Performance Evaluation of RTS/CTS Scheme in Beacon-Enabled IEEE 802.15.6 MAC Protocol for Wireless Body Area Networks
Abstract
1. Introduction
Contribution
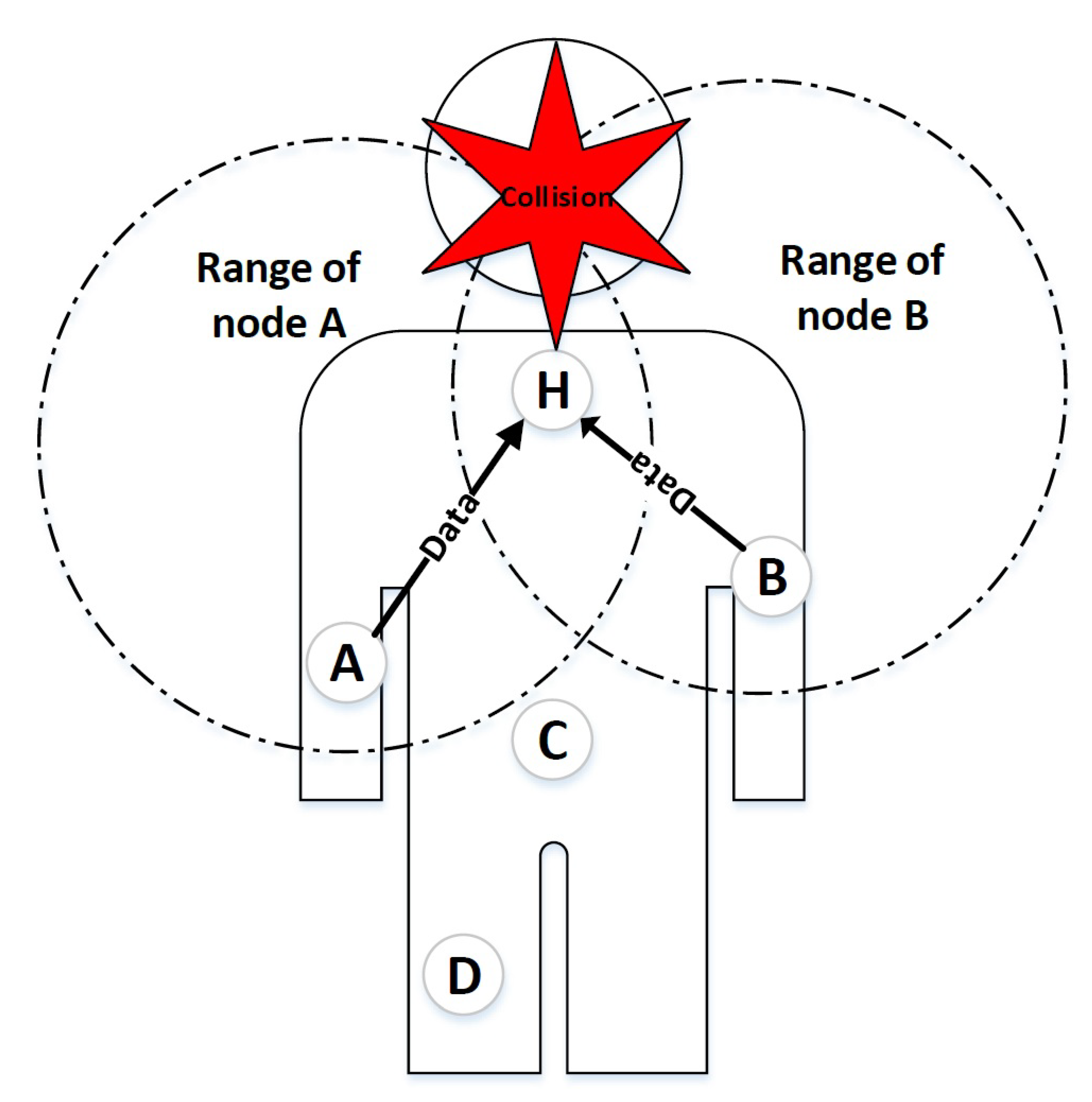
- We employ RTS/CTS scheme to solve hidden node problems in IEEE 802.15.6 CSMA/CA based networks.
