1. Introduction
Unmanned Aerial Vehicles (UAVs) are an emerging technology designed to flight with no human pilot. The UAV use was initially motivated by military applications, including reconnaissance, surveillance, and tracking [
1,
2]. This is due to the fact that the UAVs can be readily equipped with sensors, cameras, radars, and more technologies for military purposes [
3,
4]. Recently, the use of UAV has unprecedentedly increased including wide range of applications, such as, public safety, police, transportation, package delivery, and environmental monitoring. UAVs offer crucial help in rescue and recovery for disaster relief operations, when public communication networks get crippled [
5], since they can form a salable and dynamic networks [
6]. The UAV ability of hovering over a targeted area is desirable in many applications, for example, a UAV can help in localization when the Global position System (GPS) unavailable or inaccurate [
7,
8].
Jamming attacks in wireless communication can be classified into two main levels [
9,
10]. First, the elementary level that includes constant, deceptive, and random jammers. The constant jammer simply transmits a random bit continually to make the available channel busy [
10]. Hence, any node within the jammer transmission range will be unable to access the channel and keep sensing until its battery depleted [
9]. While the deceptive jammer, as the name suggested, tries to mimic the original transmission by sending regular packets towards the target node. In this case, all of the nodes located around the jammer will switch to receive mode and process the received corrupted data. The random jammer switches to active mode and transmitting jamming signals towards the target for a certain time and then return to sleep mode [
11,
12]. Second, the advanced level that might include the barge and the spot jammers. Here, the jammers sense all available channels; once it detects the channel used by legitimate one, it immediately transmits its signal to jam it. The jammers change their frequencies from carrier to another aiming to block all sub-channels [
13]. Detecting the UAV jamming location is the first step towards preventing such an attack. By finding the UAV location, any appropriate action can be taken against the enemy UAV; e.g., physically destroying it or jam the Jammer by another jamming source [
14,
15].
Tracking and localization jammers in wireless communication networks are still challenging topics. The used algorithms can be categorized into two main groups: range-free and range-based schemes [
16]. The accuracy of the range-free techniques is based on nodes locations and the change of network topology. In this context, the Centroid Localization (CL) algorithm [
17] and Weighted Centroid (WCL) algorithm [
18] are examples of range-free techniques. They are both sensitive to node locations and the number of nodes deployed. The location accuracy increases when the number of nodes affected by the jamming signal increases [
18,
19]. Therefore, the range free method is inaccurate when the affected nodes are fewer and are located closer to each other. However, the range-based method utilizes the so-called Jammer Received Signal Strength (JRSS) in order to detect and predict jammers’ physical locations. This method tries to estimate the JRSS of the original signal, hence more reliable results can be achieved when compared to its range-free counterpart. Centralized Extended Kalman Filtering (EKF-Centr) was proposed in [
20], where the algorithm is based on the received jammer’s power from the boundary nodes at each time step. It was found [
20,
21] that the tracking efficiency increases when the number of boundary nodes increases.
A method for detecting jammer’s location utilizing the Packet Delivery Ratio (PDR) rate at each node was reported in [
22]. In [
23], the adaptive RSSI filtering technique is employed to improve the measured RSSI signal degraded due to multipath effects with the aim to enhance the localization accuracy and to reduce the computational complexity of the tracking system. The RSSI based approaches that Kalman filtering to estimate the target position are presented in [
24,
25]. They considered that, during jamming attacks, both the Signal to Noise Ratio (SNR) and PDR decrease as the amount of noise increases. Therefore, any node that has a lower PDR than expected is considered as a near jammer node and the gradient descent technique is employed in order to track the jamming source [
22]. Wide-band jammer localization method introduced in [
26], where a combination of Difference of Arrivals (DOA), Time Difference of Arrivals (TDOA), and EKF used. More explicitly, the DOA was utilized in order to provide the EKF with an accurate initial position, while the TDOA helped the EKF for fast converge. The efficiency of this method depends on the number nodes used for localization and tracking processes [
26].
In summary, the aforementioned existing solutions have one of several drawbacks, such as (i) higher computationally complex due to heavy computational requirements for DOA/TDOA estimation [
26], (ii) sensitive to node locations and the number of nodes deployed [
18,
19], (iii) require a large computations for centralized processing and dependency on large number of boundary nodes [
20], and (iv) highly sensitive to noise power (or SNR) [
22]. Against these techniques, we proposed two novels distributed Extended Kalman Filter (EKF) based schemes:
Distributed EKF (DEKF) scheme while using information of the received power from the jammer at a single boundary node only.
Distance Ratio aided Distributed EKF (DEKF-DR) based scheme utilizing an edge node in addition to a single boundary node.
In general, these two methods require less computation due to distributed processing. Among these methods, DEKF-DR is the most promising, as it only uses a single node and its one neighbor to estimate received powers while offering the best accuracy when compared to the DEKF and the EKF-Centr (which is also modified for the 3-D scenario) techniques.
The paper is organized, as follows: following the introduction, the system model is presented in
Section 2.
Section 3 introduces the concept of Distance Ratio. In
Section 4, an overview of the standard Extended Kalman Filter is provided and the proposed distributed Extended Kalman Filter for 3-D Jammer’s Localization are developed.
Section 5 provides extension of the existing centralized EKF-aided jammers Localization scheme to 3-D scenario. The results and discussion are provided in
Section 6. Finally, concluding remarks are given in
Section 7.
