1. Introduction
Group communication is a special type of communication over wired and wireless networks wherein data are exchanged in the form of broadcast packets. During the last decades, many new technologies and concepts, especially based on the theory of group communication, have been implemented. Due to the flexibility and scalability of group communication, increasing attention has been drawn towards new applications such as vehicular communication, social media, digital media, control systems, billing systems, and infotainment in an Internet of Things (IoT) paradigm.
Vehicular communication technologies have been steadily developing and are recently playing an important role in future autonomous cooperative driving. Vehicle-to-everything V2X represents modern vehicular communication technology and intelligent traffic management for autonomous driving, where X represents anything such as infrastructure, vehicles, pedestrians, and roads. The two leading V2X technologies are long-term evolution-vehicle (LTE-V) technology and dedicated short-range communications (DSRC) technology. To exchange credentials and security information among the vehicles within the network, vehicles communicate through vehicle-to-vehicle (V2V) and vehicle-to-infrastructure (V2I) communication [
1]. In V2V communication, vehicles communicate with neighboring vehicles mostly via broadcast messages, whereas in V2I communication, vehicles communicate with roadside units (RSUs) or base stations via unicast messages.
The security problem of our concern is the establishment and maintenance of a secure V2X communication via broadcast messages in a dynamic and distributed key management fashion. In this paper, the V2X broadcast communication is referred to as V2X group communication. Recent studies have proposed several approaches for enhancing the V2X group communications security with improved availability, authentication, integrity, and nonrepudiation. However, only few solutions have been reported for confidentiality and privacy problems in V2X group communications, while their importance is rapidly growing. Therefore, ensuring data confidentiality and privacy in V2X group communications is considered a major obstacle for the widespread deployment of V2X communications. To provide a secure group communication in V2X, it is necessary to create, manage, and distribute the group keys securely with a low communication overhead [
2,
3].
Group key management algorithms can be categorized into two types: centralized and distributed group key management. While the centralized group key management is suitable for symmetric cryptography algorithms, it suffers from high overhead in computation, communication, and storage. The distributed group key management allows every node in the group to participate in the interactive computation of the group key. Hence, it distributes the key management load to all the group members, thereby providing a higher security level and fault-tolerance in integrity and confidentiality. In view of these benefits, we chose the distributed approach [
4].
Distributed key management methods are built without a central entity or authority. In these methods, each member of the group is equally trusted and required to participate in managing the keying material. Distributed key management in group communication includes the following operations: generation of cryptographic keys, exchange of keys, rekeying, and update of the keys [
5]. The distributed key management methods are commonly used in ad hoc and dynamic networks.
Several solutions have proposed hybrid architectures that are built with centralized and distributed key management methods. Hybrid architectures improve the scalability and performance of group key generation and distribution processes. Therefore, the proposed architecture can also be extended to a hybrid key management approach. However, the hybrid key management approach is beyond the scope of this paper.
Moreover, confidentiality is an important security requirement for V2X communications to ensure the group’s data privacy. Confidentiality guarantees that only the vehicles within the group can access the data, while nonmember vehicles cannot understand the secured contents [
1,
6]. Without providing a confidentiality mechanism, group members’ messages are particularly vulnerable to different attacks in vehicular networks. In these cases, the attacker can gather information about details such as the vehicle’s location and routes, and the user’s privacy. Moreover, the attacker may cause serious problems in the future.
In current V2X implementations, several applications require message confidentiality. Only safety-related messages do not contain sensitive information. Therefore, confidentiality mechanisms are unnecessary for them. However, messages from a multitude of applications, such as infotainment content distribution, sensor data sharing and security credentials management (key and certificate management) services, toll payments, internet services over RSUs, group information sharing, and billing, use a confidentiality mechanism (e.g., message encryption method) [
7]. In most of the previous approaches, message confidentiality was achieved by using the symmetric or the public key method.
Numerous academic studies have been conducted on the security and confidentiality requirements in V2X communications. Although previous studies have been able to meet most of these requirements for V2X communications, they are not fully safe. Additionally, most of them also suffer from low performance in terms of computation and communication overhead and high storage. Therefore, we propose a new encryption method for broadcast messages, which is integrated with the group key management algorithm for the confidentiality of V2X communications. We provide a detailed description and performance evaluations of the proposed method using different V2V communication test scenarios.
Our main contributions are as follows:
First, we propose a new matrix-based Scalable and Secure Group Key Management Method for V2V group communications. It enables fast and reliable key update mechanisms to highly dynamic vehicular networks.
Secondly, we propose a new lightweight encryption algorithm that can be easily integrated with the proposed group key management method. It provides group data confidentiality at a lower communication cost than conventional methods.
Then, we formally analyze the security strength of the proposed method and prove that it meets the security and privacy requirements.
Finally, we provide a performance evaluation of the proposed method using different V2V communication test scenarios.
The remainder of the article comprises the following sections.
Section 2 reviews related work on group key management and the confidentiality of vehicular communication networks.
Section 3 introduces the system model of the proposed group security method, while
Section 4 presents a description of the proposed group key management and message encryption technique for V2V group communications is explained in
Section 5.
Section 6 shows the security proof and analysis of the proposed method.
Section 7 analyzes the computation cost and communication overhead of the proposed method. Finally,
Section 8 concludes this paper.
2. State of the Art
Recently, several studies have been reported in areas related to V2X communication, which include broadcasting, routing, quality of service, and security and privacy. Protecting inter-vehicular communication is of utmost importance, since malicious attacks can cause serious casualties. However, it is significantly more challenging than general wireless communications, since the messages are primarily broadcasted and vehicles are highly mobile. Several V2X security methods have been proposed and standardized by organizations such as the Institute of Electrical and Electronics Engineers (IEEE), the European Telecommunications Standards Institute (ETSI), and the 3rd Generation Partnership Project (3GPP). As most of the existing methods are designed for unicast messages, which cannot properly protect V2X broadcasted messages, new studies have been reported in the field of key management, certificate management, identity- and blockchain-based security mechanisms, as well as group encryption and digital signatures based on the public key method.
We analyze selected research with a focus on our primary concern, i.e., group key management and encryption for V2X communications.
Relatively little research has been done on secure group communication and group key management. The previous group key agreement protocols have primarily used group Diffie–Hellman, CLIQUES, tree-based group Diffie-Hellman (DH), and elliptic curve DH methods [
4,
5,
8,
9,
10]. However, these protocols are not directly applicable in V2X networks because of implementation and deployment problems. The main drawback of these group key management protocols is their centralized key generation mechanism that requires key distribution from a server.
For example, Zheng et al. [
11] proposed two centralized group key management protocols, Chinese remaindering group key (CRGK) and fast Chinese remaindering group key (FCRGK) based on the Chinese remainder theorem (CRT). The proposed approach is suitable for small to medium-sized dynamically changing groups, with minimized storage and broadcast messages. However, the computation cost of the CRGK was very high, especially for the key distribution operation. In 2009, Zhou and Ou [
12] also designed a group key distribution algorithm based on the CRT. The main advantage of [
12] is that it reduces the key server’s computation cost during group key distribution. When the number of group members increases to a certain number, the key server computing time will decrease. The algorithm of [
12], however, incurs excessive costs in organizing group subtrees and computing root IDs in the group member subtrees.
In 2014, Niu [
4] proposed an Elliptic curve Diffie-Hellman (ECDH)-based scalable distributed key management scheme for secure group communication. It introduced group key establishment and rekeying algorithms that depend on changes in the numbers of members. In the method of [
4], distributed key generation architecture is used to reduce the key management load on the centralized server. Nevertheless, the computational cost and key size increase with the increase in group size. In addition, DH-based schemes are not an efficient solution for medium and large dynamic groups.
The protocols described above are not suitable for the rapidly changing dynamic structure of V2X networks.
In 2015, Park and Seo [
8] proposed a fast group key dissemination scheme for out-of-range V2I communications. The authors considered the issue of group key dissemination for the V2V-based group communication scenario, where vehicles cannot reach RSUs for a period. However, they assume that at least one vehicle has updated its group key via a prior V2I communication. In other words, that particular vehicle had V2I communication with an RSU for group key update. The rest of the vehicles in the V2V communication group may try to update their own group keys by requesting their neighboring vehicles within the group. However, this protocol requires long request–response messages to exchange keys, which results in a significant network overhead. In addition, only the key distribution center is responsible for generating, distributing, and managing all the keys for all the vehicles. Such centralized key management systems tend to impose substantial complexity and overhead on security establishment processes. In 2016, Vijayakumar [
13] proposed a dual group key management scheme for vehicular networks. In this scheme, vehicles are categorized into three classes with different authority levels to access the service. It employs CRT for the distribution and updating of a group key and thus, provides a lower computational cost than other related methods. However, key generation and management of this method require that new vehicles in the network must have a direct connection with the trusted authority (TA) for key generation and updating. This method, therefore, is not suitable for highly dynamic V2V communications that need to operate for an extended period without RSU.
In 2018, Li et al. [
2] analyzed various key generation and management methods based on a secret key, group key, and subgroup keys for vehicular communications. Additionally, they suggested an effective group key management protocol that provides message authentication and confidentiality. This protocol uses a cloud-based infrastructure to solve group formation, group key generation, and key distribution issues to reduce the computational complexity. Liu et al. [
14] designed a secure and efficient group key agreement scheme for vehicular ad hoc networks (VANET). They attempted to reduce the computational cost of key calculation and agreement by using powerful RSU and TA, which is similar to Li’s cloud-based infrastructure [
2]. The method described in [
14], however, requires vehicle registration and verification processes with TA for group key agreement. It also requires complex bilinearity for every member’s group key generation, which implies excessive computational time.
This discussion indicates that there are still many open issues in group key management in V2X communications that demand efficient approaches:
Most of the previous methods use the V2I or TA infrastructure for the group key management process. Moreover, they did not clearly define group key generation or updates. Additionally, they did not implement a mechanism for new vehicles to join and leave the V2V network.
