IMSC-EIoTD: Identity Management and Secure Communication for Edge IoT Devices
Abstract
1. Introduction
- A detailed analysis of the current state of identity management for the IoT
- A decentralized edge-fog based identity management architecture is proposed for edge IoT devices and gateways.
- A new authentication mechanism for IoT devices is proposed with dynamic authorization and/or access control mechanism near the edge IoT devices where access to new resources is granted, and activities are recorded with the context information.
- A new secure communication protocol is proposed for edge IoT devices and IoT gateways and it is verified using the Scyther security verification tool.
- The proposed architecture is verified and simulated using the SPIN verification tool.
2. Background and Motivation
2.1. IoT Identity Management
2.2. IoT Authentication
2.3. IoT Authorization
2.4. IoT Communication Process
2.5. IoT Data Aggregation and Processing Models
2.5.1. Centralized Data Processing Model
2.5.2. Decentralized and Distributed Data Processing Model
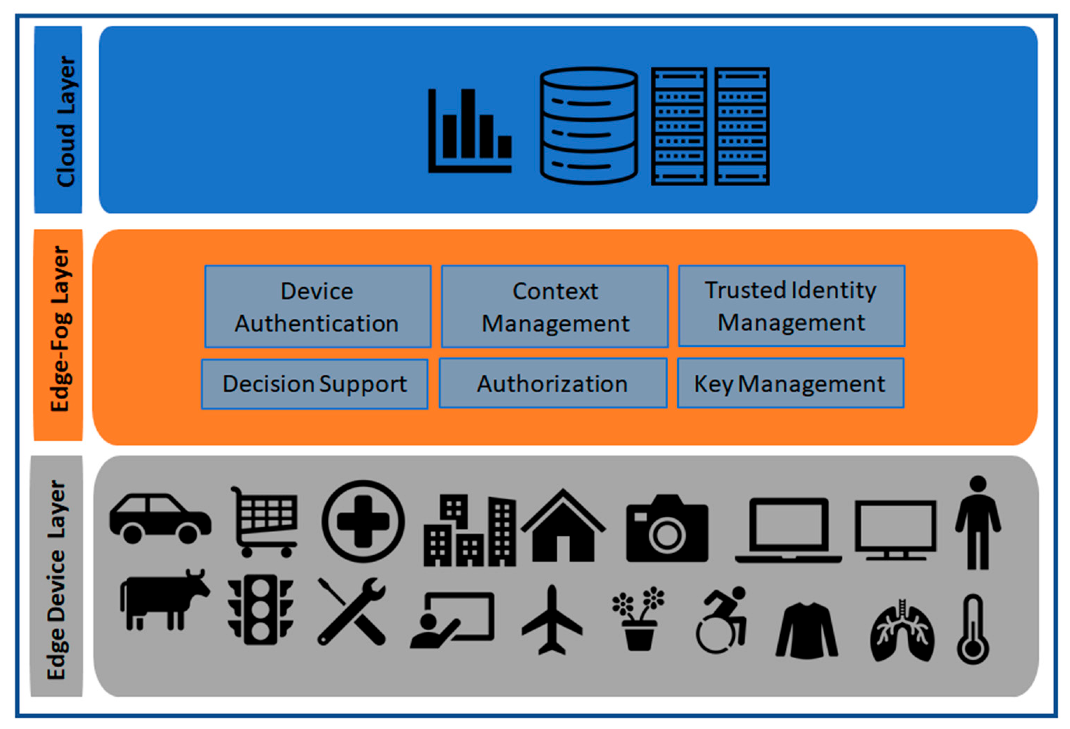
2.6. IoT Architecture
2.6.1. IoT Application Layer
2.6.2. Cloud Computing Layer
2.6.3. Fog Computing Layer
2.6.4. Edge Computing Layer
2.6.5. IoT End Device Layer
2.7. IoT Trust Management Model
3. Related Works
4. Proposed Model
4.1. IoT Identity Management Ontology
4.2. IoT Identity Management and Secure Communication Model
4.2.1. Notation of Terms
4.2.2. Assumptions
4.2.3. Decentralized and Distributed IoT Network Model
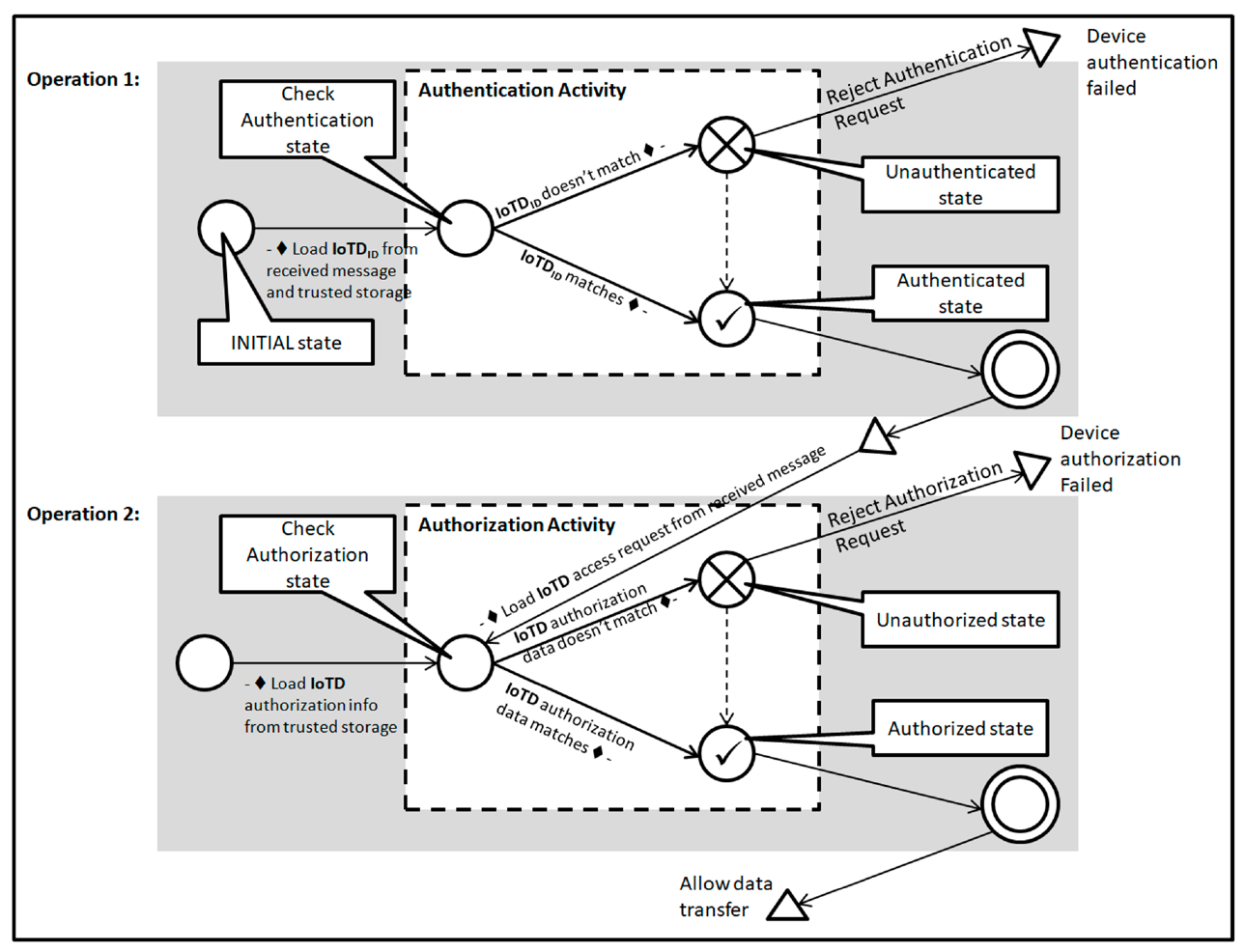
4.3. Primitive State Machine Representation of IoT Identity Management
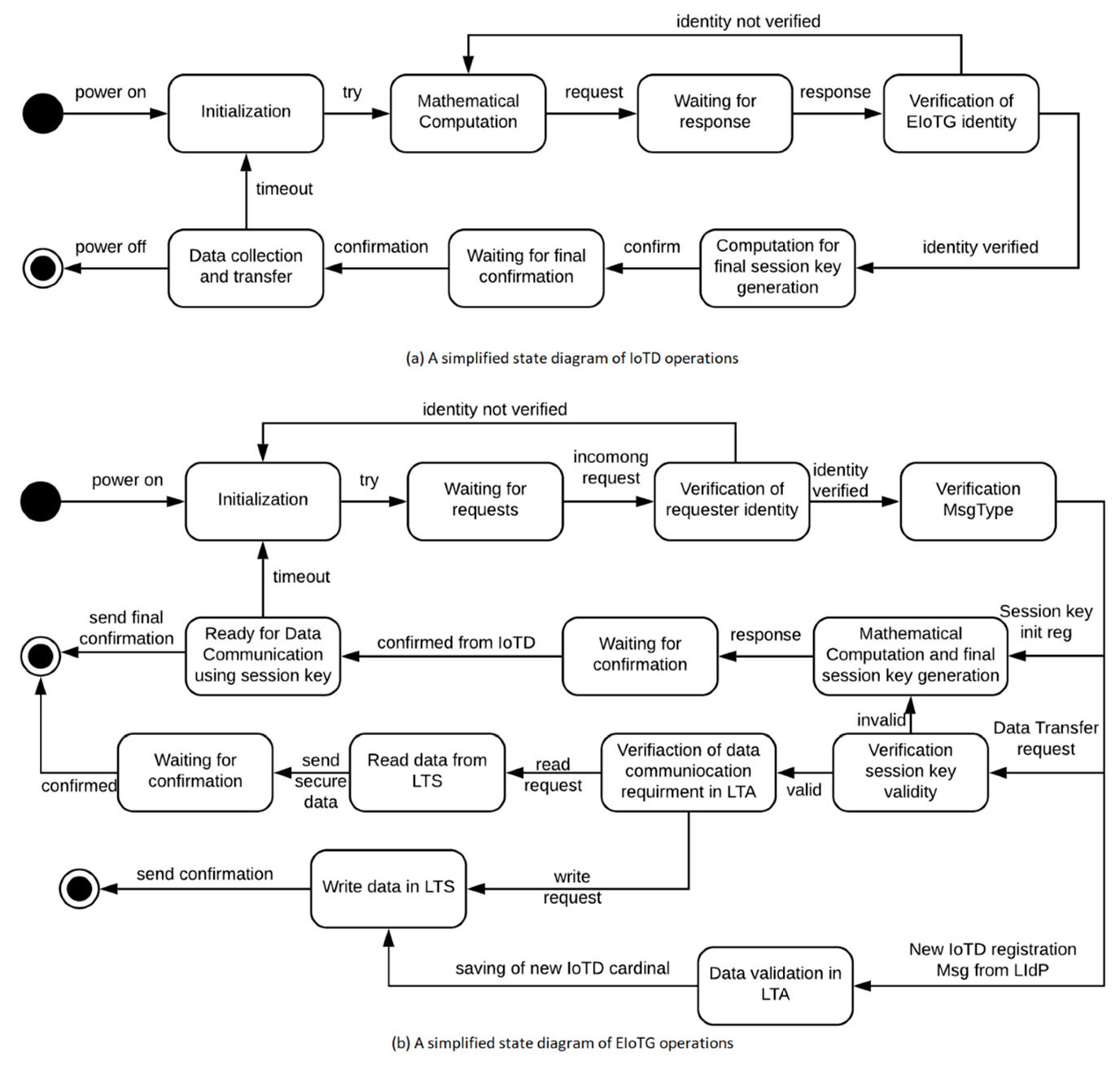
4.4. Secure Communication Protocol for IoT
5. Results and Performance Evaluation
5.1. Identity Management Model Performance
5.1.1. Security
5.1.2. Privacy
5.1.3. Trustworthiness
5.1.4. Mobility
5.1.5. Usability
5.1.6. Affordability
5.1.7. Law enforcement
5.1.8. Interoperability
5.1.9. Functionality
5.1.10. Scalability
5.1.11. Administration
5.1.12. Comparative Analysis
5.2. Informal Security Analysis
5.2.1. Mutual Authentication
5.2.2. Confidentiality
5.2.3. Integrity
5.2.4. Availability
5.2.5. Reply Attack
5.2.6. Denial of Service (DoS) Attack
