent Logical Nodes. IEEE Trans. Ind. Electron. 2012, 59, 2351–2362. [Google Scholar] [CrossRef]
- Zhabelova, G.; Vyatkin, V.; Dubinin, V.N. Toward Industrially Usable Agent Technology for Smart Grid Automation. IEEE Trans. Ind. Electron. 2015, 62, 2629–2641. [Google Scholar] [CrossRef]
- Yan, Y.; Qian, Y.; Sharif, H.; Tipper, D. A Survey on Smart Grid Communication Infrastructures: Motivations, Requirements and Challenges. IEEE Commun. Surv. Tutor. 2013, 15, 5–20. [Google Scholar] [CrossRef]
- Lundstrom, B.; Chakraborty, S.; Lauss, G.; Bründlinger, R.; Conklin, R. Evaluation of system-integrated smart grid devices using software- and hardware-in-the-loop. In Proceedings of the 2016 IEEE Power Energy Society Innovative Smart Grid Technologies Conference (ISGT), Minneapolis, MN, USA, 6–9 September 2016; pp. 1–5. [Google Scholar]
- Metke, A.R.; Ekl, R.L. Security Technology for Smart Grid Networks. IEEE Trans. Smart Grid 2010, 1, 99–107. [Google Scholar] [CrossRef]
- Fan, Z.; Kulkarni, P.; Gormus, S.; Efthymiou, C.; Kalogridis, G.; Sooriyabandara, M.; Zhu, Z.; Lambotharan, S.; Chin, W.H. Smart Grid Communications: Overview of Research Challenges, Solutions, and Standardization Activities. IEEE Commun. Surv. Tutor. 2013, 15, 21–38. [Google Scholar] [CrossRef]
- Saputro, N.; Akkaya, K.; Uludag, S. A survey of routing protocols for smart grid communications. Comput. Netw. 2012, 56, 2742–2771. [Google Scholar] [CrossRef]
- Lytras, M.D.; Chui, K.T. The Recent Development of Artificial Intelligence for Smart and Sustainable Energy Systems and Applications. Energies 2019, 12, 3108. [Google Scholar] [CrossRef]
- Moslehi, K.; Kumar, R. A Reliability Perspective of the Smart Grid. IEEE Trans. Smart Grid 2010, 1, 57–64. [Google Scholar] [CrossRef]
- Sharma, P.K.; Chen, M.; Park, J.H. A Software Defined Fog Node Based Distributed Blockchain Cloud Architecture for IoT. IEEE Access 2018, 6, 115–124. [Google Scholar] [CrossRef]
- Xu, T.; Wendt, J.B.; Potkonjak, M. Security of IoT systems: Design challenges and opportunities. In Proceedings of the 2014 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), San Jose, CA, USA, 2–6 November 2014; pp. 417–423. [Google Scholar]
- Alaba, F.A.; Othman, M.; Hashem, I.A.T.; Alotaibi, F. Internet of Things security: A survey. J. Netw. Comput. Appl. 2017, 88, 10–28. [Google Scholar] [CrossRef]
- Radoglou Grammatikis, P.I.; Sarigiannidis, P.G.; Moscholios, I.D. Securing the Internet of Things: Challenges, threats and solutions. Internet Things 2019, 5, 41–70. [Google Scholar] [CrossRef]
- Prinsloo, J.; Sinha, S.; von Solms, B. A Review of Industry 4.0 Manufacturing Process Security Risks. Appl. Sci. 2019, 9, 5105. [Google Scholar] [CrossRef]
- Sadeghi, A.; Wachsmann, C.; Waidner, M. Security and privacy challenges in industrial Internet of Things. In Proceedings of the 2015 52nd ACM/EDAC/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 8–12 June 2015; pp. 1–6. [Google Scholar]
- Hao, P.; Wang, X.; Shen, W. A Collaborative PHY-Aided Technique for End-to-End IoT Device Authentication. IEEE Access 2018, 6, 42279–42293. [Google Scholar] [CrossRef]
- Zhang, Y.; Xu, L.; Dong, Q.; Wang, J.; Blaauw, D.; Sylvester, D. Recryptor: A Reconfigurable Cryptographic Cortex-M0 Processor With In-Memory and Near-Memory Computing for IoT Security. IEEE J. Solid-State Circuits 2018, 53, 995–1005. [Google Scholar] [CrossRef]
- Khari, M.; Garg, A.K.; Gandomi, A.H.; Gupta, R.; Patan, R.; Balusamy, B. Securing Data in Internet of Things (IoT) Using Cryptography and Steganography Techniques. IEEE Trans. Syst. Man Cybern. Syst. 2020, 50, 73–80. [Google Scholar] [CrossRef]
- Almajed, H.N.; Almogren, A.S. SE-Enc: A Secure and Efficient Encoding Scheme Using Elliptic Curve Cryptography. IEEE Access 2019, 7, 175865–175878. [Google Scholar] [CrossRef]
- Li, R.; Song, T.; Mei, B.; Li, H.; Cheng, X.; Sun, L. Blockchain for Large-Scale Internet of Things Data Storage and Protection. IEEE Trans. Serv. Comput. 2019, 12, 762–771. [Google Scholar] [CrossRef]
- Shen, M.; Tang, X.; Zhu, L.; Du, X.; Guizani, M. Privacy-Preserving Support Vector Machine Training Over Blockchain-Based Encrypted IoT Data in Smart Cities. IEEE Internet Things J. 2019, 6, 7702–7712. [Google Scholar] [CrossRef]
- Duan, Y.; Sun, X.; Che, H.; Cao, C.; Li, Z.; Yang, X. Modeling Data, Information and Knowledge for Security Protection of Hybrid IoT and Edge Resources. IEEE Access 2019, 7, 99161–99176. [Google Scholar] [CrossRef]
- Underwood, S. Blockchain beyond Bitcoin. Commun. ACM 2016, 59, 15–17. [Google Scholar] [CrossRef]
- Huh, S.; Cho, S.; Kim, S. Managing IoT devices using blockchain platform. In Proceedings of the 2017 19th International Conference on Advanced Communication Technology (ICACT), Bongpyeong, Korea, 19–22 February 2017; pp. 464–467. [Google Scholar]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Ángel Prada-Delgado, M.; Baturone, I.; Dittmann, G.; Jelitto, J.; Kind, A. PUF-derived IoT identities in a zero-knowledge protocol for blockchain. Internet Things 2020, 9, 100057. [Google Scholar] [CrossRef]