In the previous methods, it is difficult and expensive to control the key update. Any change in the network structure or constraints requires the generation of a new key set. If the key update period is too long, the corresponding key may be exposed [
15]. However, if it is too short, unnecessary or meaningless key updates lead to excessive overhead for the key distribution process in a highly dynamic V2X communication environment.
Several previous methods require large key storage. For example, current V2X security standards like IEEE and ETSI require pre-stored key materials and certificates. This results in a large overhead on memory size and search time for an appropriate certificate. As storage in V2X nodes is generally limited, it is more desirable for each vehicle to generate temporary keys using only keying materials such as key generation parameters.
Attribute-based encryption (ABE) is regarded as an excellent candidate due to its ability to provide data confidentiality in a dynamic network. ABE methods can be classified as a public-key encryption method. In ABE, vehicles can share encrypted data based on attributes (e.g., vehicle ownership, vehicle types, location, and time stamp). Only those vehicles whose attributes comply with the access policy can generate a key and decrypt the encrypted data.
Huang and Verma [
16] proposed one of the first ABE-based confidentiality methods for vehicular networks as a flexible and secure key management framework. This framework provides an integrated solution to data access control, key management, security policy enforcement, and secures group formation in a dynamic vehicular communication environment. In ABE methods, all usable keys and ciphertext are labeled with certain attributes that are selected based on various road conditions; therefore, the encryption keys are dynamically updated when the road conditions change.
Afterward, Liu et al. [
17] proposed an extended ciphertext policy, attribute-based encryption (CP-ABE) algorithm with multiple authorities and authorized vehicles that exploit attribute-based signatures. Controlling access to network infrastructure usually requires frequent connection with the certificate authority via architectures like multi-hierarchical RSUs. In the paper by [
18], the authors proposed a secure billing protocol over an attribute-based encryption method for vehicular cloud computing. A lightweight attribute-based encryption protocol is proposed to guarantee access control to the purchased services, derived from the elliptic curve integrated encryption scheme (ECIES). This protocol is used for billing transaction confidentiality for the roadside cloud zone [
18]. In 2017, Xia et al. [
19] proposed an adaptive forwarding scheme for multimedia data privacy preservation in vehicular networks that employ attribute-based encryption based on ciphertext policy. Moreover, the authors used the CP-ABE delegation scheme with a decision tree algorithm to forward encrypted multimedia data. Additionally, RSUs dynamically decide whether to delegate decryption of messages before forwarding them to vehicles. A decision tree offers an efficient mechanism for nodes to easily maintain network parameters such as distance measurements, the exact number of vehicles, data types, and ciphertext size. However, this scheme takes a long time to operate, as it often involves RSUs managing the key materials. A revocable access control scheme [
20] using multiauthority CP-ABE to provide decryption and lower computation costs was proposed. This method can protect the network from static corruption of the authorities with low overhead of communications and computation for decryption. However, this method suffers from high computational complexity in setup, key generation, and encryption operations. In addition, its bilinear pairing is a complex and time-consuming operation. A hierarchical ABE is proposed by [
21] to provide a secure message access control framework in vehicular cloud computing. This framework generates persistent or dynamic attribute keys independently for individual vehicles. Thus, it allows vehicles to share their confidential messages with other vehicles that satisfy the predefined access policy.
This review of previous work reveals that the main problem with ABE-based methods lies in the overhead of handling a large number of attributes and ensuring their independence. If to reduce the overhead, we limit the number of attributes, then the system cannot properly resist attacks. Employing more attributes increases computational overhead in the ABE data encryption and decryption phases. By using strong encryption and decryption based on persistent attributes, Ref. [
21] decreases the computational overhead for access control of on-board units (OBUs) in vehicles.
Given the problems described, previous confidentiality methods are not commonly adopted for V2V communications. In summary, the key generation is controlled by the third trusted authority (RSU or TA) in all the previous methods. Furthermore, the computational complexity is unacceptably high, especially in the security initialization (setup) and in the message encryption process. Computational performance is regarded as one of the most important factors in determining the V2X security method. The V2X security overhead imposes both bandwidth utilization costs on the communication links and computational costs on the nodes. The computational cost depends on the underlying security algorithms and their associated parameters. Hence, the new framework must provide an integrated solution that can substantially reduce the computational cost in data access control, key management, security policy enforcement, and secure group formation, even under highly dynamic vehicular network environments.
In our paper, we propose a new group key management and group encryption algorithm that provides high speed and short latency. Due to the real-time behavior of V2X communication, long delays of messages can have a significant impact on V2X security applications. Therefore, this paper proposes a fast encryption and decryption algorithm for V2X networks that is used for key generation, secure certificate distribution, and secure multimedia confidential data communication among the vehicles and infrastructure. The paper covers only V2V group communication scenarios.
The proposed scheme introduces a matrix-based scalable and secure group key management method (2SGKM) and the message encryption (ME) method for V2V group communications. It enables a fast and reliable key update, as well as group data confidentiality at a lower communication cost than conventional methods.
3. Problem and Objectives
In this section, we discuss the problem background, introduce the system model and assumptions, and identify our design goals.
3.1. Background
The ITS communication security standards for V2X have been developed by dedicated working groups within the standardization organizations such as the ETSI TC ITS WG5 working group in Europe and the IEEE 1609.2 working group in the USA. The IEEE 1609 DSRC WG has developed a standard for secure wireless communications for safety applications and Wireless Access in Vehicular Environments (WAVE) management messages (IEEE 1609.2). In IEEE 1609.2, the service for message authenticity and integrity verification is based on digital signatures using the elliptic curve digital signature algorithm (ECDSA) [
22].
The IEEE 1609.2 standard defines the security data structures and secure message formats. It also describes the process of secure messages within the DSRC/WAVE system [
22,
23]. The existing V2X security frameworks are derived from general wireless networks and, thus, have critical drawbacks as listed below:
- 1.
Certificate distribution: The IEEE 1609.2 design allows a device to protect privacy by changing its certificate. The current standard uses peer-to-peer certificate distribution (P2PCD). However, P2PCD is not applicable to the group- or cluster-based communications with high dynamics and decentralized distribution. Notably, V2X communications are mainly conducted in a decentralized and ad hoc manner.
- 2.
Cryptomaterial management: Previous security frameworks usually have overly long certificates that are often longer than the message. This tends to cause a substantial performance loss.
- 3.
Key management: They use inefficient protocols for key generation, key lifecycle management, and key distribution, which have a large impact on secure communication performance.
IEEE 1602.2 describes the basic key management standard for secure WAVE services [
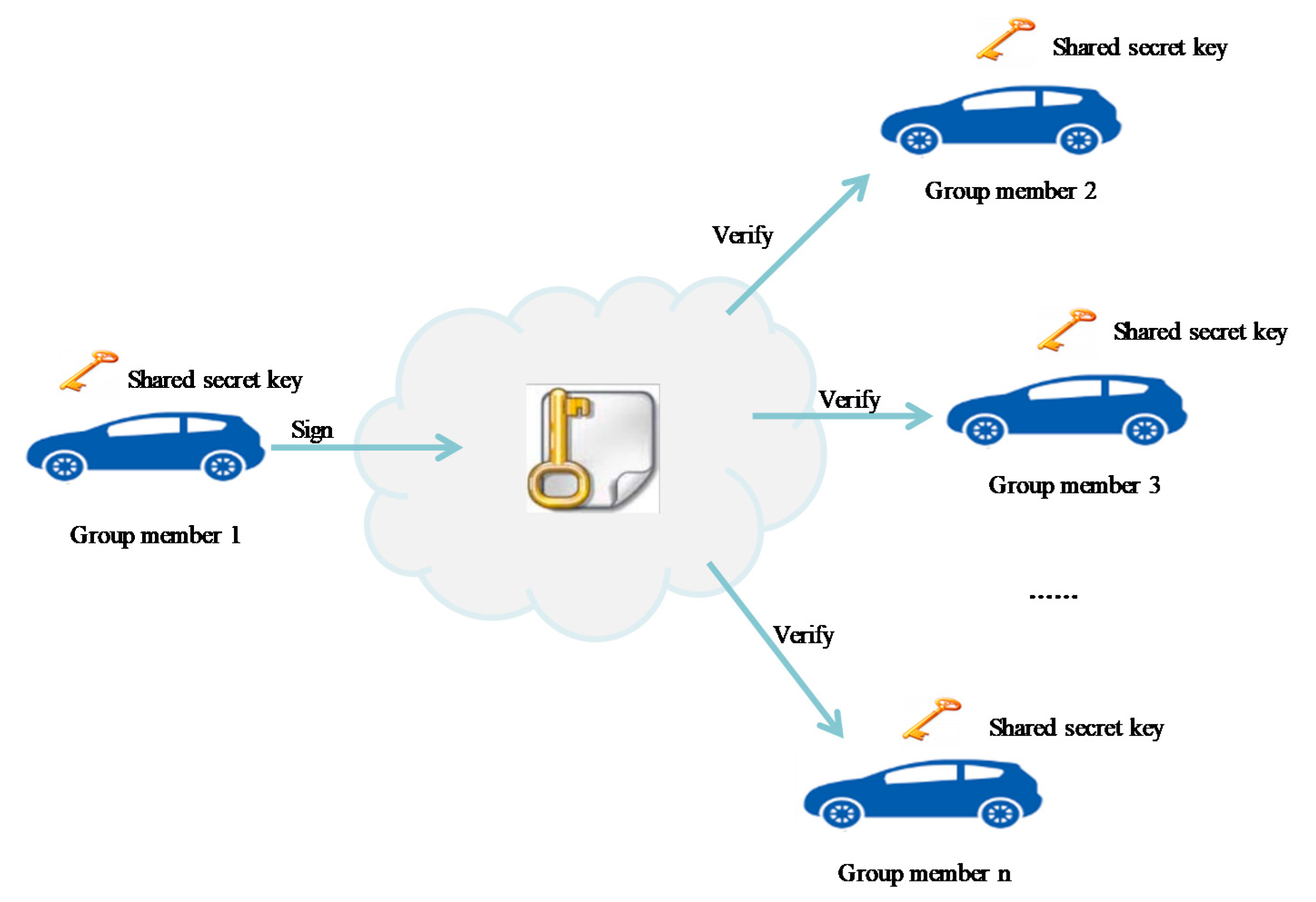
23]. Most of the conventional methods use a shared secret key that must be exchanged by all the nodes for data integrity verification and confidentiality in V2X communications. Although the shared key method can be used for broadcasting V2X messages, it requires that all vehicles exchange a common key, which can expose such methods to dangers of hacking.
