Reusable Mesh Signature Scheme for Protecting Identity Privacy of IoT Devices
Abstract
1. Introduction
1.1. Background
1.2. Our Contributions
- We present a syntax for mesh signature in IoT. Compared with the works of [2,4], we further clearly describe the frame of mesh signature in IoT. Under the proposed syntax, we present a fully anonymous mesh signature scheme for IoT devices, where the IoT devices may be seen as the signers to sign their data and their specific identities can be hidden. Additionally, the atomic signatures on the same data can be reusable so as to decrease the number of signatures generated by IoT devices.
- In our proposed scheme, we have limitedly defined the access structure of language expression by monotone-span programs, thus the proposed mesh signature can resist the collusion attacks and its access structure still support generalized monotone predicates. Also, under the security frame proposed by [2,4], our proposed scheme is secure in the standard model, where the security of our scheme can be reduced to the CDH assumption. Also, the proposed scheme has the anonymity with enough security to protecting the identities of IoT devices.
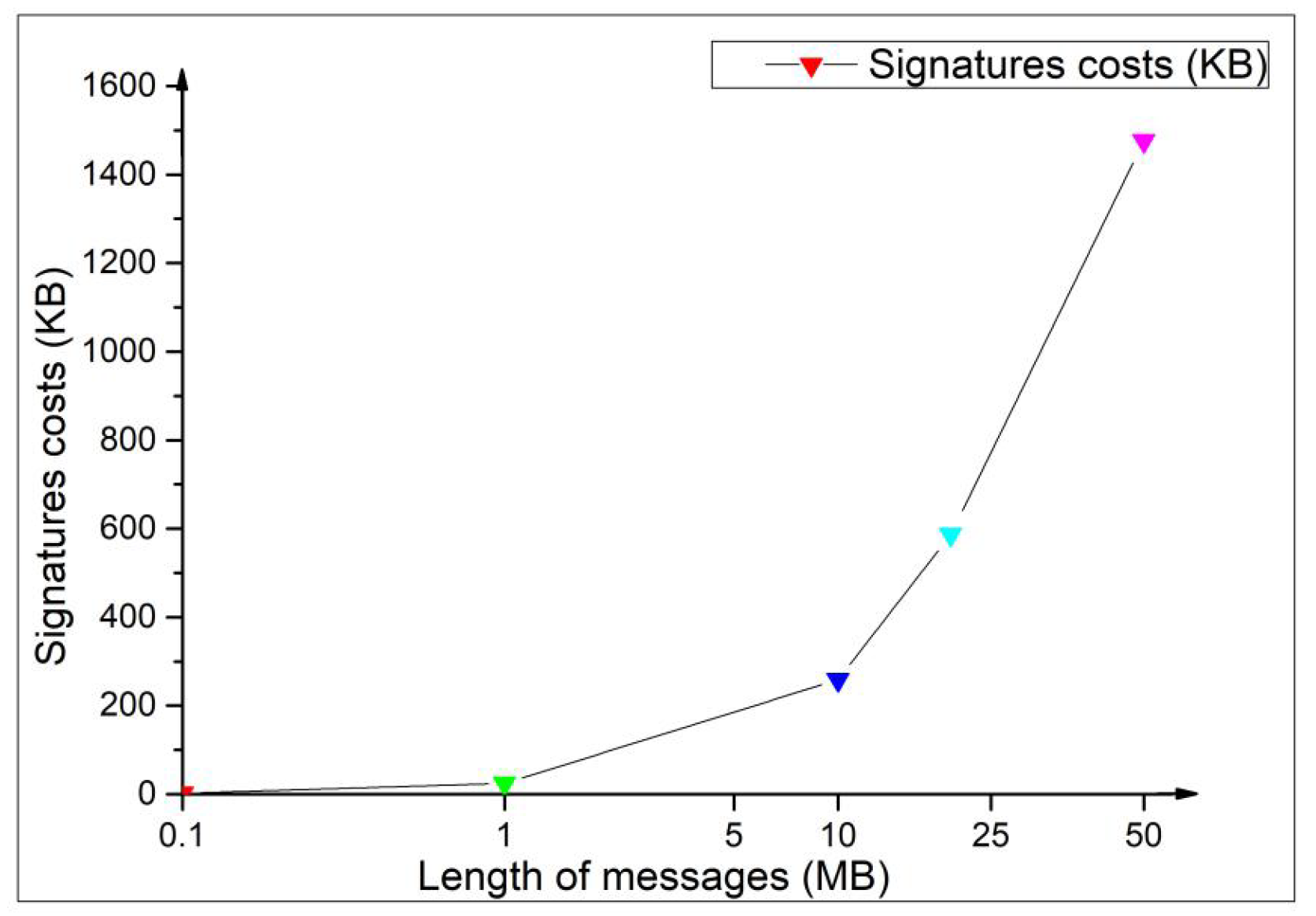
- Compared with the original mesh signature scheme [2], the proposed scheme preserves the original modularity. Although generating atomic signatures in the proposed scheme needs more computational cost, the proposed scheme has less computational costs on generating final mesh signature and signature verification. Since atomic signatures are reusable, the proposed scheme has more advantages on generating final mesh signature by reconstructing atomic signatures. According to our experiment, it is feasible that the proposed scheme is used to protect the identity privacy of IoT devices.
