TrustWalker: An Efficient Trust Assessment in Vehicular Internet of Things (VIoT) with Security Consideration
Abstract
1. Introduction
Research Contributions
- First, based on our trust model, we propose on-demand trust enhanced routing (TER) among vehicles in VIoT, which extends trust-based source routing mechanisms by combining with the TW algorithm. Our proposed TER scheme predicts the next route-finding and efficient route discovery based on the current node threshold trust value and the TW algorithm for transmitting the information.
- Second, for the performance evaluation of the proposed TER, we compare it with the performance of two other routing protocols even though they do not have trust mechanism among communicating nodes. One is an authenticated anonymous secure routing (AASR) scheme that uses a cryptographic operation, and the other is standard AODV routing. Based on the analytical results, it is shown that the proposed TER is a promising approach in enhancing packet delivery, minimizing E2E delay, and resisting against malicious threats.
- Third, we argue that the proposed TER can resist certain malicious attacks by the continuous update of route trust by taking the latest interactions among peers. The TER helps us to cope with malicious attacks, e.g., black hole and zigzag.
- Finally, taking advantage of the TW algorithm, we can efficiently assess trust in large scale vehicular networks. Therefore, it can be seen that the proposed TW algorithm can also be applicable to interpersonal trust assessment in online social networks.
2. Related Work
2.1. Trust Models in Vehicular Networks
2.1.1. Entry-Oriented Trust Models
2.1.2. Data-Oriented Trust Models
2.1.3. Combined Trust Models
2.2. Secure Routing in Vehicular Networks
3. System Model, Trust Model and Design Goals
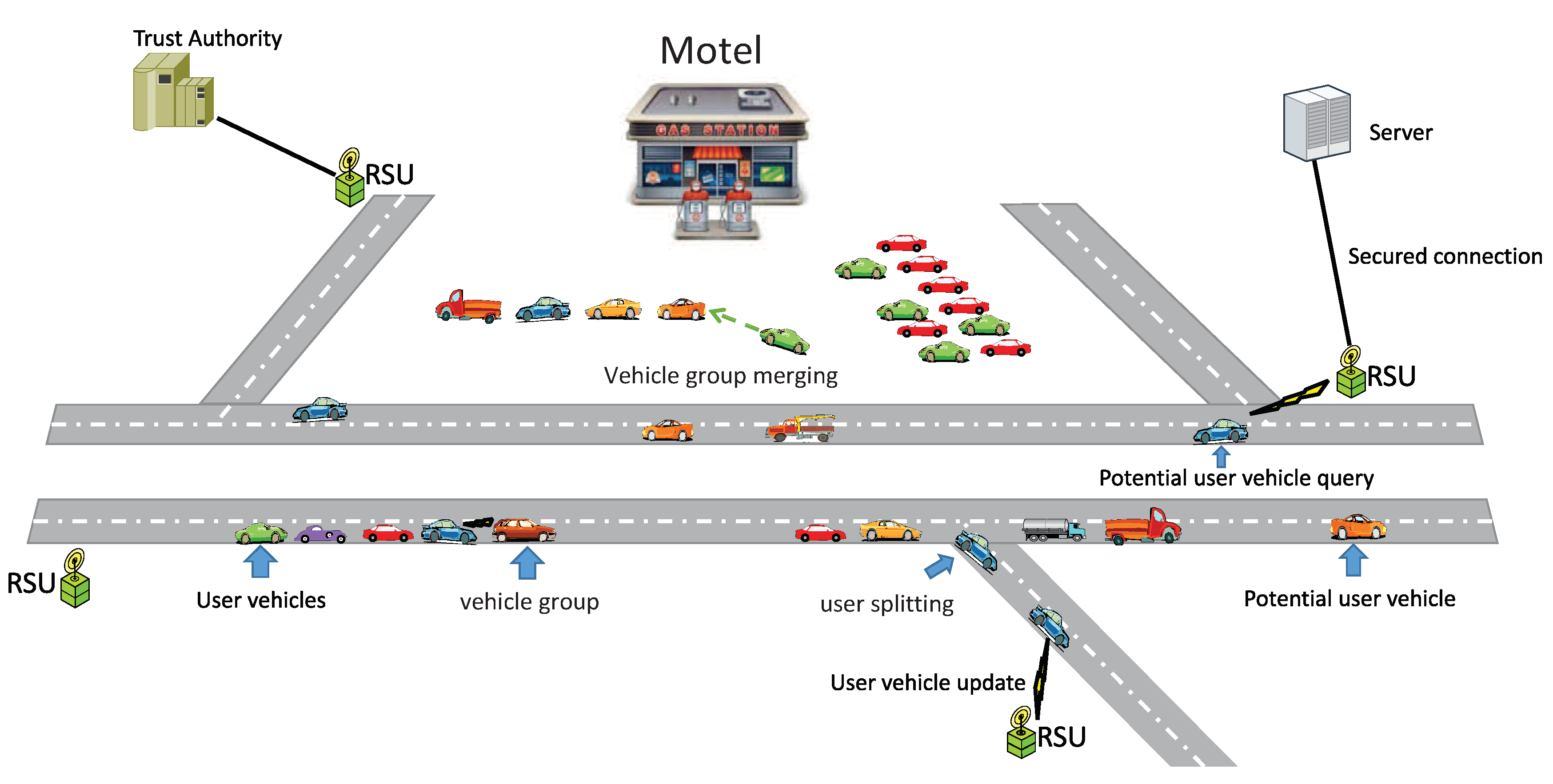
3.1. System Model
3.2. Trust Model
3.3. Design Goals
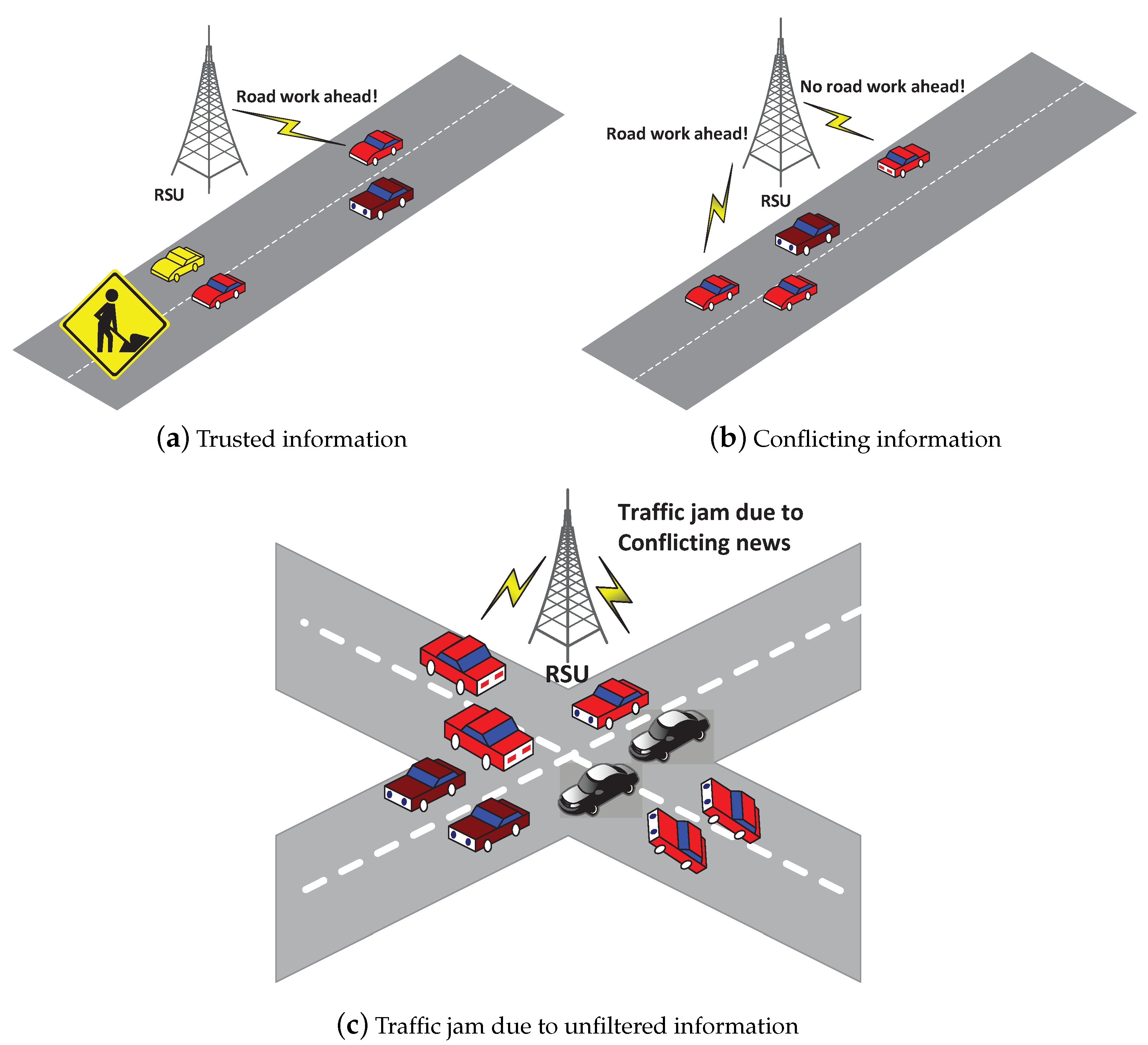
- Accurate trust assessment: Many malicious attacks can interrupt vehicular networks. During the aforementioned situation, a trust management scheme is urgently needed to rank good and bad vehicles.
