1. Introduction
Towards realizing the emerging applications supported by the fifth generation (5G) wireless networks and the Internet of Things (IoT), while demanding ultra-reliable and low latency communication (URLLC), ubiquitous, distributed, and intelligent computing is one of the key enabling technologies. IoT is foreseen to reach 500 billion devices connected to the Internet by 2030 [
1], while the global mobile traffic is expected to increase seven-fold by 2021 [
2]. Thus, it is evident that traditional cloud computing architectures cannot support the latency constraints of the next generation networking environments, such as Tactile Internet [
3]. The reasons are that the powerful cloud centers are often deployed far away from the end users; thus, huge amounts of traffic are usually transmitted through intermediate nodes resulting in heavy load, congestion, delay uncertainties, high energy consumption, and multiple security threats [
4]. Thus, multi-access edge computing (MEC), which brings computing resources from the core network to the edge network, becomes a natural and promising solution to support these applications.
Combined with the MEC concept, Unmanned Aerial Vehicles (UAVs), equipped with communication and computing facilities, become a core component of next generation networks due to their salient attributes, such as hovering ability, flexibility and effortless deployment, maneuverability, mobility, low cost, strong line-of-sight (LoS) connection links, adjustable usage, and adaptive altitude [
5]. The MEC servers are embedded in the UAVs that fly in closer proximity to the users compared to the conventional MEC servers typically residing at the Macro Base Stations (MBSs) of the macrocells or at the Access Points (APs) of the small cells [
6]. Thus, the UAV-mounted MEC servers more efficiently support the end users applications’ data offloading and processing at the flying edge servers, by creating a flexible and dynamic computing environment paradigm [
7].
1.1. Related Work
Cheng et al. [
8] discuss the benefits introduced by the UAV-mounted MEC servers with respect to caching and computing, in a hybrid architecture consisting of UAV-mounted and ground MEC servers. Luo et al. [
9] introduce a cloud-based UAV-assisted system and study its stability with respect to the sensors big data offloading rate. Valentino et al. [
10] consider a fleet of UAV-mounted MEC servers and the optimization problem of increasing the UAVs fleet lifetime, while decreasing the overall computation time of the users’ offloaded tasks is formulated and solved. In particular, the authors exploit neighboring UAV clusters with sufficient computing resources to offload the users’ computation tasks.
Xiong et al. [
11] formulate a joint optimization problem to optimize the users’ data offloading to the UAV-mounted MEC servers, the UAVs’ trajectory, and the data allocation during transmission to the different UAVs. An end-to-end solution is introduced by Jeong et al. [
12], where the authors jointly optimize the users’ data offloading to the UAV-mounted MEC servers (i.e., uplink) and the output processed data returned to the users (i.e., downlink), while considering the computation tasks’ latency constraints. Jeong et al. [
13] focus on the UAV-mounted MEC servers’ energy constraints to jointly optimize the users’ data offloading by considering orthogonal and non-orthogonal communication multiple access techniques, and the UAVs’ trajectory. Furthermore, Zhou et al. consider a wireless powered communication environment in [
14,
15], where the UAVs except from acting as UAV-mounted MEC servers providing computing services to the end-users, they also provide energy to them. Accordingly, the users can exploit the harvested energy to perform local computing and/or transmit their data to the UAV-mounted MEC servers.
1.2. Motivation and Contributions
All the aforementioned research works, though having demonstrated significant benefits and potential, have made two fundamental assumptions regarding the examined UAV-assisted multi-access edge computing system: (i) the UAV-mounted MEC servers offer their communication and computing services to the users for free; and (ii) the users act as neutral utility maximizers aiming at simply maximizing their perceived satisfaction from offloading and processing their data to the UAV-mounted MEC servers, thus exhibiting a risk-neutral behavior. However, in a realistic communication and computing environment, both assumptions may not always hold true.
The operator of the UAV-mounted MEC server should enjoy some form of profit by offering its computing services and capabilities to the end-users. Depending on the operation mode, business model and use case under consideration, the profit could be—either explicit or implicit—expressed in different forms (e.g., monetary cost, etc.) [
16,
17]. In our work, we consider that the profit for the UAV-Mounted MEC server originates directly from applying a usage-based charging policy for allowing the exploitation of the server’s computing resources.
Moreover, it has been argued recently that in real life the end-users are characterized by loss averse and risk seeking behavior in terms of exploiting the system’s available resources, especially in resource-constrained environments (e.g., [
18,
19,
20]). In our case, the resources that the users may opt for and compete for refer to the UAV-mounted MEC server’s computing resources. Specifically, based on the users’ behavioral characteristics, some users may act aggressively and opportunistically in terms of offloading their data to the UAV-mounted MEC servers in order to avoid consuming their personal resources to process their data. Those users exhibit risk seeking behavior, as the UAV-mounted MEC server may not be able to serve all the users’ data offloading and processing requests. On the other hand, there are more conservative users, who exhibit loss averse behavior, thus being more willing to process their data locally at their devices, instead of taking the risk of finally not being served by the UAV-mounted MEC server due to the potential overexploitation of the latter.
Towards jointly addressing the aforementioned assumptions and filling the respective research gaps, in this paper, we exploit the power and principles of Prospect Theory [
18] to capture the users risk-based behavior in their data offloading decision-making process, under the operation framework of a usage-based pricing mechanism of the UAV-mounted MEC servers’ computing resources. To the best of our knowledge, this is the first research work in the existing literature that jointly combines a pricing-aware and risk-aware framework to deal with the data offloading problem in UAV-mounted multi-access edge computing systems.
In particular, we assume that the users have two available options for executing their tasks, namely the local computation and the remote computation, the latter achieved through data offloading. The local computation resources of the user’s device act as safe resources, since the users do not compete with each other for consuming those resources. On the other hand, the computation resources of the UAV-mounted MEC server are treated as a Common Pool of Resources (CPR), as they are non-excludable, i.e., all the users have the right to exploit them, while they are rivalrous and subtractable, i.e., their exploitation by one user reduces the ability to be exploited by another user. In principle, the UAV-mounted MEC server resources have the potential to provide significantly higher satisfaction to the user (compared to the lower satisfaction that could be obtained through the limited user local computation resources), if properly utilized and allocated. However, if the users selfishly offload their data to the UAV-mounted MEC server, then the computing capabilities of the latter will be overexploited resulting in suboptimal outcomes for the entire set of users, possibly leading to the complete “failure” of the CPR UAV-mounted MEC server. The failure of the CPR UAV-mounted MEC server refers to its inability to concurrently handle the large amount of offloaded data and corresponding computation tasks by the users, due to its limited computation capability.
