1. Introduction
Wireless Sensor Network (WSN) is widely spread through various firms such as shrewd homes, shrewd manufactory, shrewd businesses, and smart health systems such as in WHSN [
1,
2,
3,
4,
5,
6,
7]. This technology aims to reduce the patient’s need to go to the hospital for checkups and allow the doctors to monitor the patients’ health status from a remotely far location at any time. In the latest years, the adaptability of WHSN consists of small sizes, lower power, cheap sensors, and enables the communication among them to occur in a short-range [
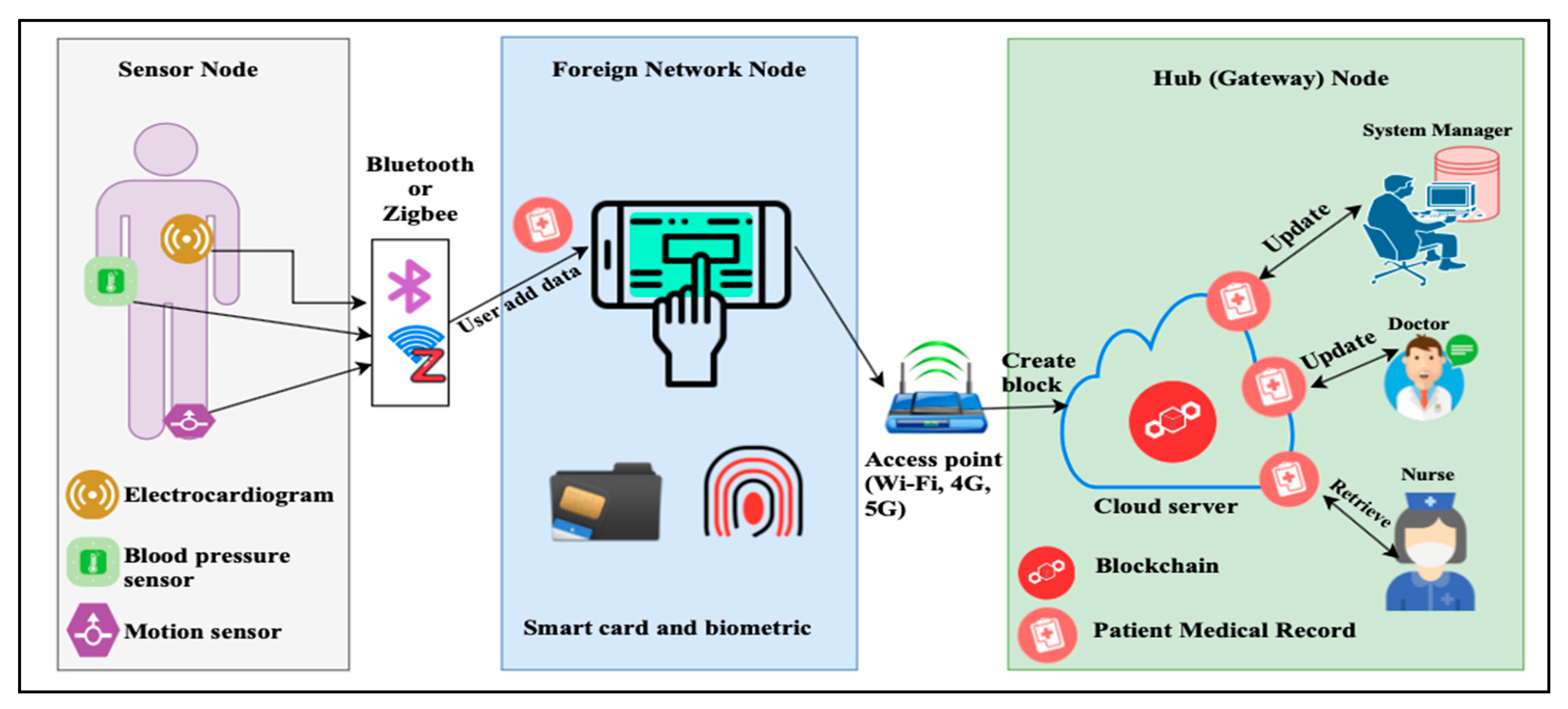
8]. Those sensors can be micro-controller, transceiver, memory, and battery. WHSN architecture supports sensors cooperation with each other’s to build the connected sensor network architecture and inspect the user’s health [
9], as depicted in
Figure 1.
The data collected by the sensor are saved for long time to increase its quality and to make better processing and analysis for better treatment choices [
10]. Also, WHSN architecture consists of weak sensors that infringe the privacy of the patient data. Many authentication schemes were proposed to solve this issue along with many others such as anonymity, eavesdropping, DoS (Denial of Service Attack), and nodes impersonation attack [
11]. After thorough analysis for the proposed schemes, we found that each has its strengths and weaknesses.
Recently, Yu and Park [
12] proposed three-factor authentication scheme (SLUA-WSN) for WSN network smart homes to enable the user of authenticating themselves in a secure manner. They claimed that their scheme is protected against impersonation, stolen integrated circuit card, and guessing attacks, and provides user-anonymity with un-traceability. However, we identified a lack of smart card data protection that leads to node impersonation and guessing in cases where stolen smart card attack occurred. Also, issues in anonymity and un-traceability arise, when all the previously mentioned acts are committed by the intruder
. Their scheme can be improved regarding computation and communication costs on both the foreign network side and gateway side too. Therefore, we propose a robust authentication scheme based on three-factor for WHSN higher performance and capacity efficiency besides advanced security to overcome the weaknesses in [
12] scheme.
1.1. Contribution and Motivation
In continuation to the development of the WHSN authentication scheme that is proposed in our previous research [
13]. We considered that the sensor node data is secure, and we proposed a secure authentication scheme between the foreign network node and the hub node. The main contributions of this article are as follows:
Performing cryptanalysis of Yu and Park [
12] scheme and show its vulnerability regarding anonymity protection, un-traceability protection, impersonation, guessing, and stolen smart card attacks.
Proposing a lightweight three-factor authentication and re-authentication schemes consist of the biometric, smart card, and password with better key management, and less operations to increase the scheme efficiency. Also, introducing additional mechanisms such as secure node addition, secure user revocation, and data transmission via blockchain.