2. System Model
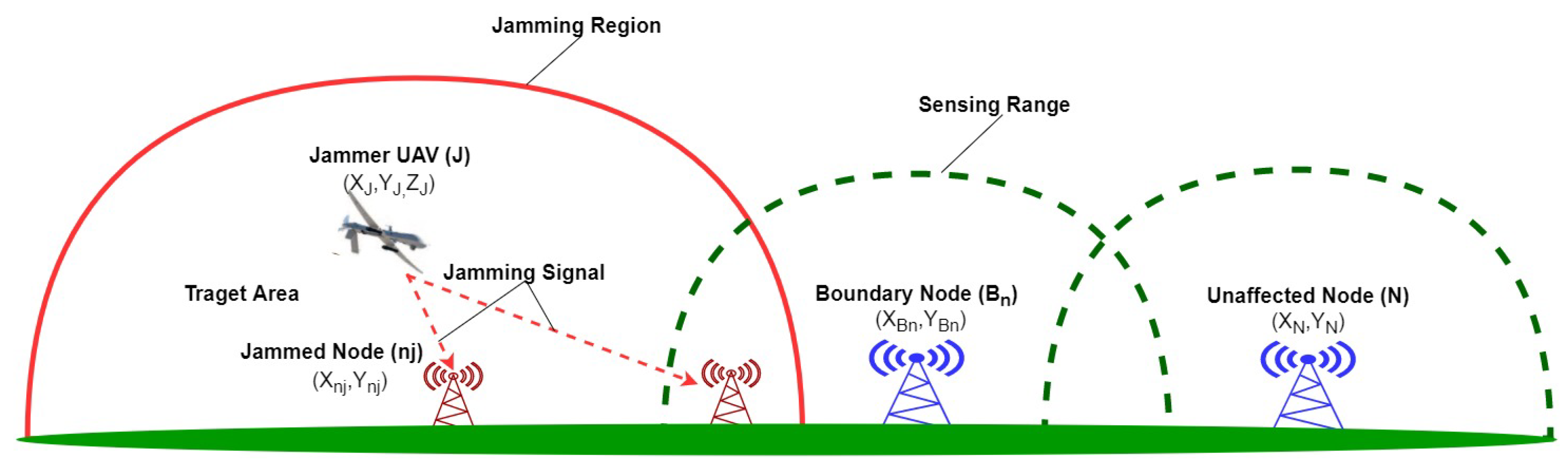
We consider a jammer UAV (J) flying above the target area and emitting its jamming signal towards base stations on the ground. There are two base stations located outside the jamming region that may transmit and receive data from each other, as shown in
Figure 1. Without loss of generality, we consider that the jammer UAV is moving in a three-dimensional Cartesian coordinates system with variable speed and constant acceleration. Constant acceleration is used in many works such as in [
4] and non-acceleration model [
27]. Non-acceleration models are commonly used in monocular SLAM systems [
27]. The base stations are at fixed positions in the XY-plane, as shown in
Figure 2. During a jamming attack, the network topology may change and nodes will be affected based on their locations and jammer’s transmission power. Note that, the key parameters are defined in
Table 1.
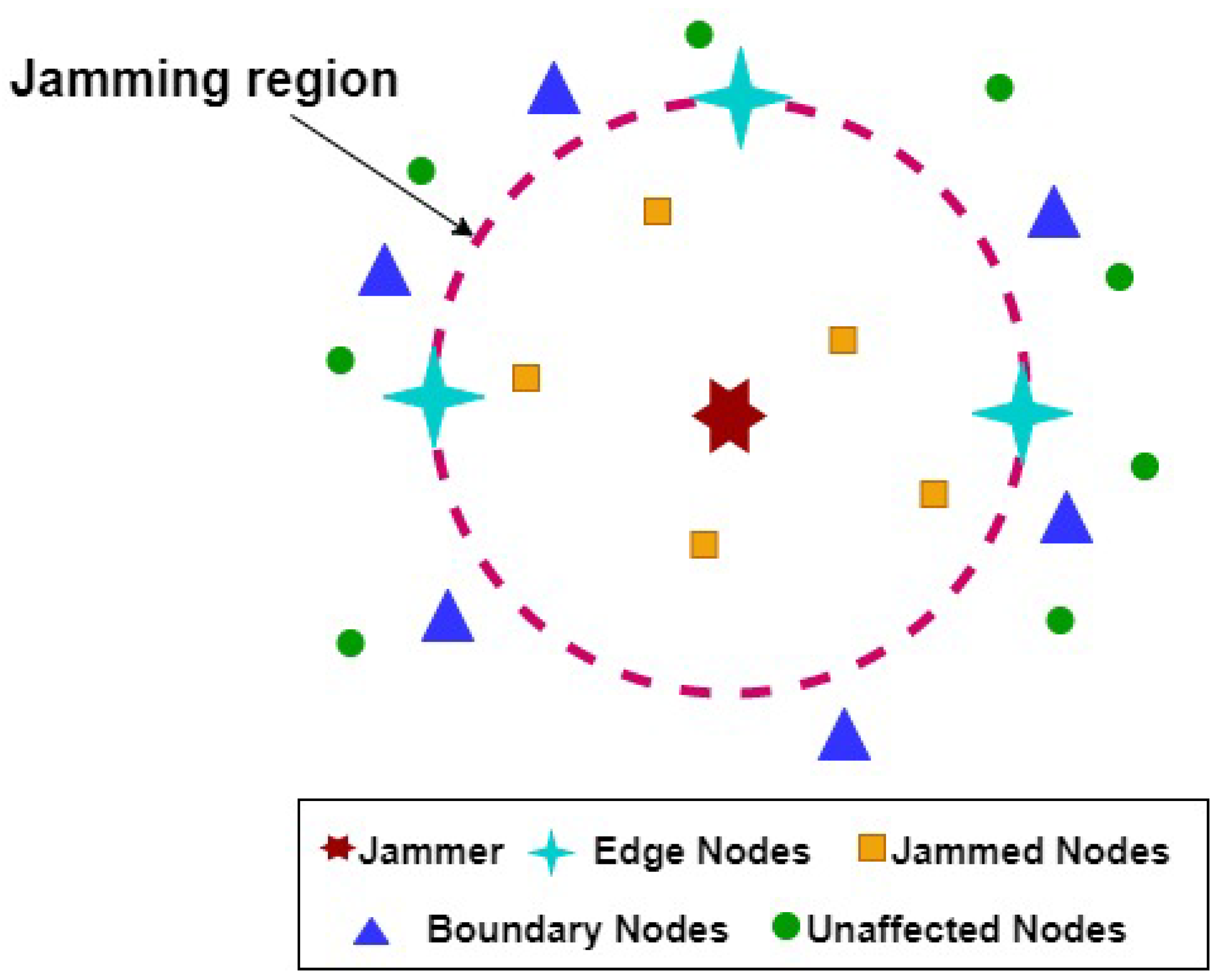
Based on jamming signal and noise powers at the received signal by sensors, the nodes are classified into three different types [
28], as shown in
Figure 3. When jamming signal attacks nodes, the SNR decreases which result in increased Bit Error Rate (BER) and decreased Packet Delivery Ratio (PDR). Thus, the system fails to decode the signal properly and it requests the re-transmission of signals. Packets received with SNR below the system threshold value
are considered invalid data and require re-transmission of data. The sensors located inside the jamming region are called Jammed Nodes,
, and have SNR less the than system threshold value (
). Hence, they are completely isolated from the network and cannot send or receive data from their neighbors. On the other hand, the nodes located near the jamming region and have SNR larger than the system threshold are known as the Boundary Nodes,
B. These nodes lost their links with some of their neighbors. However, they might still have active links with unaffected sensors and can communicate with them. Lastly, the nodes outside the attacked area with SNR larger than the system threshold value are called Unaffected Nodes
N.