- Herder, C.; Yu, M.; Koushanfar, F.; Devadas, S. Physical Unclonable Functions and Applications: A Tutorial. Proc. IEEE 2014, 102, 1126–1141. [Google Scholar] [CrossRef]
- Shamsoshoara, A.; Korenda, A.; Afghah, F.; Zeadally, S. A survey on physical unclonable function (PUF)-based security solutions for Internet of Things. Comput. Netw. 2020, 183, 107593. [Google Scholar] [CrossRef]
- Mpitziopoulos, A.; Gavalas, D.; Konstantopoulos, C.; Pantziou, G. A survey on jamming attacks and countermeasures in WSNs. IEEE Commun. Surv. Tutor. 2009, 11, 42–56. [Google Scholar] [CrossRef]
- Becher, A.; Benenson, Z.; Dornseif, M. Tampering with Motes: Real-World Physical Attacks on Wireless Sensor Networks. In Security in Pervasive Computing; Clark, J.A., Paige, R.F., Polack, F.A.C., Brooke, P.J., Eds.; Springer Berlin Heidelberg: Berlin/Heidelberg, Germany, 2006; pp. 104–118. [Google Scholar]
- Bogdanov, A. Multiple-Differential Side-Channel Collision Attacks on AES. In Cryptographic Hardware and Embedded Systems—CHES 2008; Oswald, E., Rohatgi, P., Eds.; Springer: Berlin/Heidelberg, Germany, 2008; pp. 30–44. [Google Scholar]
- Heer, T.; Garcia-Morchon, O.; Hummen, R.; Keoh, S.L.; Kumar, S.S.; Wehrle, K. Security Challenges in the IP-based Internet of Things. Wirel. Pers. Commun. 2011, 61, 527–542. [Google Scholar] [CrossRef]
- Liu, J.; Xiao, Y.; Chen, C.L.P. Authentication and Access Control in the Internet of Things. In Proceedings of the 2012 32nd International Conference on Distributed Computing Systems Workshops, Macau, China, 18–21 June 2012; pp. 588–592. [Google Scholar]
- Hossain, M.M.; Fotouhi, M.; Hasan, R. Towards an Analysis of Security Issues, Challenges, and Open Problems in the Internet of Things. In Proceedings of the 2015 IEEE World Congress on Services, New York, NY, USA, 27 June–2 July 2015; pp. 21–28. [Google Scholar]
- Bysani, L.K.; Turuk, A.K. A Survey on Selective Forwarding Attack in Wireless Sensor Networks. In Proceedings of the 2011 International Conference on Devices and Communications (ICDeCom), Mesra, India, 24–25 February 2011; pp. 1–5. [Google Scholar]
- Krontiris, I.; Giannetsos, T.; Dimitriou, T. Launching a Sinkhole Attack in Wireless Sensor Networks; The Intruder Side. In Proceedings of the 2008 IEEE International Conference on Wireless and Mobile Computing, Networking and Communications, Avignon, France, 12–14 October 2008; pp. 526–531. [Google Scholar]
- Pongle, P.; Chavan, G. A survey: Attacks on RPL and 6LoWPAN in IoT. In Proceedings of the 2015 International Conference on Pervasive Computing (ICPC), Pune, India, 8–10 January 2015; pp. 1–6. [Google Scholar]
- Sankara Narayanan, S.; Murugaboopathi, G. Modified secure AODV protocol to prevent wormhole attack in MANET. Concurr. Comput. Pract. Exp. 2020, 32, e5017. [Google Scholar] [CrossRef]
- Magotra, S.; Kumar, K. Detection of HELLO flood attack on LEACH protocol. In Proceedings of the 2014 IEEE International Advance Computing Conference (IACC), Gurgaon, India, 21–22 February 2014; pp. 193–198. [Google Scholar]
- Duggempudi, S.R.; Anil Kumar, V.; Sethumadhavan, M. Acknowledgement Spoofing at Kernel Level and TCP Sender Behaviour Analysis. In Soft Computing and Signal Processing; Reddy, V.S., Prasad, V.K., Wang, J., Reddy, K.T.V., Eds.; Springer: Singapore, 2020; pp. 673–681. [Google Scholar]
- Siris, V.A.; Papagalou, F. Application of anomaly detection algorithms for detecting SYN flooding attacks. In Proceedings of the IEEE Global Telecommunications Conference (GLOBECOM ’04), Dallas, TX, USA, 29 November–3 December 2004; Volume 4, pp. 2050–2054. [Google Scholar]
- Lo, N.W.; Yeh, K. De-synchronization attack on RFID authentication protocols. In Proceedings of the 2010 International Symposium On Information Theory Its Applications, Taichung, Taiwan, 17–20 October 2010; pp. 566–570. [Google Scholar]
- Joo, D.; Kim, T. Managing clock skews in clock trees with local clock skew requirements using adjustable delay buffers. In Proceedings of the 2015 International SoC Design Conference (ISOCC), Gyungju, Korea, 2–5 November 2015; pp. 137–138. [Google Scholar]
- Buttyan, L.; Schaffer, P.; Vajda, I. Resilient aggregation with attack detection in sensor networks. In Proceedings of the Fourth Annual IEEE International Conference on Pervasive Computing and Communications Workshops (PERCOMW’06), Pisa, Italy, 13–17 March 2006; pp. 5–336. [Google Scholar]
- Verma, S.; Kawamoto, Y.; Fadlullah, Z.M.; Nishiyama, H.; Kato, N. A Survey on Network Methodologies for Real-Time Analytics of Massive IoT Data and Open Research Issues. IEEE Commun. Surv. Tutor. 2017, 19, 1457–1477. [Google Scholar] [CrossRef]
- Hossein Motlagh, N.; Mohammadrezaei, M.; Hunt, J.; Zakeri, B. Internet of Things (IoT) and the Energy Sector. Energies 2020, 13, 494. [Google Scholar] [CrossRef]
- Liu, Y.; Yang, C.; Jiang, L.; Xie, S.; Zhang, Y. Intelligent Edge Computing for IoT-Based Energy Management in Smart Cities. IEEE Netw. 2019, 33, 111–117. [Google Scholar] [CrossRef]
- Patel, P.; Intizar Ali, M.; Sheth, A. On Using the Intelligent Edge for IoT Analytics. IEEE Intell. Syst. 2017, 32, 64–69. [Google Scholar] [CrossRef]