- The relay ratio improvement: The target vehicle in VIoT may drop the information due to selfishness or other packet dropping attacks. In this situation, if a requesting vehicle randomly selects a target vehicle, then the relay ratio will be degraded. Therefore, we need an efficient trust assessment scheme to improve the relay ratio by selecting a reliable vehicle.
- Robustness against adversaries: The central security architecture should be capable of tackling adversaries, i.e., the collusion of vehicles to provide bogus feedback to RSU [35]. The central authority also makes sure that RSUs are not compromised in VIoT.
3.4. Adversary Model
- Simple Attack (SA): In this attack, an attacker manipulates other nodes to interrupt the normal communication going on by altering the route information and data forwarding packets.
- Black Hole Attack (BH): In the Black hole attack, an attacker first convinces the normal node by claiming that it has the shortest path to its desired destination. Once this normal node sends all packet to the attacker and after getting all packets, it drops all packets, and the normal node becomes a victim. The attacker is difficult to recognize and remains active in the system.
- Zigzag (On-and-off) Attack (ZA): In this attack, the malicious nodes may act good and bad with changing alternative behavior. The malicious node on for a few seconds to send some packets and then suddenly gets off and drops the packets due to many selfish reasons.
4. Trust Model
4.1. Classification of Trust Types
4.2. Direct Trust
4.3. Indirect/Recommended Trust
4.3.1. Consensus Combination
4.3.2. Discounting Combination
5. Framework for Proposed TER
5.1. Routing Table Extension
5.2. Trust Judging and Update Rules
- If the belief of neighbor vehicle x in z is greater than the given threshold, then it will trust vehicle z and vise versa.
- If the uncertainty of vehicle x in vehicle z is greater than , x ask for a digital signature verification from vehicle z and waits for it. If x successfully verifies z’s signature then x will start communicating with vehicle z.
- If two neighbor vehicles had positive interaction, then the trust repository is updated by increment the trust in the correspondent vehicle, and the inverse is true also.
- If two vehicles have any uncertainty between each other, then we use . Here, u is the maximum uncertainty from vehicle x to vehicle z. It is because the two vehicles never interacted by the given expiry time of 5 s.
