Abstract
This paper studies the secure communication of a non-orthogonal multiple-access (NOMA) relaying system in the presence of an eavesdropper in which the NOMA communication between a source and two users is assisted by an energy-harvesting (EH) relay. The relay extracts a part of its received signal strength using a power-splitting (PS) policy then harvests energy using a non-linear EH (NLEH) circuit. A friendly jammer sends jamming signals to help secure communication. The jammer is exploited as an additional energy source. A store-and-transmit (SaT) scheme which allows the EH relay to perform energy storing and information transmitting is proposed. For performance evaluation, the closed-form expressions for three metrics, secrecy outage probability (SOP), average achievable secrecy rate (AASR) and average stored energy (ASE) are derived. These results enable studies on the effects of various system parameters, such as NOMA power-allocation factors, target secrecy rates, jammer’s location, and relay’s power levels, on the system performance.
1. Introduction
The rapidly growing demand for radio connectivity in both industrial and residential use has caused various issues in wireless networks: faster battery drain at the device, various access required at the base station, and higher security risk. This motivated studies on relevant efficient techniques. Wireless energy harvesting (WEH), which enables devices charging by scavenging energy from ambient radio signals, physical layer security (PLS), which provides secure communication by exploiting the physical nature of wireless channels, and non-orthogonal multiple access (NOMA), which supports high spectral efficiency, low latency, and massive access by modulating signal on the power domain, are expected as strong candidates to help the future wireless systems overcome these issues.
Based on the fact that radio signal can carry both the energy and information, the author of [1] designed two WEH receiver architectures to allow a simultaneous wireless information and power transfer (SWIPT), time-switching (TS) and power-splitting (PS) where the energy harvesting (EH) and information decoding (ID) functions are separated in time domain and power domain, respectively. The trade-off between harvested energy and information rate of diverse SWIPT systems using TS and PS policies was characterized in [1,2,3]. The works of [4,5] examined different techniques to improve the performance of SWIPT systems via enhancing the amount of harvested energy, such as multi-antenna energy harvester, multi-band energy harvester, and interference-aided WEH. In addition, the work of [6] proposed to exploit both downlink and uplink transmissions of a multi-user TMDA-based system to boost the harvested energy at users. The presence of WEH receivers can be regarded as a potential security threat to wireless communication; hence, security in SWIPT has gained much interest from recent studies. The works of [7,8] used a beamforming technique to increase the secrecy capacity and/or harvested energy of multi-antenna SWIPT systems by optimizing the beamforming vectors. On the other studies, friendly jamming signals were employed to improve secure communication via an EH relay in which the jammer can interfere with wire-tapped information and provide additional energy at the relay [9]. Another approach presented in [10,11] is to use WEH nodes as jammers that employ their harvested energy to assist the secure links.
In the NOMA scenario, the work of [12] designed strategies for a wireless-powered uplink NOMA to maximize the system throughput or achieve the high fairness in throughput of users. A similar work concerning the energy-and-rate efficiency was presented in [13]. The authors of [14] exploited the advantage in distance of the near user (NU) to perform a SWIPT-based cooperative communication; hence, NU can set up an additional link to the far user (FU) using its harvested energy. The work of [15] designed a strategy to maximize the harvested energy of each harvester in a cognitive radio (CR) NOMA system, especially, the non-linear energy harvesting (NLEH) model was considered. The works of [16,17] investigated the NOMA communications for the WEH machine-to-machine networks and focused on minimizing the total energy consumption at the devices and gateways via joint power control and time allocation. To guarantee security in multi-user networks, the studies on secure communication of SWIPT-based NOMA systems are needed. The work of [18] investigated the secure transmission of a WEH relaying networks via analyzing the secrecy outage probability (SOP) and secrecy throughput in a delay-limited mode. The works of [19] considered a downlink NOMA system containing several EH receivers that can wiretap confidential information. To maximize the sum secrecy rate of this system, a strategy for optimizing NOMA power-allocation factors was proposed. The authors of [20] studied secrecy energy efficient in a CR-NOMA system with NLEH. This work focused on developing strategies to find the optimal transmit powers of WEH secondary transmitters for given conditions of energy channels.
It is seen that most studies on PLS in SWIPT-based NOMA systems were performed under the assumption of a linear energy harvesting (LEH) model. In addition, the NLEH model proposed in [21] is not mathematically tractable [22]; hence, simpler alternative NLEH models are employed to obtain analytical results for system performance. Motivated by the above assessments, this paper studies the secure communication of a SWIPT-based cooperative NOMA system with NLEH and friendly jamming, and derives analytical results that facilitate performance evaluation and system design. In this system, a source communicates with two users via a NLEH relay that harvests energy form the source signal and jamming signal. The use of friendly jammer can reduce the security risk from a passive eavesdropper. The contributions of this paper are described as follows.
- We propose a store-and-transmit (SaT) scheme providing multi-transmit-power levels (MTPLs) at the EH relay. This simplifies the design of EH transceivers, reduces the energy wasted due to ineffective connectivity, and enables the relay to store a part of energy to maintain its important activities (for the harvest-to-transmit (HtT) scheme, the EH relay uses all the harvested energy to transmit information and maintains its important activities with its limited battery reserves). Moreover, the SaT scheme allows the calculations in performance to become analytically tractable. By using accordant MTPLs, the obtained analytical results for the SaT scheme can allow evaluations in the system performance of the HtT scheme.
