Design of a FlexRay/Ethernet Gateway and Security Mechanism for In-Vehicle Networks
Abstract
1. Introduction
2. Related Works
2.1. Gateways
2.2. Automotive Ethernet and Security
3. Proposed Methodology
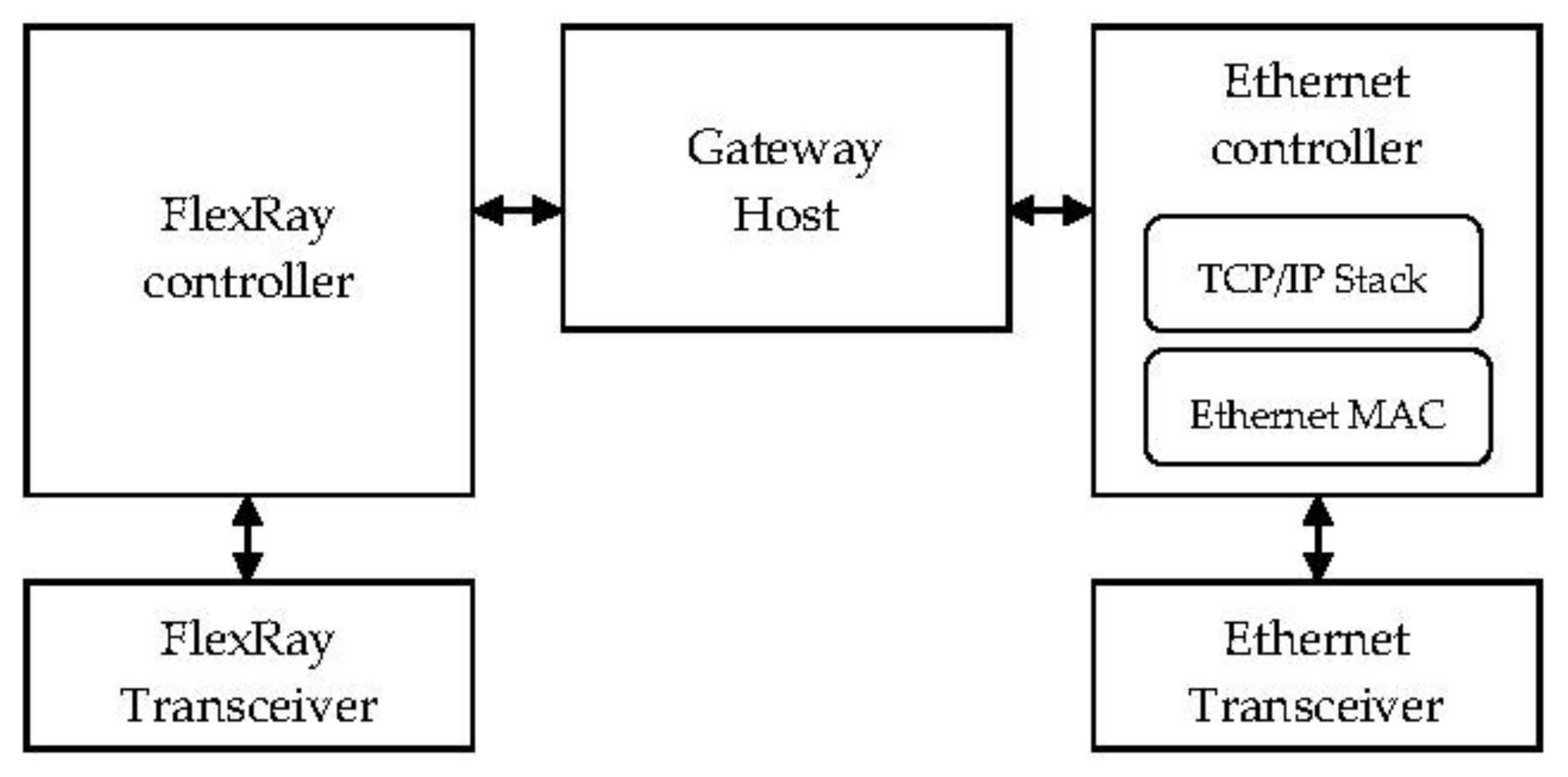
3.1. System Architecture
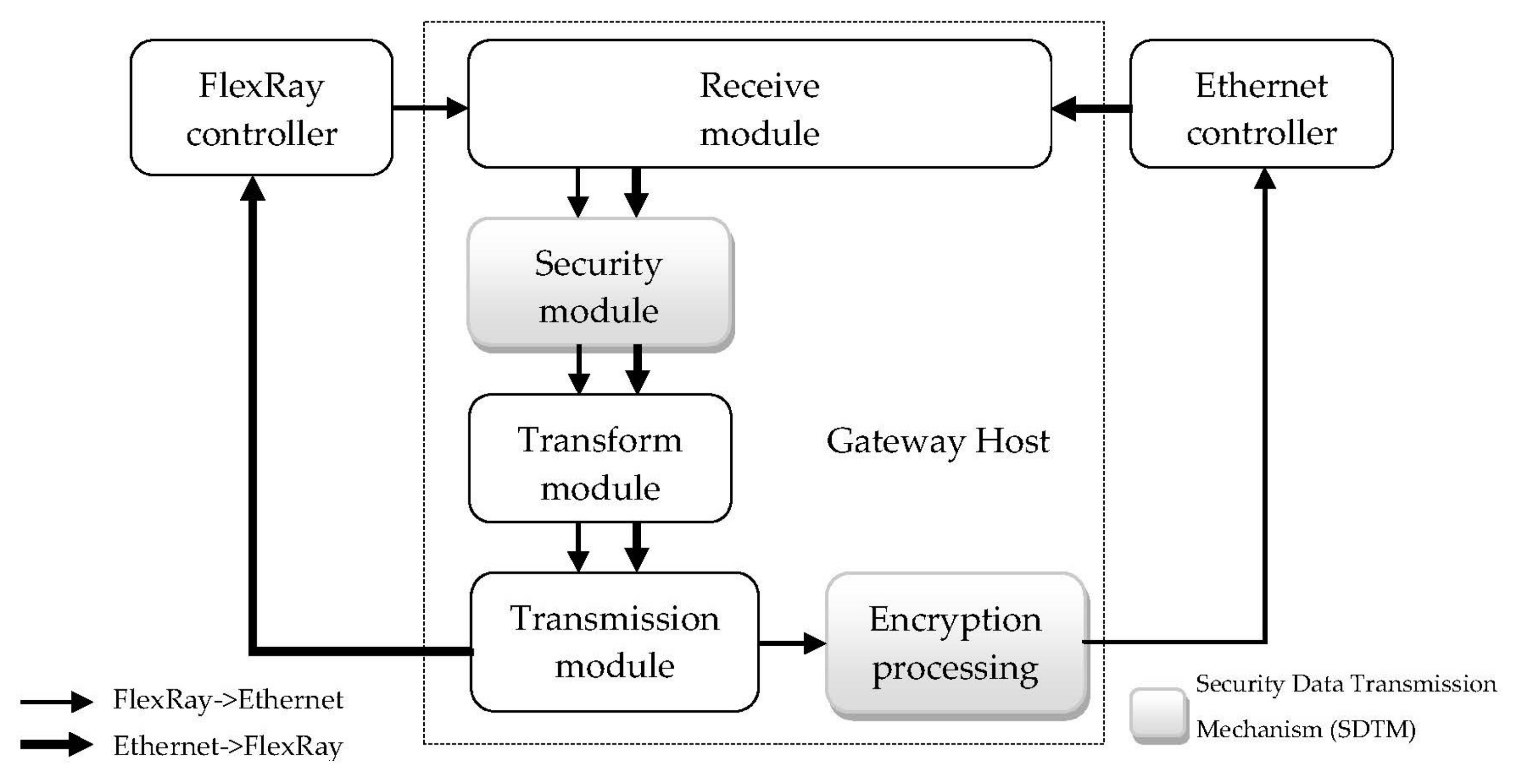
3.2. The Gateway Host