1.3. Organization
2. Related Work
3. Preliminaries
3.1. Bilinear Maps
3.2. Computational Diffie–Hellman Assumption
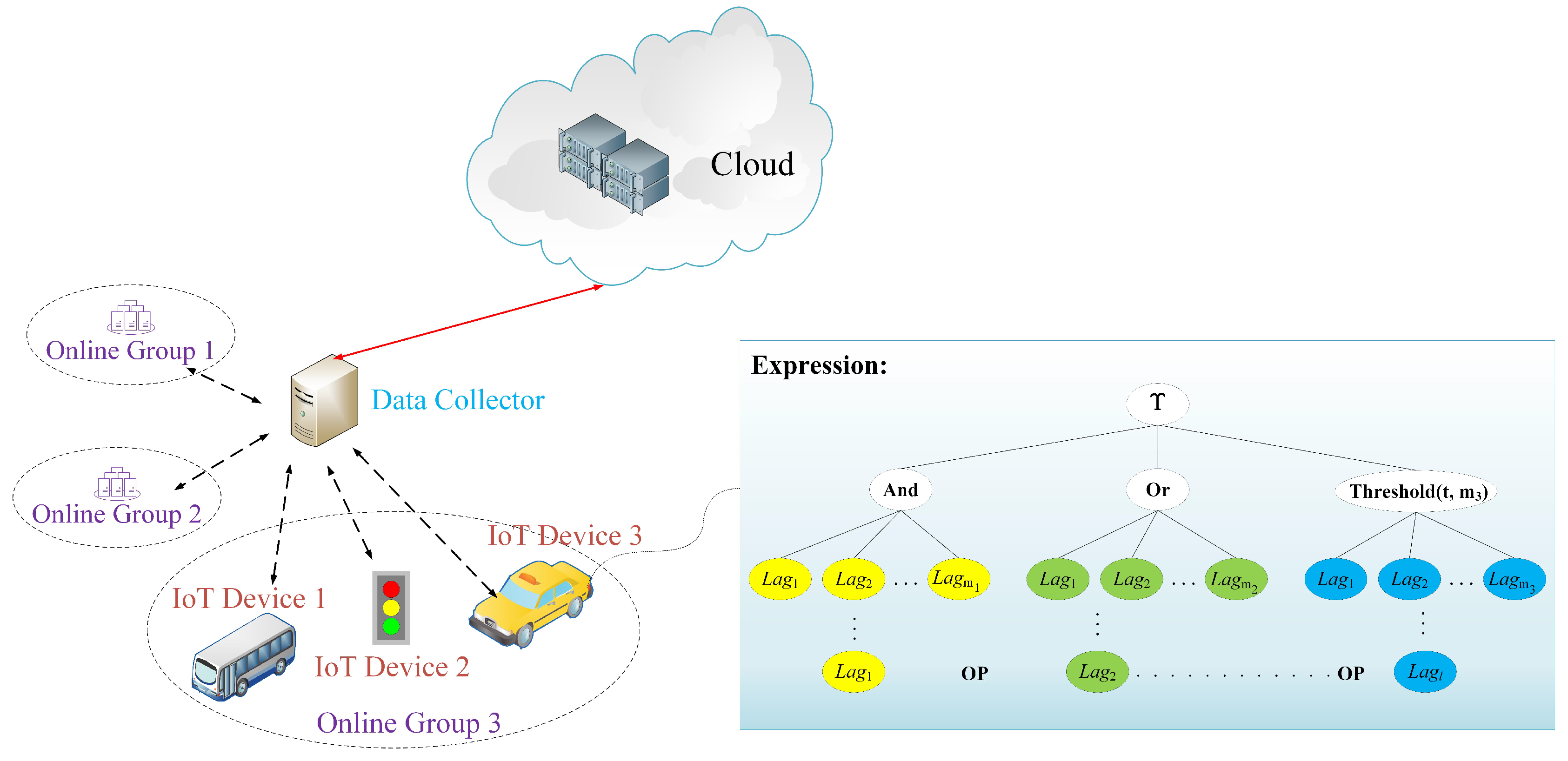
3.3. Monotone-Span Programs
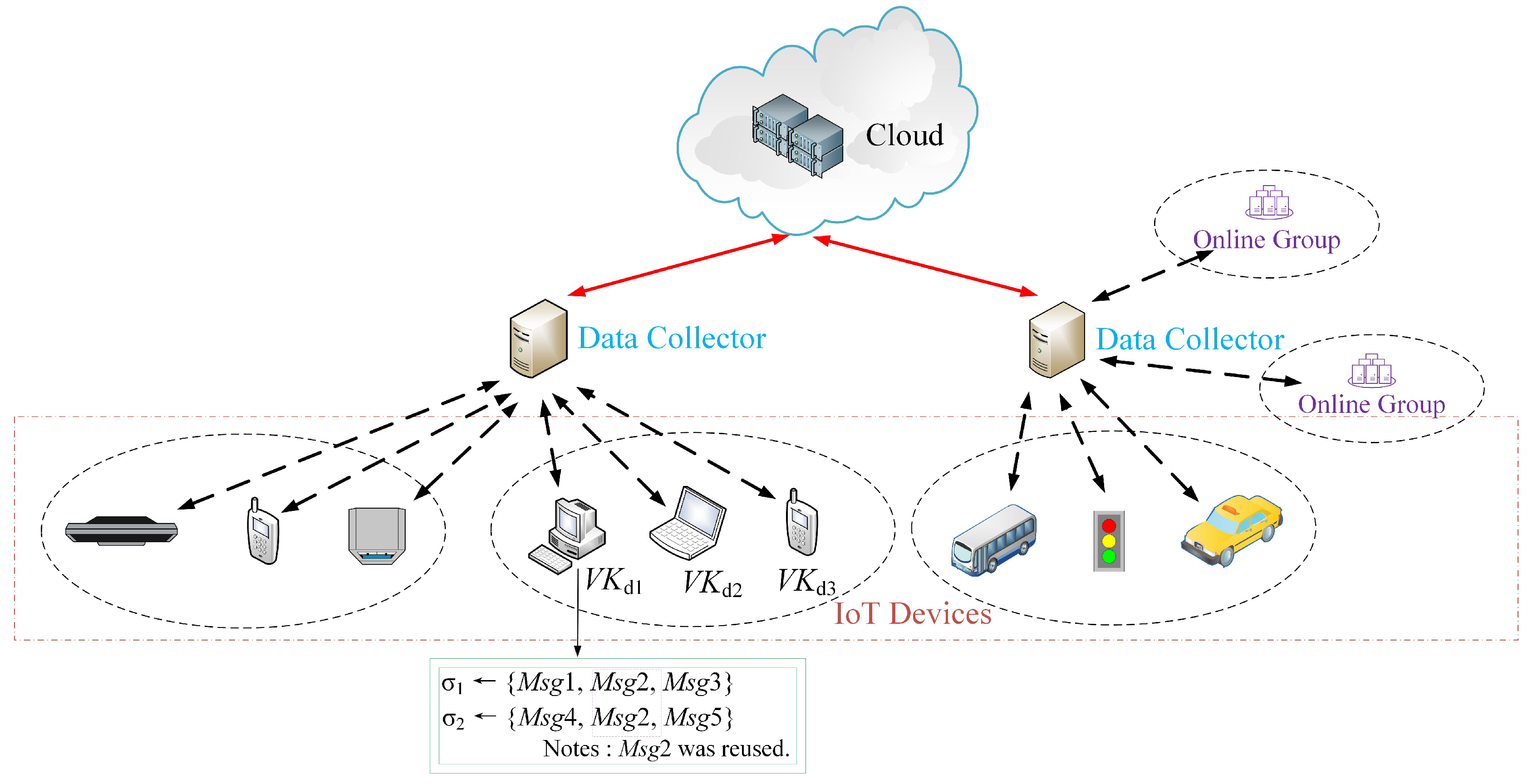
4. A Syntax for MS in IoT
- (1)
- System-Setup: The authority system runs the randomized algorithm, and inputs a security parameter . In addition, the algorithm outputs all related public system parameters and a master system private key on the parameter .
- (2)
- Generate-Key: The authority system runs the randomized algorithm, and inputs (, ), and then outputs the IoT device’s private/public key pair to the device i, where (we set that n is the number of the IoT devices).
- (3)
- Mesh-Sign: The randomized algorithm generates a mesh signature. The IoT device i issues its message set (data) and then signs the message set, thus the device i runs the algorithm: (a) the algorithm inputs (, , , ), and then outputs a monotone boolean expression Υ and the atomic signatures ; (b) the algorithm inputs (, , , Υ), and then outputs a mesh signature Φ, where is a list of all the public keys of the devices involved with this signing; (c) the algorithm run by the device i sends the message set , the boolean expression Υ and the mesh signature Φ to the IoT data collector.
- (4)
- Mesh-Verify: The IoT data collector verifies the standard mesh signature Φ on Υ and . The IoT data collector runs the deterministic algorithm, and inputs (, , , Υ, Φ), and then outputs the result, or .
5. Improved Mesh Signature Scheme for IoT Devices
- (1)
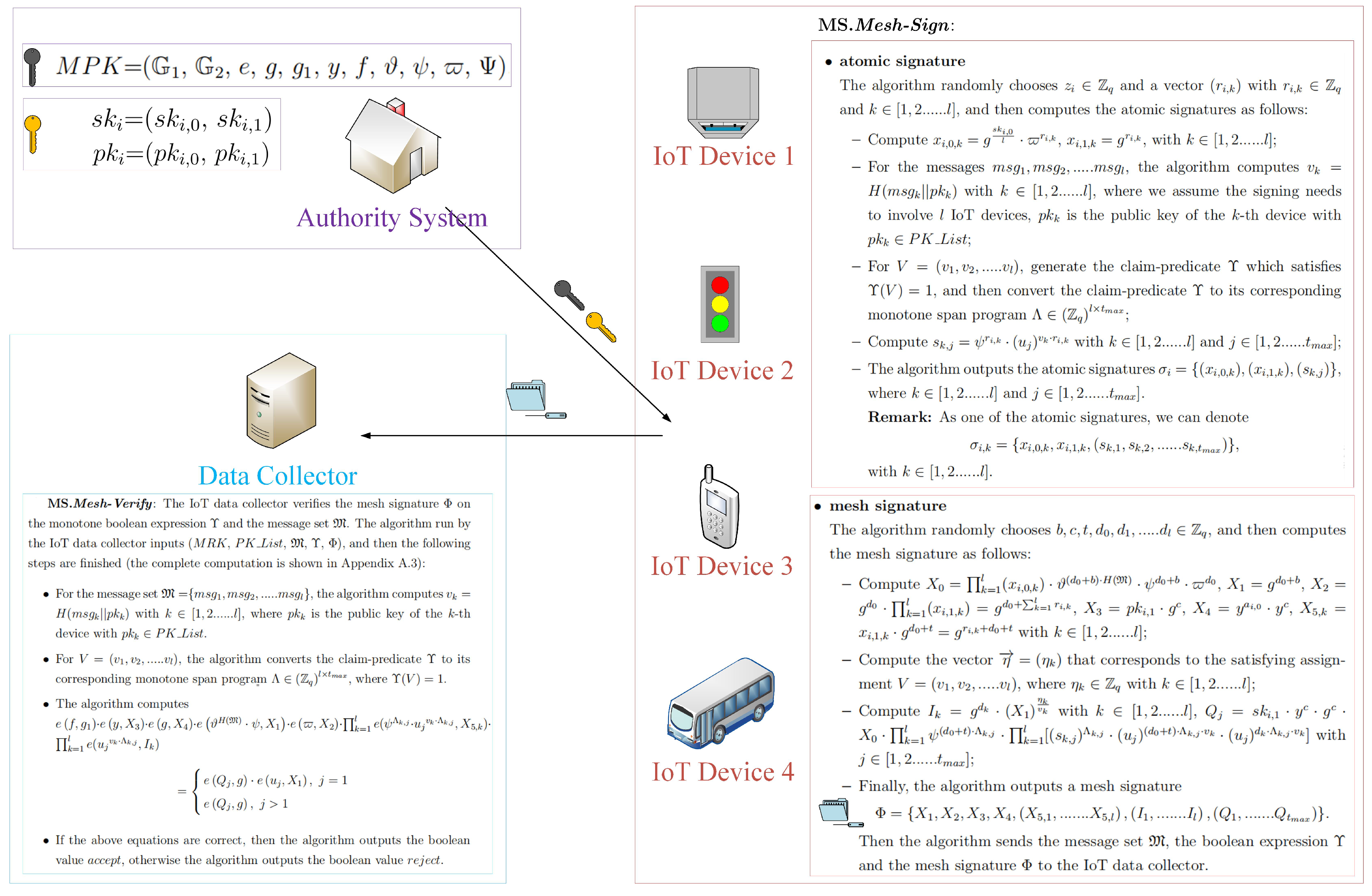