Figure 1 illustrates such a shared key security protocol for V2X.
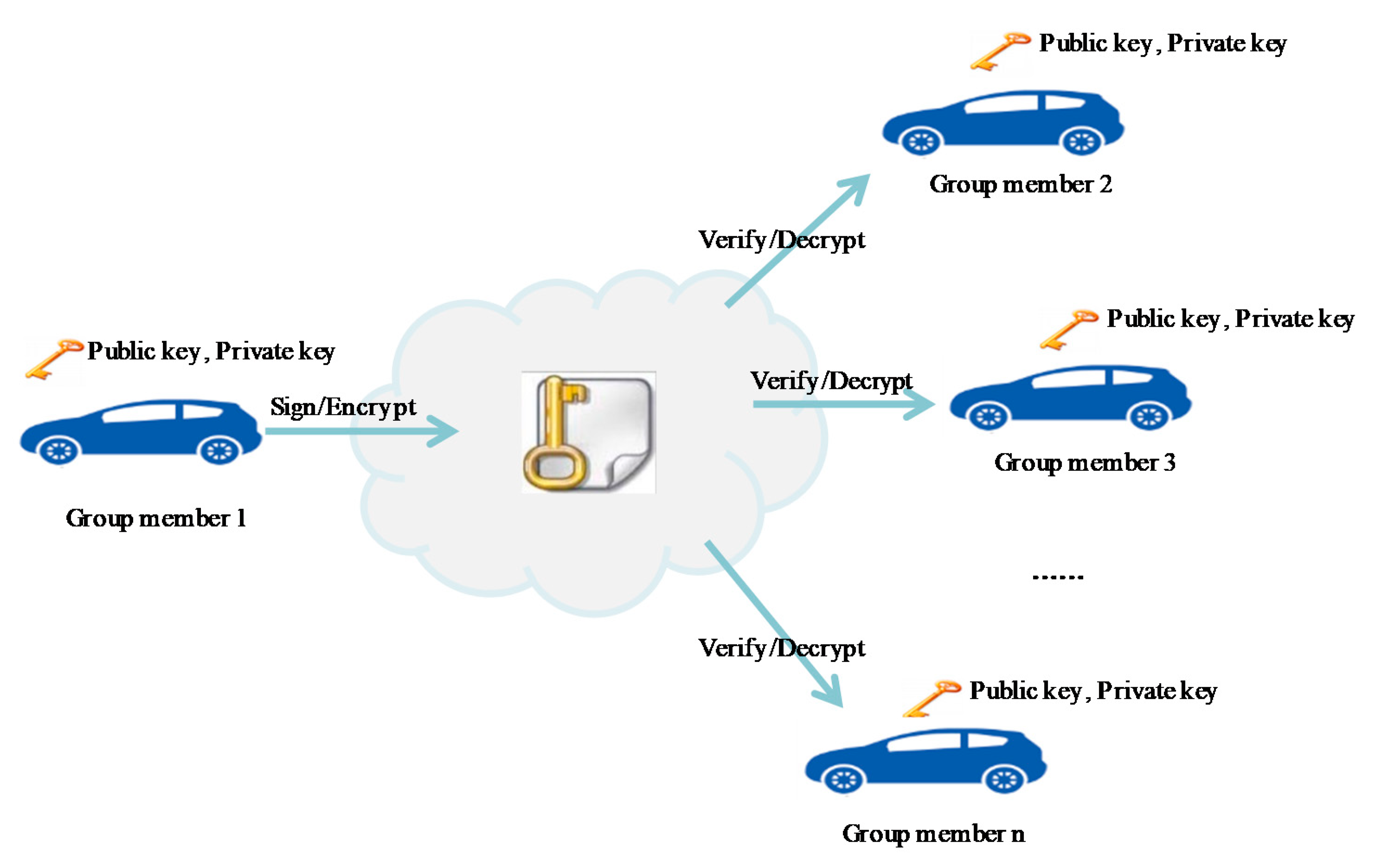
Another popular conventional method is public-key cryptography, which uses a pair of public and private keys for each node in the network [
22]. The main drawback of this method is that the single public and private key is broadcasted to all members or distributed with peer-to-peer communication between the members with certificates. If a hacker compromises the private key or a certificate, the hacker can listen to the communications and react to the movements of another member (
Figure 2).
With conventional security protocols, it is extremely difficult to guarantee that public and private keys are used only by group members and to prevent other malicious nodes from posing as members. It is also very difficult to determine how many members are using these keys to securely broadcast data in the network. Additionally, it is highly challenging to update the keys in conventional public key-based methods.
Our objective is to allow secure and confidential broadcast communications among network members. To explain our proposal, here we define the network of nodes within a one-hop neighbor as a group. We also define the nodes within a group as group members. One of the group members is elected as the group manager, who generates the group key and distributes it to the members
3.2. Proposed Model
To address the problems listed above, we propose a group key-based public cryptographic algorithm for V2V broadcast communication. The main idea of the proposed algorithm lies in the use of a single public key for multiple private keys for each member of the group.
Figure 3 illustrates an example of a group of n members, where a single group public key can be used for n private keys for all n members.
Our proposed 2SGKM provides fast asymmetric key cryptography that maintains a group public key and multiple private keys for each V2X network group. In each group, a group key is created and distributed by a group leader, thus providing efficiency in key distribution and maintenance. Groups are geodynamically formed within the leader transmission range, and keys are generated and updated based on the number of group members [
24].
The properties of the proposed algorithm are summarized as follows:
A single public key and multiple private keys are generated to support future data confidentiality and privacy in V2X group communication.
The group manager is only responsible for the generation and distribution of group public keys.
Each member generates its own private key; thus, private keys are never transmitted.
The same group public key is used by all member vehicles to encrypt messages.
Each vehicle uses its individual private key for decrypting received messages.
If a new member joins the group, other members maintain their private keys, while only the group public key is regenerated by the group manager’s vehicle. This reduces the computation and communication overhead.
The proposed method provides a faster computation time than the existing methods.
3.3. Problem Statement and Design Objectives
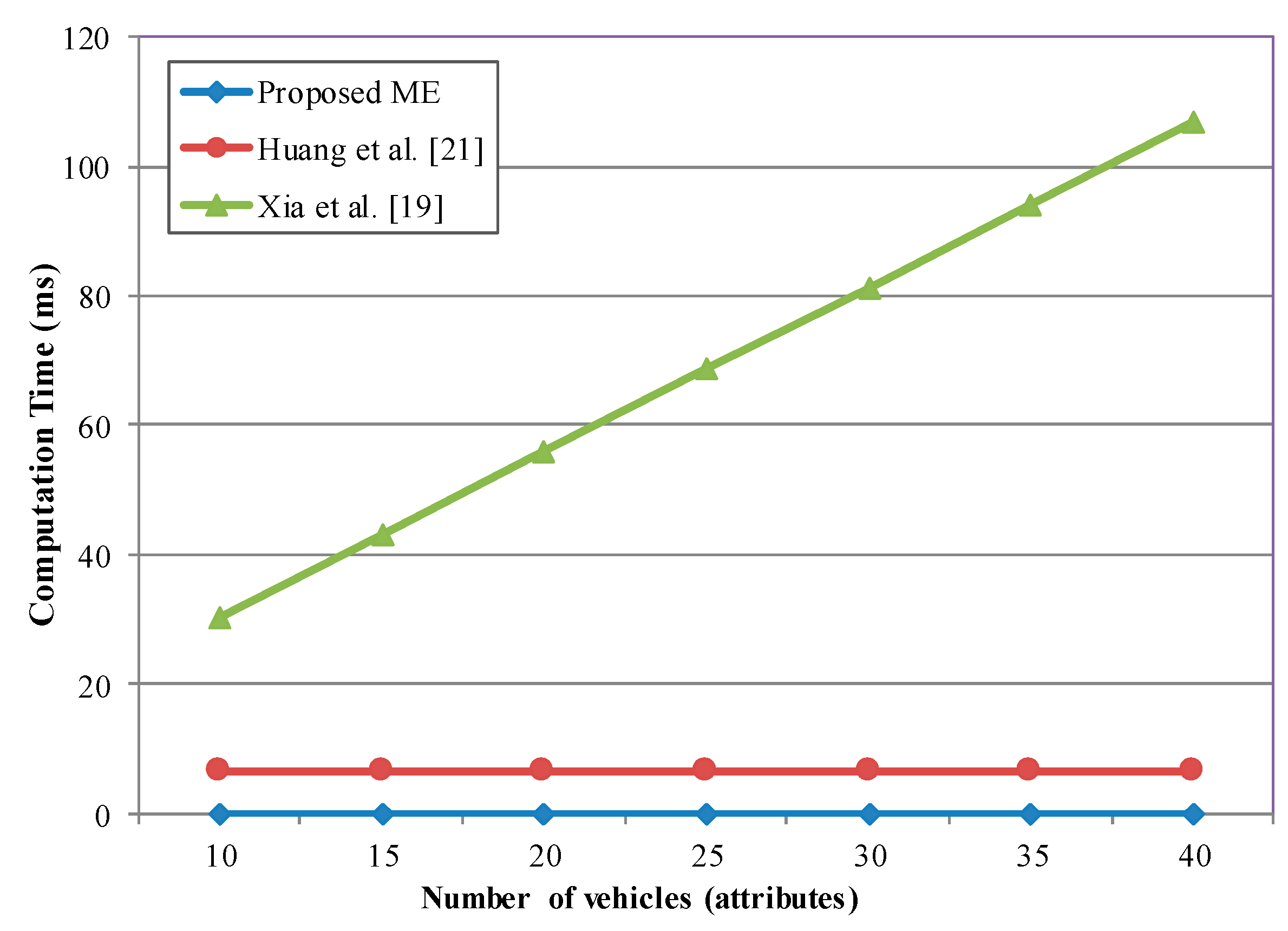
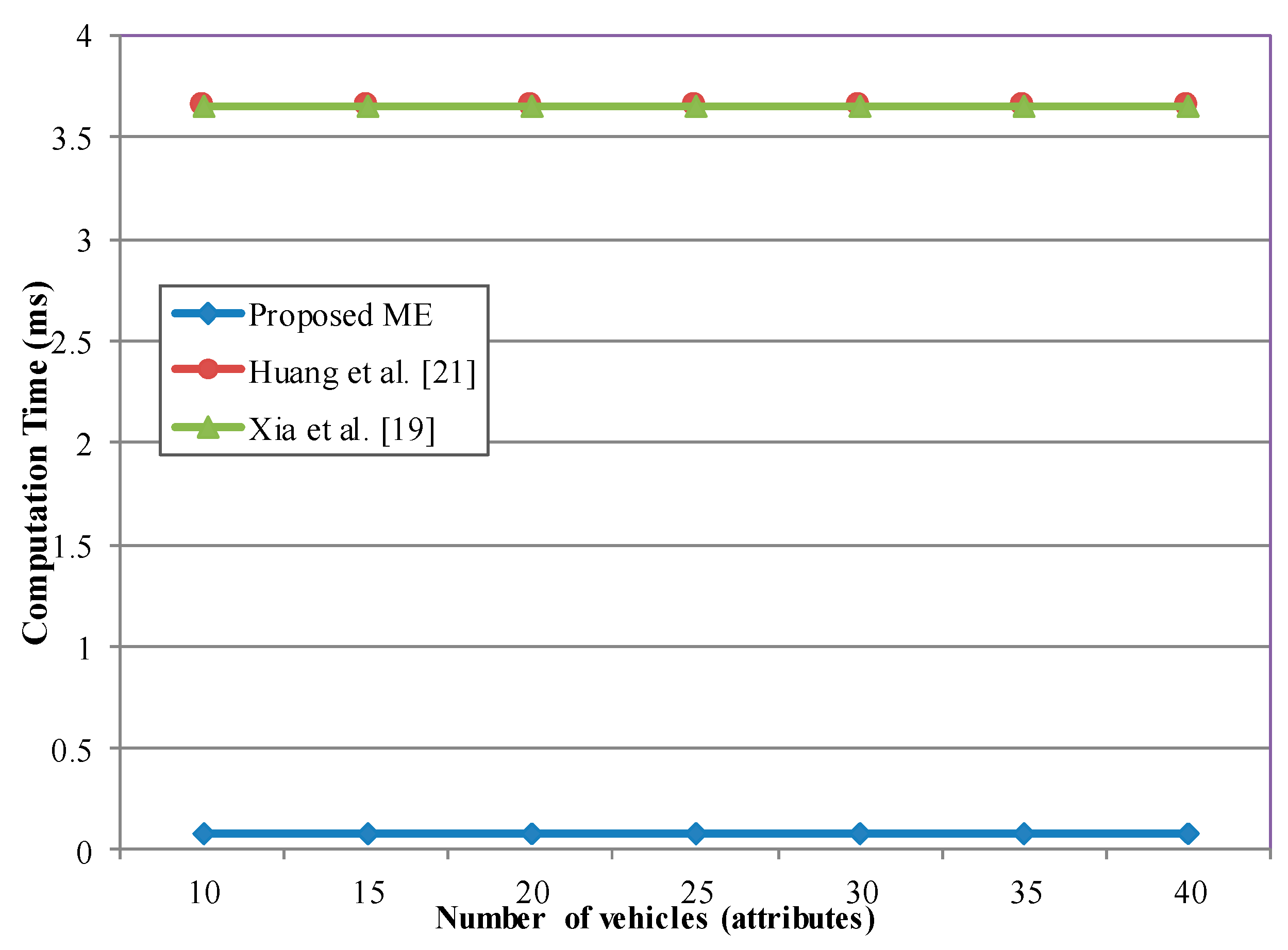
We know that for secure V2X communications, both security and privacy are essential. These issues are mainly solved with cryptographic operations. Cryptographic operations also place a large computational burden on receivers that wish to verify or decrypt these messages. According to IEEE 1609, a vehicle sends a basic safety message (BSM) within the time interval of 100–300 ms. Encryption and decryption of a message every 100 ms may not seem to cause significant overhead, even for the conventional public key-based schemes. However, in the case where the network has 50–200 vehicles within the communication range, each receiver needs to verify around 200–1000 messages per second, which often entails excessive computational overhead for the vehicle’s integrated system. Moreover, public key certificates have to be frequently verified as well. However, this operation is only used to provide message authentication and integrity. The integrity protection is not the focus of this study.
The requirements for network security are growing intensively with the development of new technologies and the deployment of more demanding applications to V2X communications. Signing and verifying messages are certainly not able to achieve fully secure communication. Confidentiality and reliability of messages and network members play an important role in safe driving today. Therefore, more scenarios such as the security credentials updating or multimedia contents distribution require message confidentiality, which is achieved with encryption methods. To our best knowledge, all currently available algorithms for public key infrastructure-based group communication schemes are far from satisfactory to this stringent time requirement. Moreover, cryptographic operations make the security protocol not scalable to traffic density. Therefore, the proposed cryptographic algorithms must be very fast so that the incoming messages can be processed and adapted to network dynamics [
