Attack Detection Using Network Coding in IoT Environment
Abstract
1. Introduction
2. Related Work
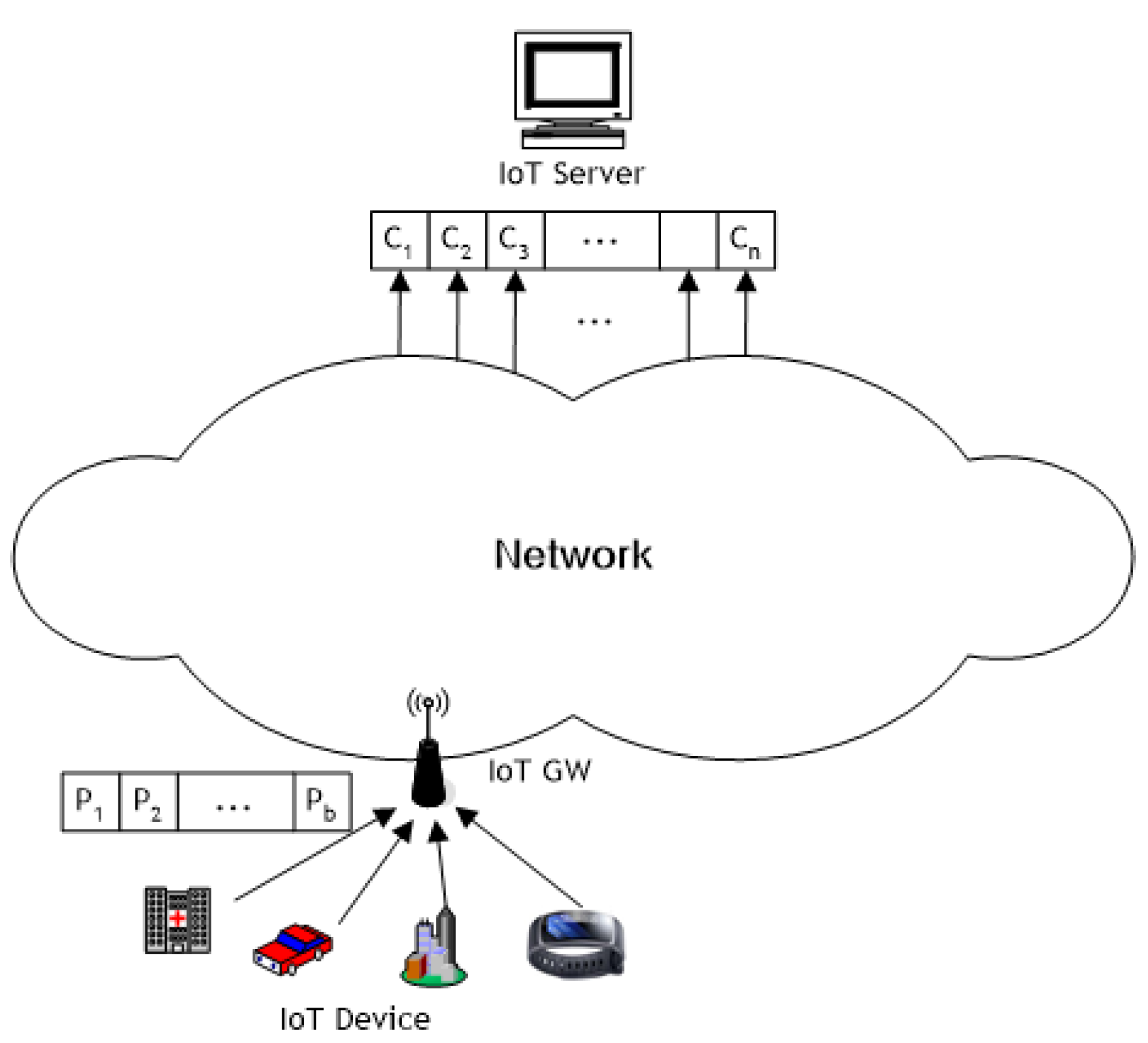
3. System Model and Descriptions
3.1. Basic Concepts
3.1.1. Operations at Source
3.1.2. Message Recovery at Destination
3.2. Attack Example
4. Attack Detection and Correction Algorithm Using Network Coding
4.1. Notations and Assumptions
- At source, a message is decomposed into b plain packets for transmission. Then they are transformed into n encoded packets with m redundancies using network coding.
- Any b packets out of the encoded n packets are required to recover the original message at destination.
- We assume that each packet is independently transferred with other packets.
- A malicious node can forge packets that appear to be “look-like-valid” combinations and send these “look-like-valid” packets instead of correct packets. We call it an attacked packet.
- It is assumed that there is no transmission error in the network, and all the packets transmitted by the source node are received by the destination node.
- b: Number of plain packets which are decomposed from a message.
- n: Number of combination packets which are encoded with the plain packets and redundancies. .
- e: Number of attacked packets among the n combination packets.
- r: Number of non-attacked, correct packets, .
- : Valid original packets which are decomposed from the original message.
- : Combination packets which are encoded from valid original packets and redundancies.
- : Erroneous combination packets which are fabricated by any attack.
- : Encoding coefficient.
- : a group.
- : group size, that is number of packets in a group .
- : Expected number of reconstructions that a group of size i can recover.
- : Actual number of reconstructions that a group of size i makes an identical result.