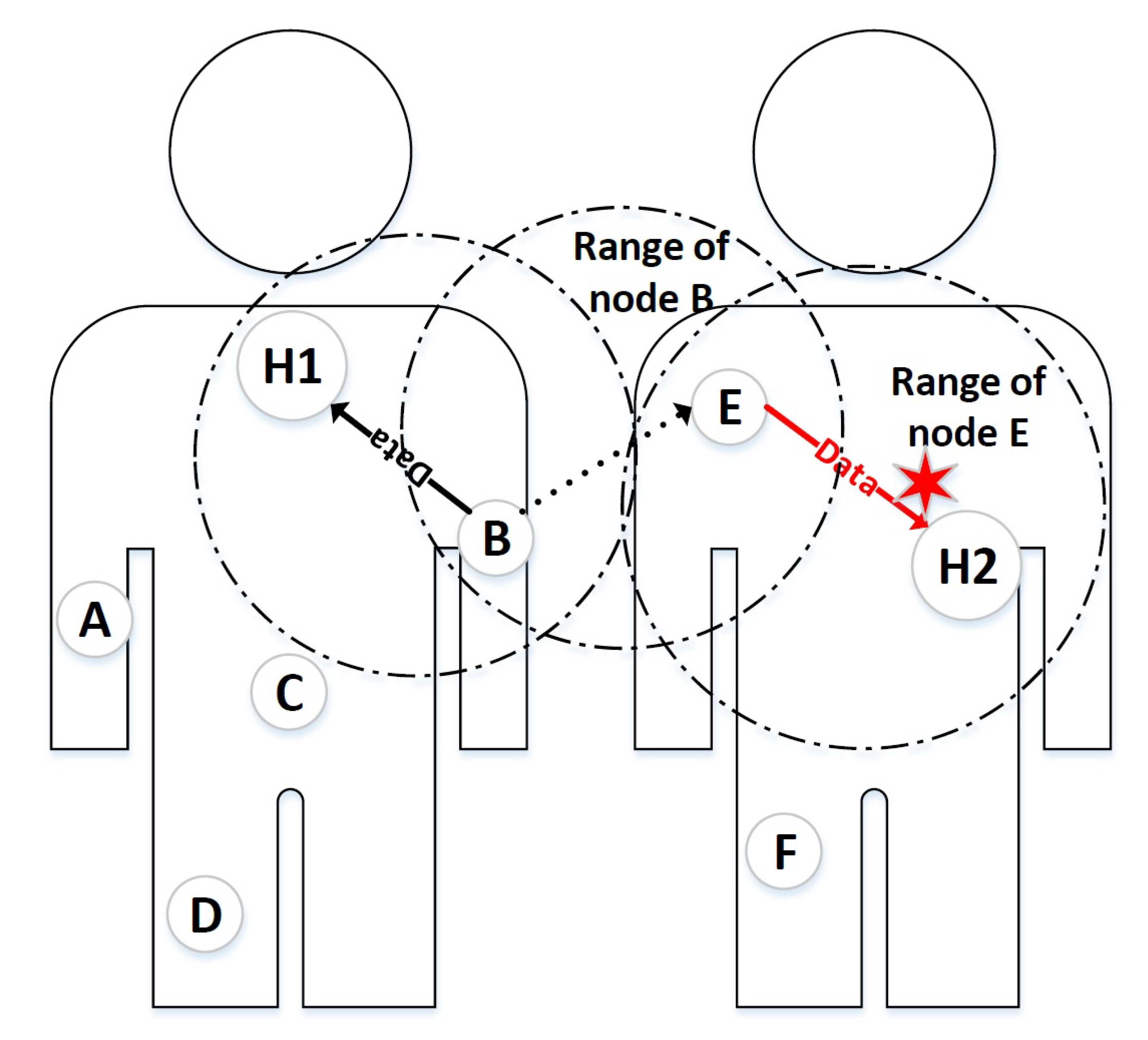
- We propose a power aware method that adjusts transmission power levels of nodes to avoid loss of RTS or CTS packets.
- We propose a mathematical model to validate the proposed approach.
- We perform extensive simulations to show effectiveness of the proposed approach over the conventional IEEE 802.15.6 CSMA/CA protocol in terms of throughput and energy consumption.
