CNN with Pose Segmentation for Suspicious Object Detection in MMW Security Images
Abstract
1. Introduction
2. Related Work
3. The Proposed Algorithm
| Algorithm 1 Convolution neural network (CNN) with Pose Segmentation. |
| Input: Complete MMW human images P. Start:
Detection result: . |
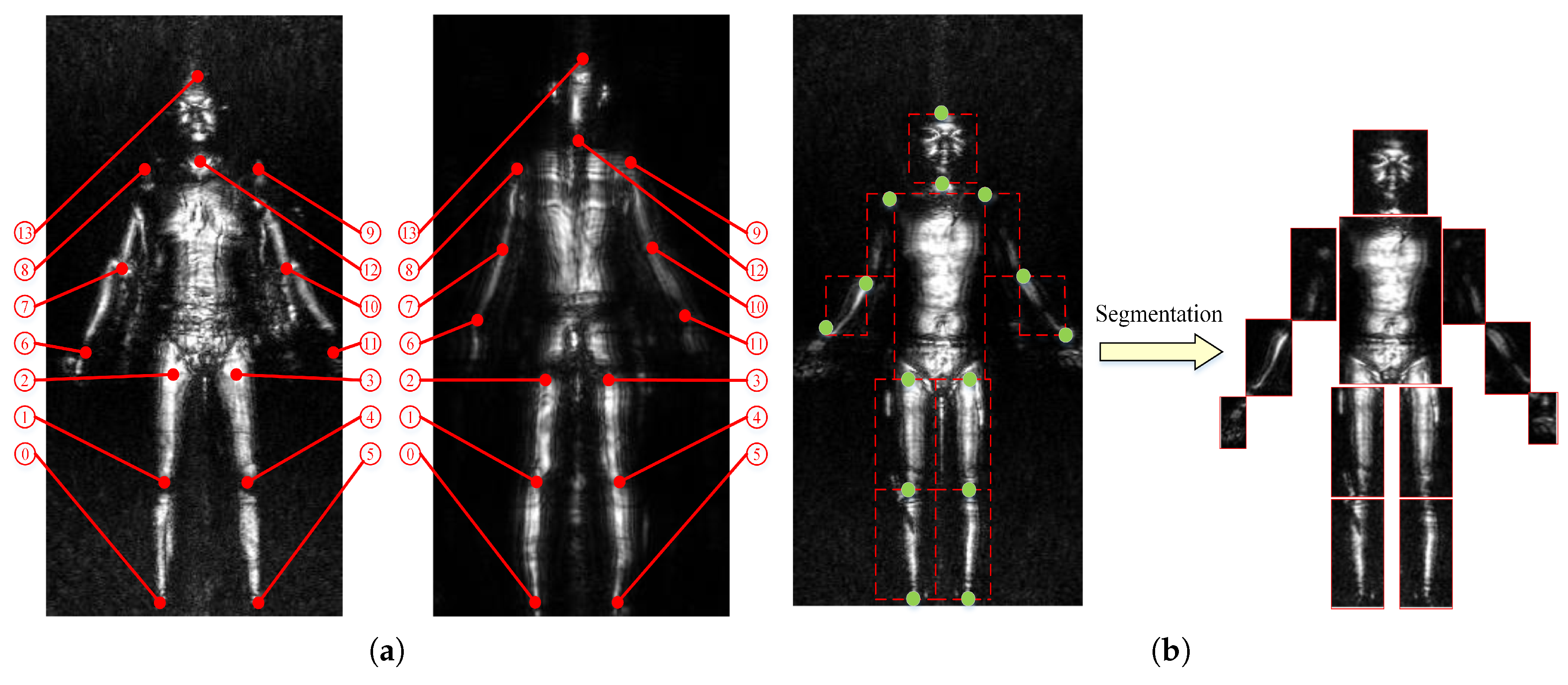
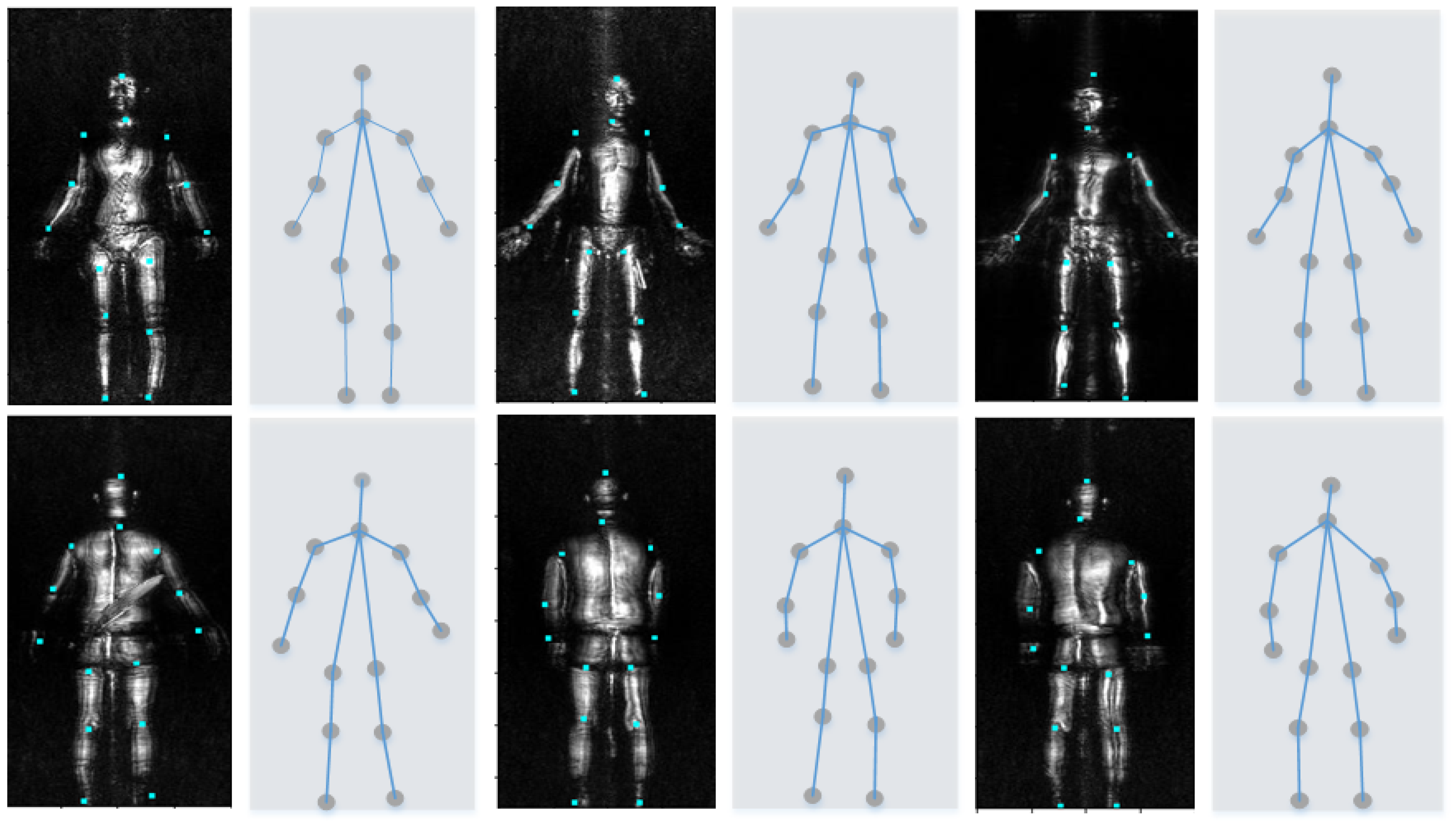
3.1. Human Posture Estimation and Image Segmentation
3.2. Suspicious Object Detector
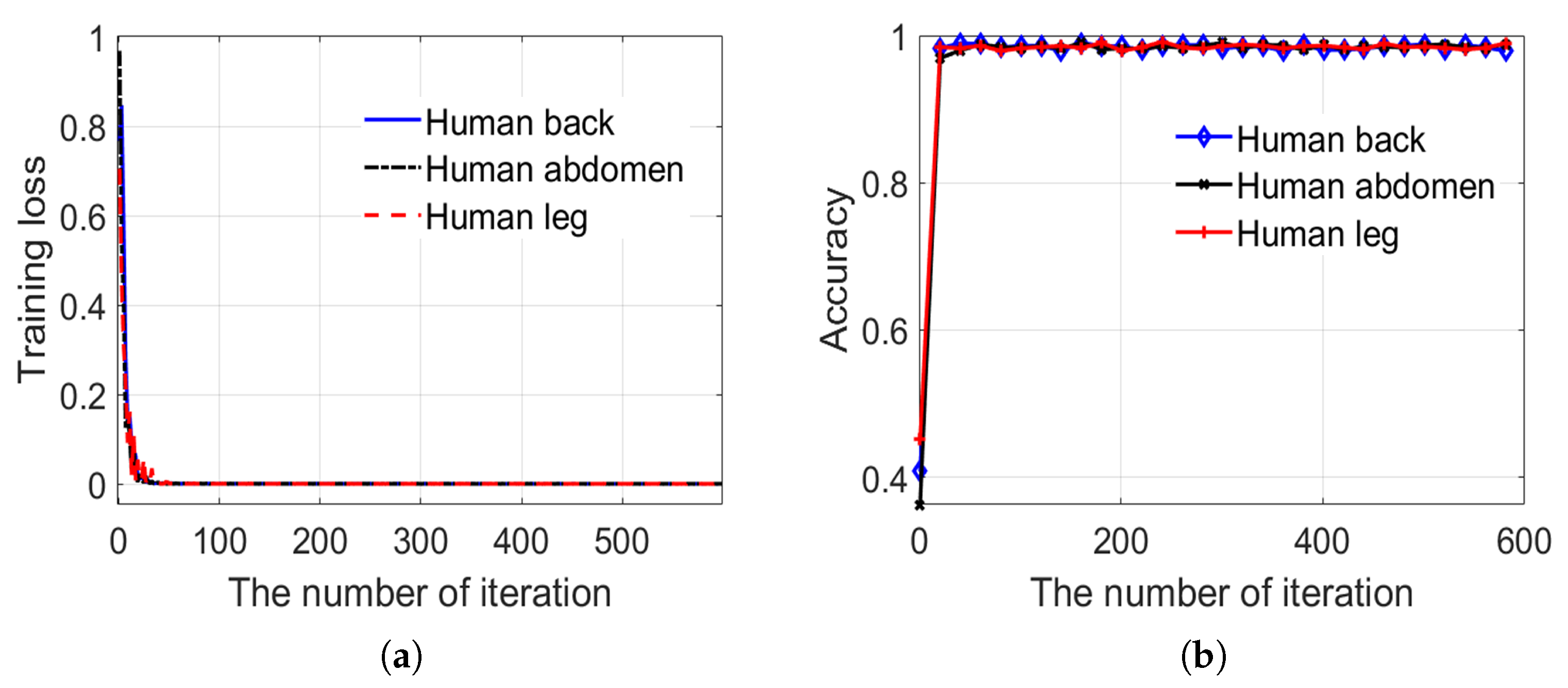
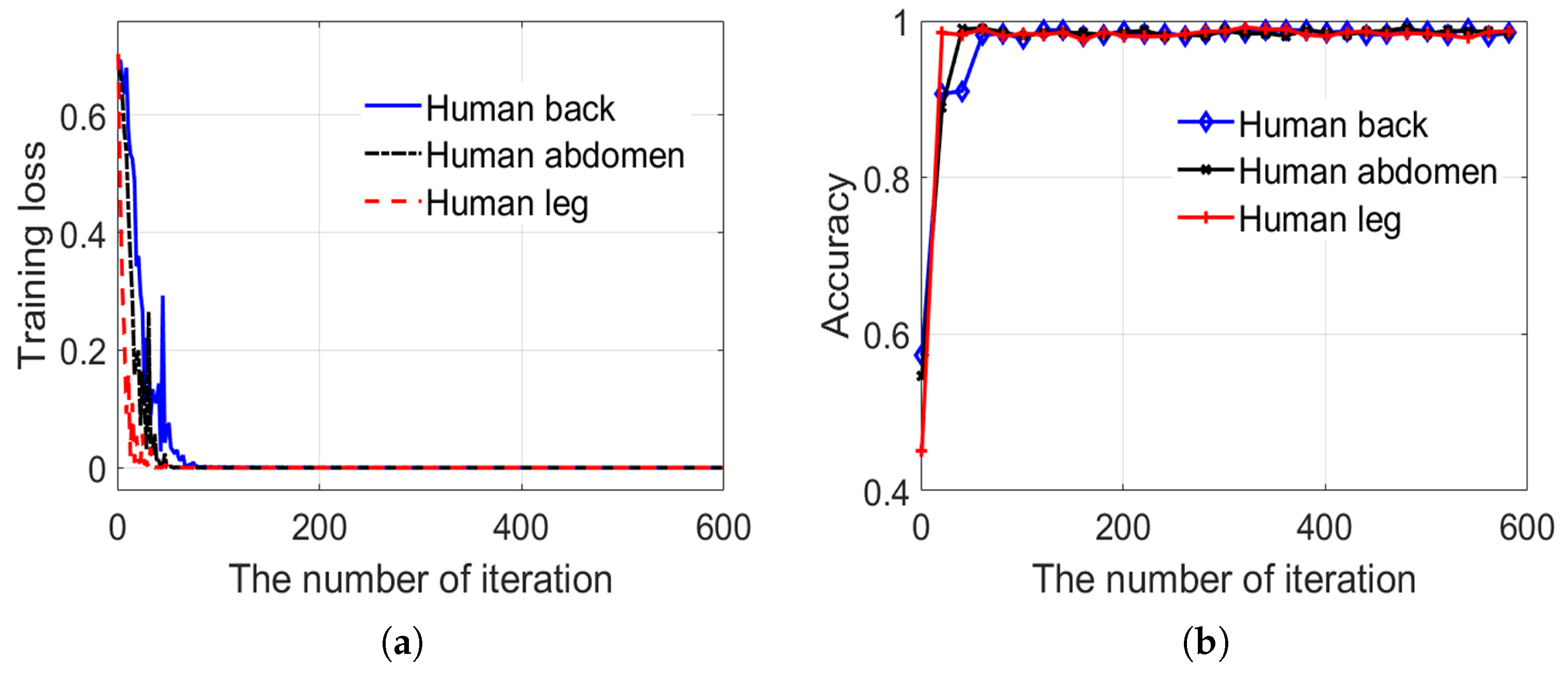
4. Experiments and Analysis
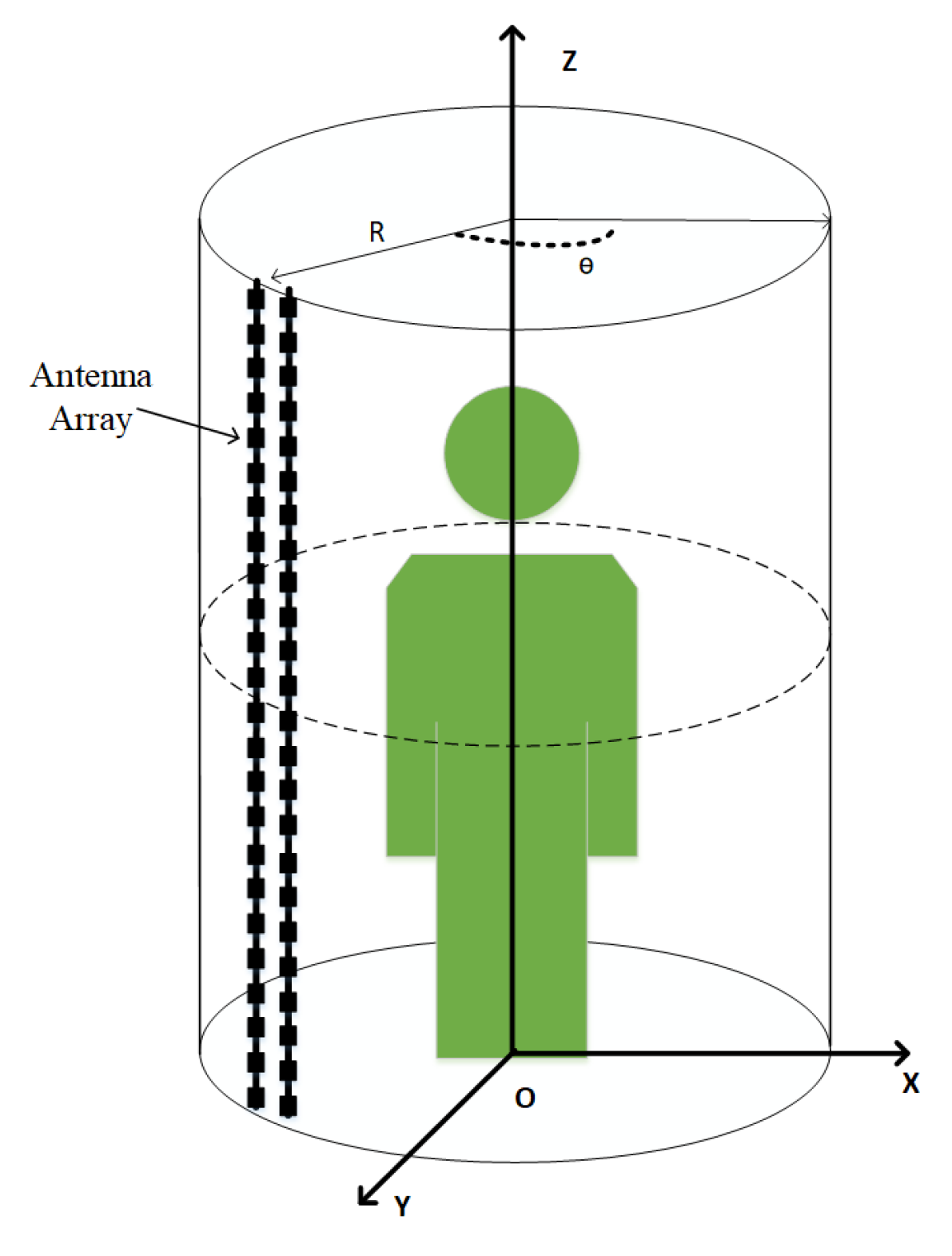
4.1. Experimental Dataset and Environment
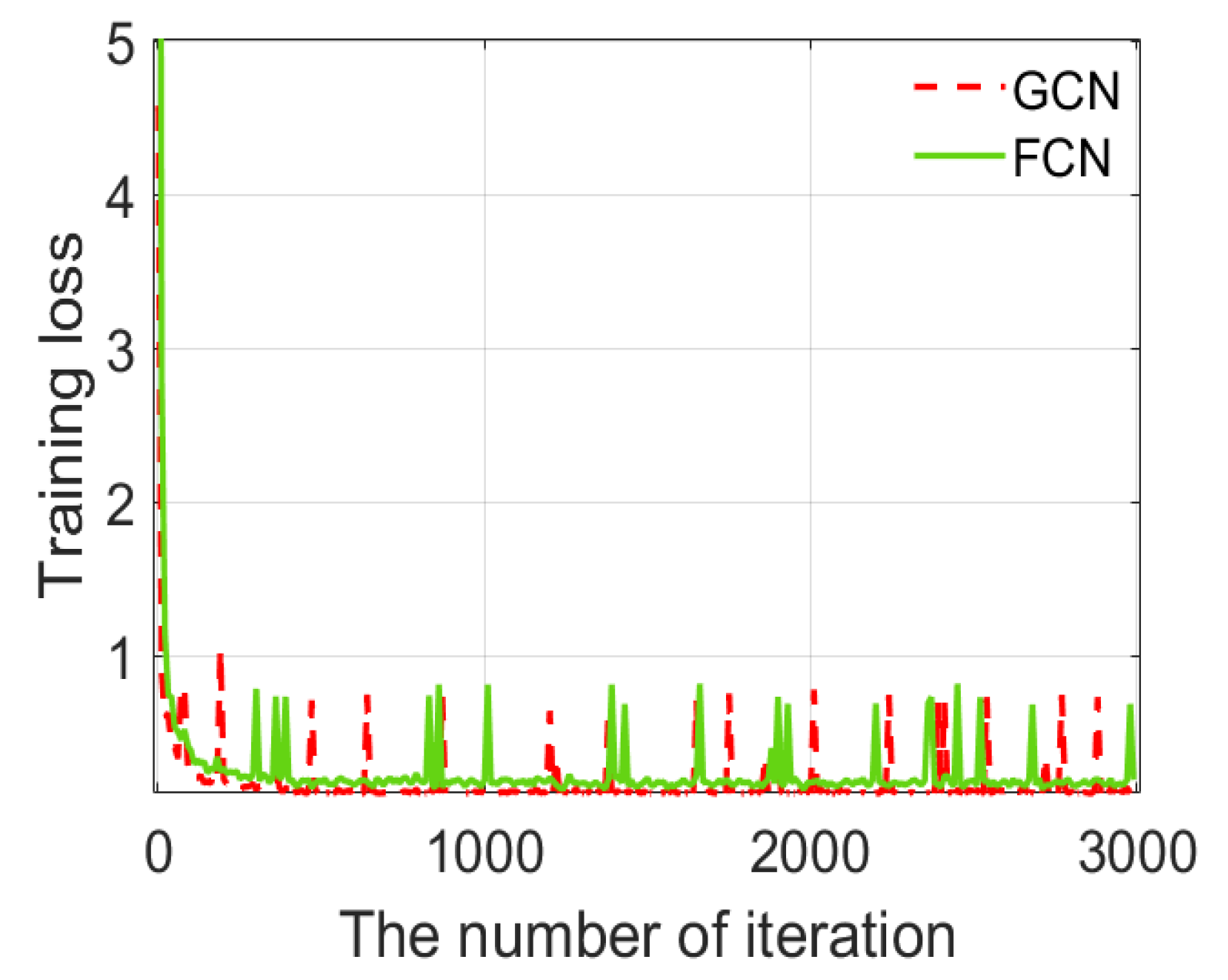
4.2. Experiments and Discussion
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Agurto, A.; Li, Y.; Tian, G.Y.; Bowring, N.; Lockwood, S. A review of concealed weapon detection and research in perspective. In Proceedings of the 2007 IEEE International Conference on Networking, Sensing and Control, London, UK, 15–17 April 2007; pp. 443–448. [Google Scholar]
- Sheen, D.M.; McMakin, D.L.; Hall, T.E. Cylindrical millimeter-wave imaging technique for concealed weapon detection. In Proceedings of the 26th AIPR Workshop: Exploiting New Image Sources and Sensors, Washington, DC, USA, 15–17 October 1997; Volume 3240, pp. 242–250. [Google Scholar]
- Sheen, D.M.; McMakin, D.L.; Hall, T.E. Three-dimensional millimeter-wave imaging for concealed weapon detection. IEEE Trans. Microw. Theory Tech. 2001, 49, 1581–1592. [Google Scholar] [CrossRef]
- García-Rial, F.; Montesano, D.; Gómez, I.; Callejero, C.; Bazus, F.; Grajal, J. Combining commercially available active and passive sensors into a millimeter-wave image for concealed weapon detection. IEEE Trans. Microw. Theory Tech. 2019, 67, 1167–1183. [Google Scholar] [CrossRef]
