1. Introduction
Internet of Things (IoT) affects services such as facility management, smart buildings, connected cities, and manufacturing applications. Low-power wide area networks (LPWAN) appear to be a long-range solution that can respond to the demands of IoT services, which involves the deployment of highly scalable systems employing low-cost edge-devices with low battery consumption [
1,
2]. Long range (LoRa), Sigfox, LTE-M, and LTE NarrowBand (NB)-IoT are currently the LPWAN technologies with the greatest momentum [
3]. In these types of LPWAN technologies, a large number of end devices (EDs) are deployed at an urban scale, and they transmit a relatively small amount of data directly to the base station (BS) or gateway, in a so-called star topology. These systems use the ALOHA-based protocol to take advantage of its low energy consumption for the media access control (MAC) protocol. Moreover, in LPWAN, the EDs use a different physical layer (PHY) to mitigate the effects of interference and noise. In particular, the PHY of LoRa technology is a derivative of the chirp spread spectrum (CSS), while that of Sigfox technology is an ultra-narrow band modulation using binary phase-shift keying.
In this paper, we focus on LoRa proposed by Semtech and promoted by the LoRa Alliance [
4], where there are three classes of EDs based on their downlink response time and energy consumption. Class A type EDs offer the best energy-saving performance by waking up only when they have data to transmit using ALOHA. Class B type EDs wake up at periodic intervals to synchronize and exchange data with the gateway. Class C mode has no downlink restrictions and can receive downlink messages any time whenever it is not in a transmitting state. Since class B and class C are extensions to the specification of class A, we consider a class A mode.
While it is well known that the maximum throughput is for a pure ALOHA protocol-based system, its throughput is obtained by assuming that a collision occurs when two or more packets arrive at the receiver in an overlapping time period. However, in a practical network, the overlapped packets can be demodulated at the receiver with a certain threshold, which is called the capture effect.
In previous work on LoRa, Centenaro et al. [
5] and Haxhibeqiri et al. [
6] demonstrated that LoRa PHY using CSS can achieve improved performance, in which the MAC protocol’s effect was expected. Magrin et al. [
7] and Abeele et al. [
8] showed the improved performance of the LoRa system through simulations. In addition, Augustin et al. [
9] established some field trials of LoRa EDs and system-level simulations of LoRa MAC procedures to evaluate the throughput of a LoRa network. Reference [
10] studied the performance analysis of LoRa modulation, in which the collisions between packets modulated with different SFs were considered. In References [
11,
12,
13,
14], the capture effect of LoRa was considered. To improve the capture effect of LoRa, Noreen et al. [
11] applied successive interference cancellation scheme, which can allow recovering of the weaker packets. In Reference [
12], the authors developed the capture effect model for analyzing the LoRa network, where the propagation loss is considered for the channel model. From a modeling point of view, in this paper, we will consider the capture effect as in References [
11,
12,
13,
14]. In contrast to References [
11,
12,
13], we will furthermore consider fading channel model as well as interfering power model according to the overlap time of interfering packet.
As mentioned above, CSS is used as a modulation scheme for LoRa systems that support the six-spreading factor (SF). This can guarantee orthogonality when, for the overlapped packets with different SF, these get a signal to interference and noise ratio (SINR) over a certain isolation threshold [
15]. Hence, we only focus on the interference caused by the co-spreading factor interference.
The main contribution of this paper is in analyzing the performance of a pure ALOHA protocol-based LoRa system with the capture effect under the orthogonality of the CSS modulation scheme. In particular, under the infinite population model for a pure ALOHA protocol, we can derive a power threshold-based analytical model for obtaining the upper bound performance for LoRa systems. For the capture effect, we introduce the pure ALOHA capture model, where the interfering power is proportional to the length of time overlapped.
The remainder of this paper is organized as follows.
Section 2 introduces the LoRa systems model with CSS scheme. The expression for the success probability is derived in
Section 3. The results of the analytical model are presented in
Section 4 and conclusions are given in
Section 5.