2. Related Work
2.1. Analysis of IEEE 802.15.6 CSMA/CA
2.2. RTS/CTS Scheme for Previous Standards
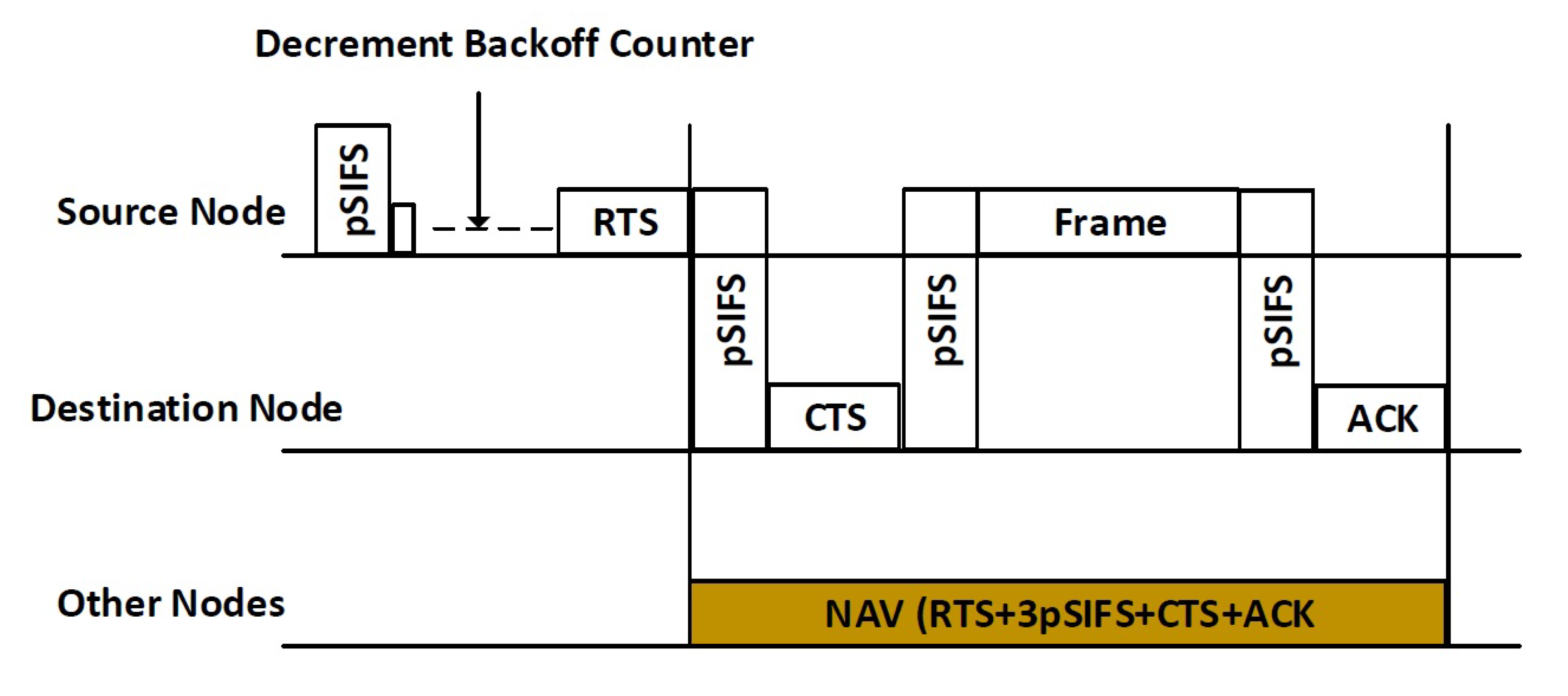
3. RTS/CTS Scheme for IEEE 802.15.6
3.1. Hidden Node Problem in IEEE 802.15.6
3.2. Exposed Node Problem in IEEE 802.15.6
3.3. Proposed RTS/CTS Scheme
| Algorithm 1 Proposed RTS/CTS scheme with power level adjustment for IEEE 802.15.6 CSMA/CA protocol. |