25].
Hence, we propose a new scheme for key management and data exchange confidentiality (2SGKM and ME) in V2V communications that satisfies the following security and design requirements:
Secure key generation: Key generation for V2X group member vehicles is accomplished by the group manager vehicle. All shared key materials are encrypted with the initial group key in the communication.
Broadcast message encryption and decryption: Only legitimate entities can observe the contents of a communication. Any member in the V2X network group can decrypt each broadcast message encrypted by any member.
Identity privacy preserving: The identity of the vehicle must be anonymous for any participant in communications. Any third party cannot obtain vehicle’s true identity through the message from a given vehicle.
Traceability of malicious vehicles: Only the group manager vehicle can identify the identity of the malicious vehicle. The malicious vehicle can steal other vehicles’ group PID-data table contents, but cannot join to a group communication without the correct group membership.
Attack resistance: The proposed secure group communication scheme can resist many common attacks, such as the replay attack and stolen table attack.
Low communication and computational overhead: The security protocol for V2X networks must ensure real-time key management and encryption/decryption of many messages in a short interval.
3.4. Lattice-Based Cryptography
In this paper, we propose a scalable and secure group key management method for V2V communication. This method employs a high-speed matrix-based encryption algorithm that is classified as a lattice-based cryptographic construction.
It is known that lattice-based constructions have strong security proofs and their implementation is relatively efficient. The security of lattice-based cryptography is based on the hard problems on point lattices in m-dimensional Euclidean space Rm.
The following describes lattice-based cryptosystems in m-dimensional Euclidean space Rm.
Definition 1. A lattice is a set of points in m-dimensional space with a periodic structure. For example, given n linearly independent vectors b1, b2, bn ∈ Rm as basis vector, a lattice L in m-dimensional Euclidean space Rm generated by them is a set defined by Equation (1) [
26].
Here, n and m integers are called the rank and dimension of the lattice, respectively.
Definition 2. Lattice computational problems consist of the shortest vector problem (SVP) and closest vector problem (CVP), which are two fundamental challenges on the lattices.
SVP, one of the most important lattice-based computational problems, requires approximating the minimal Euclidean length of a nonzero lattice vector [
26].
Definition 3. (Shortest vector problem (SVP)) Given any basis matrix B ∈ Zm×n of a lattice L (B), find a shortest nonzero vector b ∈ L such that || b || = Dmin (L).
An integer lattice
L which satisfies
⊆
L ⊆
Zn for some integer
q is called
q-ary lattice where
q is an integer modulus. There are two hard problems, a small integer solution (SIS) and inhomogeneous small integer solution (ISIS), related to
q-ary lattices. The ISIS problem is more complex; solving this problem for a small solution is sufficiently difficult [
27].
Definition 4. (Inhomogeneous small integer solution (ISIS)) Given an m × n integral matrix A ∈with integer modulo q,
a real constant β and a random vector y∈find a vector x ∈ Zn\{0} such that Ax = y (mod q) and || x || < β [
27].
These ISIS problems have a number of solutions for their appropriate equations. Finding as a small solution, however, is as difficult as the worst-case problems in lattices.
These problems are regarded as extremely hard to solve in reasonable computation time, even with approximation factors that are polynomial in
n, and even with a quantum computer. Therefore, lattice-based cryptographic constructions provide a promising future for the postquantum cryptography [
26]. Since the proposed matrix-based method falls into a class of lattice-based cryptography, it can provide high level of security.
4. Proposed Group Key Management Method
The main objective of the proposed solution is to develop a matrix-based scalable distributed group key management scheme for V2V group communication that works with a single group public key and multiple private keys for all vehicles. In the following subsections, we describe the main elements of the proposed algorithm: V2V group organization, key generation and distribution, and key updates.
This paper focuses on V2V group communication. It is assumed that every vehicle is equipped with an OBU device. Additionally, each vehicle’s OBU contains a security module that is built based on the proposed scheme and its information never disclosed. The notations used in this paper are listed in
Table 1.