To treat this situation and differentiate the performance and usage of the available computation resources, we capitalize on the theory of Tragedy of the Commons [
21,
22], while also introducing a usage-based pricing mechanism to capture the users’ cost for exploiting the server’s computation resources. The proposed pricing mechanism implicitly introduces a more social behavior to the users and supports the fairness among them, in terms of competing for the UAV-mounted MEC server’s computation resources. The users’ behavioral characteristics in the data offloading decision-making process, is captured through the principles of Prospect Theory that models users’ decisions under the uncertainty of the available computation resources at the UAV-mounted MEC server. Prospect Theory is a well known behavioral economic theory studying the autonomous decision-making of the individuals under risk and uncertainty of the associated payoff of their choices, which is estimated with some probability [
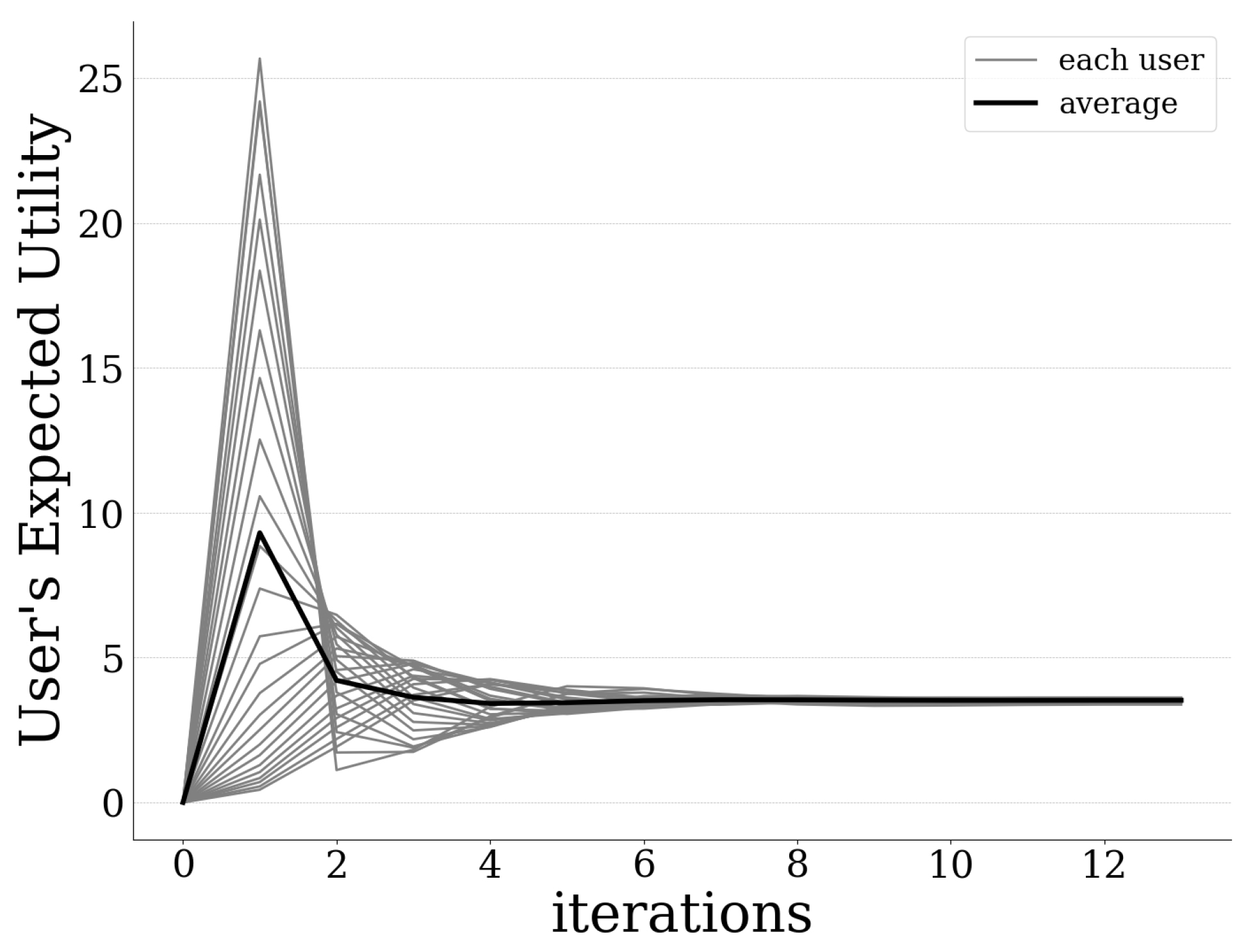
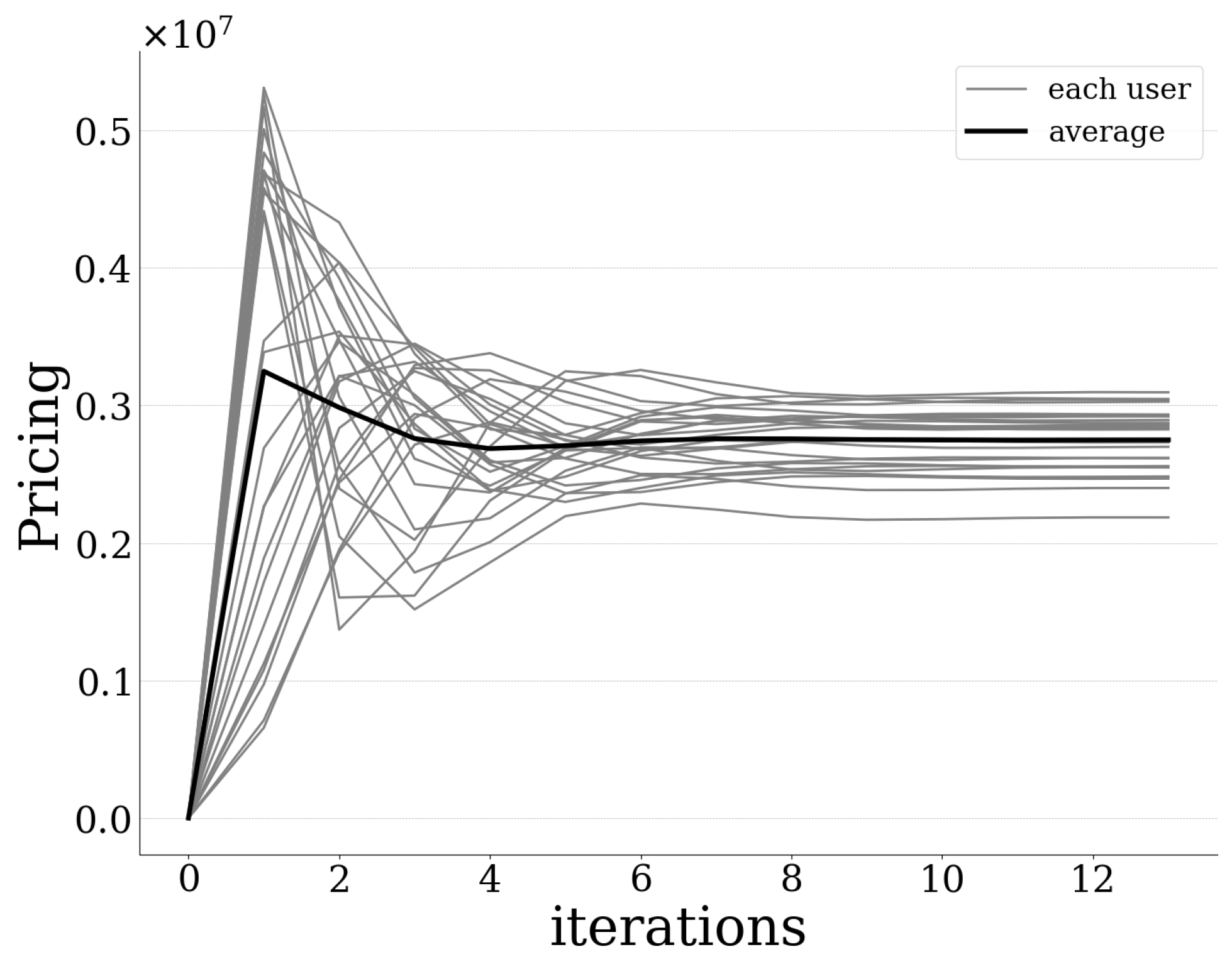
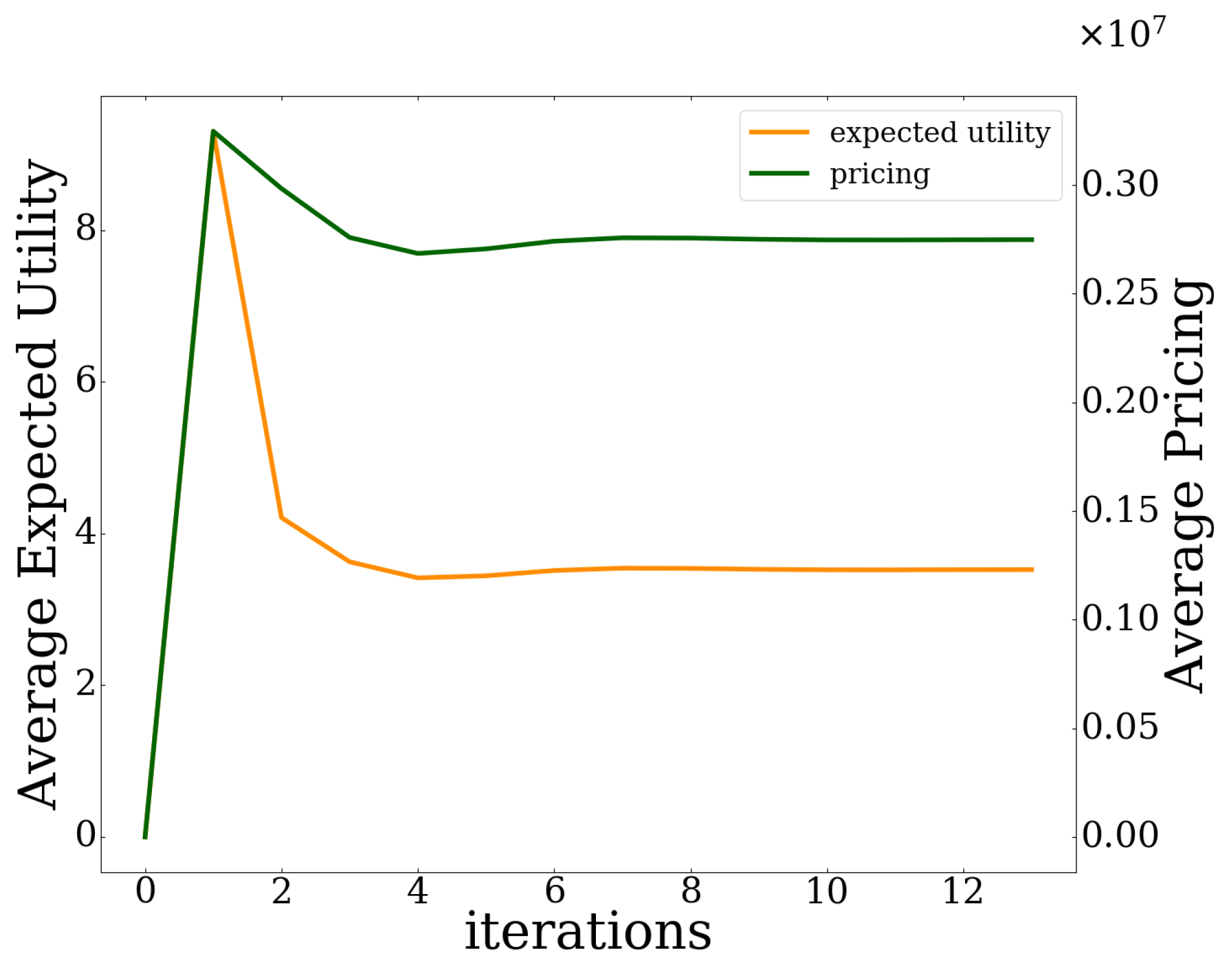
23]. The performance evaluation and validation of the proposed pricing and risk-aware data offloading framework in UAV-assisted MEC systems is achieved via modeling and simulation, in terms of efficient exploitation of all the available computation resources, realistic capturing of users’ interaction with the computing environment, and its scalability.
1.3. Outline
The rest of this paper is organized as follows.
Section 2 presents the considered system model, while
Section 3 initially discusses the main principles of Prospect Theory and the theory of the Tragedy of the Commons, and then accordingly designs and formulates the users’ prospect-theoretic utility function.
Section 4 introduces the pricing and risk-aware data offloading framework in a UAV-assisted multi-access edge computing system by formulating and solving the corresponding optimization data offloading problem, via adopting the theory of S-modular games. In
Section 5, a low complexity and iterative algorithm is introduced to determine the Pure Nash Equilibrium (PNE) of the users’ data offloading optimization problem.
Section 6 contains the performance evaluation of the proposed framework, while
Section 7 concludes the paper.