2. System Model
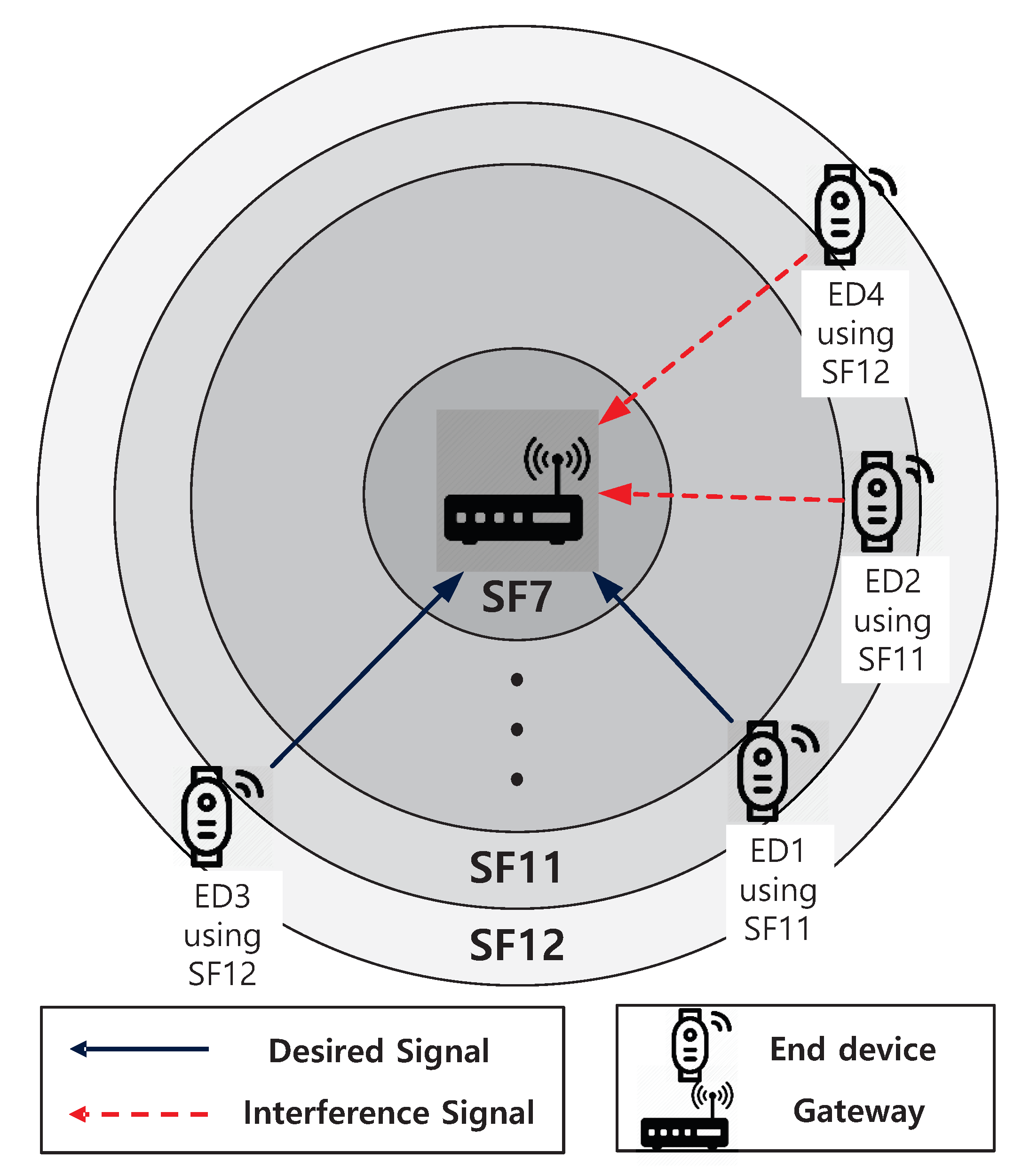
Suppose an LoRa network composed of EDs and a gateway, where EDs are uniformly deployed over a circular area cell and can communicate with a gateway at the center of the cell. As shown in
Figure 1 and
Table 1, a cell is divided into six zones which can be referred to as
to
according to SF. We assume that the new packet generation process of EDs in a cell follows a Poisson process with a mean request rate of
(packets/s). Then, EDs arriving in a zone
i generate a packet at an interval, which is exponentially distributed with mean
, where
is the fraction of the
area to the cell. We further assume that one ED can only hold one packet, and that it will not generate a new packet until it has a success or collision for the transmitted packet, where the length of a packet,
T, is normalized to one. Additionally, we consider the infinite population model where aggregate traffic, that is, the sum of new packets transmitted by non-backlogged EDs and those retransmitted by backlogged ones constitutes a Poisson process.