5.2.7. Man-In-The-Middle Attack
5.2.8. Physical Attack
5.2.9. Impersonation Attack
5.2.10. Forward and Backward Secrecy
5.3. Formal Security Analysis
5.3.1. Scenario Description
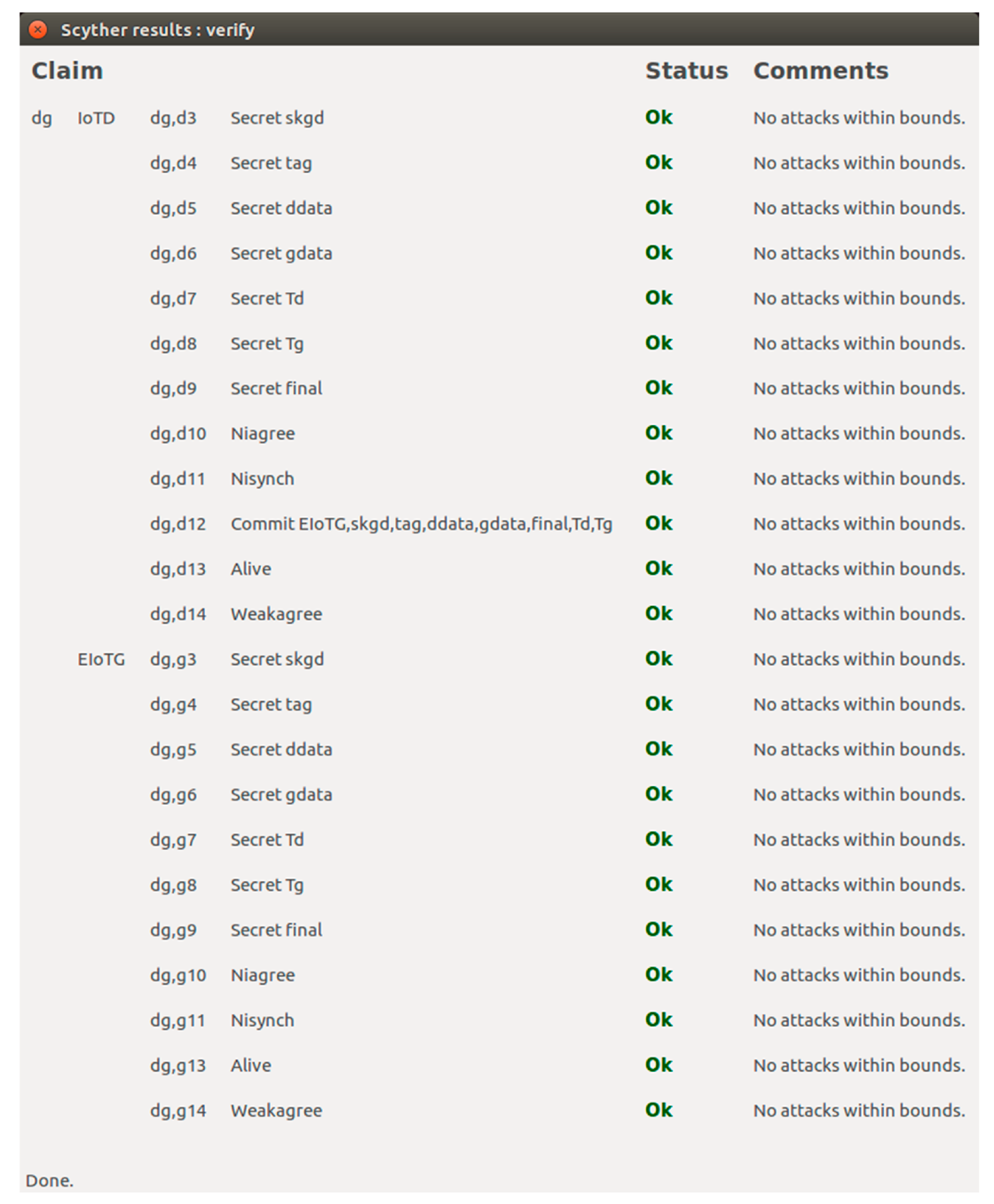
5.3.2. Scyther Simulation Results
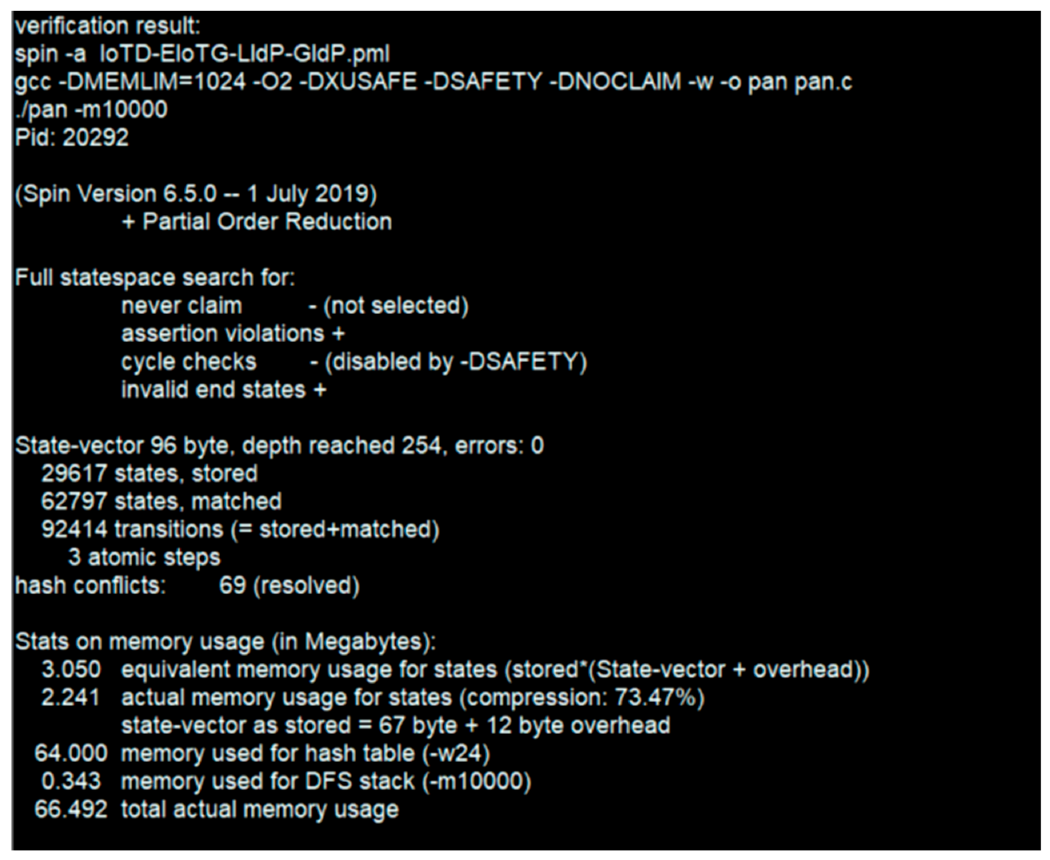
5.4. Verification of Proposed Model
6. Discussion
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Sadique, K.M.; Rahmani, R.; Johannesson, P. Towards Security on Internet of Things: Applications and Challenges in Technology. Procedia Comput. Sci. 2018, 141, 199–206. [Google Scholar] [CrossRef]
- Miorandi, D.; Sicari, S.; De Pellegrini, F.; Chlamtac, I. Internet of Things: Vision, application areas and research challenges. In Proceedings of the International Conference on IoT Society Mobile, Analytics and Cloud, I-SMAC 2017, Palladam, India, 10–11 February 2017; Volume 10, pp. 583–587. [Google Scholar] [CrossRef]
- Macedo, E.L.C.; De Oliveira, E.A.R.; Silva, F.H.; Mello, R.R.; Franca, F.M.G.; Delicato, F.C.; De Rezende, J.F.; De Moraes, L.F.M. On the security aspects of Internet of Things: A systematic literature review. J. Commun. Netw. 2019, 21, 444–457. [Google Scholar] [CrossRef]
- Bandyopadhyay, D.; Sen, J. Internet of things: Applications and challenges in technology and standardization. Wirel. Pers. Commun. 2011, 58, 49–69. [Google Scholar] [CrossRef]
- Ray, P.P. A survey on Internet of Things architectures. J. King Saud Univ. Comput. Inf. Sci. 2018, 30, 291–319. [Google Scholar] [CrossRef]
- Restuccia, F.; D’Oro, S.; Melodia, T. Securing the Internet of Things: New Perspectives and Research Challenges. IEEE Internet Things J. 2018, 1, 1–16. [Google Scholar]
- Kouicem, D.E.; Bouabdallah, A.; Lakhlef, H.; Kouicem, D.E.; Bouabdallah, A.; Lakhlef, H. Internet of things security: A top-down survey. Comput. Netw. 2018, 141, 199–221. [Google Scholar] [CrossRef]
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A Survey on Internet of Things: Architecture, Enabling Technologies, Security and Privacy, and Applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Sadique, K.M.; Rahmani, R.; Johannesson, P. Fog Computing for Trust in the Internet of Things (IoT): A Systematic Literature Review. In