- Zhang, L.; Hao, Y.; Parini, C.G. Millimeter wave imaging system parameters at 95 GHz. IET Microw. Antennas Propag. 2011, 5, 528–534. [Google Scholar] [CrossRef]
- Andrews, D.A.; Harmer, S.W.; Bowring, N.J.; Rezgui, N.D.; Southgate, M.J. Active millimeter wave sensor for standoff concealed threat detection. IEEE Sens. J. 2013, 13, 4948–4954. [Google Scholar] [CrossRef]
- Elboushi, A.; Sebak, A. Active millimeter-wave imaging system for hidden weapons detection. In Proceedings of the 29th National Radio Science Conference (NRSC), Cairo, Egypt, 10–12 April 2012; pp. 111–118. [Google Scholar]
- Sheen, D.M.; McMakin, D.L.; Collins, H.D.; Hall, T.E. Near-field millimeter-wave imaging for weapons detection. In Applications of Signal and Image Processing in Explosives Detection Systems; International Society for Optics and Photonics: Bellingham, WA, USA, 1993; Volume 1824, pp. 223–233. [Google Scholar]
- Sheen, D.M.; McMakin, D.L.; Hall, T.E. Near-field three-dimensional radar imaging techniques and applications. Appl. Opt. 2010, 49, E83–E93. [Google Scholar] [CrossRef] [PubMed]
- Sheen, D.M.; Hall, T.E.; McMakin, D.L.; Jones, A.M.; Tedeschi, J.R. Three dimensional radar imaging techniques and systems for near-field applications. In Radar Sensor Technology XX; International Society for Optics and Photonics: Bellingham, WA, USA, 2016; Volume 9829, p. 98290V. [Google Scholar]
- Bertl, S.; Dallinger, A.; Detlefsen, J. Interferometric focusing for the imaging of humans. IET Radar Sonar Navig. 2010, 4, 457–463. [Google Scholar] [CrossRef]
- Appleby, R.; Robertson, D.A.; Wikner, D. Millimeter wave imaging: A historical review. In Passive and Active Millimeter-Wave Imaging XX; International Society for Optics and Photonics: Bellingham, WA, USA, 2017; Volume 10189, p. 1018902. [Google Scholar]