In our system, successful packet transmission can proceed in two ways: The first one is that in which a tagged packet is to be considered a successful packet transmission when there are no overlapped packets during a period of collision for a tagged packet. The second case is that the signal-to-interference noise ratio (SINR) of a tagged packet received at the gateway is more than a predefined threshold value, where a tagged packet undergoes collisions with other packets. For this case, we assume that, for the asynchronously received packets, the gateway’s receiver attempts to decode the first receiving packet and treats other packets as interfering packets.
Let
and
be the success probabilities of the first and second cases, respectively. For a zone
i, the throughput of the system with capture is expressed as
where
, as has been well known that the success probability of a pure ALOHA system without the capture effect, is
. Thus, the normalized total throughput is expressed as
where
denotes the capture effect probability for a zone
i, which will be derived in the next section.
3. Analysis
In this section, we establish the analytic model for the capture effect probability,
, which is based on the power threshold model. Although, for this model, noise will be ignored in the analysis for the sake of simplicity, we take noise in simulations into account and compare the results of the analysis with the simulation results in
Section 4.
Lemma 1. For , the probability that the first arriving packet will have a collision in region i, , is expressed as Proof. As mentioned in the system model, we assume that the packet generate process follows a Poisson process with a mean request rate of
for a region
i. From this assumption, the probability that a packet is arrived after idle,
, is expressed as
Note that, for , the success probability without the capture effect is . Thus, . □
In order to establish the power threshold model, we assume that the power of the packet received at the gateway from an ED
j is as follows
where
is the transmission power of a ED and
indicates the small-scale fading, which is assumed to be exponentially distributed with mean
, that is, Rayleigh fading.
denotes path loss at a distance
between ED
j and the gateway, where
denotes the path-loss exponent.
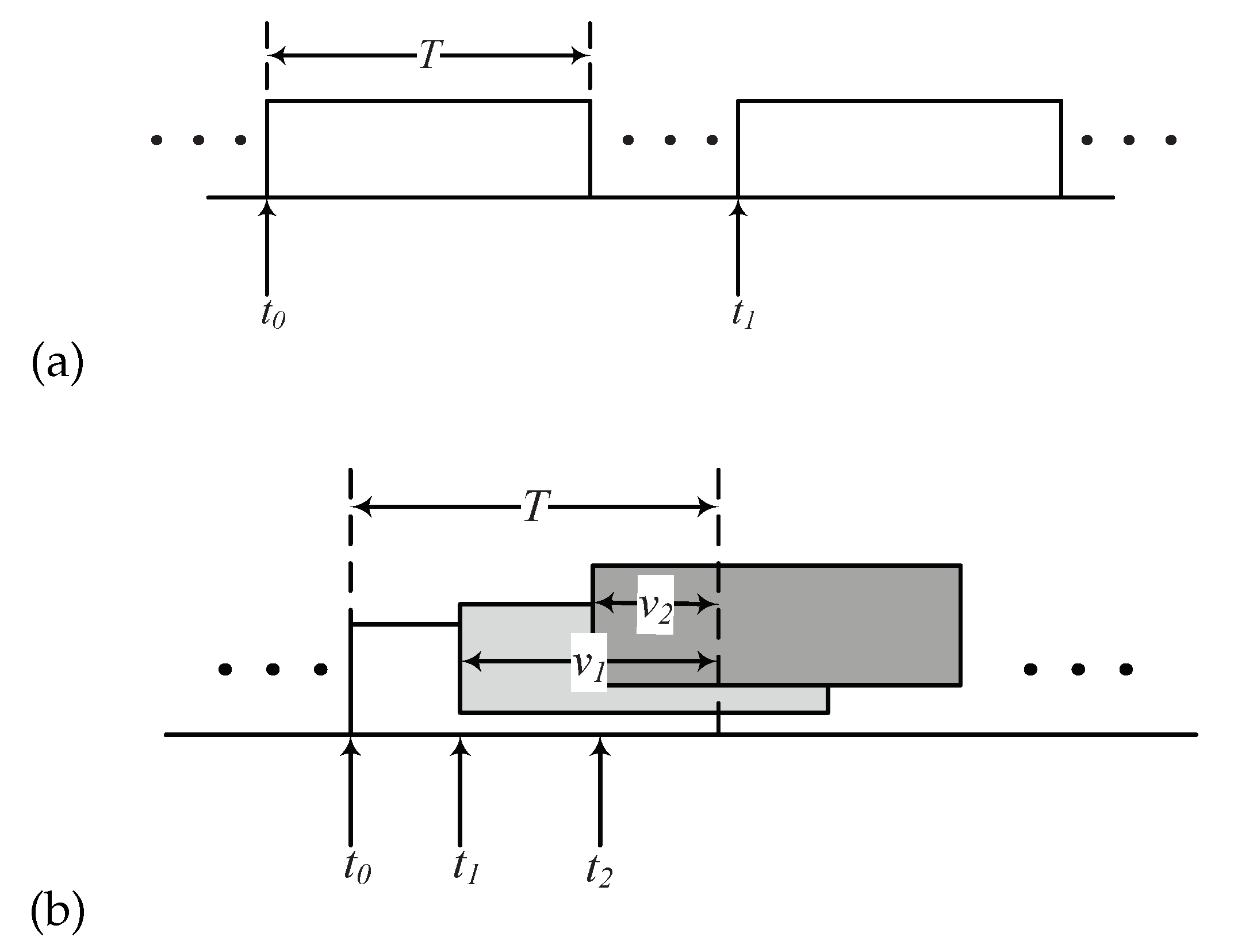
Suppose that the interfering power is proportional to the length of the time overlapped during the transmission time of the target packet, that is,
. Then, let us consider that a packet received at
is corrupted by the other packet transmissions occurring at
and
in
Figure 2. In such a scenario, the sum of the interference power is
. Based on this assumption, the SINR of the target packet received at the gateway from the target ED with
m interfering packets can be expressed as
where
denotes additive noise,
is the distance between the target ED and the gateway, and
is the distance between the interfering ED and the gateway. Additionally, in (6),
denotes the normalized length of the time interval for interfering packet
m, which is expressed as
where
and
denote the arrival times of the target packet and interfering packet
m, respectively.