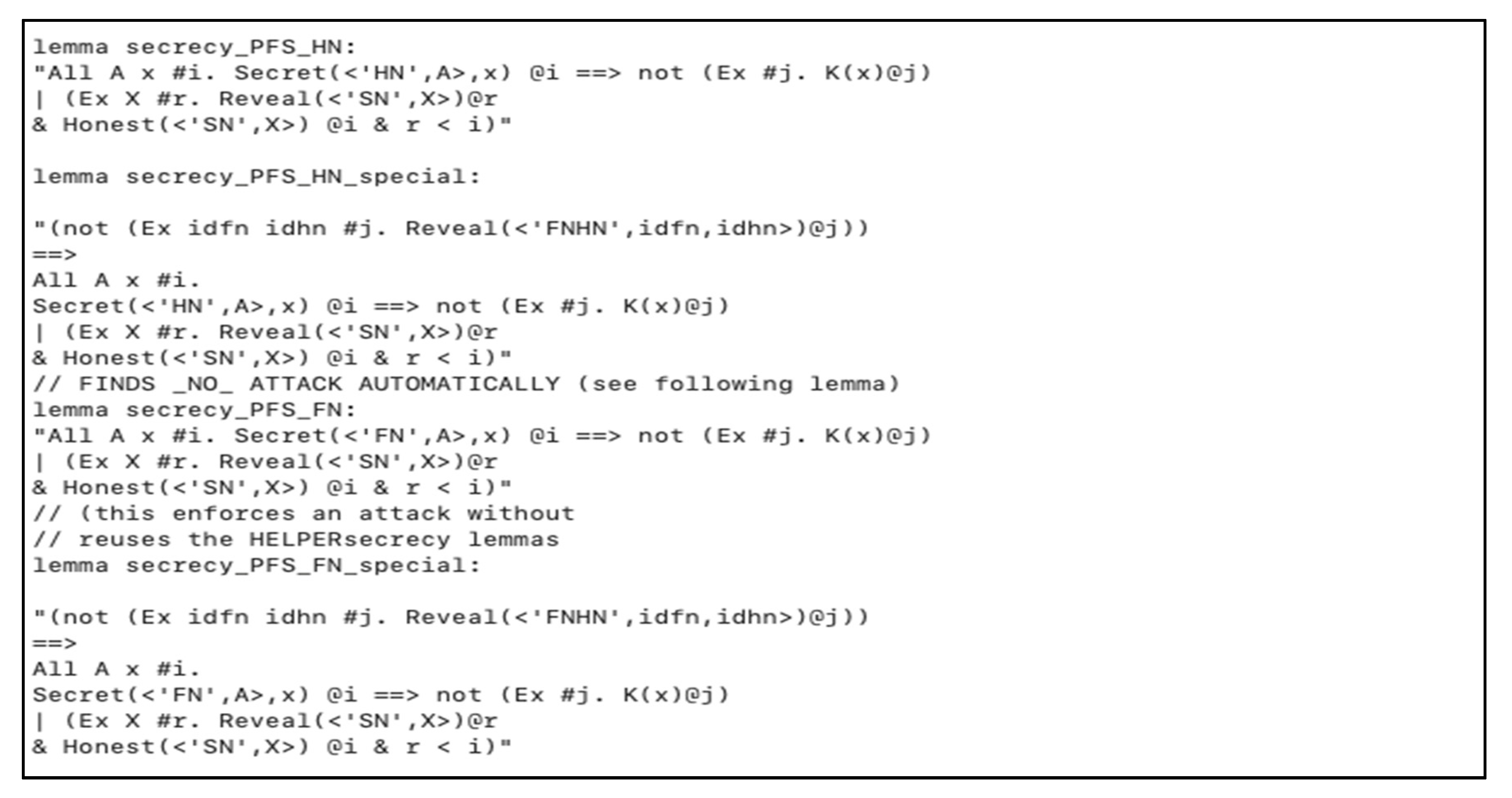
Validate the scheme BAN logic, and Tamarin simulation tool to prove its authentication, key agreement, and security. The results validated the scheme security versus replay, and session hijacking attacks, plus it achieved perfect forward secrecy along with authentication and key agreement.
Calculate the efficiency of the new scheme with computation in line with communication costs and storage. It showed an advantage of our scheme over [
12] structure regarding computation cost, communication cost, and storage capacity.
The motivations of our work are described below:
The noticeable drawbacks in most of WHSN structures, and their weaknesses towards most well-known attacks such as impersonation, session hijacking, and stolen smartcard attacks.
Designing authentication scheme needs to achieve system scalability along with security.
WHSN authentication schemes must provide appropriate complexity algorithm in conjunction the system capabilities along with capacity.
Accordingly, we proposed a lightweight authentication scheme to enhance the security and solve the performance deficiencies in [
12]. The newly proposed scheme will provide more security with less hash functions and high parameters confusion. It is secure against offline/online shared secret guessing, brute force, replay, impersonation, eavesdropping, collision, and jamming attacks. Also, it provides numerous security features such as anonymity, integrity, un-traceability, key agreement, and mutual authentication. Likewise, the scheme is appropriate for WHSN constraint system due to its efficiency in comparison to other authentication schemes.
1.2. Organization
The remaining of this article is structured as follows. We present the state-of-art for WSN architecture in
Section 2 and explain the preliminaries in
Section 3.
Section 4 analyzes Yu and Park’s structure, and
Section 5 illustrates a protected and efficient authentication schemes for WHSN architecture to improve the downfalls of Yu and Park’s scheme.
Section 6 assesses the security evaluation of the new scheme by executing informal and formal analysis containing BAN logic along with Tamarin simulation.
Section 7 shows the outcomes of the efficiency analysis of the new scheme in comparison with the associated schemes. Finally, the conclusion is discussed in
Section 8.
2. Related Works
In recent years, numerous access control and authentication systems were suggested to secure the data in WHSN technology. Some schemes are non-cryptographic based schemes that rely on the physiological signal, channel-based schemes that rely on special software or sensor, and cryptographic based schemes which are more popular [
14].
Chang et al. and Park et al. [
15,
16] had offered an authentication structure between the user node and the gateway node and utilized a honeyword checker for the password security. Also, their scheme used random number generator from the Elliptic curve along with a hash function right before sending the authentication request. Consequently, C. Wang et al. [
17] had cryptanalyzed both schemes and exposed their lack of anonymity along with their vulnerability to known session-specific temporary information (KSSTI), and privileged-user attacks. Therefore, ref. [
17] suggested an improved anonymity three-factor authentication scheme utilizing an Elliptic curve cryptosystem (ECC). The structure relied on the biometric fuzzy extractor method to enhance scheme security against password guessing and identity spoofing. Unfortunately, their scheme suffered from issues in anonymity as well as backward secrecy attack when the user loses his/her smartcard, and due to some parameters lack protection.
Similarly, Challa et al. [
18] recommended an authentication system with three factors in wireless body area network (WBAN) architecture based on the pubic key and Elliptic curve structure to create a secure system. They declared that their system is strong versus several types of attacks such as insider attack, password cracking, stolen smart-card, denial-of-service, known session key, masquerading, session hijacking, and replay attacks. However, their scheme lacked anonymity of the user and sensor identities. Also, the weak protection to the public key by the user phone and temporary identity made the scheme weak toward anonymity and guessing attack due to the exposure of random parameters in the open channel.