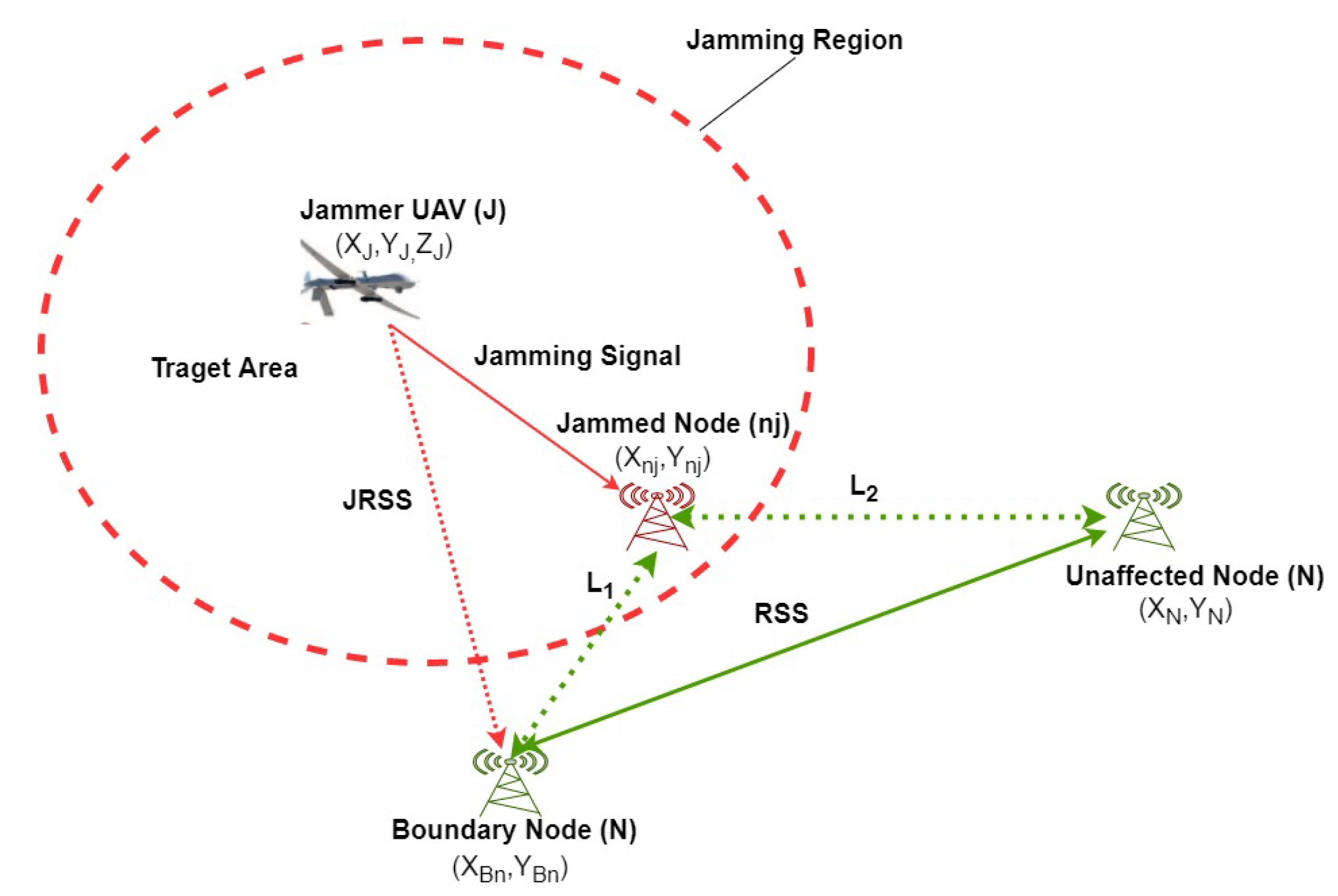
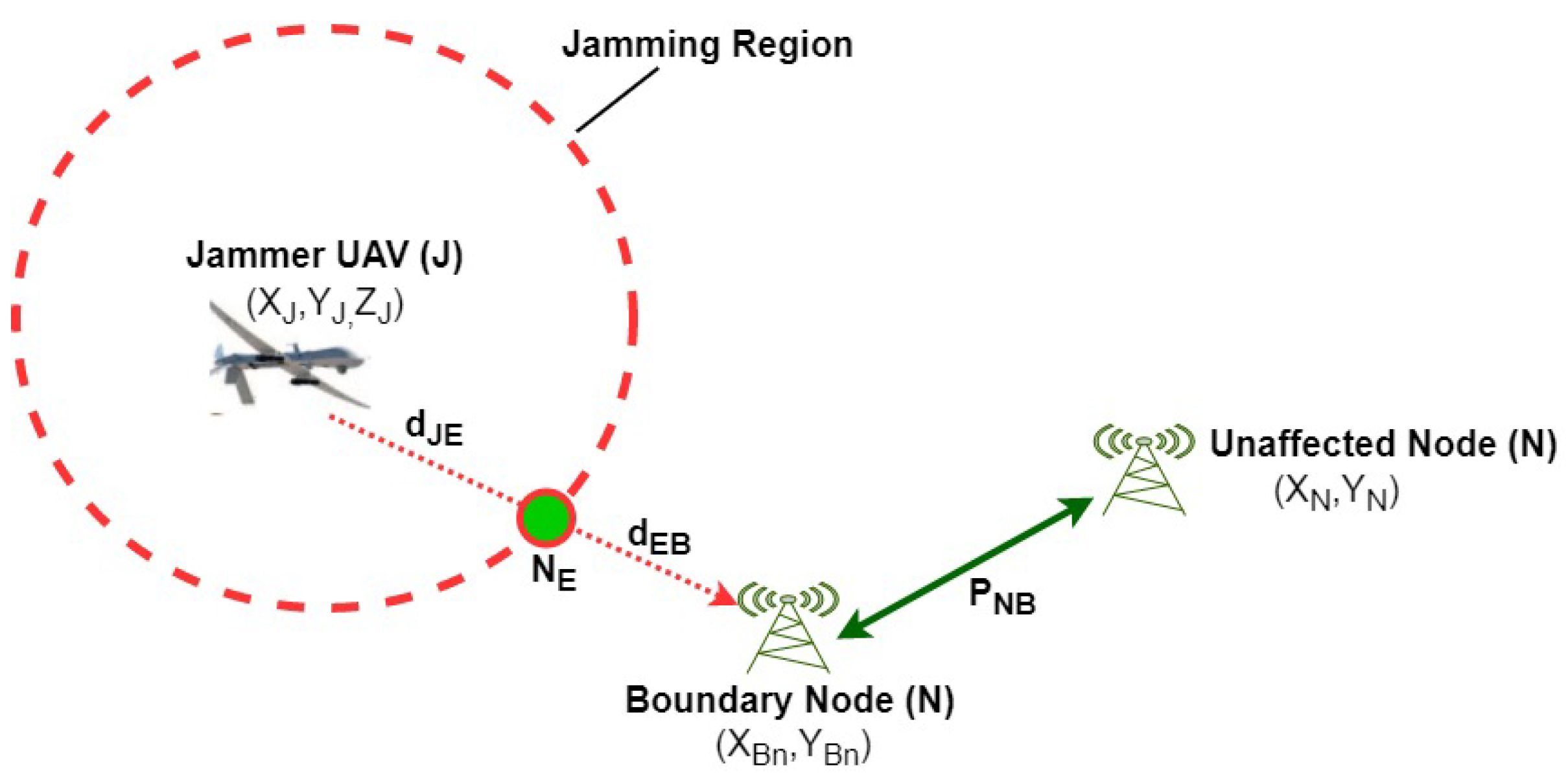
3. Concept of Distance Ratio ()
In this section, we described the concept of distance ratio which was introduced in [
29]. Moreover, we extended the distance ratio concept to three-dimensional space
. This concept will be later utilized in order to develop the EKF algorithm in
Section 4. Note that,
Table 1 defines the main parameters. The distance ratio concept is based on signal to noise ratio at the edge node
, jamming power received by boundary node
B and Received Signal Strength (RSS) from
B, as shown in
Figure 4. Here,
and
are the distances from the jammer to the boundary node and from the jammer to the edge node, respectively. Thus, we can express
and
, respectively, as:
and
The SNR decreases when the jammer moves towards the target node until it drops to below an acceptable threshold value. This results in a jammed node and communication channel being completely blocked. Therefore, the node has SNR approximately equal to the system threshold value
located on the jamming edge. We use this observation in order to estimate the unknown distances between the jammer and edge node. The jamming power received by the boundary node is following the Log-distance shadowing model where it an extension of the Friis equation and it is proportional inverse to the distance, as follows:
where
is the jamming power received at distance
d, and
is the jammer’s transmission power, the path loss exponent
n, depending on the environment and it is variant from physical environment to other. In this paper we assumed it equal to 2 for free space environment, or Line of Sight (LoS). The Gaussian noise with zero mean denoted by
.
k is constant and depend on the antenna characteristics.
is the distance between jammer and the boundary node.
Similarly, the jamming power received by the edge node (represented by
) can be expressed as:
Next, we define the distance ratio (
) as the ratio of
to
, that is:
Now, using the geometry that is shown in
Figure 4, we conclude that the distances
,
, and
are related as:
Thus, we can also relate
and
while using the following:
As a result, we can relate the power terms
and
with the aid of distance ratio to obtain:
Similarly, it can be shown that
and
can be related as:
Later, in
Section 3, we will explain how the above equations can help us in the development of a distributed Extended Kalman Filter (EKF) algorithm for the jammer’s 3D location estimation.
4. Proposed Distributed Extended Kalman Filter Based 3D Jammer’s Localization Schemes
The Extended Kalman Filtering is an extension of Linear Kalman Filter (LKF), which is capable to take into account the nonlinearity of the system model. More specifically, the EKF employs the first-order linearization of the nonlinear system in a recursive fashion to find the estimates current mean and the covariance of the state vector [