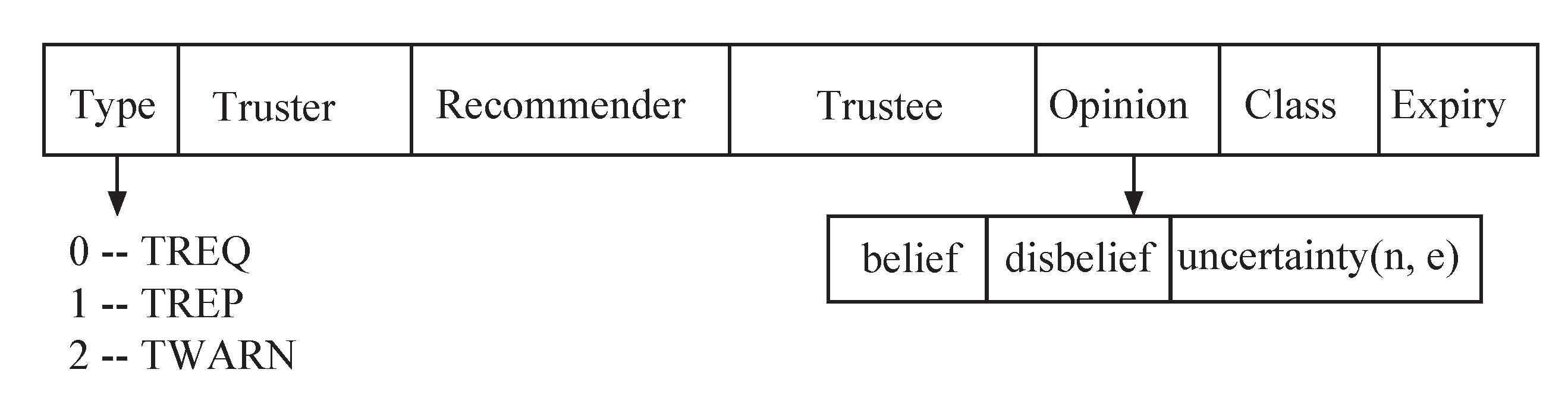
5.3. Information Exchange Protocol
6. Route Discovery by TW
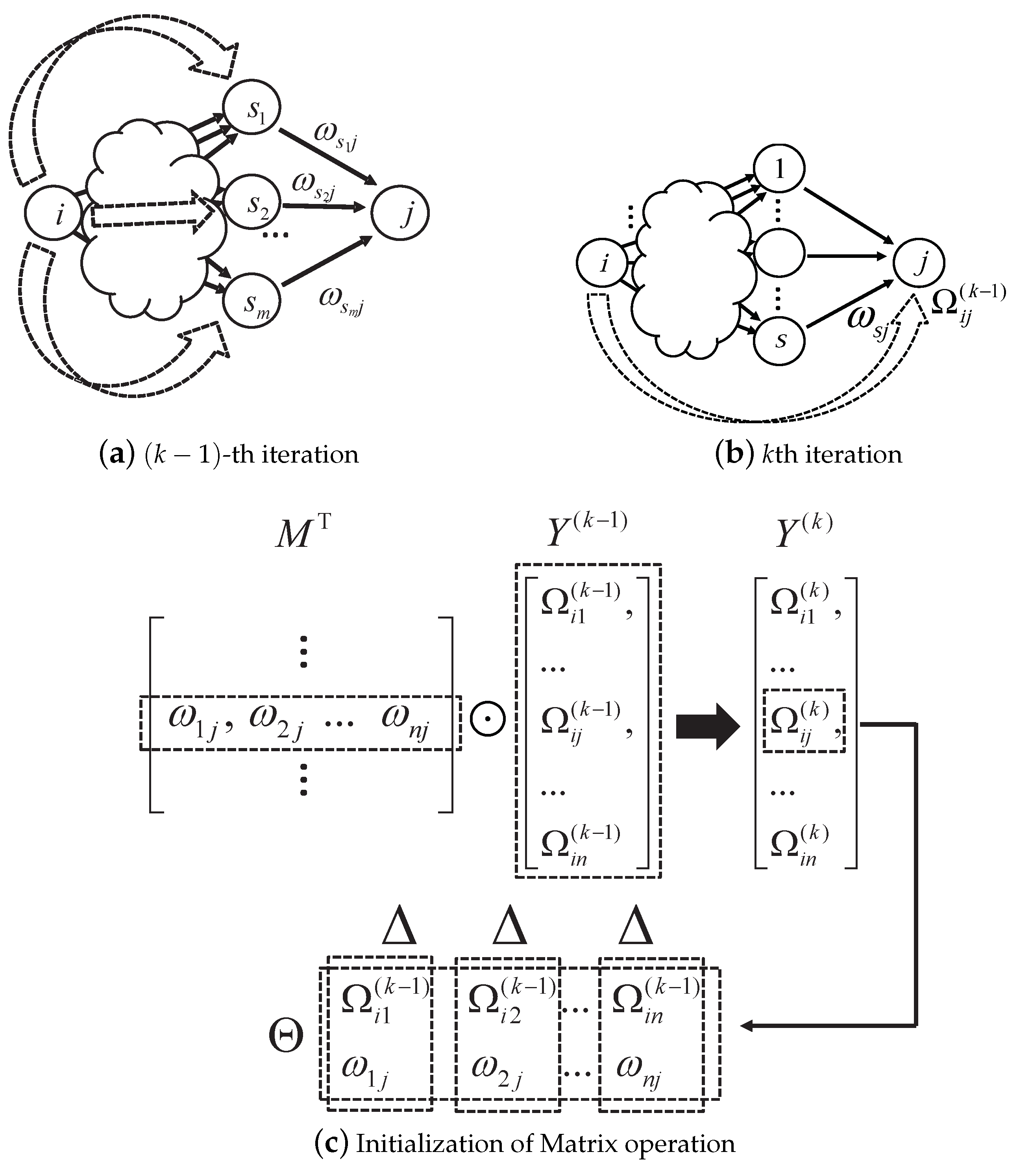
6.1. Design of TW
6.2. Operations in TW
6.3. TW Algorithms
| Algorithm 1: Route Discovery by TW |
REQUIRE: A directed graph G with a truster i and the maximum searching level H ENSURE: opinion on J where 1. Initialize and based on G 2. 3. While do 4. 5. for all columns s.t. do 6. 7. for all direct opinion s.t. do 8. 9. if then 10. 11. end if 12. end for 13. 14. end for 15. end while 16. return |
| Algorithm 2: Authentication from user i to j in k-hop by TW |
Exchange opinion about opinion matrix i with all neighbors of individual vector j using the TW information exchange protocol.; 1. /* Verify the trustworthiness of */ 2. /* and judge the next step using conditions set in Table 1 */ 3. if 4. trust and forward RREQ/RREP 5. elseif 6. distrust for expiry time 7. elseif request and verify digital certificate 8. else 9. /* the confidence about trustworthiness is decreased*/ request and verify j’s certificates, by default 10. endif |
7. Route Maintenance
7.1. Computation of Route Trust
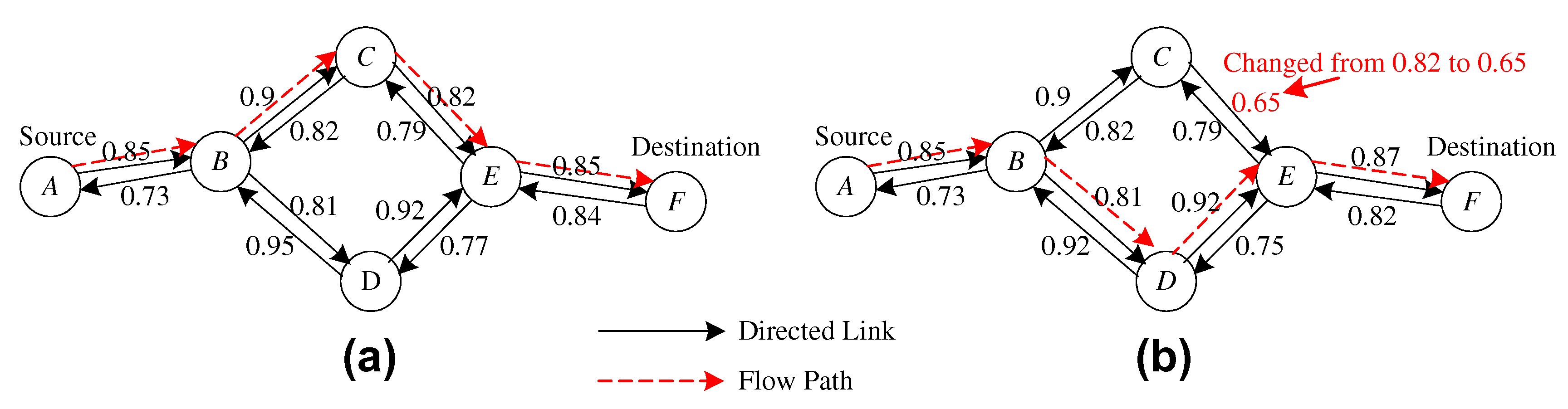
7.2. Route Hand-Off
7.3. Route Error
7.4. Dealing with Node Mobility
8. Simulation Setup and Results
8.1. Attack Pattern and Evaluation Metrics
8.2. Performance Analysis
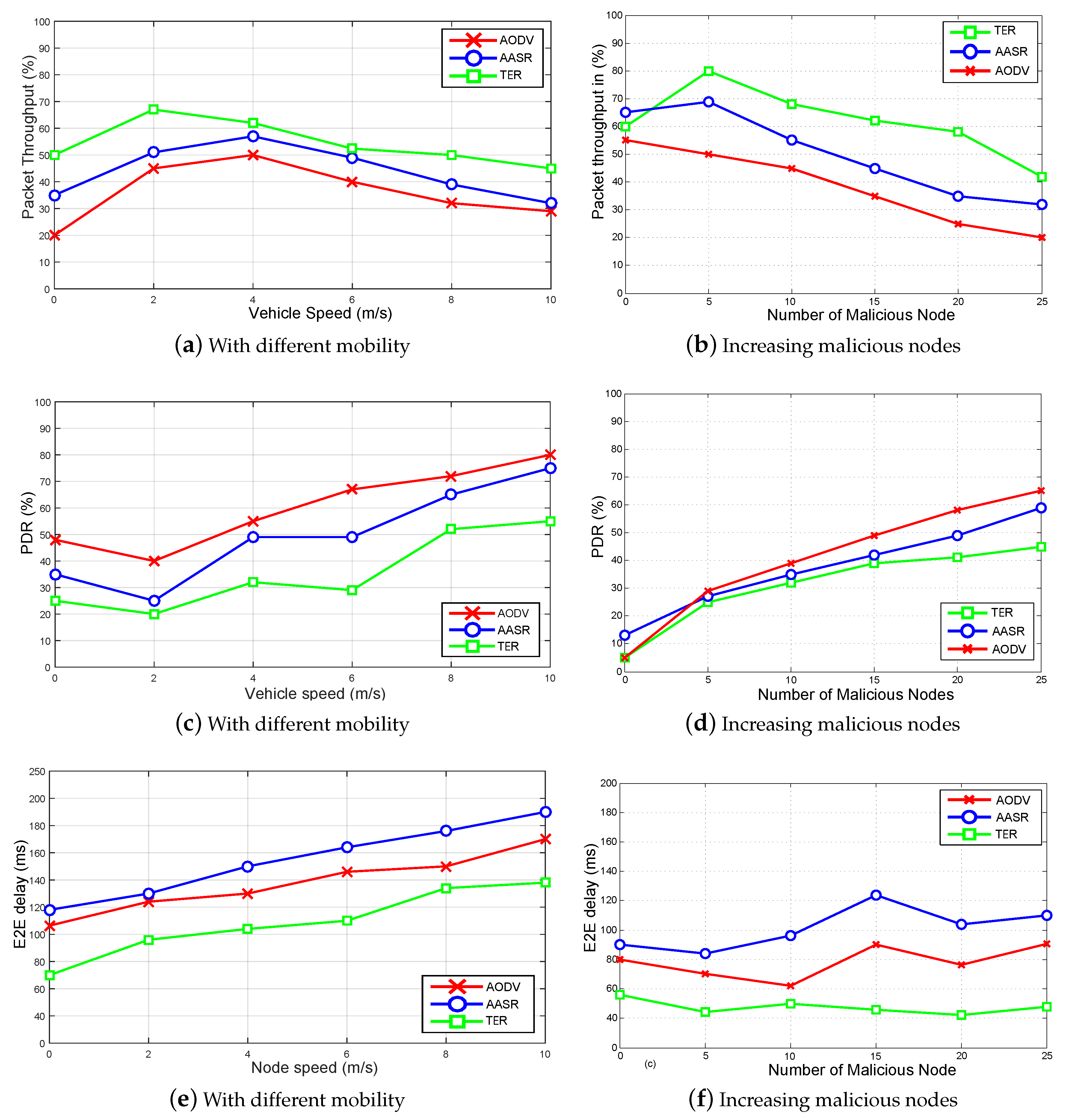
8.2.1. Test: 1 Packet Throughput, PDR, and E2E Delay with Different Vehicles Mobility and Increasing Malicious Nodes
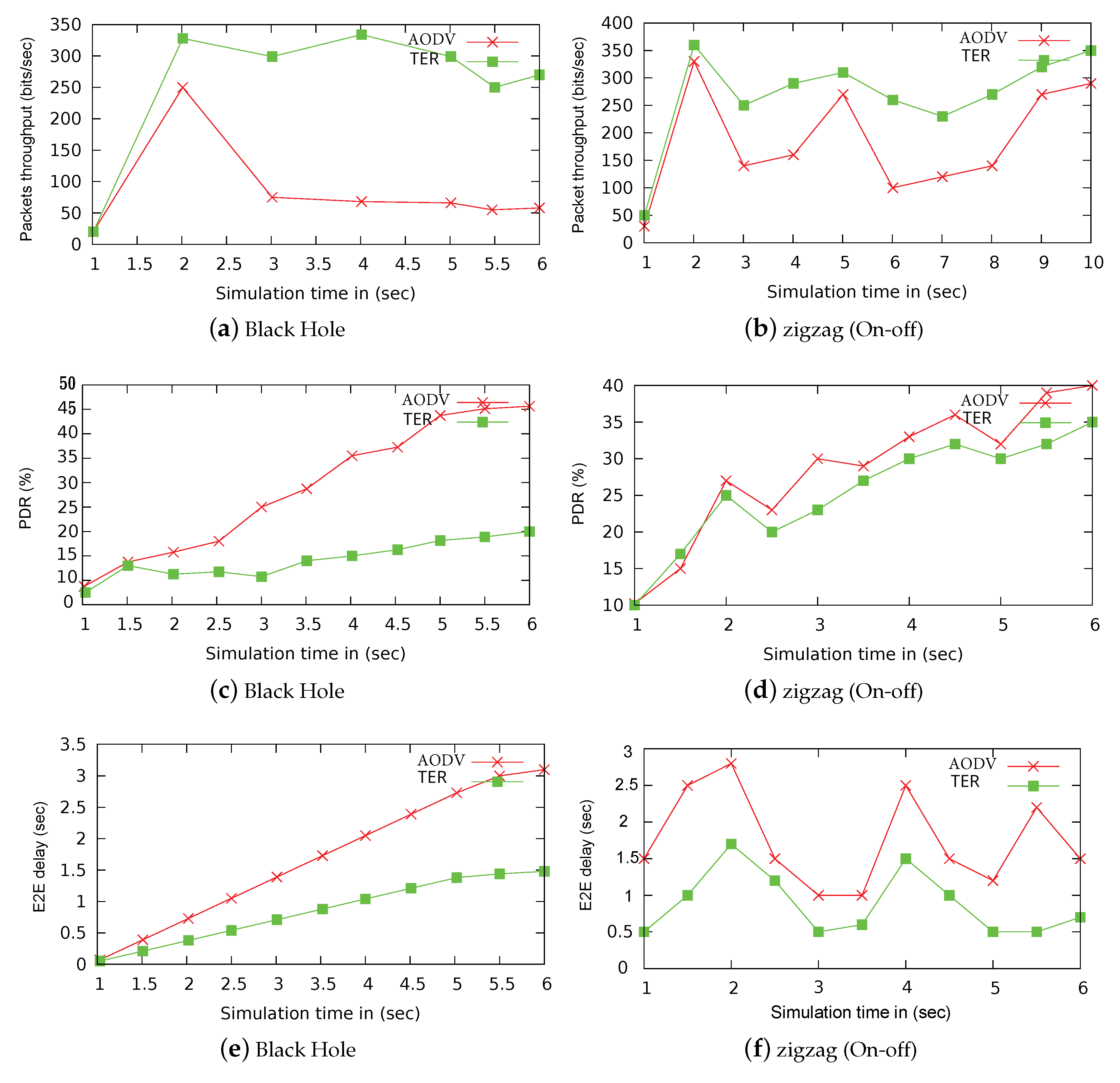
8.2.2. Test: 2 Packet Throughput, PDR, and E2E Delay under Black Hole and Zigzag Attacks
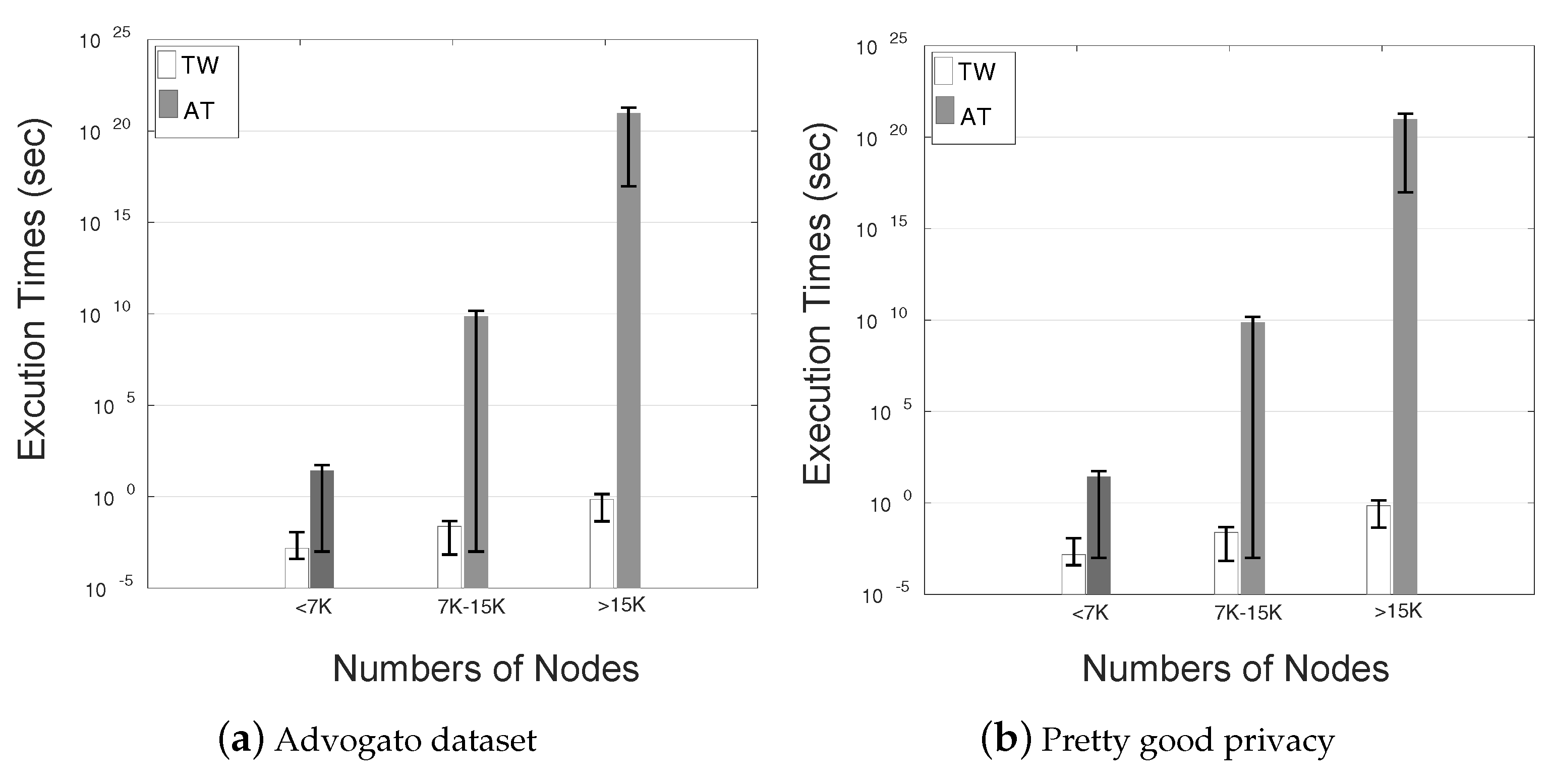
8.3. Execution Time
9. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Zikria, Y.B.; Afzal, M.K.; Kim, S.W. Internet of Multimedia Things (IoMT): Opportunities, Challenges and Solutions. Sensors 2020, 20, 2334. [Google Scholar] [CrossRef] [PubMed]
- Schmidt, T.; Philipsen, R.; Themann, P.; Ziefle, M. Public perception of V2x-technology-evaluation of general advantages, disadvantages and reasons for data sharing with connected vehicles. IEEE Intell. Veh. Symp. 2016, 1, 1344–1349. [Google Scholar]
- Mai, A.; Schlesinger, D. Connected Vehicles. 2011. Available online: https://www.cisco.com/c/dam/en_us/about/ac79/docs/mfg/Connected-Vehicles_Service_Provider.pdf (accessed on 15 May 2020).