Mo and Chen [
19] had analyzed the security flaws in the proposed three-factor scheme in WSN by Lu et al. [
20] and found that their structure is suspectable to offline password cracking, known session-specific temporary information attacks, and lack of session key backward secrecy. Therefore, ref. [
19] had offered a three-factor authentication structure utilized user biometric, smart card and key where they used hash function and Elliptic curve (ECC) to protect the passwords and security parameters. But the issue is the user anonymity might be compromised because the user identity is only protected by random number and biometric which both might be easily guessed and spoofed by the intruder
.
To deal with the sensitivity of data issues, Garg et al. [
21] proposed a system using the Elliptic curve, signatures, and blockchain for WHSN to protect the transmitted data in an insecure channel and provide anonymity. Their scheme included the identity of the trusted authority as an additional secure parameter to authenticate between the communicated nodes. Although that their scheme deployed a great combination of cryptographic and emerging technologies to protect the data, it might face DoS attack and communication delay between the nodes, because of the heavy computation along with high storage cost. Ali et al. [
22] had cryptanalyzed Liu and Chung [
23] scheme and found out that it is unguarded to lost smart-card, offline key cracking, insider, and masquerading attacks. Moreover, ref. [
22] had analyzed [
18]’s approach, and found that it has correctness issues, broadcasting problems, lack of authentication between the trusted authority and sensor nodes, replay attack, Denial of Service (DoS), and forgery attacks.
Therefore, Ali et al. [
22] had suggested a secure and lightweight three-factor authentication process for WHSN which employed both ECC, and bilinear pairing to resolve the issues in [
18,
23] schemes. Although their scheme is guarded against impersonation, privileged-insider, offline password cracking, stolen smart-card, and replay attacks, but it still has high computation cost and delays in communication due to extensive cryptographic operations.
One of the significant issues that faces the IoT authentication structures is jamming attack, when the intruder