30].
Consider the following non-linear state transition model:
where
represents the state vector,
is the input vector,
represents the non-linear state transition function, and
is a zero mean Gaussian process noise with a covariance matrix
, i.e.,
. Now, the measurement vector
can be expressed as:
where
is a zero mean Gaussian measurement noise with a covariance matrix
, i.e.,
. Here,
represents non-linear function for the measurement process. The EKF estimates the current position in two main steps, prediction and update state [
31]. Next, we can define the following Jacobian matrices as:
the conventional EKF algorithm can be summarized, as follows:
where
is the Kalman gain and
is the state error covariance matrix estimate at time instant
.
Next, we propose our distributed EKF-based two different methods for the 3-D Jammer’s Localization. These are presented in the ensuing sub-sections.
4.1. Distributed Extended Kalman Filter (DEKF) for 3D Localization
In this method, a distributed scenario is considered, where each node employs the standard EKF by using the information of the received power from the jammer at the nearby boundary node of the jamming region, as shown in
Figure 3. This scheme is termed as Distributed Extended Kalman Filter (DEKF). In the DEKF approach, every node process the jamming power and estimate the jammer’s location locally without the need to collaborate with another node. Thus, for the jammer’s 3D localization task with the DEKF, the state vector will take the following form:
The Jammer’s motion can be described using the well-known Kinetic equation model given by:
Thus, the Jacobian matrix
can be expressed as:
Additionally, the covariance matrix of process noise
and the covariance matrix of measurement noise
can be written, respectively, as:
Now, assume that every sensor node provides the measurements of jammer’s velocity components
, acceleration
components, and the power received, which are captured by boundary node denoted as
. Hence, the measurement vector can be set up as:
Thus, in this scenario, both the observation function
and the Jacobian matrix
can be described, respectively, as:
and
In order to evaluate the partial derivatives appearing in the above Jacobian matrix, we have to utilize the relation between the received power (
) and distance of jammer from the boundary node (
) given in Equation (
1). The distance of jammer from the boundary node can be evaluated while using the following expression:
where (
) is the boundary node. Thus, the first derivative of jamming power with respect to jammer’s position at time
k becomes as follows:
where
C is a constant given by:
Hence, the proposed DEKF for the three-dimensional (3D) localization can be implemented while using the Equations (
13)–(
17) with the aid of Equations (
20), (
25)–(
30).