Each vehicle maintains a pseudo identity data (PID-data) table in its security module that contains a set of PIDs and key generation and encryption algorithm parameters, as shown in
Table 2. Vehicles always update their tables from trusted authority (TA) once they get into the radio range of an RSU. To protect the privacy, it is necessary that vehicles do not have unique pseudo identity. They use one of the pseudo identities stored in the PID-data table.
In the proposed method, the real identity of the vehicles is hidden and not used in V2V group communication.
4.1. Group Establishment and Group Manager Election
A group of vehicles is established by selecting vehicles moving in the same direction within the transmission range. There are various group establishment methods. Hence, we assume that one of the existing methods can be applied to establish a group.
Once a group is established, a group manager vehicle is elected, which is responsible for the generation and distribution of the public and private keys to be used in the group. For the group manager election, the existing clustering algorithms can also be used, which elects a vehicle as a group manager (cluster head) among the group members
mi [
28,
29,
30,
31]. In addition, a vehicle regarded as most stable and trustable is elected as a group manager by the election algorithm. However, a complete study of the group manager election is beyond the scope of this paper.
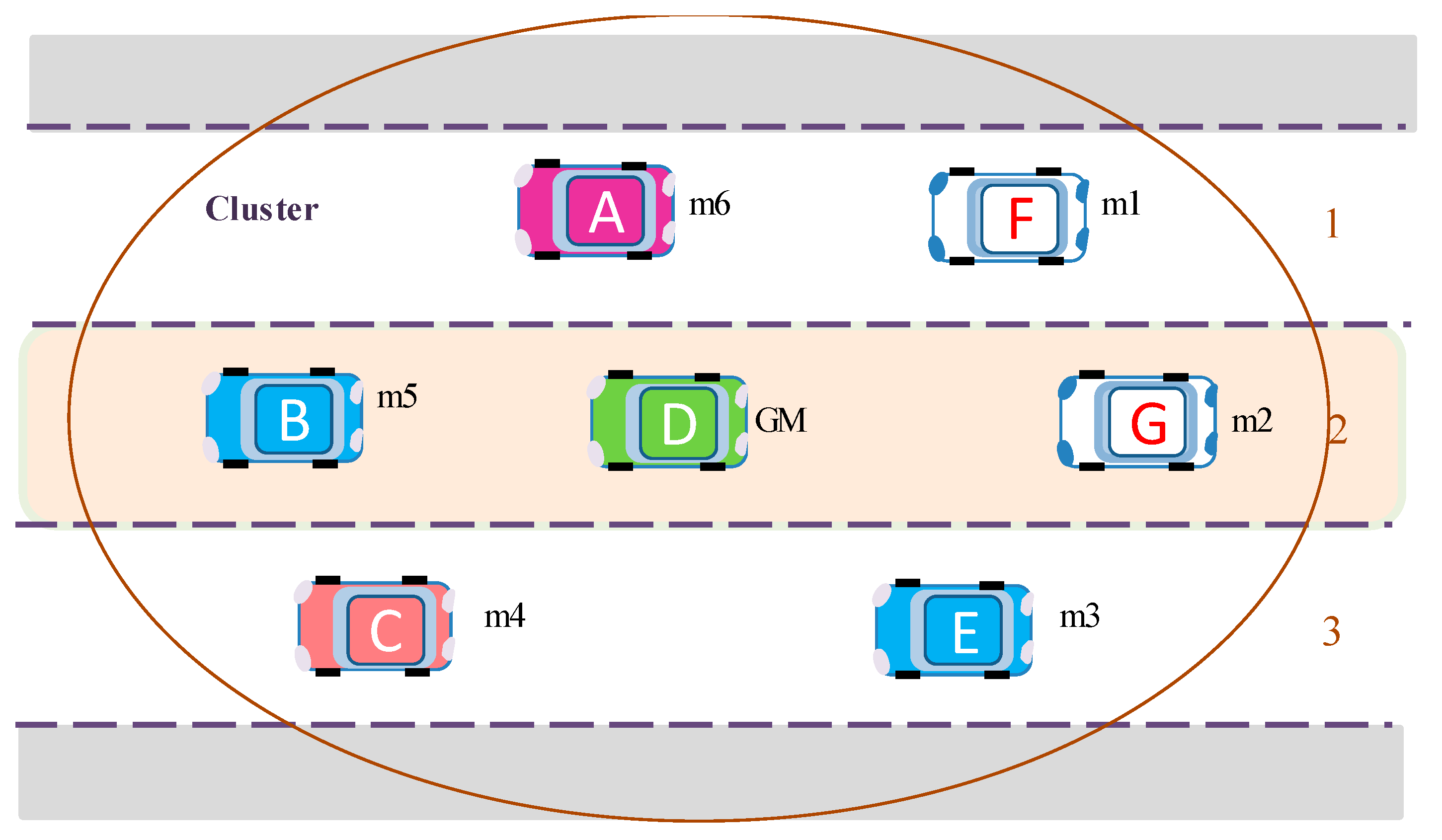
Figure 4 shows an example of group establishment, where a group (cluster) is constructed and vehicle D is elected as a group manager (GM).
4.2. Group Key Generation
All the vehicles in the group are operating the proposed cryptosystems. The individual vehicles generate a different ternary seed matrix
AS defined by Equation (2) as an
n ×
n size ternary matrix whose elements
ann are randomly chosen.
where
(mod
p) ≠ 0 with a small prime number
p. The elements
ann of matrix
AS are ternary values randomly chosen from [−1,0,1]. The variable
p is chosen to satisfy gcd (
p,
q) = 1, and to reduce the complexity of the function by module
p.
The group manager (GM) maintains the information of all the members (
PIDi, member’s matrix key data for group key generation, location (joined), and the request time to join the group) by periodically exchanging vehicle information messages such as a basic safety message (BSM) of IEEE 1609.
PIDi is a randomly selected unique 8-byte identity number in the PID-data table that is generated by the TA or the service provider in vehicle registration [
32,
33]. The member’s matrix key data for group key generation
Di is computed as follows:
Based on the matrix key data of all members, GM generates a group public key Gpub for broadcast communication in the group.