- MS.System-Setup: The system runs this setup algorithm, and inputs the parameter (used as the security level). Also, we set that and are the groups of prime order q, g is a generator of , and that denotes the bilinear map. In addition, we set that denotes one hash function and it can be used to output integers in . Additionally, we assume that the monotone span programs related to claim-predicates have their width at most in our construction.Then the following parameters are outputted in the system. The algorithm randomly chooses and sets . Five group elements y, f, , and are randomly picked. Also, the algorithm generates a -length vector , whose element is randomly picked from . Finally the algorithm outputs the public parameters = (, , e, g, , y, f, , , , ), where is a master private key in the system.
- (2)
- MS.Generate-Key: The system runs the algorithm and then generates IoT device’s private/public key pair. For the device i, the algorithm inputs (, ), and then it randomly picks , sets and computes , and , where we set = (, ) as the private key of the device i and = (, ) as the public key of the device i.
- (3)
- MS.Mesh-Sign: The IoT device i signs a message set , where the message set . The device i runs the algorithm, and then inputs (, , , ) where is a list of the public keys of the IoT devices involved with this signing, and then the following steps are finished:
- atomic signatureThe algorithm randomly chooses and a vector () with and , and then computes the atomic signatures as follows:
- -
- Compute , , with ;
- -
- For the messages , the algorithm computes with , where we assume the signing needs to involve l IoT devices, is the public key of the k-th device with ;
- -
- For , generate the claim-predicate which satisfies , and then transform the claim-predicate to its corresponding monotone span program ;
- -
- Compute with and ;
- -