Lemma 2. For (7), the mean of ,, is 1/2 and the probability that the SINR of the target ED exceeds some predefined threshold value, , is Proof. Note that, although the inter-arrival times of packets are exponentially distributed with mean
, the time epochs of the Poisson packet arrivals in a fixed interval
T are uniformly distributed. Thus, for
, it is a uniformly distributed between 0 and
T, that is, the pdf of
t,
. Thus, the mean of
,
, is obtained by
By substituting (9) into (6), the SINR can be expressed as
Therefore, is (8). □
Lemma 3. When we do not consider the noise, the probability density function (pdf) of the SIR is expressed aswhere . Proof. From a high SIR approximation, (6) can be expressed as
with
. For a given
and
, the upper bound of the received SIR is expressed as
In order to obtain the pdf of
z, first let
and
. As
and
follow exponential distributions, the pdfs of
x and
y are
and
, respectively. Note that, for the sum of
m independent exponential distributions, we used an Erlang-
m, where
is the gamma function. For given
m interferences, the pdf of
is obtained as
where
denotes the cumulative distribution function of
. Next, the pdf of
is obtained as presented in (11), where we have used
. □
Lemma 4. For a given threshold and , the capture effect probability in a region i can be expressed aswhere denotes the probability that there are m interfering packets, that is, by the Poisson arrival process. Proof. In (15), we evaluate
as
which is reduced to (15). Note that we used
in (a). Further, we used
in (b). □