- Huang, M.; Liu, A.; Xiong, N.N.; Wang, T.; Vasilakos, A.V. A Low-Latency Communication Scheme for Mobile Wireless Sensor Control Systems. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 317–332. [Google Scholar] [CrossRef]
- Mekki, K.; Bajic, E.; Chaxel, F.; Meyer, F. A comparative study of LPWAN technologies for large-scale IoT deployment. ICT Express 2019, 5, 1–7. [Google Scholar] [CrossRef]
- Zhou, W.; Jia, Y.; Peng, A.; Zhang, Y.; Liu, P. The Effect of IoT New Features on Security and Privacy: New Threats, Existing Solutions, and Challenges Yet to Be Solved. IEEE Internet Things J. 2019, 6, 1606–1616. [Google Scholar] [CrossRef]
- Trump, B.D.; Florin, M.; Matthews, H.S.; Sicker, D.; Linkov, I. Governing the Use of Blockchain and Distributed Ledger Technologies: Not One-Size-Fits-All. IEEE Eng. Manag. Rev. 2018, 46, 56–62. [Google Scholar] [CrossRef]
- Belotti, M.; Božić, N.; Pujolle, G.; Secci, S. A Vademecum on Blockchain Technologies: When, Which, and How. IEEE Commun. Surv. Tutor. 2019, 21, 3796–3838. [Google Scholar] [CrossRef]
- Nofer, M.; Gomber, P.; Hinz, O.; Schiereck, D. Blockchain. Bus. Inf. Syst. Eng. 2017, 59, 183–187. [Google Scholar] [CrossRef]
- Wang, M.; Duan, M.; Zhu, J. Research on the Security Criteria of Hash Functions in the Blockchain. In Proceedings of the 2nd ACM Workshop on Blockchains, Cryptocurrencies, and Contracts, Incheon, Korea, 4 June 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 47–55. [Google Scholar]
- Mingxiao, D.; Xiaofeng, M.; Zhe, Z.; Xiangwei, W.; Qijun, C. A review on consensus algorithm of blockchain. In Proceedings of the 2017 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Banff, AB, Canada, 5–8 October 2017; pp. 2567–2572. [Google Scholar]
- Huang, K.; Zhang, X.; Mu, Y.; Rezaeibagha, F.; Du, X.; Guizani, N. Achieving Intelligent Trust-Layer for Internet-of-Things via Self-Redactable Blockchain. IEEE Trans. Ind. Inform. 2020, 16, 2677–2686. [Google Scholar] [CrossRef]
- Wang, Q.; Jia, Z.; Wang, T.; Shen, Z.; Zhao, M.; Chen, R.; Shao, Z. A Highly Parallelized PIM-Based Accelerator for Transaction-Based Blockchain in IoT Environment. IEEE Internet Things J. 2020, 7, 4072–4083. [Google Scholar] [CrossRef]
- Mylrea, M.; Gourisetti, S.N.G. Blockchain for Supply Chain Cybersecurity, Optimization and Compliance. In Proceedings of the 2018 Resilience Week (RWS), Denver, CO, USA, 20–23 August 2018; pp. 70–76. [Google Scholar]
- Mylrea, M.; Gourisetti, S.N.G. Blockchain for smart grid resilience: Exchanging distributed energy at speed, scale and security. In Proceedings of the 2017 Resilience Week (RWS), Wilmington, DE, USA, 18–22 September 2017; pp. 18–23. [Google Scholar]
- Peck, M.E.; Wagman, D. Energy trading for fun and profit buy your neighbor’s rooftop solar power or sell your own-it’ll all be on a blockchain. IEEE Spectr. 2017, 54, 56–61. [Google Scholar] [CrossRef]
- Mylrea, M.; Gupta Gourisetti, S.N.; Bishop, R.; Johnson, M. Keyless Signature Blockchain Infrastructure: Facilitating NERC CIP Compliance and Responding to Evolving Cyber Threats and Vulnerabilities to Energy Infrastructure. In Proceedings of the 2018 IEEE/PES Transmission and Distribution Conference and Exposition (T & D), Denver, CO, USA, 16–19 April 2018; pp. 1–9. [Google Scholar]
- Andoni, M.; Robu, V.; Flynn, D.; Abram, S.; Geach, D.; Jenkins, D.; McCallum, P.; Peacock, A. Blockchain technology in the energy sector: A systematic review of challenges and opportunities. Renew. Sustain. Energy Rev. 2019, 100, 143–174. [Google Scholar] [CrossRef]
- Sanseverino, E.R.; Di Silvestre, M.L.; Gallo, P.; Zizzo, G.; Ippolito, M. The Blockchain in Microgrids for Transacting Energy and Attributing Losses. In Proceedings of the 2017 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Exeter, UK, 21–23 June 2017; pp. 925–930. [Google Scholar]
- Lei, K.; Du, M.; Huang, J.; Jin, T. Groupchain: Towards a Scalable Public Blockchain in Fog Computing of IoT Services Computing. IEEE Trans. Serv. Comput. 2020, 13, 252–262. [Google Scholar] [CrossRef]
- Zhaofeng, M.; Xiaochang, W.; Jain, D.K.; Khan, H.; Hongmin, G.; Zhen, W. A Blockchain-Based Trusted Data Management Scheme in Edge Computing. IEEE Trans. Ind. Inform. 2020, 16, 2013–2021. [Google Scholar] [CrossRef]
- Hasan, H.R.; Salah, K.; Jayaraman, R.; Omar, M.; Yaqoob, I.; Pesic, S.; Taylor, T.; Boscovic, D. A Blockchain-Based Approach for the Creation of Digital Twins. IEEE Access 2020, 8, 34113–34126. [Google Scholar] [CrossRef]
- Memon, R.A.; Li, J.P.; Nazeer, M.I.; Khan, A.N.; Ahmed, J. DualFog-IoT: Additional Fog Layer for Solving Blockchain Integration Problem in Internet of Things. IEEE Access 2019, 7, 169073–169093. [Google Scholar] [CrossRef]
- Fu, Y.; Zhu, J. Big Production Enterprise Supply Chain Endogenous Risk Management Based on Blockchain. IEEE Access 2019, 7, 15310–15319. [Google Scholar] [CrossRef]
- Peck, M.E. Blockchain world - Do you need a blockchain? This chart will tell you if the technology can solve your problem. IEEE Spectr. 2017, 54, 38–60. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; pp. 557–564. [Google Scholar]
- Marsalek, A.; Zefferer, T. A Correctable Public Blockchain. In Proceedings of the 2019 18th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/13th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE), Rotorua, New Zealand, 5–8 August 2019; pp. 554–561. [Google Scholar]