- Lee, D.S.; Yeom, S.; Son, J.Y.; Kim, S.H. Automatic image segmentation for concealed object detection using the expectation-maximization algorithm. Opt. Express 2010, 18, 10659–10667. [Google Scholar] [CrossRef] [PubMed]
- Yeom, S.; Lee, D.S.; Jang, Y.; Lee, M.K.; Jung, S.W. Real-time concealed-object detection and recognition with passive millimeter wave imaging. Opt. Express 2012, 20, 9371–9381. [Google Scholar] [CrossRef] [PubMed]
- Yu, C.C.; Zhang, G.F.; Gao, Y. Improved threshold-based segmentation method for millimeter wave radiometric image. In Proceedings of the 2019 International Conference on Modeling, Simulation, Optimization and Numerical Techniques (SMONT 2019), Shenzhen, China, 27–28 February 2019. [Google Scholar]
- Al-Shoukry, S. An automatic hybrid Approach to Detect Concealed Weapons Using Deep Learning. ARPN J. Eng. Appl. Sci. 2017, 12, 4736–4741. [Google Scholar]
- Tapia, S.L.; Molina, R.; de la Blanca, N.P. Using machine learning to detect and localize concealed objects in passive millimeter-wave images. Eng. Appl. Artif. Intell. 2018, 67, 81–90. [Google Scholar] [CrossRef]
- Kowalski, M. Real-time concealed object detection and recognition in passive imaging at 250 GHz. Appl. Opt. 2019, 58, 3134–3140. [Google Scholar] [CrossRef] [PubMed]
- Li, Y.; Peng, Z.; Pal, R.; Li, C. Potential active shooter detection based on radar micro-doppler and range-doppler analysis using artificial neural network. IEEE Sens. J. 2013, 13, 4224–4228. [Google Scholar] [CrossRef]
- Isiker, H.; Ünal, I.; Tekbas, M.; Özdemir, C. An auto-classification procedure for concealed weapon detection in millimeter-wave radiometric imaging systems. Microw. Opt. Technol. Lett. 2018, 60, 583–594. [Google Scholar] [CrossRef]