4.2. Distance Ratio Based Distributed Extended Kalman Filter (DEKF-DR) for the 3D Localization
In this section, we proposed a distributed EKF by utilizing an additional edge node
E in addition to a single boundary node
B, as shown in
Figure 4. For this purpose, we utilize the concept of Distance Ratio (
) described in
Section 3. Because both the distances
and
are unknown and the SNR at the edge node equal to the system threshold value
, we can estimate the distance ratio by SNR and power relations as follows:
where
is the power received at the unaffected node
N from the boundary node
B. Thus, once the
is evaluated while using above relation, we can utilize it in Equations (
8) and (
9). Moreover, the distances can be expressed in terms of
as
Again, the state vector
,
the Jacobian matrix, and the process noise
can be defined by Equations (
18), (
20) and (
21), respectively. However, the measurement vector incorporates the power measurements from a single boundary node (i.e.,
) and from Edge node (i.e.,
and
), that is,
therefore, the covariance matrix of measurement noise
become
Thus, the Jacobian matrix
can be obtained, as follows:
Therefore, the first derivative of jamming power with respect to jammer’s position at time
k will be resulted in the following expressions:
where,
Thus, the proposed DEKF-DR algorithm for the 3D localization as explained in Algorithm 1 can be implemented while using the Equations (
13)–(
17) with the aid of Equations (
37)–(
47).
| Algorithm 1:Pseudo-code of DEKF-DR |
- 1:
Set the system threshold value = . - 2:
Initialize time index the boundary node index and the neighbor node index . - 3:
Input:, . - 4:
Output:. - 5:
repeat - 6:
. - 7:
Capture the . - 8:
Estimate . - 9:
Compute the using Equation ( 5). - 10:
Compute the and using Equations ( 8) and ( 9). - 11:
. - 12:
. - 13:
. - 14:
Estimate using Equation ( 1). - 15:
. - 16:
. - 17:
. - 18:
. - 19:
- 20:
until {Final time }
|
5. Extension of the Centralized Extended Kalman Filter (EKF-Centr) for the 3-D Localization
In the centralized EKF, every node near the jamming region may receive the jamming signal and transfer the collected data to a centralized base station, where the EKF is employed. Therefore, the EKF-Centr is designed to receive the jamming information at each time step
k from all of the boundary nodes (say total
boundary nodes). Thus, the state vector
and
the Jacobian matrix remains the same as appeared in Equations (
18) and (
20), respectively. However, the measurement vector incorporates the power measurements from all
boundary nodes, which is,
Additionally, the covariance matrix of measurement noise
Consequently, the Jacobian matrix for the measurement will become:
Similar to the previous case, in order to evaluate the partial derivatives in the above, we utilize the distance of jammer from each boundary node. Thus, for the
i-th boundary node, the jammer’s distance is given by:
Therefore, the first derivative of jamming power with respect to jammer’s position will become:
where
is the constant for the
i-th node and is given by:
In summary, the proposed EKF-Centr algorithm for the 3D localization can be implemented using the Equations (
13)–(
17) with the aid of Equations (
50), (
52)–(
55).
Remark 1. At this stage, it is important to contrast the major differences among the two proposed algorithms (the DEKF and the DEKF-DR) and the conventional EKF-Centre. By observing the Jacobian matrix , it can be deduced that the size of is adjusted, depending on the number of nodes utilized in the localization process. In the DEKF, there is only one boundary node to detect the jammer’s location with the aid of received power only in distributed mechanism. In the EKF-Centr, there are nodes utilized to locate the jammer’s location by sending all of the information to a centralized node. Finally, in the DEKF-DR, a single boundary node along with an edge node is used in distributed fashion.
6. Results and Discussion
We considered the first scenario in which the jammer UAV hovers in three-dimensional space with constant acceleration equal to zero and variable velocity at each time step in order to evaluate the performance of the proposed algorithm. The boundary node or the tracker is located at the position with transmitting power dBm. The neighbor node near the boundary is located at with the same transmitting power as that of the boundary node. The jammer UAV starts at position with starting time equal to zero and transmitting power equals to dBm. The sensing range of the boundary node is equal to 16 meters and the jammer UAV transmitting range is around 90 m. In the first experiment, the initial position for the original trajectory and UAV are .
