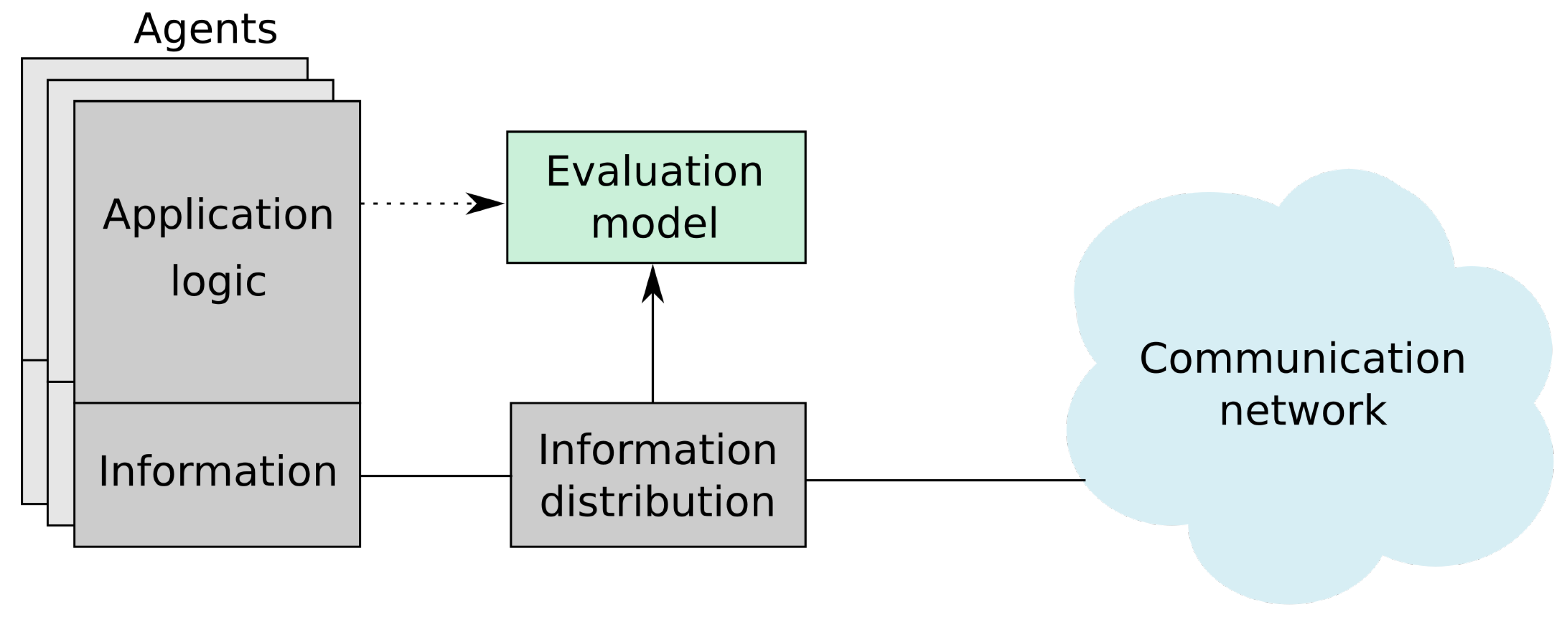
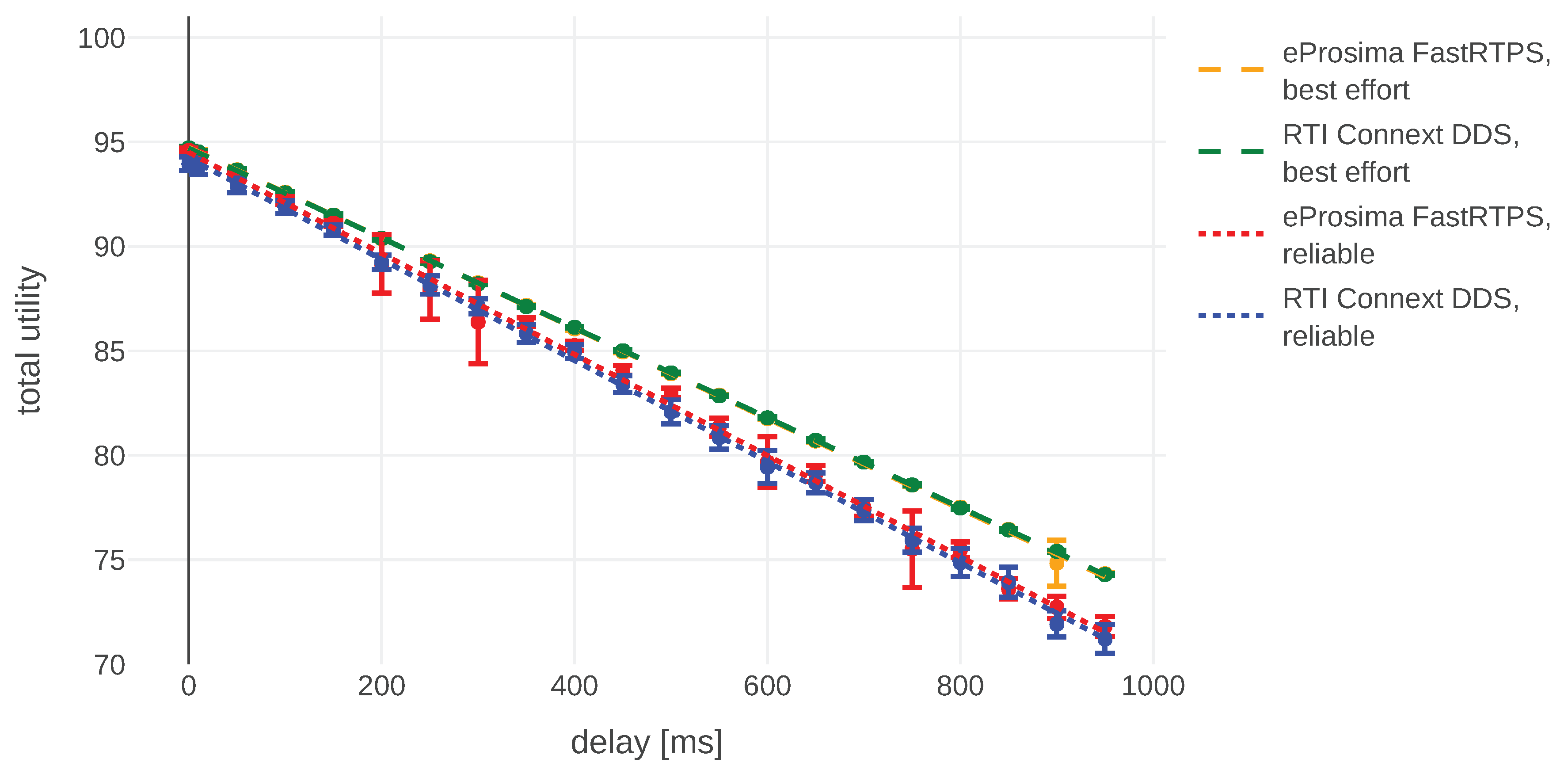
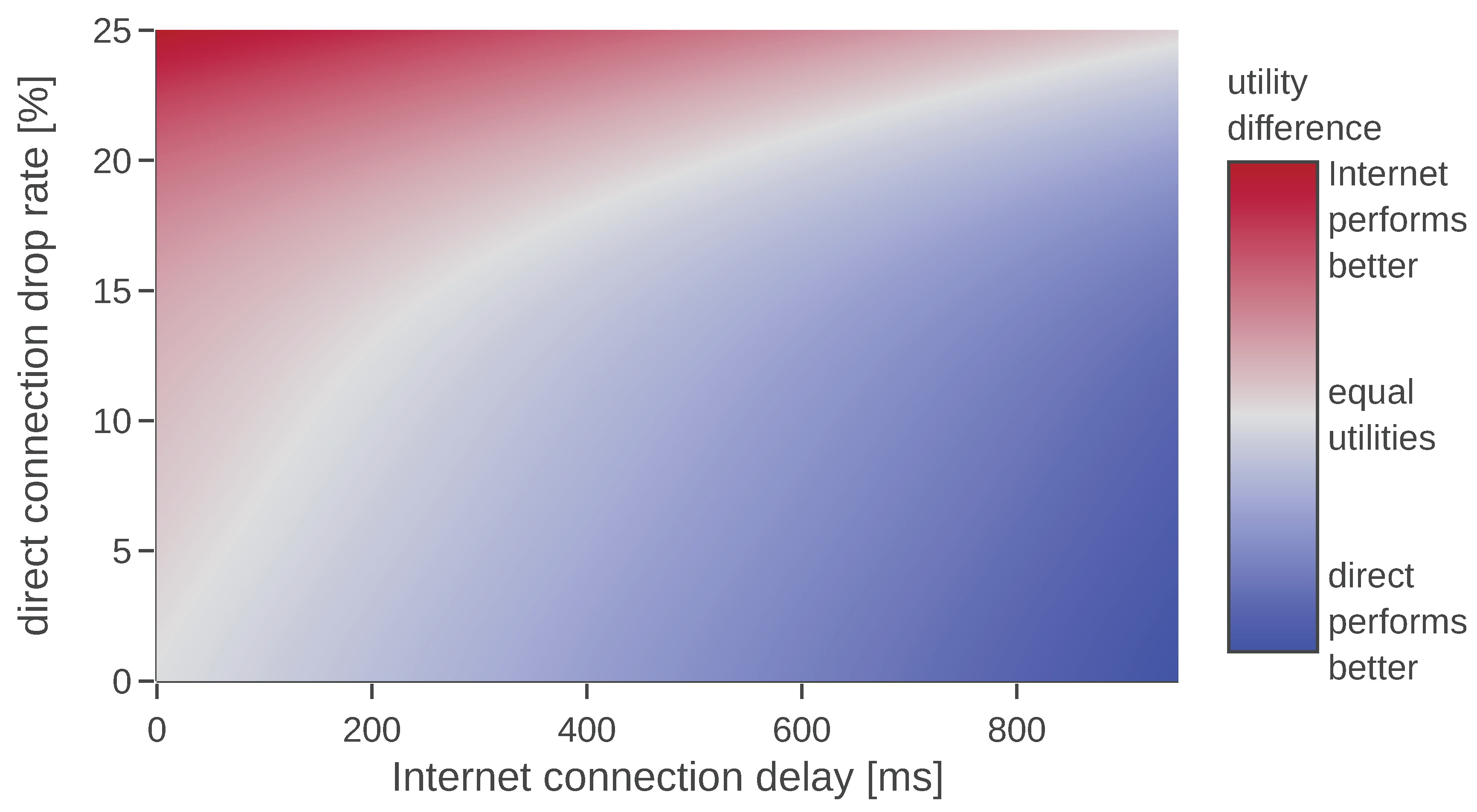
4.1. Agents’ Properties
In this section we analyze two types of information, both of them representing robots’ properties: battery level and position in 2D. The definitions of utility of messages containing information of these types, depend on the way the information provided by these messages is used. For example, consider using the position of another robot to estimate how far it is from a given point. We can assume this distance in the worst case will change linearly over time, based on the maximum speed of the robot. However, if we use the last received position in order to estimate where exactly the agent is now, the probability of estimating the exact position, based only on the maximum speed and the last received position decreases quadratically over time in the 2D case (the agent can go into any direction on a plane) and cubicly over time in the 3D case (it potentially travels in any direction in space).