| Algorithm 1. Data path from FlexRay to Ethernet |
| Inputs: Frame of FlexRay Outputs: Frame of Ethernet |
|
| Algorithm 2. Data path from Ethernet to FlexRay |
| Inputs: Frame of Ethernet Outputs: Frame of FlexRay |
|
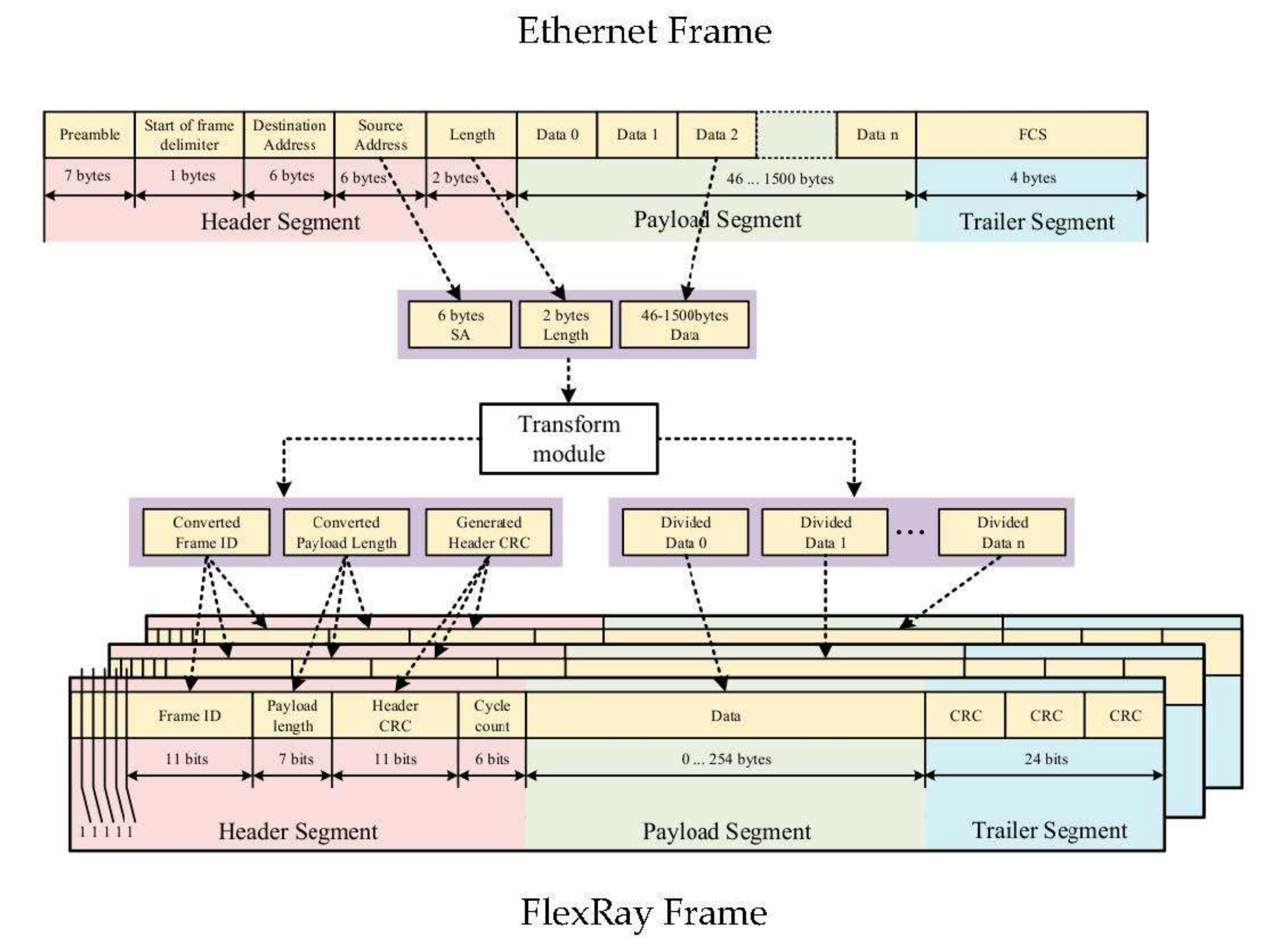
3.3. Implementation of the Proposed Gateway
3.4. Design of the Secure Data Transmission Mechanism
- Risk-control strategies
- Encryption methods
- DES is a classical symmetric-key algorithm for the encryption of electronic data with a 56-bit key size. The operation speed of encryption is the fastest of the three encryption methods, but the DES key is easy to break in a short period of time.