4.2. Characteristics of Encoded Packets
4.2.1. Group
4.2.2. Consistency
| Algorithm 1: The conditions of consistency. |
| if is group if group has consistency |
4.3. Algorithm
| Algorithm 2: Attack detection and correction algorithm at destination. |
| For all n received encoding packets Calculate all reconstructions For all reconstructions Classify and group identical reconstruction result For all group i if , set group i to true For all if set group i to consistency For all groups with consistency Find the group with the largest size |
- Consider the case where . Two groups with r and with e can be formed, and the of each group becomes and . We have , so it is possible to apply majority rule to identify the valid message.
- Suppose that a group consists of packets, and and . Assume that the reconstructions of encoded packets generate one identical result. Since , encoded packets could not generate a solution. If , , and this group is not subject to majority rule and the group can be selected by majority rule. For this group to be consistent, the maximum value of would be . Now let be . With and , we have . When , even if this group with attacked packets has one identical solution and it is consistent, , therefore the group is dropped by majority rule.
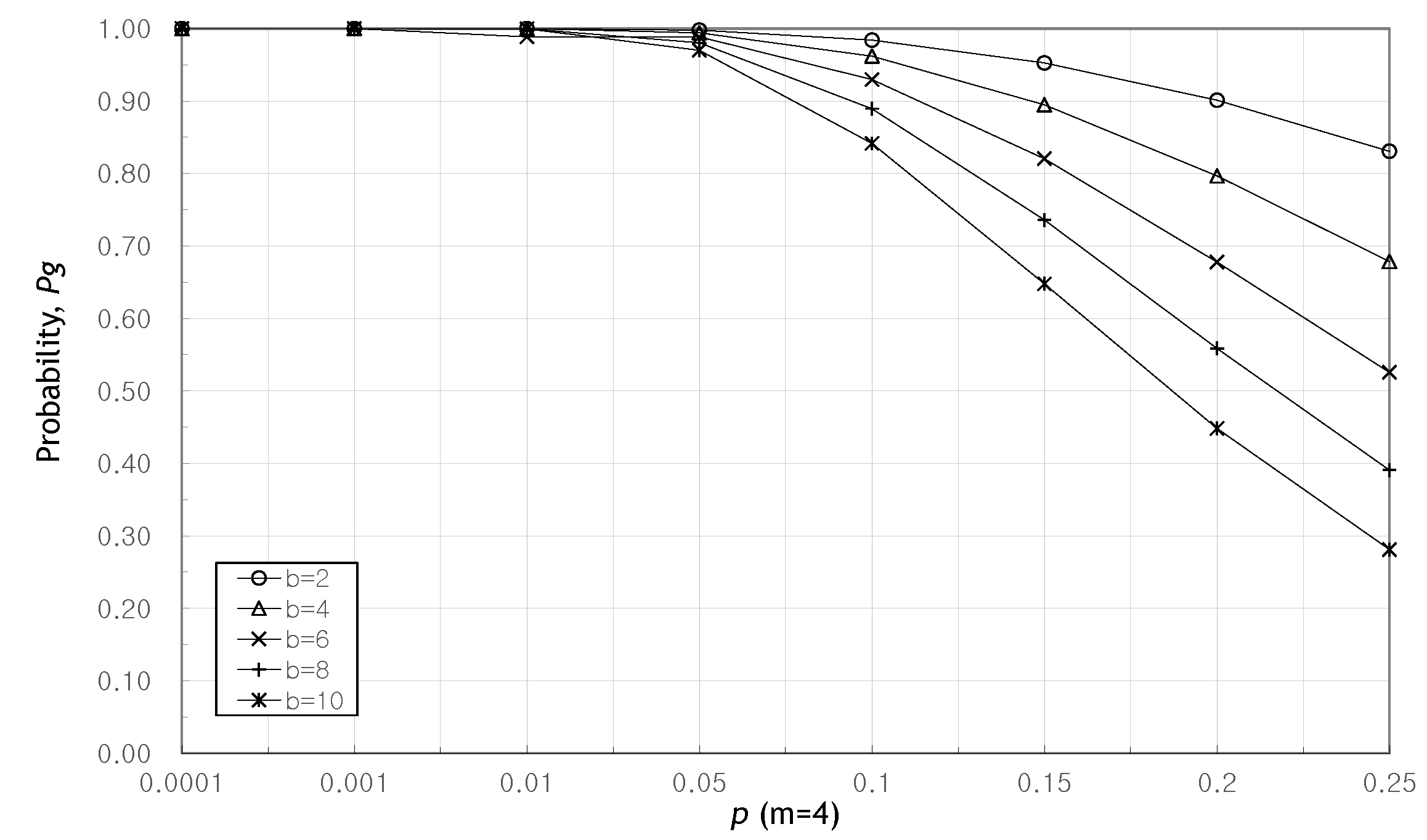
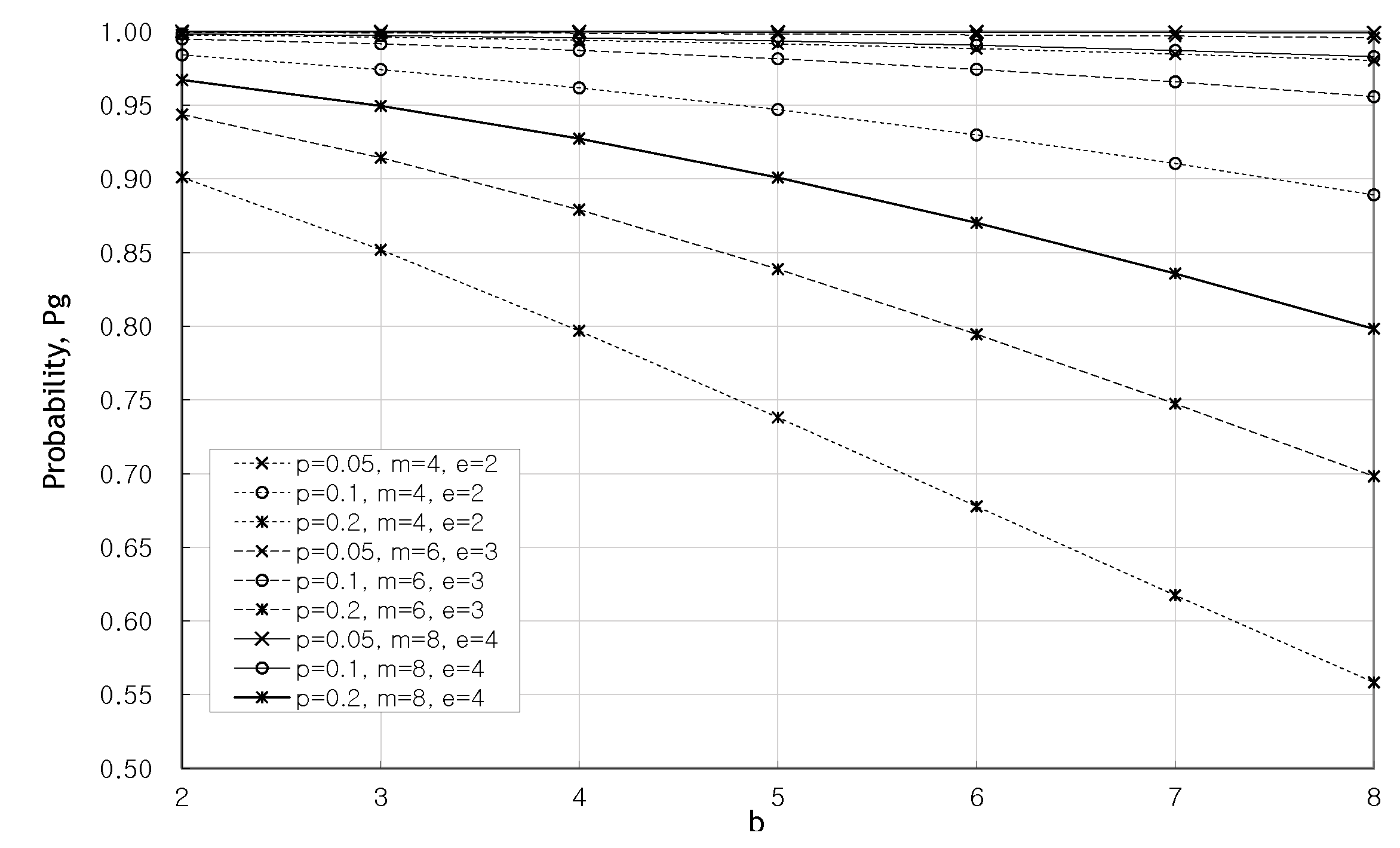
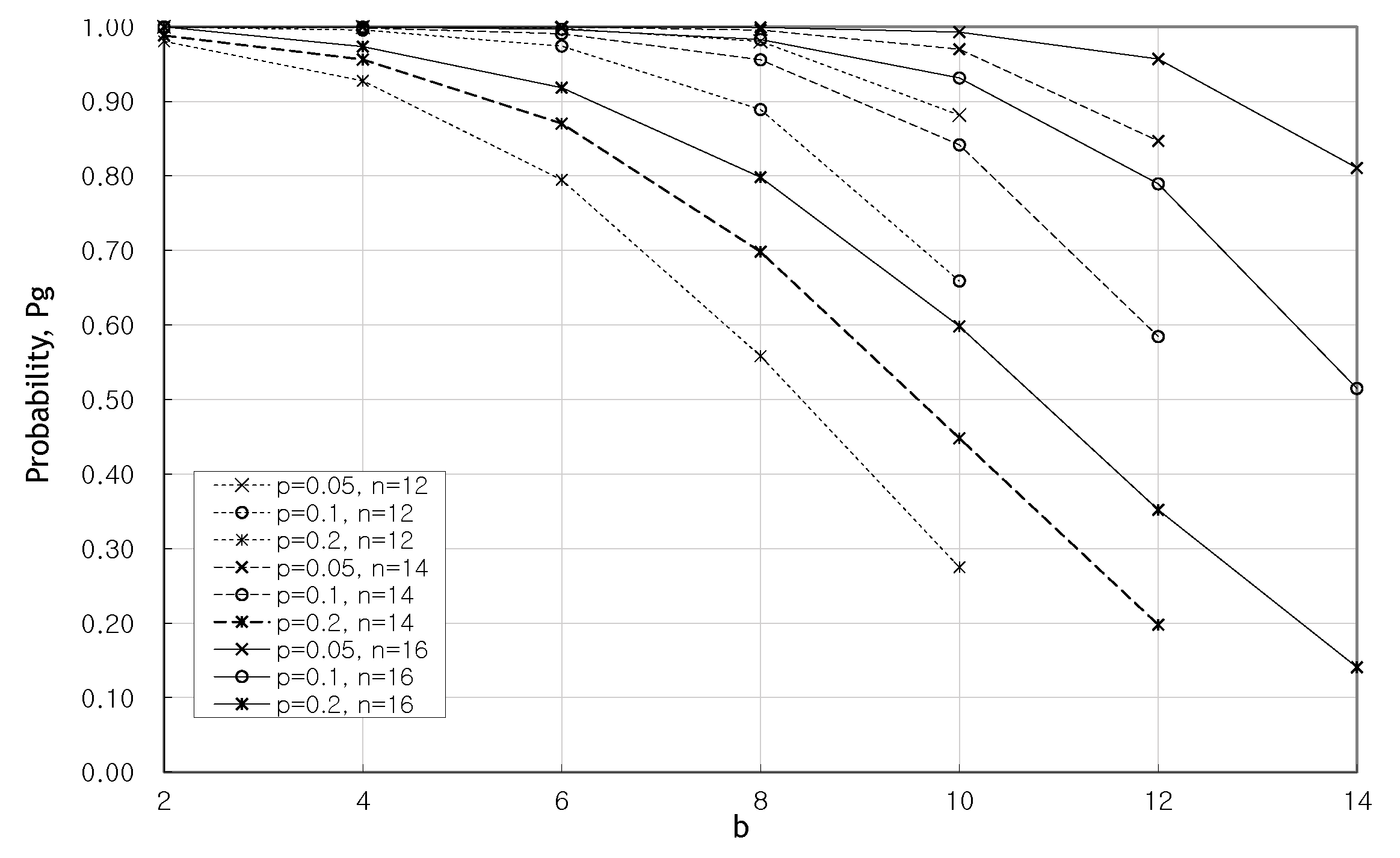
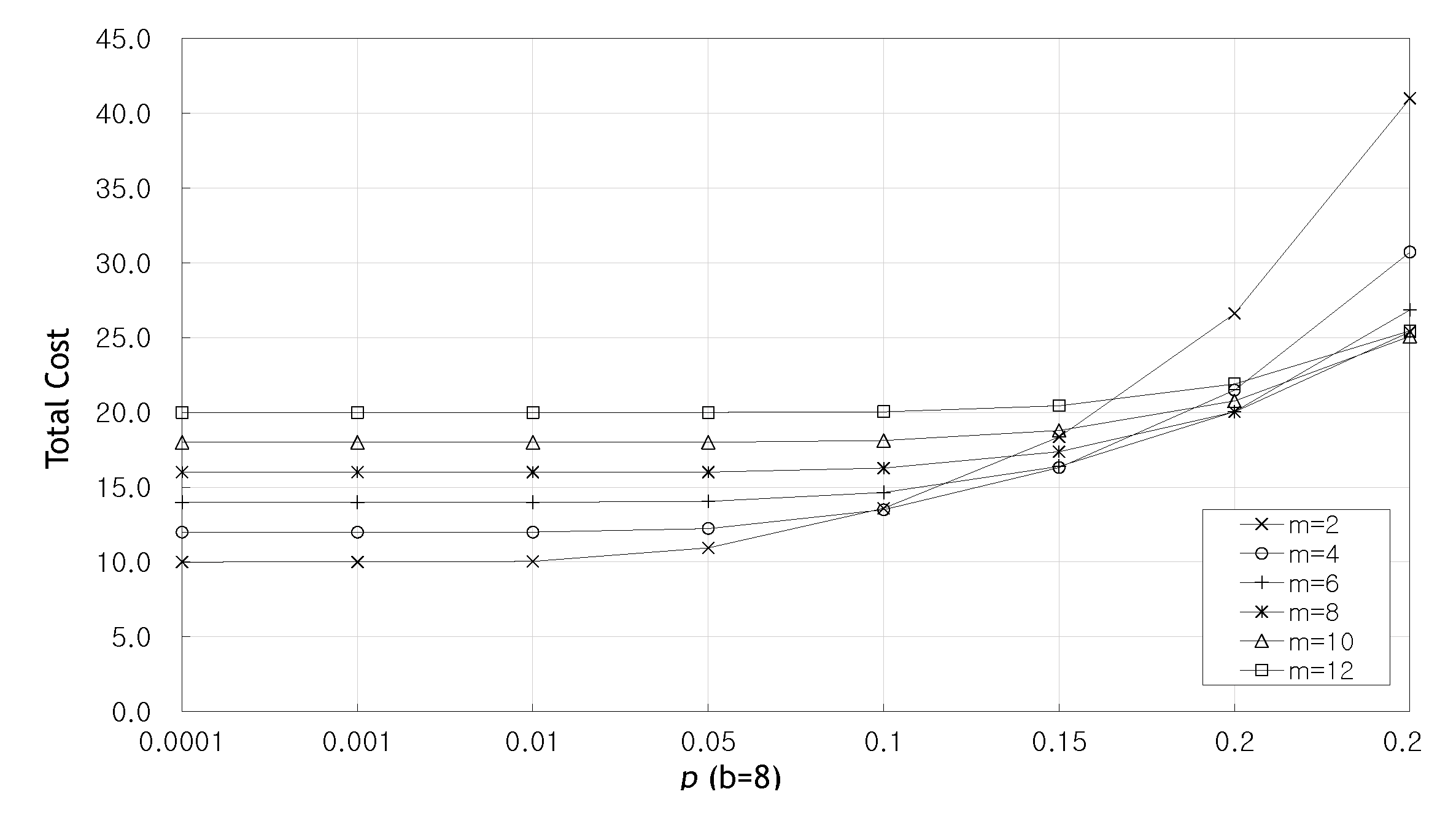
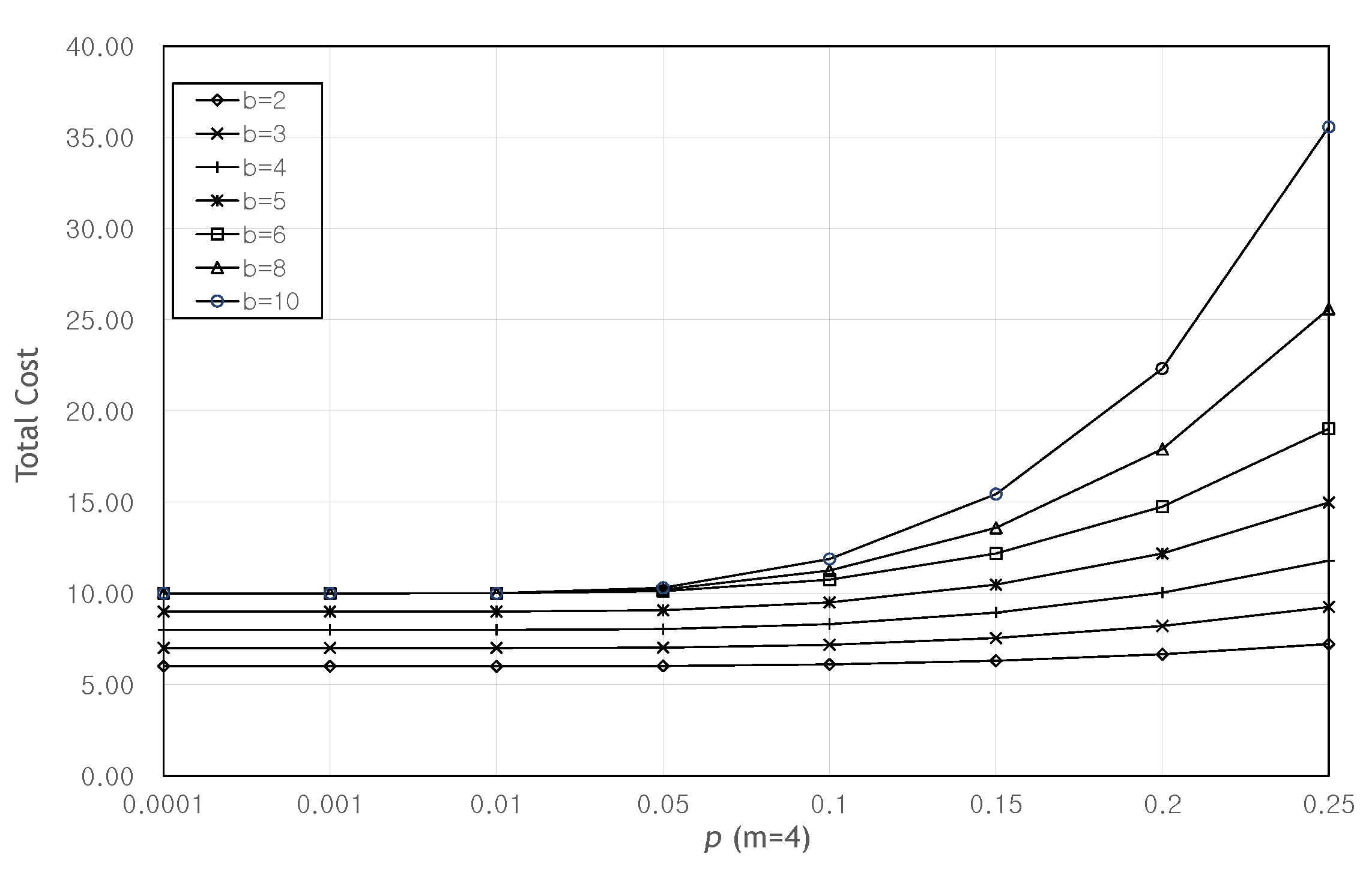
5. Performance Analysis and Results
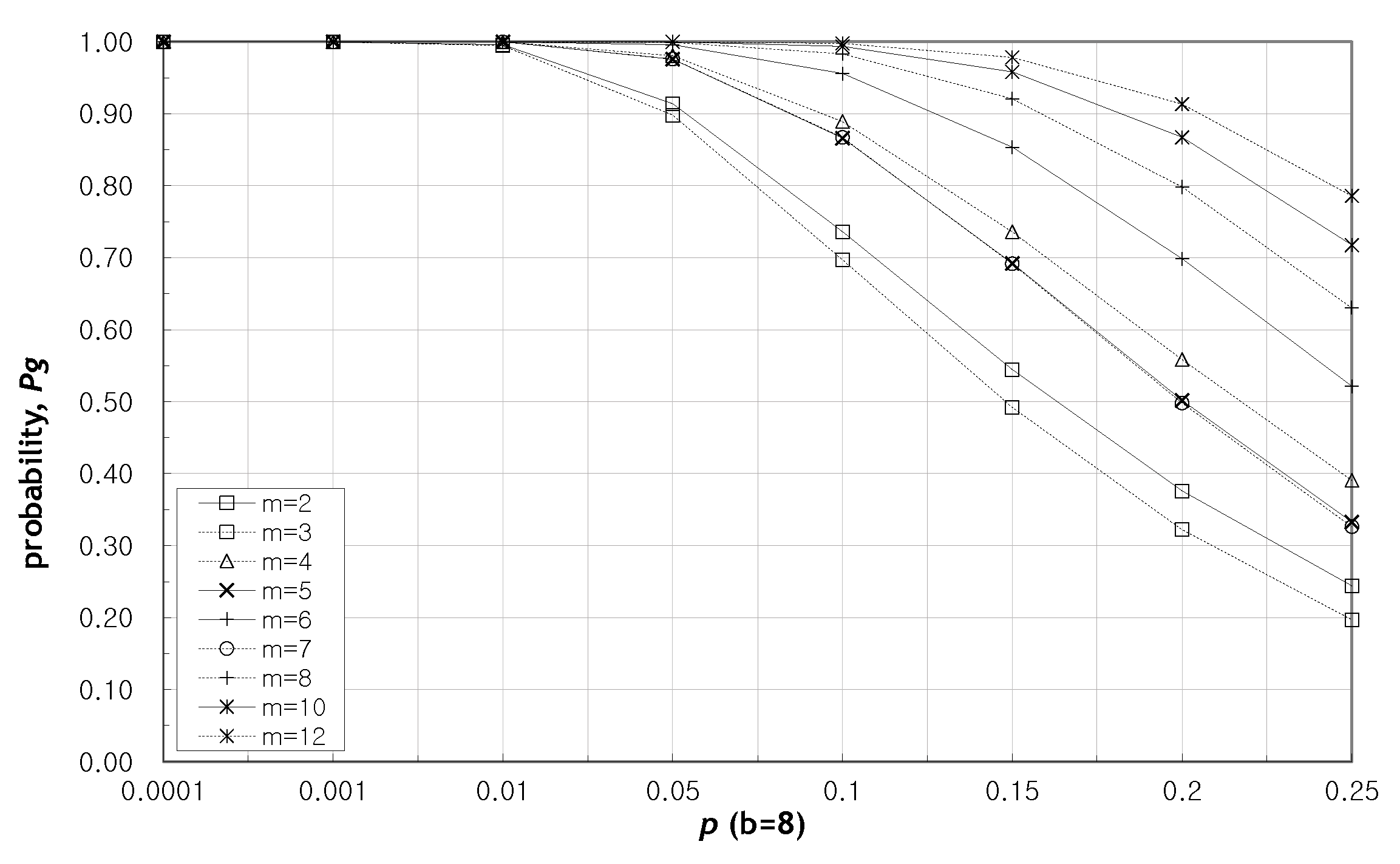
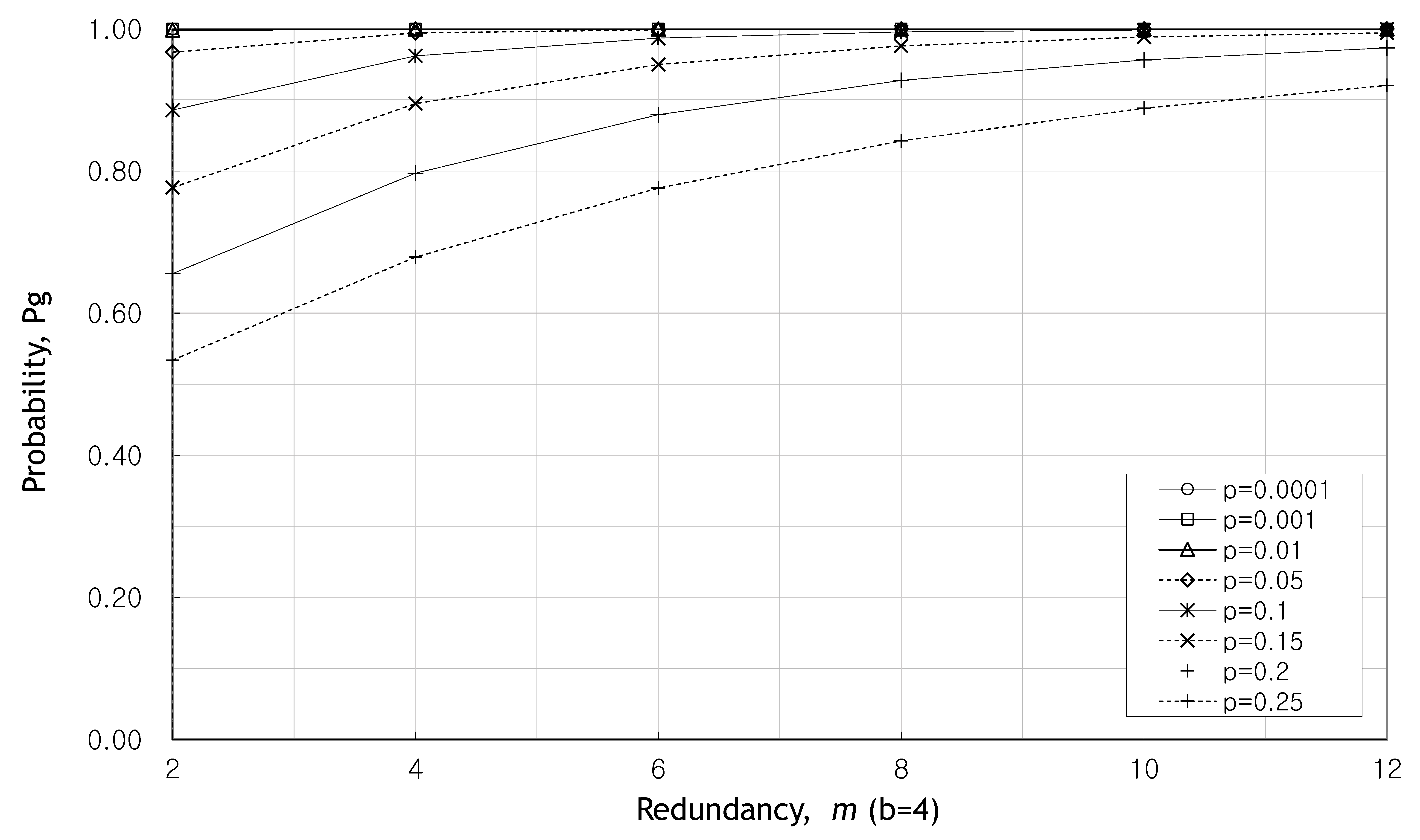
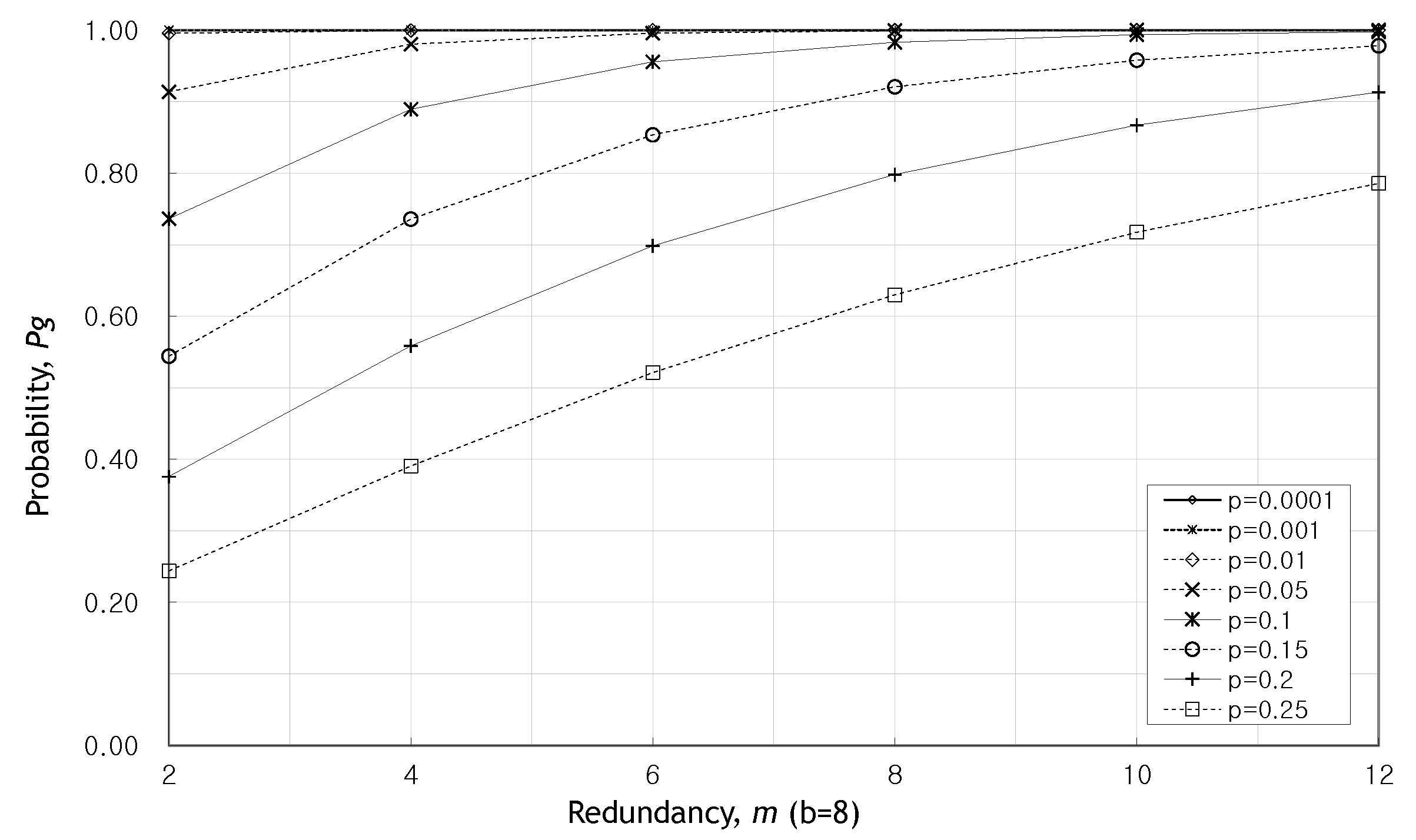
5.1. Performance Analysis
5.2. Results and Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Peralta, G.; C-Fuentes, R.G.; Bilbao, J.; Crespo, P.M. Homomorphic Encryption and Network Coding in IoT Architectures: Advantages and Future Challenges. Electronics 2019, 8, 827. [Google Scholar] [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Li, J.; Liu, Y.; Zhang, Z.; Ren, J.; Zhao, N. Towards Green IoT Networking: Performance Optimization of Network Coding Based Communication and Reliable Storage. IEEE Access 2017, 5, 8780–8791. [Google Scholar] [CrossRef]