- The algorithm outputs the atomic signatures , where and .Remark.As one of the atomic signatures, we can denotewith .
- mesh signatureThe algorithm randomly chooses , and then computes the mesh signature as follows:
- -
- Compute , , , , , with ;
- -
- Compute the vector related to the satisfying assignment , where with ;
- -
- Compute with , with ;
- -
- The algorithm finally generates and outputs a mesh signatureThen the algorithm sends the message set , the boolean expression and the mesh signature to the IoT data collector.
- (4)
- MS.Mesh-Verify: The IoT data collector verifies the mesh signature on the monotone boolean expression and the message set . The algorithm run by the IoT data collector inputs (, , , , ), and then the following steps are finished (the complete computation is shown in Appendix A.3):
- For the message set , the algorithm computes with , where is the public key of the k-th device with .
- For , the algorithm transforms the claim-predicate to the monotone span program , where .
- The algorithm computesIf the equation is correct, the algorithm outputs , otherwise it outputs .
6. Analysis of Our Scheme
6.1. Security Analysis
6.2. Efficiency Analysis
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Appendix A.
Appendix A.1. Unforgeability
- Generate-Key(): Given the public parameters , for the device i, the algorithm randomly chooses , sets and computes , and , where = (, ) is the private key of the device i and = (, ) is the public key of the device i, and then the private/public key pair is passed to the adversary .Remark.To the correctness of and , they may be changed as follows:Setting , then and . Therefore, and is a valid private/public key pair.If mod q, the above procedure cannot occur and aborts. Otherwise, a private/public key pair is outputted to .