- Three performance metrics, SOP, average achievable secrecy rate (AASR) and average stored energy (ASE), are studied for performance evaluation. We derive closed-form expressions for the SOP (for the whole communication and for the case that the relay is active) and the AASR of each user; in addition, we derive an exact analytical expression for the ASE. We use Montes-Carlo simulations to verify the accuracy of the analytical results.
- Finally, the effect of various key system parameters, the location of jammer, target secrecy rates, NOMA power-allocation factors, transmit-power strategies (TPSs) at the EH relay, on the system performance, is studied to provide insight into the system design.
The rest of this paper is organized as follows. The system model and preliminary results are presented in Section 2. In Section 3, analytical expressions for the SOP, AASR and ASE are derived. Simulation results and discussions are presented in Section 4. Finally, the conclusion is presented in Section 5. Appendix A–Appendix D present the proofs of the propositions.
Notation: We use to denote the link from node A to node B; ⊗ is the XOR operator; is a complex Gaussian distribution with zero mean and variance ; is the exponential integral function [23] (Eq. (8.211.1)); is the generalized hypergeometric function [23] (Eq. (9.14.1)); is the expectation of a random variable (RV) X; is the conditional expectation of X given an event Y; and .
2. System Model and Preliminary Results
2.1. System Model
We consider an EH relaying NOMA system, as shown in Figure 1a, including a source S, a destination D, a decode-and-forward (DF) NLEH relay R, a friendly jammer J, an eavesdropper E and two users, i.e., a NU and a FU . Due to the presence of E, which tries to overhear the user’s confidential information, J is employed to send jamming signals to interfere with E and these signals can be exploited as an additional energy source for R. All nodes are single–antenna devices. We assume that (i) , and E are close to the cell edge; hence, there are no direct links from S to and E, and the users and E decode the source’s information via relay’s forwarded signal; (ii) the channels undergo independently and non-identically distributed (i.n.i.d.) Rayleigh fading; (iii) the channels are constants during a block time T; (iv) local channel state information (CSI) is available at each node; and (v) the jamming signal is only revealed to legitimate nodes.
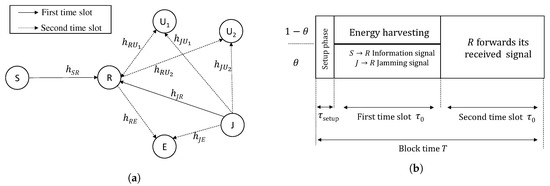
Figure 1.
(a) The system model and (b) The power-splitting policy at R.
Assumption (v) is explained as the follows. Each legitimate node and J establish a shared secret key, i.e., , using CSI-based key generation method [24]. Then J broadcasts two combined keys and . Using their own key, all legitimate nodes can discover all secret keys while E cannot do that due to lack of global CSI; hence, only legitimate nodes can eliminate the jamming signal on their received signals. Let denote the duration for the setup phase consuming for channel estimation and secret key generation. The remain of block time T is separated into two equal time slots, , (illustrated in Figure 1b) and the communication during each time slot is described in Section 2.3 and Section 2.4.
2.2. Non-Liner Energy Harvesting Model and Store-and-Transmit Protocol
Figure 2a–c show the relations between the received power and harvested power for the LEH and NLEH models. The LEH model assumes a linear relationship at the harvester where is energy conversion efficiency. However, measurements in [25,26] show the non-linear relationship between and which is well modeled using a logistic function as [18]
where is the maximum harvested power of the harvester, and and are EH parameters of the harvester. It is seen from (1) that the random variables in are input variables of an exponential function, this leads to the impossibility of grouping or separating independent random variables to perform further calculations. For that reason, the studies on SWIPT systems commonly adopt the LEH model to simplify calculations instead of using (1).
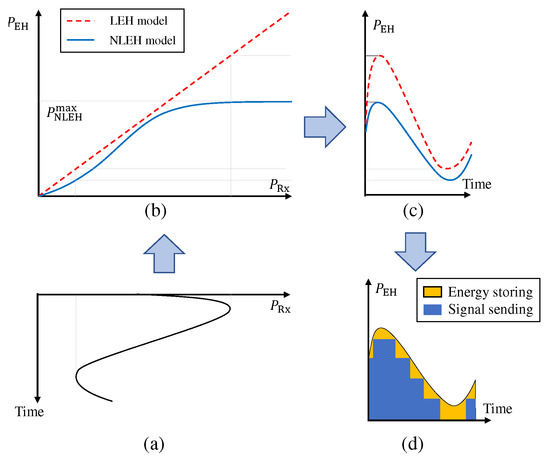
Figure 2.
(a) The received power at the harvester, (b) the LEH and NLEH models, (c) the harvested energy and (d) the SaT scheme with NLEH.
In this paper, we propose a new SaT scheme aiming to support the SWIPT relaying systems. Specifically, this scheme allows the EH relay to choose the appropriate transmit-power level and then perform the energy-storing and information-forwarding tasks simultaneously (as illustrated in Figure 2d). The SaT scheme includes MTPLs represented by an output-power space (OPS) where are transmit-power levels supported at R and satisfy . For a given , the instantaneous transmit power of R, , is a function of determined by a TPS as the follows.