4. Numerical Studies
In order to characterize LoRa systems, this section presents a normalized total throughput
S and the packet capture effect probability
in (15). First, for the power threshold model, we assume that all EDs have a Rayleigh fading with unit mean, that is,
, as shown in
Section 2, to see the effect of SF on intra cell interference alone. Therefore, the important parameters that can be varied are
and
G. In what follows, we set
(dBm), whereas the noise power spectral density is −174 dBm/Hz for a bandwidth of 125 KHz. Note that, in each figure, the lines denote the analysis results while the marks indicate the simulation results.
In order to verify Equations (3) and (8),
Figure 3 shows the probability that the first packet arrives with collision
and mean length of time interval
with respect to
. To obtain
of maximizing
, we consider a solution of
. In this way, we can obtain
at
.
gets the maximum value of 0.25 at approximately 0.7. For
, we demonstrated via simulation that if the time epochs of Poisson packet arrivals at a fixed interval are uniformly distributed,
remains constant at 0.5.
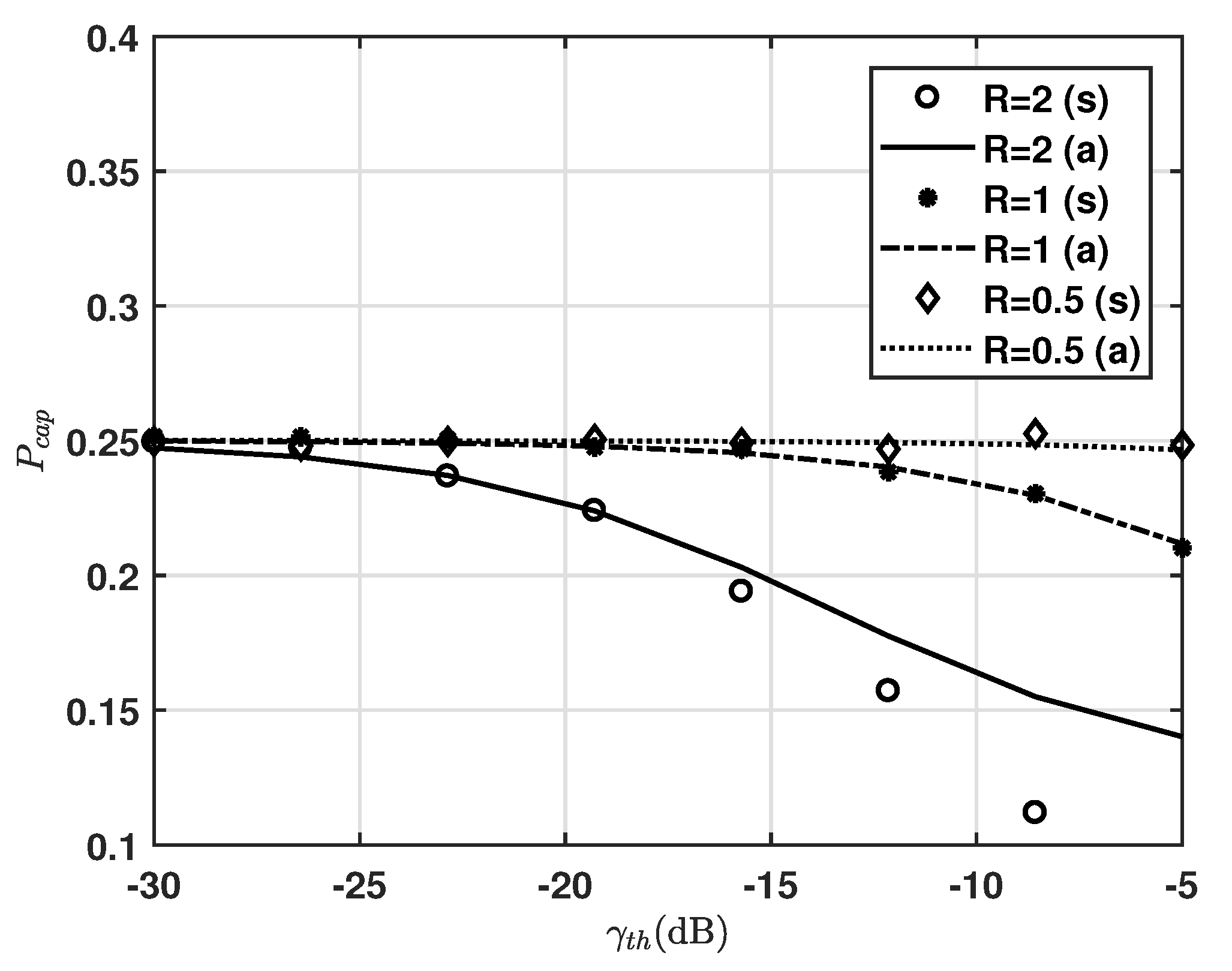
Figure 4 shows the capture effect probability for
(dB)
, where
and
. We can see that, as
increases, the capture effect diminishes. We can also see that, as
R decreases,
remains constant at 0.25 in varying
. This means that most of the first arriving packets with collision are successfully received for low
R. It is noticeable that