- Atomic-Sign(): Given the public parameters , the public key list and the message , where is a list of the public keys of the devices involved with this query (with respect to the device i), the algorithm finishes the following steps:
- -
- The algorithm randomly chooses and a vector () with and , computes and with , and then saves where ;
- -
- The message is divided to ; then the algorithm computes with , where we assume the signing needs to involve l devices, is the public key of the k-th device with ;
- -
- For , generate the claim-predicate which satisfies , and then transform the claim-predicate to the monotone span program ;
- -
- Compute with and ;
- -
- The algorithm outputs the atomic signatures to , where and .
If mod q with , then the above procedure cannot ocur and aborts. Otherwise, the atomic signatures are passed to the adversary . - Mesh-Sign(): Given the public parameters , the atomic signatures on the public key list and the message (with respect to the device i), and the monotone boolean expression , the algorithm finishes the following steps:
- -
- Choose randomly, compute , , , , according to the corresponding , with ;
- -
- Compute the vector related to the satisfying assignment , where with ;
- -
- Compute with , with ;
- -
- The algorithm finally generates and outputs a mesh signature.
Similarly, setting , is a valid mesh signature. If mod q, the above procedure cannot occur and aborts. Otherwise, a mesh signature is outputted to .
- (a)
- Mesh-Verify(, , , , );
- (b)
- did not query Generate-Key on any public key belongs to , and it did not query Mesh-Sign on the related inputs , and .
- ,,,,,,.
- (a)
- mod q in related key queries;
- (b)
- mod q for all in related atomic signature queries;
- (c)
- mod q in related mesh signature queries.
Appendix A.2. Anonymity
- Generate-Key(): Given the public parameters , for the device i, the algorithm randomly chooses , sets and computes , and , where = (, ) is the private key of the device i and = (, ) is the public key of the device i, and then the private/public key pair is passed to the adversary . Similarly, setting , then and . Therefore, and is a valid private/public key pair.If mod q, the above procedure cannot occur and aborts. Otherwise, a private/public key pair is outputted to .
- Atomic-Sign(): Given the public parameters , the public key list and the message , where is a list of the public keys of the devices involved with this query (with respect to the device i), the algorithm finishes the following steps:
- -
- The algorithm randomly chooses and a vector () with and , computes and with , and then saves where ;
- -
- The message is divided to ; then the algorithm computes with , where we assume the signing needs to involve l devices, is the public key of the k-th device with ;
- -
- For , generate the claim-predicate which satisfies , and then transform the claim-predicate to the monotone span program ;
- -
- Compute with and ;
- -
- The algorithm outputs the atomic signatures to , where and .
If mod q with , then the above procedure cannot occur and will abort; otherwise the atomic signatures are passed to the adversary . - Mesh-Sign(): Given the public parameters , the atomic signatures on the public key list and the message (with respect to the device i), and the monotone boolean expression , the algorithm finishes the following steps:
- -
- Choose randomly, compute , , , , according to the corresponding , with ;
- -
- Compute the vector related to the satisfying assignment , where with ;
- -
- Compute with , with ;
- -
- The algorithm finally generates and outputs a mesh signature.
Similarly, setting , is a valid mesh signature. If mod q, the above procedure cannot occur and aborts. Otherwise, a mesh signature is passed to .
- (a)
- The adversary did not make query to Generate-Key on (and );
- (b)
- The adversary did not make query to Atomic-Sign on (and );
- (c)
- The adversary did not make query to Mesh-Sign on (and ).
- Generate-Key(): Given the public parameters , for the device i, the algorithm randomly chooses , sets and computes , and , where = (, ) is the private key of the device i and = (, ) is the public key of the device i, and then the private/public key pair is passed to the adversary . Similarly, setting , then and . Therefore, and is a valid private/public key pair.If mod q, the above procedure cannot occur and aborts. Otherwise, a private/public key pair is outputted to .
- Atomic-Sign(): Given the public parameters , the public key list and the message , where is a list of the public keys of the devices involved with this query (with respect to the device i), the algorithm finishes the following steps:
- -
- The algorithm randomly chooses and a vector () with and , computes and with , and then saves where ;
- -
- The message is divided to ; then the algorithm computes with , where we assume the signing needs to involve l devices, is the public key of the k-th device with ;
- -
- For , generate the claim-predicate which satisfies , and then transform the claim-predicate to the monotone span program ;
- -
- Compute with and ;
- -
- The algorithm outputs the atomic signatures to , where and .
If mod q with , the above procedure cannot be occur and will abort; otherwise the atomic signatures are passed to the adversary . - Mesh-Sign(): Given the public parameters , the atomic signatures on the public key list and the message (with respect to the device i), and the monotone boolean expression , the algorithm finishes the following steps:
- -
- Choose randomly, compute , , , , according to the corresponding , with ;
- -
- Compute the vector related to the satisfying assignment , where with ;
- -
- Compute with , with ;
- -
- The algorithm finally generates and outputs a mesh signature
Similarly, setting , is a valid mesh signature. If mod q, the above procedure cannot occur and aborts. Otherwise, a mesh signature is passed to .
- ,,,,,,.
- (a)
- mod q in the related key queries of Queries Phases 1 and 2;
- (b)
- mod q for all in the related atomic signature queries of Queries Phases 1 and 2;
- (c)
- mod q in the related mesh signature queries of Queries Phases 1 and 2.