The remaining harvested energy after sending information at power is stored in the battery of R for maintaining other important activities. The power for energy storing is given by
The randomness of effects on both and . The ASE is discussed in Section 3.3 and the cumulative distribution function (CDF) of is presented in Proposition 1. By using the SaT scheme, the calculations for system performance of NLEH relaying systems become analytically tractable. Moreover, with sufficient number of transmits-power levels and a small “power gap” between two consecutive transmit-power levels in , the system performance for the SaT scheme is close to that for the HtT scheme; hence, the SaT scheme can be considered to be an approximate solution to access the system performance of the HtT-based NLEH relaying systems.
2.3. Communication in the First Time Slot
During this time slot, S broadcasts an information at power where and are the desired information of and , respectively, and are NOMA power-allocation factors at S and . R uses PS policy, as shown in Figure 1b, to harvest energy. Moreover, J gives an addition energy at R by sending jamming signal at power . Letting and be the channel coefficient and distance of the link (node A and node B can be and J), respectively, the received information signal at the antenna of R is . Next, R uses a portion for EH and the rest portion for information decoding (ID); hence, the received power at the EH component and input signal at the ID component are expressed as
where ; and is an additive white Gaussian noise (AWGN) at R. From Assumption (ii), is an exponential RV with parameter where is path loss exponent. The probability density function (PDF) and CDF of are given by and , respectively.
Since R can eliminate the effect of the jamming signal in (5), the SNR for and the SINR for obtained at R by using successive interference cancellation (SIC) receiver are given by
where the parameters , are defined in Table 1. The approximation at (a) is based on the assumption that the noise power is small as compared to the interference caused by .

Table 1.
The list of parameters .
Proposition 1.
The CDF and PDF of a RV are respectively expressed by
The CDF of , where and the probability are respectively expressed by
where and .
2.4. Communication in the Second Time Slot
After decoding and , R encodes them as then forwards to the users at power where and are NOMA power-allocation factors at R and . During this time slot, J also sends jamming signal at power to interfere with E. The received signals at nodes are respectively given by
where is the AWGN at .
Since and can eliminate the effect of on its signal, the SINRs for at and are respectively given as
Using the SIC receiver, can decode with the SNR given as
Since E cannot eliminate the effect of on its signal, the SNR for and SINR for obtained at E by using SIC receiver are given as
where . Moreover, we denote as a RV which represents for as .
The approximations at and are based on the assumption that the noise power is small as compared to the interference caused by and .
Proposition 2.
The CDF and the PDF of Z are given by
Proof.
(18) and (19) are obtained via solving and , respectively. □
2.5. The Achievable Secrecy Rates
By definition, the achievable secrecy rate is the maximum secrecy rate for sending confidential information to a legitimate node while the eavesdropper is unable to decode any information. Letting be the achievable rate for at the node , the achievable secrecy rate for for overall system is calculated by.
where is the condition for successfully decoding at both and , hence, SIC at operates correctly.
3. System Performance Analysis
3.1. The Secrecy Outage Probability (SOP)
For NOMA communications, the SOP is defined as the probability of occurring the secrecy outage event, i.e., the achievable secrecy rate of a user is less than its target secrecy rate, at any user. We study the SOP in two scenarios where the outage events are counted over the relay’s transmission duration (i.e., R is "ON"), , and the whole communication duration (i.e., for both cases R is "ON" and "OFF"), . With given target secrecy rates for , and , and are respectively calculated as
where is the probability of the event that R is "OFF" and the expression for is presented in Proposition 3. represents for the outage event that occurs when R forwards the information but the instantaneous secrecy rates at the users do not satisfy the user’s target secrecy rates. is counted for whole the communication duration, hence, the expression for is obtained using Bayes’s law as follows:
Proposition 3.


Table 2.
The analytical expressions for and
Proof.
See Appendix A. □
It is seen from (22) that is a lower bound for . When is set at high values, the increase in can result the worse and better (note that is an increasing function of ; for practical scenarios, should be greater than a minimum threshold of the incident power, i.e., , to activate the EH circuit). An appreciate choice for OPS could be exploited to guarantee different goals of the system. For providing reliable communication, the OPS includes high power levels to reduce ineffective communication caused by low relay transmit powers. For frequent communication, the OPS can exploit low power levels. The jamming signal strengths are also an important factor in the SOP. Specifically, the harvested energy is enhanced, and the overhearing rate is decreased when the jamming signal strengths at R and E increase, respectively. This leads to improvement in the SOP.
3.2. The Average Achievable Secrecy Rate (AASR)
3.2.1. The Average Achievable Secrecy Rate for
Let be the event that the transmit power of R is , i.e., , be an event space defined as , and be the event of existing secure communication for during the second time-slot communication (or ). The AASR of , , is calculated by averaging the random variable for all possible cases of (represented by ) and (due to the presences of random channel gains, and are random events). Using the law of total expectation, is calculated as
The factor indicates the effect of the setup phase duration on the AASRs. In the multiple-user scenario, the increase in causes a significant influence on the amount of the received confidential data. Using the fact that , we can obtain an upper bound for as follows.
Proposition 4.

The analytical expression for is given by the following equation.
where and are given in (28)–(30), and the expressions for and are presented inTable 3.

Table 3.
The analytical expressions for and .
Proof.
See Appendix B. □
3.2.2. The Average Achievable Secrecy Rate for
The AASR for is calculated by
The approximation at is achieved by using and . Similarity, we can attain an upper bound for as follows
Proposition 5.