Proceedings of the 2020 International Conference on Computer Science, Engineering and Applications, Gunupur, India, 13–14 March 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Keoh, S.L.; Kumar, S.S.; Tschofenig, H. Securing the internet of things: A standardization perspective. IEEE Internet Things J. 2014, 1, 265–275. [Google Scholar] [CrossRef]
- Al-fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar]
- Sadique, K.M.; Rahmani, R.; Johannesson, P. Identity Management in Internet of Things: A Software-Defined Networking Approach; Springer: Singapore, 2020; Volume 602, ISBN 978-981-15-0828-8. [Google Scholar]
- Zhang, Z.K.; Cho, M.C.Y.; Wang, C.W.; Hsu, C.W.; Chen, C.K.; Shieh, S. IoT security: Ongoing challenges and research opportunities. In Proceedings of the 2014 IEEE 7th International Conference on Service-Oriented Computing and Applications, Matsue, Japan, 17–19 November 2014; pp. 230–234. [Google Scholar] [CrossRef]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A Survey on Security and Privacy Issues in Internet-of-Things. IEEE Internet Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Ezema, E.; Abdullah, A.; Mohd, N.F.B. Open Issues and Security Challenges of Data Communication Channels in Distributed Internet of Things (IoT): A Survey. Circ. Comput. Sci. 2018, 3, 22–32. [Google Scholar] [CrossRef][Green Version]
- Hokeun Kim, E.A.L. Authentication and Authorization for the Internet of Things. IEEE Comput. Soc. 2017, 17, 27–33. [Google Scholar] [CrossRef]
- Kim, H.; Kang, E.; Lee, E.A.; Broman, D. A Toolkit for Construction of Authorization Service Infrastructure for the Internet of Things. In Proceedings of the 2nd International Conference on Internet-of-Things Design and Implementation, Pittsburgh, PA, USA, 18–21 April 2017; pp. 147–158. [Google Scholar] [CrossRef]
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; Coen-Porisini, A. Security, privacy and trust in Internet of things: The road ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Granjal, J.; Monteiro, E.; Sa Silva, J.; Silva, J.S.; Sa Silva, J. Security for the Internet of Things: A Survey of Existing Protocols and Open Research Issues. IEEE Commun. Surv. Tutorials 2015, 17, 1294–1312. [Google Scholar] [CrossRef]