Figure 5 illustrates the initialization step of the proposed group key algorithm. Suppose the group comprises six members,
m1,
m2,
m3,
m4,
m5,
m6, and vehicle D is elected as GM. Each vehicle generates its own
seed matrix, which is used for generating public and private group keys.
The key generation for the group is conducted by the following process:
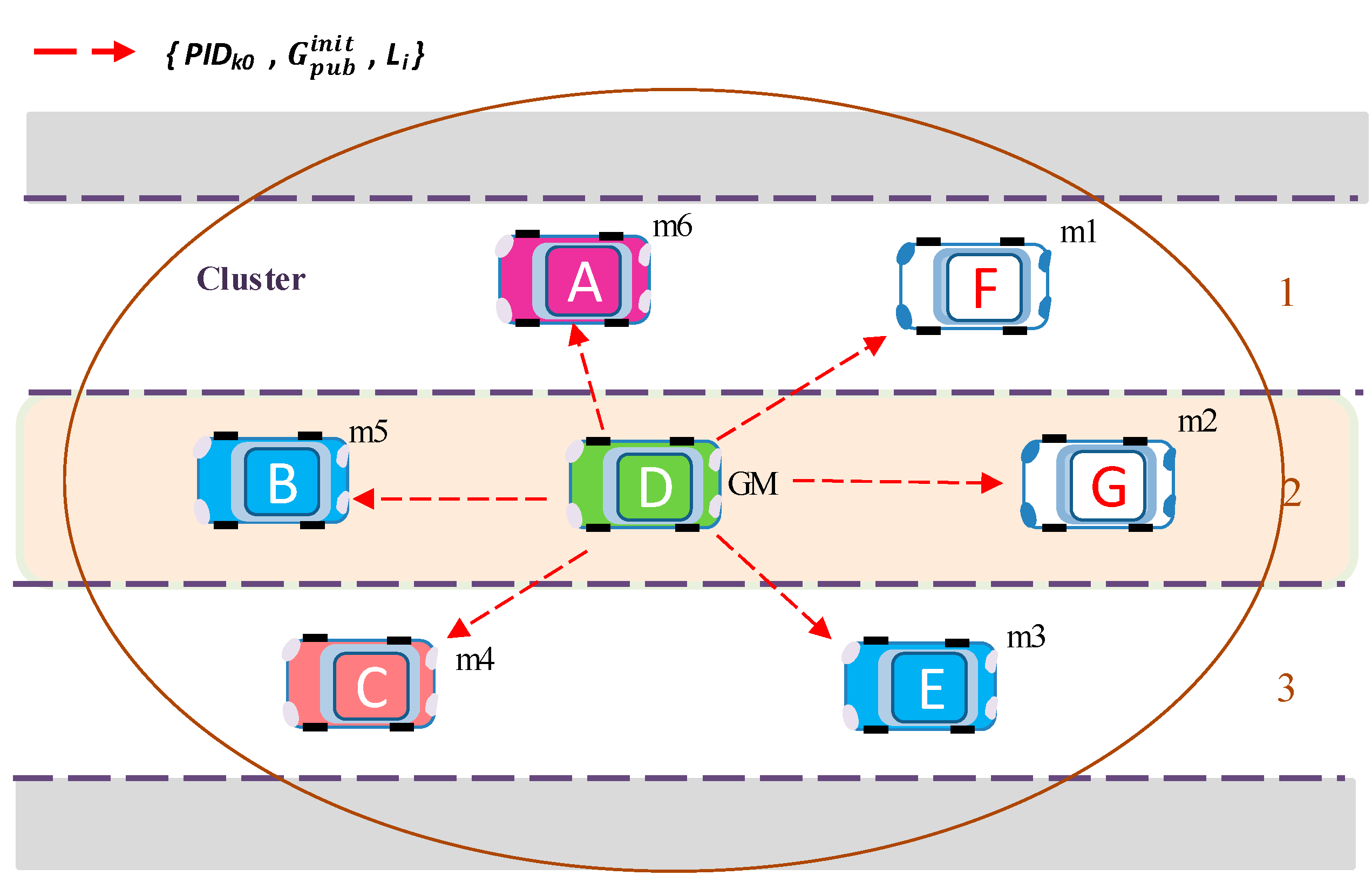
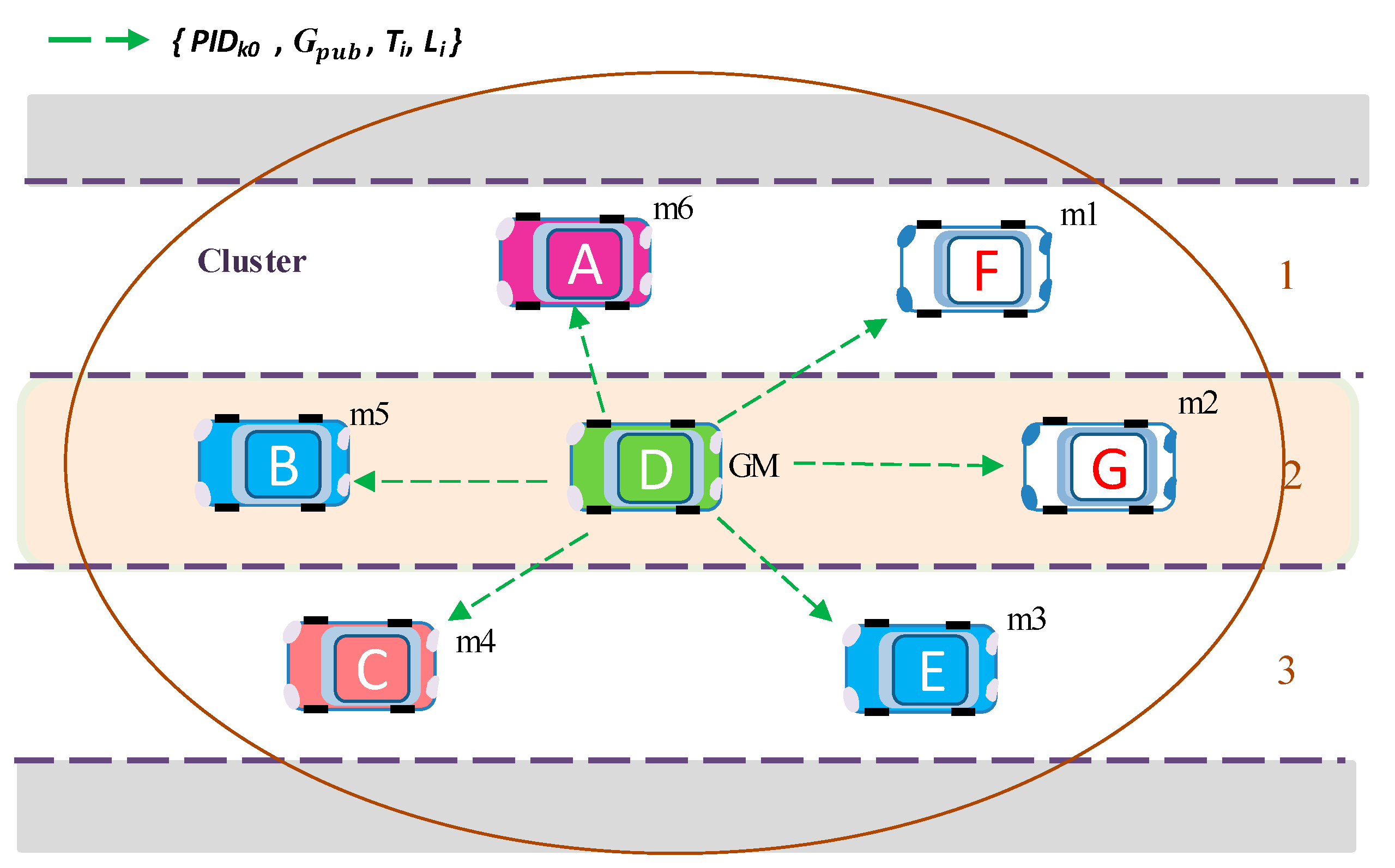
GM generates the initial group public key
and broadcasts to all members of the group with
PIDk0 (
Figure 5). This key is then used by group members to encrypt key request materials. GM’s initial group public key is calculated with Equation (4):
Here,
DGM denotes the GM’s matrix key data for group key generation. In addition,
g is a randomly generated ternary matrix of the same size as matrix
. The matrix
g is generated by each GM for its group and is used to distinguish the groups.
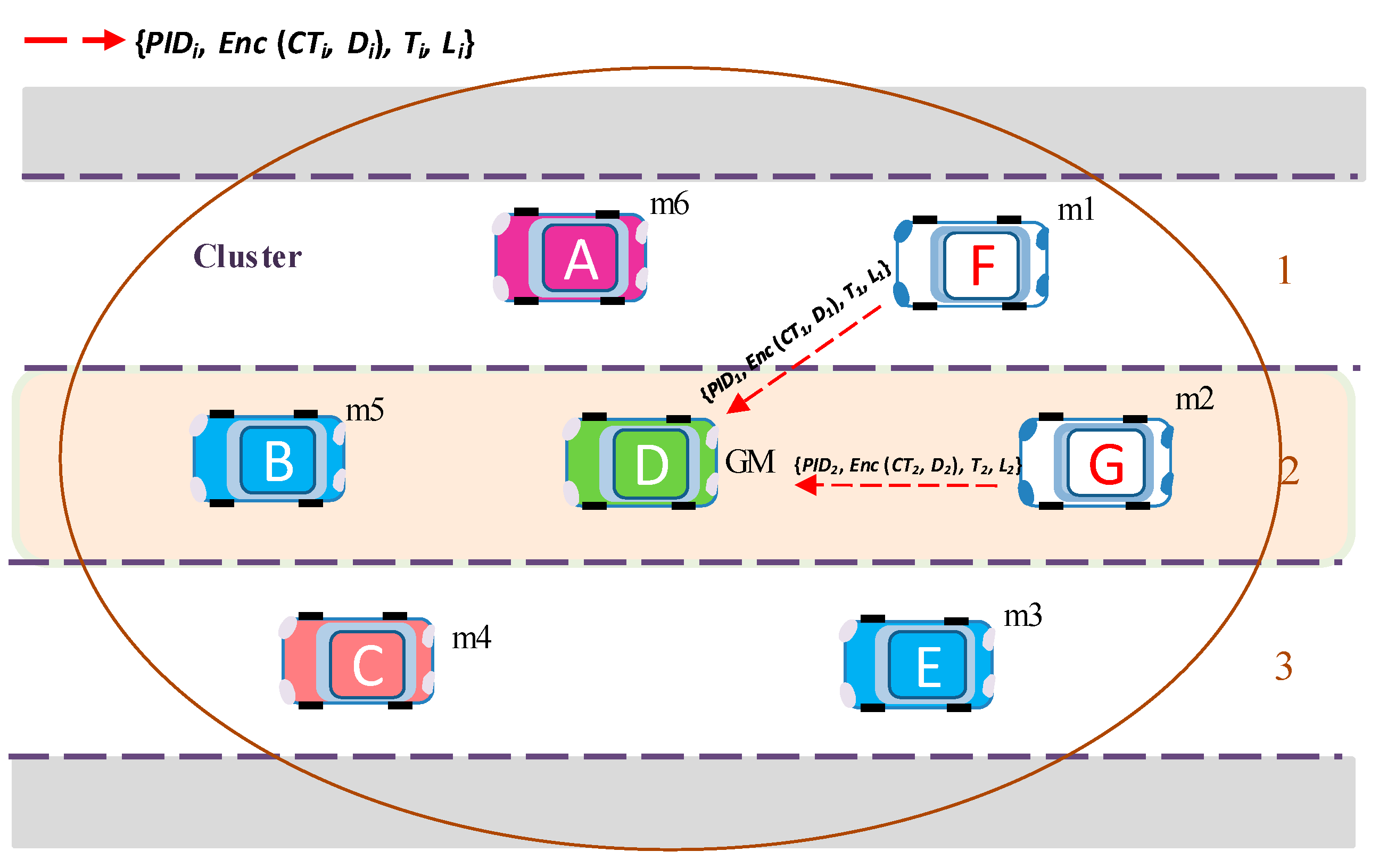
After receiving the initial group public key and PIDk0, group members configure security parameters with PIDk0 from PID-data table, and start generating key request messages Mi = {PIDi, Enc (CTi, Di), Ti, Li} using this key. Here, CTi is contents type. The contents type CT is attached to the message by the sender, before encryption, and used to check the application type by the receiver after decryption.
For example, member
m1 generates its own ternary seed matrix
(
), computes
D1, and makes its own key request message with encrypted contents expressed by
M1 = {
PID1,
Enc (
CT1,
D1),
T1,
L1} and sends it to GM.
PIDi is randomly selected from
PID1,
PID2,
PIDk. The message encryption and decryption algorithms are explained in
Section 5.
Similarly, member m2 generates key request message M2 = {PID2, Enc (CT2, D2), T2, L2} encrypted with the initial group key , and then m2 sends M2 to GM.
All other
mi members near group manager GM generate
Mi and send the key request messages to GM (
Figure 6).
After receiving key request messages from all members who intend to join the group, GM checks the PIDs, decrypts the messages and creates the information table for all members. GM saves the Media Access Control (MAC) address of a newly joining member and verifies whether the new member is a legitimate one with correct PIDi. Based on the information table, GM in a V2V environment can stop a malicious vehicle from joining or rejoining the group. Afterward, the GM vehicle calculates the group public key Gpub using the information for secure group communication.
The GM vehicle uses Equation (5) to calculate the group public key
Gpub:
Here,
k indicates the number of members, while
DGM and
g are defined in Equation (4).