The analytical expression for is given by the following equation.
where is calculated by
Proof.
See Appendix C. □
For , it is seen from the definition of and (A17) that the increase in the jamming signal strength at E leads to the increase in and (by degrading ), and the increase in the jamming signal strength at R leads to the increase in (by enhancing ). For , there is an upper limit for , i.e., (as observed in (33)), and reaches iff or is very small. With the presence of jammer, the eavesdropping rate can be reduced, hence, and can be set at the same value to gain the high AASRs for both users.
3.3. The Average Stored Energy (ASE)
After extracting the amount of energy for information forwarding, the average remaining energy at R for energy storing is given by
Proposition 6.
The analytical expression for the ASE is given by the following equation.
where , for the case of ,
and for the case of ,
with and defined as
Proof.
See Appendix D. □
The first element of the right-hand side (RHS) of (36), i.e., , is the average harvested energy of R, and it is a constant for a given system configuration. The remain of the RHS of (36) is the portion of harvested energy employed for information forwarding. Therefore, the ASE depends on the selected MTPLs in OPS. To enhance and AASR, R should store less energy and use higher portion of harvested energy to assist the communication. This means that the OPS should include more MTPLs with small “power gap”. To guarantee a target values of ASE, the OPS should include fewer MTPLs with equal “power gaps”. As shown Figure 2d, the equal “power gaps” can allow R to send information at more effective power levels. For the HtT scheme, the ASE is equal to 0. Since the ASE depends on , it receives lower values when the system spends more time for the setup phase.
4. Results and Discussions
In this section, we present numerical results to validate the analytical expressions presented in Section 3. Unless otherwise specified, we set dBm, , bits/sec/Hz, bits/sec/Hz, mW, and (We use the parameters of the NLEH model given in [27]). We assume that for the two-user case; hence, we do not examine the effects of on the AASR results. The coordinates (in meters) in the two-dimensional plane of and J (as illustrated in Figure 1a) are set at and , respectively. We consider the SaT scheme in two scenarios, MTPL and STPL. The STPL is a simpler case of the MTPL where R supports only one transmit-power level. For the MTPL, we examined four OPSs given as mW, mW, mW and mW. For the STPL, the supported transmit-power level of R is examined in four cases, i.e., 5 mW, 10 mW, 15 mW, and 20 mW. Moreover, we consider the case that R uses the HtT scheme to assist the communication and show that the SaT scheme using approximates well the HtT scheme.
In Figure 3, we show the effects of required secrecy rates, and , on the SOP. and show increasing trends with the increases in and/or . It is easy to show that bits/s/Hz. The analytical results match well with the simulation results except for the case that gets close to and gets relatively low values. At higher values of , i.e., 15 mW and 20 mW, the accuracy of the analytical results is improved significantly. The reason is the approximations at (13), (14) and (A13) become less accurate when is low and approximates , respectively. It is seen in Figure 3a that there is a change in the effective values of , which yields the lowest for the STPL. With the increase in , R chooses higher transmit-power levels to achieve the lowest . This disadvantage is overcome by the MTPL. By sending information at diverse transmits powers, the MTPL shows its superiority in improving the secrecy outage performance. The HtT scheme achieves the best performance and the analytical results for the SaT scheme using approximate well with the simulation results for the HtT scheme.
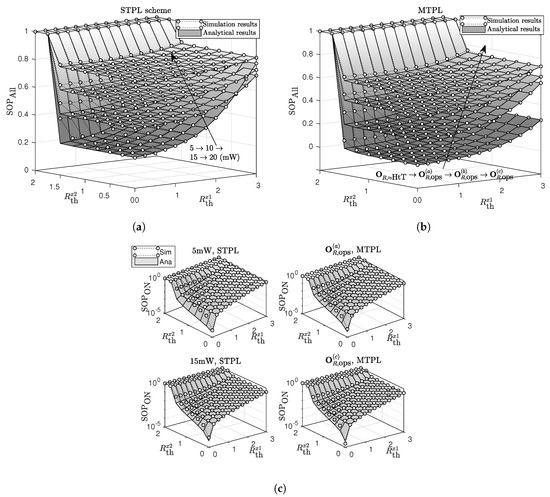
Figure 3.
The effect of and on (a) SOPAll for the STPL scheme, (b) SOPAll for the MTPL scheme, and (c) SOPON for both STPL and MTPL schemes.
In Figure 4, we show the effects of NOMA power-allocation factors, , on the secrecy performance. Similarly, for given value of , there is an upper limit for , denoted as (using (7), (13) and (14), we can show that ). The SOP is equal to zero as or , and achieves good values as is around . The less accuracy of the analytical results when approximates and gets relatively low values can be explained in a similar way as discussed in Figure 3. For the AASR results, the secrecy rates of and follow different trends, i.e., increasing function and decreasing function of , respectively, that are the common trends for all NOMA systems. The AASR of for the MTPL outperforms that for the STPL due to the great advantage in using multiple transmit-power levels. The analytical results of the AASR of for both STPL and MTPL are the same; however, their simulation results indicate that the MTPL gives higher secrecy rates and fits the analytical results better than the STPL.