 |
4. Performance Evaluation
4.1. Numerical Model
4.2. Simulation Environment
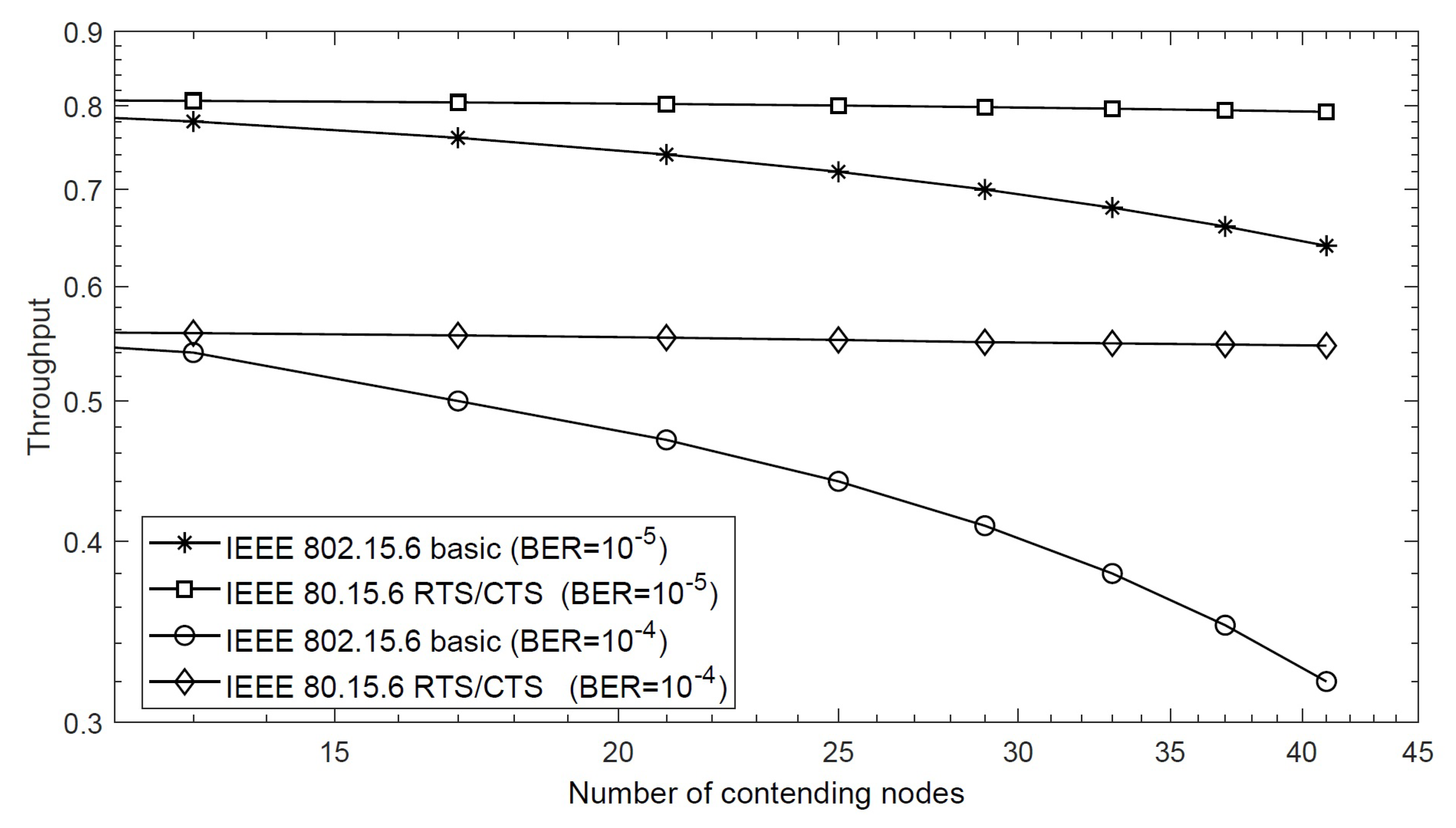
4.3. Results
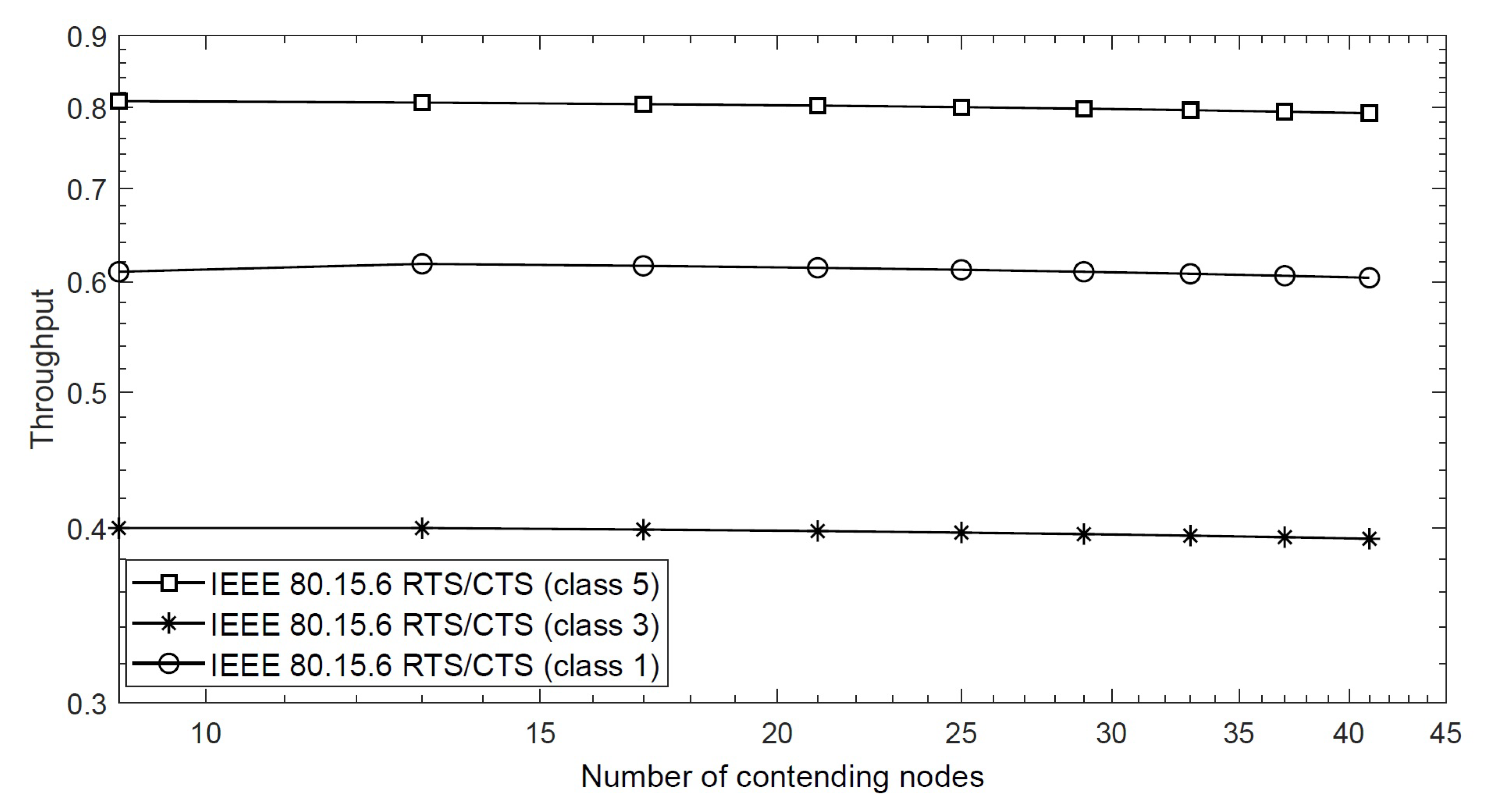
4.3.1. Throughput
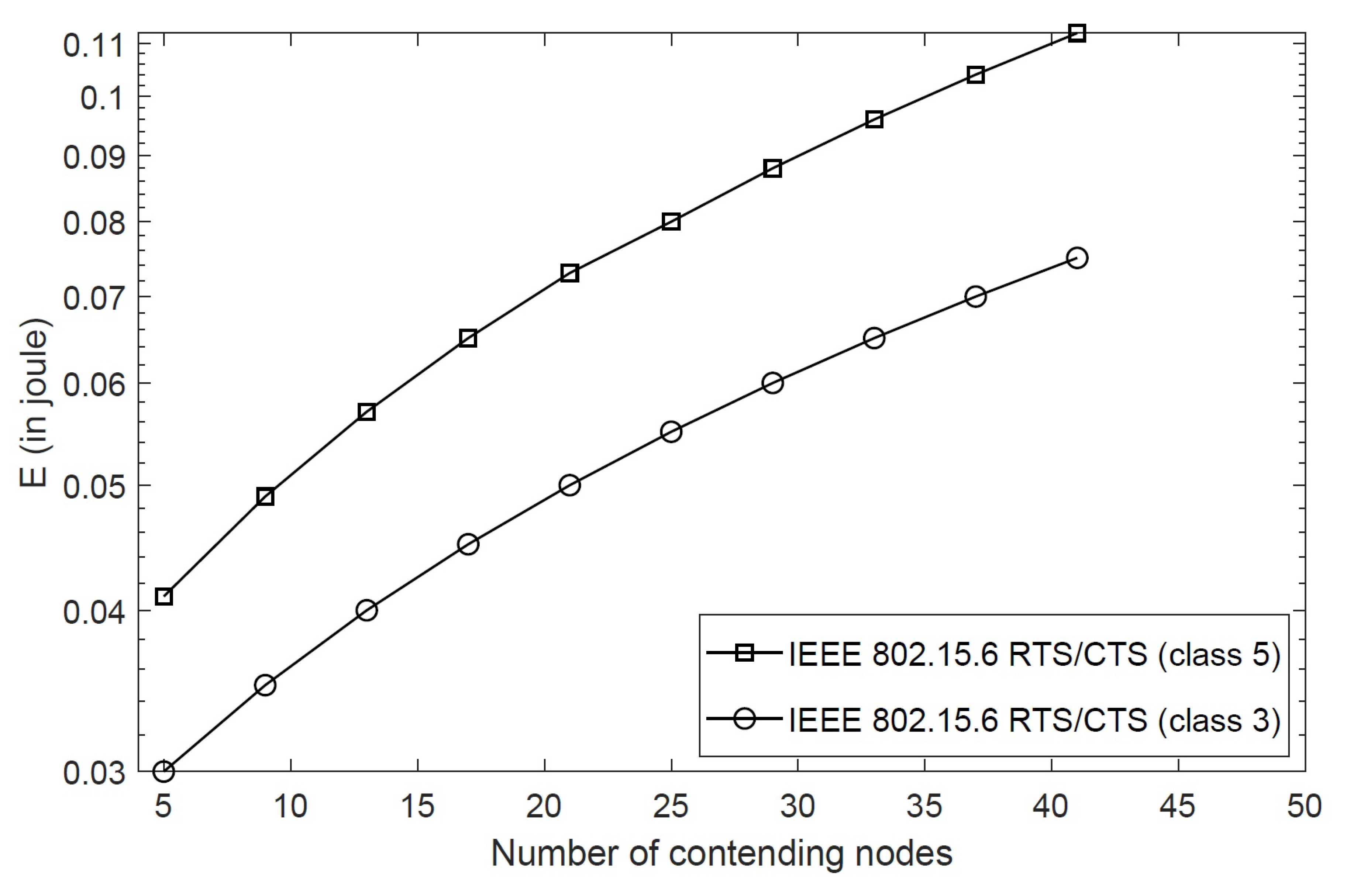
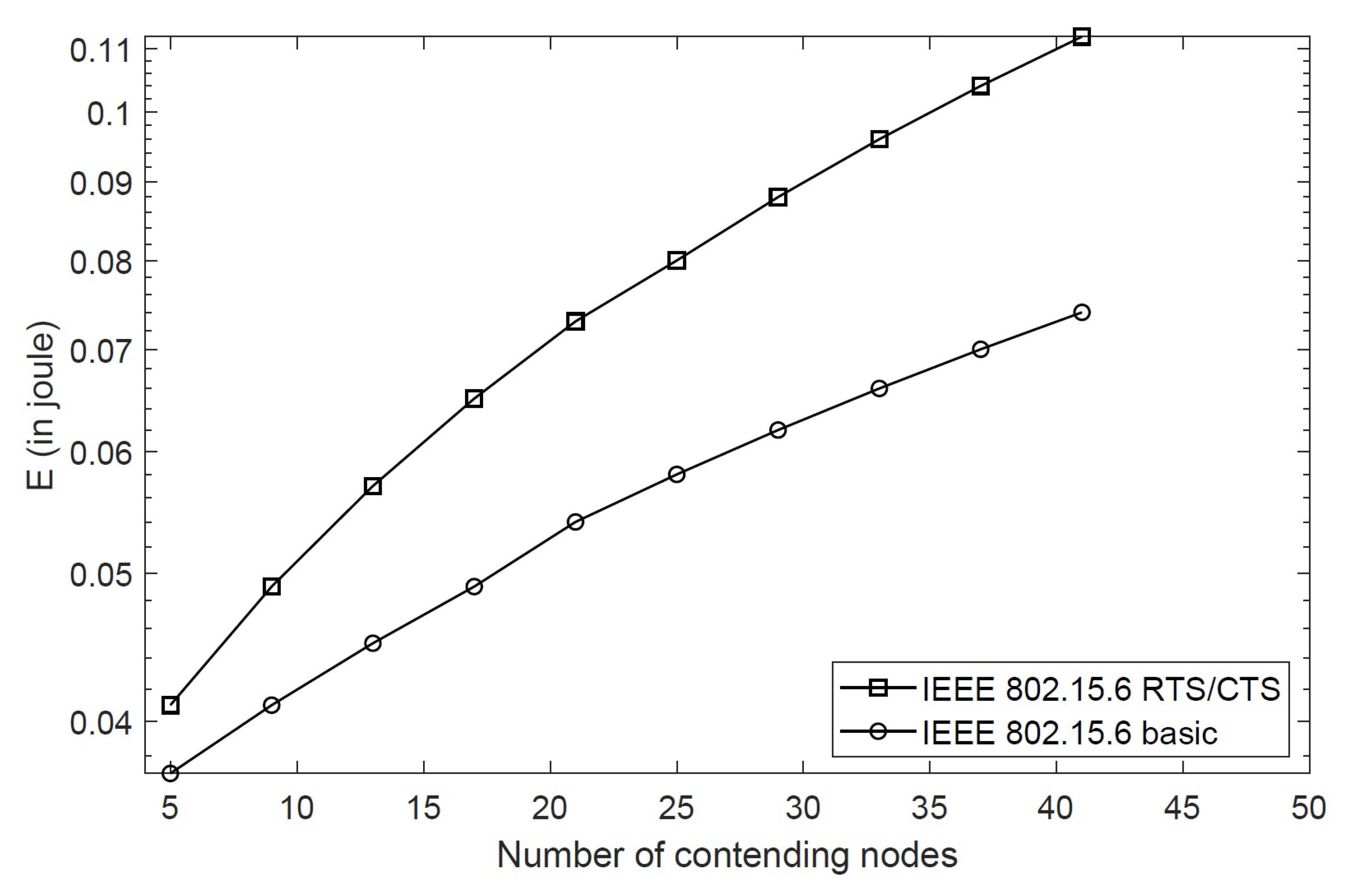
4.3.2. Energy Consumption
5. Conclusions and Future Works
5.1. Conclusions
5.2. Future Work
- Research work on the development of energy efficient routing protocols over the IEEE 802.15.6 standard is required to enable communication between multiple WBANs.
- Further research at MAC layer is required to study exposed node problems when multiple WBANs coexist.
- Performance evaluation of scheduled-based mechanisms used in the IEEE 802.15.6 standard may be studied for different medical applications.
- The effects of adjusting transmission power levels of nodes in the RTS/CTS based IEEE 802.15.6 networks may be extensively studied in the future.
Author Contributions
Funding
Conflicts of Interest
References
- Who. Available online: https://www.who.int/ (accessed on 19 October 2019).
- Cms. Available online: https://www.cms.gov/ (accessed on 19 October 2019).