- Huang, D.; Ma, X.; Zhang, S. Performance Analysis of the Raft Consensus Algorithm for Private Blockchains. IEEE Trans. Syst. Man Cybern. Syst. 2020, 50, 172–181. [Google Scholar] [CrossRef]
- Zhang, X.; Chen, X. Data Security Sharing and Storage Based on a Consortium Blockchain in a Vehicular Ad-hoc Network. IEEE Access 2019, 7, 58241–58254. [Google Scholar] [CrossRef]
- Fan, M.; Zhang, X. Consortium Blockchain Based Data Aggregation and Regulation Mechanism for Smart Grid. IEEE Access 2019, 7, 35929–35940. [Google Scholar] [CrossRef]
- Bach, L.M.; Mihaljevic, B.; Zagar, M. Comparative analysis of blockchain consensus algorithms. In Proceedings of the 2018 41st International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 21–25 May 2018; pp. 1545–1550. [Google Scholar]
- Gramoli, V. From blockchain consensus back to Byzantine consensus. Future Gener. Comput. Syst. 2020, 107, 760–769. [Google Scholar] [CrossRef]
- Sankar, L.S.; Sindhu, M.; Sethumadhavan, M. Survey of consensus protocols on blockchain applications. In Proceedings of the 2017 4th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 6–7 January 2017; pp. 1–5. [Google Scholar]
- Zoican, S.; Vochin, M.; Zoican, R.; Galatchi, D. Blockchain and Consensus Algorithms in Internet of Things. In Proceedings of the 2018 International Symposium on Electronics and Telecommunications (ISETC), Timisoara, Romania, 8–9 November 2018; pp. 1–4. [Google Scholar]
- Kumar, G.; Saha, R.; Rai, M.K.; Thomas, R.; Kim, T. Proof-of-Work Consensus Approach in Blockchain Technology for Cloud and Fog Computing Using Maximization-Factorization Statistics. IEEE Internet Things J. 2019, 6, 6835–6842. [Google Scholar] [CrossRef]
- Cho, H. ASIC-Resistance of Multi-Hash Proof-of-Work Mechanisms for Blockchain Consensus Protocols. IEEE Access 2018, 6, 66210–66222. [Google Scholar] [CrossRef]
- Niya, S.R.; Schiller, E.; Cepilov, I.; Maddaloni, F.; Aydinli, K.; Surbeck, T.; Bocek, T.; Stiller, B. Adaptation of Proof-of-Stake-based Blockchains for IoT Data Streams. In Proceedings of the 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Seoul, Korea, 14–17 May 2019; pp. 15–16. [Google Scholar]
- Bentov, I.; Lee, C.; Mizrahi, A.; Rosenfeld, M. Proof of Activity: Extending Bitcoin’s Proof of Work via Proof of Stake [Extended Abstract]y. SIGMETRICS Perform. Eval. Rev. 2014, 42, 34–37. [Google Scholar] [CrossRef]
- Denning, D.E.; Branstad, D.K. A Taxonomy for Key Escrow Encryption Systems. Commun. ACM 1996, 39, 34–40. [Google Scholar] [CrossRef]
- O’Neil, P.E. The Escrow Transactional Method. ACM Trans. Database Syst. 1986, 11, 405–430. [Google Scholar] [CrossRef]
- Sukhwani, H.; Martínez, J.M.; Chang, X.; Trivedi, K.S.; Rindos, A. Performance Modeling of PBFT Consensus Process for Permissioned Blockchain Network (Hyperledger Fabric). In Proceedings of the 2017 IEEE 36th Symposium on Reliable Distributed Systems (SRDS), Hong Kong, China, 26–29 September 2017; pp. 253–255. [Google Scholar]
- Fan, X.; Chai, Q. Roll-DPoS: A Randomized Delegated Proof of Stake Scheme for Scalable Blockchain-Based Internet of Things Systems. In Proceedings of the 15th EAI International Conference on Mobile and Ubiquitous Systems: Computing, Networking and Services, New York, NY, USA, 5–7 November 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 482–484. [Google Scholar]
- Benji, M.; Sindhu, M. A Study on the Corda and Ripple Blockchain Platforms. In Advances in Big Data and Cloud Computing; Peter, J.D., Alavi, A.H., Javadi, B., Eds.; Springer: Singapore, 2019; pp. 179–187. [Google Scholar]
- Di Silvestre, M.L.; Gallo, P.; Ippolito, M.G.; Sanseverino, E.R.; Sciumè, G.; Zizzo, G. An Energy Blockchain, a Use Case on Tendermint. In Proceedings of the 2018 IEEE International Conference on Environment and Electrical Engineering and 2018 IEEE Industrial and Commercial Power Systems Europe (EEEIC/I CPS Europe), Palermo, Italy, 12–15 June 2018; pp. 1–5. [Google Scholar]
- IEEE Blockchain Standards, P2418 Series. 2018. Available online: https://blockchain.ieee.org/standards. (accessed on 31 August 2020).
- Lima, C. Developing Open and Interoperable DLTBlockchain Standards [Standards]. Computer 2018, 51, 106–111. [Google Scholar] [CrossRef]
- Anjum, A.; Sporny, M.; Sill, A. Blockchain Standards for Compliance and Trust. IEEE Cloud Comput. 2017, 4, 84–90. [Google Scholar] [CrossRef]
- Blockchain and Distributed Ledger Technologies, ISO/TC307. Available online: https://www.iso.org/committee/6266604.html (accessed on 31 August 2020).
- Enterprise Ethereum Alliance. 2018. Available online: https://entethalliance.org/ (accessed on 2 September 2020).
- International Telecommunication Union, Focus Group on Application of Distributed Ledger Technology. 2018. Available online: https://www.itu.int/en/ITU-D/Statistics/Pages/publications/misr2018.aspx (accessed on 2 September 2020).
- W3C Community and Business, Blockchain Community Group. 2018. Available online: https://www.w3.org/community/blockchain/ (accessed on 2 September 2020).