- Mejri, M.N.; Ben-Othman, J.; Hamdi, M. Survey on VANET security challenges and possible cryptographic solutions. Veh. Commun. 2014, 1, 53–66. [Google Scholar] [CrossRef]
- Wang, L.; Liu, X. NOTSA: Novel OBU with three-level security architecture for internet of vehicles. IEEE Internet Things J. 2018, 5, 3548–3558. [Google Scholar] [CrossRef]
- Jiang, S.; Zhu, X.; Wang, L. An efficient anonymous batch authentication scheme based on HMAC for VANETs. IEEE Trans. Intell. Transp. Syst. 2016, 17, 2193–2204. [Google Scholar] [CrossRef]
- Al-Kahtani, M.S. Survey on security attacks in vehicular ad hoc networks (VANETs). In Proceedings of the IEEE 6th International Conference on Signal Processing and Communication Systems, Gold Coast, QLD, Australia, 12–14 December 2012; pp. 1–9. [Google Scholar]
- Hu, H.; Lu, R.; Zhang, Z.; Shao, J. REPLACE: A reliable trust-based platoon service recommendation scheme in VANET. IEEE Trans. Veh. Technol. 2016, 66, 1787–1797. [Google Scholar] [CrossRef]
- Sohail, M.; Wang, L.; Ali, R.; Rahim, S.; Yao, J. Efficient data handover and intelligent information assessment in software-defined vehicular social networks. IET Intell. Transp. Syst. 2019, 13, 1814–1821. [Google Scholar] [CrossRef]
- Zhang, J. A Survey on Trust Management for VANETs. In Proceedings of the IEEE International Conference on Advanced Information Networking and Applications, Singapore, 22–25 March 2011; pp. 105–112. [Google Scholar]
- Sohail, M.; Wang, L. 3VSR: Three valued secure routing for vehicular ad hoc networks using sensing logic in adversarial environment. Sensors 2018, 18, 856. [Google Scholar] [CrossRef]
- Liu, G.; Yang, Q.; Wang, H.; Lin, X.; Wittie, M.P. Assessment of multi-hop interpersonal trust in social networks by Three-Valued Subjective Logic. In Proceedings of the IEEE conference on Computer Communications (INFOCOM), Toronto, ON, Canada, 27 April–2 May 2014; pp. 1698–1706. [Google Scholar]
- Sohail, M.; Wang, L.; Jiang, S.; Zaineldeen, S.; Ashraf, R.U. Multi-hop interpersonal trust assessment in vehicular ad-hoc networks using three-valued subjective logic. IET Inf. Secur. 2018, 13, 223–230. [Google Scholar] [CrossRef]