2. System Model
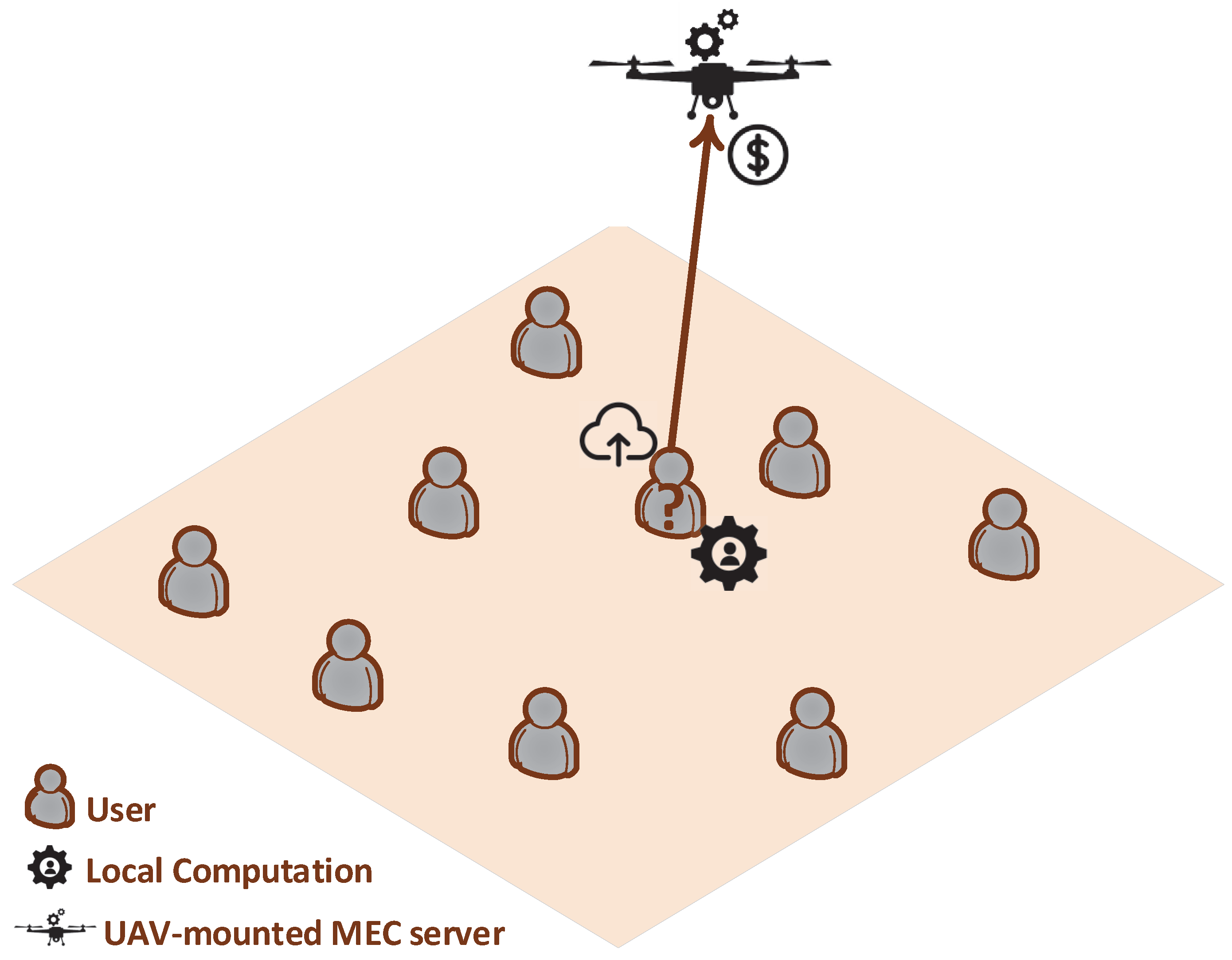
A UAV-assisted multi-access edge computing system is considered consisting of a set of mobile users
and a UAV-mounted MEC server attached to the UAV. Each user
n has a computation task
that needs to execute. Each task is accordingly defined as
, where
[bits] is the user’s
n size of the input data needed for the computation task and
[CPU-cycles] is the number of CPU cycles required in order to accomplish the computation task. The UAV-mounted MEC server is available to the users to offload and process their data remotely instead of processing them locally on their device and consuming their own local resources. Each user decides to offload
[bits] data to the UAV-mounted MEC server, while the rest (
) [bits] data are processed locally on the user’s device. An indicative topology of the considered UAV-assisted MEC system is presented in
Figure 1. In this work we mainly focus on the modeling and provisioning of the computing resources, rather than on the user to UAV wireless communication aspects. The UAV flexibility and adaptability capabilities can ensure strong communication channels and links with the users.
For each user
n, the time
[s] to process the whole amount of data
locally is defined as:
where
[CPU-cycles/s] is the computation capability of each user’s
n device. Apart from the processing time needed, each computation task has some energy requirements as well. The energy
[J] needed to process the whole amount of data
locally for each user
n is defined as:
where
[J/CPU-cycle] is the coefficient denoting the consumed energy per CPU cycle locally at each user’s
n device.
We assume that the UAV-mounted MEC server applies a fair usage-based pricing policy to the users, while charging them proportionally to their offloaded data and to their demand of consuming computation resources, as they are indicated by the nature of their computation task. Thus, the cost imposed by the UAV-mounted MEC server to the user
n in order to process the user’s offloaded data
is defined as:
where
c [1/CPU-cycles] represents a constant pricing factor imposed by the UAV-mounted MEC server to every user. Intuitively, the cost imposed to each user (Equation (3)) is proportional to the percentage of the number of CPU cycles
of the user’s computation task that is actually offloaded, i.e., the greater the part of the computation task offloaded to the UAV-mounted MEC server is, the greater is the cost that the user experiences by the UAV-mounted MEC server to process remotely its data. It is noted that, without loss of generality, the cost
imposed by the UAV-mounted MEC server to the user
n in order to process the offloaded data of the latter is assumed to be a unitless metric in this research work, and can represent any type of usage-based cost or monetary cost in a realistic implementation. Based on the above proposed model, we can therefore formulate the problem of determining the optimal
that each user should offload considering each user’s risk-aware behavioral characteristics and the pricing imposed by the UAV-mounted MEC server.
3. Users Prospect-Theoretic Utility Function in UAV-Assisted MEC Environment
In the dynamic computation environment considered in this research work, consisting of the UAV-mounted MEC server’s and the users’ local computing capabilities, the users exhibit a risk-aware behavior in terms of deciding where to process the data of their computation tasks. Therefore, the users do not act as risk-neutral utility maximizers following the conventional Expected Utility Theory (EUT) [
23], but instead they rather exhibit a loss averse or gain seeking behavior when utilizing the UAV-mounted MEC server’s computation resources. To capture the exploitation and usage characteristics and principles of the available computation resources in the considered UAV-assisted MEC system, we adopt the theory of the Tragedy of the Commons [
22]. Specifically, the UAV-mounted MEC server’s computation resources are considered as a Common Pool of Resources (CPR), as all the users have access to them and can offload their data to the UAV-mounted MEC server in order to be processed. If the users overexploit the computation resources of the UAV-mounted MEC server, the latter will fail to serve their computation demands and none of the users will be satisfied. On the other hand, the user’s device’s local computation resources are considered as safe resources, as each user exclusively exploits them for its own benefit. It is noted that the safe resources provide a guaranteed satisfaction to the user; however, the user can potentially experience lower satisfaction compared to exploiting the CPR, as the user has to spend its own resources, e.g., energy to process locally its data.