This distinction in the interpretation of position data serves as a good illustration of one of the most important properties of the introduced model: the ability to abstract communication from mission logic. Once the utility functions are defined, the evaluation model allows us to treat all the messages in exactly the same way, independently of the way the message is used by the mission.
4.1.1. Battery Level
We assume agents are exchanging messages containing their battery levels. The algorithm running on each agent directly uses the data from the most recent message and assumes it to be correct, even if it is outdated. From this message, it extracts the information about the sender’s availability, i.e., if the sender’s battery is depleted, it is no longer available.
In order to introduce the message utility function for this scenario, we define
as a pessimistic battery depletion rate, i.e., a rate that is higher than the maximum possible battery consumption rate. Hence, the battery level after time
drops in the worst case by
The utility of a message reflects the ratio between a pessimistic real battery level at a given time and the message data.
Here, the max aggregation function is used, because the algorithm running on an agent always uses the most useful message, which in this case is always the most recent message.
The message utility and aggregation functions for the battery information are defined as follows:
By studying
Figure 2 presenting the plot of Equations (9) and (10) for an example instance of the given mission, we can observe some properties of these utilities. First of all, a message is useful for the receiver, starting from its reception time to the time when the battery would be completely depleted in the worst case (assuming pessimistic depletion rate). The utility decreases over time as soon as the message is generated. This is based on the intuition that we have the perfect information only at the time of measurement. The more time has passed, the less precise information we have about when the battery is going to deplete. Additionally, we can observe that the utility falls faster when the measured battery level is low.