sends jamming signal during the update of authentication values, and parameters [
24]. In this context, two authentication schemes proposed by Shen et al. and Tewari et al. [
25,
26] that employed simple operations such as hash, XOR, and random number generators. Their schemes focused on time duration of the session, mutual random number generation, and keeping the latest identities of the communicating entities to increase the protection against jamming attacks.
Recently, Yu and Park [
12] proposed SLUA-WSN which is a lightweight three-factor authentication scheme with secure user authentication system. Their scheme has the best in efficiency of all the previous schemes in the state-of-art, and the best robustness against sensor node capture, replay attack, insider attack, and impersonation attack, also it guarantees un-traceability and mutual authentication. Thus, SLUA-WSN is appropriate for applied WHSN environments because it is the strongest and efficient than related schemes. Their scheme suffers from stolen smart cards and shared secret key guessing because of the number of stored parameters in the smartcard. Secondly, there is no mechanism to check the validity of the generated random number at the first communication session between FN and GW. There must be a validation method to check whether the user generated the accepted random number that is generated before or not in case of mobile lost/smart card lost attacks.
5. Proposed Protocol
We explain our suggested authentication scheme assuming that our sensor node is trusted node and we want to secure the communication between the hub node and foreign network node. As the foreign network node works as a data collector for the sensor node and ensures the security of the transmitted parameters to the hub node. The scheme ensures strong authentication between FN-HN due to its three-factor authentication nature, and complex parametric system. In the below explanation, we showed the system five phases such as FN pre-deployment and registration, FN-HN authentication, re-authentication, safe node addition, user revocation, and secure data transmission via blockchain. Refer to
Table 2 below for the notations.
5.1. Initialization Stage