- Gordon, W.J.; Catalini, C. Blockchain Technology for Healthcare: Facilitating the Transition to Patient-Driven Interoperability. Comput. Struct. Biotechnol. J. 2018, 16, 224–230. [Google Scholar] [CrossRef] [PubMed]
- Swan, M. Chapter Five–Blockchain for Business: Next-Generation Enterprise Artificial Intelligence Systems. In Blockchain Technology: Platforms, Tools and Use Cases; Advances in Computers; Raj, P., Deka, G.C., Eds.; Elsevier: New York, NY, USA, 2018; Volume 111, pp. 121–162. [Google Scholar]
- Lin, H.; Bergmann, N. IoT Privacy and Security Challenges for Smart Home Environments. Information 2016, 7, 44. [Google Scholar] [CrossRef]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A Survey on Security and Privacy Issues in Internet-of-Things. IEEE Internet Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Arias, O.; Wurm, J.; Hoang, K.; Jin, Y. Privacy and Security in Internet of Things and Wearable Devices. IEEE Trans. Multi-Scale Comput. Syst. 2015, 1, 99–109. [Google Scholar] [CrossRef]
- Haowen, C.; Perrig, A. Security and privacy in sensor networks. Computer 2003, 36, 103–105. [Google Scholar] [CrossRef]
- Hunter, P. Hardware-based security: FPGA-based devices. Comput. Fraud Secur. 2004, 2004, 11–12. [Google Scholar]
- Asif, R.; Buchanan, W.J. Quantum-to-the-Home: Achieving Gbits/s Secure Key Rates via Commercial Off-the-Shelf Telecommunication Equipment. Secur. Commun. Netw. 2017, 2017, 7616847. [Google Scholar] [CrossRef]
- Rivest, R.L.; Shamir, A.; Adleman, L. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Chen, Y.; Ku, W. Self-Encryption Scheme for Data Security in Mobile Devices. In Proceedings of the 2009 6th IEEE Consumer Communications and Networking Conference, Las Vegas, NV, USA, 10–13 January 2009; pp. 1–5. [Google Scholar]
- Suh, G.E.; Devadas, S. Physical Unclonable Functions for Device Authentication and Secret Key Generation. In Proceedings of the 2007 44th ACM/IEEE Design Automation Conference, San Diego, CA, US, 4–8 June 2007; pp. 9–14. [Google Scholar]
- Yoo, S.K.; Karakoyunlu, D.; Birand, B.; Sunar, B. Improving the Robustness of Ring Oscillator TRNGs. ACM Trans. Reconfigurable Technol. Syst. 2010, 3, 1–30. [Google Scholar] [CrossRef]
- Anderson, J.H. A PUF design for secure FPGA-based embedded systems. In Proceedings of the 2010 15th Asia and South Pacific Design Automation Conference (ASP-DAC), Taipei, Taiwan, 18–21 January 2010; pp. 1–6. [Google Scholar]
- İsmail, K.; Turan Özcerit, A. The design and realization of a new high speed FPGA-based chaotic true random number generator. Comput. Electr. Eng. 2017, 58, 203–214. [Google Scholar]
- Pérez-Jiménez, M.; Sánchez, B.; Migliorini, A.; Alcarria, R. Protecting Private Communications in Cyber-Physical Systems through Physical Unclonable Functions. Electronics 2019, 8, 390. [Google Scholar] [CrossRef]
- Ibrahim, O.A.; Nair, S. Cyber-physical security using system-level PUFs. In Proceedings of the 2011 7th International Wireless Communications and Mobile Computing Conference, Istanbul, Turkey, 4–8 July 2011; pp. 1672–1676. [Google Scholar]
- Babaei, A.; Schiele, G. Physical Unclonable Functions in the Internet of Things: State of the Art and Open Challenges. Sensors 2019, 19, 3208. [Google Scholar] [CrossRef]
- Gao, Y.; Al-Sarawi, S.F.; Abbott, D. Physical unclonable functions. Nat. Electron. 2020, 3, 81–91. [Google Scholar] [CrossRef]
- Sebastian, A.; Le Gallo, M.; Khaddam-Aljameh, R.; Eleftheriou, E. Memory devices and applications for in-memory computing. Nat. Nanotechnol. 2020, 15, 529–544. [Google Scholar] [CrossRef]
- Leem, J.W.; Kim, M.S.; Choi, S.H.; Kim, S.R.; Kim, S.W.; Song, Y.M.; Young, R.J.; Kim, Y.L. Edible unclonable functions. Nat. Commun. 2020, 11, 328. [Google Scholar] [CrossRef]
- Chen, A. Utilizing the Variability of Resistive Random Access Memory to Implement Reconfigurable Physical Unclonable Functions. IEEE Electron. Device Lett. 2015, 36, 138–140. [Google Scholar] [CrossRef]
- Claes, M.; van der Leest, V.; Braeken, A. Comparison of SRAM and FF PUF in 65nm Technology. In Information Security Technology for Applications; Laud, P., Ed.; Springer: Berlin/Heidelberg, Germany, 2012; pp. 47–64. [Google Scholar]
- Saha, R.; Geetha, G.; Kumar, G.; Kim, T.H. RK-AES: An Improved Version of AES Using a New Key Generation Process with Random Keys. Secur. Commun. Netw. 2018, 2018, 9802475. [Google Scholar] [CrossRef]
- McGrath, T.; Bagci, I.E.; Wang, Z.M.; Roedig, U.; Young, R.J. A PUF taxonomy. Appl. Phys. Rev. 2019, 6, 011303. [Google Scholar] [CrossRef]
- Vijayakumar, A.; Patil, V.; Kundu, S. On Improving Reliability of SRAM-Based Physically Unclonable Functions. J. Low Power Electron. Appl. 2017, 7, 2. [Google Scholar] [CrossRef]
- Shifman, Y.; Miller, A.; Keren, O.; Weizmann, Y.; Shor, J. A Method to Improve Reliability in a 65-nm SRAM PUF Array. IEEE Solid-State Circuits Lett. 2018, 1, 138–141. [Google Scholar] [CrossRef]
- Tehranipoor, F.; Karimian, N.; Yan, W.; Chandy, J.A. DRAM-Based Intrinsic Physically Unclonable Functions for System-Level Security and Authentication. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2017, 25, 1085–1097. [Google Scholar] [CrossRef]