- AES supersedes the DES with a 128-bit key size. It is a subset of the Rijndael block cipher. Research into attacks on AES encryption has continued since the standard was finalized in 2000, which means the security is sufficient for modern vehicle communications.
- AES-CCM is one of the authenticated encryption schemes as specified by the National Institute of Standards and Technology (NIST) [24]. The CCM mode is a mode of AES operation for cryptographic block ciphers and is used to protect the static segment of FlexRay, which is recommended by the IEEE 802.11 standard. Thus, the AES-CCM is considered the future encryption method in the IoV [25].
4. Experimental Results
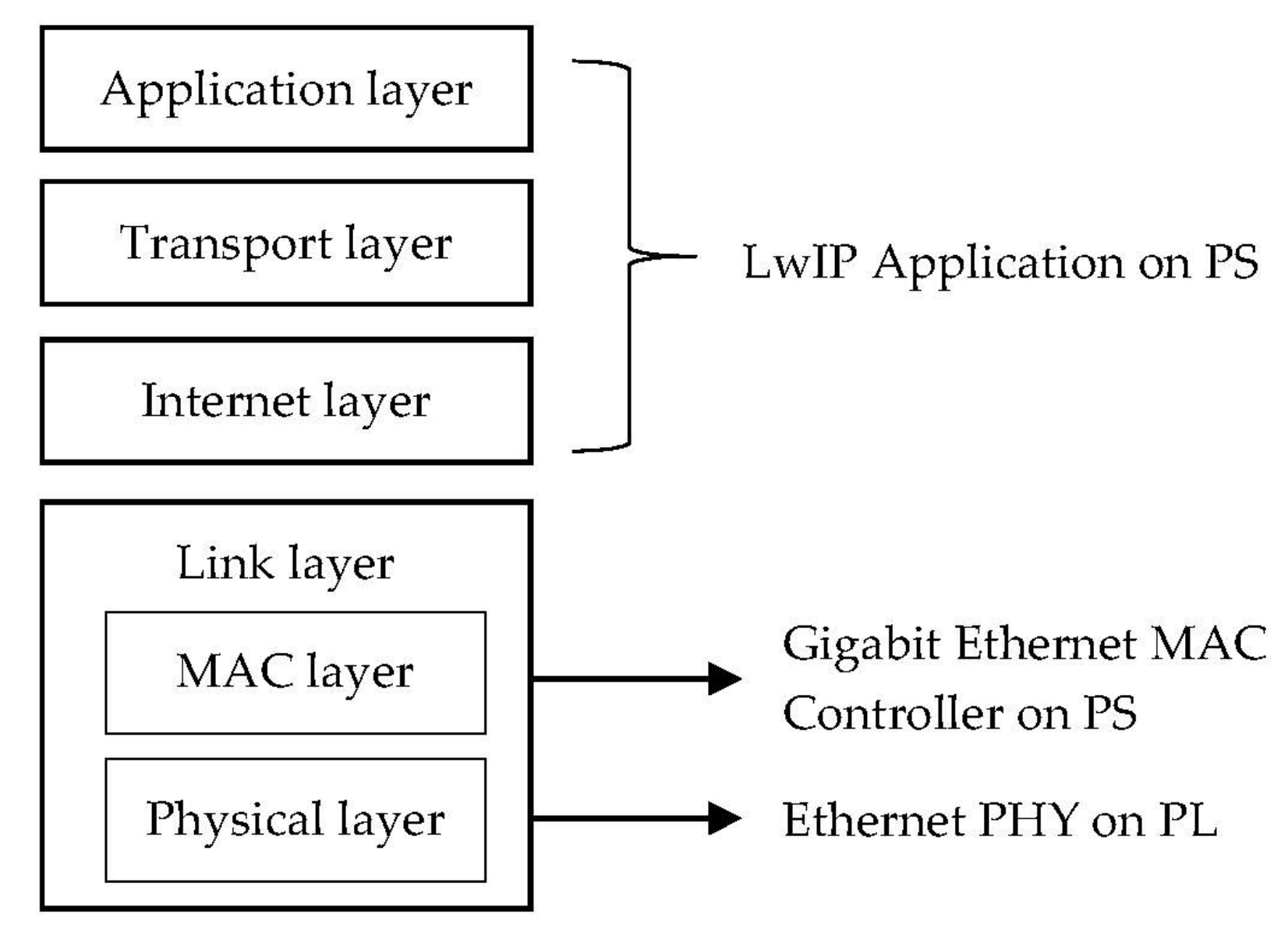
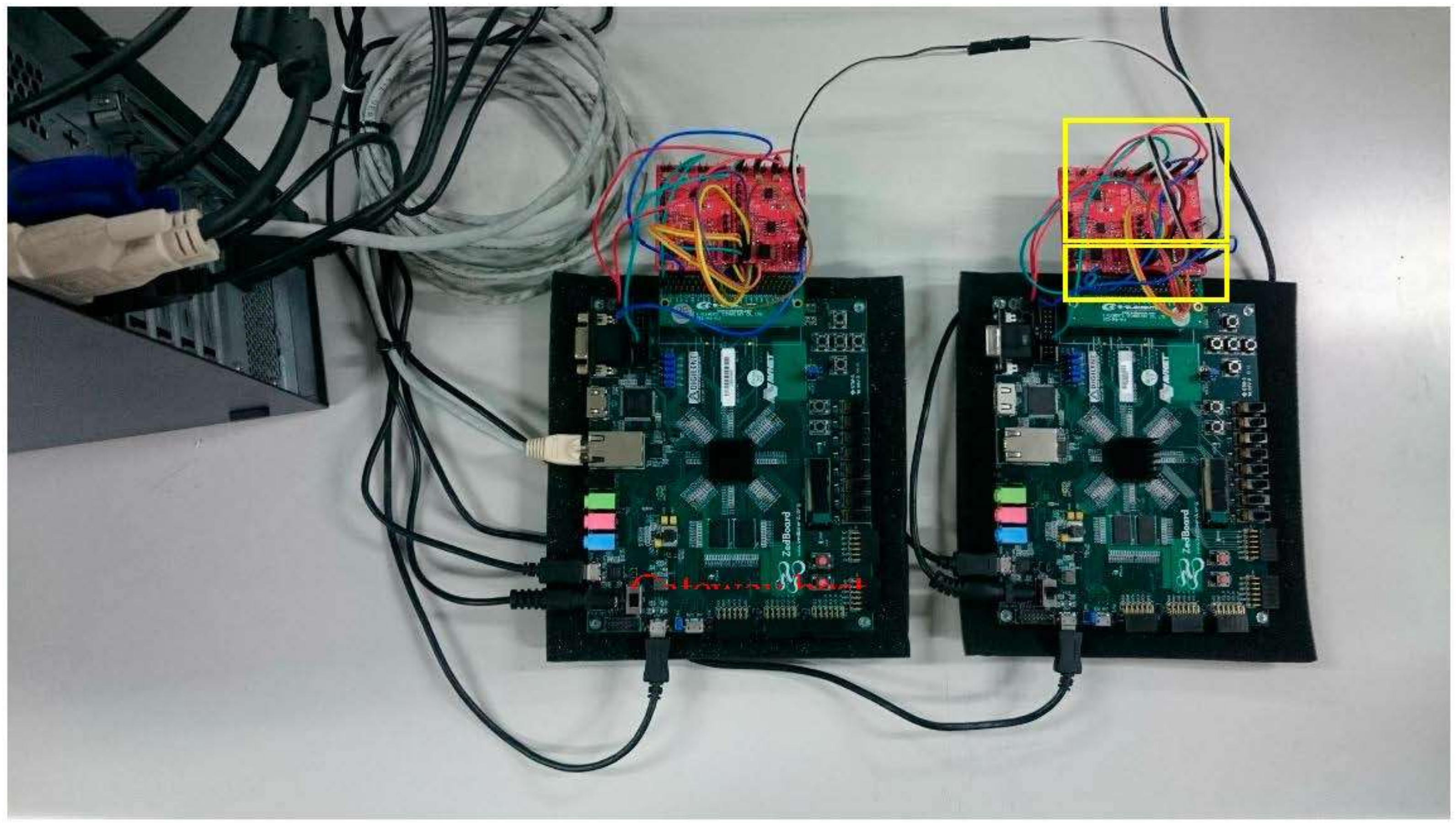
4.1. Experimental Platform and Environment
4.2. Execution Time Management and Analysis
4.3. Cost of Security Mechanism
4.4. Performance Evaluation
- (1)
- Using the HW/SW (hardware/software) method, data communication is implemented between the FlexRay and Ethernet network.