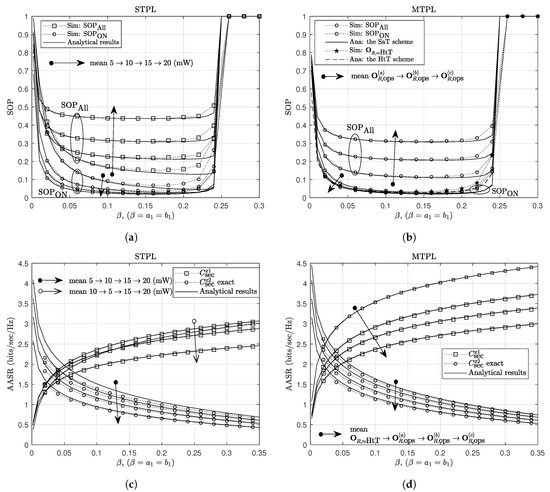
Figure 4.
The effect of NOMA power-allocation factors on (a) the SOP for the STPL scheme, (b) the SOP for the MTPL scheme, (c) the AASR for the STPL scheme, and (d) the AASR for the MTPL scheme. Other parameters: J(1.5,−3).
In Figure 5, we present the effect of the energy harvesting coefficient on the secrecy performance. As shown that the secrecy performance improves when increases from 0 to an optimal value of , denoted by , then it degrades with further increase in . These trends are explained using the effect of on the signal strength employed for information decoding and energy harvesting (i.e., and , respectively). As shown in Figure 5, varies in the range of [0.1,0.2]. The trend for is similar to that for except for the case shifts to 1. Because the is calculated for the case that R harvests enough energy to send information at power ; hence, if mW, does not tend to 0 when shifts to 1. Moreover, the probability that R is ON becomes very small when is close to 1; hence, this causes the less accuracy in simulation results. For the , since R almost assists the communication during all block times, and get similar values. The effect of observed in Figure 5 agrees with previous studies in SWIPT relaying system. The obtained results indicate that NLEH relay uses higher portions (i.e., lower values of ) of its received signal strength for energy harvesting to archive the optimal performance as compared to studies with the LEH model (e.g., in [4] and in [28]).
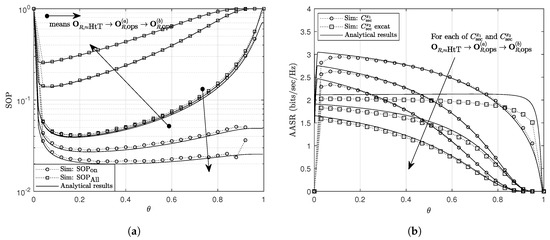
Figure 5.
The effect of θ on (a) the SOP and (b) the AASR. Other parameters: PS = PJ = 27 dBm, a1 = b1 = 0.1, (, ) = (1, 0.6) bits/sec/Hz.
In Figure 6, we show the effect of jammer’s location on the secrecy performance. When J moves far from R, the decrease in received power of R and the increase in wiretapping rate of E cause the lower secrecy performance. The and AASR converge to low positive values when J shifts to the coordinate (9,−10).This result indicates that without jammer, the system can satisfy low security-level requirements, such as . In this case, the secrecy capacity only depends on the relay’s active-state probability and the difference in channel gains between legitimate links (i.e., and ) and illegitimate link (i.e., ). Considering the of the STPL, the improves during range , then it degrades with the further increase in . The reason is when J moves toward the coordinate (3,-4), the shorter distance causes the higher interference at E (note that the signal strength at E is constant due to fixed values of in the STPL) leading to the enhancement in secrecy rate. This trend is unclear in Figure 6b because the distance can also affect the values of . The results in Figure 6 confirm that the jamming signal plays an important role in improving the security rates.
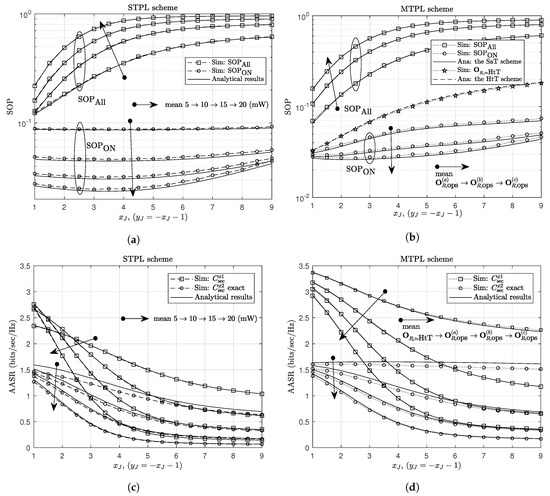
Figure 6.
The effect of the jammer’s location on (a) the SOP for the STPL scheme, (b) the SOP for the MTPL scheme, (c) the AASR for the STPL scheme, and (d) the AASR for the MTPL scheme.
In Figure 7, we examine the system performance under two TPSs, at R, i.e., and ( involves a practical harvester where mW, and involves an ideal harvester with mW), and different transmit-power configurations at the energy sources, i.e., 23 dBm, 27 dBm and 30 dBm schemes. The output-power levels, , for is determined by where is the minimum power supported at EH transceiver ( mW and mW for and , respectively). There are two effects of increasing N on the TPSs. The first effect is the smaller “power gap” between two successive power levels when N increases. Since R uses the remaining energy for energy storing after it extracts amount energy for assisting the communication, the smaller “power gap” causes the lower stored energy at R; hence, the ASE is a decreasing function of N. When lifts, the higher remaining energy attained in range can yield the greater ASE (as shown in Figure 7, the ASE for is greater than that for ). The second effect is that the transmit powers of R are spread over , such as and shift to and , respectively. This makes R help the communication more frequently with more appropriate transmit powers. Therefore, the and AASR achieve better values as N increases. The frequent operation of R achieved by low values of does not give any advantages in enhancing . On the other hand, lower values of causes more outage events. As a result, the becomes worse as N increases.