- Yo, B.; Li, J.; Li, Y. Distributed Data Aggregation Scheduling in Wireless Sensor Networks. ACM Trans. Sens. Netw. 2015, 11, 2159–2167. [Google Scholar] [CrossRef]
- Ozdemir, S.; Xiao, Y. Secure data aggregation in wireless sensor networks: A comprehensive overview. Comput. Netw. 2009, 53, 2022–2037. [Google Scholar] [CrossRef]
- Anantharam, P.; Barnaghi, P.; Sheth, A. Data processing and semantics for advanced internet of things (IoT) applications: Modeling, annotation, integration, and perception. In Proceedings of the International Conference on Web Intelligence, Mining and Semantics, Madrid, Spain, 12–14 June 2013. [Google Scholar]
- Flouris, I.; Giatrakos, N.; Deligiannakis, A.; Garofalakis, M.; Kamp, M.; Mock, M. Issues in complex event processing: Status and prospects in the Big Data era. J. Syst. Softw. 2017, 127, 217–236. [Google Scholar] [CrossRef]
- Dias de Assunção, M.; da Silva Veith, A.; Buyya, R. Distributed data stream processing and edge computing: A survey on resource elasticity and future directions. J. Netw. Comput. Appl. 2018, 103, 1–17. [Google Scholar] [CrossRef]
- Amadeo, M.; Campolo, C.; Molinaro, A.; Ruggeri, G. IoT data processing at the edge with named data networking. In Proceedings of the 24th European Wireless 2018 “Wireless Futures in the Era of Network Programmability, EW 2018, Catania, Italy, 2–4 May 2018; pp. 38–43. [Google Scholar]
- El-Sayed, H.; Sankar, S.; Prasad, M.; Puthal, D.; Gupta, A.; Mohanty, M.; Lin, C. Edge of things: The big picture on the integration of edge, IoT and the cloud in a distributed computing environment. IEEE Access 2018, 6, 1706–1717. [Google Scholar] [CrossRef]
- Burhan, M.; Rehman, R.A.; Khan, B.; Kim, B.S. IoT elements, layered architectures and security issues: A comprehensive survey. Sensors 2018, 18, 2796. [Google Scholar] [CrossRef]
- Rahmani, R.; Kanter, T. Layering the Internet-of-Things with Multicasting in Flow- Sensors for Internet-of-Services. Int. J. Multimed. Ubiquitous Eng. 2015, 10, 37–52. [Google Scholar] [CrossRef]