- Zalivaka, S.S.; Ivaniuk, A.A.; Chang, C. Reliable and Modeling Attack Resistant Authentication of Arbiter PUF in FPGA Implementation With Trinary Quadruple Response. IEEE Trans. Inf. Forensics Secur. 2019, 14, 1109–1123. [Google Scholar] [CrossRef]
- Mazady, A.; Rahman, M.T.; Forte, D.; Anwar, M. Memristor PUF—A Security Primitive: Theory and Experiment. IEEE J. Emerg. Sel. Top. Circuits Syst. 2015, 5, 222–229. [Google Scholar] [CrossRef]
- Lu, X.; Hong, L.; Sengupta, K. CMOS Optical PUFs Using Noise-Immune Process-Sensitive Photonic Crystals Incorporating Passive Variations for Robustness. IEEE J. Solid-State Circuits 2018, 53, 2709–2721. [Google Scholar] [CrossRef]
- Chellappa, S.; Clark, L.T. SRAM-Based Unique Chip Identifier Techniques. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2016, 24, 1213–1222. [Google Scholar] [CrossRef]
- Avvaru, S.V.S.; Zeng, Z.; Parhi, K.K. Homogeneous and Heterogeneous Feed-Forward XOR Physical Unclonable Functions. IEEE Trans. Inf. Forensics Secur. 2020, 15, 2485–2498. [Google Scholar] [CrossRef]
- Grubel, B.C.; Bosworth, B.T.; Kossey, M.R.; Sun, H.; Cooper, A.B.; Foster, M.A.; Foster, A.C. Silicon photonic physical unclonable function. Opt. Express 2017, 25, 12710–12721. [Google Scholar] [CrossRef]
- Skoric, B.; Schrijen, G.J.; Ophey, W.; Wolters, R.; Verhaegh, N.; van Geloven, J. Experimental Hardware for Coating PUFs and Optical PUFs. In Security with Noisy Data: On Private Biometrics, Secure Key Storage and Anti-Counterfeiting; Tuyls, P., Skoric, B., Kevenaar, T., Eds.; Springer: London, UK, 2007; pp. 255–268. [Google Scholar]
- Das, J.; Scott, K.; Rajaram, S.; Burgett, D.; Bhanja, S. MRAM PUF: A Novel Geometry Based Magnetic PUF with Integrated CMOS. IEEE Trans. Nanotechnol. 2015, 14, 436–443. [Google Scholar] [CrossRef]
- Xu, X.; Liang, H.; Huang, Z.; Jiang, C.; Ouyang, Y.; Fang, X.; Ni, T.; Yi, M. A highly reliable butterfly PUF in SRAM-based FPGAs. IEICE Electron. Express 2017. [Google Scholar] [CrossRef]
- Dong, Y.; Xu, J.; Guo, P. An Anti-interference Design based on Glitch PUF. In Proceedings of the 2019 IEEE 9th International Conference on Electronics Information and Emergency Communication (ICEIEC), Beijing, China, 12–14 July 2019; pp. 217–221. [Google Scholar]
- Kim, M.; Moon, D.; Yoo, S.; Lee, S.; Choi, Y. Investigation of Physically Unclonable Functions Using Flash Memory for Integrated Circuit Authentication. IEEE Trans. Nanotechnol. 2015, 14, 384–389. [Google Scholar] [CrossRef]
- Chen, Q.; Csaba, G.; Lugli, P.; Schlichtmann, U.; Rührmair, U. The Bistable Ring PUF: A new architecture for strong Physical Unclonable Functions. In Proceedings of the 2011 IEEE International Symposium on Hardware-Oriented Security and Trust, San Diego, CA, USA, 5–6 June 2011; pp. 134–141. [Google Scholar]
- Roberts, J.; Bagci, I.E.; Zawawi, M.A.M.; Sexton, J.; Hulbert, N.; Noori, Y.J.; Young, M.P.; Woodhead, C.S.; Missous, M.; Migliorato, M.A.; et al. Using Quantum Confinement to Uniquely Identify Devices. Sci. Rep. 2015, 5, 16456. [Google Scholar] [CrossRef] [PubMed]
- Bossuet, L.; Ngo, X.T.; Cherif, Z.; Fischer, V. A PUF Based on a Transient Effect Ring Oscillator and Insensitive to Locking Phenomenon. IEEE Trans. Emerg. Top. Comput. 2014, 2, 30–36. [Google Scholar] [CrossRef]
- Qin, S.J.; Cherry, G.; Good, R.; Wang, J.; Harrison, C.A. Semiconductor manufacturing process control and monitoring: A fab-wide framework. J. Process Control. 2006, 16, 179–191. [Google Scholar] [CrossRef]
- Clark, L.T.; Medapuram, S.B.; Kadiyala, D.K.; Brunhaver, J. Physically Unclonable Functions Using Foundry SRAM Cells. IEEE Trans. Circuits Syst. I Regul. Pap. 2019, 66, 955–966. [Google Scholar] [CrossRef]
- Colombier, B.; Bossuet, L.; Fischer, V.; Hély, D. Key Reconciliation Protocols for Error Correction of Silicon PUF Responses. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1988–2002. [Google Scholar] [CrossRef]
- Yu, M.; Devadas, S. Secure and robust error correction for physical unclonable functions. IEEE Des. Test Comput. 2010, 27, 48–65. [Google Scholar] [CrossRef]
- Bruneau, N.; Danger, J.L.; Facon, A.; Guilley, S.; Hamaguchi, S.; Hori, Y.; Kang, Y.; Schaub, A. Development of the Unified Security Requirements of PUFs During the Standardization Process. In Innovative Security Solutions for Information Technology and Communications; Lanet, J.L., Toma, C., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 314–330. [Google Scholar]
- Danger, J.; Guilley, S.; Nguyen, P.; Rioul, O. PUFs: Standardization and Evaluation. In Proceedings of the 2016 Mobile System Technologies Workshop (MST), Milan, Italy, 23 September 2016; pp. 12–18. [Google Scholar]
- Chatterjee, B.; Das, D.; Maity, S.; Sen, S. RF-PUF: Enhancing IoT Security Through Authentication of Wireless Nodes Using In-Situ Machine Learning. IEEE Internet Things J. 2019, 6, 388–398. [Google Scholar] [CrossRef]
- Delvaux, J. Machine-Learning Attacks on PolyPUFs, OB-PUFs, RPUFs, LHS-PUFs, and PUF–FSMs. IEEE Trans. Inf. Forensics Secur. 2019, 14, 2043–2058. [Google Scholar] [CrossRef]
- Delvaux, J.; Verbauwhede, I. Fault Injection Modeling Attacks on 65 nm Arbiter and RO Sum PUFs via Environmental Changes. IEEE Trans.on Circuits Syst. I Regul. Pap. 2014, 61, 1701–1713. [Google Scholar] [CrossRef]