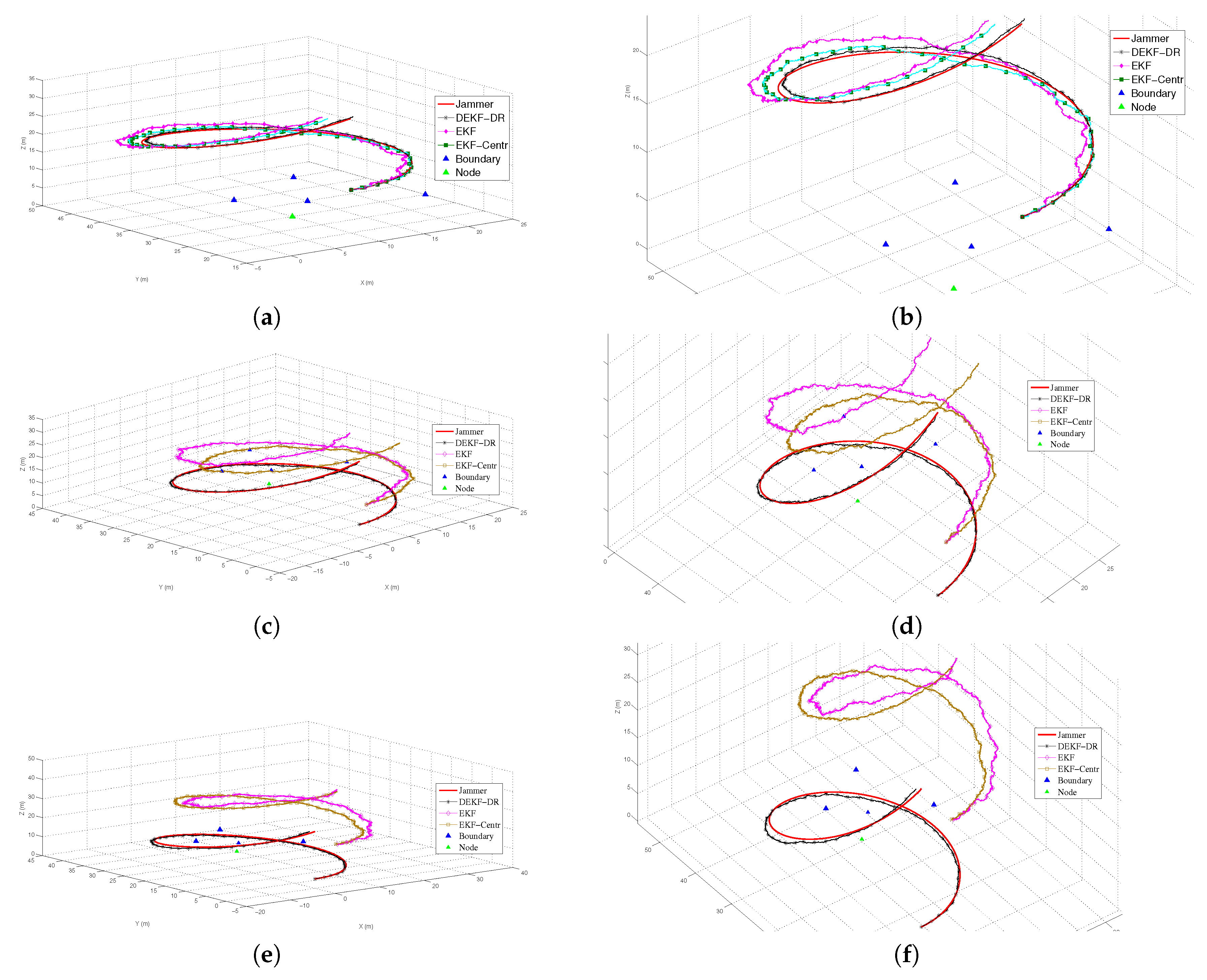
It can be depicted with the results that are shown in
Figure 5a that the proposed the DEKF-DR has better localization performance in comparison with the DEKF and the EKF-Centr. To measure the performance and the robustness of the proposed algorithm, we have set the starting positions different for both the original trajectory and the UAV, such that the original trajectory started at position
, while the initial positions for the UAV are
in
Figure 5c and (13,9,14)
Figure 5e. It can be easily seen that the proposed DEKF-DR has outperformed its counterparts in both experiments and able to estimate the jammer more accurately. In contrast, the DEKF and EKF-Centr had a shift in tracking the jammer’s location, as shown in
Figure 5c,e. Here, the blue triangle and the green triangle represent the boundary nodes and the neighbor nodes, respectively. The second scenario is to evaluate the centralized EKF, where the four boundary nodes located at positions
,
,
and
, as shown in
Figure 5. The system threshold value
and the path loss factor
n for free space set to 2, as in
Table 2.
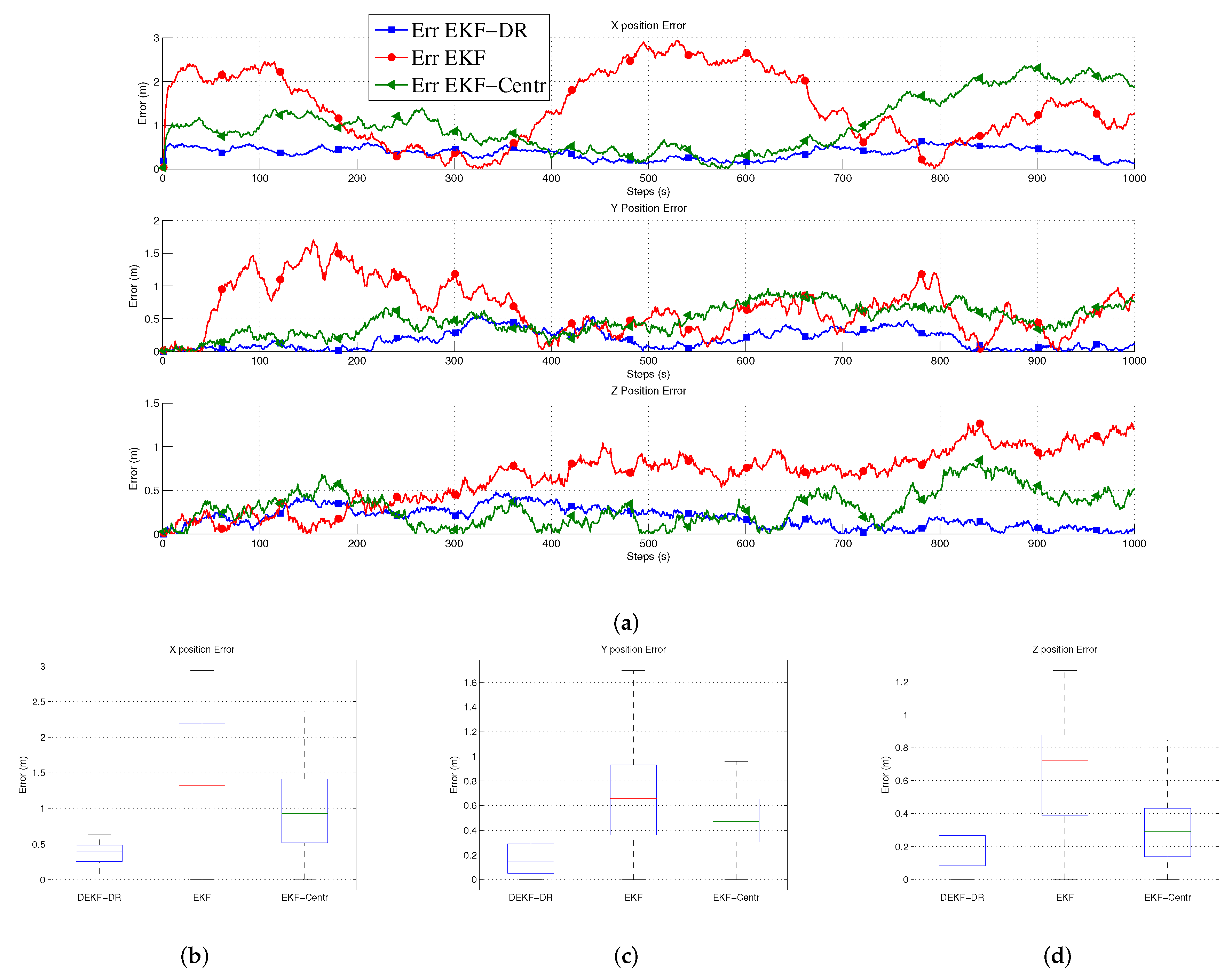