- Sadique, K.M.; Rahmani, R.; Johannesson, P. Trust in Internet of Things: An architecture for the future IoT network. In Proceedings of the 2018 International Conference on Innovation in Engineering and Technology (ICIET), Stuttgart, Germany, 17–20 June 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Pramanik, P.K.D.; Choudhury, P. IoT data processing: The different archetypes and their security and privacy assessment. In Internet of Things (IoT) Security: Fundamentals, Techniques and Applications; River Publisher: Gistrup, Denmark, 2018; pp. 37–54. [Google Scholar]
- Sobh, T.S. Identity management using SAML for mobile clients and Internet of Things. J. High Speed Netw. 2019, 25, 101–126. [Google Scholar] [CrossRef]
- Fremantle, P.; Aziz, B. Cloud-based federated identity for the Internet of Things. Ann. Telecommun. 2018, 73, 415–427. [Google Scholar] [CrossRef]
- Bierzynski, K.; Escobar, A.; Eberl, M. Cloud, fog and edge: Cooperation for the future? In Proceedings of the 2017 2nd International Conference on Fog and Mobile Edge Computing (FMEC), Valencia, Spain, 8–11 May 2017; pp. 62–67. [Google Scholar] [CrossRef]
- Pan, J.; McElhannon, J. Future Edge Cloud and Edge Computing for Internet of Things Applications. IEEE Internet Things J. 2018, 5, 439–449. [Google Scholar] [CrossRef]
- Dastjerdi, A.V.; Gupta, H.; Calheiros, R.N.; Ghosh, S.K.; Buyya, R. Fog Computing: Principles, Architectures, and Applications; Elsevier Inc.: Amsterdam, The Netherlands, 2016; Volume I. [Google Scholar]
- Abbas, N.; Zhang, Y.; Taherkordi, A.; Skeie, T. Mobile Edge Computing: A Survey. IEEE Internet Things J. 2018, 5, 450–465. [Google Scholar] [CrossRef]
- Ni, J.; Zhang, K.; Lin, X.; Shen, X.S. Securing Fog Computing for Internet of Things Applications: Challenges and Solutions. IEEE Commun. Surv. Tutor. 2018, 20, 601–628. [Google Scholar] [CrossRef]
- Roman, R.; Lopez, J.; Mambo, M. Mobile edge computing, Fog et al.: A survey and analysis of security threats and challenges. Future Gener. Comput. Syst. 2018, 78, 680–698. [Google Scholar] [CrossRef]
- Yan, Z.; Zhang, P.; Vasilakos, A.V. A survey on trust management for Internet of Things. J. Netw. Comput. Appl. 2014, 42, 120–134. [Google Scholar] [CrossRef]
- El-Hajj, M.; Fadlallah, A.; Chamoun, M.; Serhrouchni, A. A survey of internet of things (IoT) authentication schemes. Sensors 2019, 19, 1141. [Google Scholar] [CrossRef]