As mentioned before, towards capturing the users’ loss averse and gain seeking behavior in terms of exploiting the CPR and safe computation resources, the principles of Prospect Theory are adopted [
24]. Prospect Theory is a behavioral economic theory that quantifies individuals’ behavioral patterns, which demonstrate systematic deviations from the Expected Utility Theory. Under the prospect theoretic model, the users experience greater dissatisfaction from a potential outcome of losses compared to their satisfaction from gains of the same amount. In addition, the level of the users’ satisfaction and dissatisfaction is evaluated with respect to a reference point, which is considered as the ground truth of the examined system. Recently, several efforts have appeared in the literature, where Prospect Theory has been adopted in various environments and application domains, including dynamic resource management in 5G wireless networks [
18,
25], public safety networks [
19], anti-jamming communications in cognitive radio networks [
20], users’ transmission power management and anti-jamming techniques in UAV-assisted networks [
5], and Quality of Experience in cyber-physical social systems [
21].
Following the principles of Prospect Theory, the user’s prospect theoretic utility is defined as [
24,
26]:
where
denotes the reference point expressing the user’s
n perceived satisfaction by processing all of its data locally at its device, which is the safe choice in terms of receiving a guaranteed satisfaction. Similarly,
denotes the user’s actual perceived satisfaction from offloading part of its data to the UAV-mounted MEC server, and is given by Equation (5) below.
The parameters
where
express the sensitivity of users to the gains and losses of their actual perceived satisfaction
, respectively. In particular, the user’s risk averse behavior in gains and risk seeking behavior in losses is captured by small values of the parameter
. Similarly, a small value of the parameter
captures a higher decrease in the user’s prospect theoretic utility, when its actual perceived satisfaction is close to the reference point. It is noted that the values of the parameters
can be determined and quantified based on statistical analysis of existing open datasets stemming from qualitative results of users’ behavioral models (e.g., [
27]). Furthermore, the loss aversion parameter
quantifies the impact of losses compared to the gains in user’s prospect theoretic utility. Specifically, for
, the user weighs the losses more than the gains, while the exact opposite holds true for
. For simplicity and without loss of generality, in this work, we assume
.
Specifically, the user’s actual perceived satisfaction from offloading part of its data (denoted by
) to the UAV-mounted MEC server is denoted as
and is formally defined as follows:
The first branch of Equation (5) expresses the user’s actual perceived satisfaction from processing all of its data locally to its mobile device. The second branch of Equation (5) captures the user’s actual perceived satisfaction by processing part of its data locally (first term) and part of them to the UAV-mounted MEC server (second term), while experiencing the corresponding usage-based cost (third term) for exploiting the UAV-mounted MEC server’s computation resources in the case that the MEC server can process all the users’ requests. The third branch of Equation (5) represents the user’s utility in the case that the MEC server fails to process the users’ data due to its overexploitation. The user’s actual perceived satisfaction from processing part of its data to the UAV-mounted MEC server depends on the server’s rate of return function
, where
,
is a normalized increasing function with respect to the users’ total demand of computation resources by the UAV-mounted MEC server. The vector