- (2)
- The risk-control strategies are related to FlexRay data signals, and the proposed Security Data Transmission Mechanism (SDTM) is integrated as an extension of the gateway.
- (3)
- The novelty of the vehicular gateway is to improve the security with little overhead, and it is more suitable for IVNs and the IoV in the future.
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- FlexRay Consortium. FlexRay Communications System—Protocol Specification—Version 2.1 Revision A. Available online: https://www.google.com.hk/url?sa=t&rct=j&q=&esrc=s&source=web&cd=1&ved=2ahUKEwi--6TIo5nnAhVjL6YKHSzcDb8QFjAAegQIBBAB&url=https%3A%2F%2Fsvn.ipd.kit.edu%2Fnlrp%2Fpublic%2FFlexRay%2FFlexRay%25E2%2584%25A2%2520Protocol%2520Specification%2520V2.1%2520Rev.A.pdf&usg=AOvVaw0snIyyfkFMHWc7KHRLdS82 (accessed on 23 January 2020).
- Shane, T.; Martin, G.; Ciaran, H.; Edward, J.; Mohan, T.; Liam, K. Intra-Vehicle Networks: A Review. IEEE Trans. Intell. Transp. Syst. 2015, 16, 534–545. [Google Scholar]
- Puhm, A.; Roessler, P.; Wimmer, M.; Swierczek, R.; Balog, P. Development of a flexible gateway platform for automotive networks. In Proceedings of the IEEE International Conference on Emerging Technologies and Factory Automation, Hamburg, Germany, 15–18 September 2008. [Google Scholar]
- Sander, O.; Hubner, M.; Becker, J.; Traub, M. Reducing latency times by accelerated routing mechanisms for an FPGA gateway in the automotive domain. In Proceedings of the IEEE International Conference on Field-Programmable Technology, Taipei, Taiwan, 8–10 December 2008. [Google Scholar]
- Herber, C.; Richter, A.; Wild, T.; Herkersdorf, A. Real-time capable CAN to AVB Ethernet gateway using frame aggregation and scheduling. In Proceedings of the Design, Automation and Test in Europe Conference and Exhibition, Grenoble, France, 20–21 March 2015. [Google Scholar]
- Kim, J.H.; Seo, S.H.; Nguyen, T.; Cheon, B.M.; Lee, Y.S.; Jeon, J.W. Gateway Framework for In-Vehicle Networks based on CAN, FlexRay and Ethernet. IEEE Trans. Veh. Technol. 2015, 64, 4472–4486. [Google Scholar] [CrossRef]
- Shreejith, S.; Mundhenk, P.; Ettner, A.; Fahmy, A.; Steinhorst, S.; Lukasiewycz, M.; Chakraborty, S. VEGa: A High Performance Vehicular Ethernet Gateway on Hybrid FPGA. IEEE Trans. Comput. 2017, 66, 1790–1803. [Google Scholar] [CrossRef]
- Lee, Y.S.; Kim, J.H.; Jeon, J.W. FlexRay and Ethernet AVB Synchronization for High QoS Automotive Gateway. IEEE Trans. Veh. Technol. 2017, 66, 5737–5751. [Google Scholar]
- Liao, R.H.; Lee, T.Y.; Lin, I.A. Design of FlexRay/Ethernet Automotive Gateway. In Proceedings of the 29th Symposium on VLSI Design/CAD, Kaohsiung, Taiwan, 7–10 August 2018. [Google Scholar]
- Mateus, K.; Königseder, T. Automotive Ethernet, 1st ed.; Cambridge University Press: Cambridge, UK, 2014. [Google Scholar]