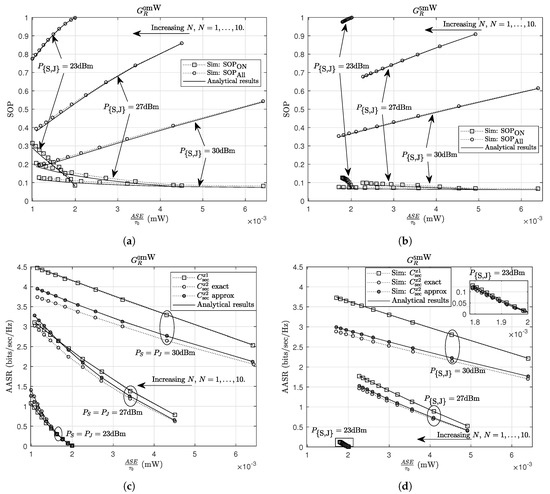
Figure 7.
The trade-off between the SOP and the ASE for (a) and (b) ; and the trade-off between the AASR and the ASE for (c) and (d) .
For three transmit-power configurations, the higher transmit powers yield better results in and AASR. The ASEs of are increasing functions of and . An interesting result is the ASEs of can achieve better values at lower values of and . For instance, when , the 27 dBm scheme yields a higher ASE as compared to the rest schemes. This result can be explained using the relay’s received power and the “power gap”. The relay’s received power for the 27 dBm scheme is not too low to gain low ASEs as observed at the 23 dBm scheme (the verify that R is almost idle in the 23 dBm scheme due to too low received power), and it is not too high to lose the great advantage in harvesting energy in range mW. These results provide useful insight in designing practical systems, such as choosing appropriate powers at the energy sources and the optimum transmit-power strategies at the EH transceivers to satisfy the requirements in secrecy capacity and amount of stored energy.
5. Conclusions
This paper studied the secrecy performance of a NOMA cooperative system via a NLEH relay. A friendly jammer, which can be an authorized node in the network, was employed to enhance the secrecy performance by rising the received power at the relay and interfering with the wiretapping link. A SaT scheme was proposed aiming to design feasible NLEH transceivers and enable energy-storing mechanism. Moreover, this scheme allowed the calculations for the , and AASR to become mathematical tractable. The analytical results obtained using the SaT scheme can enable analytical performance evaluations for the HtT-based NLEH relaying systems, which cannot be achieved by the direct approaches. The current study considers NOMA communications for two users; however, the analysis results for this study can be extended to the multiple-user scenario. The accuracy of the calculation was verified by simulation which showed that the analytical results agree well with simulation results for most considered cases. In addition, it pointed out the special cases causing the less accuracy for the analytical results, i.e., the target secrecy rate of the FU is chosen with inappropriate values or the relay’s transmit power is too low. The STPL was examined to confirm the superiority of the MTPL in enhancing the secrecy performance. Moreover, the effects of system parameters on the SOP, AASR and ASE were investigated. These effects provided insight into the system design. For instance, the OPS should include both high and low MTPLs with equal “power gaps” to archive the best secrecy performance, and the number of MTPLs is smaller enough to allow energy storing at relay; for a given OPS, the transmit powers at the source and jammer could be appropriately selected to guarantee the ASE at relay; the use of jammer produces a great advantages in enhancing harvested energy and secrecy performance; and the analytical results allow network designers to find optimal values for key system parameters, e.g., the optimal power-splitting ratio for the considered system is around 0.2. The more general model where the eavesdropper is not close to the cell edge and is capable of receiving signals from both the source and relay will be our future works. To confine the eavesdropping capability for this model, different transmit codewords can be exploited [29].
Author Contributions
Conceptualization, V.P.T. and I.-P.H.; Investigation, V.P.T.; Methodology, V.P.T. and I.-P.H.; Writing–original draft preparation, V.P.T.; Writing–review and editing, V.P.T. and I.-P.H.; Project administration, I.-P.H.; Funding acquisition, I.-P.H. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by Basic Science Research Program(2018R1A2B6001680) and the Priority Research Centers Program(2019R1A6A1A03032988) through the National Research Foundation of Korea.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A. Proof for Proposition 3
Since , is considered in two cases: (i.e., ) and (i.e., ), as follows.
By substituting (20) and (21) into (A1), and analyzing the independent elements in and , we can rewrite as the follows
Similarly, is rewritten as
In (A7), denotes the event that the first-hop communication is not outage and .
Appendix A.1. Calculation for
Using the expressions for and , we can rewrite as
The calculations for are considered in three cases
Appendix A.2. Calculation for
It is seen that and do not have any exact close-form expressions due to their complexity. However in the case that the noise power, , is small as compared to the interference caused by and , we have , hence, can be approximated by
where .
The calculations for are considered in two cases:
- For , we have .
- For , is rewritten bySubstituting (19) and the CDF of into (A14) yieldsUsing partial integration and [23] (Eq. (3.352.1)) we can show thatUsing (A16), the expression for in this case is obtained as in Table 2.