In this stage, the parameter generation and registration of this protocol engaged the SM to choose secret identities, parameters and keys and allow all the entities to share securely the generated arguments over an offline and secure channel to SN, FN, and HN:
The SM stores the , , and in the SM memory.
SM chooses secret key , and as a secret parameter to be added to the node’s keys for the confusion.
SM computes the secret key between the parameters
SM calculates a new shadow identity for all the communicated nodes to ensure their anonymity during the communication and transmits those identities over a secure channel.
HN communicates with
SN to generate secret parameters in a secure channel to authenticate each other during the communication.
SN saves the newly generated secret parameter in a secure location.
HN communicates with
FN to generate secret parameters in a secure channel to authenticate each other during the communication.
FN keeps the new produced secret parameter in a secure location to enable the user from registering securely in the WHSN authentication system.
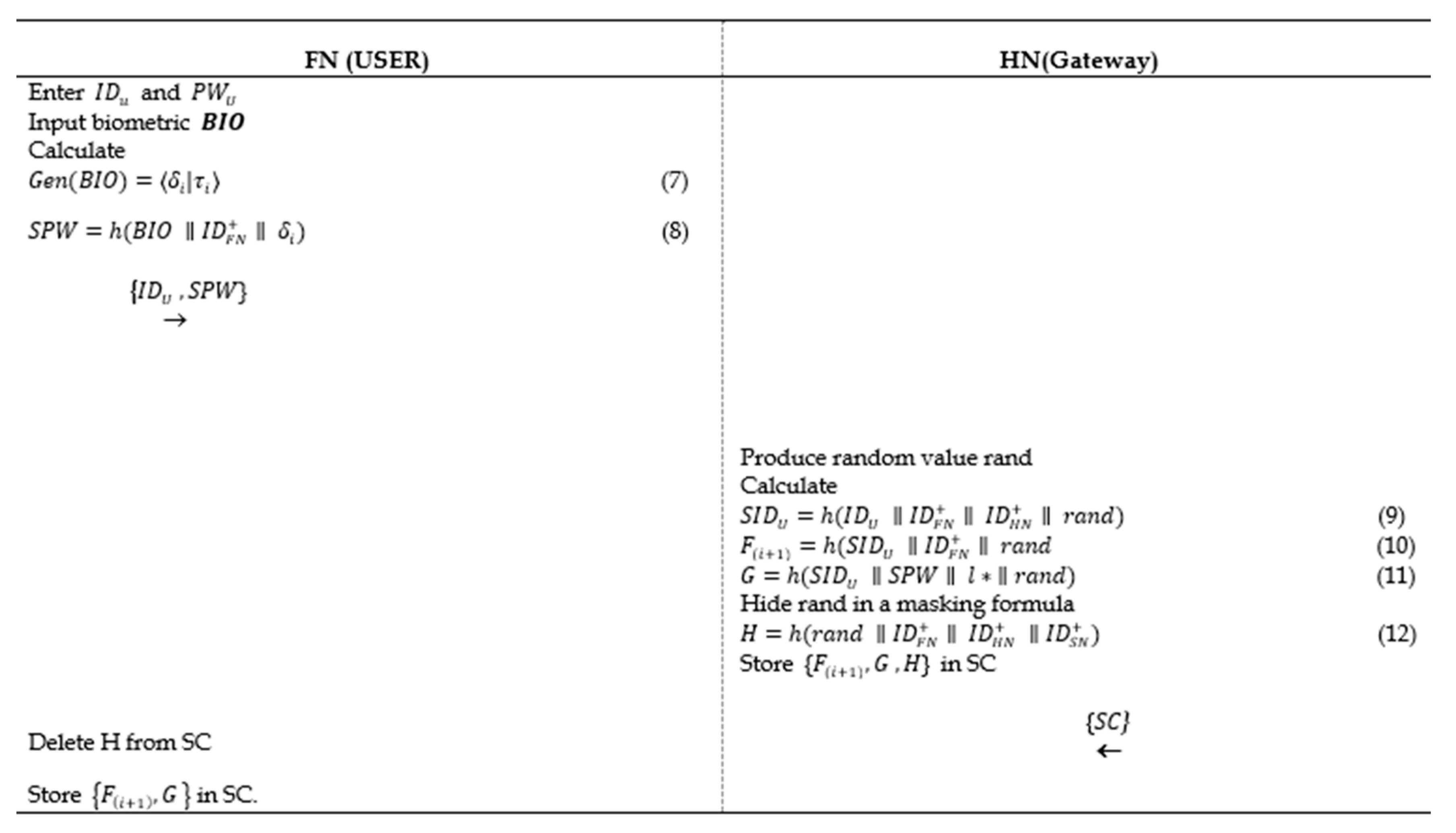
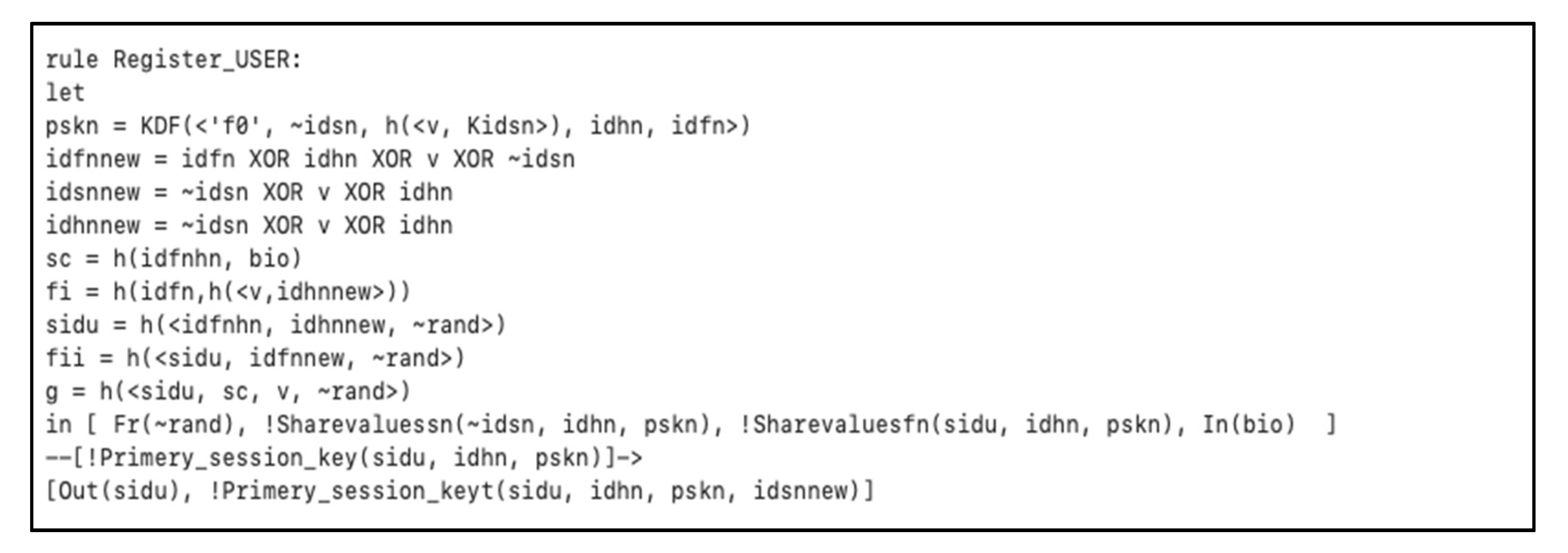
5.2. Registration Phase
In this phase, the client uses his/her smartphone to enter the password, identity, and biometric to allow the HN from generating an authentication smart card securely:
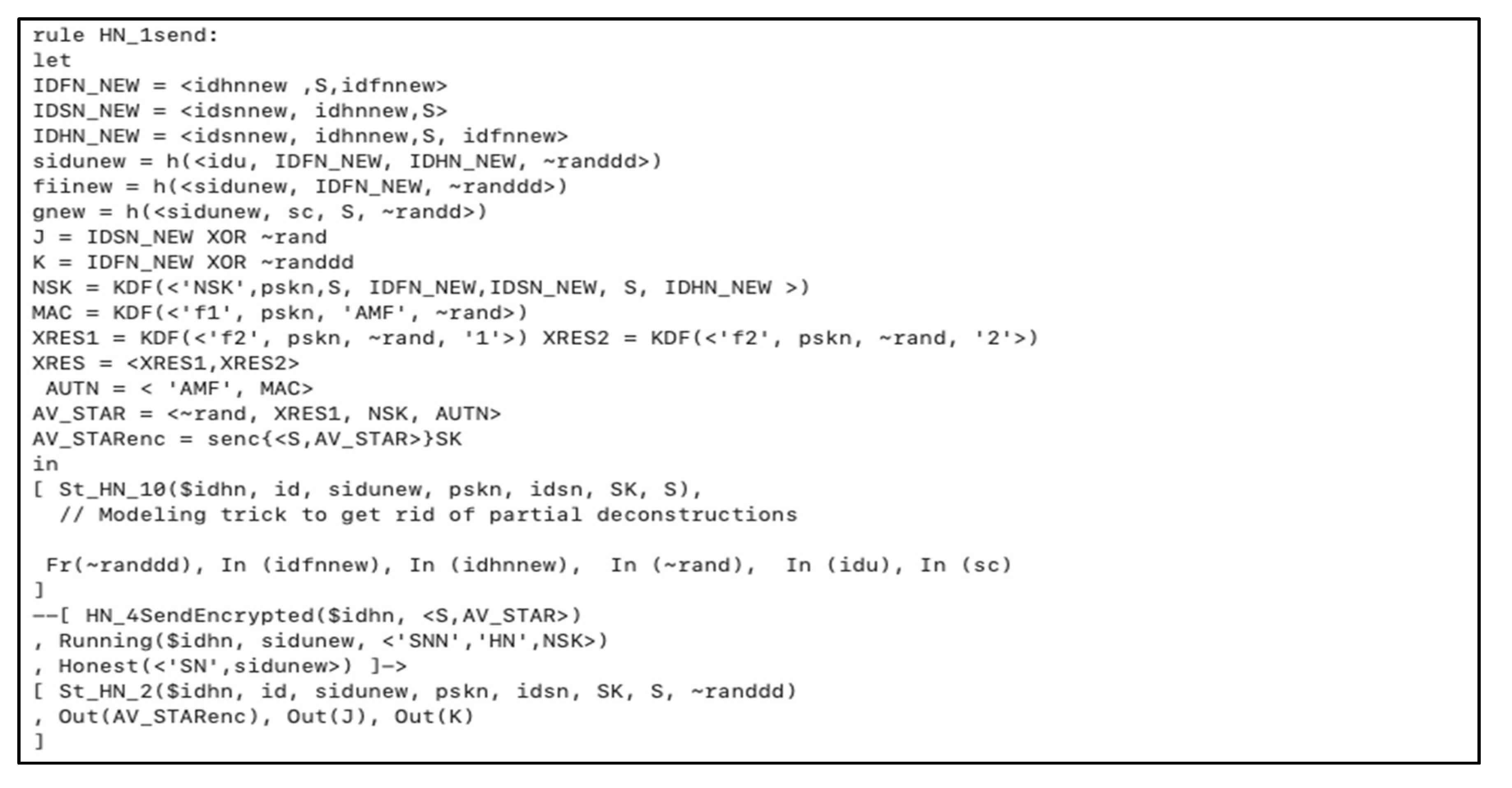
5.3. P-I: Authentication Phase
In this section, we assumed that the
SN is a trusted node and
FN authenticates itself and
SN to the
HN. Furthermore, it encompasses four phases of communications including
FN,
HN, and
SN depicted in the
Figure 3 below and denoted as follows:
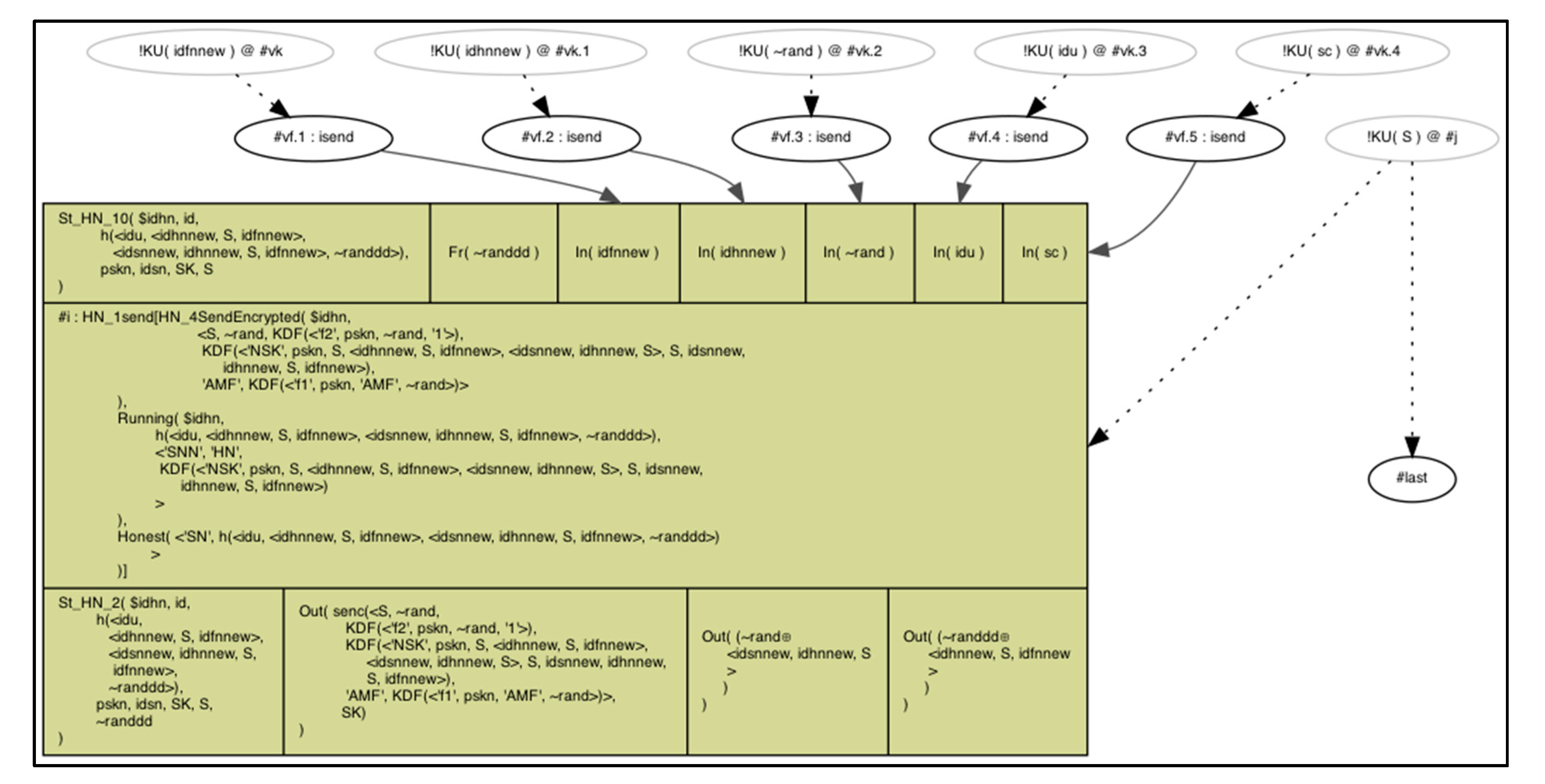
Step 1:
The user inserts the smart card, enters his/her , , imprints the biometric , and calculates from Formula (7) and from Formula (8). Also, computes from Formula (11).
FN checks whether
, then continue, else abort the session.
FN generates a new timestamp
random value
and calculates the following:
The previous step is very important to prevent jamming attack in any communication session. It allows both FN and HN to be part of generating random numbers that supports the session key formation.
FN sends the parameters to the HN in the open channel .
Step 2:
HN performs the following:
Verify the time to prevent a replay attack.