- Boneh, D.; Freeman, D.; Waters, B.; Katz, J. Signing a Linear Subspace: Signatures for Network Coding. In International Workshop on Public Key Cryptography; Springer: Berlin/Heidelberg, Germany, 2009. [Google Scholar]
- Ahlswede, R.; Cai, N.; Li, S.-Y.R.; Yeung, W. Network Information Flow. IEEE Trans. Inf. Theory 2000, 46, 1204–1216. [Google Scholar] [CrossRef]
- Lima, L.; Vilela, J.P.; Oliveira, P.F.; Barros, J. Network Coding Security: Attacks and Countermeasures. arXiv 2008, arXiv:0809.1366. [Google Scholar]
- Yu, Z.; Wei, Y.; Ramkumar, B.; Guan, Y. An Efficient Scheme for Securing XOR Network Coding against Pollution Attacks. In Proceedings of the IEEE INFOCOM 2009, Rio de Janeiro, Brazil, 19–25 April 2009. [Google Scholar]
- Shafagh, H.; Hithnawi, A.; Burkhalter, L.; Fischli, P.; Duquennoy, S. Secure Sharing of Partially Homomorphic Encrypted IoT Data. In Proceedings of the 15th ACM Conference on Embedded Network Sensor Systems ACM SenSys’17, Delft, The Netherlands, 5–8 November 2017. [Google Scholar]