denotes the data offloading strategies of all the users in the examined system to the UAV-mounted MEC server. For demonstration purposes and without loss of generality, the users’ total demand function
of computation resources by the UAV-mounted MEC server is defined as follows:
where
is a positive constant calibrating the sigmoidal curve of Equation (6) based on the computing capabilities of the UAV-mounted MEC server. The users’ total computation demand function
is a continuous and strictly increasing function with respect to the users’ total amount of offloaded data. Equation (6) is a representative example of the users’ total computation demand function, while any other function that follows the above described properties can be adopted for the following analysis without loss of generality. In a nutshell, the UAV-mounted MEC server’s rate of return function
provides positive experience, i.e.,
, if the server has sufficient computation resources to serve the users’ total computation demand
. The UAV-mounted MEC server’s rate of return function
is a continuous, monotonically decreasing, and concave function with respect to the users’ total demand of computation resources, since the server’s computation resources assigned to each user and correspondingly the users’ perceived actual satisfaction decrease for increasing values of the users’ total computation demand [
28]. For demonstration purposes, in this paper, we adopt an indicative rate of return function that respects all aforementioned properties and is defined as follows:
Following the above discussion and focusing on the user’s prospect theoretic utility function, as defined in Equation (4), it is noted that the first branch of Equation (4) expresses the user’s n risk-aware satisfaction in the case that the UAV-mounted MEC server survives and can support the users’ total computation demand. In that case, each user targets at the maximization of its gains, while, in the opposite case, i.e., the second branch of Equation (4), the user targets at the minimization of its losses, as the UAV-mounted MEC server has failed due to overexploitation.
If the UAV-mounted MEC-server survives, then the user’s actual utility is determined by the second branch of Equation (5), given that the user offloaded part of its data to the MEC server. Thus, in combination with the first branch of Equation (4), the user’s prospect theoretic utility is given as follows:
If the opposite holds true, that is, the UAV-mounted MEC server’s computation resources are overexploited by the users and the server fails to serve them, then by combining the second branch of Equation (4) and the third branch of Equation (5), the user’s prospect theoretic utility can be written as follows:
Furthermore, the probability of failure of the UAV-mounted MEC server, which is the server’s probability to fail serving the users’ total computation demand
(Equation (6)), is denoted by
. The UAV-mounted MEC server’s probability of failure function
is assumed to be continuous, strictly increasing, convex, and twice differentiable function with respect to the users’ total computation demand
. In the following, we adopt the square function to present the UAV-mounted MEC server’s probability of failure, as shown below:
It is noted that the rest of the paper’s analysis still holds true for any probability of failure function that is characterized by the properties described above and the selection of the square function for the probability of failure is mainly made for presentation purposes. Accordingly, the UAV-mounted MEC server’s probability to survive and process the users’ total amount of offloaded data are
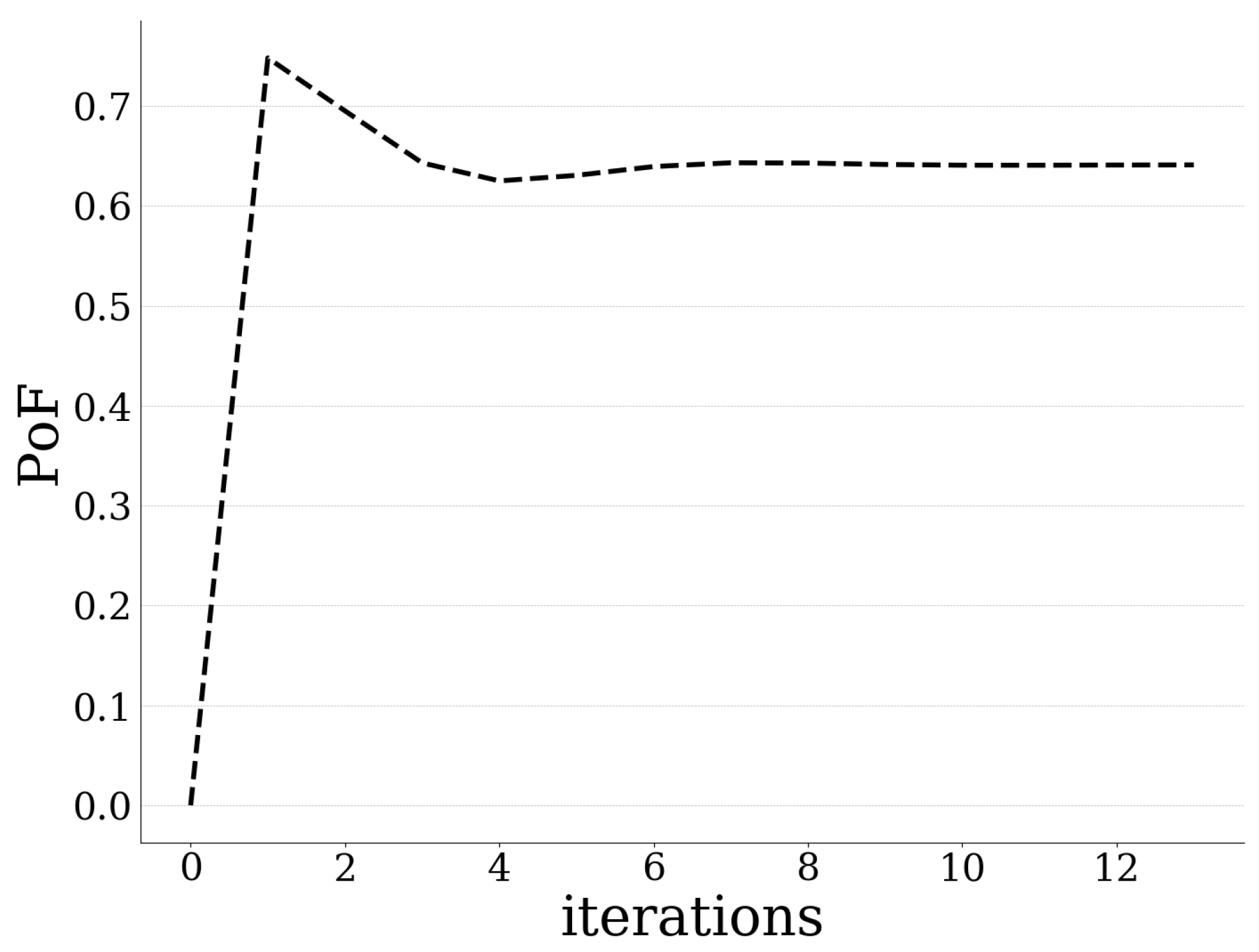
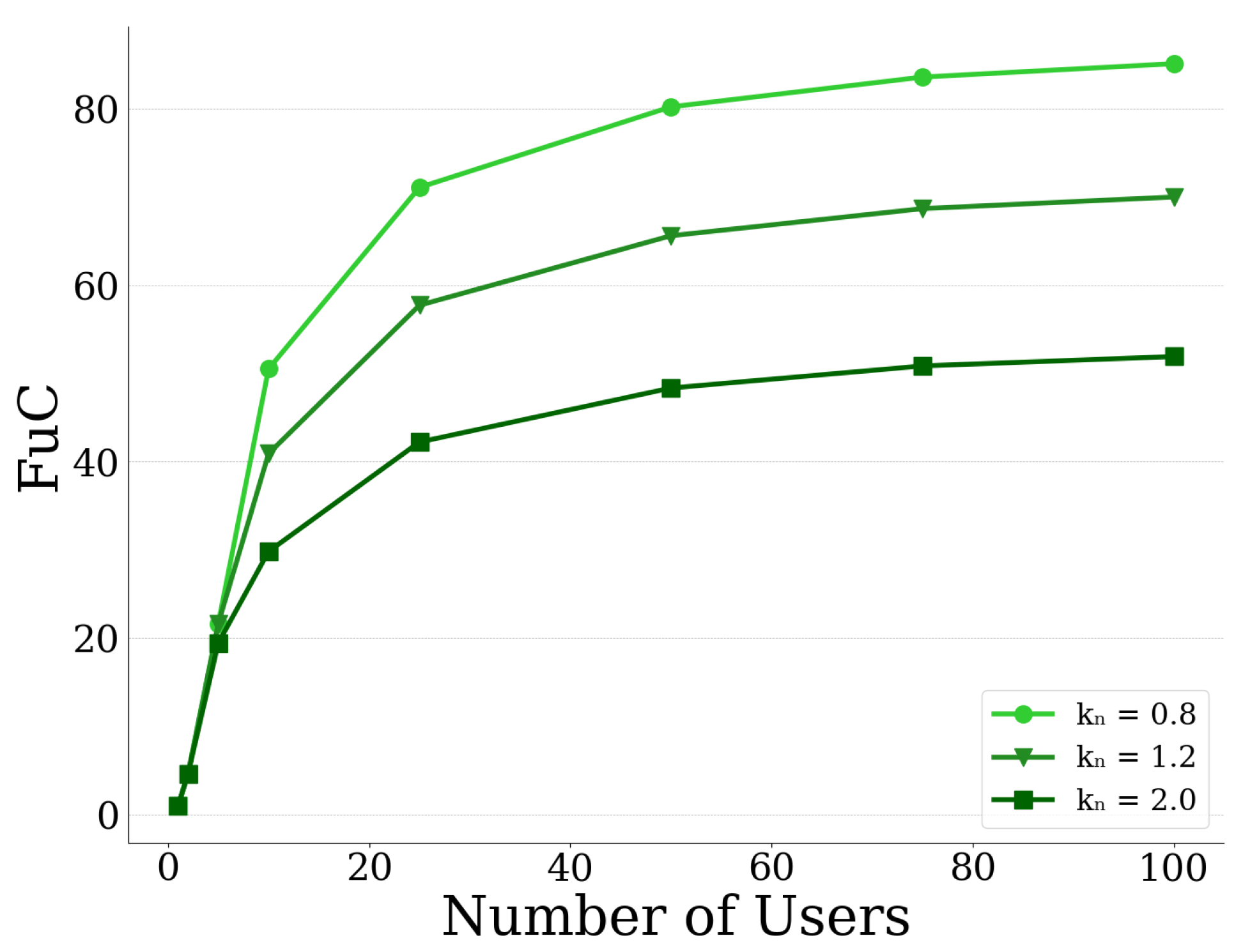
. Moreover, due to the nature of the user’s total computation demand (Equation (6)), the UAV-mounted MEC server’s probability of failure (Equation (10)) is convex on low to medium users’ computation demand and concave on high demand, while it asymptotically converges to one, as shown in
Figure 2.