- Abreu, V.; Santin, A.O.; Viegas, E.K.; Cogo, V.V. Identity and Access Management for IoT in Smart Grid. Adv. Intell. Syst. Comput. 2020, 1151, 1215–1226. [Google Scholar] [CrossRef]
- Hsu, C.L.; Chuang, T.H.; Chen, Y.H.; Lin, T.W.; Lu, H.C. A dynamic identity end-to-end authentication key exchange protocol for IoT environments. In Proceedings of the 2017 12th International Conference on Digital Information Management ICDIM 2017, Fukuoka, Japan, 12–14 September 2014; pp. 133–138. [Google Scholar] [CrossRef]
- Van Thuan, D.; Butkus, P.; Van Thanh, D. A user centric identity management for Internet of Things. In Proceedings of the 2014 International Conference on IT Convergence and Security (ICITCS), Beijing, China, 28–30 October 2014; pp. 9–12. [Google Scholar] [CrossRef]
- Gómez-Cárdenas, A.; Masip-Bruin, X.; Marín-Tordera, E.; Kahvazadeh, S. A Novel and Scalable Naming Strategy for IoT Scenarios; Springer Nature Switzerland AG: Cham, Switzerland, 2019; Volume 880, ISBN 9783030026868. [Google Scholar]
- Sarma, A.C.; Girão, J. Identities in the future internet of things. Wirel. Pers. Commun. 2009, 49, 353–363. [Google Scholar] [CrossRef]
- Santos, B.; Dzogovic, B.; Feng, B.; Do, V.T.; Jacot, N.; Van Do, T. Cross-Federation Identities for IoT Devices in Cellular Networks. In Proceedings of the 2019 24th IEEE International Conference on Emerging Technologies and Factory Automation (ETFA), Zaragoza, Spain, 10–13 September 2019; pp. 1745–1751. [Google Scholar] [CrossRef]
- Kirubadevi, T.; Ramamoorthy, S.; Rajavarman, V.N. Device identification and authentication for internet of things using predefined characteristics. J. Phys. Conf. Ser. 2019, 1362. [Google Scholar] [CrossRef]
- Ganzha, M.; Paprzycki, M.; Pawlowski, W.; Szmeja, P.; Wasielewska, K. Identifier management in semantic interoperability solutions for IoT. In Proceedings of the 2018 IEEE International Conference on Communications Workshops (ICC Workshops), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Weidenfeller, T.; Bausch, C. Cross-domain: Identity of things. Ericsson Rev. 2017, 94, 32–41. Available online: https://www.ericsson.com/en/reports-and-papers/ericsson-technology-review/articles/cross-domain-identity-of-things (accessed on 22 July 2020).