- Yu, H.; Lee, H.; Jeon, H. What is 5G? Emerging 5G Mobile Services and Network Requirements. Sustainability 2019, 9, 1848. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, L.; Chen, H.H. Message authentication using proxy vehicles in vehicular ad hoc networks. IEEE Trans. Veh. Technol. 2014, 64, 3697–3710. [Google Scholar] [CrossRef]
- Chen, X.; Wang, L. A cloud-based trust management framework for vehicular social networks. IEEE Access 2017, 5, 2967–2980. [Google Scholar] [CrossRef]
- Liu, W.; Yu, M. AASR: Authenticated anonymous secure routing for MANETs in adversarial environments. IEEE Trans. Veh. Technol. 2014, 63, 4585–4593. [Google Scholar] [CrossRef]
- Rasool, I.U.; Zikria, Y.B.; Kim, S.W. A Review of WAVE Multichannel Operational MAC Protocols: QoS Analysis and Other Related Issues. Int. J. Distrib. Sens. Netw. 2017, 13, 1–22. [Google Scholar] [CrossRef]
- Gerlach, M. Trust for Vehicular Applications. In Proceedings of the IEEE Eighth International Symposium on Autonomous Decentralized Systems (ISADS’07), Sedona, AZ, USA, 21–23 March 2007; pp. 295–304. [Google Scholar]
- Minhas, U.F.; Zhang, J.; Tran, T.; Cohen, R. A multifaceted approach to modeling agent trust for effective communication in the application of mobile ad hoc vehicular networks. IEEE Trans. Syst. Man Cybern. Part C Appl. Rev. 2010, 41, 407–420. [Google Scholar] [CrossRef]
- Mármol, F.G.; Pérez, G.M. TRIP, a trust and reputation infrastructure-based proposal for vehicular ad hoc networks. J. Netw. Comput. Appl. 2012, 35, 934–941. [Google Scholar] [CrossRef]
- Raya, M.; Papadimitratos, P.; Gligor, V.D.; Hubaux, J.P. On Data-Centric Trust Establishment in Ephemeral Ad Hoc Networks. In Proceedings of the IEEE 27th Conference on Computer Communications (INFOCOM), Phoenix, AZ, USA, 13–18 April 2008; pp. 1238–1246. [Google Scholar]
- Huang, Z.; Ruj, S.; Cavenaghi, M.A.; Stojmenovic, M.; Nayak, A. A social network approach to trust management in VIoT. P2P Netw. Appl. 2014, 7, 229–242. [Google Scholar]
- Soleymani, S.A.; Abdullah, A.H.; Hassan, W.H.; Anisi, M.H.; Goudarzi, S.; Baee, M.A.R.; Mandala, S. Trust management in vehicular ad hoc network: A systematic review. EURASIP J. Wirel. Commun. Netw. 2015, 1, 146. [Google Scholar] [CrossRef]