If then continue, else terminate the process.
Calculate from Formula (10).
Check if to validate the user identity and remain, else terminate the process.
HN should keep track of each used random number in the scheme to avoid replay attack or impersonation attacks.
Calculate , from Formula (13) and check if the has been used before, if it is not continue to extract , and check if the to authenticate the sensor node.
Calculate from Formula (6) to authenticate the FN.
from Formula (14) to validate the shared secret key.
After authenticating the SN and FN, HN generates new random nonce , new timestamp and calculates the following
Deduce from Formula (2), from Formula (3), from Formula (4).
Calculate Formula (1)
Compute Formula (9) and update from Formula (10), from Formula (11). The above formulas ensure our scheme robustness towards jamming attack, due to the usage of old identities and keys in the generation of the new system parameters.
Create security parameters to hide the new values:
HN sends the parameters to the FN in the open channel .
Step 3:FN → SN (M3 = {J, K, })
FN performs the following:
Verify the time to prevent a replay attack.
If then proceed, else halt the connection.
Upon receiving the parameters FN calculates the following:
Deduce from Formula (15), from Formula (2), from Formula (3), from Formula (4) .
Replace from Formula (10), from Formula (11), and add the new parameters to the SC {.
FN sends the parameters to the SN in the open channel .
Step 4: → SN (M4 = {K})
Upon receiving the parameters SN calculates the following:
Verify the time to prevent a replay attack.
If then proceed, else terminate the session.
Deduce from Formula (2), from Formula (3), from Formula (4).
, then replace Formula (1). Save the new parameters in the SN memory and establish the new session key.
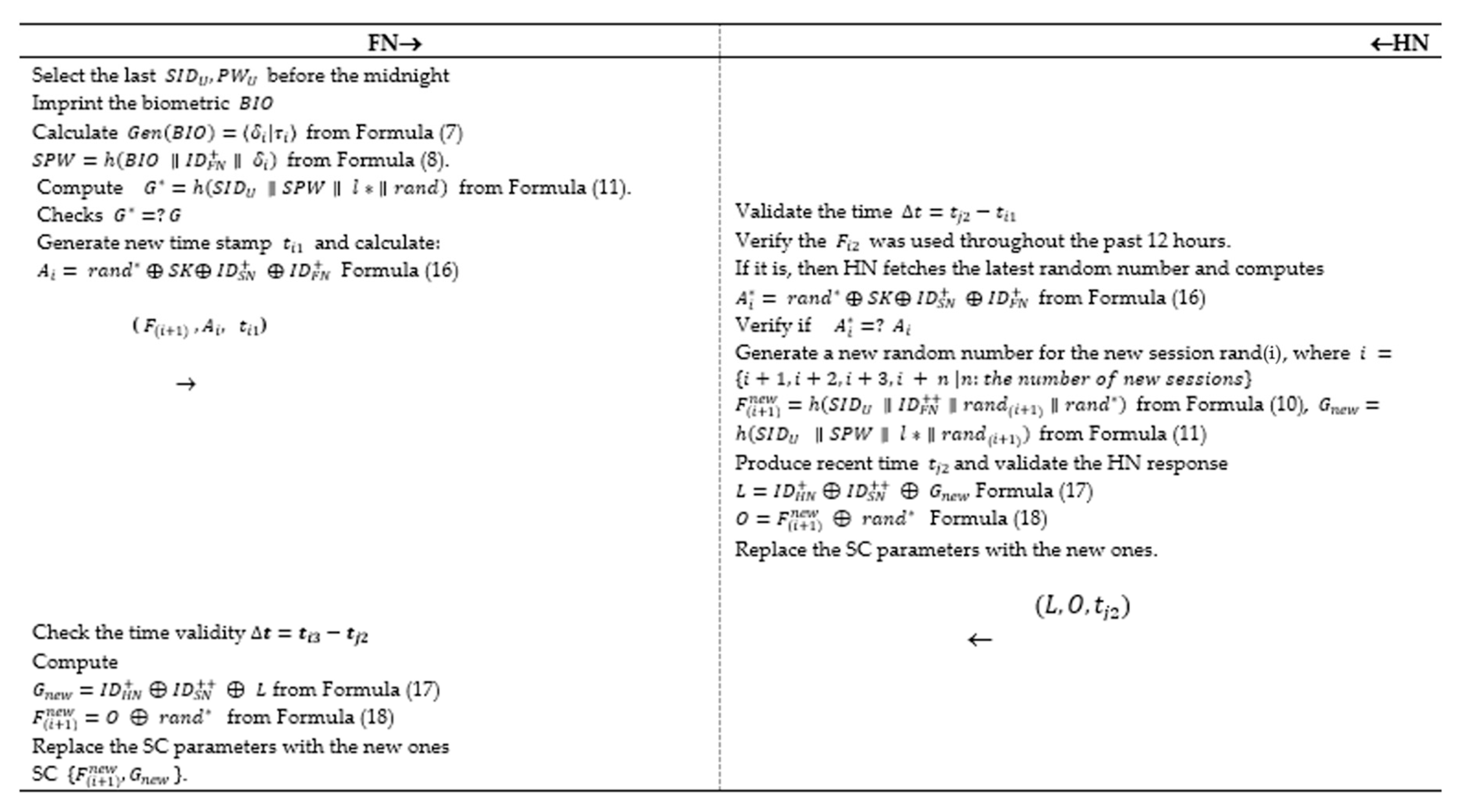
5.4. P-II: Re-Authentication Phase
After an effective authentication session, the user is qualified to approach the system services. The authentic client might want to reach to some facilities throughout the day before night-time. Furthermore, it is timewasting, and un-efficient to compute all the values of the updated authentication session for the verified client. Hence, it necessitates the concept of re-authentication to improve the scheme efficiency, as shown in
Figure 4. The stages of the re-authentication are as follows:
The user enters to his/her account to approach some data from the smartphone.
Step 1:FN → HN (M1 = ())
The FN calls the last before the night-time to confirm the FN to the GW.
Imprint the biometric
Calculate from Formula (7) and in Formula (8).
Compute from Formula (11).
Check if no abort, and if yes continue.
Generate new time stamp
and calculate
Send the following parameters {} to the HN for authentication.
Step 2:HN → FN (M3 = {})
Verify the time , to prevent replay attack.
If then remain, else cancel the session.
HN checks if was generated throughout the past 12 h.
If yes, then HN gets the newest random nonce and computes the fresh key from Formula (16).
Check if if equal, then proceed.
Produce a new random nonce for the new connection rand (i), where , then compute the following to replace the SC old parameters with the new ones: from Formula (10), from Formula (11).
Produce recent time
and confirm the
HN response.