- El Kaed, C.; Ponnouradjane, A. A Model Driven Approach Accelerating Ontology-based IoT Applications Development. In Proceedings of the Posters and Demos Track of the 13th International Conference on Semantic Systems—SEMANTiCS2017 Co-Located with the 13th International Conference on Semantic Systems, Amsterdam, The Netherlands, 11–14 September 2017; p. 2063. [Google Scholar]
- Mao, Y.; You, C.; Zhang, J.; Huang, K.; Letaief, K.B. A Survey on Mobile Edge Computing: The Communication Perspective. IEEE Commun. Surv. Tutor. 2017, 19, 2322–2358. [Google Scholar] [CrossRef]
- Murdoch, S.J. Introduction to Trusted Execution Environments (TEE)—IY5606; CiteSeerx: University Park, PA, USA, 2015. [Google Scholar]
- Sabt, M.; Achemlal, M.; Bouabdallah, A. Trusted execution environment: What it is, and what it is not. In Proceedings of the 2015 IEEE Trustcom/BigDataSE/ISPA, Helsinki, Finland, 20–22 August 2015; Volume 1, pp. 57–64. [Google Scholar] [CrossRef]
- McGillion, B.; Dettenborn, T.; Nyman, T.; Asokan, N. Open-TEE—An open virtual trusted execution environment. In Proceedings of the 2015 IEEE Trustcom/BigDataSE/ISPA, Helsinki, Finland, 20–22 August 2015; Volume 1, pp. 400–407. [Google Scholar] [CrossRef]
- Chen, S.; Kalbarczyk, Z.; Xu, J.; Iyer, R.K. A Data-Driven Finite State Machine Model for Analyzing Security Vulnerabilities. In Proceedings of the IEEE International Conference on Dependable Systems and Networks, San Francisco, CA, USA, 22–25 June 2003; pp. 605–614. [Google Scholar] [CrossRef]
- Koblitz, N. Elliptic Curve Cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Wei, J.; Viet, T.; Phuong, X.; Yang, G.; Member, S. An Efficient Privacy Preserving Message Authentication Scheme for Internet-of-Things. Internet Things 2020. [Google Scholar] [CrossRef]
- Zhang, J.; Chen, B.; Zhao, Y.; Cheng, X.; Hu, F. Data Security and Privacy-Preserving in Edge Computing Paradigm: Survey and Open Issues. IEEE Access 2018, 6, 18209–18237. [Google Scholar] [CrossRef]
- Wang, W.; Lu, Z. Cyber security in the Smart Grid: Survey and challenges. Comput. Netw. 2013, 57, 1344–1371. [Google Scholar] [CrossRef]
- Staite, C.; Bahsoon, R. Evaluating identity management architectures. In Proceedings of the 3rd international ACM SIGSOFT symposium on Architecting Critical Systems, Bertinoro, Italy, 25–28 June 2012; pp. 11–20. [Google Scholar] [CrossRef]
- Boujezza, H.; Al-Mufti, M.; Ayed, H.K.; Saidane, L. A taxonomy of identities management systems in IOT. In Proceedings of the IEEE/ACS International Conference on Computer Systems and Applications (AICCSA), Agadir, Morocco, 29 November–2 December 2016. [Google Scholar] [CrossRef]
- Haidar, A.N.; Abdallah, A.E. Comparison and evaluation of identity management in three architectures for virtual organizations. In Proceedings of the 2008 The Fourth International Conference on Information Assurance and Security, Naples, Italy, 8–10 September 2008; pp. 21–26. [Google Scholar] [CrossRef]
- Frustaci, M.; Pace, P.; Aloi, G.; Fortino, G. Evaluating critical security issues of the IoT world: Present and future challenges. IEEE Internet Things J. 2018, 5, 2483–2495. [Google Scholar] [CrossRef]
- The Scyther Tool. Available online: http://www.cs.ox.ac.uk/people/cas.cremers/scyther/ (accessed on 2 October 2020).