is quite sensitive to the ratio of the distance from target ED to the gateway and from interfering ED to the gateway. The gaps between analysis and simulations are particularly clear for
, whereas those for
and 1 still show good agreement. Such gaps come from the term whose denominator has an effect of noise, where the simulation result includes the noise effect while Equation (
15) does not, while those gaps decrease as
R decreases. Therefore, we use Equation (
15) to obtain the upper bound performance.
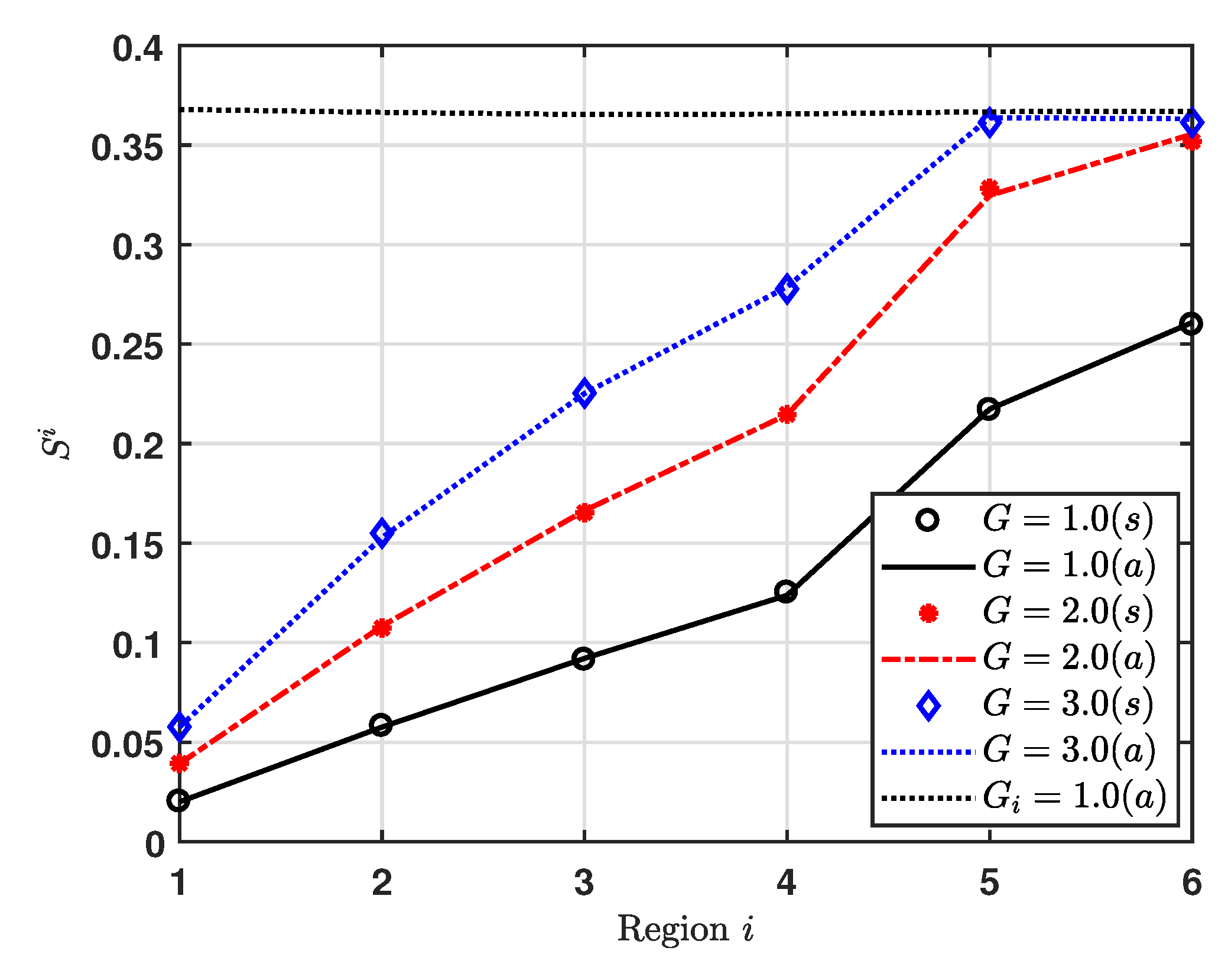
Figure 5 shows the capture effect probability for region
i, where EDs are uniformly deployed over a circular area cell for
1, 2 and 3. Additionally, we consider
for all regions, where that value makes the maximum
, as shown in
Figure 3. We can see that, for low
G, the capture effect probability increases as the index of region increases. Further, we can also see that, as
G increases,
changes. For
2 and 3, the regions to maximum capture effect probability are regions 6 and 5, respectively. It is noticeable that
is quite sensitive to not only
G but also the area of region. For example,
and
obtain about
at
and
, respectively.
Figure 6 shows the normalized throughput for region
i, at
1, 2, and 3. Additionally, we consider
for all regions, where to obtain
of maximizing
on the upper bound condition, we consider a solution of
. Then, we get
at
. As expected from the capture effect probability result, the normalized throughput increases as the index of region increases for
1 and 2. For
3, the region 5 gets the maximum normalized throughput.