Subsequently, GM generates a key response message, encrypted with the new group public key
Gpub and broadcasts it to all members with an encrypted information message (
Figure 7). This message contains the
PIDi and the new group public key with the data contents.
Each vehicle generates its own private key
Prmi using the ternary seed matrix
(
), which is used to decrypt the received messages. The private key is calculated by Equation (6), which takes the inverse of the ternary seed matrix followed by a modular operation with
p, which is a small finite field prime integer.
Here, we calculate () as follows: () = (())−1 (mod p).
Members use their private keys to decrypt the received messages, while each member uses the group public key Gpub to encrypt their transmitted message.
4.3. Rekeying Mechanism
To provide back-and-forth secrecy in group communication, the proposed scheme must be scalable to network changes. Any change in group membership invokes the rekeying process of the group public key while satisfying the requirement that the previous group public key is still active for existing members. Contemporary research suggests that rekeying should be performed in three cases:
When a member wants to change its key material to protect its privacy and credential;
When a new member joins the group;
When a member leaves the group.
4.3.1. Group Rekeying Mechanism
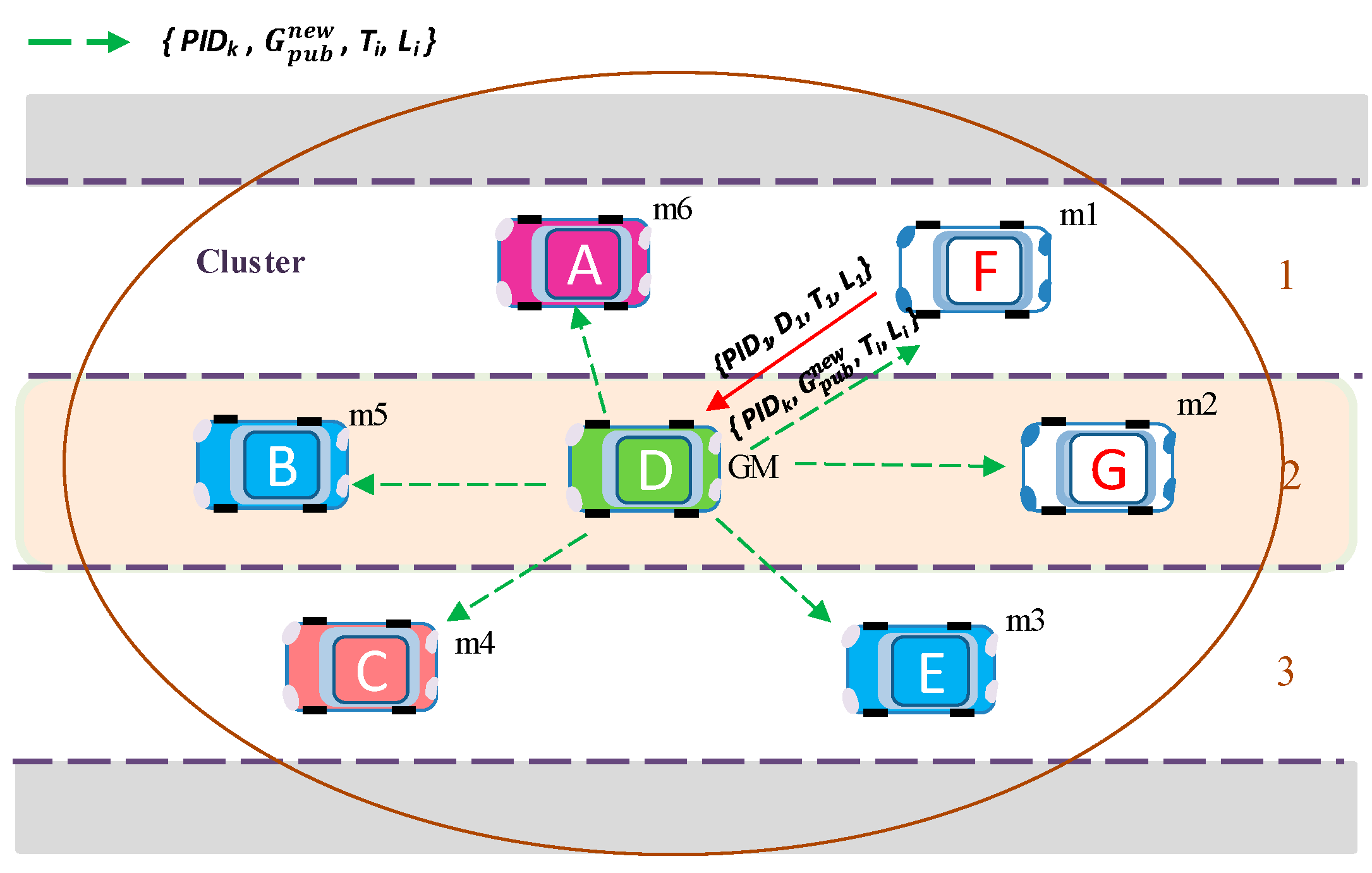
If the
i-th member vehicle wants to change its key material, it sends an encrypted key request message
Mi = {
PIDi,
Enc (
CTi,
Di),
Ti,
Li} to the GM with new matrix key data for group key generation
Di and an appropriate
PIDi. Afterward, GM generates a new group public key
using Equation (5) and broadcasts
to the group in an encrypted message. Upon receiving a new group public key
, the group members update their public key for future message encryption. For example, in
Figure 8, (previously joined) existing member
m1 sends a new matrix key data
D1, and then GM updates the group public key
Gpub by a new group public key
.
The process of updating a new group public key only requires two message exchanges with fast computation of a new group key, whenever any member (or group manager) wants to change their key materials. In addition, the updated group public key is broadcast to all members at once. Therefore, the rekeying process involves little overhead in processing and transmission time.
4.3.2. Mechanism for Joining Members
When a new member joins the group, the group public key must be updated to provide backward-compatible security processing. Without a rekeying process, new members cannot access the secure group communications and, thus, cannot receive any data from the group.
Assuming that
k members have joined the group, for secure group communication, every message carries group public key
Gpub. Nongroup vehicles that are near a group vehicle can also receive messages but cannot decrypt the secret contents. However, they may be allowed to extract the location of the vehicle and the public key from the message group. Suppose that a new member
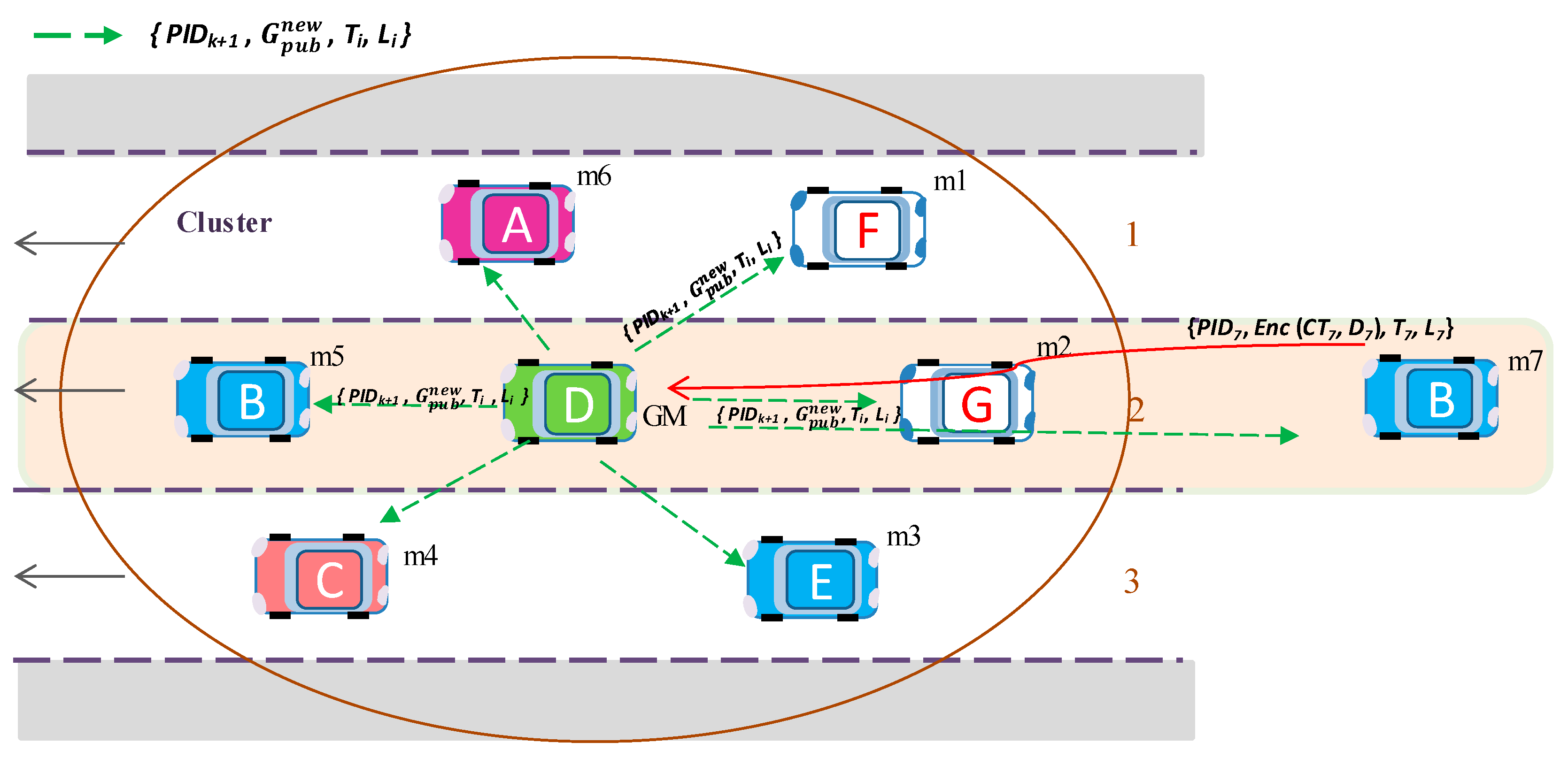
mk+1 wants to join the group. As described above,
mk + 1 generates a key request message encrypted with a group public key and sends it to GM. The GM generates a new group public key
with Equation (7):
Afterward, GM generates a new key response message that is encrypted with , and GM then broadcasts to the group the encrypted information message. The information message consists of the PIDk + 1, new updated group public key , and the encrypted data contents.