- Monir, M.; Abdel-Hamid, A.; El Aziz, M.A. A categorized trust-based message reporting scheme for VIoT. In International Conference on Security of Information and Communication Networks; Springer: Berlin/Heidelberg, Germany, 2013; pp. 65–83. [Google Scholar]
- Li, W.; Song, H. ART: An attack-resistant trust management scheme for securing vehicular ad hoc networks. IEEE Trans. Intell. Transp. Syst. 2015, 17, 960–969. [Google Scholar] [CrossRef]
- Patel, N.J.; Jhaveri, R.H. Trust based approaches for secure routing in VANET: A Survey. Procedia Comput. Sci. 2015, 45, 592–601. [Google Scholar] [CrossRef]
- Perkins, C.E.; Royer, E.M. Ad-hoc on-demand distance vector routing. In Proceedings of the WMCSA’99. Second IEEE Workshop on Mobile Computing Systems and Applications, New Orleans, LA, USA, 25–26 February 1999; pp. 90–100. [Google Scholar]
- Nzouonta, J.; Rajgure, N.; Wang, G.; Borcea, C. VANET routing on city roads using real-time vehicular traffic information. IEEE Trans. Veh. Technol. 2009, 58, 3609–3626. [Google Scholar] [CrossRef]
- Bravo-Torres, J.F.; López-Nores, M.; Blanco-Fernández, Y.; Pazos-Arias, J.J.; Ramos-Cabrer, M.; Gil-Solla, A. Optimizing reactive routing over virtual nodes in VANETs. IEEE Trans. Veh. Technol. 2015, 65, 2274–2294. [Google Scholar] [CrossRef]
- Xia, H.; Jia, Z.; Li, X.; Ju, L.; Sha, E.H.M. Trust prediction and trust-based source routing in mobile ad hoc networks. Ad Hoc Netw. 2013, 11, 2096–2114. [Google Scholar] [CrossRef]
- Xia, H.; Yu, J.; Tian, C.L.; Pan, Z.K.; Sha, E. Light-weight trust-enhanced on-demand multi-path routing in mobile ad hoc networks. J. Netw. Comput. Commun. 2016, 62, 112–127. [Google Scholar] [CrossRef]
- Li, X.; Lyu, M.R.; Liu, J. A trust model based routing protocol for secure ad hoc networks. In Proceedings of the IEEE Aerospace Conference Proceedings (IEEE Cat. No.04TH8720), Big Sky, MT, USA, 6–13 March 2004; pp. 1286–1295. [Google Scholar]
- Jøsang, A. A logic for uncertain probabilities. Fuzziness Knowl. Based Syst. 2001, 9, 279–311. [Google Scholar] [CrossRef]
- Yao, J.; Han, Z.; Sohail, M.; Wang, L. A Robust Security Architecture for SDN-Based 5G Networks. Future Internet 2019, 11, 85. [Google Scholar] [CrossRef]
- Pirzada, A.A.; Datta, A.; McDonald, C. Propagating trust in ad-hoc networks for reliable routing. In Proceedings of the International Workshop on Wireless Ad-Hoc Networks, Oulu, Finland, 31 May–3 June 2004; pp. 58–62. [Google Scholar]