Finally, Proposition 3 is proven.
Appendix B. Proof for Proposition 4
Using the expressions for and , and analyzing the independently elements in (26), we can rewrite (26) as
Appendix B.1. Calculation for
We rewrite as
Appendix B.2. Calculation for
Using expression of , can be rewritten as
Using partial integration, we can prove the following equation
where is an antiderivative of a continuous function on and satisfies . Please note that does not need to be a CDF.
Using (A20) for solving , and then using [23] (Eq. (8.211.1)), is rewritten as in (A21). After some manipulations and using [30] (Eq. (4.2.1) and Eq. (4.2.9)), can be expressed as in (A22). It is seen that follows the form of (A20) (for on ; and for on ). By reformulating the integral in with (A20) and using [23] (Eq. (8.211.1)) (only for ). The expressions for are expressed as in (A23). Using (A21)–(A23), the expression for is obtained as in Table 3.
Appendix B.3. Calculation for
By substituting the expressions for and , can be rewritten as
where .
Using where and , we can rewrite as
Solving the second integral with the help of partial fraction expansion method, is obtained as
Since (A26) follows the form of (A20), (A26) can be solved using (A20) and [23] (Eq. (8.211.1)). The expression for is given as in Table 3.
Finally, Proposition 4 is proven.
Appendix C. Proof for Proposition 5
From (32) and (33), it is seen that . To derive the expression for , we need the CDF of the RV . The CDF of U can be obtained using the (18) as follows.
Next, we rewrite as
The integral in (A28) is solved using (A20). Substituting (A28) into , Proposition 5 is proved.
Appendix D. Proof for Proposition 6
Before analyzing , we study two integrals and , which are useful to find the expression for , where and c are positive real numbers. Letting , we can rewrite and as
Using [23] (Eq. (9.111)), can be expressed as in (39).
In the following, we show the steps to solve . First, we find the antiderivative of using the Taylor series as the follows.
The equality at is obtained using [23] (Eq. (9.14.1)). Then, we perform partial integration on for the two functions and , hence, is rewritten as
Finally, with the help of [23] (Eq. (7.512.12)), is be expressed as in (40).
Appendix D.1. Calculation for in the case of
In this case, is rewritten by using (9) as follows.
Using , is calculated as in (37).
Appendix D.2. Calculation for in the case of
In this case, is rewritten by using (9) as follows.
Using , is calculated as in (38).
Finally, Proposition 6 is proven.
References
- Zhang, R.; Ho, C. MIMO Broadcasting for Simultaneous Wireless Information and Power Transfer. IEEE Trans. Wirel. Commun. 2013, 12, 1989–2001. [Google Scholar] [CrossRef]
- Liu, L.; Zhang, R.; Chua, K. Wireless Information Transfer with Opportunistic Energy Harvesting. IEEE Trans. Wirel. Commun. 2013, 12, 288–300. [Google Scholar] [CrossRef]
- Liu, L.; Zhang, R.; Chua, K. Wireless Information; Power Transfer: A Dynamic Power Splitting Approach. IEEE Trans. Commun. 2013, 61, 3990–4001. [Google Scholar] [CrossRef]
- Zhu, G.; Zhong, C.; Suraweera, H.; Karagiannidis, G.; Zhang, Z.; Tsiftsis, T. Wireless Information and Power Transfer in Relay Systems With Multiple Antennas and Interference. IEEE Trans. Commun. 2015, 63, 1400–1418. [Google Scholar] [CrossRef]
- Muncuk, U.; Alemdar, K.; Sarode, J.; Chowdhury, K. Multiband Ambient RF Energy Harvesting Circuit Design for Enabling Batteryless Sensors and IoT. IEEE Internet Things 2018, 5, 2700–2714. [Google Scholar] [CrossRef]
- Yang, Z.; Xu, W.; Pan, Y.; Pan, C.; Chen, M. Optimal Fairness-Aware Time and Power Allocation in Wireless Powered Communication Networks. IEEE Trans. Commun. 2018, 66, 3122–3135. [Google Scholar] [CrossRef]
- Niu, H.; Zhang, B.; Guo, D. Outage Constrained Robust Beamforming and Power Splitting for Secure MISO SWIPT Channel. IEEE Wirel. Commun. Lett. 2017, 6, 826–829. [Google Scholar] [CrossRef]
- Zhu, Z.; Chu, Z.; Zhou, F.; Niu, H.; Wang, Z.; Lee, I. Secure Beamforming Designs for Secrecy MIMO SWIPT Systems. IEEE Wirel. Commun. Lett. 2018, 7, 424–427. [Google Scholar] [CrossRef]
- Nguyen-Huu, P.; Ho-Van, K.; Bao, V. Secrecy outage analysis of energy harvesting two-way relaying networks with friendly jammer. IET Commun. 2019, 13, 1877–1885. [Google Scholar] [CrossRef]
- Liu, W.; Zhou, X.; Durrani, S.; Popovski, P. Secure Communication with a Wireless-Powered Friendly Jammer. IEEE Trans. Wirel. Commun. 2016, 15, 401–415. [Google Scholar] [CrossRef]