- Li, T.; Chen, W.; Tang, Y.; Yan, H. A Homomorphic Network Coding Signature Scheme for Multiple Sources and its Application in IoT. Secur. Commun. Netw. 2018, 2018, 6. [Google Scholar] [CrossRef]
- Wu, G.; Wang, J.; Wang, Y.; Yao, L. Pollution Attack Resistance Dissemination in VANETs Based on Network Coding. Procedia Comput. Sci. 2016, 83, 131–138. [Google Scholar] [CrossRef]
- Cheng, C.; Lee, J.; Jiang, T.; Takagi, T. Security Analysis and Improvements on Two Homomorphic Authentication Schemes for Network Coding. IEEE Trans. Inf. Forensics Secur. 2016, 11, 993–1002. [Google Scholar] [CrossRef]
- Li, J.; Li, T.; Ren, J.; Chao, H. Enjoy the Benefit of Network Coding: Combat Pollution Attacks in 5G Multihop Networks. Wirel. Commun. Mob. Comput. 2018, 2018, 13. [Google Scholar] [CrossRef]
- Mamidwar, N.V.; Gothawal, D. Schemes against Pollution Attack in Network Coding: A Survey. Int. J. Comput. Sci. Inf. Technol. 2015, 6, 5085–5089. [Google Scholar]