4.1.2. Position
In this example, the agents exchange position information. This position information is handled in a similar way as the battery level information, with two small differences. First, instead of using a battery depletion rate, we define the area where the agent can be after time
as
Second, we define an area
A, which could either be the maximum area of a mission or an area big enough that knowing the agent is somewhere in that area does not bring any valuable information. The utility of a message over time is defined as a ratio between the complement of the area where the agent can be and
A. Such a definition maintains the following property: if the exact position of an agent is known, the utility equals 1 and it drops to 0 when there is no information about the agent’s position (it can be anywhere in
A). Similarly to the battery level example, the position information also uses the
max aggregation function:
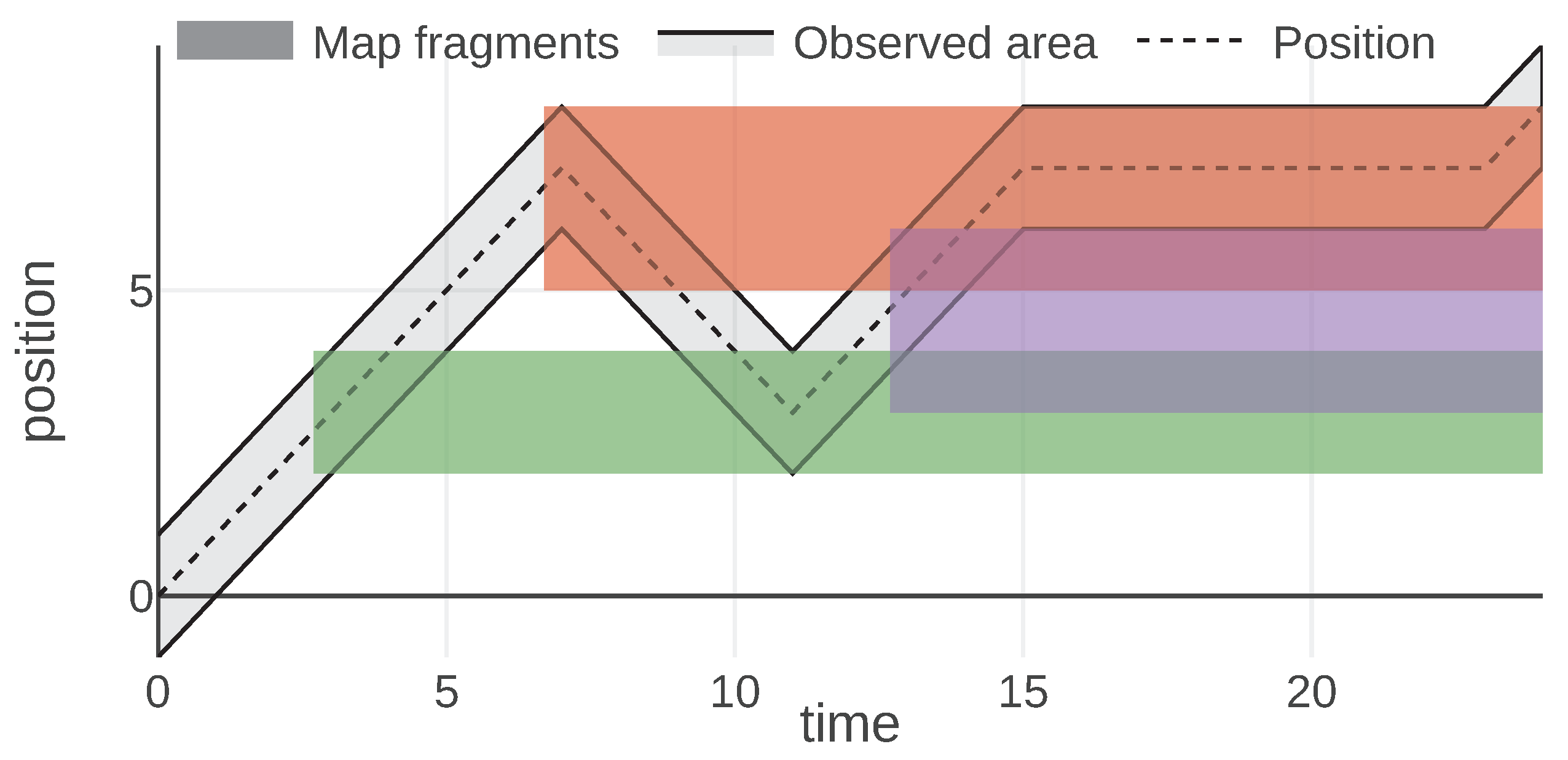
Equations (12) and (13) are plotted in
Figure 3. The result is very similar to the battery type, but the utility decreases quadratically over time. Additionally, the utility is independent of both the message content (last known position) and the state, so the shape of the message utility function is always the same.