- Fung, C.J.; Zhang, J.; Aib, I.; Boutaba, R. Dirichlet-based trust management for effective collaborative intrusion detection networks. IEEE Trans. Netw. Serv. Manag. 2011, 8, 79–91. [Google Scholar] [CrossRef]
- Cardoso, R.C.; Gomes, A.J.; Freire, M.M. A user trust system for online games—Part II: A subjective logic approach for trust inference. IEEE Trans. Comput. Intell. AI Games 2016, 9, 354–368. [Google Scholar] [CrossRef]
- Van, D.H.; Kargl, F.; Abu-Sharkh, O.M. Enhanced position verification for VIoT using subjective logic. In Proceedings of the IEEE 84th Vehicular Technology Conference (VTC-Fall), Montreal, QC, Canada, 18–21 September 2016; pp. 1–7. [Google Scholar]
- Sohail, M.; Wang, L.; Yamin, B. Trust model based uncertainty analysis between multi-path routes in MANET using subjective logic. In China Conference on Wireless Sensor Networks; Springer: Singapore, 2017; pp. 319–332. [Google Scholar]
- Sohail, M.; Wang, L.; Yamin, B. Trust mechanism based AODV routing protocol for forward node authentication in mobile ad hoc network. In International Conference on Mobile Ad-Hoc and Sensor Networks; Springer: Singapore, 2017; pp. 338–349. [Google Scholar]
- NS. The Network Simulator. Available online: http://www.isi.edu/nsnam/ns/ (accessed on 15 May 2020).
- Online. Advogato. Available online: http://konect.uni-koblenz.de/networks/advogato (accessed on 15 May 2020).
- Online. Pretty Good Privacy PGP. Available online: http://konect.uni-koblenz.de/networks/arenas-pgp (accessed on 15 May 2020).
- Golbeck, J.; Hendler, J. Filmtrust: Movie recommendations using trust in web-based social networks. In Proceedings of the IEEE Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 8–10 January 2006; pp. 282–286. [Google Scholar]
- Hang, C.W.; Wang, Y.; Singh, M.P. Operators for Propagating Trust and Their Evaluation in Social Networks; Dept. of Computer Science, North Carolina State University: Raleigh, NC, USA, 2008. [Google Scholar]
- Online. Python. Available online: http://www.python.org/ (accessed on 15 May 2020).
| Standard On-Demand Routing | Trust Enhanced Routing |
|---|---|
| Sending node IP address | Receiving node IP address |
| Sending node seq number | Receiving node seq number |