Appendix A.3. Correctness
- ,,,,,,,.
References
- Karati, A.; Islam, S.H.; Karuppiah, M. Provably Secure and Lightweight Certificateless Signature Scheme for IIoT Environments. IEEE Trans. Ind. Inf. 2018, 14, 3701–3711. [Google Scholar] [CrossRef]
- Boyen, X. Mesh Signatures-How to Leak a Secret with Unwitting and Unwilling Participants. In Advances in Cryptology—EUROCRYPT 2007; Springer-Verlag: Berlin/Heidelberg, Germany, 2007. [Google Scholar]
- Rivest, R.; Shamir, A.; Tauman, Y. How to leak a secret. In Asiacrypt 2001, LNCS 2248; Boyd, C., Ed.; Springer: Berlin/Heidelberg, Germany, 2001; pp. 552–565. [Google Scholar]
- Boyen, X. Unconditionally Anonymous Ring and Mesh Signatures. J. Cryptol. 2016, 29, 729–774. [Google Scholar] [CrossRef]
- Maji, H.K.; Prabhakaran, M.; Rosulek, M. Attribute-Based Signatures, Topics in Cryptology-CT-RSA 2011, LNCS 6558; Springer-Verlag: Berlin/Heidelberg, Germany, 2011; pp. 376–392. [Google Scholar]
- Chaum, D.; van Heyst, E. Group Signatures. In Eurocrypt’91, LNCS 547; Springer: Berlin/Heidelberg, Germany, 1991; pp. 257–265. [Google Scholar]
- Liu, J.K.; Wei, V.K.; Wong, D.S. Linkable spontaneous anonymous group signature for ad hoc groups. In ACISP 2004: Information Security and Privacy; Springer: Berlin/Heidelberg, Germany, 2004; pp. 325–335. [Google Scholar]
- Chow, S.S.M.; Liu, J.K.; Wong, D.S. Robust receipt-free election system with ballot secrecy and verifieability. NDSS 2008, 8, 81–94. [Google Scholar]
- Tsang, P.P.; Wei, V.K. Short linkable ring signatures for e-voting, e-cash and attestation. In ISPEC 2005: Information Security Practice and Experience; Springer: Berlin/Heidelberg, Germany, 2005; pp. 48–60. [Google Scholar]
- Susilo, W.; Mu, Y. Non-Interactive Deniable Ring Authentication. In ICISC 2003: Information Security and Cryptology—ICISC 2003; Springer: Berlin/Heidelberg, Germany, 2004; pp. 386–401. [Google Scholar]
- Laguillaumie, F.; Vergnaud, D. Multi-designated Verifiers Signatures. In ICICS 2004, Volume 3269 of Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2004; pp. 495–507. [Google Scholar]
- Gu, K.; Wu, N.; Yin, B.; Jia, W. Secure Data Query Framework for Cloud and Fog Computing. IEEE Trans. Netw. Serv. Manag. 2019. [Google Scholar] [CrossRef]
- Gu, K.; Wu, N.; Yin, B.; Jia, W. Secure Data Sequence Query Framework Based on Multiple Fogs. IEEE Trans. Netw. Serv. Manag. 2019. [Google Scholar] [CrossRef]
- Gu, K.; Wang, K.; Yang, L. Traceable Attribute-Based Signature. J. Inf. Secur. Appl. 2019, 49, 102400. [Google Scholar] [CrossRef]
- Gu, K.; Dong, X.; Wang, L. Efficient Traceable Ring Signature Scheme without Pairings. Adv. Math. Commun. 2019. [Google Scholar] [CrossRef]
- Yu, F.; Liu, L.; Xiao, L.; Li, K.; Cai, S. A robust and fixed-time zeroing neural dynamics for computing time-variant nonlinear equation using a novel nonlinear activation function. Neurocomputing 2019, 350, 108–116. [Google Scholar] [CrossRef]
- Yu, F.; Liu, L.; He, B.; Huang, Y.; Shi, C.; Cai, S.; Song, Y.; Du, S.; Wan, Q. Analysis and FPGA Realization of a Novel 5D Hyperchaotic Four-Wing Memristive System, Active Control Synchronization, and Secure Communication Application. Complexity 2019, 2019, 4047957. [Google Scholar] [CrossRef]
- Yu, F.; Zhang, Z.; Liu, L.; Shen, H.; Huang, H.; Shi, C.; Cai, S.; Song, Y.; Du, S.; Xu, Q. Secure communication scheme based on a new 5D multistable four-wing memristive hyperchaotic system with disturbance inputs. Complexity 2020, 2020, 5859273. [Google Scholar] [CrossRef]
- Chen, Y.; Wang, J.; Xia, R.; Zhang, Q.; Cao, Z.; Yang, K. The visual object tracking algorithm research based on adaptive combination kernel. J. Ambient Intell. Humaniz. Comput. 2019, 10, 4855–4867. [Google Scholar] [CrossRef]
- Li, W.; Chen, Z.; Gao, X.; Liu, W.; Wang, J. Multi-Model Framework for Indoor Localization under Mobile Edge Computing Environment. IEEE Internet Things J. 2019, 6, 4844–4853. [Google Scholar] [CrossRef]