- Wallgren, L.; Raza, S.; Voigt, T. Routing Attacks and Countermeasures in the RPL-Based Internet of Things. Int. J. Distrib. Sens. Netw. 2013, 9, 794326. [Google Scholar] [CrossRef]
- Rührmair, U.; Sehnke, F.; Sölter, J.; Dror, G.; Devadas, S.; Schmidhuber, J. Modeling Attacks on Physical Unclonable Functions. In Proceedings of the 17th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 4–8 October 2010; pp. 237–249. [Google Scholar]
- Helfmeier, C.; Boit, C.; Nedospasov, D.; Seifert, J. Cloning Physically Unclonable Functions. In Proceedings of the 2013 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Austin, TX, USA, 2–3 June 2013; pp. 1–6. [Google Scholar]
- Rührmair, U.; Sölter, J. PUF modeling attacks: An introduction and overview. In Proceedings of the 2014 Design, Automation Test in Europe Conference Exhibition (DATE), Dresden, Germany, 24–28 March 2014; pp. 1–6. [Google Scholar]
- Sahoo, D.P.; Nguyen, P.H.; Mukhopadhyay, D.; Chakraborty, R.S. A Case of Lightweight PUF Constructions: Cryptanalysis and Machine Learning Attacks. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2015, 34, 1334–1343. [Google Scholar] [CrossRef]
- Delvaux, J.; Verbauwhede, I. Side channel modeling attacks on 65nm arbiter PUFs exploiting CMOS device noise. In Proceedings of the 2013 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Austin, TX, USA, 2–3 June 2013; pp. 137–142. [Google Scholar]
- Nedospasov, D.; Seifert, J.; Helfmeier, C.; Boit, C. Invasive PUF Analysis. In Proceedings of the 2013 Workshop on Fault Diagnosis and Tolerance in Cryptography, Santa Barbara, CA, USA, 20–20 August 2013; pp. 30–38. [Google Scholar]
- Merli, D.; Schuster, D.; Stumpf, F.; Sigl, G. Semi-Invasive EM Attack on FPGA RO PUFs and Countermeasures. In Proceedings of the Workshop on Embedded Systems Security, Taipei, Taiwan, 9–14 October 2011; Association for Computing Machinery: New York, NY, USA, 2011. [Google Scholar]
- Zhang, J.; Wu, Q.; Lyu, Y.; Zhou, Q.; Cai, Y.; Lin, Y.; Qu, G. Design and Implementation of a Delay-Based PUF for FPGA IP Protection. In Proceedings of the 2013 International Conference on Computer-Aided Design and Computer Graphics, Guangzhou, China, 16–18 November 2013; pp. 107–114. [Google Scholar]
- Potkonjak, M.; Goudar, V. Public Physical Unclonable Functions. Proc. IEEE 2014, 102, 1142–1156. [Google Scholar] [CrossRef]
- McGraw, G. Software security. IEEE Secur. Priv. 2004, 2, 80–83. [Google Scholar] [CrossRef]
- Potlapally, N. Hardware security in practice: Challenges and opportunities. In Proceedings of the 2011 IEEE International Symposium on Hardware-Oriented Security and Trust, San Diego, CA, USA, 5–6 June 2011; pp. 93–98. [Google Scholar]
- Jin, Y. Introduction to Hardware Security. Electronics 2015, 4, 763–784. [Google Scholar] [CrossRef]
- Islam, M.N.; Kundu, S. Enabling IC Traceability via Blockchain Pegged to Embedded PUF. ACM Trans. Des. Autom. Electron. Syst. 2019, 24, 1–23. [Google Scholar] [CrossRef]
- Mohanty, S.P.; Yanambaka, V.P.; Kougianos, E.; Puthal, D. PUFchain: A Hardware-Assisted Blockchain for Sustainable Simultaneous Device and Data Security in the Internet of Everything (IoE). IEEE Consum. Electron. Mag. 2020, 9, 8–16. [Google Scholar] [CrossRef]
- Patil, A.S.; Hamza, R.; Yan, H.; Hassan, A.; Li, J. Blockchain-PUF-Based Secure Authentication Protocol for Internet of Things. In Algorithms and Architectures for Parallel Processing; Wen, S., Zomaya, A., Yang, L.T., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 331–338. [Google Scholar]
- Barbareschi, M.; De Benedictis, A.; La Montagna, E.; Mazzeo, A.; Mazzocca, N. PUF-Enabled Authentication-as-a-Service in Fog-IoT Systems. In Proceedings of the 2019 IEEE 28th International Conference on Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE), Napoli, Italy, 12–14 June 2019; pp. 58–63. [Google Scholar]
- Bordel Sánchez, B.; Alcarria, R.; Robles, T.; Jara, A. Protecting Physical Communications in 5G C-RAN Architectures through Resonant Mechanisms in Optical Media. Sensors 2020, 20, 4104. [Google Scholar] [CrossRef]
- Buchanan, W.J.; Li, S.; Asif, R. Lightweight cryptography methods. J. Cyber Secur. Technol. 2017, 1, 187–201. [Google Scholar] [CrossRef]
- Ometov, A.; Masek, P.; Malina, L.; Florea, R.; Hosek, J.; Andreev, S.; Hajny, J.; Niutanen, J.; Koucheryavy, Y. Feasibility characterization of cryptographic primitives for constrained (wearable) IoT devices. In Proceedings of the 2016 IEEE International Conference on Pervasive Computing and Communication Workshops (PerCom Workshops), Sydney, Australia, 14–18 March 2016; pp. 1–6. [Google Scholar]
- Yanambaka, V.P.; Mohanty, S.P.; Kougianos, E. Making Use of Manufacturing Process Variations: A Dopingless Transistor Based-PUF for Hardware-Assisted Security. IEEE Trans. Semicond. Manuf. 2018, 31, 285–294. [Google Scholar] [CrossRef]
- Zhu, F.; Li, P.; Xu, H.; Wang, R. A Lightweight RFID Mutual Authentication Protocol with PUF. Sensors 2019, 19, 2957. [Google Scholar] [CrossRef] [PubMed]
- Zhang, J.; Hu, X.; Ning, Z.; Ngai, E.C.; Zhou, L.; Wei, J.; Cheng, J.; Hu, B. Energy-Latency Tradeoff for Energy-Aware Offloading in Mobile Edge Computing Networks. IEEE Internet Things J. 2018, 5, 2633–2645. [Google Scholar] [CrossRef]