| ⋯ | ⋯ |
| hop count | same |
| ⋯ | ⋯ |
| Expire time | Expire time |
| ⋯ | Positive evidence (trust field) |
| ⋯ | Negative evidence (trust field) |
| ⋯ | Opinion metric |
| ⋯ | Trust update |
| >0.5 | Verify signature. | ||
| >0.5 | Distrust a vehicle till expiry time. | ||
| >0.5 | Trust a vehicle. | ||
| ≤0.5 | ≤0.5 | ≤0.5 | Request and verify authentication. |
| Examined Protocol | TER |
|---|---|
| Simulation time | 100 (s) |
| Number of nodes | 50 |
| Simulation area | 1000 m × 1000 m |
| Movement model | Random way point |
| Vehicle speed | 0~10 m/s |
| Transmission range | 250 m |
| Physical link bandwidth | 11 Mb |
| Traffic type | CBR/UDP |
| Packet size | 512 bytes |
| Connection rate | 4 pkt/s |
| Pause time | 5 s |
| Routing Attacks | Black Hole, On-off attack |
| Number of malicious nodes | 0~25 |
| Datasets | Vertices’s | Edges | Ave. Deg | Diameter |
|---|---|---|---|---|
| Advogato | 6542 | 51,227 | 19.5 | 4.83 |
| PGP | 10,682 | 24,315 | 24 | 4.52 |
| Trust Level | Trust Opinion | Trust Value |
|---|---|---|
| 1 | (0.08,0.82,0,0.1) | 0.08 |
| 2 | (0.26,0.64,0,0.1) | 0.26 |
| 3 | (0.63,0.27,0,0.1) | 0.63 |
| 4 | (0.85,0.05,0,0.1) | 0.85 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sohail, M.; Ali, R.; Kashif, M.; Ali, S.; Mehta, S.; Zikria, Y.B.; Yu, H. TrustWalker: An Efficient Trust Assessment in Vehicular Internet of Things (VIoT) with Security Consideration. Sensors 2020, 20, 3945. https://doi.org/10.3390/s20143945
Sohail M, Ali R, Kashif M, Ali S, Mehta S, Zikria YB, Yu H. TrustWalker: An Efficient Trust Assessment in Vehicular Internet of Things (VIoT) with Security Consideration. Sensors. 2020; 20(14):3945. https://doi.org/10.3390/s20143945
Chicago/Turabian StyleSohail, Muhammad, Rashid Ali, Muhammad Kashif, Sher Ali, Sumet Mehta, Yousaf Bin Zikria, and Heejung Yu. 2020. "TrustWalker: An Efficient Trust Assessment in Vehicular Internet of Things (VIoT) with Security Consideration" Sensors 20, no. 14: 3945. https://doi.org/10.3390/s20143945
APA StyleSohail, M., Ali, R., Kashif, M., Ali, S., Mehta, S., Zikria, Y. B., & Yu, H. (2020). TrustWalker: An Efficient Trust Assessment in Vehicular Internet of Things (VIoT) with Security Consideration. Sensors, 20(14), 3945. https://doi.org/10.3390/s20143945