Figure 6a shows the position errors in three-dimension space (x, y, z) at each time step. Here, the jammer UAV is moving in 1000 steps to measure the performance of the EKF-DR. The proposed algorithm can estimate the jammer position more accurately when compared to the EKF-Centr and the DEKF. The maximum position error is less than 0.6 meters compared to 2.9 m and 2.4 m for the DEKF and the EKF-Centr, respectively. The DEKF-DR performed better as the average localization error is about 0.3 m on the x-axis, 0.1 m on the y-axis, and 0.18 on the z-axis, as shown in
Figure 6b–d, respectively. In the same figure, the box plot represents the median of the localization error. Here, the median error for x position is less than 0.2 m compared to 1.3 m and 0.92 m for DEKF and EKF-Centr, respectively. Similarly, the median error for the z position is less than 0.29 m for the DEKF-DR compared to its counterparts. These results further verifies the superiority of the DEKF-DR to detect the jammer location in three-dimensional space. It can be seen from these results that the conventional EKF has reached sometime a very low error close to zero. However, its error is highly fluctuating and sometimes reaches to very high value. This is also illustrated in the statistical information provided by the box plot. These results show highly inconsistent behavior of estimation by the EKF, which is not desirable in real practice. On the other hand, the proposed EKF-DR has consistent estimation performance with lesser median localization error. Moreover, the DEKF-DR has lesser computational complexity than its counterparts. Furthermore,