- Maqueda, I.G.; de la Blanca, N.P.; Molina, R.; Katsaggelos, A.K. Fast millimeter wave threat detection algorithm. In Proceedings of the 2015 23rd European Signal Processing Conference (EUSIPCO), Nice, France, 31 August–4 September 2015; pp. 599–603. [Google Scholar]
- Martinez, O.; Ferraz, L.; Binefa, X.; Gomez, I.; Dorronsoro, C. Concealed object detection and segmentation over millimetric waves images. In Proceedings of the 2010 IEEE Computer Society Conference on Computer Vision and Pattern Recognition-Workshops, San Francisco, CA, USA, 13–18 June 2010; pp. 31–37. [Google Scholar]
- Yeom, S.; Lee, D.S.; Son, J.Y.; Kim, S.H. Concealed object detection using passive millimeter wave imaging. In Proceedings of the 2010 4th International Universal Communication Symposium, Beijing, China, 18–19 October 2010; pp. 383–386. [Google Scholar]
- Shen, X.; Dietlein, C.R.; Grossman, E.; Popovic, Z.; Meyer, F.G. Detection and segmentation of concealed objects in terahertz images. IEEE Trans. Image Process. 2008, 17, 2465–2475. [Google Scholar] [CrossRef] [PubMed]
- Yeom, S.; Lee, D.S.; Son, J.Y.; Jung, M.K.; Jang, Y.; Jung, S.W.; Lee, S.J. Real-time outdoor concealed-object detection with passive millimeter wave imaging. Opt. Express 2011, 19, 2530–2536. [Google Scholar] [CrossRef]
- Yu, W.Y.; Chen, X.G.; Wu, L. Segmentation of concealed objects in passive millimeter-wave images based on the Gaussian mixture model. J. Infrared Millim. Terahertz Waves 2015, 36, 400–421. [Google Scholar] [CrossRef]
- Trofimov, V.A.; Trofimov, V.V. New way for both quality enhancement of THz images and detection of concealed objects. In Terahertz Emitters, Receivers, and Applications VI; International Society for Optics and Photonics: Bellingham, WA, USA, 2015; Volume 9585, p. 95850R. [Google Scholar]