- Soares, F.L.; Campelo, D.R.; Yan, Y.; Ruepp, S.; Dittmann, L.; Ellegard, L. Reliability in Automotive Ethernet Networks. In Proceedings of the IEEE International Conference on the Design of Reliable Communication Networks, Kansas City, MO, USA, 24–27 March 2015. [Google Scholar]
- Sakiz, F.; Sen, S. A survey of attacks and detection mechanisms on intelligent transportation systems: VANETs and IoV. Ad. Hoc. Netw. 2017, 61, 33–50. [Google Scholar] [CrossRef]
- Irshad, A.S.; Iftikhar, A.; Halabi, H.; Manan, J.L.B.A. Classes of attacks in VANET. In Proceedings of the IEEE Saudi International Electronics, Communications and Photonics Conference, Riyadh, Saudi Arabia, 24–26 April 2011. [Google Scholar]
- Bittl, S. Attack potential and efficient security enhancement of automotive bus networks using short MACs with rapid key change. Commun. Technol. Veh. 2014, 113–125. [Google Scholar] [CrossRef]
- TCP Connection Monitoring System. In Proceedings of the International Conference on Computational Intelligence & IoT, Tripura, India, 11–15 December 2018; pp. 419–423.
- Ethernet_Frame. Available online: https://en.wikipedia.org/wiki/Ethernet_frame (accessed on 1 March 2018).
- PATAK Engineering FlexRay Controller Documentation. Available online: http://patakengineering.eu/download/FlexRayController.pdf (accessed on 6 March 2018).
- Dunkels, A. Design and Implementation of the lwIP TCP/IP Stack. Available online: http://www.sics.se/~adam/lwip/doc/lwip.pdf. (accessed on 7 July 2018).
- Liu, J.J.; Zhang, S.B.; Sun, W.; Shi, Y.P. In-Vehicle Network Attacks and Countermeasures: Challenges and Future Directions. IEEE Netw. 2017, 31, 55–58. [Google Scholar] [CrossRef]
- Fadlullah, Z.M.; Nishiyama, H.; Kato, N.; Fouda, M.M. Intrusion Detection System (IDS) for Combating Attacks Against Cognitive Radio Networks. IEEE Netw. 2013, 31, 51–56. [Google Scholar] [CrossRef]
- Wang, L.; Liu, X. NOTSA: Novel OBU With Three-Level Security Architecture for Internet of Vehicles. IEEE Internet Things J. 2018, 5, 3548–3558. [Google Scholar] [CrossRef]
- X-By-Wire Team. X-By-Wire: Safety Related Fault Tolerant Systems in Vehicles. Project No. BE 95/1329. Available online: https://cordis.europa.eu/project/id/BRPR950032 (accessed on 23 January 2020).
- A Structured Approach to Anomaly Detection for In-Vehicle Networks. In Proceedings of the 6th IEEE International Conference on Information Assurance and Security, Atlanta, GA, USA, 22–23 August 2010.
- National Institute of Standards and Technology. Recommendation for Block Cipher Mode of Operation: The CCM Mode for Authentication and Confidentiality. Available online: https://www.nist.gov/publications/recommendation-block-cipher-modes-operation-ccm-mode-authentication-and-confidentiality (accessed on 23 January 2020).
- Hung, C.W.; Hsu, W.T. Power Consumption and Calculation Requirement Analysis of AES for WSN IoT. Sensors 2018, 18, 1675. [Google Scholar] [CrossRef] [PubMed]
- Wireshark Go Deep. Available online: https://www.wireshark.org/ (accessed on 10 March 2018).