- Li, Y.; Zhu, T. Gait-Based Wi-Fi Signatures for Privacy-Preserving. In Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security (ASIA CCS ’16), Xi’an, China, 30 May–3 June 2016; pp. 571–582. [Google Scholar] [CrossRef]
- Sun, J.; Su, Y.; Qin, J.; Hu, J.; Ma, J. Outsourced Decentralized Multi-authority Attribute Based Signature and Its Application in IoT. IEEE Trans. Cloud Comput. 2019. [Google Scholar] [CrossRef]
- Xie, R.; He, C.; Xu, C.; Gao, C. Lattice-based dynamic group signature for anonymous authentication in IoT. Ann. Telecommun. 2019, 74, 531–542. [Google Scholar] [CrossRef]
- Mughal, M.A.; Luo, X.; Ullah, A.; Ullah, S.; Mahmood, Z. A Lightweight Digital Signature Based Security Scheme for Human-Centered Internet of Things. IEEE Access 2018, 6, 31630–31643. [Google Scholar] [CrossRef]
- Cui, H.; Deng, R.H.; Liu, R.H.; Yi, X.; Li, Y. Server-Aided Attribute-Based Signature With Revocation for Resource-Constrained Industrial-Internet-of-Things Devices. IEEE Trans. Ind. Inf. 2018, 14, 3724–3732. [Google Scholar] [CrossRef]
- Li, F.; Zheng, Z.; Jin, C. Secure and efficient data transmission in the Internet of Things. Telecommun. Syst. 2016, 62, 111–122. [Google Scholar] [CrossRef]
- Libert, B.; Peters, T.; Yung, M. Scalable Group Signatures with Revocation. In Advances in Cryptology-EUROCRYPT 2012; Springer-Verlag: Berlin/Heidelberg, Germany, 2012; pp. 609–627. [Google Scholar]
- Libert, B.; Peters, T.; Yung, M. Scalable Group Signatures with Almost-for-Free Revocation. In Advances in Cryptology-CRYPTO2012; Springer-Verlag: Berlin/Heidelberg, Germany, 2012; pp. 571–589. [Google Scholar]
- Ibraimi, L.; Nikova, S.; Hartel, S.; Jonker, W. An Identity-Based Group Signature with Membership Revocation in the Standard Model. Available online: http:/doc.utwente.nl/72270/1/Paper.pdf (accessed on 28 January 2020).
- Emura, K.; Miyaji, A.; Omote, K. An r-Hiding Revocable Group Signature Scheme: Group Signatures with the Property of Hiding the Number of Revoked Users. Eur. J. Appl. Math. 2014, 2014, 983040. [Google Scholar] [CrossRef]
- Gu, K.; Yang, L.; Wang, Y.; Wen, S. Traceable Identity-Based Group Signature. RAIRO-Theor. Inf. Appl. 2016, 50, 193–226. [Google Scholar] [CrossRef]
- Yuen, T.H.; Liu, J.K.; Au, M.H.; Susilo, W.; Zhou, J. Efficient linkable and/or threshold ring signature without random oracles. Comput. J. 2013, 56, 407–421. [Google Scholar] [CrossRef]
- Liu, J.K.; Au, M.H.; Susilo, W.; Zhou, J. Linkable Ring Signature with Unconditional Anonymity. IEEE Trans. Knowl. Data Eng. 2014, 26, 157–165. [Google Scholar] [CrossRef]
- Au, M.H.; Liu, J.K.; Susilo, W.; Yuen, T.H. Secure ID-Based Linkable and Revocable-iff-Linked Ring Signature with Constant-Size Construction. Theor. Comput. Sci. 2013, 469, 1–14. [Google Scholar] [CrossRef]
- Kaafarani, A.E.; Ghadafi, E.; Khader, D. Decentralized Traceable Attribute-Based Signatures. In Topics in Cryptology—CT-RSA 2014; Springer-Verlag: Berlin/Heidelberg, Germany, 2014; pp. 327–348. [Google Scholar]
- Ghadafi, E. Stronger Security Notions for Decentralized Traceable Attribute-Based Signatures and More Efficient Constructions. In Topics in Cryptology—CT-RSA 2015; Springer-Verlag: Berlin/Heidelberg, Germany, 2015; pp. 391–409. [Google Scholar]
- Gu, K.; Jia, W.; Wang, G.; Wen, S. Efficient and secure attribute-based signature for monotone predicates. Acta Inf. 2017, 54, 521–541. [Google Scholar] [CrossRef]
- Song, T.; Li, R.; Mei, B.; Yu, J.; Xing, X.; Cheng, X. A privacy preserving communication protocol for IoT applications in smart homes. IEEE Internet Things J. 2017, 4, 1844–1852. [Google Scholar] [CrossRef]
- Dwivedi, A.D.; Srivastava, G.; Dhar, G.; Singh, R. A decentralized privacy-preserving healthcare blockchain for IoT. Sensors 2019, 19, 326. [Google Scholar] [CrossRef] [PubMed]
- Sharma, S.; Chen, K.; Sheth, K. Toward practical privacy-preserving analytics for IoT and cloud-based healthcare systems. IEEE Internet Comput. 2018, 22, 42–51. [Google Scholar] [CrossRef]
- Zhou, J.; Cao, Z.; Dong, X.; Vasilakos, A. Security and privacy for cloud-based IoT: Challenges. IEEE Commun. Mag. 2017, 55, 26–33. [Google Scholar] [CrossRef]