- Sugiyama, M. Introduction to Statistical Machine Learning; Morgan Kaufmann: San Mateo, CA, USA, 2015. [Google Scholar]
- Ganapathi, A.S. Predicting and Optimizing System Utilization and Performance via Statistical Machine Learning. Ph.D. Thesis, University of California, Berkele, CA, USA, 2009. [Google Scholar]
- Lafferty, J.; Wasserman, L. Challenges in statistical machine learning. Stat. Sin. 2006, 16, 307–322. [Google Scholar]
- Girshick, R.; Donahue, J.; Darrell, T.; Malik, J. Rich feature hierarchies for accurate object detection and semantic segmentation. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Columbus, OH, USA, 24–27 June 2014; pp. 580–587. [Google Scholar]
- Ren, S.; He, K.M.; Girshick, R.; Sun, J. Faster R-CNN: Towards real-time object detection with region proposal networks. In Proceedings of the Advances in Neural Information Processing Systems 28 (NIPS 2015), Montreal, QC, Canada, 7–12 December 2015; pp. 91–99. [Google Scholar]
- He, K.M.; Gkioxari, G.; Dollar, P.; Girshick, R.B. Mask R-CNN. IEEE Trans. Pattern Anal. Mach. Intell. 2018, 42, 386–397. [Google Scholar] [CrossRef]
- Liu, Z.; Lyu, Y.; Wang, L.; Han, Z. Detection Approach Based on an Improved Faster RCNN for Brace Sleeve Screws in High-Speed Railways. IEEE Trans. Instrum. Meas. 2020, 69, 4395–4403. [Google Scholar] [CrossRef]
- Gong, X.; Su, H.; Xu, D.; Zhang, J.; Zhang, L.; Zhang, Z. Visual Defect Inspection for Deep-Aperture Components with Coarse-to-Fine Contour Extraction. IEEE Trans. Instrum. Meas. 2020, 69, 3262–3274. [Google Scholar] [CrossRef]
- Wu, H.; Gao, W.; Xu, X. Solder Joint Recognition Using Mask R-CNN Method. IEEE Trans. Compon. Packag. Manuf. Technol. 2020, 10, 525–530. [Google Scholar] [CrossRef]
- Xu, Z.; Liu, S.; Shi, J.; Lu, C. Outdoor RGBD Instance Segmentation with Residual Regretting Learning. IEEE Trans. Image Process. 2020, 29, 5301–5309. [Google Scholar] [CrossRef] [PubMed]