- Iyengar, S.; Bonda, F.T.; Gravina, R.; Guerrieri, A.; Fortino, G.; Sangiovanni-Vincentelli, A. A Framework for Creating Healthcare Monitoring Applications Using Wireless Body Sensor Networks. In Proceedings of the 3rd International ICST Conference on Body Area Networks, Tempe, AZ, USA, 13–15 March 2008; pp. 1–2. [Google Scholar]
- Fortino, G.; Parisi, D.; Pirrone, V.; Di Fatta, G. BodyCloud: A SaaS approach for community Body Sensor Networks. Futur. Gener. Comput. Syst. 2014, 35, 62–79. [Google Scholar] [CrossRef]
- Shokeen, S.; Parkash, D. A Systematic Review of Wireless Body Area Network. In Proceedings of the 2019 International Conference on Automation, Computational and Technology Management (ICACTM), London, UK, 24–26 April 2019; pp. 58–62. [Google Scholar]
- Mohammed, M.S.; Sendra, S.; Lloret, J.; Bosch, I. Systems and WBANs for controlling obesity. J. Healthc. Eng. 2018. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Y.; Gravina, R.; Lu, H.; Villari, M.; Fortino, G. PEA: Parallel electrocardiogram-based authentication for smart healthcare systems. J. Netw. Comput. Appl. 2018, 117, 10–16. [Google Scholar] [CrossRef]
- IEEE 802.15.4 Standard for Low-Rate WPANs. 2003. Available online: https://standards.ieee.org/project/802_15_4.html (accessed on 21 April 2020).
- Smart, G.; Deligiannis, N.; Surace, R.; Loscrí, V.; Fortino, G.; Andreopoulos, Y. Decentralized Time-Synchronized Channel Swapping for Ad Hoc Wireless Networks. IEEE Trans. Veh. Technol. 2015, 65, 8538–8553. [Google Scholar] [CrossRef]
- IEEE 802.15.6 standard for WBAN. 2012. Available online: https://standards.ieee.org/standard/802_15_6-2012.html (accessed on 21 April 2020).
- Barbi, M.; Sayrafian, K.; Alasti, M. Using RTS/CTS to enhance the performance of IEEE 802.15.6 CSMA/CA. In Proceedings of the 2016 IEEE 27th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Valencia, Spain, 4–8 September 2016; pp. 1–5. [Google Scholar]
- Bianchi, G. Performance analysis of the IEEE 802.11 distributed coordination function. IEEE J. Sel. Areas Commun. 2000, 18, 535–547. [Google Scholar] [CrossRef]
- Rashwand, S.; Mišić, J. Effects of access phases lengths on performance of IEEE 802.15.6 CSMA/CA. Comput. Netw. 2012, 56, 2832–2846. [Google Scholar] [CrossRef]
- Sarkar, S.; Misra, S.; Bandyopadhyay, B.; Chakraborty, C.; Obaidat, M.S. Performance Analysis of IEEE 802.15.6 MAC Protocol under Non-Ideal Channel Conditions and Saturated Traffic Regime. IEEE Trans. Comput. 2015, 64, 2912–2925. [Google Scholar] [CrossRef]
- Rashwand, S.; Misic, J.; Khazaei, H. Performance analysis of IEEE 802.15.6 under saturation condition and error-prone channel. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Cancun, Quintana Roo, Mexico, 28–31 March 2011; pp. 1167–1172. [Google Scholar]
- Li, C.; Geng, X.; Yuan, J.; Sun, T. Performance Analysis of IEEE 802.15.6 MAC Protocol in Beacon Mode with Superframes. KSII Trans. Internet Inf. Syst. 2013, 7, 1108–1130. [Google Scholar]
- Kim, E.-J.; Kim, H.; Kim, D.; Kim, D. Adaptive Priority-based Medium Access Control Protocol for IEEE 802.15.6 Wireless Body Sensor Networks. Sens. Mater. 2018, 30, 1707. [Google Scholar] [CrossRef]
- Yuan, D.; Zheng, G.; Ma, H.; Shang, J.; Li, J. An Adaptive MAC Protocol Based on IEEE802.15.6 for Wireless Body Area Networks. Wirel. Commun. Mob. Comput. 2019, 2019, 1–9. [Google Scholar] [CrossRef]
- Hiep, P.T. Statistical method for performance analysis of WBAN in time-saturation. EURASIP J. Wirel. Commun. Netw. 2014, 2014, 221. [Google Scholar] [CrossRef]
- Khan, P.; Ullah, N.; Ali, F.; Ullah, S.; Hong, Y.-S.; Lee, K.-Y.; Kim, H. Performance Analysis of Different Backoff Algorithms for WBAN-Based Emerging Sensor Networks. Sensors 2017, 17, 492. [Google Scholar] [CrossRef] [PubMed]