Combining Equations (8)–(10), the user’s expected prospect theoretic utility by offloading
data to the UAV-mounted MEC server is defined as follows, jointly capturing the uncertainty of the UAV-mounted MEC server’s computation resources, the pricing of the UAV-mounted MEC server, as well as the user’s risk-aware characteristics in its data offloading decision:
7. Conclusions
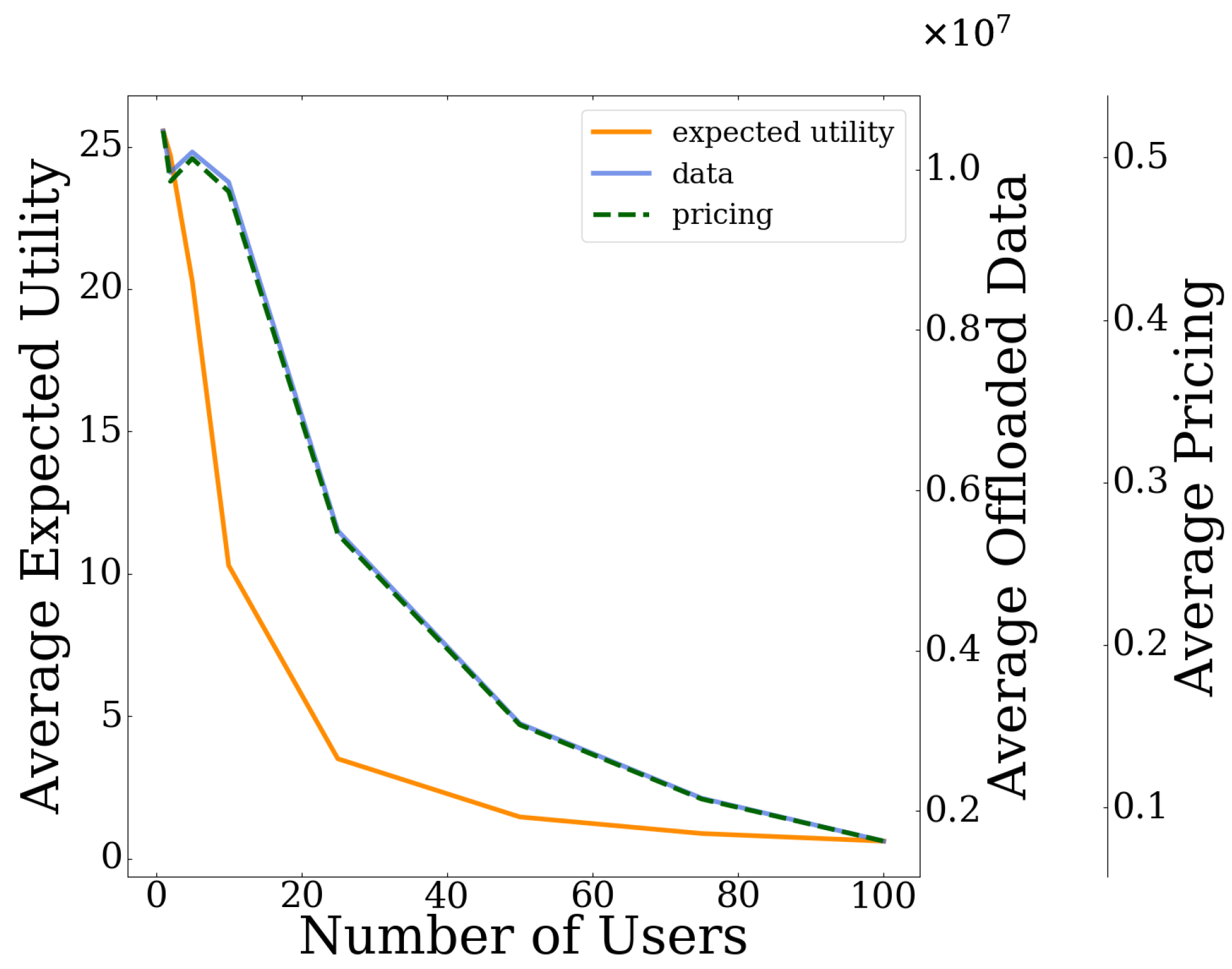
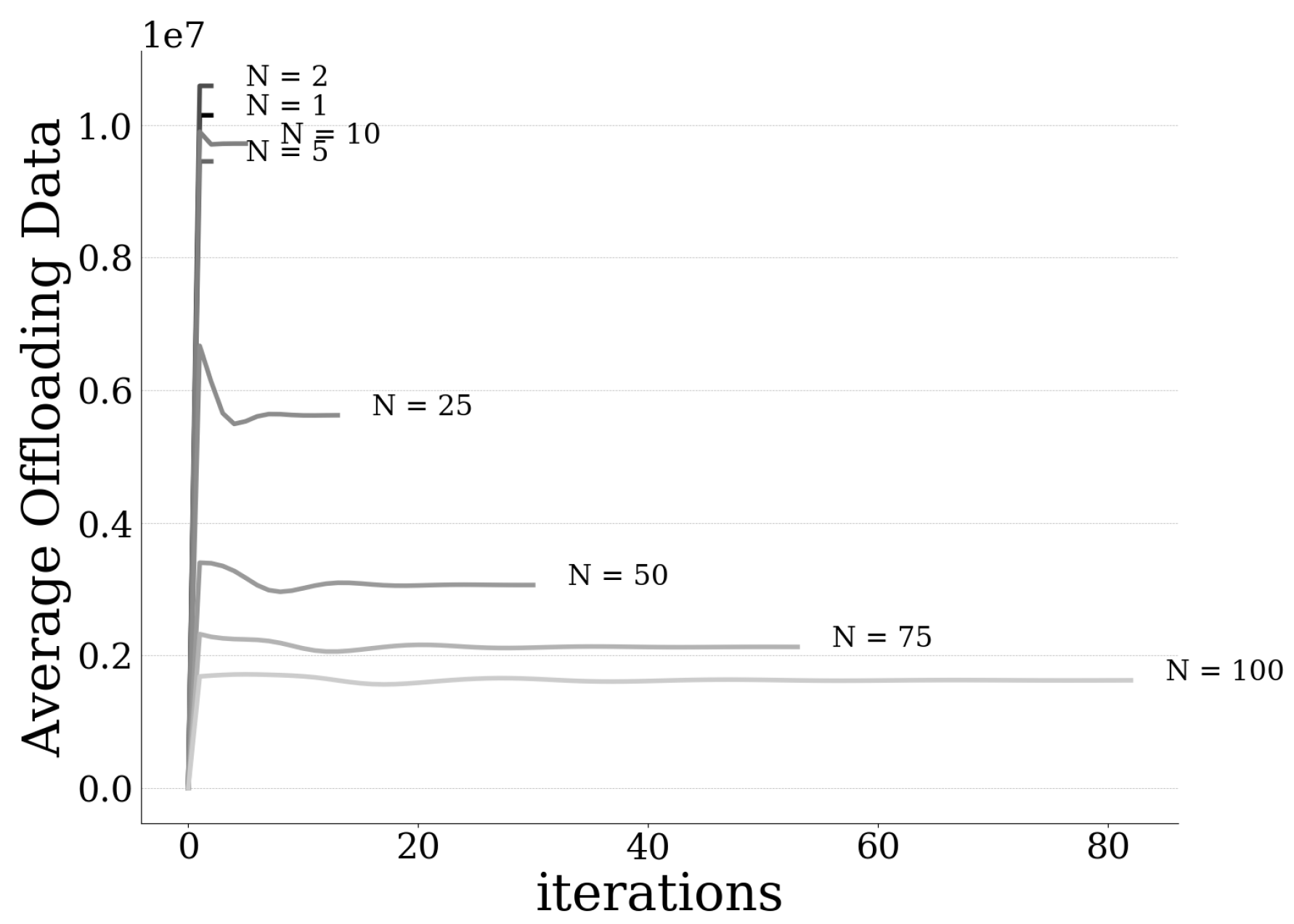
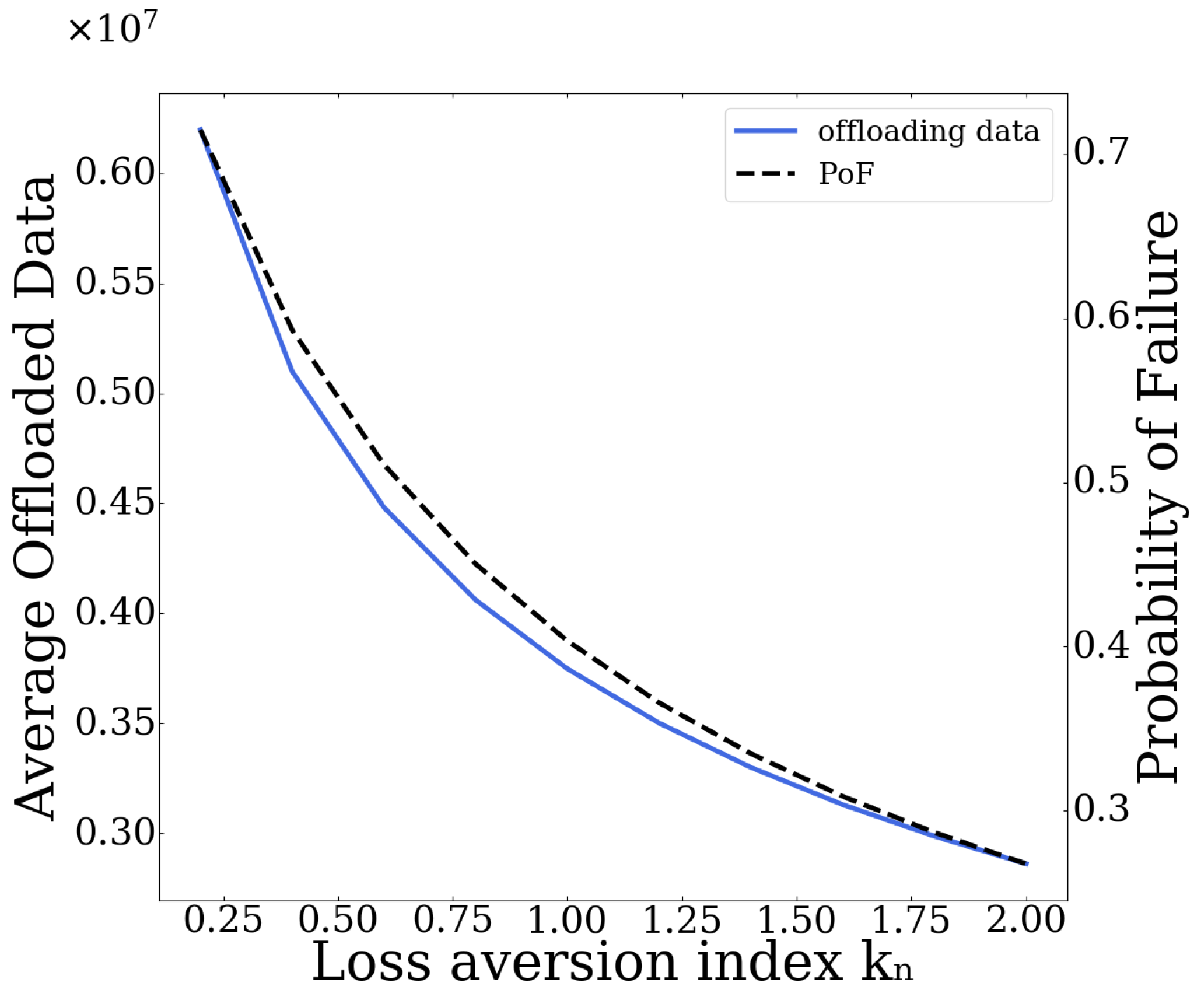
In this paper, a resource-based pricing and user risk-aware data offloading framework is proposed for UAV-assisted multi-access edge computing systems. In particular, a usage-based pricing mechanism is introduced regarding the exploitation of the MEC server’s computing capabilities by the users, and is properly incorporated within the principles and modeling of Prospect Theory, which is used to capture the users’ risk-aware behavior in the overall data offloading decision-making. Initially, the user’s prospect-theoretic utility function is formulated by quantifying the user’s risk seeking and loss aversion behavior, while taking into account the pricing mechanism. Accordingly, the users’ pricing and risk-aware data offloading problem is formulated as a distributed maximization problem of each user’s expected prospect-theoretic utility function and addressed as a non-cooperative game among the users. The existence of a Pure Nash Equilibrium for the formulated non-cooperative game is shown based on the theory of submodular games. An iterative and distributed algorithm is introduced that converges to the PNE, following the learning rule of the best response dynamics. Detailed numerical results are presented highlighting the operation feature and scalability properties of the proposed framework, while at the same time providing useful insights about the benefits of adopting the usage-based pricing scheme.
Our current and future research work focuses on treating the overall key problem of data offloading in various cloud computing environments, such as fog computing, where a large number of computing devices imposes additional scalability and stability challenges. Moreover, it is noted that, in this work, the data offloading problem was mainly treated from a computing resources perspective. However, depending on the environment assumed, the overall process could be affected by the wireless communication aspects between the UAV and users. The proposed framework could be adapted and extended to treat this aspect, either implicitly through the cost factors and functions considered when using the server resources, or explicitly by modeling the transmission characteristics (e.g., delay, rate, energy) involved in the offloading process.