- Cremers, C.J.F. The scyther tool: Verification, falsification, and analysis of security protocols—Tool paper. In Proceedings of the 20th International Conference, CAV 2008, Princeton, NJ, USA, 7–14 July 2008; pp. 414–418. [Google Scholar] [CrossRef]
- Darbandeh, F.G.; Safkhani, M. A New Lightweight User Authentication and Key Agreement Scheme for WSN. Wirel. Pers. Commun. 2020. [Google Scholar] [CrossRef]
- Trinh, C.; Huynh, B.; Lansky, J.; Mildeova, S.; Safkhani, M.; Bagheri, N.; Kumari, S.; Hosseinzadeh, M. A Novel Lightweight Block Cipher-Based Mutual Authentication Protocol for Constrained Environments. IEEE Access 2020, 8, 165536–165550. [Google Scholar] [CrossRef]
- Nikooghadam, M.; Amintoosi, H.; Kumari, S. A provably secure ECC-based roaming authentication scheme for global mobility networks. J. Inf. Secur. Appl. 2020, 54, 102588. [Google Scholar] [CrossRef]
- Deebak, B.D.; Al-Turjman, F. A smart lightweight privacy preservation scheme for IoT-based UAV communication systems. Comput. Commun. 2020, 162, 102–117. [Google Scholar] [CrossRef]
- Rostampour, S.; Safkhani, M.; Bendavid, Y.; Bagheri, N. ECCbAP: A secure ECC-based authentication protocol for IoT edge devices. Pervasive Mob. Comput. 2020, 67, 101194. [Google Scholar] [CrossRef]
- Adeli, M.; Bagheri, N.; Meimani, H.R. On the designing a secure biometric-based remote patient authentication scheme for mobile healthcare environments. J. Ambient Intell. Humaniz. Comput. 2020. [Google Scholar] [CrossRef]
- Holzmann, G.J. SPIN Model Checker. The: Primer and Reference Manual; Addison-Wesley Professional: Boston, MA, USA, 2003. [Google Scholar]
- Ben-Ari, M. Principles of the Spin Model Checker; Springer-Verlag London Ltd.: London, UK, 2008. [Google Scholar]















| Notation | Description |
|---|---|
| IoTD | IoT Device |
| EIoTG | Edge IoT Gateway |
| LIdP | Local Identity Provider |
| GIdP | Global Identity Provider |
| IDIoTD, IDEIoTG, IDLIdP, IDGIdP | Identities of IoTD, EIoTG, LIdP and GIdP |
| PbkEIoTG, PbKLIdP, PbKGIdP | Public keys of EIoTG, LIdP and GIdP |
| PrkEIoTG, PrKLIdP, PrKGIdP | Private keys of EIoTG, LIdP and GIdP |
| SrKIoTD-EIoTG | Shared key for IoTD and EIoTG |
| SkIoTD-EIoTG | Session key for IoTD and EIoTG |
| Features 1 | Paper References (Discussed) | Paper References (Not Discussed) | IMSC-EIoTD (Our Approach) |
|---|---|---|---|
| Security | [31,32,41,42,44,45,46,47,48,49] | [43] | Addressed |
| Privacy | [31,32,42,44,45] | [41,43,46,47,48,49] | Discussed |
| Trustworthiness | [31,46,49] | [32,41,42,43,44,45,46,47,48] | Described |
| Mobility | [31,43,44,45,47] | [32,41,42,46,48,49] | Addressed |
| Usability | [45,46] | [31,32,41,42,43,44,47,48,49] | Discussed |
| Affordability | [31,32,41,42,43,44,45,46,47,48,49] | Discussed | |
| Law enforcement | [31,32,41,42,43,44,45,46,47,48,49] | Discussed | |
| Interoperability | [31,44,45,46,47,48,49] | [32,41,42,43] | Discussed |
| Functionality | [31,44,45,46,47,49] | [32,41,42,43,48] | Described |
| Scalability | [31,41,44,48] | [32,42,43,45,46,47,49] | Addressed |
| Administration | [31,45,49] | [32,41,42,43,44,46,47,48] | Described |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sadique, K.M.; Rahmani, R.; Johannesson, P. IMSC-EIoTD: Identity Management and Secure Communication for Edge IoT Devices. Sensors 2020, 20, 6546. https://doi.org/10.3390/s20226546
Sadique KM, Rahmani R, Johannesson P. IMSC-EIoTD: Identity Management and Secure Communication for Edge IoT Devices. Sensors. 2020; 20(22):6546. https://doi.org/10.3390/s20226546
Chicago/Turabian StyleSadique, Kazi Masum, Rahim Rahmani, and Paul Johannesson. 2020. "IMSC-EIoTD: Identity Management and Secure Communication for Edge IoT Devices" Sensors 20, no. 22: 6546. https://doi.org/10.3390/s20226546
APA StyleSadique, K. M., Rahmani, R., & Johannesson, P. (2020). IMSC-EIoTD: Identity Management and Secure Communication for Edge IoT Devices. Sensors, 20(22), 6546. https://doi.org/10.3390/s20226546