4.2. Mission Status Commands
During a mission, it might be required to communicate a status of the mission to all agents involved in it. Examples of statuses include:
waiting for mission start,
mission in progress,
abandon mission,
mission finished. The main characteristic of this type of information is that, as soon as the new message is generated, the mission status changes and all the old messages are not valid anymore. We express that with a constant message utility function and the
last aggregation function:
Figure 4 presents a plot of the aggregation and utility functions for an example communication scenario. An agent aggregates the utility when it knows the current mission status. Each delayed message means that the agent does not know the current status; thus, the final utility is decreased. In the figure this shows as a lack of aggregated utility between the generation and reception of each message. Note that the utility of each message never drops, e.g., the utility of the green message is equal to 1 for almost the whole mission. It is the aggregation function that decides which message should be considered at which point in time and introduces the areas of no utility.
It can be easily observed that, for this information type, a communication scheme that minimizes transmission delays is preferred. The fact that the communication is evaluated from the receiver’s perspective makes such a definition possible—the sender would not have access to information about delays without any additional protocol.
Because the last aggregation function is being used, the approach is only useful to evaluate the performance at the end of the mission assuming a reliable communication channel. Sometimes it might be beneficial to compute the utilities live, while the mission is in progress. Unfortunately, because of the receiver-centric nature of the model, in that case we cannot use the generation time of a new message, because that message might not have been delivered yet. Instead, we can change our modeling approach and define utility as a probability that the status of the mission did not change since the message we have received was generated.
We assume that changes of the status of a mission could be modeled as a Poisson point process, i.e., a process where events (in this case status changes) appear independently at a constant average rate
. Then, a time between events is modeled using exponential distribution. From a memorylessness property of that distribution we know that we can also use it to express a distribution of a time between an observation of a status (i.e., the time when a message is generated) and a change of that status. So the probability that an event occurred since the last observation is expressed using a cumulative distribution function (CDF) of exponential distribution:
. We are interested in an inverse of this event (i.e., that the status did
not change), so we can define the utility as:
We use the
max aggregation function, because we are interested in the message that gives us the maximum probability that a status did not change since it was received. These functions are plotted in
Figure 5 for an example of a mission with
. We can observe that the utility falls down rapidly. Therefore, an information of this kind should be repeated periodically to increase the probability that it is still valid.
4.3. Mission Objectives
Mission objectives, although conceptually similar to mission status, are distinctively different from them. Examples of objectives include: explore sector A, monitor sector B, map sector C. They define goals to be pursued during the mission by agents.
We say that an agent is working on an objective if it actively tries to fulfill it. For instance, if it received a message explore sector A, immediately it does not receive any utility, but it knows that traveling through this sector is beneficial for the mission. We say that it starts to work on this objective as soon as it decides to go to this sector and explore it and this is the time when the utility of this message rises. However, it does not necessarily mean that the agent has to explore the whole sector; it can contribute some work and then continue with a different objective.
This example demonstrates that the message utility is related to the agent’s state (in this case with respect to the objectives that the agent is trying to fulfill) and that it varies over time. It is worth noting that the utility of the message is not necessarily decreasing over time; in this case, it will be equal to 0 at the time of reception and will rise as soon as the agent decides to work on the objective.
An agent cannot start the work on an objective before a message introducing this objective is received by it. It is, however, possible that an agent will work on multiple objectives at the same time. Therefore, we will treat the utilities associated with each objective independently. Hence, the sum aggregation function is used.
For the sake of simple presentation, we assume all objectives have equal importance and each unit of time spent working on the objective is equally useful. Thus, we define the utility of a message that contains objective
o as 1 whenever the agent is actively working on objective
o and 0 otherwise:
where
is the objective introduced in message
m and
is a set of objectives on which the agent was actively working in state
s.
The assumptions about equal importance and constant utility are not required. For some missions it might be more practical to assume the message utility is given by a decreasing function (e.g., if joining at the beginning makes an agent more useful). We could also assign higher utilities to the more important objectives.