Figure 9 illustrates how a new member joins the group and updates the group key. First, member
m7 sends new matrix key data
D7 to join the group. Afterward, GM generates a new group public key
and broadcasts it to the group.
Some group members may not receive due to collisions or channel fading. In such cases, they can continue using the old group public key Gpub. Such members using the old key, as well as members using the new key, can decrypt the messages in the group. Furthermore, all old members can also decrypt messages from new members encrypting messages using the new key. However, when some members encrypt the message using the old key, the new member cannot decrypt this message.
As described above, existing group members can also use old and new public keys for message encryption after member joining. When a new member joins the group, the member sends matrix key data for group key generation. Moreover, this member’s matrix key data is still a group public key container. In any case, these data are saved until the member leaves the group. When another member joins, GM generates a new key with the existing and new member’s matrix key materials. In that case, the old and the new group key are applied to previously joined members.
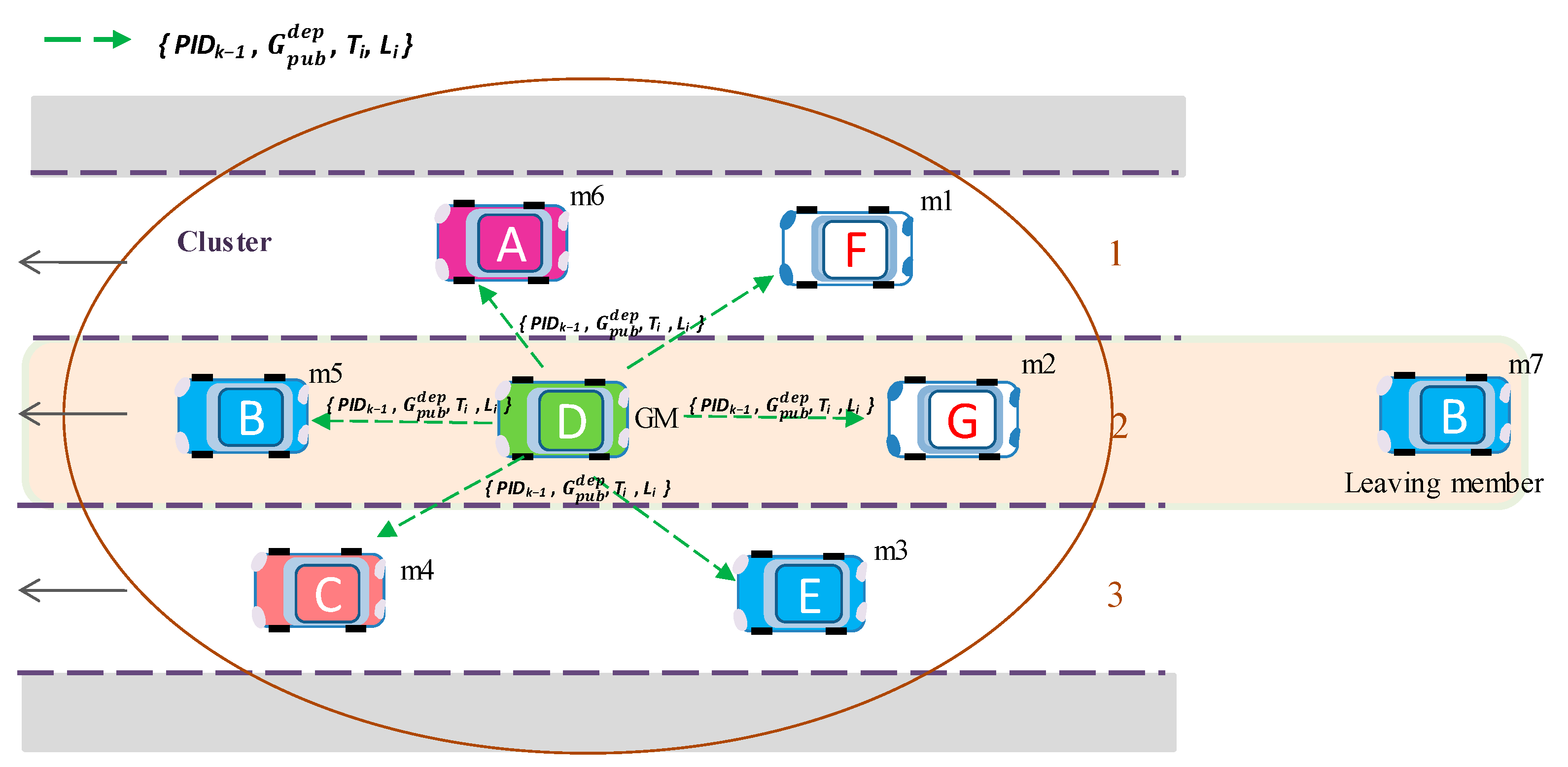
4.3.3. Mechanism for Departing Members
In the case of any vehicle leaving the group, the group public key must be updated to preserve the forwarding secrecy. In the method, a special forwarding secure encryption scheme is proposed for V2X communications. This scheme adds a group key update algorithm in a member departure case, which ensures that members can use a new group public key with previous private keys in each member’s departing period to encrypt it and thus, avoid the problems caused by key exposure. Clearly, due to the unique nature of this algorithm, the departed members would not affect the group security. A new group public key ensures that the departed member cannot decrypt messages and its matrix key data are no longer valid. After member departure, some members may not receive the new generated group public key from GM. In this case, the remaining members can continue using the old key. However, it is more efficient to update the group public key for forwarding secrecy.
In the proposed method, GM checks the existence of group members in communication. If GM discovers that any member
mk is not participating in the communication, GM declares the departure of
mk and deletes
mk from the information table of members. Afterward, GM performs a rekeying process to update the group public key
(key updated with departing member) as follows:
Figure 10 illustrates an example where member
m7 is leaving the group and GM generates a new group public key
and broadcasts it to the group.
In the departure process, the private keys of existing members do not need to change. Therefore, use of the old group public key is allowed. However, members may be exposed to security attacks if the old key is used for an extended period. In this case, an intruder may compromise the old key and transmit corrupted messages.
For the members that leave the group, we do not require a special message like a departure request message. In the proposed method, we utilize a local dynamic map (LDM) updated by all the members and the group managers on the road. If GM discovers a group member moving out of its communication range in LDM, GM waits for enough departure time Tdepart before deleting the member. After waiting Tdepart, GM updates the group public key with key . By using Tdepart in this way, we can avoid too frequent updates of the group public key.
If the GM vehicle plans to leave the group, it selects the new group manager vehicle based on the information table. We assume that a newly trusted GM receives the information table from the previous GM via a secure channel. After that, the new GM starts to control the secure group communication.
5. Encryption of Broadcast Messages
In this section, we explain the secure message broadcasting operation from GM to vehicles and between member vehicles in a group. To improve confidentiality, the messages should be exchanged in an encrypted form so that unauthorized or nonmember vehicles cannot access the messages. The steps involved in the secure message transmission in vehicular communications are described below.
Message Encryption (ME): In our paper, we propose a high-speed matrix-based message encryption algorithm with low latency. This algorithm is designed by using lattice-based cryptographic construction. Lattice-based cryptography is a generic term for constructions of cryptographic primitives that involve lattices, either in the construction itself or in the security proof. Lattice-based constructions are currently important candidates for postquantum cryptography. Unlike more widely used and known public-key schemes (RSA (Rivest-Shamir-Adleman), Diffie–Hellman, bilinear pairings based or elliptic-curve cryptosystems), which are easily attacked by a quantum computer, some lattice-based constructions appear to be resistant to attacks by both classical and quantum computers. Furthermore, many lattice-based constructions are more secure under the assumption that certain well-studied computational lattice problems cannot be solved efficiently.
The proposed algorithm is an asymmetric encryption algorithm supporting a single public key for the group and multiple private keys for group members. Message encryption starts by generating a group public key for the joined member vehicles.
Given a message
msgi of a member
mi, the encryption of
msgi = {
P1,
P2,
Pk,
PK} using group public key
Gpub is represented by Equation (9).
Here,
Cimsg = {
C1,
C2,
Ck,
CK} is the resulting cryptotext, while
r indicates a square matrix of order
n that is randomly generated in the interval [−1, 0, 1]. In addition,
msgi is the payload for encryption of member
mi with block containers {
P1,
P2,
Pk}.
An encrypted message, supplemented with the encryption timestamp and vehicle position information
Mi = {
PIDi,
Cimsg,
Ti,
Li} is broadcasted to the group members, as illustrated by
Figure 11.
Message decryption: Upon receiving encrypted messages Mi = {PIDi, Ci, Ti, Li}, vehicles in the group decrypt the message using their private key Prmi and check its usability with the timestamp and other parameters. Only valid messages are loaded into the applications.
For any member of the group, a received cryptomessage
Cimsg = {
C1,
C,
Ck,
CK} is decrypted by the decryption process as follows:
where
Pk′ denotes the resulting decrypted message and
Prmi = {
(
),
(
)} is the private key of the
i-th member. Here, we calculate the total decrypted payload with
msgi′ = {
P1′,
P2′,
Pk′,
PK′}.
Using the encryption and decryption process based on the group key generation method described above, the proposed method can substantially improve vehicular communications security and, thus, ensure the security of both autonomous and regular vehicles.
Finally, the overall flow of message exchanges between the group manager (GM) and group members is shown in
Figure 12, including the flow of message encryption and decryption.