- Tapia, S.L.; Molina, R.; de la Blanca, N.P. Detection and localization of objects in passive millimeter wave images. In Proceedings of the 2016 24th European Signal Processing Conference (EUSIPCO), Budapest, Hungary, 29 August–2 September 2016; pp. 2101–2105. [Google Scholar]
- Tapia, S.L.; Molina, R.; de la Blanca, N.P. Deep CNNs for object detection using passive millimeter sensors. IEEE Trans. Circuits Syst. Video Technol. 2019, 29, 2580–2589. [Google Scholar] [CrossRef]
- Yuan, J.X.; Guo, C.G. A deep learning method for detection of dangerous equipment. In Proceedings of the 2018 Eighth International Conference on Information Science and Technology (ICIST), Cordoba, Spain, 30 June–6 July 2018; pp. 159–164. [Google Scholar]
- Guo, L.; Qin, S.Y. High-performance detection of concealed forbidden objects on human body with deep neural networks based on passive millimeter wave and visible imagery. J. Infrared Millim. Terahertz Waves 2019, 40, 314–347. [Google Scholar] [CrossRef]
- Liu, T.; Zhao, Y.; Wei, Y.C.; Zhao, Y.F.; Wei, S.K. Concealed object detection for activate millimeter wave image. IEEE Trans. Ind. Electron. 2019, 66, 9909–9917. [Google Scholar] [CrossRef]
- Liu, C.Y.; Yang, M.H.; Sun, X.W. Towards robust human millimeter wave imaging inspection system in real time with deep learning. Prog. Electromagn. Res. 2018, 161, 87–100. [Google Scholar] [CrossRef]
- Zhang, J.S.; Xing, W.J.; Xing, M.D.; Sun, G.C. Terahertz image detection with the improved faster region-based convolutional neural network. Sensors 2018, 18, 2327. [Google Scholar] [CrossRef]
- Yang, X.; Wu, T.; Zhang, L.; Yang, D.; Wang, N.; Song, B.; Gao, X. CNN with spatio-temporal information for fast suspicious object detection and recognition in THz security images. Signal Process. 2019, 160, 202–214. [Google Scholar] [CrossRef]