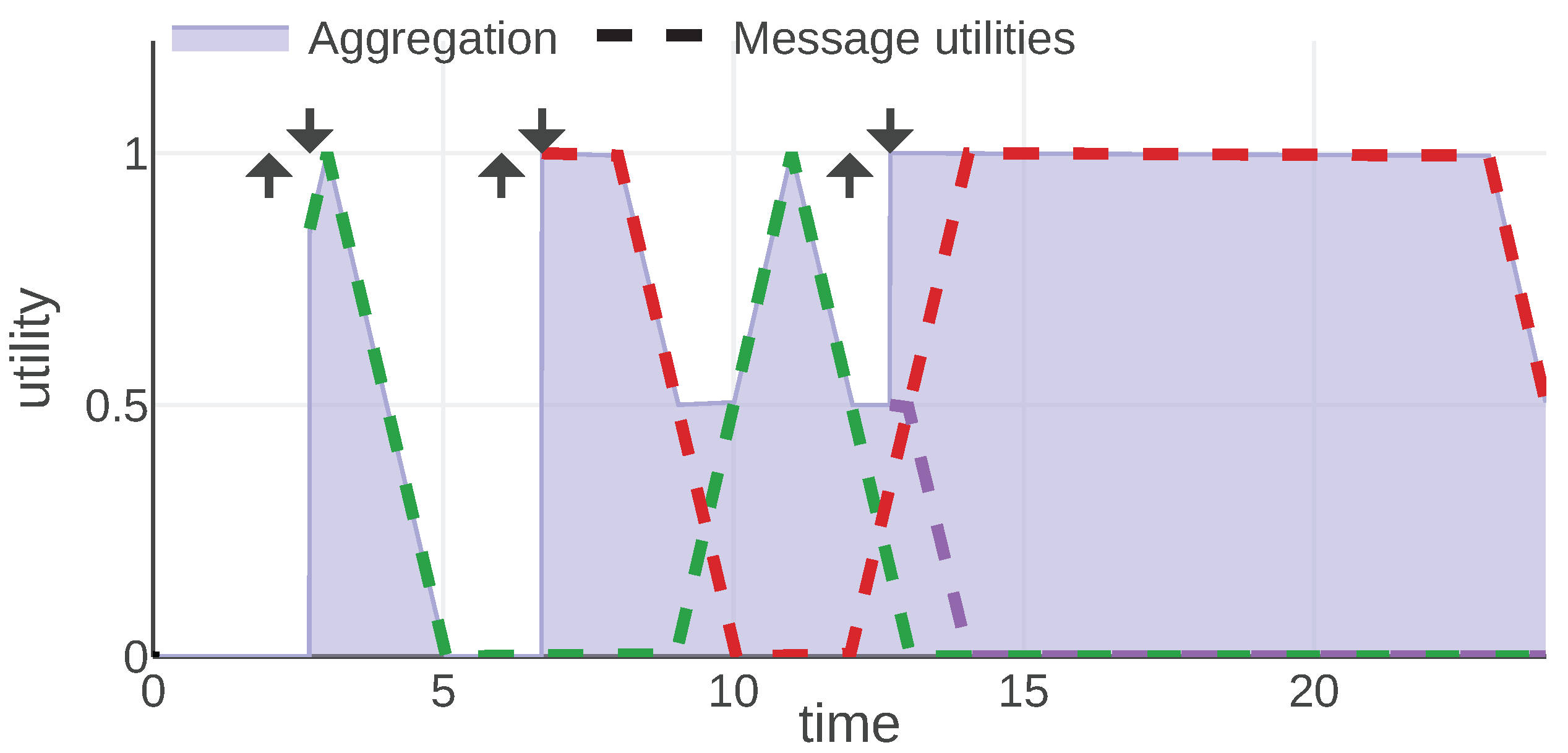
Figure 6 presents a plot of aggregation and message utility functions for an example communication scenario. In this scenario, the agent was working on three objectives:
between time 1 and 9,
between time 7 and 20 and
between time 12 and 20. During time periods
and
the agent is working on two objectives simultaneously. The aggregated utility at each given time is the number of objectives the agent is working on at that time.
If the message corresponding to a particular objective is not received, the agent does not know about it and cannot work on this objective. The utility will not be generated. Therefore, a communication scheme that prioritizes the objectives that are more important to be worked on by the agent will perform well in the evaluation framework.
4.5. Image Streaming
Another interesting kind of information that could be distributed between agents is a stream of images, for instance being captured by a camera of one of the agents. The analysis is motivated by a surveillance mission, where multiple agents (e.g., drones) are monitoring an area and taking pictures of some targets. They exchange these pictures in order to offload some computations and share the knowledge about targets. We focus on situations, where a ground personnel may connect to such drones in order to preview the exchanged image stream. We assume each message contains a single image. We call a stream of such messages viewed by humans a video.
Clearly, there is a wealth of techniques aiming at optimizing video streaming performance. The role of this model is to evaluate those approaches. The simplified example presented here focuses only on one aspect of Quality of Experience (in this case a perceived frame rate) but it could be used as a basis for more complete solutions. In this article, the image streaming information type serves as an opportunity to demonstrate a different approach to defining the utility model instance. So far, message utility functions were defined in a structural fashion, i.e., we were arguing about the amount of information that each message brings at a time instance and constructing the functions accordingly. This time, we first specify some properties of the resulting total utility and based on that we come up with a form of message utility function.
We base our definition of the model on an assumption that the human perception of a frame rate of a video can be modeled by the Weber–Fechner law [
26]. The law relates the subjective perception of human senses (
p) to the objective stimulus intensity (
f) and claims that this relationship is logarithmic:
for some
and
.
is a smallest stimulus that can be perceived.