| Method | Development Board | Manufacturer | Platform Clock | Security Mechanism |
|---|---|---|---|---|
| Kim [6] | MPC5668EVB | NXP | 116 MHz | not included |
| Shreejith [7] | ZC702, ZC706 | Xilinx | 200 MHz | not included |
| Lee [8] | TC275EVB | Infineon | 200 MHz | not included |
| This paper | XC7Z020 | Xilinx | 100 MHz | included |
| Security Level | Applications (Examples) | Security Mechanism | |||
|---|---|---|---|---|---|
| Receive Status | Frame CRC | UDP Header | MAC Address/ID | ||
| High | Powertrain systems X-by-wire | enable | enable | enable | enable |
| Medium | Collision avoidance system Electronic stability control | enable | enable | enable | disable |
| Low | suspension Traction control system | enable | enable | disable | disable |
| Encryption Methods | Parameters | |||
|---|---|---|---|---|
| Data Block (Bits) | Key Length (Bits) | Rounds (Times) | Mode of Operation | |
| DES | 64 | 56 | 16 | N/A |
| AES | 128 | 128/192/256 | 10/12/14 | ECB-mode |
| AES-CCM | 128 | 128/192/256 | 10/12/14 | CCM-mode |
| Proposed Architectures | Implementation Platform/OS | EDK/Tools | Resource Measurement |
|---|---|---|---|
| FlexRay Node | Xilinx Zedboard Zynq-7000 AP SoC | Xilinx Vivado 2018.1 | Xilinx Vivado 2018.1 utilization report |
| Proposed Gateway host | Xilinx Zedboard Zynq-7000 AP SoC | Xilinx Vivado 2018.1 Xilinx ISE 14.7 | Xilinx Vivado 2018.1 utilization report |
| Ethernet End | Windows 7 Professional Intel Core i7 3.6 GHz | Network Debug Assistant Wireshark | N/A |
| Messages Path | Latency Components | |||
|---|---|---|---|---|
| FlexRay Node (PL) | Gateway Host (PL) | Ethernet End (LwIP in PS) | Total Run Time | |
| FlexRay -> Ethernet (with AES-CCM) | 8.25 | 4.67 | 5.55 | 18.47 |
| Ethernet -> FlexRay | 7.96 | 6.71 | 1.36 | 16.03 |
| Implementation Method | Resource Consumption (Reg, LUTs) | Resource (LUTs) | Power Consumption |
|---|---|---|---|
| Proposed gateway | 1.00× (4950), 1.00× (4880) | 9.3% | 1.00× |
| Proposed gateway with SDTM | 1.25× (6125), 1.24× (6182) | 11.62% | 1.01× |
| Message Path | Receive Module | Security Module | Transform Module | Transmission Module | Total Runtime |
|---|---|---|---|---|---|
| FlexRay -> Ethernet | 0.86 | 0.47 | 2.13 | 1.21 | 4.67 |
| Ethernet ->FlexRay | 1.14 | 0.61 | 3.72 | 1.24 | 6.71 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, T.-Y.; Lin, I.-A.; Liao, R.-H. Design of a FlexRay/Ethernet Gateway and Security Mechanism for In-Vehicle Networks. Sensors 2020, 20, 641. https://doi.org/10.3390/s20030641
Lee T-Y, Lin I-A, Liao R-H. Design of a FlexRay/Ethernet Gateway and Security Mechanism for In-Vehicle Networks. Sensors. 2020; 20(3):641. https://doi.org/10.3390/s20030641
Chicago/Turabian StyleLee, Trong-Yen, I-An Lin, and Ren-Hong Liao. 2020. "Design of a FlexRay/Ethernet Gateway and Security Mechanism for In-Vehicle Networks" Sensors 20, no. 3: 641. https://doi.org/10.3390/s20030641
APA StyleLee, T.-Y., Lin, I.-A., & Liao, R.-H. (2020). Design of a FlexRay/Ethernet Gateway and Security Mechanism for In-Vehicle Networks. Sensors, 20(3), 641. https://doi.org/10.3390/s20030641