- Pang, L.; Liu, H.; Chen, Y.; Miao, J. Real-time Concealed Object Detection from Passive Millimeter Wave Images Based on the YOLOv3 Algorithm. Sensors 2020, 20, 1678. [Google Scholar] [CrossRef]
- Yeom, S.; Lee, D.S.; Son, J.Y. Shape feature analysis of concealed objects with passive millimeter wave imaging. Prog. Electromagn. Res. 2015, 57, 131–137. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, G.F.; Zhou, L.Y. Study on MMW radiation characteristics and imaging of stereoscopic metal targets. In Selected Papers of the Chinese Society for Optical Engineering Conferences held October and November 2016; International Society for Optics and Photonics: Bellingham, WA, USA, 2017; Volume 10255, p. 102551K. [Google Scholar]
- Bertl, S.; Detlefsen, J. Effects of a reflecting background on the results of active MMW SAR imaging of concealed objects. IEEE Trans. Geosci. Remote Sens. 2011, 49, 3745–3752. [Google Scholar] [CrossRef]
- Wei, S.E.; Ramakrishna, V.; Kanade, T.; Sheikh, Y. Convolutional Pose Machines. In Proceedings of the 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Las Vegas, NV, USA, 27–30 June 2016. [Google Scholar]
- Peng, C.; Zhang, X.; Yu, G.; Luo, G.; Sun, J. Large Kernel Matters—Improve Semantic Segmentation by Global Convolutional Network. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Honolulu, HI, USA, 21–26 July 2017; pp. 1743–1751. [Google Scholar]
- Hensman, P.; Masko, D. The Impact of Imbalanced Training Data for Convolutional Neural Networks. Bachelor’s Thesis, KTH Royal Institute of Technology, Stockholm, Sweden, 2015. [Google Scholar]