Change the tuple values with the new ones , and save them to the SC.
Send the following parameters { to FN.
Step 3: → FN (M4 = {})
Check the time validity . If then proceed, else halt the connection.
Compute the following from Formula (17), from Formula (18).
Change the parameters with the fresh ones , and save them to the SC.
A protected connection can be initiated between FN and GW.
5.5. Secure Node Addition
SM adds new nodes to the system and performs the following:
Step 1: User sends a request to add new .
The client needs to normally log into the session with his/her credentials, inserts SC, enters and , imprints the biometric , and generates time stamp
Step 2: SM receives the request of the user to create new .
SM checks the time validity .
If then proceed, else halt the session.
SM opens the message to generate the new identity for the sensor and calculates from Formula (2) and make a new secret parameter from Formula (5).
The newly generated values are shared securely with the user and saved into the device’s memories.
SM broadcast the new identity to all the communicating nodes for future access.
5.6. Secure User Revocation
In the below steps, SM revokes the user card from the system to add new one and performs the following:
Step 1: The user sends a request to remove his/her previous card and adds a new to the system.
The user needs to normally log in to the session with his/her credentials, inserts SC, enters , , imprints the biometric , and generates time stamp
Step 2: SM receives the user request to revoke from the system.
SM checks the time validity .
If then continue, else abort the session.
SM checks the secret parameters and the request of the user via from Formula (5).
Send a secure link to the user to open, add his/her new , , and .
The user sends the new parameter securely over the secure one-time link to the SM.
SM receives the request, generates new random value
, and computes the following:
Add the new values to the smart card .
User receives the new smart card , replaces the new parameters , and retrieves the random number from , then deletes it from the new smart card in a secure channel. The new set of parameters will be .
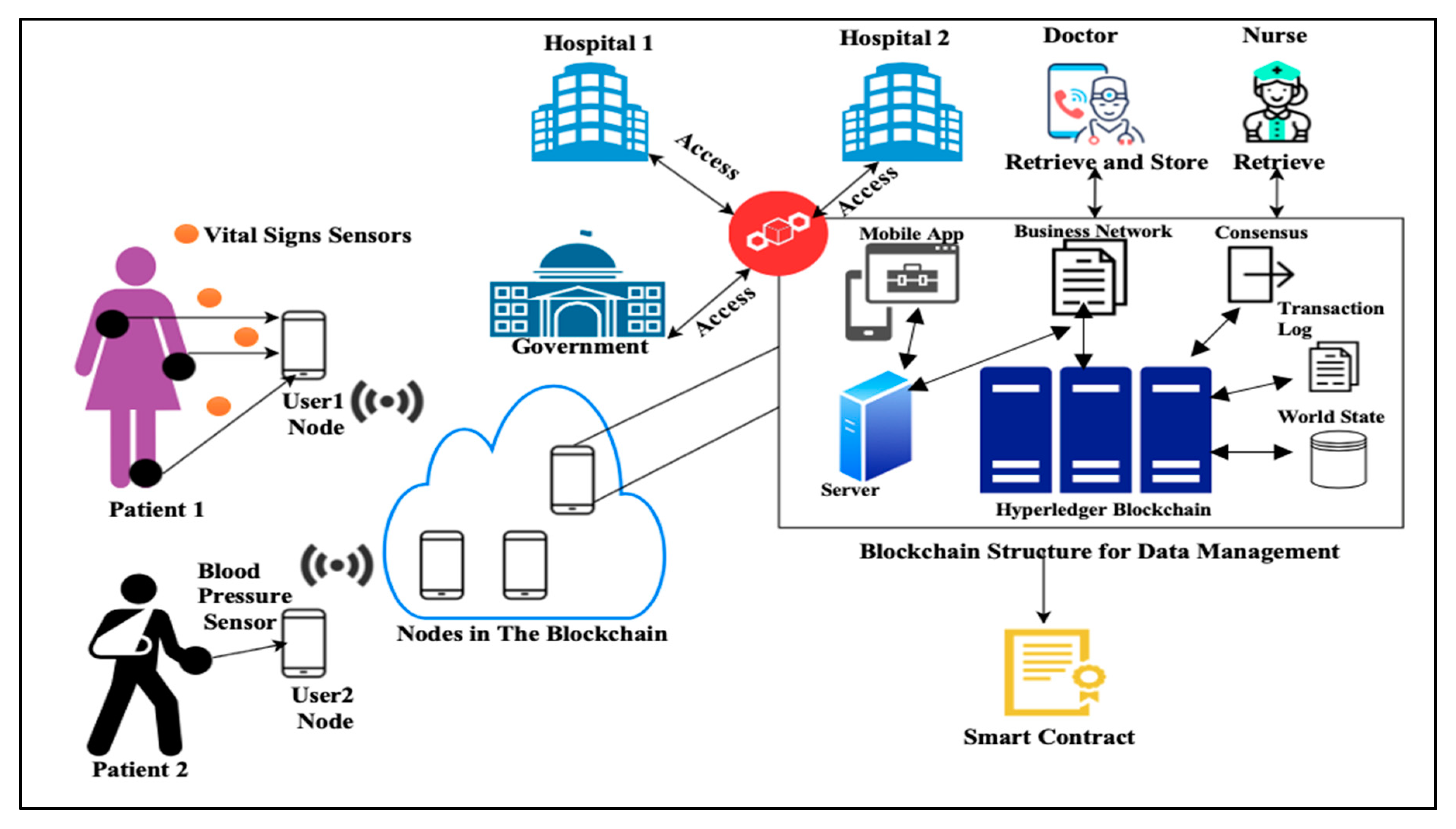
5.7. Secure Data Transmission via Blockchain
In [
12] scheme, there is no defined strategy to protect the stored data for retrieval or other usages after successful authentication. Since most of the WHSN structures are based on main centralized data storage that is accessible by the assigned doctor. So, this could put patient information in danger due to this source of error. Whereas the blockchain adds-up the data to blocks and splits them. Therefore, the integrity of the data is kept, each transaction is encrypted. Access control policies guarantee privacy [
31]. Several methods were proposed to aid the purpose smart contract establishing along with patient identity tracking. In the case of government authorities who want to evaluate a medical facility service or measure the spread of a disease, the authorities need to have access to all the citizens’ information.
We adopted [
32] method who proposed a Hyperledger blockchain which supports consensus algorithms that only permit the authenticated patients, and communications, and only accept reserved as well as confidential transactions. The Hyperledger blockchain consists of the transaction log that tackles all the changes made to the connections and changes the value of the world state. The blocks are built by a collection of transactions sent to the evaluator peer to simulate it, vote on it, and approve it. The structure of communication, electronic contracts, access policies are stored in the business network that the user can interact with from a mobile application connected to a server, where all the communication are encrypted by hashing to be able to access the blockchain for data storage and retrieval.