- Gope, P.; Sikdar, B. Lightweight and privacy-preserving two-factor authentication scheme for IoT devices. IEEE Internet Things J. 2018, 6, 580–589. [Google Scholar] [CrossRef]
- Li, X.; Liu, S.; Wu, F.; Kumari, S.; Rodrigues, J. Privacy preserving data aggregation scheme for mobile edge computing assisted IoT applications. IEEE Internet Things J. 2018, 6, 4755–4763. [Google Scholar] [CrossRef]
- Shen, M.; Tang, X.; Zhu, L.; Du, X.; Guizani, M. Privacy-preserving support vector machine training over blockchain-based encrypted IoT data in smart cities. IEEE Internet Things J. 2019, 6, 7702–7712. [Google Scholar] [CrossRef]
- Lu, R. A new communication-efficient privacy-preserving range query scheme in fog-enhanced IoT. IEEE Internet Things J. 2018, 6, 2497–2505. [Google Scholar] [CrossRef]
- Huang, P.; Guo, P.; Li, M.; Fang, Y. Practical Privacy-preserving ECG-based Authentication for IoT-based Healthcare. IEEE Internet Things J. 2019, 6, 9200–9210. [Google Scholar] [CrossRef]
- Jiang, L.; Chen, L.; Giannetsos, T.; Luo, B.; Liang, K.; Han, J. Toward Practical Privacy-Preserving Processing Over Encrypted Data in IoT: An Assistive Healthcare Use Case. IEEE Internet Things J. 2019, 6, 10177–10190. [Google Scholar] [CrossRef]
- Ma, Z.; Liu, Z.; Liu, X.; Ma, J.; Li, F. Privacy-Preserving Outsourced Speech Recognition for Smart IoT Devices. IEEE Internet Things J. 2019, 6, 8406–8420. [Google Scholar] [CrossRef]
- Zhao, Y.; Yang, L.T.; Sun, J. Privacy-Preserving Tensor-Based Multiple Clusterings on Cloud for Industrial IoT. IEEE Trans. Ind. Inf. 2018, 15, 2372–2381. [Google Scholar] [CrossRef]
- Gan, X.; Li, X.; Huang, Y.; Fu, L.; Wang, X. When Crowdsourcing Meets Social IoT: An Efficient Privacy-Preserving Incentive Mechanism. IEEE Internet Things J. 2019, 6, 9707–9721. [Google Scholar] [CrossRef]
- Gochoo, M.; Tan, T.H.; Huang, S.C.; Batjargal, T.; Hsieh, J.; Alnajjar, F.S.; Chen, Y. Novel IoT-Based Privacy-Preserving Yoga Posture Recognition System Using Low-Resolution Infrared Sensors and Deep Learning. IEEE Internet Things J. 2019, 6, 7192–7200. [Google Scholar] [CrossRef]
- Xu, C.; Ren, J.; Zhang, D.; Zhangm, Y. Distilling at the edge: A local differential privacy obfuscation framework for IoT data analytics. IEEE Commun. Mag. 2018, 56, 20–25. [Google Scholar] [CrossRef]
| Atomic Signatures | Mesh Signature | Verification | |
|---|---|---|---|
| Original scheme [2] | |||
| Our scheme | |||
| Computational Costs (ms) | |||||||
|---|---|---|---|---|---|---|---|
| 1 | 1 | 10 | 20 | 30 | 40 | 50 | |
| Original scheme [2] | Atomic Signatures | 1.958 | 1.746 | 1.590 | 1.605 | 1.566 | 1.629 |
| Mesh Signature | 91.495 | 583.225 | 1038.55 | 1617.78 | 2003.15 | 2270.82 | |
| Verification | 61.457 | 339.048 | 593.315 | 1001.73 | 1263.15 | 1473.34 | |
| Our scheme | Atomic Signatures | 7.890 | 78.850 | 164.900 | 236.100 | 313.600 | 387.250 |
| Mesh Signature | 37.752 | 353.003 | 881.153 | 981.836 | 1551.64 | 1675.29 | |
| Verification | 37.910 | 441.830 | 591.710 | 1000.43 | 1150.84 | 1128.29 | |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gu, K.; Zhang, W.; Lim, S.-J.; Sharma, P.K.; Al-Makhadmeh, Z.; Tolba, A. Reusable Mesh Signature Scheme for Protecting Identity Privacy of IoT Devices. Sensors 2020, 20, 758. https://doi.org/10.3390/s20030758
Gu K, Zhang W, Lim S-J, Sharma PK, Al-Makhadmeh Z, Tolba A. Reusable Mesh Signature Scheme for Protecting Identity Privacy of IoT Devices. Sensors. 2020; 20(3):758. https://doi.org/10.3390/s20030758
Chicago/Turabian StyleGu, Ke, WenBin Zhang, Se-Jung Lim, Pradip Kumar Sharma, Zafer Al-Makhadmeh, and Amr Tolba. 2020. "Reusable Mesh Signature Scheme for Protecting Identity Privacy of IoT Devices" Sensors 20, no. 3: 758. https://doi.org/10.3390/s20030758
APA StyleGu, K., Zhang, W., Lim, S.-J., Sharma, P. K., Al-Makhadmeh, Z., & Tolba, A. (2020). Reusable Mesh Signature Scheme for Protecting Identity Privacy of IoT Devices. Sensors, 20(3), 758. https://doi.org/10.3390/s20030758