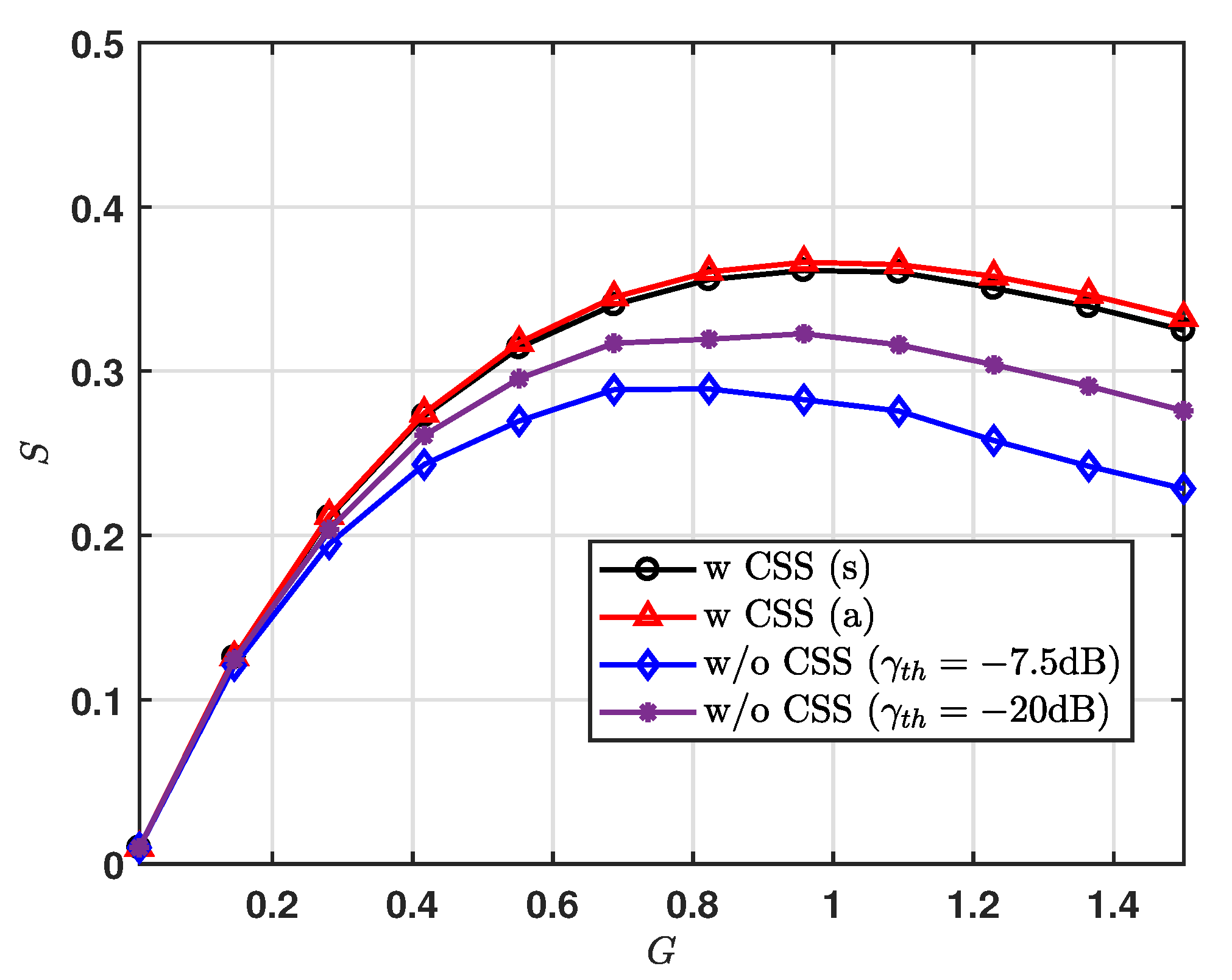
In
Figure 7, we present the normalized total throughput,
S, for varying
G. For the system without the CSS modulation scheme, we set
(dB)
and
, and obtain the results via simulation only, where the noise effect is considered for simulation results. We can see that, for the result of CSS scheme, the gaps between upper bound analysis and simulations are closed. It is noticeable that most of the first arriving packets with collisions are successfully received. Further, we can also see that the CSS scheme can achieve the increased normalized throughput for a given
G. As expected from the result of the normalized throughput for region, we observe that the LoRa system using the CSS scheme can achieve maximum
S at
1.0.