Another method is discussed by [
21] that utilized the blockchain technology to store the individual data safely in the cloud. The sensor nodes contain some data that needs to be stored in the gateway safely for another retrieval or processing. The sensor sends encrypted data with the shared key to the foreign network along with the current timestamp. The foreign network node checks the timeliness and decrypts the data to get the information, then encrypts the data again with its pre-shared key to be sent to the hub node. The hub node decodes the info and checks the timestamp for validity to start building a data block. The block is added to the blockchain when all the communicated entities agreed upon the block contents in peer to peer cloud server network. After successfully gathering a group of valid data, the hub node starts to build transaction values and adds them together in one block to enable the system manager to create a blockchain of data for storage, deletion, update, and retrieve. The proposed method suggested the usage of cryptographic hash to encode the transmitted blocks and compute the ‘‘Merkle tree root’’ (MR) for the tree building. MR is a technique used in cryptocurrency to assure the data integrity in a peer-to-peer network structure. All the block information such as block owner and block payload are computed with the current block hash (CBHash). The hub node embeds the hashed identity of the user and sends the block of data to the system manager which uses ‘‘Ripple Protocol Consensus Algorithm (RPCA)’’ [
33] for node verification and addition. Suppose that a user wants to access some data from a specific block, the user has to log in successfully to the connected hub node. So, as the hub node uses the user key that matches the user identity from the block, performs a hash function on data, decrypts the encrypted data to extract the hashes values and compare them with the computed hash for integrity check. Then, the hub node transmits the data to the user and the user decrypts the data with his/her key to retrieve the information from the block, as depicted in
Figure 5.
8. Conclusions
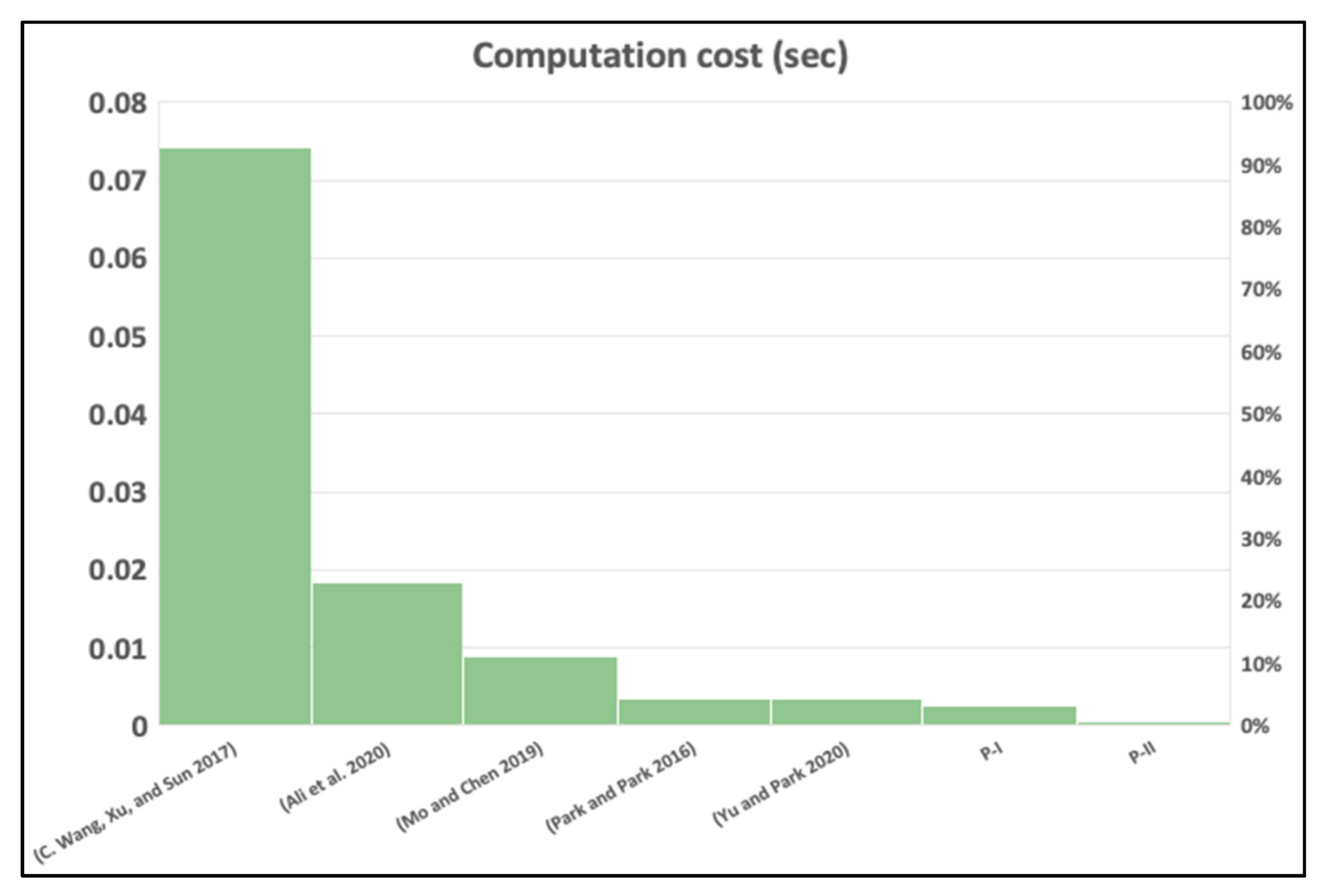
WHSN is a modern trend that deals with significant information from the patients that must be protected. It received major attention from the information security developers and vendors, who put big efforts in increasing the guardedness of the WHSN system and speed up the performance. Therefore, we analyzed the latest schemes in the field and we found that [
12] to be the most efficient and secure one. So, we cryptanalyze it and we discovered that the scheme needs enhancement to achieve both security and performance. Consequently, a three-factor authentication scheme based on the biometric, smart card, and password is proposed. The scheme was formally validated by BAN logic and simulated with Tamarin prover to confirm its security and mutual authentication. Moreover, the informal analysis proved that the above scheme achieved the suggested security requirements like, anonymity, offline/online shared secret guessing,
FN-
SN replay attack, brute force attack,
FN/
HN impersonation, integrity, session hijacking, eavesdropping attack, un-traceability, and collision attack. Finally, we conducted performance evaluation to compute our scheme efficiency and we found out that our scheme has better computation cost, communication cost, storage cost, and energy consumption than the related schemes. To conclude, the future direction of our research will employ blockchain technology in WHSN authentication in-depth and more attacks simulation in the proverif tool.