- Ayday, E.; Delgosha, F.; Fekri, F. Location-Aware Security Services for Wireless Sensor Networks using Network Coding. In Proceedings of the 26th IEEE International Conference on Computer Communications, Barcelona, Spain, 6–12 May 2007. [Google Scholar]
- Cheng, W.; Yu, L.; Wang, W. Trusted Network Coding in Wireless Ad Hoc Networks. In Proceedings of the 2010 IEEE Global Telecommunications Conference (GLOBECOM), Miami, FL, USA, 6–10 December 2010. [Google Scholar]
- Ji, S.; Chen, T.; Zhong, S. Wormhole Attack Detection Algorithms in Wireless Network Coding Systems. IEEE Trans. Mob. Comput. 2015, 14, 660–674. [Google Scholar] [CrossRef]
- Oliveira, C.H.S.; G-Doudane, Y.; Brito, C.E.F.; Lohier, S. Optimal Network Coding-Based In-Network Data Storage and Data Retrieval for IoT /WSNs. In Proceedings of the IEEE 14th International Symposium on Network Computing and Applications (NCA2015), Cambridge, MA, USA, 28–30 September 2015. [Google Scholar]
- Lei, K.; Zhong, S.; Zhu, F.; Xu, K.; Zhang, H. An NDN IoT Content Distribution Model With Network Coding Enhanced Forwarding Strategy for 5G. IEEE Trans. Ind. Inform. 2018, 14, 2725–2735. [Google Scholar] [CrossRef]
- Cebe, M.; Kaplan, B.; Akkaya, K. A Network Coding based Information Spreading Approach for Permissioned Blockchain in IoT Settings. In Proceedings of the 15th EAI International Conference on Mobile and Ubiquitous Systems: Computing, Networking and Service (Mobiquitous’18), New York, NY, USA, 5–7 November 2018; pp. 470–475. [Google Scholar]
- Dong, J.; Curtmolab, R.; Nita-Rotarua, C. Secure Network Coding for Wireless Mesh Networks: Threats, Challenges, and Directions. In 4th Workshop on Secure Network Protocols 2008(NPSec 2008); Elsevier: Amsterdam, The Netherlands, 2008; pp. 33–38. [Google Scholar]
- Wang, S.; Zhao, J.; Wang, X. Is Network Coding Helpful for BitTorrent: From a Practitioner’s Perspective. In Proceedings of the 19th International Conference on Computer Communications and Networks (ICCCN), Zurich, Switzerland, 2–5 August 2010; pp. 1–6. [Google Scholar]
- Rabin, M. Efficient Dispersal of Information for Security, Load Balancing, and Fault Tolerance. J. Assoc. Comput. Mach. 1989, 36, 335–348. [Google Scholar] [CrossRef]
- Barros, J. Mixing Packets: Pros and Cons of Network Coding. In Proceedings of the 11th International Symposium on (WPMC’08), Lapland, Finland, 8–11 September 2008. [Google Scholar]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, Y.; Lee, G.Y. Attack Detection Using Network Coding in IoT Environment. Sensors 2020, 20, 1180. https://doi.org/10.3390/s20041180
Lee Y, Lee GY. Attack Detection Using Network Coding in IoT Environment. Sensors. 2020; 20(4):1180. https://doi.org/10.3390/s20041180
Chicago/Turabian StyleLee, Yong, and Goo Yeon Lee. 2020. "Attack Detection Using Network Coding in IoT Environment" Sensors 20, no. 4: 1180. https://doi.org/10.3390/s20041180
APA StyleLee, Y., & Lee, G. Y. (2020). Attack Detection Using Network Coding in IoT Environment. Sensors, 20(4), 1180. https://doi.org/10.3390/s20041180