In our case, the observed subjective quality is the smoothness of the video and an objective measure is expressed in frames per second (FPS). The utilities provided by the model should be proportional to the perceived quality, hence in the definition of the model we aim at having the logarithmic relationship between utilities and FPS. Therefore the model should have the following property:
where
is a message set which results in a video being streamed at
f FPS, formally:
Even though in the original formulation of Fechner’s law (Equation (23)) the natural logarithm is used, we can change the base of the logarithm by substituting
, where
B is a new base of the logarithm and
S is the parameter of the model. We have decided to use
, which is often used in IT applications. The final form of the utility function is:
Next, we introduce a message utility function and we show that the obtained model fulfills the requirement defined in Equation (26). For the sake of simple presentation, in this analysis we assume the absence of delays (i.e., the frame is received at the same time it is being generated). We take delays into account in the definition of message utility, so they will lead to a lower total utility value, but we do not examine their impact. Naturally, we use the
max aggregation function since the last frame always brings the most useful information. Let us assume a message utility function has the following form:
By solving a system of Equations (26) and (27) we can find out that the proposed model indeed results in a pursued relationship for
and arbitrary
l. Unfortunately, this definition is impractical: it might result in an infinitely large or negative utility value, which might mean that receiving some messages introduces loss or disproportionately huge gains.
Therefore, we have decided to limit the values of Equation (27) by capping them to [0, 1], while still using the
max aggregation function. It results in the following model:
The maximum value of total utility per second is limited to 1, by such an approach. We assign this value to an exchange that results in a video streamed with frame rate of
FPS. Any exchange that results in a higher frame rate should receive the same utility, formally:
If we had tried to pursue the same approach as we did with the
(Equation (27)) utility function, i.e., tried to solve a system of Equations (26), (28) and (30), there would have been no solutions. The model received in that case no longer results in the logarithmic relationship we were pursuing. However, if instead of looking for solutions for any
f in Equation (26) we pick just one frequency
, we get the following results:
In practice it means that the relationship is not logarithmic anymore. In the “ideal” case, each time the frequency was divided by
B, the utility was lowered by
S. In the new model this property holds only for a specific frequency
. However, in practice it should not be a problem, as usually the system will aim at streaming videos close to some predefined frame rate and we will be evaluating exchanges that result in frame rates similar to that one. Additionally, the relationship we have achieved is indeed very close to logarithmic.
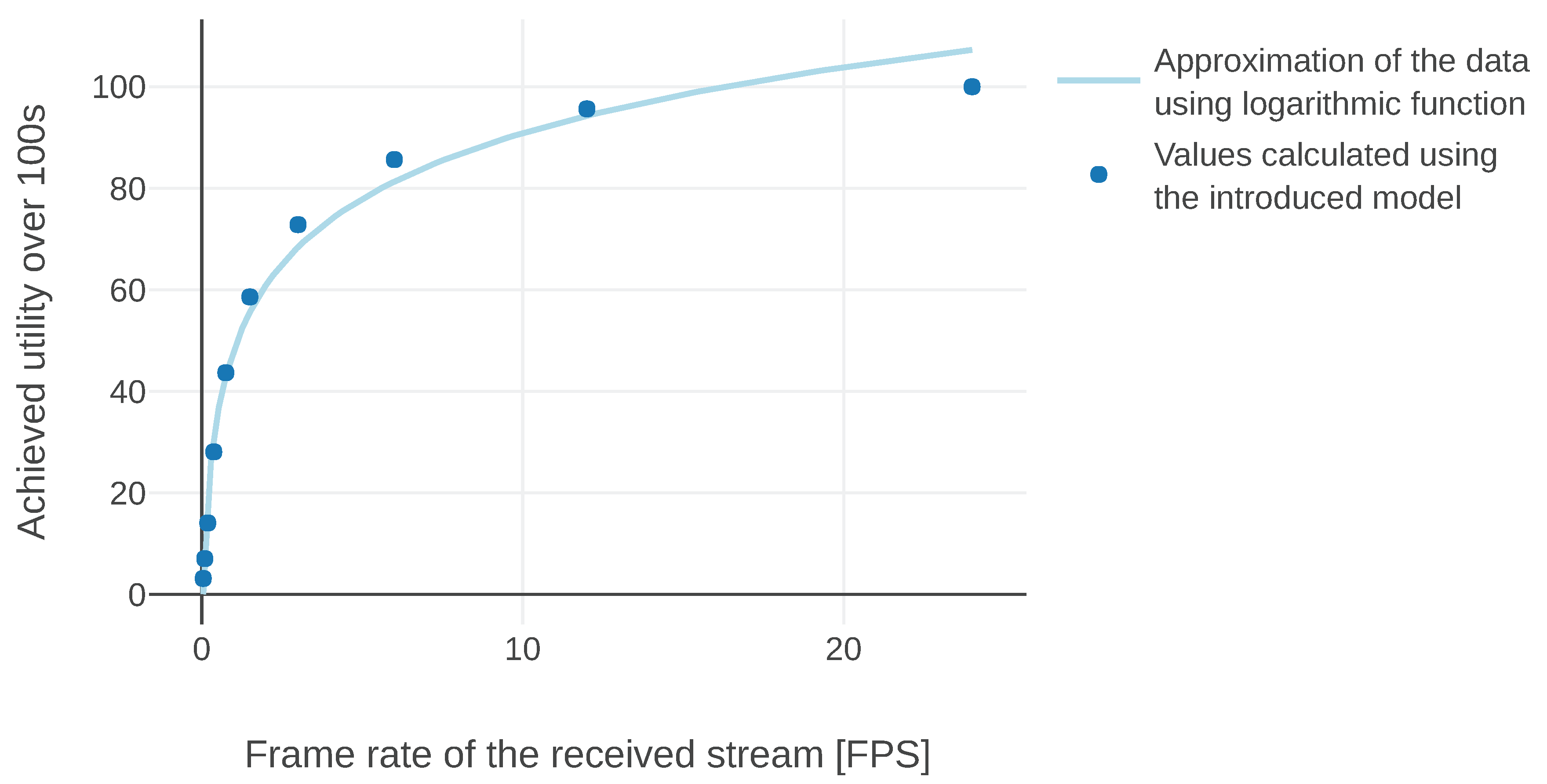
We have calculated the values of parameters
k and
l for
,
, and
. Then, we have simulated missions in which images were sent with different frame rates over 100 s. In practice, it means that we were evaluating the model for different
. The utilities generated during these simulations are presented in