- Pulgar, F.J.; Rivera, A.J.; Charte, F.; del jesus, M.J. On the impact of imbalanced data in convolutional neural networks performance. In Proceedings of the International Conference on Hybrid Artificial Intelligence Systems Springer, La Rioja, Spain, 21–23 June 2017; Volume 10334, pp. 220–232. [Google Scholar]



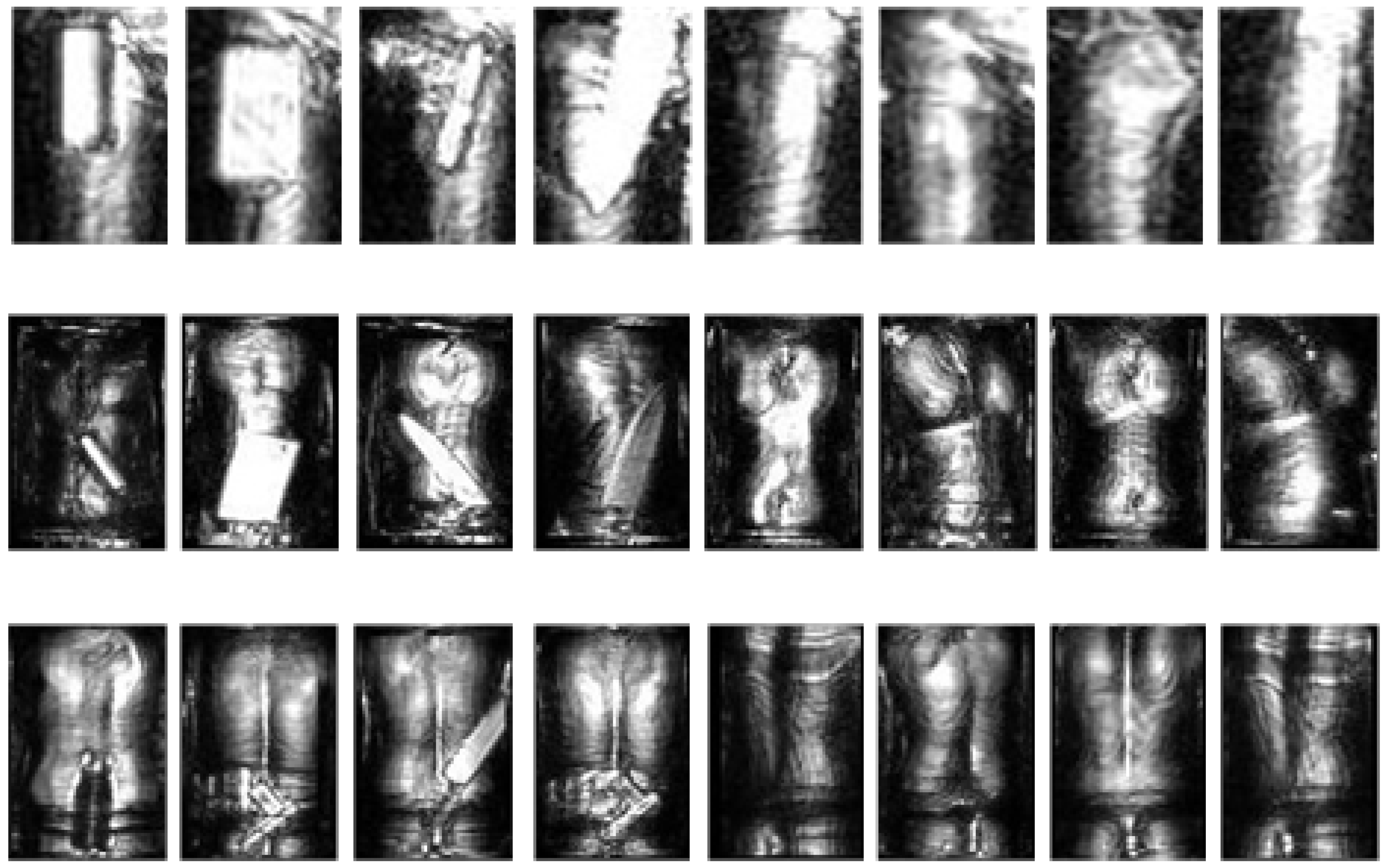

| Category | Total | Phone | Bottle | Pistol | Knife |
|---|---|---|---|---|---|
| Number | 2440 | 84 | 480 | 960 | 916 |
| Category | Back | Abdomen | Leg |
|---|---|---|---|
| Negative Samples | 258 | 246 | 263 |
| Positive Samples | 339 | 268 | 300 |
| Proposed Method | Faster R-CNN | Mask R-CNN | |||
|---|---|---|---|---|---|
| 894 (TP) | 13 (FP) | 605 (TP) | 293 (FP) | 898 (TP) | 413 (FP) |
| 754 (TN) | 13 (FN) | 474 (TN) | 302 (FN) | 354 (TN) | 9 (FN) |
| Methods | ACC | PPV | TPR | FPR | F1 | MCC |
|---|---|---|---|---|---|---|
| Mask R-CNN | 74.79 | 68.50 | 99.00 | 53.85 | 0.81 | 54.60 |
| Faster R-CNN | 64.46 | 67.34 | 66.70 | 38.20 | 0.67 | 28.48 |
| Proposed Method | 98.45 | 98.57 | 98.57 | 1.69 | 0.98 | 96.87 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Meng, Z.; Zhang, M.; Wang, H. CNN with Pose Segmentation for Suspicious Object Detection in MMW Security Images. Sensors 2020, 20, 4974. https://doi.org/10.3390/s20174974
Meng Z, Zhang M, Wang H. CNN with Pose Segmentation for Suspicious Object Detection in MMW Security Images. Sensors. 2020; 20(17):4974. https://doi.org/10.3390/s20174974
Chicago/Turabian StyleMeng, Zhichao, Man Zhang, and Hongxian Wang. 2020. "CNN with Pose Segmentation for Suspicious Object Detection in MMW Security Images" Sensors 20, no. 17: 4974. https://doi.org/10.3390/s20174974
APA StyleMeng, Z., Zhang, M., & Wang, H. (2020). CNN with Pose Segmentation for Suspicious Object Detection in MMW Security Images. Sensors, 20(17), 4974. https://doi.org/10.3390/s20174974