- Xing, H.; Wong, K.; Chu, Z.; Nallanathan, A. To Harvest and Jam: A Paradigm of Self-Sustaining Friendly Jammers for Secure AF Relaying. IEEE Trans. Signal Process. 2015, 63, 6616–6631. [Google Scholar] [CrossRef]
- Diamantoulakis, P.; Pappi, K.; Ding, Z.; Karagiannidis, G. Wireless-Powered Communications With Non-Orthogonal Multiple Access. IEEE Trans. Wirel. Commun. 2016, 15, 8422–8436. [Google Scholar] [CrossRef]
- Tang, J.; Yu, Y.; Liu, M.; So, D.; Zhang, X.; Li, Z.; Wong, K. Joint Power Allocation and Splitting Control for SWIPT-enabled NOMA Systems. IEEE Trans. Wirel. Commun. 2020, 19, 120–133. [Google Scholar] [CrossRef]
- Liu, Y.; Ding, H.; Shen, J.; Xiao, R.; Yang, H. Outage Performance Analysis for SWIPT-Based Cooperative Non-Orthogonal Multiple Access Systems. IEEE Commun. Lett. 2019, 23, 1501–1505. [Google Scholar] [CrossRef]
- Wang, Y.; Wu, Y.; Zhou, F.; Chu, Z.; Wu, Y.; Yuan, F. Multi-Objective Resource Allocation in a NOMA Cognitive Radio Network With a Practical Non-Linear Energy Harvesting Model. IEEE Access 2018, 6, 12973–12982. [Google Scholar] [CrossRef]
- Yang, Z.; Xu, W.; Pan, Y.; Pan, C.; Chen, M. Energy Efficient Resource Allocation in Machine-to-Machine Communications With Multiple Access and Energy Harvesting for IoT. IEEE Internet Things 2018, 5, 229–245. [Google Scholar] [CrossRef]
- Yang, Z.; Pan, Y.; Xu, W.; Guan, R.; Wang, Y.; Chen, M. Energy efficient resource allocation for machine-to-machine communications with NOMA and energy harvesting. In Proceedings of the 2017 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Atlanta, GA, USA, 1–4 May 2017; pp. 145–150. [Google Scholar]
- Vo, V.; So-In, C.; Tran, H.; Tran, D.; Heng, S.; Aimtongkham, P.; Nguyen, A. On Security and Throughput for Energy Harvesting Untrusted Relays in IoT Systems Using NOMA. IEEE Access 2019, 7, 149341–149354. [Google Scholar] [CrossRef]
- Tang, J.; Dai, T.; Cui, M.; Zhang, X.; Shojaeifard, A.; Wong, K.; Li, Z. Optimization for Maximizing Sum Secrecy Rate in SWIPT-Enabled NOMA Systems. IEEE Access 2018, 6, 43440–43449. [Google Scholar] [CrossRef]
- Wang, D.; Men, S. Secure Energy Efficiency for NOMA Based Cognitive Radio Networks with Nonlinear Energy Harvesting. IEEE Access 2018, 6, 62707–62716. [Google Scholar] [CrossRef]
- Boshkovska, E.; Ng, D.; Zlatanov, N.; Schober, R. Practical Non-Linear Energy Harvesting Model and Resource Allocation for SWIPT Systems. IEEE Commun. Lett. 2015, 19, 2082–2085. [Google Scholar] [CrossRef]
- Chen, Y.; Zhao, N.; Alouini, M. Wireless Energy Harvesting Using Signals From Multiple Fading Channels. IEEE Trans. Commun. 2017, 65, 5027–5039. [Google Scholar] [CrossRef]
- Gradshteyn, I.; Ryzhik, I.; Jeffrey, A.; Zwillinger, D. Table of Integral, Series and Products, 7th ed.; Elsevier: Amsterdam, The Netherlands, 2007. [Google Scholar]
- Li, H.; Zhang, Q.; Yuan, H. Channel state information based key generation vs. side-channel analysis key information leakage. In Proceedings of the 2011 5th International Conference on Network and System Security, Milan, Italy, 6–8 September 2011. [Google Scholar]
- Le, T.; Mayaram, K.; Fiez, T. Efficient Far-Field Radio Frequency Energy Harvesting for Passively Powered Sensor Networks. IEEE J. Solid-State Circuits 2008, 43, 1287–1302. [Google Scholar] [CrossRef]
- Guo, J.; Zhu, X. An improved analytical model for RF-DC conversion efficiency in microwave rectifiers. In Proceedings of the 2012 IEEE/MTT-S International Microwave Symposium Digest, Montreal, QC, Canada, 17–22 June 2012. [Google Scholar]
- Boshkovska, E.; Ng, D.; Zlatanov, N.; Koelpin, A.; Schober, R. Robust Resource Allocation for MIMO Wireless Powered Communication Networks Based on a Non-Linear EH Model. IEEE Trans. Commun. 2017, 65, 1984–1999. [Google Scholar] [CrossRef]
- Nasir, A.; Zhou, X.; Durrani, S.; Kennedy, R. Relaying Protocols for Wireless Energy Harvesting and Information Processing. IEEE Trans. Wirel. Commun. 2013, 12, 3622–3636. [Google Scholar] [CrossRef]
- Zheng, T.; Wang, H.; Liu, F.; Lee, M. Outage Constrained Secrecy Throughput Maximization for DF Relay Networks. IEEE Trans. Commun. 2015, 63, 1741–1755. [Google Scholar] [CrossRef]
- Murray, G.; Edward, W. A Table of Integrals of the Exponential Integral. NIST J. Res. 1969, 73B, 191–210. [Google Scholar]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).