Figure 9. The blue line represents an ideal model while circles correspond to utilities achieved by simulating the modified version. We find the resulting model satisfactory, because it is motivated by an abstraction of human perception, which itself often does not strictly adhere to the logarithmic relationship.
Figure 10 presents a plot of the utility and aggregation functions from the introduced model. We can observe that exactly for
the function is flat. If messages were to be exchanged with a higher frequency than
, the result will just be a constant function. After that time period, the function decreases logarithmically. The slope of that decrease can be adjusted with the
S parameter.
In the following paragraphs, we examine the possibility to include source adaptation in the model. Most types of data can be adapted in order to reduce the amount of data sent while sacrificing the information content. A video stream is a good example, because image compression techniques can achieve a very good compression rate while the stream still looks good for a viewer. Of course, an important part of video adaptation is reducing its frame rate. However, this part is already taken into account by the model, as it assigns lower utilities when the message (an image) is not received, therefore penalizing lower FPS streams. In the following, we will only examine how to incorporate into the model the information about a lower quality of a transferred message (e.g., a lower resolution).
We model adaptation in the following way. First of all, we define the notion of a version of a message. Each message could be available in multiple versions. They are all generated at the same time and they all represent the same knowledge, but the information content might differ, i.e., for any message, a sender can decide to send an adapted (e.g., lower quality) version of that message. We call “the best version of a message” a version that has the highest information content. For instance, in the case of a video stream it could mean that the same image can be sent in multiple resolutions. The best version of that message will be the image with highest resolution available for the sender.
The evaluation model should take the existence of those versions into account and assign lower utilities to versions of messages that contain less information. At any point in time the sender can decide to re-transmit the same message in a different version (e.g., in a higher resolution). As soon as a better version is received, the evaluation model should use it instead of the previous one.
In order to implement these features, we make two changes to the model introduced in
Section 3. First of all, the model did not include the notion of versions of messages. Hence, in the case of the
max aggregation function, we redefine each message in the model as being the best version of that message at a given time (all other versions are not used). It means that the definition of
from Equation (3) changes and should contain only the best versions of all messages available at time
t. Second, we need to introduce a version of the message utility function that takes adaptation into account. Our example is based on video streaming messages, because it uses the image resolution, but a similar parameter of a message can be used for any other type. The adaptation is realized by changing the resolution of images. We assume the utility of the adapted image is proportional to its diagonal, expressed in number of pixels. The message utility function takes the following form:
where
is a diagonal of the image provided in message
m and
d is a diagonal of a frame in a maximum available resolution on the sender’s side.