- Yang, Z.; Yang, K.; Lei, L.; Zheng, K.; Leung, V.C.M. Blockchain-Based Decentralized Trust Management in Vehicular Networks. IEEE Internet Things J. 2019, 6, 1495–1505. [Google Scholar] [CrossRef]
- Braeken, A. PUF Based Authentication Protocol for IoT. Symmetry 2018, 10, 352. [Google Scholar] [CrossRef]
- Gao, Y.; Li, G.; Ma, H.; Al-Sarawi, S.F.; Kavehei, O.; Abbott, D.; Ranasinghe, D.C. Obfuscated challenge-response: A secure lightweight authentication mechanism for PUF-based pervasive devices. In Proceedings of the 2016 IEEE International Conference on Pervasive Computing and Communication Workshops (PerCom Workshops), Sydney, NSW, Australia, 14–18 March 2016; pp. 1–6. [Google Scholar]
- Lunardi, R.C.; Michelin, R.A.; Neu, C.V.; Zorzo, A.F. Distributed access control on IoT ledger-based architecture. In Proceedings of the NOMS 2018—2018 IEEE/IFIP Network Operations and Management Symposium, Taipei, Taiwan, 23–27 April 2018; pp. 1–7. [Google Scholar]
- Reyna, A.; Martín, C.; Chen, J.; Soler, E.; Díaz, M. On blockchain and its integration with IoT. Challenges and opportunities. Future Gener. Comput. Syst. 2018, 88, 173–190. [Google Scholar] [CrossRef]
- Hang, L.; Kim, D.H. Design and Implementation of an Integrated IoT Blockchain Platform for Sensing Data Integrity. Sensors 2019, 19, 2228. [Google Scholar] [CrossRef]
- Chen, S.; Li, B.; Cao, Y. Intrinsic Physical Unclonable Function (PUF) Sensors in Commodity Devices. Sensors 2019, 19, 2428. [Google Scholar] [CrossRef]
- Debe, M.; Salah, K.; Rehman, M.H.U.; Svetinovic, D. IoT Public Fog Nodes Reputation System: A Decentralized Solution Using Ethereum Blockchain. IEEE Access 2019, 7, 178082–178093. [Google Scholar] [CrossRef]
- Liu, H.; Han, D.; Li, D. Fabric-iot: A Blockchain-Based Access Control System in IoT. IEEE Access 2020, 8, 18207–18218. [Google Scholar] [CrossRef]
- Dai, W.; Deng, J.; Wang, Q.; Cui, C.; Zou, D.; Jin, H. SBLWT: A Secure Blockchain Lightweight Wallet Based on Trustzone. IEEE Access 2018, 6, 40638–40648. [Google Scholar] [CrossRef]
- Yilmaz, Y.; Gunn, S.R.; Halak, B. Lightweight PUF-Based Authentication Protocol for IoT Devices. In Proceedings of the 2018 IEEE 3rd International Verification and Security Workshop (IVSW), Costa Brava, Spain, 2–4 July 2018; pp. 38–43. [Google Scholar]
- Liao, B.; Ali, Y.; Nazir, S.; He, L.; Khan, H.U. Security Analysis of IoT Devices by Using Mobile Computing: A Systematic Literature Review. IEEE Access 2020, 8, 120331–120350. [Google Scholar] [CrossRef]
- Negka, L.; Gketsios, G.; Anagnostopoulos, N.A.; Spathoulas, G.; Kakarountas, A.; Katzenbeisser, S. Employing Blockchain and Physical Unclonable Functions for Counterfeit IoT Devices Detection. In Proceedings of the International Conference on Omni-Layer Intelligent Systems, Crete, Greece, 5–7 May 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 172–178. [Google Scholar]
- Jansen-Vullers, M.; van Dorp, C.; Beulens, A. Managing traceability information in manufacture. Int. J. Inf. Manag. 2003, 23, 395–413. [Google Scholar] [CrossRef]
- Lu, Q.; Xu, X. Adaptable Blockchain-Based Systems: A Case Study for Product Traceability. IEEE Softw. 2017, 34, 21–27. [Google Scholar] [CrossRef]
- Liu, H.; Zhang, Y.; Yang, T. Blockchain-Enabled Security in Electric Vehicles Cloud and Edge Computing. IEEE Netw. 2018, 32, 78–83. [Google Scholar] [CrossRef]
| Platform | Blockchain | Consensus | Smart Contracts |
|---|---|---|---|
| Ethereum | Public and Permission-Based | PoS | Yes |
| IBM Watson Hyper-ledger | Permission-Based | PBTF/SIEVE | Yes |
| Multichain | Permission-Based | PBTF | Yes |
| Litecoin | Public | Scrypt | No |
| Waltonchain | Permission-Based | PoC | No |
| Lisk | Public and Permission-Based | DPoS | Yes |
| Edenchain | Permission-Based | PoS | Yes |
| Quorum | Permission-Based | Multiple | Yes |
| Moeco | Private and Permission-Based | Exonum | Yes |
| HDAC | Permission-Based | ePoW, Trust-based | Yes |
| IOTA | Permission-Based | PoW | Yes |
| NetObjex | Permissionless | Hedera Hashgraph | Yes |
| Service Execution Time (ms) | ||||||
|---|---|---|---|---|---|---|
| Device Registration | Sensor Reading | |||||
| Min | Avg | Max | Min | Avg | Max | |
| 50 Devices | 2262 | 2286 | 2375 | 1974 | 2490 | 2770 |
| 150 Devices | 2257 | 2335 | 2801 | 1696 | 2679 | 3005 |
| 250 Devices | 2254 | 2585 | 3004 | 2043 | 2767 | 3322 |
| 500 Devices | 2267 | 2923 | 4013 | 2689 | 3012 | 4983 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Asif, R.; Ghanem, K.; Irvine, J. Proof-of-PUF Enabled Blockchain: Concurrent Data and Device Security for Internet-of-Energy. Sensors 2021, 21, 28. https://doi.org/10.3390/s21010028
Asif R, Ghanem K, Irvine J. Proof-of-PUF Enabled Blockchain: Concurrent Data and Device Security for Internet-of-Energy. Sensors. 2021; 21(1):28. https://doi.org/10.3390/s21010028
Chicago/Turabian StyleAsif, Rameez, Kinan Ghanem, and James Irvine. 2021. "Proof-of-PUF Enabled Blockchain: Concurrent Data and Device Security for Internet-of-Energy" Sensors 21, no. 1: 28. https://doi.org/10.3390/s21010028
APA StyleAsif, R., Ghanem, K., & Irvine, J. (2021). Proof-of-PUF Enabled Blockchain: Concurrent Data and Device Security for Internet-of-Energy. Sensors, 21(1), 28. https://doi.org/10.3390/s21010028