- Li, C.; Yuan, X.; Yang, L.; Song, Y. A Hybrid Lifetime Extended Directional Approach for WBANs. Sensors 2015, 15, 28005–28030. [Google Scholar] [CrossRef] [PubMed]
- Shakir, M.; Rehman, O.U.; Rahim, M.; Alrajeh, N.; Khan, Z.A.; Khan, M.A.; Niaz, I.A.; Javaid, N. Performance Optimization of Priority Assisted CSMA/CA Mechanism of 802.15.6 under Saturation Regime. Sensors 2016, 16, 1421. [Google Scholar] [CrossRef]
- Zhang, R.; Moungla, H.; Mehaoua, A. Delay Analysis of IEEE 802.15.6 CSMA/CA Mechanism in Duty-Cycling WBANs. In Proceedings of the 2015 IEEE Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; pp. 1–6. [Google Scholar]
- Weyulu, E.; Hanada, M.; Kim, M.W. Optimizing RTS/CTS to improve throughput in ad hoc WLANs. In Proceedings of the 2017 Federated Conference on Computer Science and Information Systems, Prague, Czech Republic, 3–6 September 2017; pp. 885–889. [Google Scholar]
- Yazid, M.; Aïssani, D.; Bouallouche-Medjkoune, L.; Amrouche, N.; Bakli, K. Modeling and enhancement of the IEEE 802.11 RTS/CTS scheme in an error-prone channel. Boil. Cybern. 2014, 27, 33–52. [Google Scholar] [CrossRef]
- Shih, K.-P.; Liao, W.-H.; Chen, H.-C.; Chou, C.-M. On avoiding RTS collisions for IEEE 802.11-based wireless ad hoc networks. Comput. Commun. 2009, 32, 69–77. [Google Scholar] [CrossRef]
- Duan, J.; Zhuang, Y.; Ma, L. An adaptive RTS/CTS mechanism in IEEE 802.15.4 for multi-hop networks. In Proceedings of the 2012 International Conference on Computational Problem-Solving (ICCP), Leshan, China, 19–21 October 2012; pp. 155–159. [Google Scholar]
- Barroca, N.; Borges, L.M.; Velez, F.J.D.S.; Chatzimisios, P. IEEE 802.15.4 MAC layer performance enhancement by employing RTS/CTS combined with packet concatenation. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10–14 June 2014; pp. 466–471. [Google Scholar]
- Wei, Z.; Sun, Y.; Ji, Y. Collision analysis of CSMA/CA based MAC protocol for duty cycled WBANs. Wirel. Netw. 2016, 23, 1429–1447. [Google Scholar] [CrossRef]
- Ullah, S.; Chen, M.; Kwak, K.-S. Throughput and Delay Analysis of IEEE 802.15.6-based CSMA/CA Protocol. J. Med Syst. 2012, 36, 3875–3891. [Google Scholar] [CrossRef] [PubMed]
- Dong, X.; Varaiya, P. Saturation throughput analysis of IEEE 802.11 wireless LANs for a lossy channel. IEEE Commun. Lett. 2005, 9, 100–102. [Google Scholar] [CrossRef]
- Ullah, S.; Tovar, E.; Kim, K.-I.; Kim, K.H.; Imran, M. Performance Analysis of Priority-Based IEEE 802.15.6 Protocol in Saturated Traffic Conditions. IEEE Access 2018, 6, 66198–66209. [Google Scholar] [CrossRef]


| Parameter | Values | Parameter | Values |
|---|---|---|---|
| RTS | 193 bits | CTS | 193 bits |
| Preamble | 90 bits | PHY | 31 bits |
| MH | 72 bits | 1 | |
| Initial | 33 mW | 8 mW | |
| pSIFS | 75 | L | 1560 bits |
| ACK | 193 bits | Power levels | 5 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ullah , S.; Hassan, M.M.; Hossain, M.S.; Alelaiwi, A. Performance Evaluation of RTS/CTS Scheme in Beacon-Enabled IEEE 802.15.6 MAC Protocol for Wireless Body Area Networks. Sensors 2020, 20, 2368. https://doi.org/10.3390/s20082368
Ullah S, Hassan MM, Hossain MS, Alelaiwi A. Performance Evaluation of RTS/CTS Scheme in Beacon-Enabled IEEE 802.15.6 MAC Protocol for Wireless Body Area Networks. Sensors. 2020; 20(8):2368. https://doi.org/10.3390/s20082368
Chicago/Turabian StyleUllah , Sana, Mohammad Mehedi Hassan, M. Shamim Hossain, and Abdulhameed Alelaiwi. 2020. "Performance Evaluation of RTS/CTS Scheme in Beacon-Enabled IEEE 802.15.6 MAC Protocol for Wireless Body Area Networks" Sensors 20, no. 8: 2368. https://doi.org/10.3390/s20082368
APA StyleUllah , S., Hassan, M. M., Hossain, M. S., & Alelaiwi, A. (2020). Performance Evaluation of RTS/CTS Scheme in Beacon-Enabled IEEE 802.15.6 MAC Protocol for Wireless Body Area Networks. Sensors, 20(8), 2368. https://doi.org/10.3390/s20082368