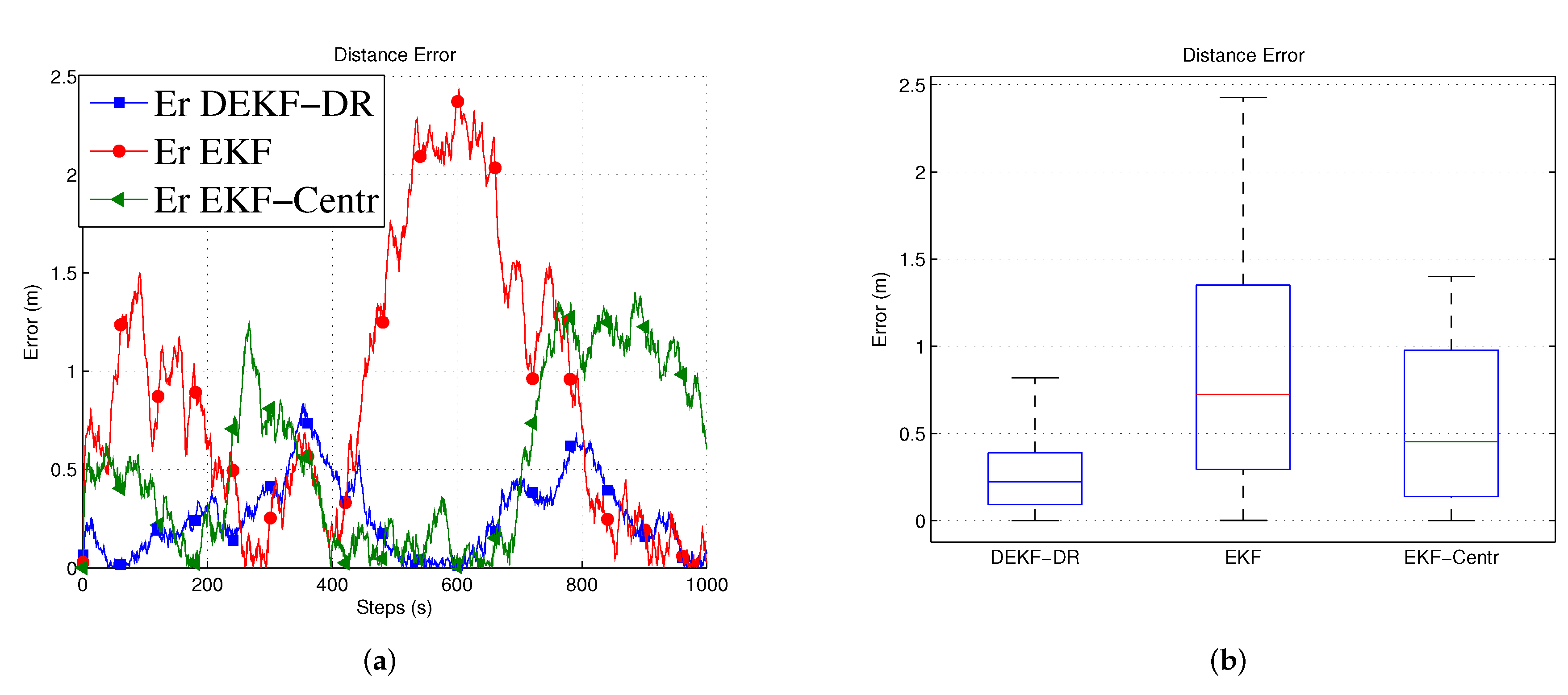
Figure 7a shows that the Euclidean distance error to the jammer. Here, it can be observed that the DEKF has poor performance, among others. This is due to the fact that it only uses one node information, which is insufficient for the Kalman filter to estimate the unknown position. On the other hand, the EKF-Centr is designed to receive the localization information from all four different nodes and, hence, it performed better than the DEKF. Finally, the DEKF-DR showed lowest distance error. as illustrated in
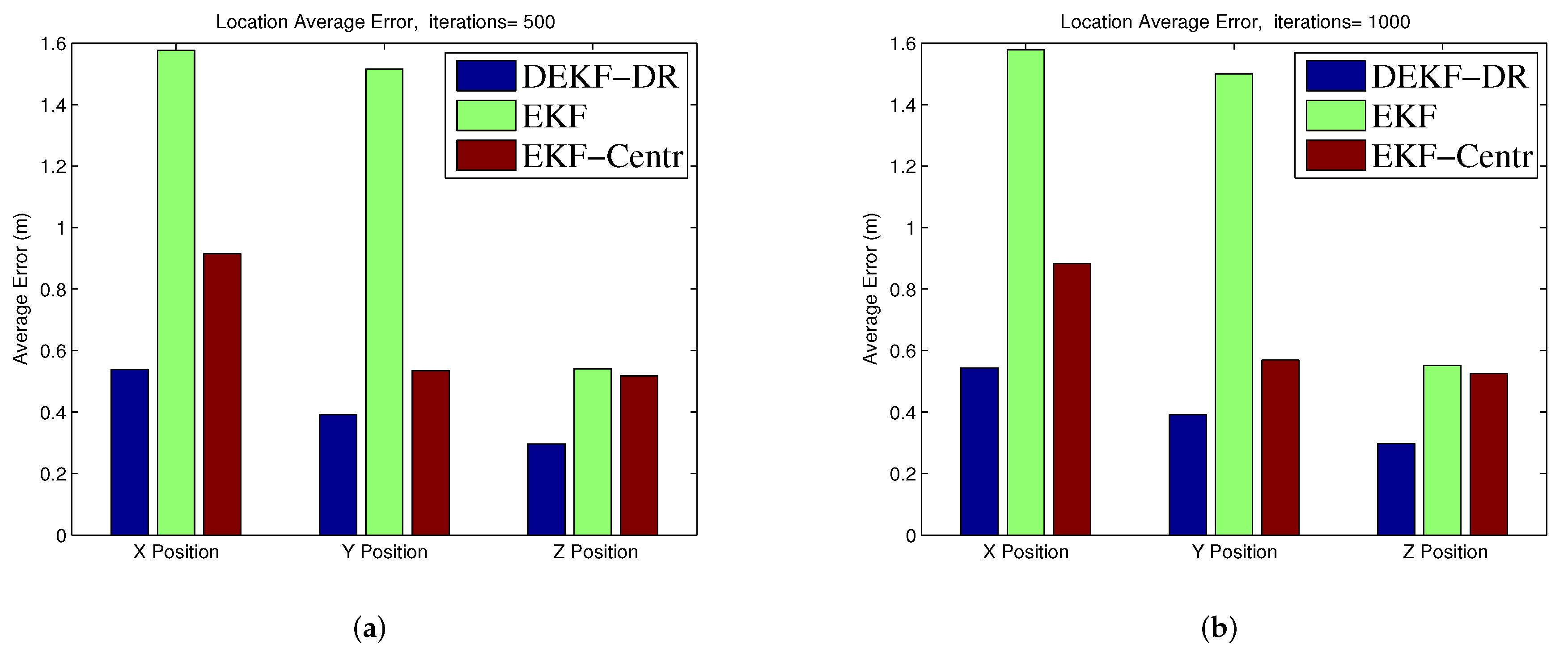
Figure 7b. Its median error is about 0.3 m when compared to 0.7 m and 0.4 m for the DEKF and the EKF-Centr, respectively. In order to measure the performance of the proposed method, we run the simulation 500 times and 1000 times, as reported in
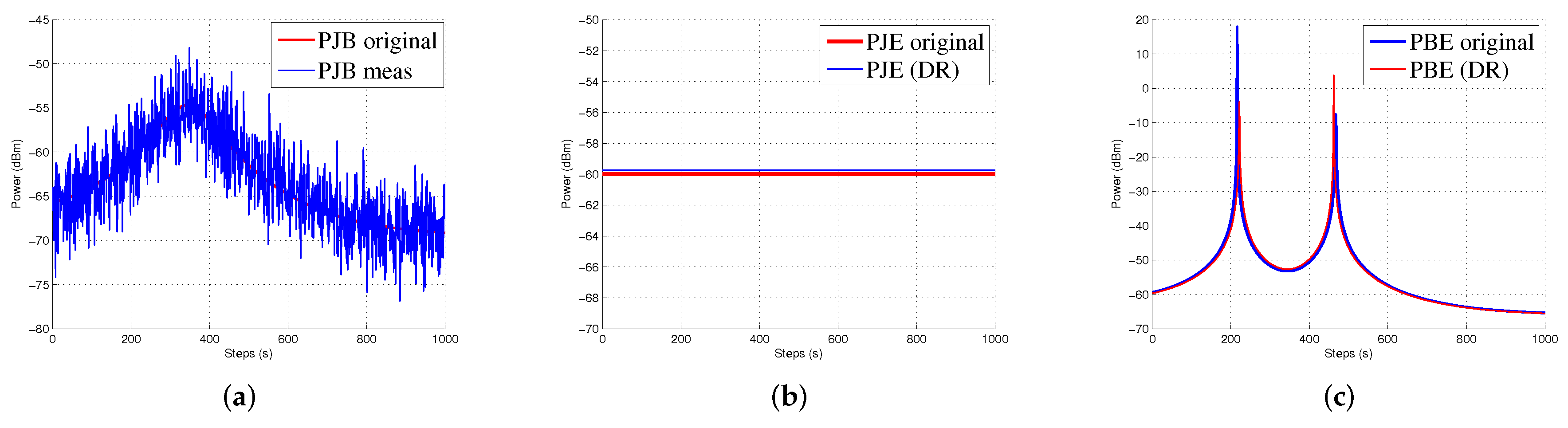
Figure 8a,b, respectively. The average error of the DEKF-DR is around 0.56 m. We estimated the jamming power at different points using the distance ratio as shown in
Figure 9. The jamming signal received by boundary node presented in
Figure 9a and jamming signal at the edge node and from the edge to the boundary node presented in
Figure 9b,c, respectively.